6c711b0cc82c5fb46e355d7a72709c10.ppt
- Количество слайдов: 15

Privilege and Policy Management for Cyber Infrastructures Dennis Kafura Markus Lorch Support provided by: March 14 -15, 2005 Commonwealth Security Information Center Fermi National Accelerator Laboratory IBM CSIIR Workshop 1

Organization ¨ Grand Challenges – Problems – Requirements ¨ PRIMA – a privilege-based approach – Models – Architecture/Mechanisms ¨ Research challenges – – Policy Obligations Enforcement Usability ¨ Relationship to I 3 P and Workshop Themes March 14 -15, 2004 CSIIR Workshop 2

Grand Challenge Problems ¨ Societal infrastructures “Develop tools and principles that allow construction of large-scale systems for important societal applications that are highly trustworthy despite being attractive targets. ” ¨ Dynamic, pervasive computing environments “For the dynamic, pervasive computing environments of the future, give computing end-users security they can understand privacy they can control. From: CRA Workshop on “Grand Research Challenges in Information Security and Assurance, ” November 2003. March 14 -15, 2004 CSIIR Workshop 3
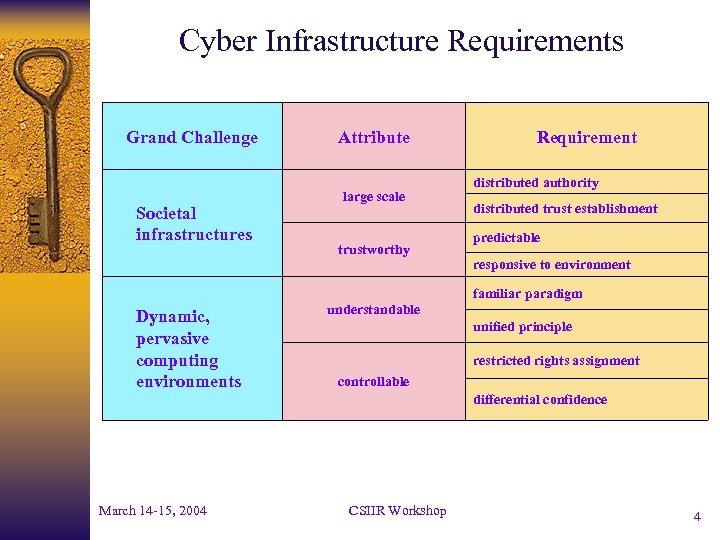
Cyber Infrastructure Requirements Grand Challenge Societal infrastructures Attribute large scale trustworthy Requirement distributed authority distributed trust establishment predictable responsive to environment familiar paradigm Dynamic, pervasive computing environments understandable unified principle restricted rights assignment controllable differential confidence March 14 -15, 2004 CSIIR Workshop 4
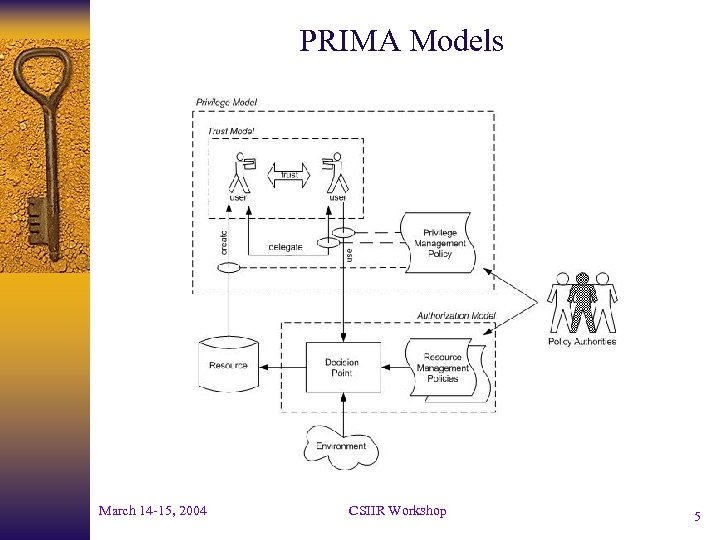
PRIMA Models March 14 -15, 2004 CSIIR Workshop 5
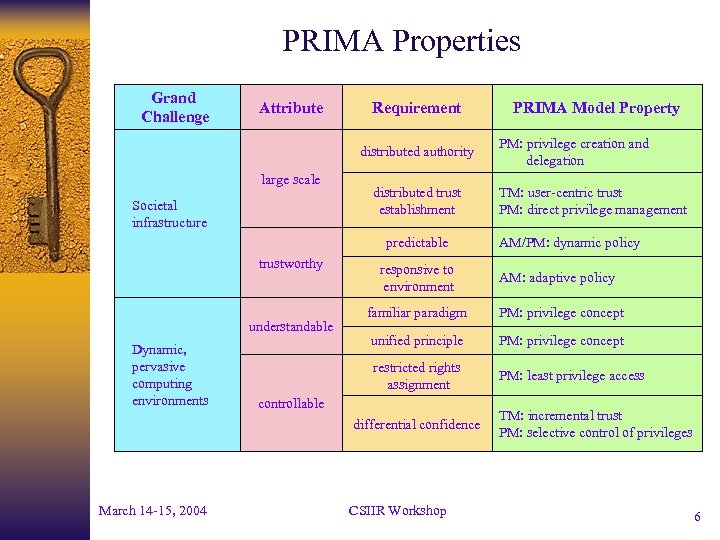
PRIMA Properties Grand Challenge Attribute Requirement distributed authority large scale Societal infrastructure distributed trust establishment predictable trustworthy TM: user-centric trust PM: direct privilege management AM/PM: dynamic policy AM: adaptive policy familiar paradigm PM: privilege concept unified principle PM: privilege concept PM: least privilege access controllable differential confidence March 14 -15, 2004 PM: privilege creation and delegation restricted rights assignment understandable Dynamic, pervasive computing environments responsive to environment PRIMA Model Property CSIIR Workshop TM: incremental trust PM: selective control of privileges 6
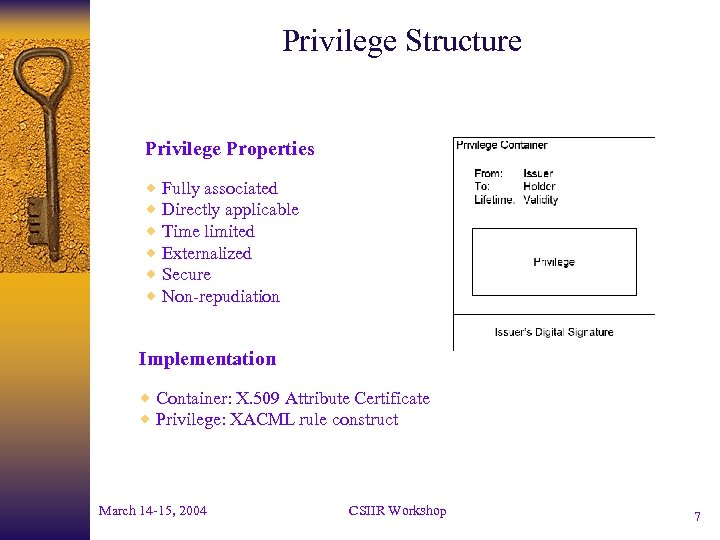
Privilege Structure Privilege Properties ® Fully associated ® Directly applicable ® Time limited ® Externalized ® Secure ® Non-repudiation Implementation ® Container: X. 509 Attribute Certificate ® Privilege: XACML rule construct March 14 -15, 2004 CSIIR Workshop 7
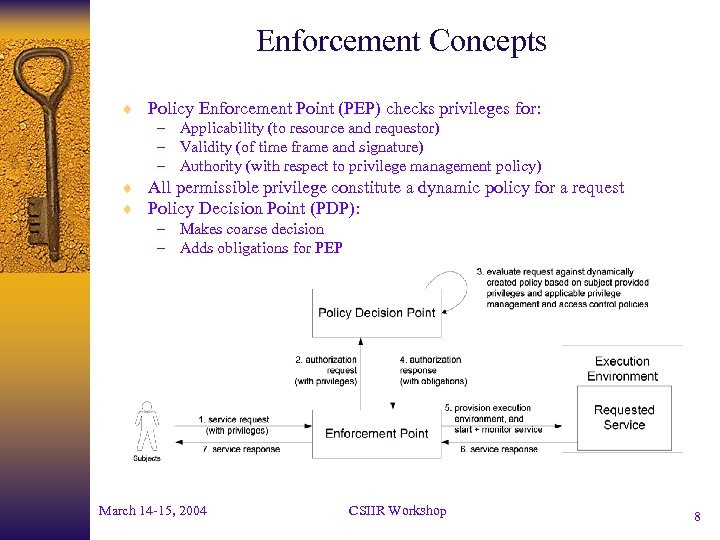
Enforcement Concepts ¨ Policy Enforcement Point (PEP) checks privileges for: – Applicability (to resource and requestor) – Validity (of time frame and signature) – Authority (with respect to privilege management policy) ¨ All permissible privilege constitute a dynamic policy for a request ¨ Policy Decision Point (PDP): – Makes coarse decision – Adds obligations for PEP March 14 -15, 2004 CSIIR Workshop 8
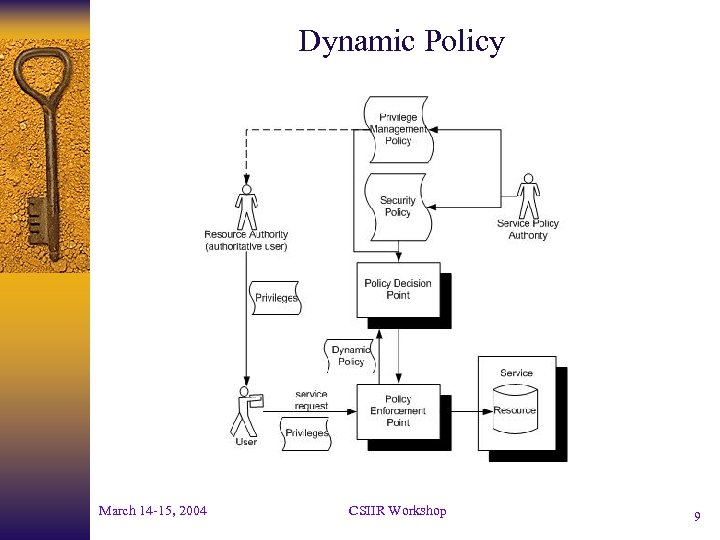
Dynamic Policy March 14 -15, 2004 CSIIR Workshop 9

Obligations ¨ Additional constraints to an authorization decision ¨ If PEP cannot fulfill an obligation then it disallows access ¨ Obligation address the mismatch in level of detail between request and policies ¨ Obligations help in maintaining system state March 14 -15, 2004 CSIIR Workshop 10

Research Challenges: Policy ¨ What can be adapted from software engineering research for policy: – Testing – Debugging – Formal Analysis – Requirements engineering ¨ Policy extensions – Threat/environment aware March 14 -15, 2004 CSIIR Workshop 11

Research Challenges: Obligations ¨ Granularity mismatch – Too many rights to be externalized – Partially addressed by dynamic policy ¨ With respect to the request – Need to add restrictions finer-grained than request March 14 -15, 2004 CSIIR Workshop 12

Research Challenges: Enforcement ¨ Evaluation of mechanisms – Dynamic user accounts – Virtual machine/sandboxing – Service containers ¨ Model – Distributing privileges to dynamically provision an execution environment, vs. – Pre-provisioning an execution environment and distributing a privilege for it March 14 -15, 2004 CSIIR Workshop 13

Research Challenges: Usability ¨ What are the right conceptual models? – Privileges – Roles – Others? Several? Combinations? ¨ How can users manage their rights? – P 3 P – Shibboleth release policies – Least-privilege control March 14 -15, 2004 CSIIR Workshop 14
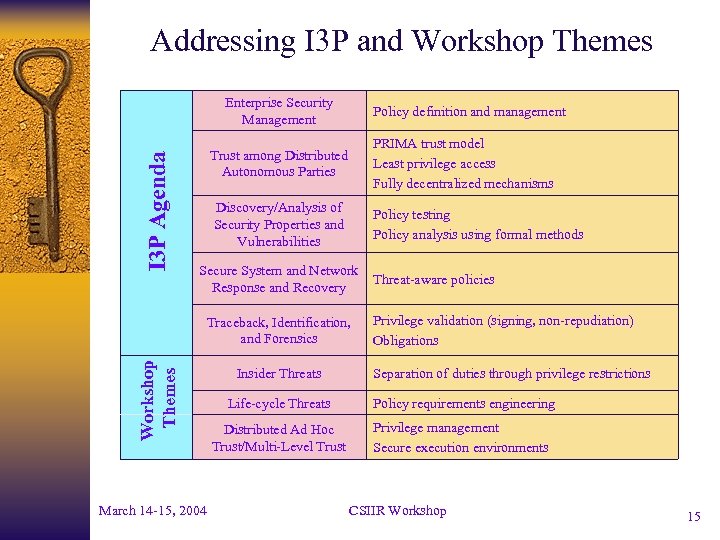
Addressing I 3 P and Workshop Themes I 3 P Agenda Enterprise Security Management Policy definition and management Trust among Distributed Autonomous Parties PRIMA trust model Least privilege access Fully decentralized mechanisms Discovery/Analysis of Security Properties and Vulnerabilities Policy testing Policy analysis using formal methods Secure System and Network Response and Recovery Workshop Themes Traceback, Identification, and Forensics March 14 -15, 2004 Insider Threats Threat-aware policies Privilege validation (signing, non-repudiation) Obligations Separation of duties through privilege restrictions Life-cycle Threats Policy requirements engineering Distributed Ad Hoc Trust/Multi-Level Trust Privilege management Secure execution environments CSIIR Workshop 15
6c711b0cc82c5fb46e355d7a72709c10.ppt