687b452931c19025930090ac265b3d4e.ppt
- Количество слайдов: 83

Policy-Guided Interactions in Ubiquitous Computing Systems A Dissertation Prospectus V. Ramakrishna Advisor: Dr. Peter Reiher Laboratory for Advanced Systems Research Department of Computer Science, UCLA

Proposal Problem l Safe spontaneous interoperation in ubiquitous computing without pre-established trust relationships or rigid protocols Solution l A generic and flexible negotiation protocol guided by local policy 2

Outline l l l Problem Introduction Proposed Solution System Research Issues Design Approach Research Plan Related and Complementary Research 3

Problem Introduction 4
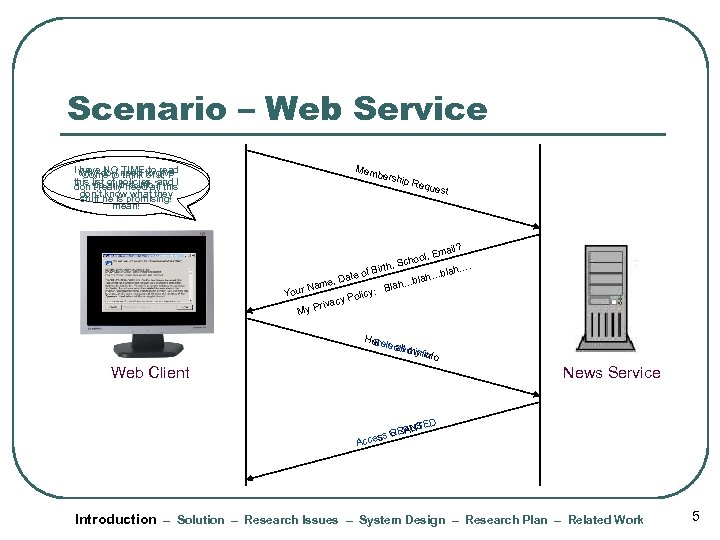
Scenario – Web Service I Why do I need to give have NO TIME to read Come to think of it, I this list all policies, and I up of this info? don’t really need all this don’t know what they stuff he is promising! mean! Mem bersh ip Re ques t il? Ema hool, , Sc. Birth blah… te of Da blah… e, ah… Nam : Bl Your olicy y. P rivac My P Here S ’s c le all ted iy m nfio nfo Web Client News Service D NTE AUS REF s GR s Acce Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 5
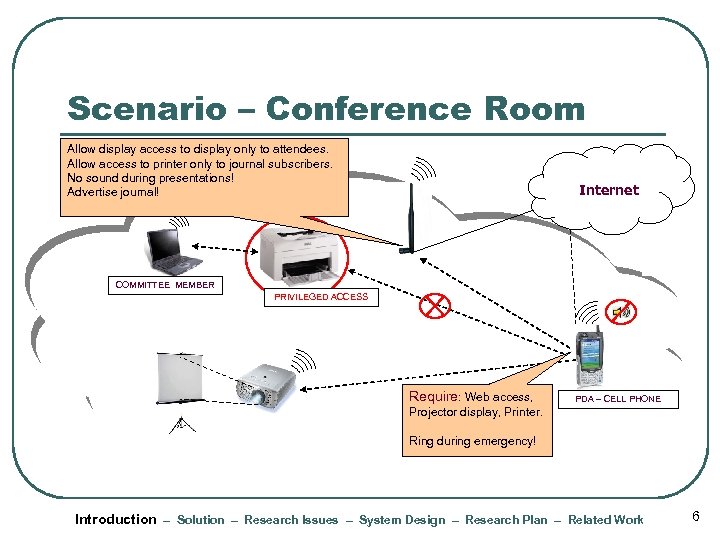
Scenario – Conference Room Allow display access to display only to attendees. Allow access to printer only to journal subscribers. No sound during presentations! Advertise journal! Internet COMMITTEE MEMBER PRIVILEGED ACCESS Require: Web access, PDA – CELL PHONE Projector display, Printer. Ring during emergency! Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 6
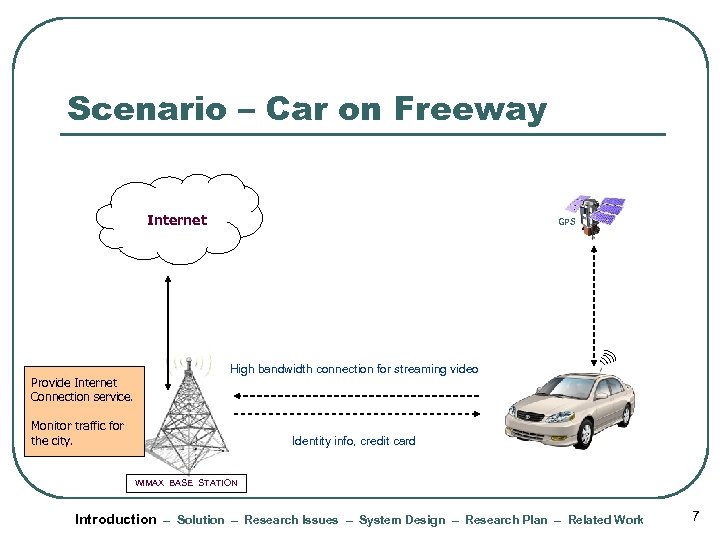
Scenario – Car on Freeway Internet Provide Internet Connection service. GPS High bandwidth connection for streaming video Monitor traffic for the city. Identity info, credit card Wi. MAX BASE STATION Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 7

Motivations l l l Scenarios support limited ways of interaction Ubicomp scenarios will have more variations Rigid policies not desirable Cannot guarantee pre-established security relationships Cannot enforce uniform interaction protocols Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 8

The Ubiquitous Computing Vision Computing services everywhere and at any time – Mark Weiser, 1991 Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 9
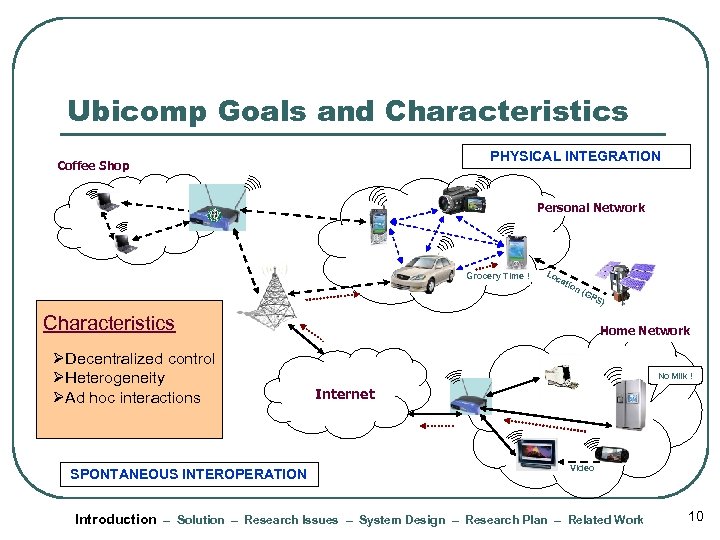
Ubicomp Goals and Characteristics PHYSICAL INTEGRATION Coffee Shop Personal Network Grocery Time ! Lo ca tio n( GP Characteristics ØDecentralized control ØHeterogeneity ØAd hoc interactions SPONTANEOUS INTEROPERATION S) Home Network No Milk ! Internet Video Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 10
Ubicomp Research l Mature research areas • Seamless mobile networking • Open systems and interfaces • Smart space projects; e. g. Intelligent Room, GAIA l Not enough consideration given to • Bottom-up growth of infrastructure • Security and privacy issues Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 11
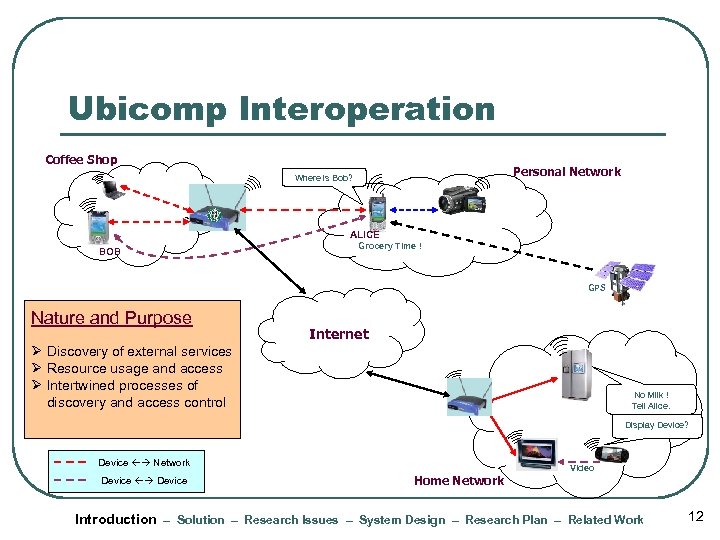
Ubicomp Interoperation Coffee Shop Personal Network Where is Bob? Connectivity? Location? ALICE BOB Grocery Time ! GPS Nature and Purpose Internet Ø Discovery of external services Ø Resource usage and access Ø Intertwined processes of discovery and access control No Milk ! Tell Alice. Display Device? Device Network Device Home Network Video Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 12
Barriers to Interoperation l Concerns l Roadblocks • Security and privacy • Dynamism and context changes • Middleware and security frameworks do not scale • Cannot force particular architectures or security • preferences as standards Cannot guarantee pre-established security relationships 13

Problems and Challenges l Hard problems • • l Match service demands to local resources within policy constraints and context Reach flexible agreements in an automated fashion Challenges in a ubicomp environment • • Heterogeneous devices and communication features Diversity in resources possessed and exported Diversity in capabilities, desires and security policies Huge number of contexts and context-sensitive constraints that cannot be anticipated in advance Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 14
In Ubicomp Environments …. . Every device and every domain will not support every service or protocol l All pairs of computing entities will not be compatible l Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 15
Drawbacks in Existing Approaches l Based on rigid and static policies l Inadequate security and access control models • Cannot resolve all conflicts • Falls short of autonomic computing • Scalability and flexibility issues • Lack of support for non-identity based trust relationships Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 16

Proposed Solution 17

Service or application layer agreements l l Based on policy Through a process of negotiation Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 18
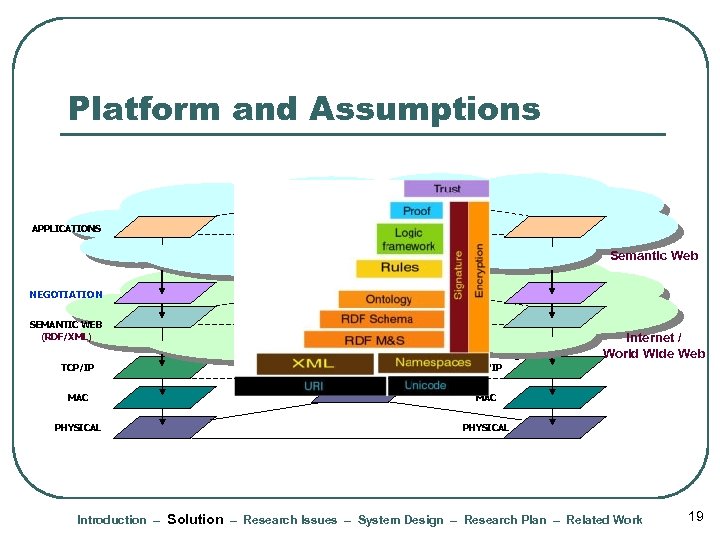
Platform and Assumptions APPLICATIONS Semantic Web NEGOTIATION SEMANTIC WEB (RDF/XML) TCP/IP MAC PHYSICAL Internet / World Wide Web TCP/IP MAC PHYSICAL Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 19

Policy-Based Management l l l Policy describes state and desired behavior Governs all actions within bounded domains Wide expressive power Guides following system aspects • • • Resource management Security and access control Context awareness Interactions between domains • • Discovery and access are the constants Policy is the only domain dependent variable Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 20
Thesis Summary l Enable negotiation-driven interaction without: • Pre-established trust relationships • Common set of service access protocols l The negotiation protocol: • Guided by local policy that constrains use and export of services • Relies on common resource semantics Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 21
Why Policy? l l Minimum necessary for interaction and agreement Why not specialized applications? • Difficult to make changes and to control • Cannot anticipate all requirements and • contexts Inter-modular dependencies difficult to handle Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 22

Interaction through Negotiation l l Bidirectional stateful protocol Strategic messaging Constant re-evaluation of goals Meta-policies and heuristics designed to reach an agreement or compromise A decentralized process of policy resolution and conflict management Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 23
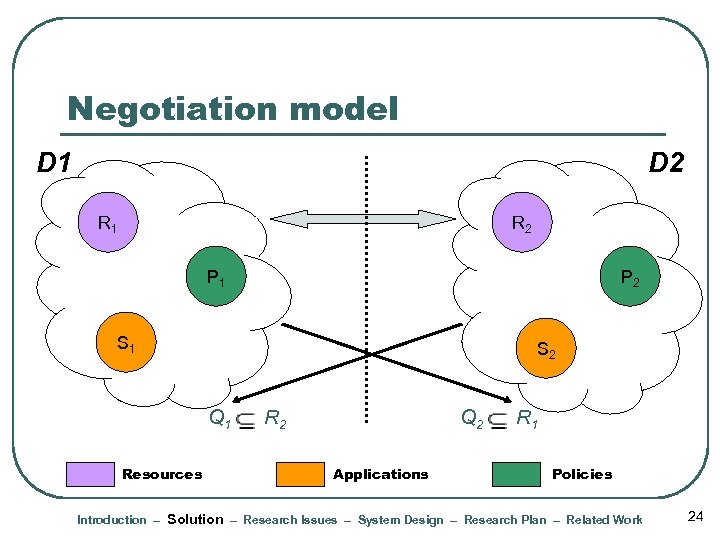
Negotiation model D 1 D 2 R 1 R 2 P 1 P 2 S 1 S 2 Q 1 Resources R 2 Q 2 Applications R 1 Policies Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 24
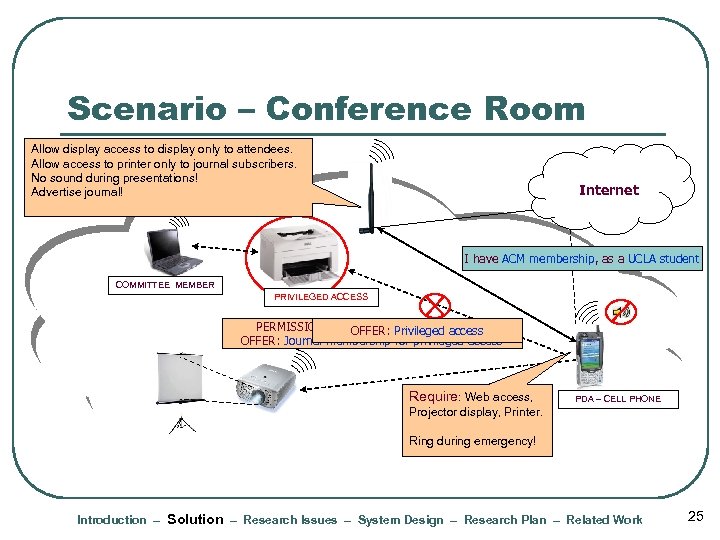
Scenario – Conference Room Allow display access to display only to attendees. Allow access to printer only to journal subscribers. No sound during presentations! Advertise journal! Internet I have ACM am just a Webas a Attendee REQUEST: membership, Access; Printer Sorry! I Display; Student UCLA student OK COMMITTEE MEMBER PRIVILEGED ACCESS PERMISSION: Projector No sounds permitted! POLICY: display, web. Member PROOF: Committee access OFFER: Privileged access OFFER: Journal membership for privileged access Require: Web access, PDA – CELL PHONE Projector display, Printer. Ring during emergency! Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 25
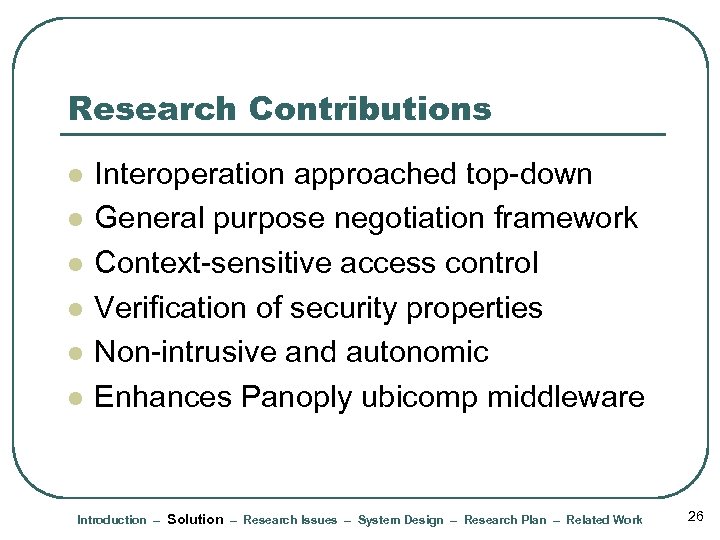
Research Contributions l l l Interoperation approached top-down General purpose negotiation framework Context-sensitive access control Verification of security properties Non-intrusive and autonomic Enhances Panoply ubicomp middleware Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 26

System Research Issues 27
Protocol Structure l Flexibility • Independent of application and domain • • l l characteristics Identify a tight set of common objects and operations Only task for users – write high level policies Extensibility Strike a useful balance by experimenting with characteristic applications Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 28

Policy Language and Reasoning Engine l l An expressive policy language Must be based on logic • Support declarative cross-domain semantics • Supports formal reasoning Must manage conflicts and maintain consistency Support efficient indexing and retrieval Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 29
Candidate Logical Framework l First order logic • Ontology includes objects and relationships • Augment with deontic concepts • Can be augmented (or restricted) to deal with • contextual and trust parameters Reasoning framework and querying algorithms Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 30
Security Aspects l l l Key research aspects • • Security benefits to ubicomp Secure negotiation protocol from compromise Security benefits • • • Concerns proper use of security mechanisms rather than propose new ones Promotes a paradigm that ensures safety is taken into consideration before interaction Allows static and dynamic detection of security conflicts Protocol security • • Cryptographic mechanisms, SSL, TLS Can the nature of the protocol itself be used to compromise security? Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 31
Trust and Access Control l l Access control framework targets • • Scalability and flexibility Based on a general notion of trust Trust model • • • Based on identity, provable relationships, properties and actions Domain and application independent Provides heuristics to compare among choices and make negotiation decisions Negotiation is a way of doing fine-grained, dynamic and context-sensitive access control Can be used to build webs of trust Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 32

Negotiation Strategies and Heuristics l l Negotiation protocol • • • Series of messaging rounds Directed towards a perceived goal Strategies to choose among various options • Eager and lazy: two extreme ends Heuristics as decision-making aid • • • Compute and re-evaluate goals Must work within policy constraints extrapolated to the current context Use trust and utility functions Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 33

Theoretical Aspects l l l Correctness Completeness Optimality Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 34
System Design Issues l l l Resource management, interfaces and access mechanisms Context Awareness Performance Fault tolerance and reliability Working with low capability devices and networks Negotiation with legacy devices and software Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 35

Design, Implementation and Evaluation 36
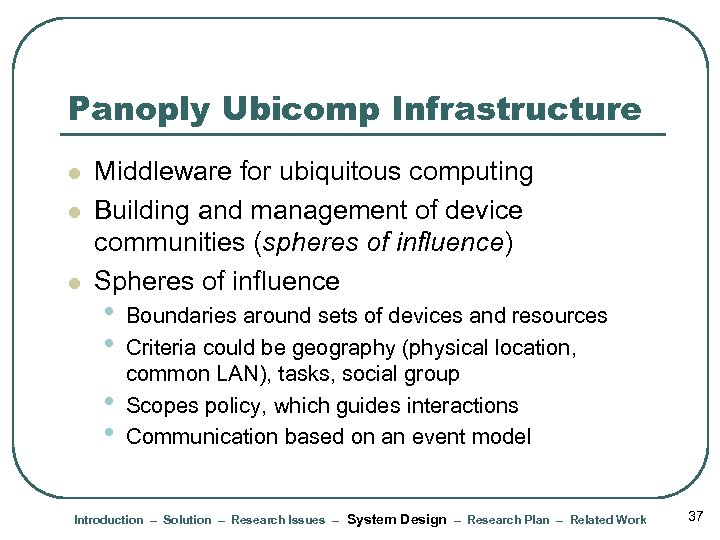
Panoply Ubicomp Infrastructure l l l Middleware for ubiquitous computing Building and management of device communities (spheres of influence) Spheres of influence • • Boundaries around sets of devices and resources Criteria could be geography (physical location, common LAN), tasks, social group Scopes policy, which guides interactions Communication based on an event model Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 37
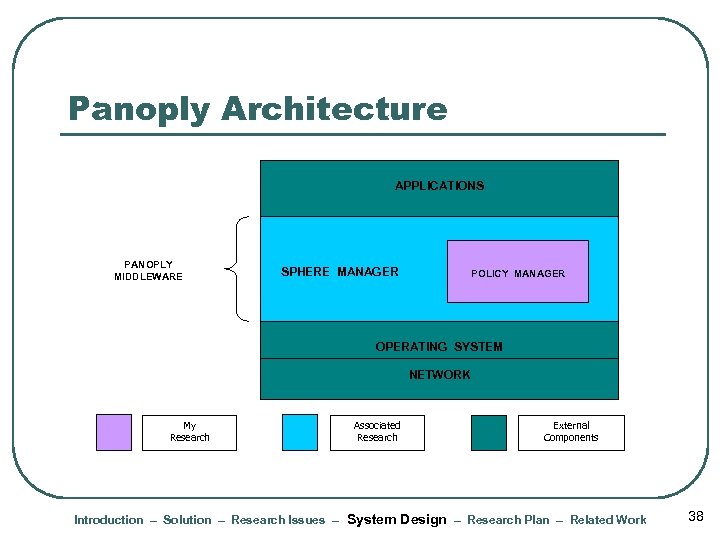
Panoply Architecture APPLICATIONS PANOPLY MIDDLEWARE SPHERE MANAGER POLICY MANAGER OPERATING SYSTEM NETWORK My Research Associated Research External Components Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 38
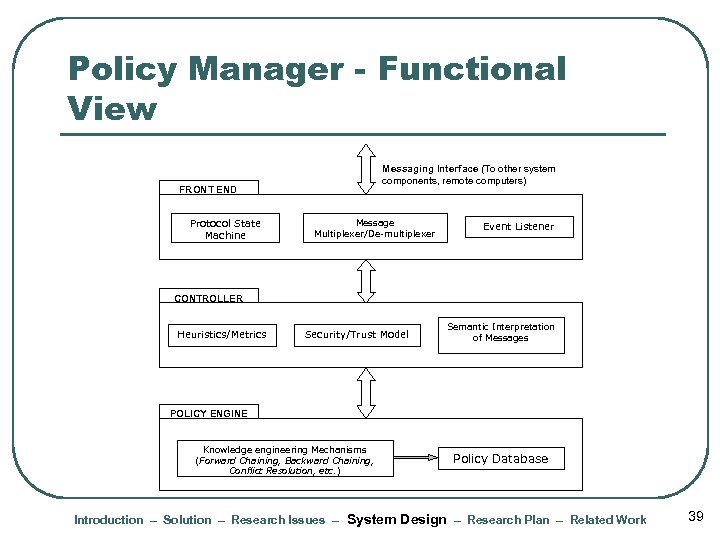
Policy Manager - Functional View Messaging Interface (To other system components, remote computers) FRONT END Protocol State Machine Message Multiplexer/De-multiplexer Event Listener CONTROLLER Heuristics/Metrics Security/Trust Model Semantic Interpretation of Messages POLICY ENGINE Knowledge engineering Mechanisms (Forward Chaining, Backward Chaining, Conflict Resolution, etc. ) Policy Database Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 39
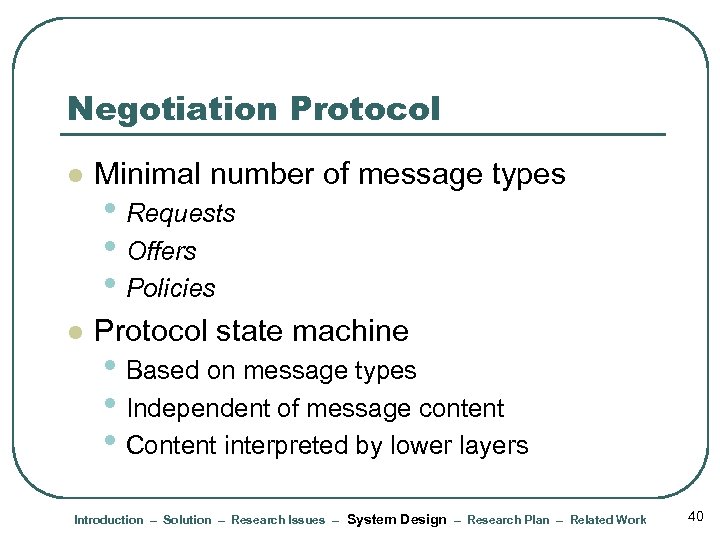
Negotiation Protocol l Minimal number of message types l Protocol state machine • Requests • Offers • Policies • Based on message types • Independent of message content • Content interpreted by lower layers Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 40
Policy Model l l Prolog used for writing policies • • • State information and rules written as predicates • • l Subset of first order logic Declarative syntax Fast algorithms for logical reasoning Designated predicates for high-level understanding External functions (Java) for non-logical tasks Develop richer ontology Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 41
Current Negotiation Model l Security model • Permit actions or accesses in a conservative manner l Negotiation goals and strategies • Fixed goals and alternatives • Fixed strategy, based on satisfaction of relevant policies Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 42
Future Models l Trust model l Negotiation strategy • Use advanced RBAC mechanisms • Trust levels for comparison of alternatives • Heuristics that allow risk-benefit analysis • Use game-theoretic notions • Utility model than can infer and compare utilities of objects and actions Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 43
Implementation l Policy Manager l Description of entities, resources and properties • Implemented in Java • Policy Engine based on SWI-Prolog • XML and RDF l Security mechanisms • X. 509 certificates • Panoply vouchers Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 44
Current Status l Basic policy manager implemented Policy engine • l Front end • l • Controller • • Implements protocol state machine Supports multiple threads • • Query the policy database Add, remove and replace statements • • Adopts simple, cautious negotiation strategy Requests, offers and checks for alternatives Integrated within a Panoply sphere • Uses events for negotiation and to obtain and update state information Principal task performed: Negotiate for membership within a sphere Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 45

Research Plan 46
Basic Policy Manager and Evaluation l Experiment with policy manager within the Panoply context • Performance evaluations • Overhead measurements • Scalability • Explore benefits through applications • Location sensitive interactive fiction • LACMA gallery experience Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 47
Modeling Issues l l Policy Language and Reasoning Engine Trust Model Resource Utility Model Negotiation Strategy and Heuristics Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 48
Complete Policy Manager l Incorporate models into negotiation heuristics • Enhance controller with strategic decision making capability l Augment spheres by adding • Resources and services • Context sensors Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 49
Analysis and evaluation l l l Generate real ubicomp scenarios Theoretical Analysis • • Correctness and completeness Efficacy of strategies Performance Evaluations • • Overhead measurements Scalability with respect to • Policy database size • Multi-session load Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 50

Evaluation of Success l Success of strategies and heuristics • Compare initial set of requirements or desires • l with the final result Compare final result with optimal result Security benefits • Amount of risk taken, or compromises made Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 51
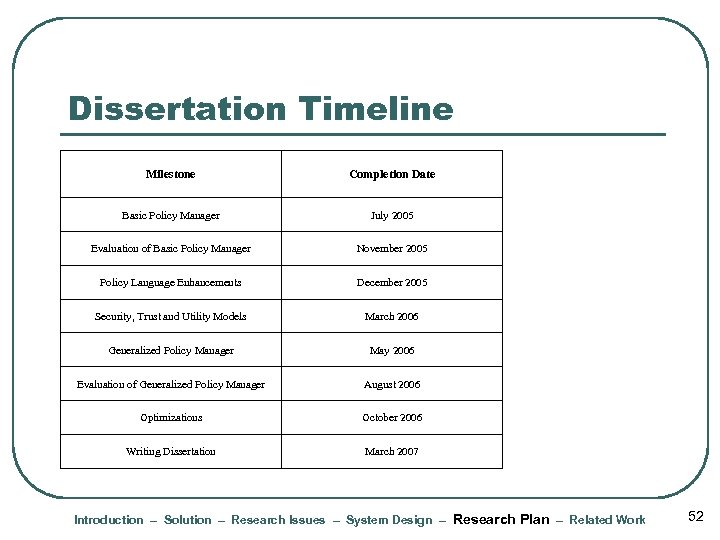
Dissertation Timeline Milestone Completion Date Basic Policy Manager July 2005 Evaluation of Basic Policy Manager November 2005 Policy Language Enhancements December 2005 Security, Trust and Utility Models March 2006 Generalized Policy Manager May 2006 Evaluation of Generalized Policy Manager August 2006 Optimizations October 2006 Writing Dissertation March 2007 Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 52

Related and Complementary Research 53

Research Areas l l Negotiation Protocols Policy Languages Ubiquitous Interoperation Middleware Access Control and Trust Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 54
Protocols and Languages l Negotiation protocols Automated trust negotiation • l • Service level negotiations in grid computing • • • Goal: client-server transactions on the web Conflicts result in failure Trust. Builder [BYU, UIUC], Peer. Trust • SNAP [ISI] Policy languages Rei pervasive computing language • • l • Trust negotiation languages – PSPL, Keynote XML-based web access control – XACML, TPL [IBM] • • Cross-application semantics Deontic concepts Semantic web ontology – DAML+OIL, OWL, SOUPA Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 55
Service Discovery and Access Control Frameworks l l l Middleware for open systems • • • Ubicomp active space middleware – Hyperglue [MIT], Cerberus [UIUC] Service discovery – JINI, UPn. P Limited security features • Advanced Role-Based Access Control Models Access Control • • Generalized RBAC Dynamic RBAC Trust frameworks • SECURE project • Reputation frameworks • • Dynamic notion of trust Trust evolution based on interaction history Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 56
Conclusion l l l Existing means of interoperation are too rigid and unsuitable for ubicomp Identify flexible policy as the minimum requirement Negotiation can be automated using logicbased policy, trust and utility models Applications can rely on the underlying system to discover and access external resources with minimal risk and adjusting with context Promote a security-oriented approach towards the design of intelligent spaces 57

Thank You Relevant publications: l Kevin Eustice, Leonard Kleinrock, Shane Markstrum, Gerald Popek, V. Ramakrishna and Peter Reiher, “Enabling Secure Ubiquitous Interactions, ” In the proceedings of the 1 st International Workshop on Middleware for Pervasive and Ad-Hoc Computing (in conjunction with Middleware 2003), 17 th June 2003 in Rio de Janeiro, Brazil. l K. Eustice, L. Kleinrock, S. Markstrum, G. Popek, V. Ramakrishna and P. Reiher, "Securing Wi. Fi Nomads: The Case for Quarantine, Examination, and Decontamination, " Proceedings of the New Security Paradigms Workshop (NSPW), 2003. 58
Conclusion l l l Existing means of interoperation are too rigid and unsuitable for ubicomp Identify flexible policy as the minimum requirement Negotiation can be automated using logicbased policy, trust and utility models Applications can rely on the underlying system to discover and access external resources with minimal risk and adjusting with context Promote a security-oriented approach towards the design of intelligent spaces 59

Security Aspects l l l Key research aspects • • What security benefits does a negotiation protocol provide to a system offering ubiquitous services? How do we secure the negotiation protocol itself from being compromised? Security benefits • • • Concerns proper use of security mechanisms rather than propose new ones Promotes a paradigm that ensures safety is taken into consideration before interaction Allows static and dynamic detection of security conflicts Protocol security • • Cryptographic mechanisms, SSL, TLS Can the nature of the protocol itself be used to compromise security? Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 60

Research Issues l l l Policy Expression and Reasoning Security and Trust Model Negotiation Heuristics and Strategies Theoretical Issues Systems Issues • Protocol flexibility and extensibility • Performance • Fault tolerance and reliability Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 61

Thesis Proposal A generic and flexible negotiation protocol guided by local policy through which devices and domains in ubicomp can interoperate spontaneously 62

Outline l l l First slide – one line summary of the problem I am tackling Ubicomp vision • • • What has been done How it has been done What is missing, or what needs to be seriously improved; i. e. motivation • • How policy is useful in ubicomp situations Domain-oriented view of world Different categories of policies Potential for conflicts with large number of policies, and the need for expressiveness, domain-independence, well-defined semantics and reasoning mechanisms My approach at a very high level, with the assumptions I make about the world Everything about policy Negotiation as a model for interactions Examples: • • Starbucks: current (simple model); then, with negotiation Another example: maybe the home video example List of benefits/research contributions Research issues Current design and implementation status Research plan and timeline Conclusion 63
Scenario Bob’s PDA DHCP Protocol Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 64
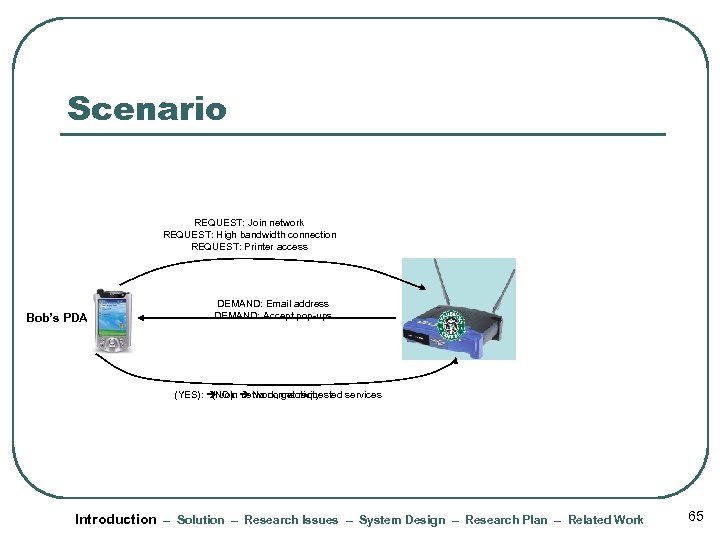
Scenario REQUEST: Join network REQUEST: High bandwidth connection REQUEST: Printer access Bob’s PDA DEMAND: Email address DEMAND: Accept pop-ups (YES): Join No connectivity (NO): network, get requested services Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 65
Ubicomp Interoperation l Nature and purpose of interoperation l Typical interactions • Discovery of external services • Access and usage of resources and data • Service discovery and access control intertwined • Mobile devices and wireless networks • Direct communication between two devices Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 66
Assumptions l l Common networking capability Common understanding of objects at the application layer • Leverage Semantic Web research • Common syntax, or annotations, using XML Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 67

Negotiation Model l l Initial state • Each entity has a set of resources, policies and initial requirements Communication protocol • • Exchange of messages that results in a maximal satisfaction of requirements as constrained by the policies Messages include requests, offers, policy rules Bi-directional protocol (after initial message) Stateful protocol 68
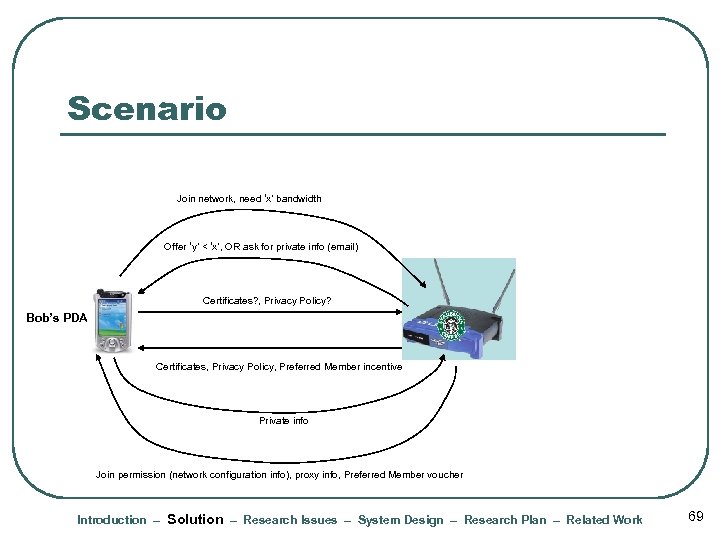
Scenario Join network, need ‘x’ bandwidth Offer ‘y’ < ‘x’, OR ask for private info (email) Certificates? , Privacy Policy? Bob’s PDA Certificates, Privacy Policy, Preferred Member incentive Private info Join permission (network configuration info), proxy info, Preferred Member voucher Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 69
Programming Languages Operating Systems My Research Artificial Intelligence Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 70

More Issues l Systems Issues • Performance (fast retrieval, fast path) • Resource description and management • Fault tolerance and reliability • Scale to multi-party negotiation • Context awareness 71

Beyond 2 -party Negotiation l Multi-session negotiation • (1 n) negotiation • Handle dependencies among multiple • l sessions Scalability issues Multi-party negotiation • (n n) negotiation • Similar dependency issues • Additional distributed systems problems 72
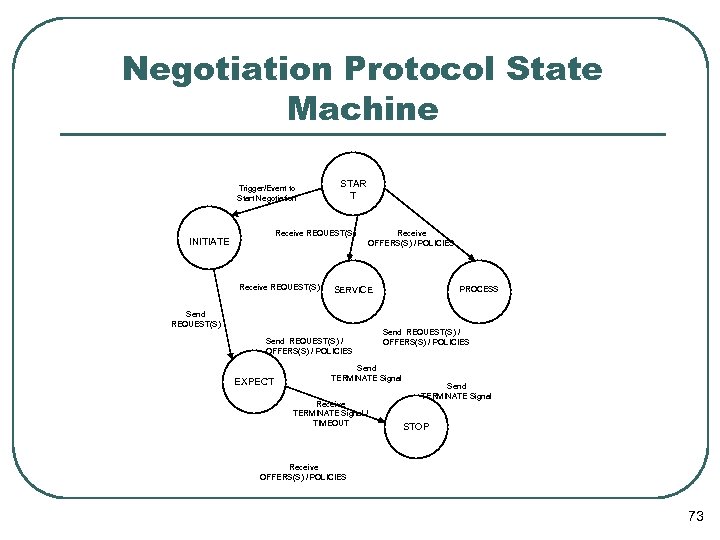
Negotiation Protocol State Machine Trigger/Event to Start Negotiation STAR T Receive REQUEST(S) INITIATE Receive REQUEST(S) PROCESS SERVICE Send REQUEST(S) / OFFERS(S) / POLICIES EXPECT Receive OFFERS(S) / POLICIES Send REQUEST(S) / OFFERS(S) / POLICIES Send TERMINATE Signal Receive TERMINATE Signal / TIMEOUT Send TERMINATE Signal STOP Receive OFFERS(S) / POLICIES 73
Implementation l Policy manager implemented in Java Prolog used for writing policies l Policy Engine based on SWI-Prolog l • Subset of first order logic • Declarative syntax • Fast algorithms for logical reasoning • Java-Prolog and Prolog-Java APIs • Open source • Meta-predicates Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 74
Implementation (continued) l Description of entities, resources, properties l Trust and Access Control Models l Negotiation goals and strategies • XML and RDF • Advanced RBAC models • Fixed goals and alternatives • Fixed strategy, based on satisfaction of relevant policies Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 75
Current Status l Minimal policy manager almost done • Negotiation protocol state machine • Policy engine mechanisms to run queries and • l return state and policy info Controller negotiates by sending requests and counter requests to till success/no progress is possible Next step – testing with Panoply spheres 76
System Optimizations and Enhancements l Design modifications and enhancements based on observed performance • Fast path for quick decision making • Emphasis on strategy that guarantees results in real time l Multi-session negotiation • Investigate inter-thread dependencies • Investigate scaling properties of currently used reasoning algorithms 77
Related Work l l l Automated trust Negotiation • • Sequence of credential exchanges that result in access granted/rejected for a resource Meant for web transactions / not for dynamic environments like ubicomp Policy Languages • • Mostly application specific Rei – targeted for pervasive computing • • Certificates/Delegations Generalized RBAC Access Control Models 78
Negotiation Protocols l l Automated trust negotiation • • Goal: client-server transactions on the web Builds up proof of access through progressive exchange of credentials Conflicts result in failure Examples: Trust. Builder [BYU, UIUC], Peer. Trust • • • A decentralized framework for dynamic resource allocation Typically neglects security concerns Example: SNAP [ISI] Service negotiation in grid computing Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 79
Policy Languages l l Rei policy language • • • Specially targeted towards pervasive computing and the semantic web Defined cross-application semantics Incorporates deontic concepts like obligations and permissions Trust negotiation languages • • Portfolio and Service Protection Language (PSPL) Key. Note • • Limited in expressiveness and support for negotiation Examples: XACML, IBM’s TPL • DAML+OIL, OWL, SOUPA Languages for access control on the web (XML-based) Ontology for the semantic web Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 80
Ubiquitous Middleware l Active Space projects • Examples: Hyperglue, Cerberus, Centaurus 2 • Generally manage resources and are context • l sensitive Limited security and access control features Service discovery frameworks • Examples: Jini, UPn. P • Emphasis on open interfaces and easy interoperation rather than security Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 81
Access Control and Trust l l l ACLs and capabilities • Not scalable or usable in dynamic conditions • • • Not very flexible Generalized RBAC (GRBAC) Dynamic RBAC (d. RBAC) Role-based Access Control Trust • Fairly well-accepted concept in ubicomp • Policy. Maker • Credentials tied to permissions rather than identity • SECURE project • • • Dynamic notion of trust Trust evolution based on interaction history Reputation frameworks Introduction – Solution – Research Issues – System Design – Research Plan – Related Work 82
Conclusion l Spontaneous ubiquitous interoperation poses many challenges • l Flexible process of reaching agreements through negotiation • • l Mechanisms exist, but no frameworks Policy management is the core Trust and utility models Existing research • • Fails to address problem in its entirety, or Produces domain-specific solutions 83
687b452931c19025930090ac265b3d4e.ppt