173ae8157fb8790248e6b96ab0f819b2.ppt
- Количество слайдов: 29

Policy-Driven Negotiations and Explanations on the Semantic Web Daniel Olmedilla L 3 s Research Center / Hannover University L 3 S Research Seminar 18 th Nov. 2005

Motivation Scenario Buying in Internet n Bob wants to access an electronic AI book at “E-Book Store” (a web site he found while surfing in Internet) n Previously, E-Book requires Bob to register providing full name, age, complete address, telephone and e-mail n Bob does not mind to give his full name and age but he does not like to provide his complete address, telephone and e-mail. However, he does not have any other option so he does it (although he does not provide his real address and telephone). n E-Book sells that book. Therefore now it asks Bob to provide his credit card information. Bob would not mind to buy the book because it is not too expensive and he is really interested in reading it. However, he has never heard about E-Book so he decides to not buy it Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 2
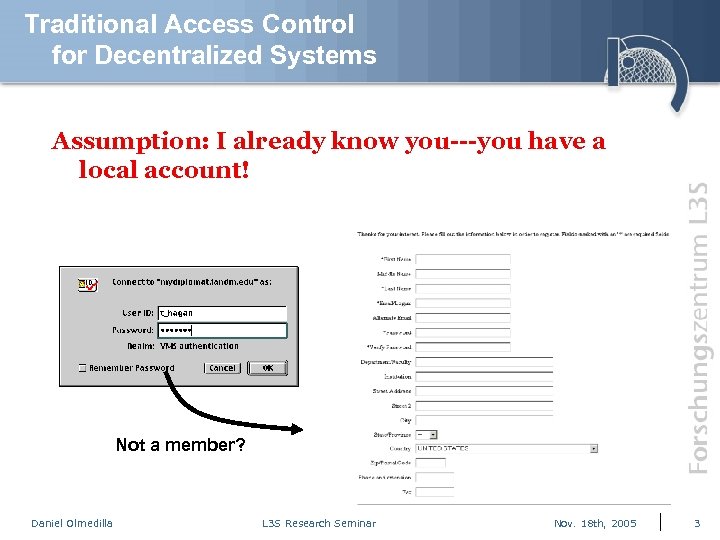
Traditional Access Control for Decentralized Systems Assumption: I already know you---you have a local account! Not a member? Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 3

Policy-Driven Negotiation (I) General Picture n Every party can define policies to control outsiders’ use of its resources § Service access control (security) § Credential disclosure control (privacy) § Business rules n Decisions are based on parties’ properties n Properties are established iteratively and bilaterally by the disclosure of certificates and declarations, i. e. negotiations [ Winsborough, Seamons, Jones. Automated Trust Negotiation. DARPA Information Survivability Conference and Exposition, 2000] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 4
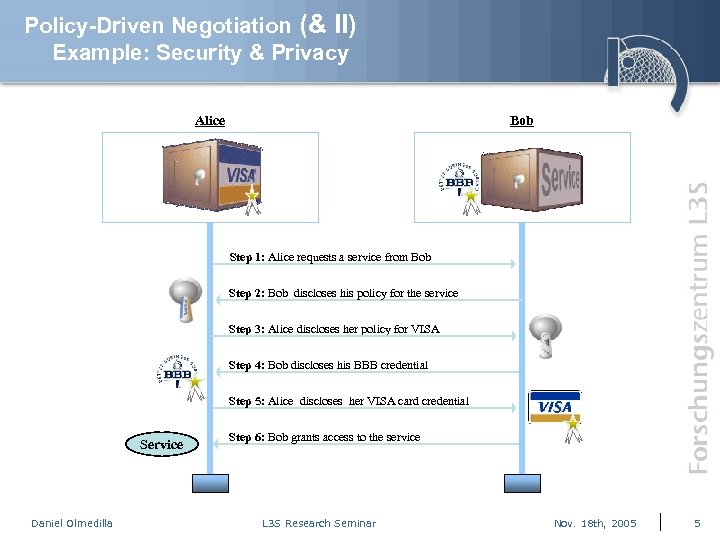
Policy-Driven Negotiation (& II) Example: Security & Privacy Alice Bob Step 1: Alice requests a service from Bob Step 2: Bob discloses his policy for the service Step 3: Alice discloses her policy for VISA Step 4: Bob discloses his BBB credential Step 5: Alice discloses her VISA card credential Service Daniel Olmedilla Step 6: Bob grants access to the service L 3 S Research Seminar Nov. 18 th, 2005 5

Policy Specification (I) What does policy refers to? The term policy refers to: n Security Policies: pose constraints on the behavior of a system n Trust Management Policies: typically used to collect user properties in open environments n Business Rules: statements about how a business is done In addition, associated to policies one needs to execute actions. Therefore also relevant: n Action Languages: used in reactive policy specification to execute actions [ Bonatti, Shahmehri, Duma, Olmedilla, Nejdl, Baldoni, Baroglio, Martelli, Patti, Coraggio, Antoniou, Peer, Fuchs. Rule-based Policy Specification: State of the Art and Future Work. Project deliverable D 1, Working Group I 2, EU No. E REWERSE ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 6

Policy Specification (& II) Integration of Policies Although many approaches have been described to address the above points, there is no common solution, integrating them all in a single framework. Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 7
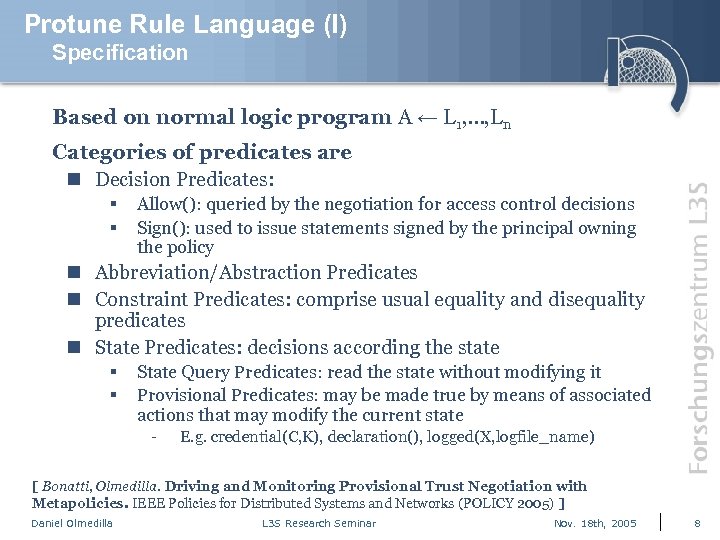
Protune Rule Language (I) Specification Based on normal logic program A ← L 1, …, Ln Categories of predicates are n Decision Predicates: § § Allow(): queried by the negotiation for access control decisions Sign(): used to issue statements signed by the principal owning the policy n Abbreviation/Abstraction Predicates n Constraint Predicates: comprise usual equality and disequality predicates n State Predicates: decisions according the state § § State Query Predicates: read the state without modifying it Provisional Predicates: may be made true by means of associated actions that may modify the current state - E. g. credential(C, K), declaration(), logged(X, logfile_name) [ Bonatti, Olmedilla. Driving and Monitoring Provisional Trust Negotiation with Metapolicies. IEEE Policies for Distributed Systems and Networks (POLICY 2005) ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 8
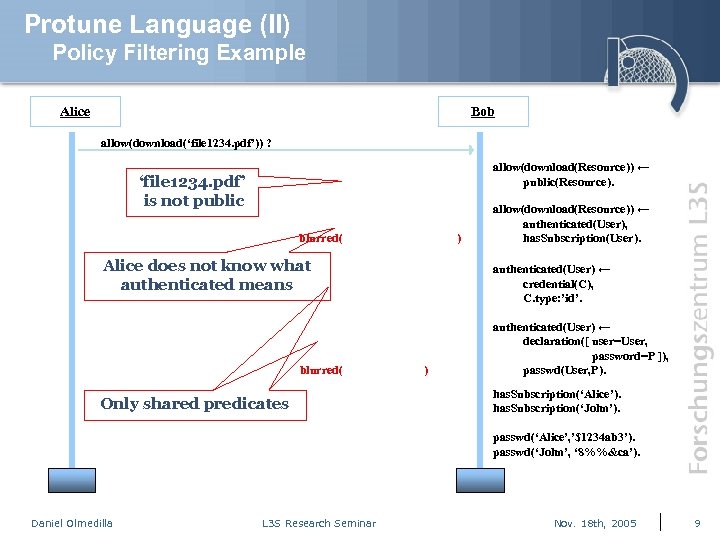
Protune Language (II) Policy Filtering Example Alice Bob allow(download(‘file 1234. pdf’)) ? allow(download(Resource)) ← public(Resource). ‘file 1234. pdf’ is not public blurred( ) Alice does not know what authenticated means blurred( Only shared predicates allow(download(Resource)) ← authenticated(User), has. Subscription(User). authenticated(User) ← credential(C), C. type: ’id’. ) authenticated(User) ← declaration([ user=User, password=P ]), passwd(User, P). has. Subscription(‘Alice’). has. Subscription(‘John’). passwd(‘Alice’, ’$1234 ab 3’). passwd(‘John’, ‘ 8%%&ca’). Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 9
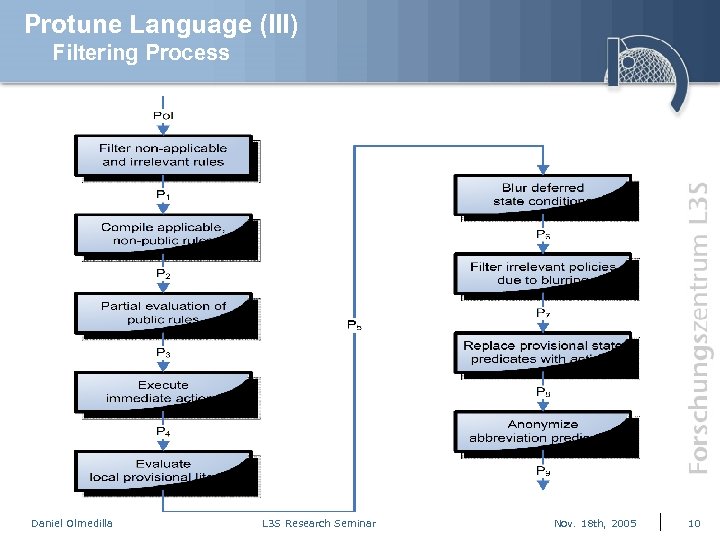
Protune Language (III) Filtering Process Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 10
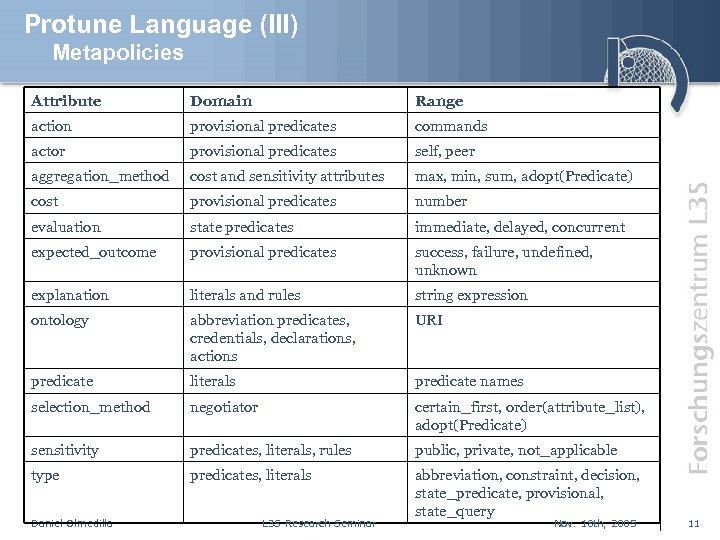
Protune Language (III) Metapolicies Attribute Domain Range action provisional predicates commands actor provisional predicates self, peer aggregation_method cost and sensitivity attributes max, min, sum, adopt(Predicate) cost provisional predicates number evaluation state predicates immediate, delayed, concurrent expected_outcome provisional predicates success, failure, undefined, unknown explanation literals and rules string expression ontology abbreviation predicates, credentials, declarations, actions URI predicate literals predicate names selection_method negotiator certain_first, order(attribute_list), adopt(Predicate) sensitivity predicates, literals, rules public, private, not_applicable type predicates, literals abbreviation, constraint, decision, state_predicate, provisional, state_query Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 11
PROTUNE Policy Language (& IV) Metapolicy Examples table(Key, Data). evaluation: immediate ← ground(Key). logged(Msg, File). action: ’echo’+Msg+’>’+File. credential(_). ontology: URI. abbrev(_). explanation: ”this condition checks…”. Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 12
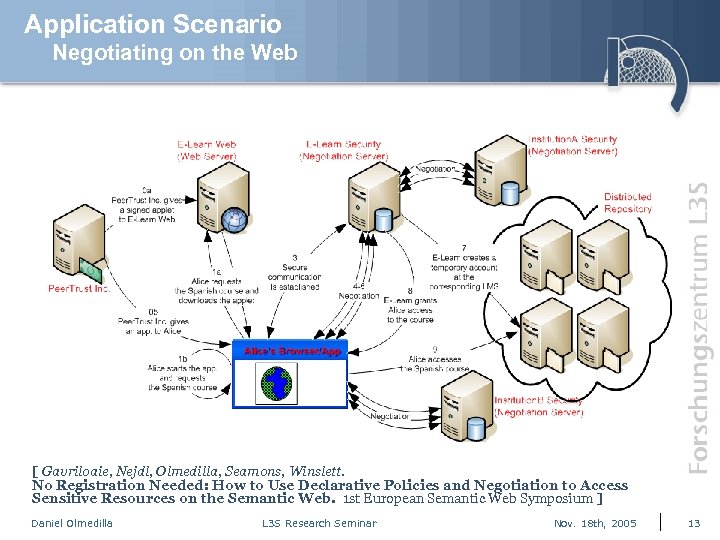
Application Scenario Negotiating on the Web [ Gavriloaie, Nejdl, Olmedilla, Seamons, Winslett. No Registration Needed: How to Use Declarative Policies and Negotiation to Access Sensitive Resources on the Semantic Web. 1 st European Semantic Web Symposium ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 13

Policy Answering & Explanations (I) Motivation Suppose Alice's request is rejected She may want to ask questions like: n Why didn't you accept my credit card? Other possible queries n How-to queries n What-if queries § Would I get the special discount on financial products X if I were locally employed? Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 14

Policy Answering & Explanations (& II) Analysis and Requirements n Easy instantiation in any given app. domain § One step extra creating literal verbalization rules n Performance § § Should not increase significantly the computational load of servers Constructed at client side n Explanation method § § Focus on the parts of the search space relevant to the user Concise (pruned irrelevant information) vs. detailed n Presentation strategies § § § Different kind of queries: why/why-not, how-to, what-if Breaking up and pruning of proofs and explanations Explanation navigation: Proof as a (potentially cyclic) hypertext n Based on § § Set of (computed) answer substitutions - Tabled explanation structure Verbalization patterns [ Bonatti, Olmedilla, Peer. Advance Policy Queries. Project deliverable D 4, Working Group I 2, EU No. E REWERSE ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 15
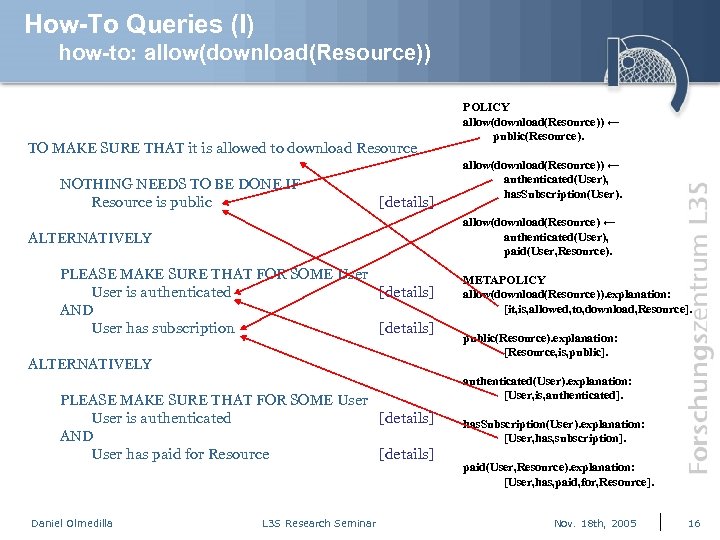
How-To Queries (I) how-to: allow(download(Resource)) TO MAKE SURE THAT it is allowed to download Resource NOTHING NEEDS TO BE DONE IF Resource is public [details] allow(download(Resource)) ← authenticated(User), has. Subscription(User). allow(download(Resource) ← authenticated(User), paid(User, Resource). ALTERNATIVELY PLEASE MAKE SURE THAT FOR SOME User is authenticated [details] AND User has subscription [details] ALTERNATIVELY PLEASE MAKE SURE THAT FOR SOME User is authenticated [details] AND User has paid for Resource [details] Daniel Olmedilla POLICY allow(download(Resource)) ← public(Resource). L 3 S Research Seminar METAPOLICY allow(download(Resource)). explanation: [it, is, allowed, to, download, Resource]. public(Resource). explanation: [Resource, is, public]. authenticated(User). explanation: [User, is, authenticated]. has. Subscription(User). explanation: [User, has, subscription]. paid(User, Resource). explanation: [User, has, paid, for, Resource]. Nov. 18 th, 2005 16
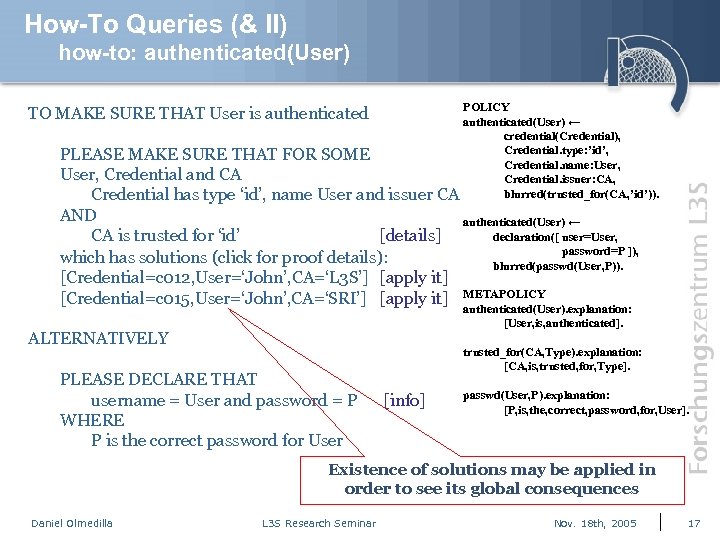
How-To Queries (& II) how-to: authenticated(User) POLICY authenticated(User) ← credential(Credential), Credential. type: ’id’, Credential. name: User, Credential. issuer: CA, blurred(trusted_for(CA, ’id’)). TO MAKE SURE THAT User is authenticated PLEASE MAKE SURE THAT FOR SOME User, Credential and CA Credential has type ‘id’, name User and issuer CA AND authenticated(User) ← declaration([ user=User, CA is trusted for ‘id’ [details] password=P ]), which has solutions (click for proof details): blurred(passwd(User, P)). [Credential=c 012, User=‘John’, CA=‘L 3 S’] [apply it] [Credential=c 015, User=‘John’, CA=‘SRI’] [apply it] METAPOLICY authenticated(User). explanation: [User, is, authenticated]. ALTERNATIVELY PLEASE DECLARE THAT username = User and password = P WHERE P is the correct password for User trusted_for(CA, Type). explanation: [CA, is, trusted, for, Type]. [info] passwd(User, P). explanation: [P, is, the, correct, password, for, User]. Existence of solutions may be applied in order to see its global consequences Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 17
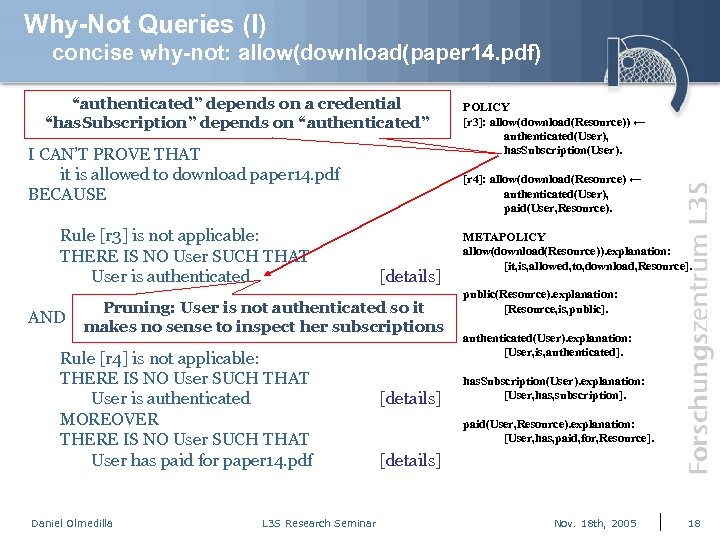
Why-Not Queries (I) concise why-not: allow(download(paper 14. pdf) “authenticated” depends on a credential “has. Subscription” depends on “authenticated” I CAN’T PROVE THAT it is allowed to download paper 14. pdf BECAUSE Rule [r 3] is not applicable: THERE IS NO User SUCH THAT User is authenticated AND [r 4]: allow(download(Resource) ← authenticated(User), paid(User, Resource). [details] Pruning: User is not authenticated so it makes no sense to inspect her subscriptions Rule [r 4] is not applicable: THERE IS NO User SUCH THAT User is authenticated MOREOVER THERE IS NO User SUCH THAT User has paid for paper 14. pdf Daniel Olmedilla L 3 S Research Seminar POLICY [r 3]: allow(download(Resource)) ← authenticated(User), has. Subscription(User). [details] METAPOLICY allow(download(Resource)). explanation: [it, is, allowed, to, download, Resource]. public(Resource). explanation: [Resource, is, public]. authenticated(User). explanation: [User, is, authenticated]. has. Subscription(User). explanation: [User, has, subscription]. paid(User, Resource). explanation: [User, has, paid, for, Resource]. [details] Nov. 18 th, 2005 18
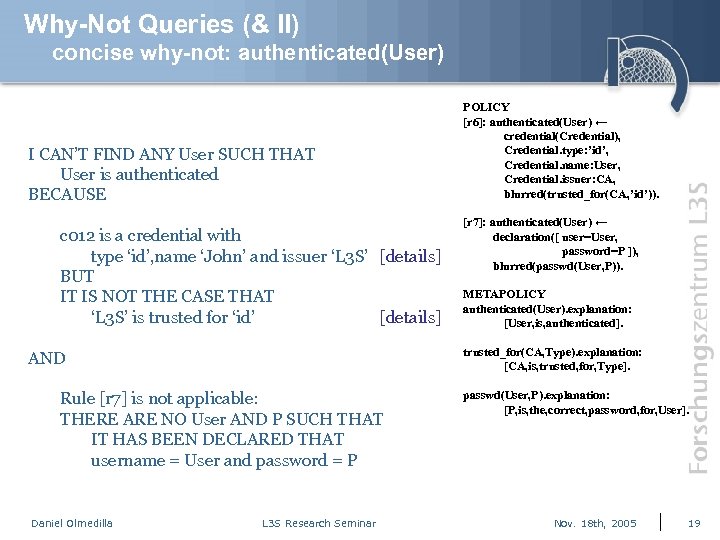
Why-Not Queries (& II) concise why-not: authenticated(User) I CAN’T FIND ANY User SUCH THAT User is authenticated BECAUSE c 012 is a credential with type ‘id’, name ‘John’ and issuer ‘L 3 S’ [details] BUT IT IS NOT THE CASE THAT ‘L 3 S’ is trusted for ‘id’ [details] [r 7]: authenticated(User) ← declaration([ user=User, password=P ]), blurred(passwd(User, P)). METAPOLICY authenticated(User). explanation: [User, is, authenticated]. trusted_for(CA, Type). explanation: [CA, is, trusted, for, Type]. AND Rule [r 7] is not applicable: THERE ARE NO User AND P SUCH THAT IT HAS BEEN DECLARED THAT username = User and password = P Daniel Olmedilla POLICY [r 6]: authenticated(User) ← credential(Credential), Credential. type: ’id’, Credential. name: User, Credential. issuer: CA, blurred(trusted_for(CA, ’id’)). L 3 S Research Seminar passwd(User, P). explanation: [P, is, the, correct, password, for, User]. Nov. 18 th, 2005 19
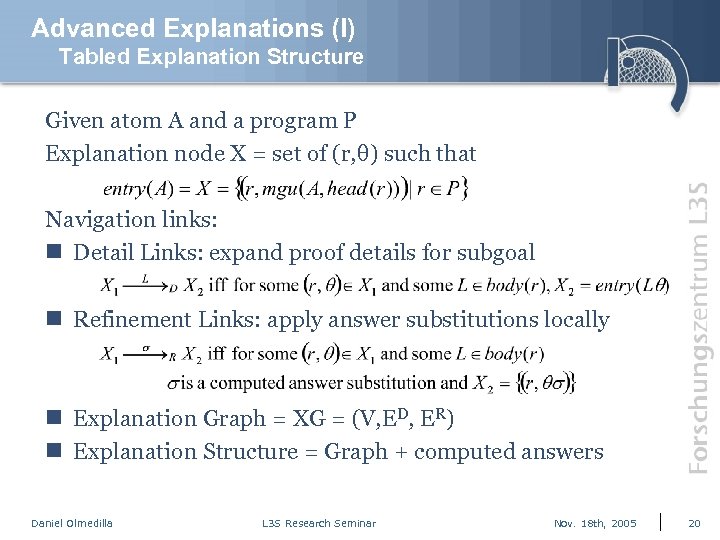
Advanced Explanations (I) Tabled Explanation Structure Given atom A and a program P Explanation node X = set of (r, θ) such that Navigation links: n Detail Links: expand proof details for subgoal n Refinement Links: apply answer substitutions locally n Explanation Graph = XG = (V, ED, ER) n Explanation Structure = Graph + computed answers Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 20

Advanced Explanations (& II) Novel Aspects n Tabled explanation structure § vs. single derivations or proof trees n Show simultaneously different proof attempts § Allow to see local (intra-proof) and global (inter-proof) n Heuristics to remove irrelevant information § But provide full explanations too n Heuristics are generic, domain independent n Lightweight and scalable § Most of computational effort is delegated to clients Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 21

REWERSE WG I 2 (I) Mission n Integration of policies § Security policies, Trust management § Business rules, Quality of service specs. n Enhance user control and awareness on system behavior n Reduce the cost of building and maintaining cooperative systems Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 22

REWERSE WG I 2 (& II) Current Actions n Adopt a rule-based policy specification language: PROTUNE § Flexible and structurally similar to the natural way policies are expressed n Advanced explanation mechanisms § To help the user to understand what policies prescribe and control n Controlled Natural Language front-end § To translate natural language text into rules § Generate automatically explanations in natural language Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 23

Further Work Other REWERSE I 2 Objectives n Negotiation Strategies n Integration of policy-based and reputation-based trust management n Integrate event-condition-action (ECA) rules n Natural language front-end to the policy domain § § Daniel Olmedilla Natural Language Processing (NLP) Automatic generation of natural language explanations from proofs and filtered policies L 3 S Research Seminar Nov. 18 th, 2005 24

Thanks! Questions? olmedilla@l 3 s. de - http: //www. l 3 s. de/~olmedilla/ Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 25
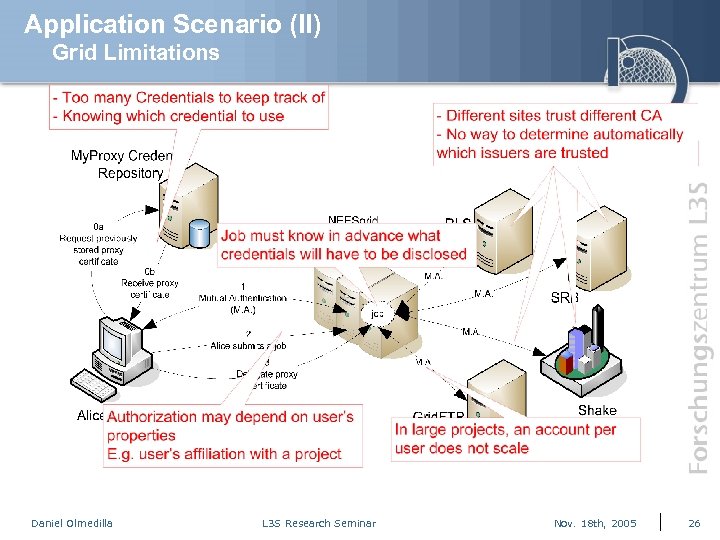
Application Scenario (II) Grid Limitations Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 26
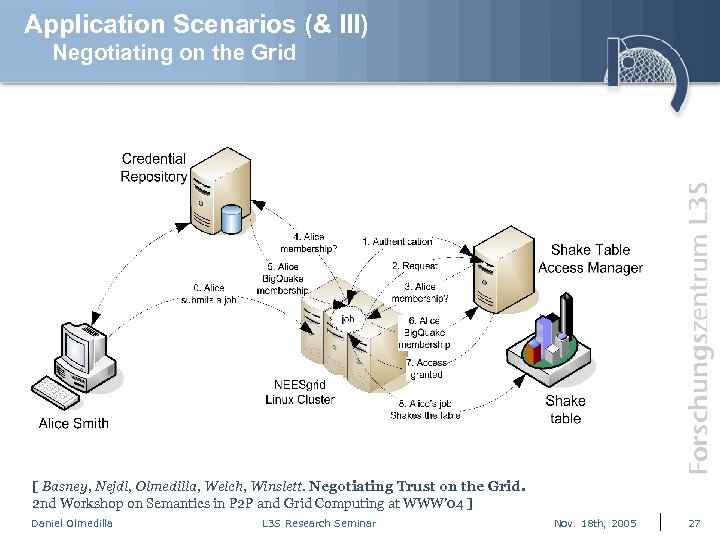
Application Scenarios (& III) Negotiating on the Grid [ Basney, Nejdl, Olmedilla, Welch, Winslett. Negotiating Trust on the Grid. 2 nd Workshop on Semantics in P 2 P and Grid Computing at WWW’ 04 ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 27

Reference Scenario (& IV) Natural Language We are aiming at natural rule/query formulation n Users can download the files in folder historical_data if the creation date precedes 1/1/2000 Policy enforcement, negotiations, query answering should all be automatically derived from such specifications n Attempto Controlled English Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 28
Trust Management Reputation-based vs Policy-based Reputation-based Policy-based access. Granted(Res) credential(X, VISA), X. type : credit card, X. owner : B. trust(A, B, download(file), 80− 100) credential(X, VISA), X. type : credit card, X. owner : B. allow(visa. Card) credential(member(Requester), bbb), trust(self, Requester, buying, X), X > 0. 8. in(trust(X, Y , A, L), reputation pckg : eval trust())) [Staab, Bhargava, Lilien, Rosenthal, Winslett, Sloman, Dillon, Chang, Hussain, Nejdl, Olmedilla, Kashya The Pudding of Trust. IEEE Intelligent Systems Journal, Vol. 19(5), Sep. /Oct. 2004 ] [ Bonatti, Duma, Olmedilla, Shahmehri. An Integration of Reputation-based and Policybased Trust Management. Submitted for Publication ] Daniel Olmedilla L 3 S Research Seminar Nov. 18 th, 2005 29
173ae8157fb8790248e6b96ab0f819b2.ppt