206593637dca365de7e24a534a34b0a1.ppt
- Количество слайдов: 20
 Preventing Insider Threats: Avoiding the Nightmare Scenario of a Good Employee Gone Bad Dawn Cappelli October 31, 2008 © 2008 Carnegie Mellon University
Preventing Insider Threats: Avoiding the Nightmare Scenario of a Good Employee Gone Bad Dawn Cappelli October 31, 2008 © 2008 Carnegie Mellon University
 TRUE STORY: Personal information stolen for millions of customers of phone companies, credit card companies and banks … Companies contracted with a consumer data organization that hired a data mining organization whose system administrator stole the data 2
TRUE STORY: Personal information stolen for millions of customers of phone companies, credit card companies and banks … Companies contracted with a consumer data organization that hired a data mining organization whose system administrator stole the data 2
 TRUE STORY: Emergency services are forced to rely on manual address lookups for 911 calls on Friday night …. Employee sabotages the system and steals all backup tapes 3
TRUE STORY: Emergency services are forced to rely on manual address lookups for 911 calls on Friday night …. Employee sabotages the system and steals all backup tapes 3
 TRUE STORY: Financial institution discovers $691 million in losses. . . Covered up for 5 years by trusted employee 4
TRUE STORY: Financial institution discovers $691 million in losses. . . Covered up for 5 years by trusted employee 4
 Agenda Introduction How bad is the insider threat? Background on CERT’s insider threat research Brief overview of findings from our research Tools for preventing or detecting insider threats 5
Agenda Introduction How bad is the insider threat? Background on CERT’s insider threat research Brief overview of findings from our research Tools for preventing or detecting insider threats 5
 What is CERT? Center of Internet security expertise Established in 1988 by the US Department of Defense on the heels of the Morris worm that created havoc on the ARPANET, the precursor to what is the Internet today Located in the Software Engineering Institute (SEI) • Federally Funded Research & Development Center (FFRDC) • Operated by Carnegie Mellon University (Pittsburgh, Pennsylvania) 6
What is CERT? Center of Internet security expertise Established in 1988 by the US Department of Defense on the heels of the Morris worm that created havoc on the ARPANET, the precursor to what is the Internet today Located in the Software Engineering Institute (SEI) • Federally Funded Research & Development Center (FFRDC) • Operated by Carnegie Mellon University (Pittsburgh, Pennsylvania) 6
 CERT’s Definition of Malicious Insider Current or former employee, contractor, or business partner who o has or had authorized access to an organization’s network, system or data and o intentionally exceeded or misused that access in a manner that o negatively affected the confidentiality, integrity, or availability of the organization’s information or information systems. Note: This presentation does not address national security espionage involving classified information. 7
CERT’s Definition of Malicious Insider Current or former employee, contractor, or business partner who o has or had authorized access to an organization’s network, system or data and o intentionally exceeded or misused that access in a manner that o negatively affected the confidentiality, integrity, or availability of the organization’s information or information systems. Note: This presentation does not address national security espionage involving classified information. 7
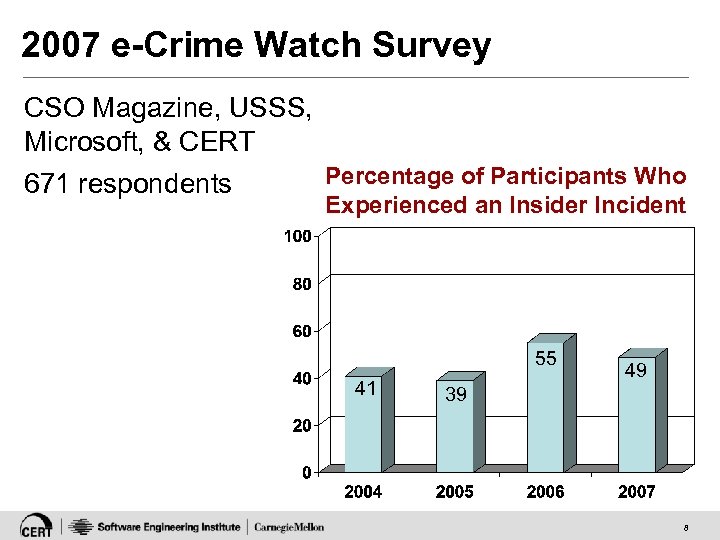 2007 e-Crime Watch Survey CSO Magazine, USSS, Microsoft, & CERT 671 respondents Percentage of Participants Who Experienced an Insider Incident 55 41 49 39 8
2007 e-Crime Watch Survey CSO Magazine, USSS, Microsoft, & CERT 671 respondents Percentage of Participants Who Experienced an Insider Incident 55 41 49 39 8
 CERT’s Insider Threat Research Insider Threat Cases Hundreds of cases have been analyzed • US cases from 1996 to 2007 in critical infrastructure sectors • US Secret Service • Carnegie Mellon Cy. Lab • Department of Defense Database Data includes both technical & behavioral information 9
CERT’s Insider Threat Research Insider Threat Cases Hundreds of cases have been analyzed • US cases from 1996 to 2007 in critical infrastructure sectors • US Secret Service • Carnegie Mellon Cy. Lab • Department of Defense Database Data includes both technical & behavioral information 9
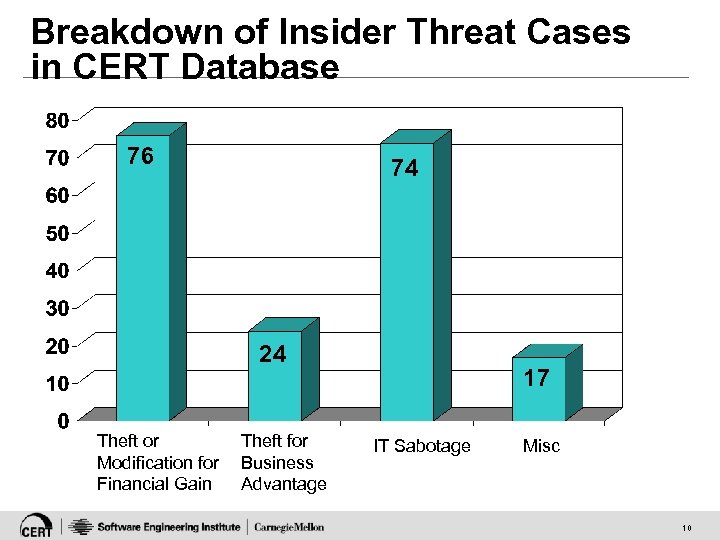 Breakdown of Insider Threat Cases in CERT Database 76 74 24 Theft or Modification for Financial Gain Theft for Business Advantage 17 IT Sabotage Misc 10
Breakdown of Insider Threat Cases in CERT Database 76 74 24 Theft or Modification for Financial Gain Theft for Business Advantage 17 IT Sabotage Misc 10
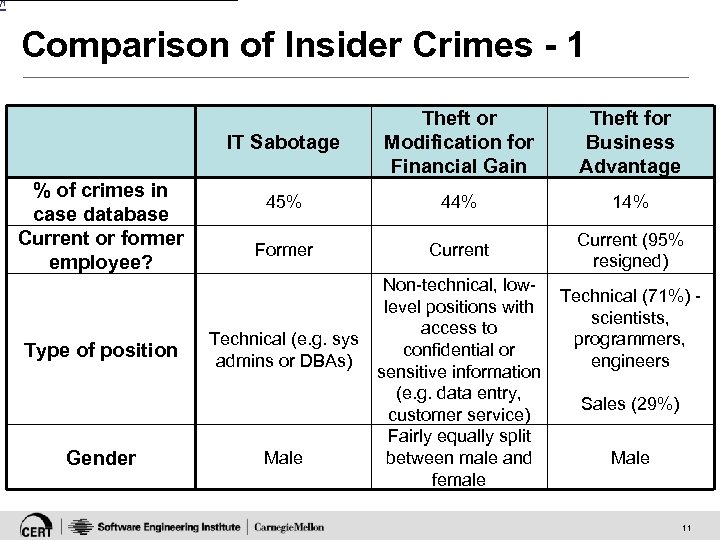 [1 Comparison of Insider Crimes - 1 IT Sabotage % of crimes in case database Current or former employee? Type of position Gender Theft or Modification for Financial Gain Theft for Business Advantage 45% 44% 14% Former Current (95% resigned) Technical (e. g. sys admins or DBAs) Male Non-technical, lowlevel positions with access to confidential or sensitive information (e. g. data entry, customer service) Fairly equally split between male and female Technical (71%) scientists, programmers, engineers Sales (29%) Male 11
[1 Comparison of Insider Crimes - 1 IT Sabotage % of crimes in case database Current or former employee? Type of position Gender Theft or Modification for Financial Gain Theft for Business Advantage 45% 44% 14% Former Current (95% resigned) Technical (e. g. sys admins or DBAs) Male Non-technical, lowlevel positions with access to confidential or sensitive information (e. g. data entry, customer service) Fairly equally split between male and female Technical (71%) scientists, programmers, engineers Sales (29%) Male 11
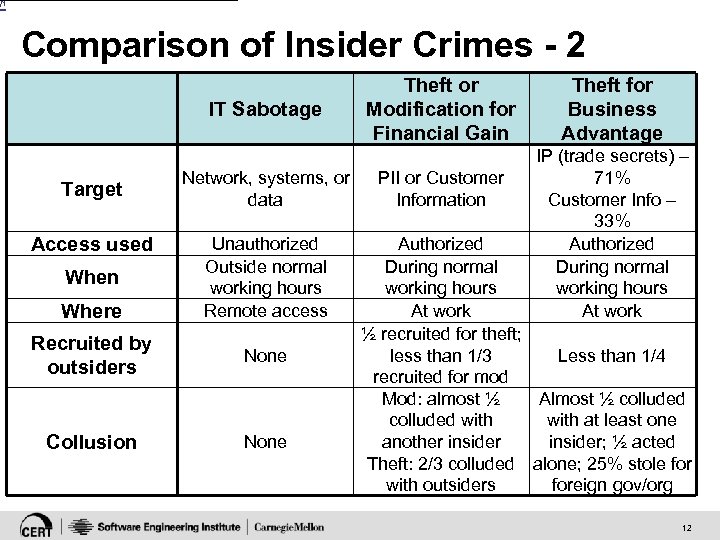 [1 Comparison of Insider Crimes - 2 IT Sabotage Target Access used When Where Network, systems, or data Unauthorized Outside normal working hours Remote access Recruited by outsiders None Collusion None Theft or Modification for Financial Gain PII or Customer Information Theft for Business Advantage IP (trade secrets) – 71% Customer Info – 33% Authorized During normal working hours At work ½ recruited for theft; less than 1/3 Less than 1/4 recruited for mod Mod: almost ½ Almost ½ colluded with at least one another insider; ½ acted Theft: 2/3 colluded alone; 25% stole for with outsiders foreign gov/org 12
[1 Comparison of Insider Crimes - 2 IT Sabotage Target Access used When Where Network, systems, or data Unauthorized Outside normal working hours Remote access Recruited by outsiders None Collusion None Theft or Modification for Financial Gain PII or Customer Information Theft for Business Advantage IP (trade secrets) – 71% Customer Info – 33% Authorized During normal working hours At work ½ recruited for theft; less than 1/3 Less than 1/4 recruited for mod Mod: almost ½ Almost ½ colluded with at least one another insider; ½ acted Theft: 2/3 colluded alone; 25% stole for with outsiders foreign gov/org 12
 What Can You Do? Review CERT’s Common Sense Guide to Prevention and Detection of Insider Threats http: //www. cert. org/archive/pdf/Common. Sense. Insider Threats. V 2. 1 -1 -070118. pdf Version 3 to be published in January 2009 13
What Can You Do? Review CERT’s Common Sense Guide to Prevention and Detection of Insider Threats http: //www. cert. org/archive/pdf/Common. Sense. Insider Threats. V 2. 1 -1 -070118. pdf Version 3 to be published in January 2009 13
 Tools for Preventing or Detecting Insider Threats 14
Tools for Preventing or Detecting Insider Threats 14
 Change Control Help to prevent or detect Planting or downloading of malicious code or unauthorized software • Unauthorized modification of critical files • Unauthorized changes to source code • Unauthorized installation of hardware devices • 15
Change Control Help to prevent or detect Planting or downloading of malicious code or unauthorized software • Unauthorized modification of critical files • Unauthorized changes to source code • Unauthorized installation of hardware devices • 15
 Data Leakage Tools Help to prevent or detect accidental or intentional leakage of confidential information Emails • Documents • Printing, copying, or downloading • Removable media • 16
Data Leakage Tools Help to prevent or detect accidental or intentional leakage of confidential information Emails • Documents • Printing, copying, or downloading • Removable media • 16
 Network/Employee Monitoring Tools Help to detect • Unauthorized access • Suspicious activity around resignation • Unauthorized escalation of privileges • Anomalous user activity 17
Network/Employee Monitoring Tools Help to detect • Unauthorized access • Suspicious activity around resignation • Unauthorized escalation of privileges • Anomalous user activity 17
 Identity Management Systems Help to • • • Prevent creation of or detect usage of backdoor accounts Implement and maintain access control Disable all access upon termination 18
Identity Management Systems Help to • • • Prevent creation of or detect usage of backdoor accounts Implement and maintain access control Disable all access upon termination 18
 Others Encryption Physical access control systems Automated data integrity checks Backup and recovery systems 19
Others Encryption Physical access control systems Automated data integrity checks Backup and recovery systems 19
 Contact Information Insider Threat Team Lead: Dawn M. Cappelli Technical Manager, Threat and Incident Management CERT Program Software Engineering Institute Carnegie Mellon University 4500 Fifth Avenue Pittsburgh, PA 15213 -3890 +1 412 268 -9136 – Phone dmc@cert. org – Email http: //www. cert. org/insider_threat/ 20
Contact Information Insider Threat Team Lead: Dawn M. Cappelli Technical Manager, Threat and Incident Management CERT Program Software Engineering Institute Carnegie Mellon University 4500 Fifth Avenue Pittsburgh, PA 15213 -3890 +1 412 268 -9136 – Phone dmc@cert. org – Email http: //www. cert. org/insider_threat/ 20


