d5d27db2985f10820dd4128f408d4c34.ppt
- Количество слайдов: 15

Practical Security In Large Scale Distributed Object Oriented Databases http: //www. slac. stanford. edu/~abh/CHEP 2000/Security/ Andrew Hanushevsky Stanford Linear Accelerator Center Produced under contract DE-AC 03 -76 SF 00515 between Stanford University and the Department of Energy Andrew Hanushevsky - CHEP, February 7 -11, 2000 1

Our Motivation & Challenge n Motivation u n Protect data from unauthorized access or modification Challenge u Supply security to an existing DBMS, Objectivity/DB F F u Support any authentication or authorization model F F F u Authentication (who am I), Authorization (what can I do), Enforcement Handle very large database collections (tera-databases and peta-bytes) At least private (e. g. , Kerberos) and public key models Authentication and authorization models are independent Sufficiently extensible to handle future protocols and models Easily implementable an deployable F F Ability to use existing security infrastructure Package system in installation replaceable units Andrew Hanushevsky - CHEP, February 7 -11, 2000 2

Critical Solution Areas n Packaging u Determines ease of deployment F n Architecture u Determines ease of implementation F n Replaceable shared libraries Layered object-oriented components Protocol u Determines extensibility F Tunneled, single-challenge, optionally arbitrated protocol Andrew Hanushevsky - CHEP, February 7 -11, 2000 3
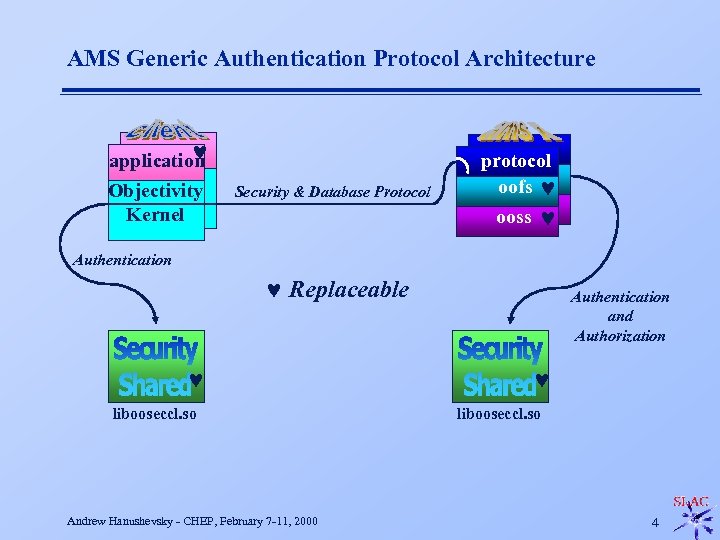
AMS Generic Authentication Protocol Architecture © application Objectivity Kernel Security & Database Protocol protocol oofs © ooss © Authentication © Replaceable © libooseccl. so Andrew Hanushevsky - CHEP, February 7 -11, 2000 Authentication and Authorization © libooseccl. so 4
Effects of Architecture & Packaging n Security protocol is tunneled via database protocol u Protocols are effectively independent F n Objectivity kernel mediates client interactions u n Same security used by every application and objectivity tool Replaceable oofs mediates server interactions u n Changes in one do not affect the other Can implement any kind of enforcement policy Security “linked” in via replaceable shared library u Can implement any kind of authentication or authorization model F F Standard authentication model is Kerberos Standard authorization model is capability-based Andrew Hanushevsky - CHEP, February 7 -11, 2000 5

Generic Authentication Protocol n Extensible u u Can accommodate diverse authentication models Example follows F Private vs public key authentication Andrew Hanushevsky - CHEP, February 7 -11, 2000 6
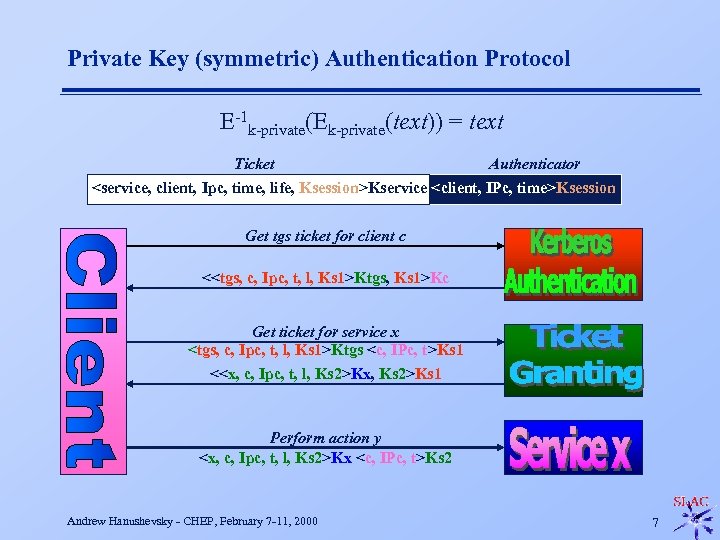
Private Key (symmetric) Authentication Protocol E-1 k-private(Ek-private(text)) = text Ticket Authenticator <service, client, Ipc, time, life, Ksession>Kservice <client, IPc, time>Ksession Get tgs ticket for client c <<tgs, c, Ipc, t, l, Ks 1>Ktgs, Ks 1>Kc Get ticket for service x <tgs, c, Ipc, t, l, Ks 1>Ktgs <c, IPc, t>Ks 1 <<x, c, Ipc, t, l, Ks 2>Kx, Ks 2>Ks 1 Perform action y <x, c, Ipc, t, l, Ks 2>Kx <c, IPc, t>Ks 2 Andrew Hanushevsky - CHEP, February 7 -11, 2000 7
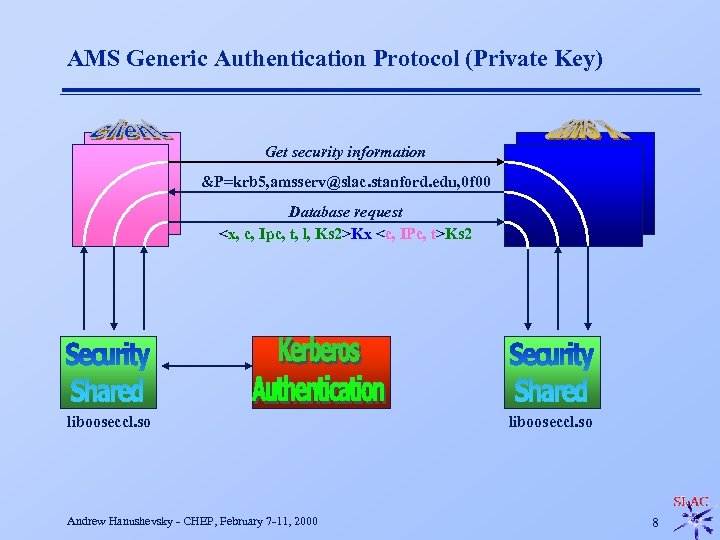
AMS Generic Authentication Protocol (Private Key) Get security information &P=krb 5, amsserv@slac. stanford. edu, 0 f 00 Database request <x, c, Ipc, t, l, Ks 2>Kx <c, IPc, t>Ks 2 libooseccl. so Andrew Hanushevsky - CHEP, February 7 -11, 2000 libooseccl. so 8
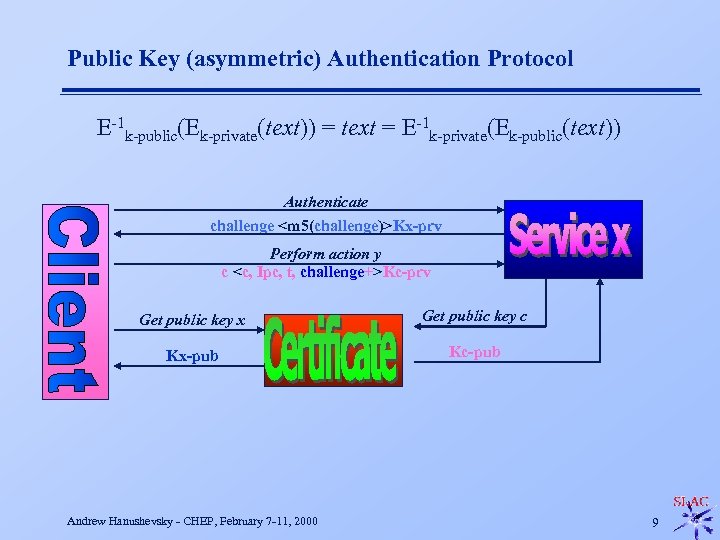
Public Key (asymmetric) Authentication Protocol E-1 k-public(Ek-private(text)) = text = E-1 k-private(Ek-public(text)) Authenticate challenge <m 5(challenge)>Kx-prv Perform action y c <c, Ipc, t, challenge+>Kc-prv Get public key x Get public key c Kx-pub Kc-pub Andrew Hanushevsky - CHEP, February 7 -11, 2000 9
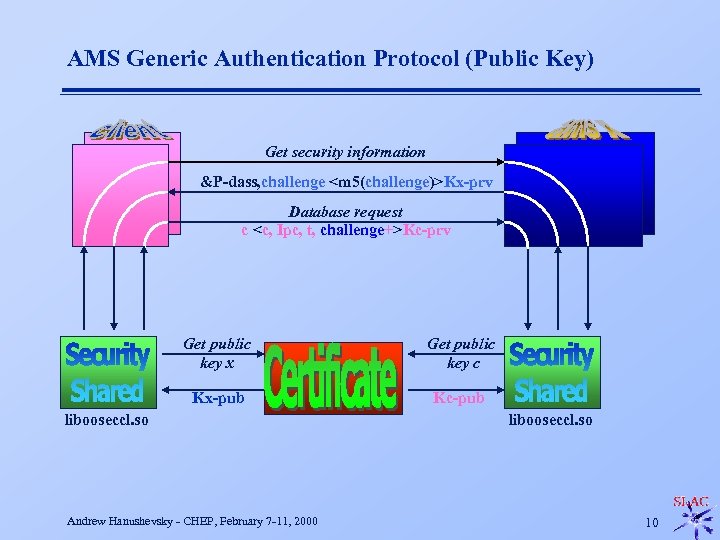
AMS Generic Authentication Protocol (Public Key) Get security information &P-dass, challenge <m 5(challenge)>Kx-prv Database request c <c, Ipc, t, challenge+>Kc-prv Get public key x Get public key c Kx-pub Kc-pub libooseccl. so Andrew Hanushevsky - CHEP, February 7 -11, 2000 libooseccl. so 10

Why is Generic Authentication Protocol Extensible? n Tunneling u u GAP is simply a wrapper for an arbitrary authentication protocol Database protocol forwards wrapped data without inspection F n GAP can support virtually any protocol u n Wrapper added and removed by shared library code Allows out-of-band arbitration CAP can support multiple protocols u Server determines which protocols are available Andrew Hanushevsky - CHEP, February 7 -11, 2000 11
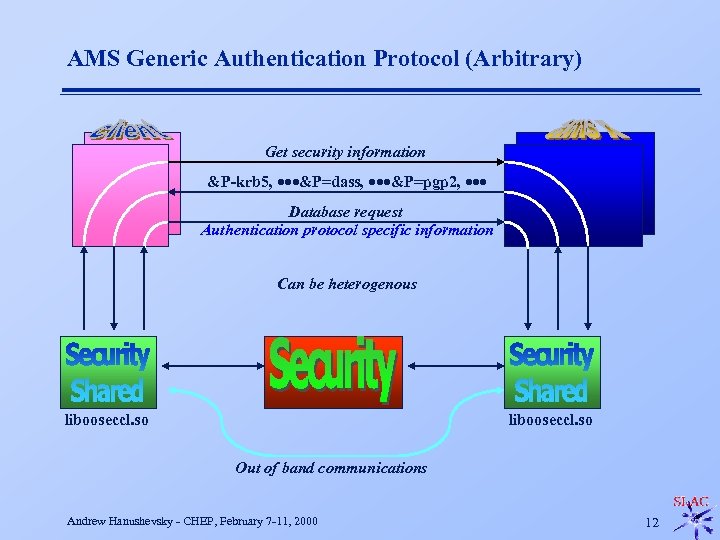
AMS Generic Authentication Protocol (Arbitrary) Get security information &P-krb 5, ···&P=dass, ···&P=pgp 2, ··· Database request Authentication protocol specific information Can be heterogenous libooseccl. so Out of band communications Andrew Hanushevsky - CHEP, February 7 -11, 2000 12
Authorization Challenge n Unencumbered AMS u Can only protect what AMS understands F n Size of all federations u Billions and billions of databases F n Amount of data is a moot point Access control list model unmanageable u Too many databases to protect F n Database files Don’t want to record usernames in many places Capability model is manageable u Few users relative to number of databases F F Usernames recorded only once Each user given access to arbitrary regions of any federation Andrew Hanushevsky - CHEP, February 7 -11, 2000 16
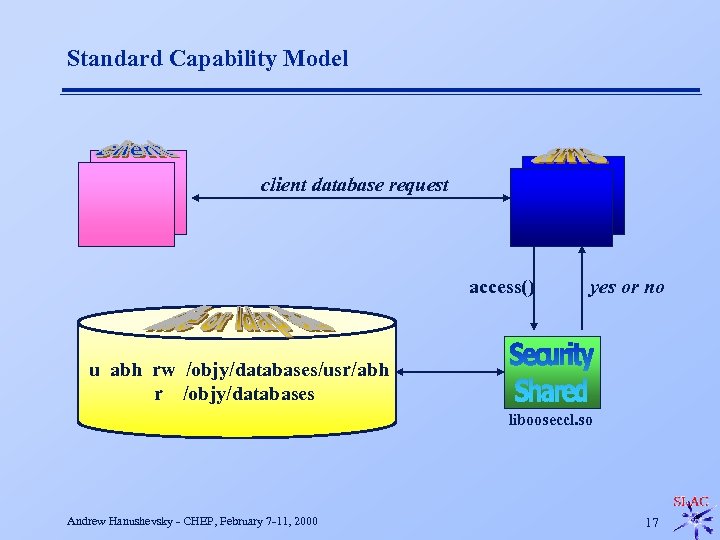
Standard Capability Model client database request access() yes or no u abh rw /objy/databases/usr/abh r /objy/databases libooseccl. so Andrew Hanushevsky - CHEP, February 7 -11, 2000 17
Summary n Scalable u n Extensible u n Can support virtually any authentication & authorization model Replaceable u n Standard is Kerberos & capabilities Packaging allows installation to easily use existing infrastructure Automatic u u Applications and Objectivity tools automatically use supplied security Circumvention detected and rejected Andrew Hanushevsky - CHEP, February 7 -11, 2000 19
d5d27db2985f10820dd4128f408d4c34.ppt