21f91784312ffff7bc08f67b8861b304.ppt
- Количество слайдов: 13
 Polish Infrastructure for Supporting Computational Science in the European Research Space Secure Access to Shibboleth Protected Clusters Jan Meizner (1), Maciej Malawski (1, 2), Marian Bubak (1, 2) (1) ACC Cyfronet AGH, ul. Nawojki 11, 30 -950 Kraków, Poland (2) Institute of Computer Science AGH , Mickiewicza 30, 30 -059 Kraków, Poland KUKDM 2010 Zakopane, 18. 03. 2010
Polish Infrastructure for Supporting Computational Science in the European Research Space Secure Access to Shibboleth Protected Clusters Jan Meizner (1), Maciej Malawski (1, 2), Marian Bubak (1, 2) (1) ACC Cyfronet AGH, ul. Nawojki 11, 30 -950 Kraków, Poland (2) Institute of Computer Science AGH , Mickiewicza 30, 30 -059 Kraków, Poland KUKDM 2010 Zakopane, 18. 03. 2010
 Outline Introduction Problem definition Scientific objectives Related work Why Shibboleth and its description Description of the proposed solution Video demo with a short introduction PAM_SHIB configuration Conclusions and future work
Outline Introduction Problem definition Scientific objectives Related work Why Shibboleth and its description Description of the proposed solution Video demo with a short introduction PAM_SHIB configuration Conclusions and future work
 Introduction The main reason for the work is to provide manageable access to clusters by using the Shibboleth architecture Scientific objectives: Providing swift access to clusters for scientists using standard command-line (console) tools Laying a foundation for Shibboleth-secured webbased applications with seamless access to computing clusters Enable access to clusters for other projects/organizations, if needed, by using Shibboleth federation mechanisms
Introduction The main reason for the work is to provide manageable access to clusters by using the Shibboleth architecture Scientific objectives: Providing swift access to clusters for scientists using standard command-line (console) tools Laying a foundation for Shibboleth-secured webbased applications with seamless access to computing clusters Enable access to clusters for other projects/organizations, if needed, by using Shibboleth federation mechanisms
 Related work Simple passwd file-based access (pam_unix) Standard solution in Linux Common in small systems (single machines) Completely not scalable Andrew G. Morgan, Linux-PAM, 2010, http: //www. kernel. org/pub/linux/libs/pam/ LDAP-based authentication (pam, ldap or similar solution) Allows centralized management of credentials No Single Sign On supported (out of the box), no federations PADL Software Pty Ltd, 2010, http: //www. padl. com/OSS/pam_ldap. html Raw key pair-based authentication (e. g. Open. SSH public key method) Equivalent to SSO if unencrypted keys are used (not secure) Requires generation of keys and distribution to all nodes and clients Open. BSD Project, Open. SSH, 2010, http: //www. openssh. com/ Software solution using X. 509 authentication (e. g. GSI-Open. SSH) Provides Single Sign-On Requires application for a certificate and its distribution to client machines University of Illinois, GSI-Enabled Open. SSH, 2010. http: //grid. ncsa. illinois. edu/ssh/ Hardware-based security solutions (e. g. smartcards) More secure and easy then “software” certificates More complicated and costly issuance procedures
Related work Simple passwd file-based access (pam_unix) Standard solution in Linux Common in small systems (single machines) Completely not scalable Andrew G. Morgan, Linux-PAM, 2010, http: //www. kernel. org/pub/linux/libs/pam/ LDAP-based authentication (pam, ldap or similar solution) Allows centralized management of credentials No Single Sign On supported (out of the box), no federations PADL Software Pty Ltd, 2010, http: //www. padl. com/OSS/pam_ldap. html Raw key pair-based authentication (e. g. Open. SSH public key method) Equivalent to SSO if unencrypted keys are used (not secure) Requires generation of keys and distribution to all nodes and clients Open. BSD Project, Open. SSH, 2010, http: //www. openssh. com/ Software solution using X. 509 authentication (e. g. GSI-Open. SSH) Provides Single Sign-On Requires application for a certificate and its distribution to client machines University of Illinois, GSI-Enabled Open. SSH, 2010. http: //grid. ncsa. illinois. edu/ssh/ Hardware-based security solutions (e. g. smartcards) More secure and easy then “software” certificates More complicated and costly issuance procedures
 Why Shibboleth? A well known solution, widely used by scientific and educational institutions Provides Single Sign-On mechanisms Federated solution - access can be granted to users from new institutions with no need to recreate accounts No need to request certificates or generate and distribute keys More secure then using unencrypted keys, more manageable then using encrypted ones Well suited for protection of web applications
Why Shibboleth? A well known solution, widely used by scientific and educational institutions Provides Single Sign-On mechanisms Federated solution - access can be granted to users from new institutions with no need to recreate accounts No need to request certificates or generate and distribute keys More secure then using unencrypted keys, more manageable then using encrypted ones Well suited for protection of web applications
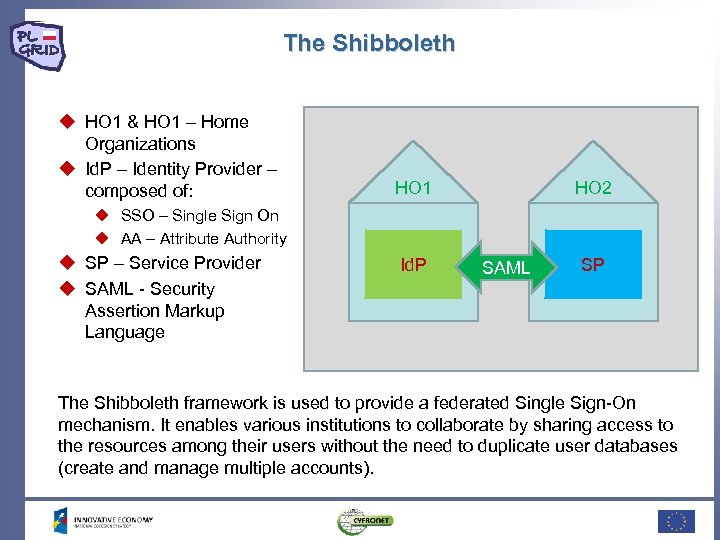 The Shibboleth HO 1 & HO 1 – Home Organizations Id. P – Identity Provider – composed of: HO 1 HO 2 SSO – Single Sign On AA – Attribute Authority SP – Service Provider SAML - Security Assertion Markup Language Id. P SAML SP The Shibboleth framework is used to provide a federated Single Sign-On mechanism. It enables various institutions to collaborate by sharing access to the resources among their users without the need to duplicate user databases (create and manage multiple accounts).
The Shibboleth HO 1 & HO 1 – Home Organizations Id. P – Identity Provider – composed of: HO 1 HO 2 SSO – Single Sign On AA – Attribute Authority SP – Service Provider SAML - Security Assertion Markup Language Id. P SAML SP The Shibboleth framework is used to provide a federated Single Sign-On mechanism. It enables various institutions to collaborate by sharing access to the resources among their users without the need to duplicate user databases (create and manage multiple accounts).
 Description of the solution The server side is composed of: Shibboleth framework deployed on at least one server for each entity providing LDAP databases for their users The pam_shib module, developed by us. This module needs to be deployed on each node to which ssh access should be provided Standard Open. SSH server (or other server with PAM support) (Optional) Custom Shibboleth-aware software on any node For the client side we provide: Custom Shibboleth Id. P Client tool Patched version of the standard Open. SSH client that can automatically use the stored handle (however, an unmodified client may also be used)
Description of the solution The server side is composed of: Shibboleth framework deployed on at least one server for each entity providing LDAP databases for their users The pam_shib module, developed by us. This module needs to be deployed on each node to which ssh access should be provided Standard Open. SSH server (or other server with PAM support) (Optional) Custom Shibboleth-aware software on any node For the client side we provide: Custom Shibboleth Id. P Client tool Patched version of the standard Open. SSH client that can automatically use the stored handle (however, an unmodified client may also be used)
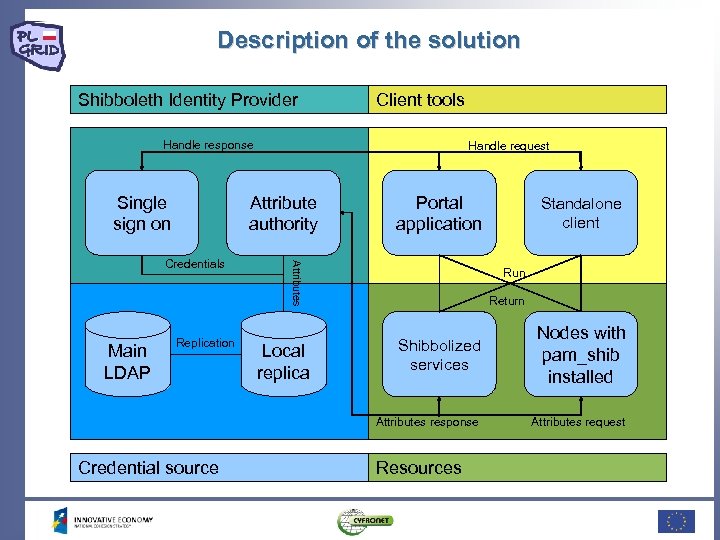 Description of the solution Shibboleth Identity Provider Client tools Handle response Single sign on Handle request Attribute authority Attributes Credentials Portal application Standalone client Run Return Credential source Local replica Shibbolized services Nodes with pam_shib installed Attributes response Main LDAP Replication Attributes request Resources
Description of the solution Shibboleth Identity Provider Client tools Handle response Single sign on Handle request Attribute authority Attributes Credentials Portal application Standalone client Run Return Credential source Local replica Shibbolized services Nodes with pam_shib installed Attributes response Main LDAP Replication Attributes request Resources
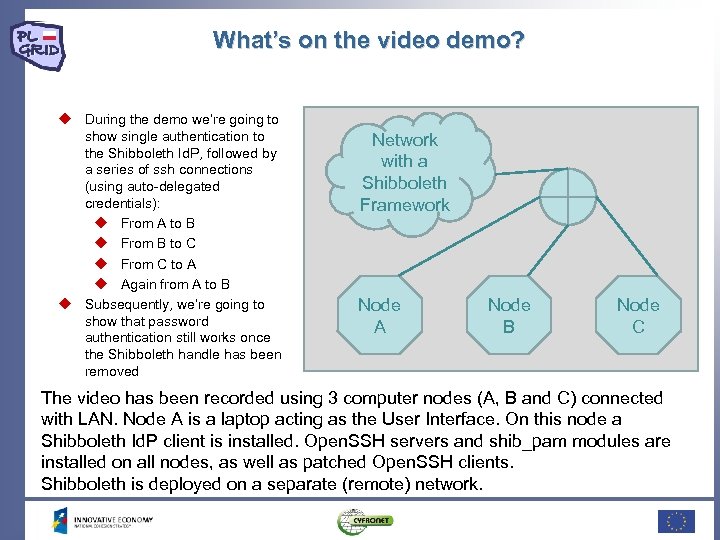 What’s on the video demo? During the demo we’re going to show single authentication to the Shibboleth Id. P, followed by a series of ssh connections (using auto-delegated credentials): From A to B From B to C From C to A Again from A to B Subsequently, we’re going to show that password authentication still works once the Shibboleth handle has been removed Network with a Shibboleth Framework Node A Node B Node C The video has been recorded using 3 computer nodes (A, B and C) connected with LAN. Node A is a laptop acting as the User Interface. On this node a Shibboleth Id. P client is installed. Open. SSH servers and shib_pam modules are installed on all nodes, as well as patched Open. SSH clients. Shibboleth is deployed on a separate (remote) network.
What’s on the video demo? During the demo we’re going to show single authentication to the Shibboleth Id. P, followed by a series of ssh connections (using auto-delegated credentials): From A to B From B to C From C to A Again from A to B Subsequently, we’re going to show that password authentication still works once the Shibboleth handle has been removed Network with a Shibboleth Framework Node A Node B Node C The video has been recorded using 3 computer nodes (A, B and C) connected with LAN. Node A is a laptop acting as the User Interface. On this node a Shibboleth Id. P client is installed. Open. SSH servers and shib_pam modules are installed on all nodes, as well as patched Open. SSH clients. Shibboleth is deployed on a separate (remote) network.
 The video demo… PAM_SHIB DEMO
The video demo… PAM_SHIB DEMO
 PAM_SHIB configuration To enable access to the node, the administrator needs to: Install required libraries (opensaml, curl and their dependencies) Install the module and the configuration file into appropriate locations (e. g. /lib/security and /etc) Add the module to service's (e. g. ssh) pam configuration following the basic authentication module (e. g. after pam_unix) Ensure that both basic (pam_unix) as well as pam_shib modules are set to be sufficient to grant access to the resources and that pam_shib has its conf parameter set to the appropriate configuration file
PAM_SHIB configuration To enable access to the node, the administrator needs to: Install required libraries (opensaml, curl and their dependencies) Install the module and the configuration file into appropriate locations (e. g. /lib/security and /etc) Add the module to service's (e. g. ssh) pam configuration following the basic authentication module (e. g. after pam_unix) Ensure that both basic (pam_unix) as well as pam_shib modules are set to be sufficient to grant access to the resources and that pam_shib has its conf parameter set to the appropriate configuration file
 Conclusions and further work The goals have been achieved – creation of the pam_shib modules broadens the pool of software that can be accessed with Shibboleth credentials. In addition to Shibboleth-enabled software that could be accessed before, various native software packages installed on clusters can now be offered to users Work is in progress on the following issues: Making the module more versatile and user friendly by providing more manageable configuration mechanisms Integrating the solution with Grid. Space 2
Conclusions and further work The goals have been achieved – creation of the pam_shib modules broadens the pool of software that can be accessed with Shibboleth credentials. In addition to Shibboleth-enabled software that could be accessed before, various native software packages installed on clusters can now be offered to users Work is in progress on the following issues: Making the module more versatile and user friendly by providing more manageable configuration mechanisms Integrating the solution with Grid. Space 2
 References J. Meizner, M. Malawski, E. Ciepiela, M. Kasztelnik, D. Harężlak, P. Nowakowski, D. Król, T. Gubała, W. Funika, M. Bubak, T. Mikołajczyk, P. Plaszczak, K. Wilk, and M. Assel. Viro. Lab Security and Virtual Organization Infrastructure. In Young Dou, Ralf Gruber, and Josef Joller, editors, Advanced Parallel Processing Technologies 8 th International Symposium, APPT 2009, Rapperswil, Switzerland, August 2425, 2009 Proceedings, volume 5737 of Lecture Notes in Computer Science, pages 230– 245. Springer, 2009 Grid. Space webpage, http: //gs. cyfronet. pl/ PL-Grid Project, http: //www. plgrid. pl/en
References J. Meizner, M. Malawski, E. Ciepiela, M. Kasztelnik, D. Harężlak, P. Nowakowski, D. Król, T. Gubała, W. Funika, M. Bubak, T. Mikołajczyk, P. Plaszczak, K. Wilk, and M. Assel. Viro. Lab Security and Virtual Organization Infrastructure. In Young Dou, Ralf Gruber, and Josef Joller, editors, Advanced Parallel Processing Technologies 8 th International Symposium, APPT 2009, Rapperswil, Switzerland, August 2425, 2009 Proceedings, volume 5737 of Lecture Notes in Computer Science, pages 230– 245. Springer, 2009 Grid. Space webpage, http: //gs. cyfronet. pl/ PL-Grid Project, http: //www. plgrid. pl/en


