d029d7de11cdf7643e4b46c293b26797.ppt
- Количество слайдов: 47

PRESENT AND FUTURE STANDARDS FOR MOBILE INTERNET AND SMART PHONE INFORMATION SECURITY Presented by Alain Sultan © ETSI 2012. All rights reserved for MIIT and TMC visit to ETSI - September 2012

Mobile Internet and Smart Phone Mobile Internet security: not addressed by 3 GPP • Mobile IP refers to extensions of IP as to be able to address mobility • But the system defined by 3 GPP is mobile by nature, so there is no need for these extensions Smart Phone security: not addressed by 3 GPP • 3 GPP defines Interfaces • The internal design of whatever system component (Mobile, Node B, MSC, etc. ) is up to each manufacturer But Security is a major topic of 3 GPP specifications, from the first phase of GSM (2 G) until the latest phase of LTE (4 G) • This is what this set of slides addresses

Standards for 2 G/3 G security
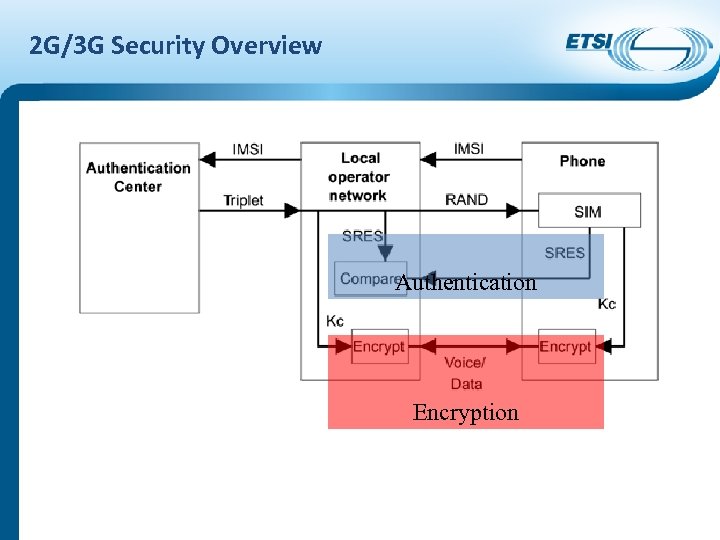
2 G/3 G Security Overview Authentication Encryption
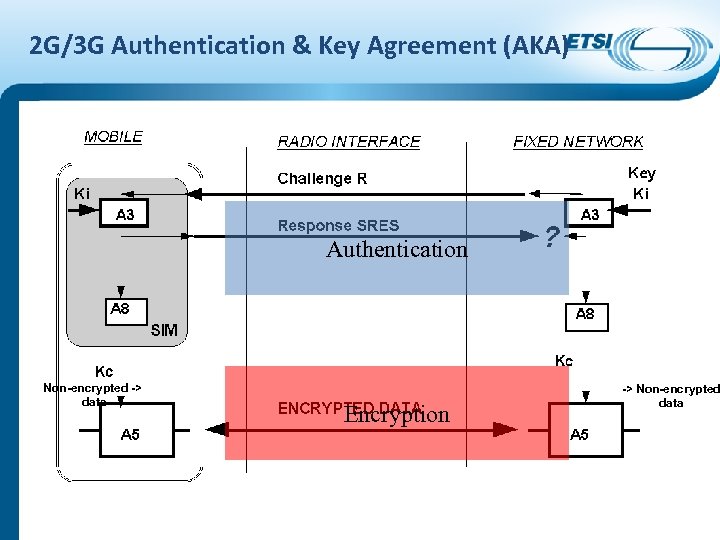
2 G/3 G Authentication & Key Agreement (AKA) Authentication Non-encrypted -> data Encryption -> Non-encrypted data
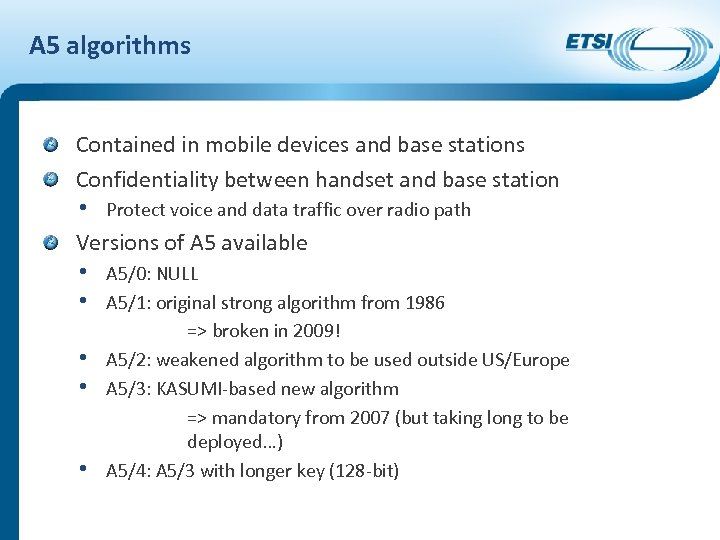
A 5 algorithms Contained in mobile devices and base stations Confidentiality between handset and base station • Protect voice and data traffic over radio path Versions of A 5 available • A 5/0: NULL • A 5/1: original strong algorithm from 1986 • • • => broken in 2009! A 5/2: weakened algorithm to be used outside US/Europe A 5/3: KASUMI-based new algorithm => mandatory from 2007 (but taking long to be deployed…) A 5/4: A 5/3 with longer key (128 -bit)

Standards for LTE security

LTE Security Characteristics of LTE Security • Re-use of UMTS Authentication and Key Agreement (AKA) • Use of USIM required (GSM SIM excluded, but Rel-99 USIM is • • sufficient) Extended key hierarchy Possibility for longer keys Greater protection for backhaul Integrated interworking security for legacy and non-3 GPP networks
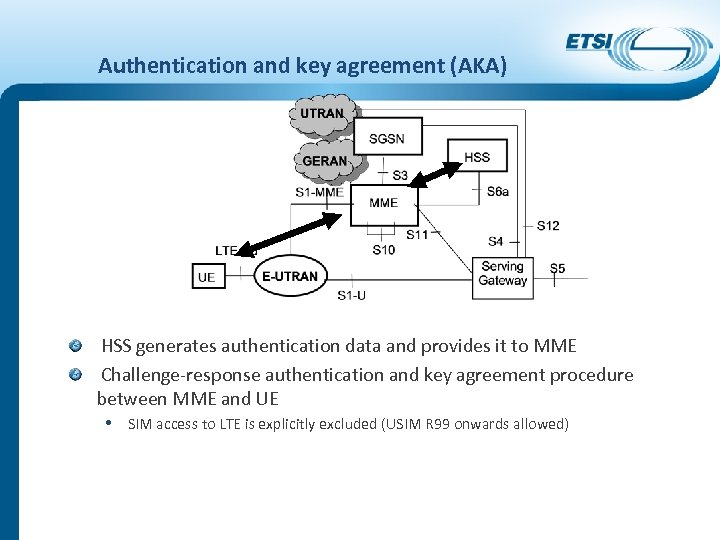
Authentication and key agreement (AKA) HSS generates authentication data and provides it to MME Challenge-response authentication and key agreement procedure between MME and UE • SIM access to LTE is explicitly excluded (USIM R 99 onwards allowed)
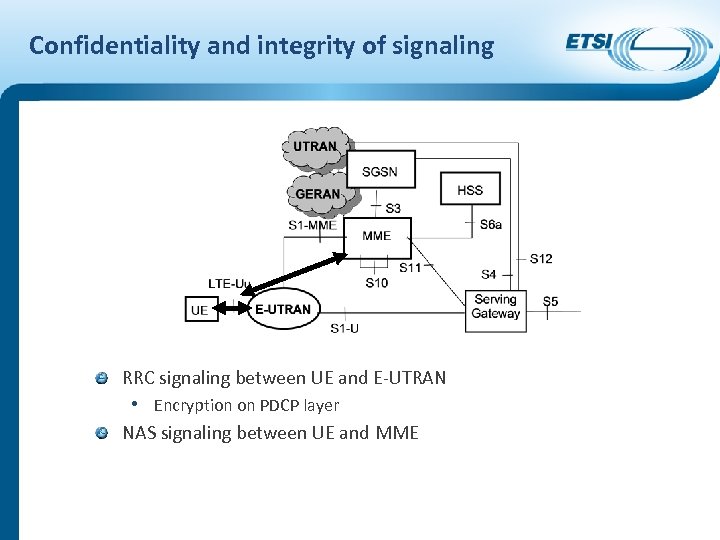
Confidentiality and integrity of signaling RRC signaling between UE and E-UTRAN • Encryption on PDCP layer NAS signaling between UE and MME
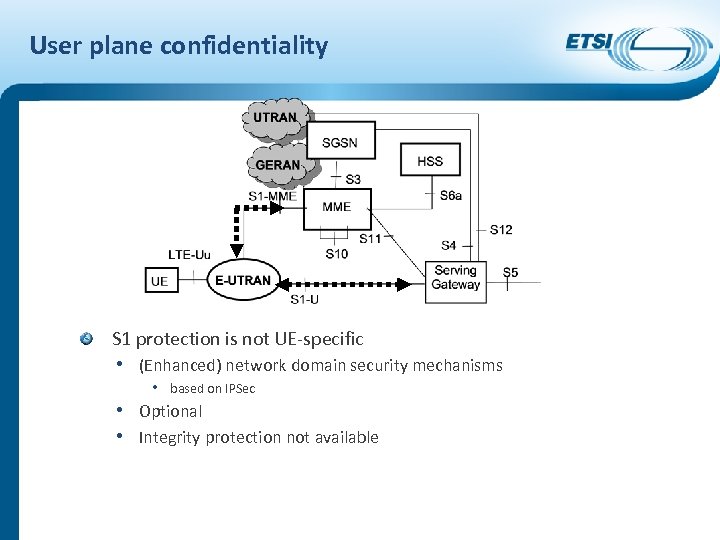
User plane confidentiality S 1 protection is not UE-specific • (Enhanced) network domain security mechanisms • • • based on IPSec Optional Integrity protection not available
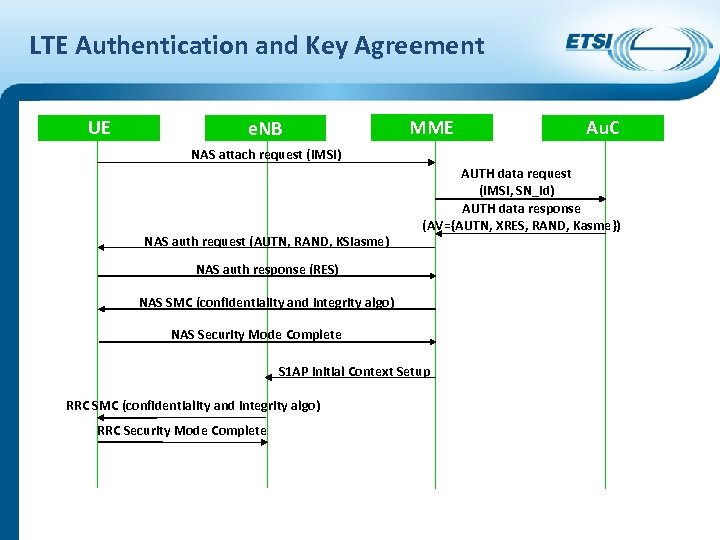
LTE Authentication and Key Agreement UE e. NB MME Au. C NAS attach request (IMSI) NAS auth request (AUTN, RAND, KSIasme) AUTH data request (IMSI, SN_id) AUTH data response (AV={AUTN, XRES, RAND, Kasme}) NAS auth response (RES) NAS SMC (confidentiality and integrity algo) NAS Security Mode Complete S 1 AP Initial Context Setup RRC SMC (confidentiality and integrity algo) RRC Security Mode Complete

Indication of access network encryption • user is informed whether confidentiality of user data is protected on the radio access link • in particular when non-ciphered calls are set-up

Security Algorithms

LTE Security Algorithms (1/2) Three separate algorithms specified • In addition to one NULL algorithm Current keylength 128 bits • Possibility to extend to 256 in the future Confidentiality protection of NAS/AS signalling recommended Integrity protection of NAS/AS signalling mandatory User data confidentiality protection recommended Ciphering/Deciphering applied on PDCP and NAS
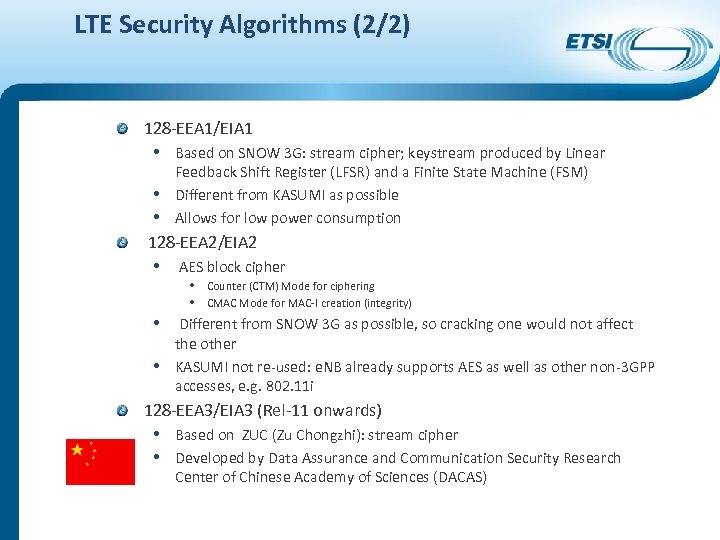
LTE Security Algorithms (2/2) 128 -EEA 1/EIA 1 • Based on SNOW 3 G: stream cipher; keystream produced by Linear • • Feedback Shift Register (LFSR) and a Finite State Machine (FSM) Different from KASUMI as possible Allows for low power consumption 128 -EEA 2/EIA 2 • AES block cipher • Counter (CTM) Mode for ciphering • CMAC Mode for MAC-I creation (integrity) • Different from SNOW 3 G as possible, so cracking one would not affect • the other KASUMI not re-used: e. NB already supports AES as well as other non-3 GPP accesses, e. g. 802. 11 i 128 -EEA 3/EIA 3 (Rel-11 onwards) • Based on ZUC (Zu Chongzhi): stream cipher • Developed by Data Assurance and Communication Security Research Center of Chinese Academy of Sciences (DACAS)

Lawful Interception
Lawful Interception in 3 GPP Cost Political Interception Business Retrieval Handover Analysis process Relations Storage Legal
Lawful Interception in EPS Context and mechanisms similar to case of UMTS PS • Different core entities (ICE, Intercepting Control Elements) • ADMF handles requests from Law Enforcement Authorities • • • target identity: IMSI, MSISDN and IMEI X 1 interface provisions ICEs and Delivery Functions X 2 delivers IRI (Intercept Related Information) X 3 delivers CC (Content of Communication) HI 1, 2, 3: Handover Interfaces with law enforcement • Convey requests for interception of targets (HI 1) • Deliver IRI (HI 2) and CC (HI 3) to LEAs
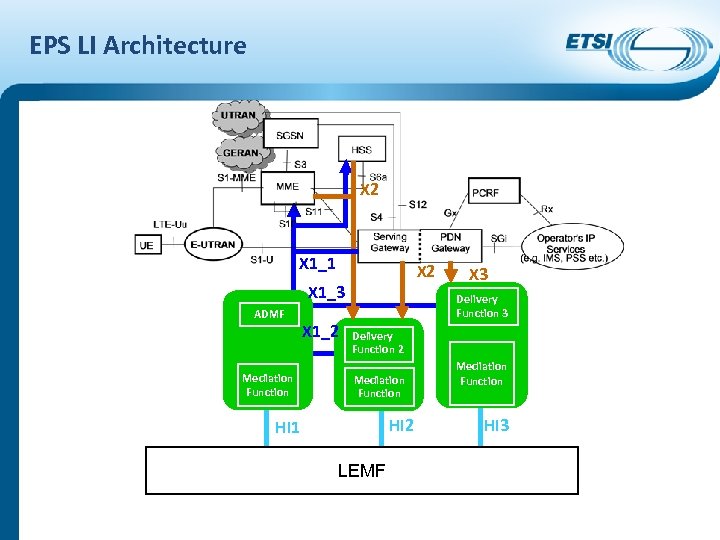
EPS LI Architecture X 2 X 1_1 X 2 X 1_3 ADMF Mediation Function X 1_2 X 3 Delivery Function 2 Mediation Function HI 2 HI 1 LEMF Mediation Function HI 3

Additional slides for more info More on LTE security • Backhaul Security • Relay Node Security IMS authentication Home (e) Node B security Status of work at 3 GPP on Security issues Main 3 GPP Security Standards

Conclusions Security is a major point of interest from GSM (2 G) up to LTE (4 G) GSM/UMTS Security: continues to evolve, recent introduction of A 5/3 (planned before attack on old A 5/1 succeeded) LTE Security: building on GSM and UMTS Security with newer security algorithms, longer keys, Extended key hierarchy Security aspects taken into consideration each time the system evolves (IMS, HNB, MTC, …)
Thank you! Contact Details: Alain. Sultan@etsi. org Thank you! 23 © ETSI 2012. All rights reserved
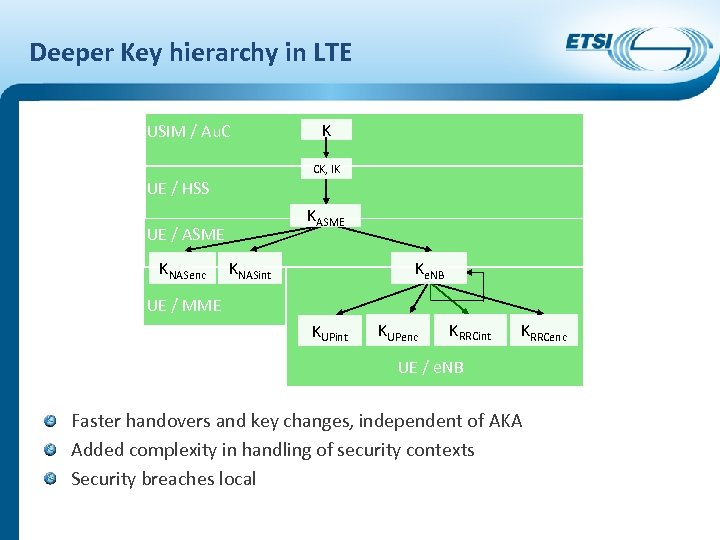
Deeper Key hierarchy in LTE USIM / Au. C K CK, IK UE / HSS KASME UE / ASME KNASenc KNASint Ke. NB UE / MME KUPint KUPenc KRRCint KRRCenc UE / e. NB Faster handovers and key changes, independent of AKA Added complexity in handling of security contexts Security breaches local

Backhaul Security

Backhaul Security Base stations becoming more powerful • LTE e. Node B includes functions of Node. B and RNC Coverage needs grow constantly Infrastructure sharing Not always possible to trust physical security of e. NB Greater backhaul link protection necessary
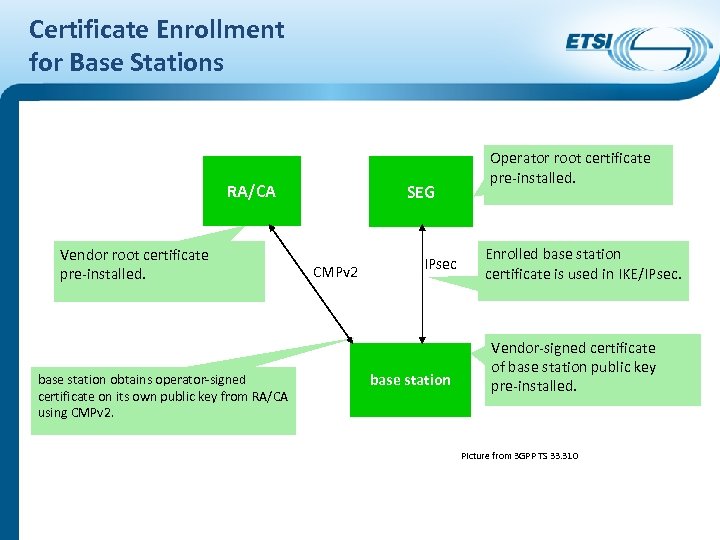
Certificate Enrollment for Base Stations RA/CA Vendor root certificate pre-installed. base station obtains operator-signed certificate on its own public key from RA/CA using CMPv 2. SEG CMPv 2 IPsec base station Operator root certificate pre-installed. Enrolled base station certificate is used in IKE/IPsec. Vendor-signed certificate of base station public key pre-installed. Picture from 3 GPP TS 33. 310

Relay Node Security
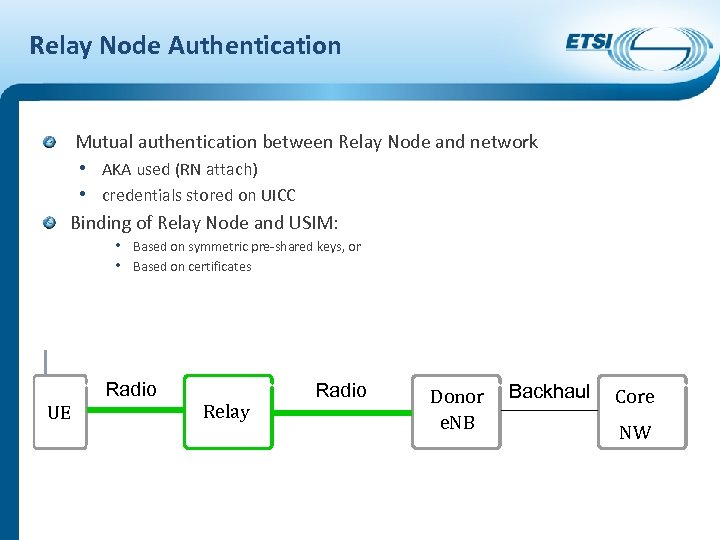
Relay Node Authentication Mutual authentication between Relay Node and network • AKA used (RN attach) • credentials stored on UICC Binding of Relay Node and USIM: • Based on symmetric pre-shared keys, or • Based on certificates UE Radio Relay Radio Donor e. NB Backhaul Core NW
Relay Node Security Control plane traffic integrity protected User plane traffic optionally integrity protected Relay Node and network connection confidentiality protected Device integrity check Secure environment for storing and processing sensitive data

IP Multimedia Subsystem (IMS) Security
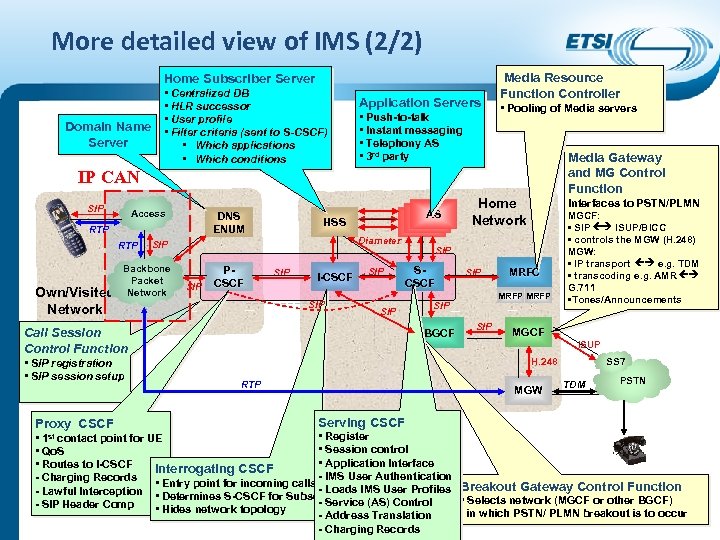
More detailed view of IMS (2/2) Home Subscriber Server Domain Name Server • Centralized DB • HLR successor • User profile • Filter criteria (sent to S-CSCF) • Which applications • Which conditions Application Servers • Push-to-talk • Instant messaging • Telephony AS • 3 rd party Media Resource Function Controller • Pooling of Media servers Media Gateway and MG Control Function IP CAN SIP Access DNS ENUM RTP Own/Visited Network HSS Diameter SIP Backbone Packet Network SIP PCSCF AS AS AS SIP I-CSCF SIP Proxy CSCF Interfaces to PSTN/PLMN SIP SCSCF SIP Call Session Control Function • SIP registration • SIP session setup Home Network SIP MRFP SIP BGCF MRFC SIP MGCF: • SIP ISUP/BICC • controls the MGW (H. 248) MGW: • IP transport e. g. TDM • transcoding e. g. AMR G. 711 • Tones/Announcements MGCF ISUP H. 248 RTP MGW SS 7 TDM PSTN Serving CSCF • Register • contact point for UE • Session control • Qo. S • Application Interface • Routes to I-CSCF Interrogating CSCF - IMS User Authentication - Charging Records • Entry point for incoming calls - Loads IMS User Profiles Breakout Gateway Control Function - Lawful Interception • Determines S-CSCF for Subscribers • Selects network (MGCF or other BGCF) - Service (AS) Control - SIP Header Comp • Hides network topology in which PSTN/ PLMN breakout is to occur - Address Translation - Charging Records 1 st
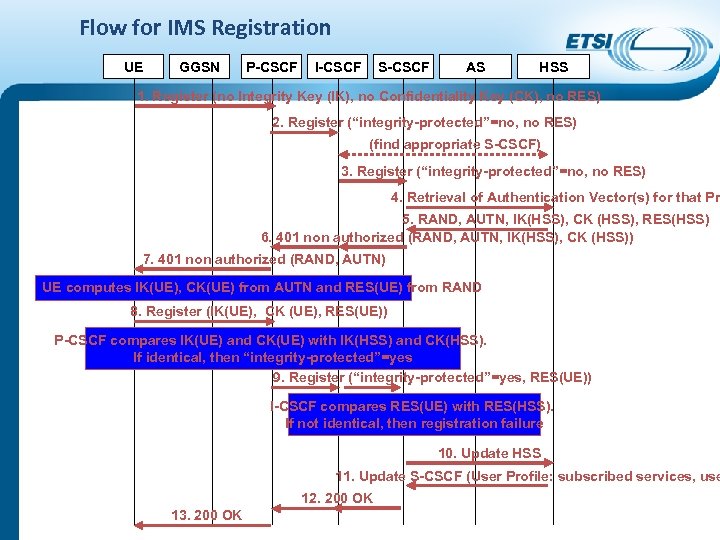
Flow for IMS Registration UE GGSN P-CSCF I-CSCF S-CSCF AS HSS 1. Register (no Integrity Key (IK), no Confidentiality Key (CK), no RES) 2. Register (“integrity-protected”=no, no RES) (find appropriate S-CSCF) 3. Register (“integrity-protected”=no, no RES) 4. Retrieval of Authentication Vector(s) for that Pr 5. RAND, AUTN, IK(HSS), CK (HSS), RES(HSS) 6. 401 non authorized (RAND, AUTN, IK(HSS), CK (HSS)) 7. 401 non authorized (RAND, AUTN) UE computes IK(UE), CK(UE) from AUTN and RES(UE) from RAND 8. Register (IK(UE), CK (UE), RES(UE)) P-CSCF compares IK(UE) and CK(UE) with IK(HSS) and CK(HSS). If identical, then “integrity-protected”=yes 9. Register (“integrity-protected”=yes, RES(UE)) I-CSCF compares RES(UE) with RES(HSS). If not identical, then registration failure 10. Update HSS 11. Update S-CSCF (User Profile: subscribed services, use 12. 200 OK 13. 200 OK

Home (e) Node B security
(out of scope for security) Datamodel cooperation with BBF ref. S 5 -091892, S 5 -092661
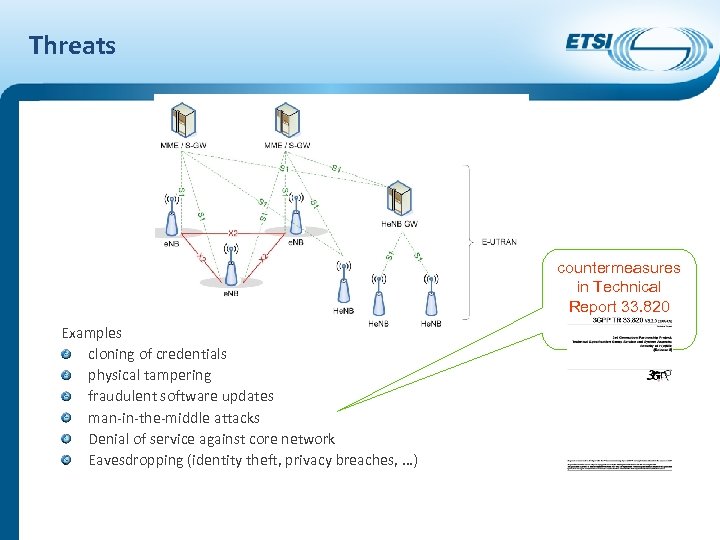
Threats countermeasures in Technical Report 33. 820 Examples cloning of credentials physical tampering fraudulent software updates man-in-the-middle attacks Denial of service against core network Eavesdropping (identity theft, privacy breaches, …)
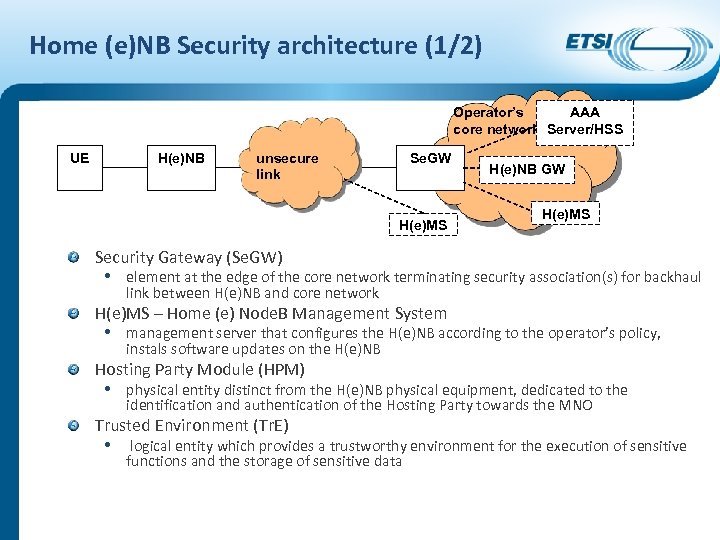
Home (e)NB Security architecture (1/2) Operator’s AAA core network Server/HSS UE H(e)NB unsecure link Se. GW H(e)MS H(e)NB GW H(e)MS Security Gateway (Se. GW) • element at the edge of the core network terminating security association(s) for backhaul link between H(e)NB and core network H(e)MS – Home (e) Node. B Management System • management server that configures the H(e)NB according to the operator’s policy, instals software updates on the H(e)NB Hosting Party Module (HPM) • physical entity distinct from the H(e)NB physical equipment, dedicated to the identification and authentication of the Hosting Party towards the MNO Trusted Environment (Tr. E) • logical entity which provides a trustworthy environment for the execution of sensitive functions and the storage of sensitive data
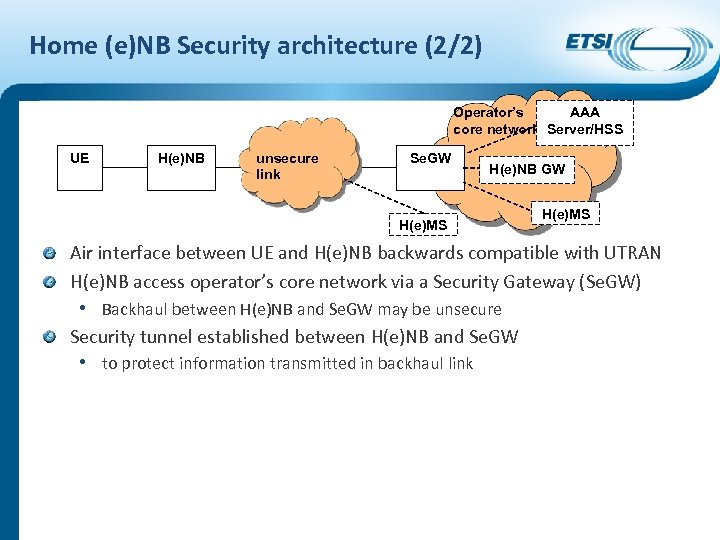
Home (e)NB Security architecture (2/2) Operator’s AAA core network Server/HSS UE H(e)NB unsecure link Se. GW H(e)NB GW H(e)MS Air interface between UE and H(e)NB backwards compatible with UTRAN H(e)NB access operator’s core network via a Security Gateway (Se. GW) • Backhaul between H(e)NB and Se. GW may be unsecure Security tunnel established between H(e)NB and Se. GW • to protect information transmitted in backhaul link
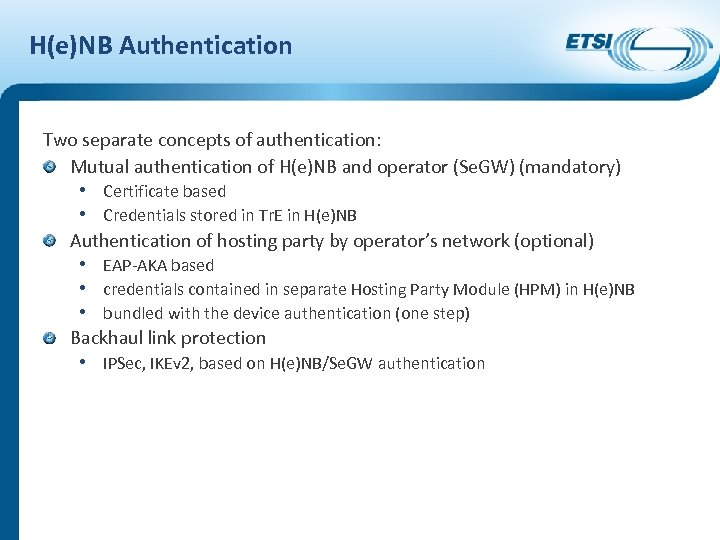
H(e)NB Authentication Two separate concepts of authentication: Mutual authentication of H(e)NB and operator (Se. GW) (mandatory) • Certificate based • Credentials stored in Tr. E in H(e)NB Authentication of hosting party by operator’s network (optional) • EAP-AKA based • credentials contained in separate Hosting Party Module (HPM) in H(e)NB • bundled with the device authentication (one step) Backhaul link protection • IPSec, IKEv 2, based on H(e)NB/Se. GW authentication
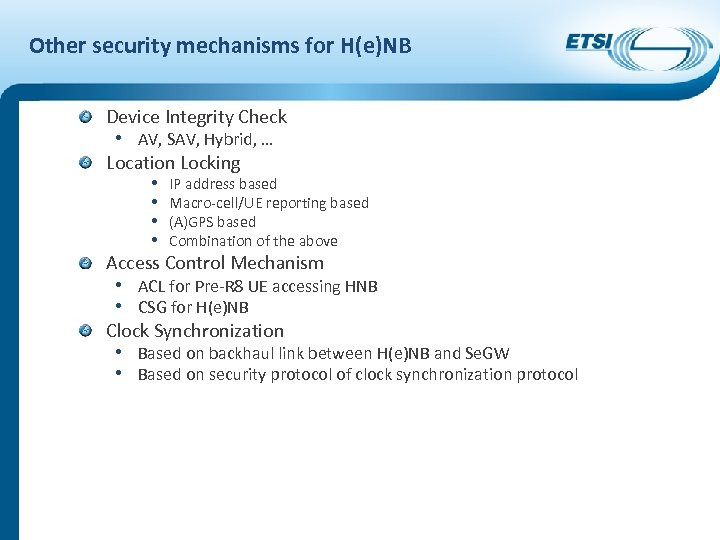
Other security mechanisms for H(e)NB Device Integrity Check • AV, SAV, Hybrid, … Location Locking • IP address based • Macro-cell/UE reporting based • (A)GPS based • Combination of the above Access Control Mechanism • ACL for Pre-R 8 UE accessing HNB • CSG for H(e)NB Clock Synchronization • Based on backhaul link between H(e)NB and Se. GW • Based on security protocol of clock synchronization protocol

H(e)NB security in the real world… location locking does NOT seem to work • in current commercial trials • HNBs operating from different countries • No roaming charges algorithm licensing is an issue • customers do not sign any agreement for use of COTS HNBs Lawful Interception • currently would not work in LIPA • would not work between CSG MSs camping on the same HNB rogue HNB roaming

Status of work at 3 GPP on Security issues

Recently completed security activities at 3 GPP (Rel-11)
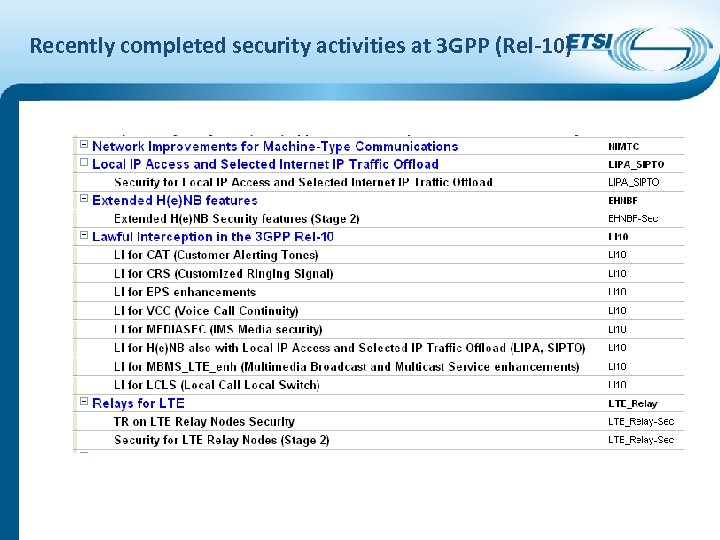
Recently completed security activities at 3 GPP (Rel-10)
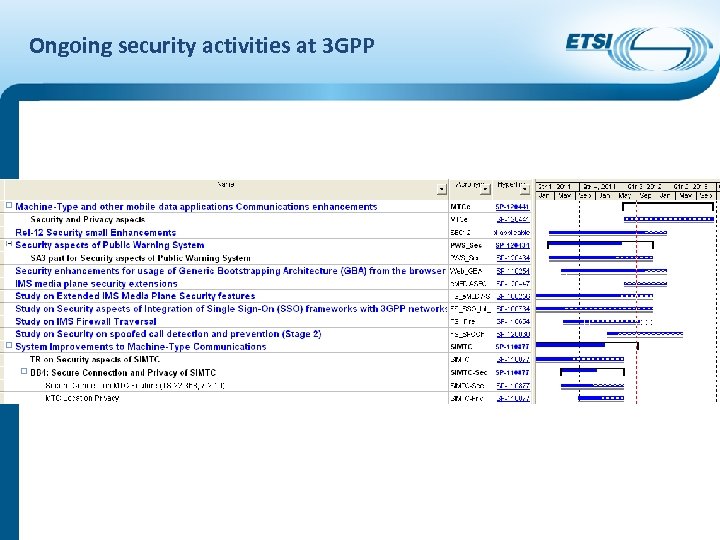
Ongoing security activities at 3 GPP

Main 3 GPP Security Standards
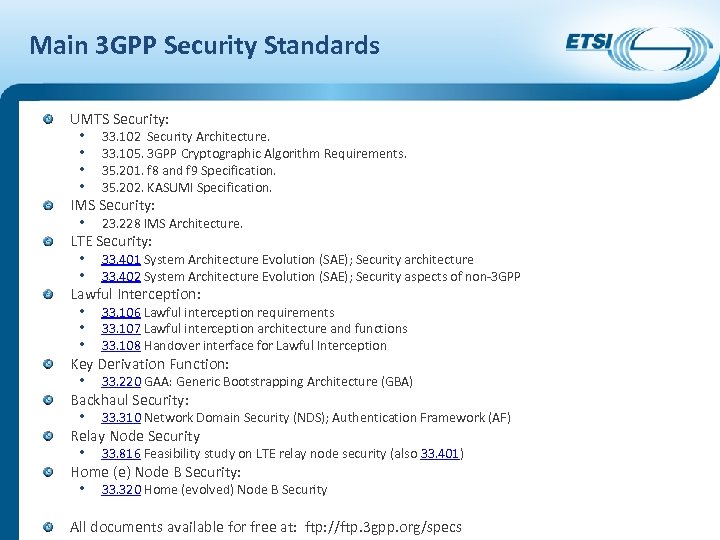
Main 3 GPP Security Standards UMTS Security: • • 33. 102 Security Architecture. 33. 105. 3 GPP Cryptographic Algorithm Requirements. 35. 201. f 8 and f 9 Specification. 35. 202. KASUMI Specification. IMS Security: • 23. 228 IMS Architecture. LTE Security: • 33. 401 System Architecture Evolution (SAE); Security architecture • 33. 402 System Architecture Evolution (SAE); Security aspects of non-3 GPP Lawful Interception: • 33. 106 Lawful interception requirements • 33. 107 Lawful interception architecture and functions • 33. 108 Handover interface for Lawful Interception Key Derivation Function: • 33. 220 GAA: Generic Bootstrapping Architecture (GBA) Backhaul Security: • 33. 310 Network Domain Security (NDS); Authentication Framework (AF) Relay Node Security • 33. 816 Feasibility study on LTE relay node security (also 33. 401) Home (e) Node B Security: • 33. 320 Home (evolved) Node B Security All documents available for free at: ftp: //ftp. 3 gpp. org/specs
d029d7de11cdf7643e4b46c293b26797.ppt