 PR SM A Secure Code Deployment Scheme for Active Networks Amdjed Mokhtari Leïla Kloul 22 November 2005
PR SM A Secure Code Deployment Scheme for Active Networks Amdjed Mokhtari Leïla Kloul 22 November 2005
 Outline PR SM Introduction & Motivation Code distribution mechanisms Security mechanisms Conclusions and future works 2
Outline PR SM Introduction & Motivation Code distribution mechanisms Security mechanisms Conclusions and future works 2
 Code distribution Code identification address Filter (@source, …) and type (TCP, …) Identifier : hash code (MD 5, …) links an identifier to its developer Code deployment In band persistence and sharing of codes Out band PR SM limited to one user class pre-selection of nodes, multiple path 3
Code distribution Code identification address Filter (@source, …) and type (TCP, …) Identifier : hash code (MD 5, …) links an identifier to its developer Code deployment In band persistence and sharing of codes Out band PR SM limited to one user class pre-selection of nodes, multiple path 3
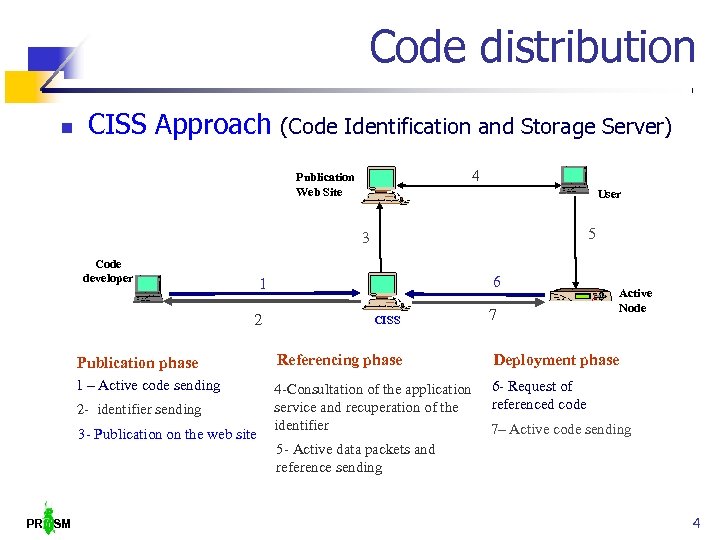 Code distribution CISS Approach (Code Identification and Storage Server) 4 Publication Web Site User 5 3 Code developer 6 1 2 CISS 7 Active Node Publication phase Referencing phase Deployment phase 1 – Active code sending 4 -Consultation of the application service and recuperation of the identifier 6 - Request of referenced code 2 - identifier sending 3 - Publication on the web site PR SM 7– Active code sending 5 - Active data packets and reference sending 4
Code distribution CISS Approach (Code Identification and Storage Server) 4 Publication Web Site User 5 3 Code developer 6 1 2 CISS 7 Active Node Publication phase Referencing phase Deployment phase 1 – Active code sending 4 -Consultation of the application service and recuperation of the identifier 6 - Request of referenced code 2 - identifier sending 3 - Publication on the web site PR SM 7– Active code sending 5 - Active data packets and reference sending 4
 Code distribution Approach multi CISS Repartition of CISS Code base management Placed at the edge of the network Distributed code bases Replicated code bases Guarantee the uniqueness of the identifier Distributed code bases management PR SM 5
Code distribution Approach multi CISS Repartition of CISS Code base management Placed at the edge of the network Distributed code bases Replicated code bases Guarantee the uniqueness of the identifier Distributed code bases management PR SM 5
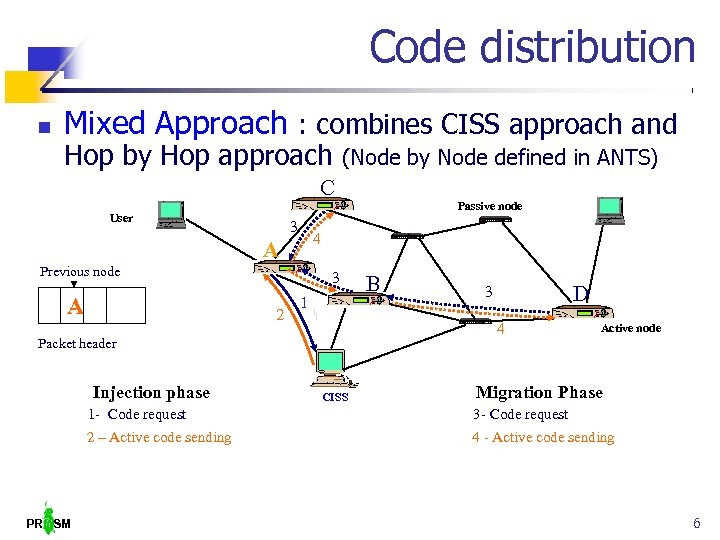 Code distribution Mixed Approach : combines CISS approach and Hop by Hop approach (Node by Node defined in ANTS) C User 3 4 A Previous node A - 3 2 1 B D 3 4 Packet header Injection phase Passive node CISS Active node Migration Phase 1 - Code request 2 – Active code sending PR SM 3 - Code request 4 - Active code sending 6
Code distribution Mixed Approach : combines CISS approach and Hop by Hop approach (Node by Node defined in ANTS) C User 3 4 A Previous node A - 3 2 1 B D 3 4 Packet header Injection phase Passive node CISS Active node Migration Phase 1 - Code request 2 – Active code sending PR SM 3 - Code request 4 - Active code sending 6
 Security mechanisms Security in code distribution Authentication Execution authorization PR SM CAAN (Certificate Authority for Active Network) Key for each entity : CISS, nodes, developers, users and also the code Utilization of a temporary keys Adaptation of ROSA technique [BAGNULO et al 02] 7
Security mechanisms Security in code distribution Authentication Execution authorization PR SM CAAN (Certificate Authority for Active Network) Key for each entity : CISS, nodes, developers, users and also the code Utilization of a temporary keys Adaptation of ROSA technique [BAGNULO et al 02] 7
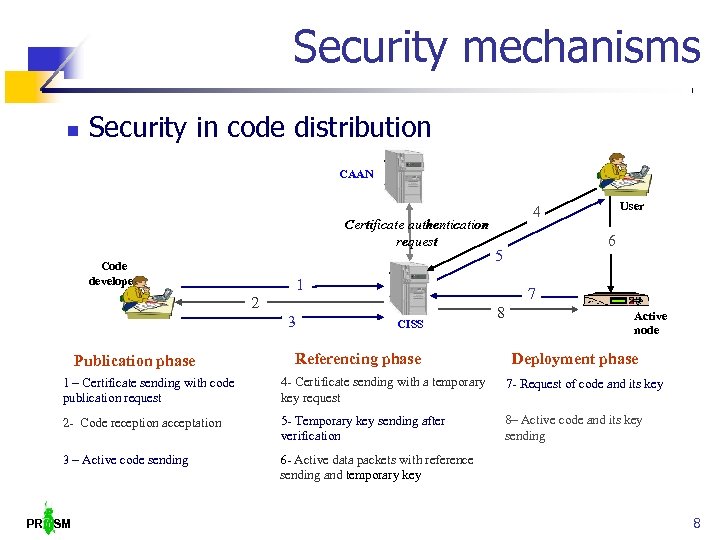 Security mechanisms Security in code distribution CAAN Certificate authentication request Code developer 7 2 Publication phase 6 5 1 3 User 4 CISS Referencing phase 8 Active node Deployment phase 1 – Certificate sending with code publication request 4 - Certificate sending with a temporary key request 7 - Request of code and its key 2 - Code reception acceptation 5 - Temporary key sending after verification 8– Active code and its key sending 3 – Active code sending 6 - Active data packets with reference sending and temporary key PR SM 8
Security mechanisms Security in code distribution CAAN Certificate authentication request Code developer 7 2 Publication phase 6 5 1 3 User 4 CISS Referencing phase 8 Active node Deployment phase 1 – Certificate sending with code publication request 4 - Certificate sending with a temporary key request 7 - Request of code and its key 2 - Code reception acceptation 5 - Temporary key sending after verification 8– Active code and its key sending 3 – Active code sending 6 - Active data packets with reference sending and temporary key PR SM 8
 Conclusions & Future works Conclusions Global scheme for code distribution based on Global scheme for the security based on Utilization temporary keys for the code deployment A certification authority (CAAN) Future works PR SM A Code Identification and Storage Server (CISS) A Publication Site Web of the CISS code base Performance analysis of the defined techniques in large scale network Evaluate the cost of the developed security mechanisms in terms of execution times 9
Conclusions & Future works Conclusions Global scheme for code distribution based on Global scheme for the security based on Utilization temporary keys for the code deployment A certification authority (CAAN) Future works PR SM A Code Identification and Storage Server (CISS) A Publication Site Web of the CISS code base Performance analysis of the defined techniques in large scale network Evaluate the cost of the developed security mechanisms in terms of execution times 9