9e14b74621d98ec6794ef06e6f7be985.ppt
- Количество слайдов: 46
 Privacy in Computing CS 6 v 81. 504 January 23, 2006
Privacy in Computing CS 6 v 81. 504 January 23, 2006
![[Privacy] has become one of the most important human rights of the modern age. [Privacy] has become one of the most important human rights of the modern age.](https://present5.com/presentation/9e14b74621d98ec6794ef06e6f7be985/image-2.jpg) [Privacy] has become one of the most important human rights of the modern age. - Privacy. International. org
[Privacy] has become one of the most important human rights of the modern age. - Privacy. International. org
 Privacy • Privacy is protected in numerous international documents. – Austrian charter: “Privacy is a key value which underpins human dignity and other key values such as freedom of association and freedom of speech. . . Privacy is a basic human right and the reasonable expectation of every person. ”
Privacy • Privacy is protected in numerous international documents. – Austrian charter: “Privacy is a key value which underpins human dignity and other key values such as freedom of association and freedom of speech. . . Privacy is a basic human right and the reasonable expectation of every person. ”
 Aspects of Privacy • Information Privacy • Bodily Privacy – Genetic tests, drug tests, cavity searches • Privacy of Communications • Territorial Privacy – Searches, surveillance, and ID checks
Aspects of Privacy • Information Privacy • Bodily Privacy – Genetic tests, drug tests, cavity searches • Privacy of Communications • Territorial Privacy – Searches, surveillance, and ID checks
 Models of Privacy Protection • Comprehensive Laws • Sectoral Laws – United States (includes HIPAA, COPPA, etc) – The article looks down on this kind of privacy protection, allows for new sectors to form without privacy protection • Self-Regulation – Article places this as more of a “theory” • Technologies of Privacy
Models of Privacy Protection • Comprehensive Laws • Sectoral Laws – United States (includes HIPAA, COPPA, etc) – The article looks down on this kind of privacy protection, allows for new sectors to form without privacy protection • Self-Regulation – Article places this as more of a “theory” • Technologies of Privacy
 Privacy not a new issue… • Sweden – Access to Public Records Act (1776) • France – Prohibition of publication of private facts (1858) • Norway – Prohibited the publication of information related to “personal or domestic” affairs (1889)
Privacy not a new issue… • Sweden – Access to Public Records Act (1776) • France – Prohibition of publication of private facts (1858) • Norway – Prohibited the publication of information related to “personal or domestic” affairs (1889)
 “No one should be subjected to arbitrary interference with his privacy, family, home, or correspondence, nor to attacks on his honour or reputation. Everyone has the right to the protection of the law against such interferences or attacks. ” - Universal Declaration of Human Rights (1948)
“No one should be subjected to arbitrary interference with his privacy, family, home, or correspondence, nor to attacks on his honour or reputation. Everyone has the right to the protection of the law against such interferences or attacks. ” - Universal Declaration of Human Rights (1948)
 Enforcement • The International Covenant on Civil and Political Rights (ICCPR) • United Nations Convention on Migrant Workers • UN Convention on Protection of the Child • European Convention for the Protection of Human Rights and Fundamental Freedoms
Enforcement • The International Covenant on Civil and Political Rights (ICCPR) • United Nations Convention on Migrant Workers • UN Convention on Protection of the Child • European Convention for the Protection of Human Rights and Fundamental Freedoms
 HIPAA • Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) – Public Law 104 -191 (August 21, 1996)
HIPAA • Health Insurance Portability and Accountability Act of 1996 (“HIPAA”) – Public Law 104 -191 (August 21, 1996)
 HIPAA’s Privacy Regulations • HIPAA required that the Secretary of Health and Human Services (“HHS”) to issue privacy regulations if, and only if, Congress did not enact privacy legislation within three years of the passage of HIPAA. – Congress did not enact legislation
HIPAA’s Privacy Regulations • HIPAA required that the Secretary of Health and Human Services (“HHS”) to issue privacy regulations if, and only if, Congress did not enact privacy legislation within three years of the passage of HIPAA. – Congress did not enact legislation
 HHS’ Privacy Rule • Three years and three months after the passage of HIPAA, HHS developed a proposed Privacy Rule and released it for public comment. – 52, 000 public comments – Finalized on December 28, 2000.
HHS’ Privacy Rule • Three years and three months after the passage of HIPAA, HHS developed a proposed Privacy Rule and released it for public comment. – 52, 000 public comments – Finalized on December 28, 2000.
 HHS’ Privacy Rule Revisions • March 2002 Revision Proposal: – 11, 000 public comments – Adopted on August 14, 2002
HHS’ Privacy Rule Revisions • March 2002 Revision Proposal: – 11, 000 public comments – Adopted on August 14, 2002
 “Summary of the Privacy Rule” • HIPAA legislation passed by Congress contained a series of sections now known as the “Administrative Simplification provisions” – Under this provision, HHS is required to publish documents such at the “Summary of the Privacy Rule” which we read.
“Summary of the Privacy Rule” • HIPAA legislation passed by Congress contained a series of sections now known as the “Administrative Simplification provisions” – Under this provision, HHS is required to publish documents such at the “Summary of the Privacy Rule” which we read.
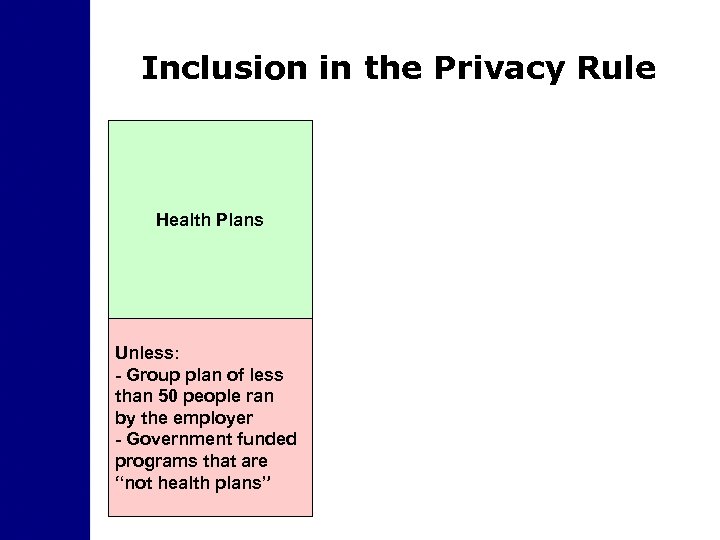 Inclusion in the Privacy Rule Health Plans Unless: - Group plan of less than 50 people ran by the employer - Government funded programs that are “not health plans”
Inclusion in the Privacy Rule Health Plans Unless: - Group plan of less than 50 people ran by the employer - Government funded programs that are “not health plans”
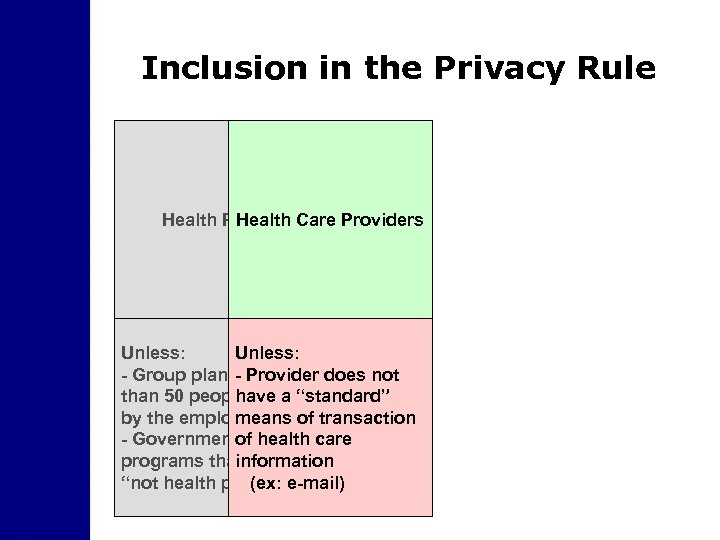 Inclusion in the Privacy Rule Health Plans Care Providers Health Unless: - Group plan of less - Provider does not than 50 people ran a “standard” have by the employer means of transaction - Governmentof health care funded programs that are information “not health plans” e-mail) (ex:
Inclusion in the Privacy Rule Health Plans Care Providers Health Unless: - Group plan of less - Provider does not than 50 people ran a “standard” have by the employer means of transaction - Governmentof health care funded programs that are information “not health plans” e-mail) (ex:
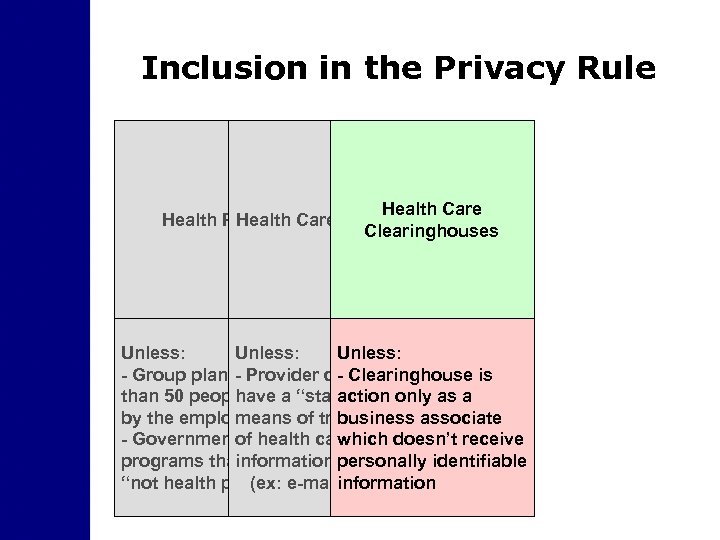 Inclusion in the Privacy Rule Health Care Health Plans Care Providers Health Clearinghouses Unless: - Group plan of less - Provider does not - Clearinghouse is than 50 people ran a “standard” only as a have action by the employer means of transaction associate business - Governmentof health care funded which doesn’t receive programs that are information personally identifiable “not health plans” e-mail) (ex: information
Inclusion in the Privacy Rule Health Care Health Plans Care Providers Health Clearinghouses Unless: - Group plan of less - Provider does not - Clearinghouse is than 50 people ran a “standard” only as a have action by the employer means of transaction associate business - Governmentof health care funded which doesn’t receive programs that are information personally identifiable “not health plans” e-mail) (ex: information
 Scope of PHI • An individuals past, present, or future: – Physical heath condition – Mental health condition – Payment of health care • An individual health care provision. …which there is a “reasonable basis to believe” the information is personally identifiable … which isn’t an employee record held by the company of employment
Scope of PHI • An individuals past, present, or future: – Physical heath condition – Mental health condition – Payment of health care • An individual health care provision. …which there is a “reasonable basis to believe” the information is personally identifiable … which isn’t an employee record held by the company of employment
 Principle of Disclosure • The Privacy Rule establishes a list of acceptable and unacceptable ways to use PHI. – Privacy Rule attempts to be a ‘catch-all’ law for privacy • The Privacy Rule may be waived by a signature of a patient. – Q: How many things do you sign when you go to the doctor? – Q: Do you know what they say? – Q: Do you really have a choice to not sign then?
Principle of Disclosure • The Privacy Rule establishes a list of acceptable and unacceptable ways to use PHI. – Privacy Rule attempts to be a ‘catch-all’ law for privacy • The Privacy Rule may be waived by a signature of a patient. – Q: How many things do you sign when you go to the doctor? – Q: Do you know what they say? – Q: Do you really have a choice to not sign then?
 Principle of Disclosure (Part 2) • The Privacy Rule does, however, ensure that individuals have access to the information stored about them. – Also allows HHS to view your medical records when they’re “undertaking a compliance investigation”
Principle of Disclosure (Part 2) • The Privacy Rule does, however, ensure that individuals have access to the information stored about them. – Also allows HHS to view your medical records when they’re “undertaking a compliance investigation”
 Explicitly Acceptable Disclosures • Disclosure to the individual (required) • Disclosure to: (allowed without consent) – Treatment Operations – Payment Operations – Health Care Operations
Explicitly Acceptable Disclosures • Disclosure to the individual (required) • Disclosure to: (allowed without consent) – Treatment Operations – Payment Operations – Health Care Operations
 Explicitly Acceptable Disclosures • Disclosures with “Opportunity to Object” – Ex: Directory of patients – Ex: Notifications • Family Members • Pharmacies • Law Enforcement (disaster relief, epidemic, etc) • Incidental disclosures – Disclosure as a result of a previous disclosure
Explicitly Acceptable Disclosures • Disclosures with “Opportunity to Object” – Ex: Directory of patients – Ex: Notifications • Family Members • Pharmacies • Law Enforcement (disaster relief, epidemic, etc) • Incidental disclosures – Disclosure as a result of a previous disclosure
 Explicitly Acceptable Disclosures • Disclosure in Public Interest and Benefit Activities – Public Health (prevention or containment of a disease) – Employees where transmission of a dangerous disease was likely – Victims of abuse, neglect, violence, etc – Heath oversight activates and judicial proceedings
Explicitly Acceptable Disclosures • Disclosure in Public Interest and Benefit Activities – Public Health (prevention or containment of a disease) – Employees where transmission of a dangerous disease was likely – Victims of abuse, neglect, violence, etc – Heath oversight activates and judicial proceedings
 Explicitly Acceptable Disclosures • Disclosure in Public Interest and Benefit Activities (cont’d) – Law enforcement purposes – Decedents – Organ, eye, tissue donations – Research purposes – Serious threat to public safety – … and more…
Explicitly Acceptable Disclosures • Disclosure in Public Interest and Benefit Activities (cont’d) – Law enforcement purposes – Decedents – Organ, eye, tissue donations – Research purposes – Serious threat to public safety – … and more…
 Authorized Uses and Disclosures • All other uses and disclosures of data but have explicit written authorization by the individual. – Q: Again, how many things do you sign when you go into a doctor for the first time?
Authorized Uses and Disclosures • All other uses and disclosures of data but have explicit written authorization by the individual. – Q: Again, how many things do you sign when you go into a doctor for the first time?
 Authorized Uses and Disclosures • Given examples: – Psychotherapy notes – Marketing – etc
Authorized Uses and Disclosures • Given examples: – Psychotherapy notes – Marketing – etc
 “Minimum Necessary” Clause • One of the central aspects of the entire Privacy Rule is that only the minimally necessary amount of PHI is disclosed.
“Minimum Necessary” Clause • One of the central aspects of the entire Privacy Rule is that only the minimally necessary amount of PHI is disclosed.
 “Minimum Necessary” Clause • However, the minimum necessary clause does not cover: – Health care providers for treatment – Individuals who is the subject of the information – Disclosures made pursuant to an authorization – Disclosure to HHS or required by law – Disclosure for HIPAA compliance reviews
“Minimum Necessary” Clause • However, the minimum necessary clause does not cover: – Health care providers for treatment – Individuals who is the subject of the information – Disclosures made pursuant to an authorization – Disclosure to HHS or required by law – Disclosure for HIPAA compliance reviews
 Other Privacy Rule Conditions • Privacy Practice Notices – Provides the “privacy policy” of the health care institution – Must be easily accessible and a receipt (signature) must be on file from every patient that they had the chance to review the notice • Patient’s right to knowledge of disclosure, with cetain limitations.
Other Privacy Rule Conditions • Privacy Practice Notices – Provides the “privacy policy” of the health care institution – Must be easily accessible and a receipt (signature) must be on file from every patient that they had the chance to review the notice • Patient’s right to knowledge of disclosure, with cetain limitations.
 Other Privacy Rule Conditions • Confidential Communications – An individual may request communications be made only at a specific telephone number or a specific address. – Furthermore, they may request that information is sent in sealed envelopes rather than postcards or other unsecured mail
Other Privacy Rule Conditions • Confidential Communications – An individual may request communications be made only at a specific telephone number or a specific address. – Furthermore, they may request that information is sent in sealed envelopes rather than postcards or other unsecured mail
 Penalties • HHS may impose monetary civil penalties for violations of the Privacy Rule: – $100 per failure to comply with a Privacy Rule requirement (up to $25, 000/yr/company for violations of the same Privacy Rule requirement)
Penalties • HHS may impose monetary civil penalties for violations of the Privacy Rule: – $100 per failure to comply with a Privacy Rule requirement (up to $25, 000/yr/company for violations of the same Privacy Rule requirement)
 Penalties • Criminal Penalties – Any person (a physical person or an incorporated company) who knowingly obtains or discloses PHI is in violation of HIPAA and faces: • Up to a $50, 000 fine • Up to a one-year prison term – An intention to sell, transfer, or use PHI increase both the fine and the prison term
Penalties • Criminal Penalties – Any person (a physical person or an incorporated company) who knowingly obtains or discloses PHI is in violation of HIPAA and faces: • Up to a $50, 000 fine • Up to a one-year prison term – An intention to sell, transfer, or use PHI increase both the fine and the prison term
 Rational for Adopting Comprehensive Privacy Laws… • To remedy past injustices • To promote electronic commerce – “These countries recognize that consumers are uneasy with the increased availability of their personal data, particularly with new means of identification and forms of transactions. ” • To ensure laws are consistent with Pan-European laws
Rational for Adopting Comprehensive Privacy Laws… • To remedy past injustices • To promote electronic commerce – “These countries recognize that consumers are uneasy with the increased availability of their personal data, particularly with new means of identification and forms of transactions. ” • To ensure laws are consistent with Pan-European laws
 Oversight of Privacy • EU Solution: – Leave it to the individual countries to have an independent enforcement body. – Often falls under the department which handles “freedom of information” in countries which do not adopt comprehensive laws
Oversight of Privacy • EU Solution: – Leave it to the individual countries to have an independent enforcement body. – Often falls under the department which handles “freedom of information” in countries which do not adopt comprehensive laws
 Oversight isn’t easy… • • Small budget Budget cuts Too few staffers Too many complaints
Oversight isn’t easy… • • Small budget Budget cuts Too few staffers Too many complaints
 “Data Havens” • Idea: If privacy laws prevents a person from storing the information they gather, why not ship it overseas? – Privacy laws now control the exporting of data. – Europe Directive (next slide)
“Data Havens” • Idea: If privacy laws prevents a person from storing the information they gather, why not ship it overseas? – Privacy laws now control the exporting of data. – Europe Directive (next slide)
 “Data Havens” • Europe Directive: – “The Member States shall provide that the transfer to a third country of personal data which are undergoing processing or are intended for processing after transfer may take place only if the third country in question ensures an adequate level of protection. ” – Q: Who defines adequate? – Q: What should that standard be?
“Data Havens” • Europe Directive: – “The Member States shall provide that the transfer to a third country of personal data which are undergoing processing or are intended for processing after transfer may take place only if the third country in question ensures an adequate level of protection. ” – Q: Who defines adequate? – Q: What should that standard be?
 Safe Harbor Agreement • Negotiations between the US and the EU to ensure that the United States has “adequate” privacy safegaurds. – Requires all signatory organizations “clear and conspicuous” notices of the kinds of information they collect, the purpose of what it’s used, and any third parties of whom the information might be disclosed to. – If information will be disclosed to a third party, an individual must be able to optout of that information collection.
Safe Harbor Agreement • Negotiations between the US and the EU to ensure that the United States has “adequate” privacy safegaurds. – Requires all signatory organizations “clear and conspicuous” notices of the kinds of information they collect, the purpose of what it’s used, and any third parties of whom the information might be disclosed to. – If information will be disclosed to a third party, an individual must be able to optout of that information collection.
 Safe Harbor Agreement • … even more provisions … – “Sensitive” information requires that an individual opts-in to the collection and distribution to a third party. – And in any case, the third party must be a signatory of the Safe Harbor Agreement. – Originations must take measures to protect safety of the data, ability individuals must be able to to correct, amend, and delete inaccurate information.
Safe Harbor Agreement • … even more provisions … – “Sensitive” information requires that an individual opts-in to the collection and distribution to a third party. – And in any case, the third party must be a signatory of the Safe Harbor Agreement. – Originations must take measures to protect safety of the data, ability individuals must be able to to correct, amend, and delete inaccurate information.
 Problems with Safe Harbor… • Self-regulator • Non-transparent • EU Commission in 2002 looked into its success – Found that it helped protect privacy, but found numerous problems – Full report was due out in 2003 • Shamed the United States • Didn’t reach far enough to end the Safe Harbor Agreement
Problems with Safe Harbor… • Self-regulator • Non-transparent • EU Commission in 2002 looked into its success – Found that it helped protect privacy, but found numerous problems – Full report was due out in 2003 • Shamed the United States • Didn’t reach far enough to end the Safe Harbor Agreement
 “There are three elements in privacy: secrecy, anonymity and solitude. It is a state which can be lost, whether through the choice of the person in that state or through the action of another person” - Ruth Gavison (Israel Democracy Institute)
“There are three elements in privacy: secrecy, anonymity and solitude. It is a state which can be lost, whether through the choice of the person in that state or through the action of another person” - Ruth Gavison (Israel Democracy Institute)
 Article 2: Who wrote it? • Privacy International – Privacy International (PI) is a human rights group formed in 1990 as a watchdog on surveillance and privacy invasions by governments and corporations. PI is based in London, England, and has an office in Washington, D. C. PI has conducted campaigns and research throughout the world on issues ranging from wiretapping and national security, to ID cards, video surveillance, data matching, medical privacy, and freedom of information and expression.
Article 2: Who wrote it? • Privacy International – Privacy International (PI) is a human rights group formed in 1990 as a watchdog on surveillance and privacy invasions by governments and corporations. PI is based in London, England, and has an office in Washington, D. C. PI has conducted campaigns and research throughout the world on issues ranging from wiretapping and national security, to ID cards, video surveillance, data matching, medical privacy, and freedom of information and expression.
 Article 1: What’s in HIPAA that’s not in the Privacy Rule? • Title I of HIPAA protects health insurance coverage for workers and their families when they change or lose their jobs. – Source: Centers for Medicare and Medicaid Services' (CMS)
Article 1: What’s in HIPAA that’s not in the Privacy Rule? • Title I of HIPAA protects health insurance coverage for workers and their families when they change or lose their jobs. – Source: Centers for Medicare and Medicaid Services' (CMS)
 Article 1: What’s in HIPAA that’s not in the Privacy Rule? • Title II requires the establishment of national standards for electronic health care transactions and national identifiers for providers, health insurance plans, and employers.
Article 1: What’s in HIPAA that’s not in the Privacy Rule? • Title II requires the establishment of national standards for electronic health care transactions and national identifiers for providers, health insurance plans, and employers.
 HIPAA • “As a matter of linguistic-political criticism, many have noted that the Act did little to actually make health insurance more "portable" in the sense of preserving access to health care when an individual changes employers. Also, despite its many new rules on the sharing of medical information, the Act did not significantly increase health insurers' "accountability" for wrongdoing. ” – Wiki. Pedia
HIPAA • “As a matter of linguistic-political criticism, many have noted that the Act did little to actually make health insurance more "portable" in the sense of preserving access to health care when an individual changes employers. Also, despite its many new rules on the sharing of medical information, the Act did not significantly increase health insurers' "accountability" for wrongdoing. ” – Wiki. Pedia
 HIPAA • New York Times (April 21, 2005) – Author writes and asks the reader to imagine a hospital stay today and a hospital stay a year and a half from now. – Claims that the hospital stay today would be like the stay a year and a half from now if HIPAA wasn’t “forced” upon the “already overburdened” healthcare industry
HIPAA • New York Times (April 21, 2005) – Author writes and asks the reader to imagine a hospital stay today and a hospital stay a year and a half from now. – Claims that the hospital stay today would be like the stay a year and a half from now if HIPAA wasn’t “forced” upon the “already overburdened” healthcare industry
 HIPAA • The article we read came from the government, covers only the Privacy Rule, and doesn’t look at enforcement issues or its actual application to society.
HIPAA • The article we read came from the government, covers only the Privacy Rule, and doesn’t look at enforcement issues or its actual application to society.


