1728676c320333aa422815eec04d82c3.ppt
- Количество слайдов: 59
 PKI SYSTEMS Concepts, Processes, Components Mert ÖZARAR Project Senior Engineer mert. ozarar@turktrust. com. tr TÜRKTRUST Information Security Services Inc. 1
PKI SYSTEMS Concepts, Processes, Components Mert ÖZARAR Project Senior Engineer mert. ozarar@turktrust. com. tr TÜRKTRUST Information Security Services Inc. 1
 Agenda Certification Authority (CA) / Certification Service Provider (CSP) Electronic Signature and Legal Validity Electronic Certificate PKI Functions and Technology PKI Components and Business Models Trust Models and PKI Architectures Certificate Life Cycle – Certificate Application, Registration, Issuance, Dissemination, Renewal, Rekey, Suspension and Revocation Processes © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 2
Agenda Certification Authority (CA) / Certification Service Provider (CSP) Electronic Signature and Legal Validity Electronic Certificate PKI Functions and Technology PKI Components and Business Models Trust Models and PKI Architectures Certificate Life Cycle – Certificate Application, Registration, Issuance, Dissemination, Renewal, Rekey, Suspension and Revocation Processes © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 2
 Certification Authority (CA) Certification Service Provider (CSP) Certification Authority: Authority trusted by one or more users to create and assign certificates (ITU-T Recommendation X. 509) – definition of “ETSI TS 101 456 – Policy requirements for certification authorities issuing qualified certificates” ‘Certification-service-provider’ means an entity or a legal or natural person who issues certificates or provides other services related to electronic signatures – definiton of “EU Directive 1999/93/EC on a Community framework for electronic signatures” © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 3
Certification Authority (CA) Certification Service Provider (CSP) Certification Authority: Authority trusted by one or more users to create and assign certificates (ITU-T Recommendation X. 509) – definition of “ETSI TS 101 456 – Policy requirements for certification authorities issuing qualified certificates” ‘Certification-service-provider’ means an entity or a legal or natural person who issues certificates or provides other services related to electronic signatures – definiton of “EU Directive 1999/93/EC on a Community framework for electronic signatures” © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 3
 Electronic Certificate Service Provider (ECSP) Article 8 (Turkish Electronic Signature Law no. 5070) Electronic certificate service providers shall be public entities and establishments and natural persons or private law legal entities that provide electronic certificates, time-stamping and other services related to electronic signatures Related services Management of electronic certificate application, generation, dissemination, revocation and renewal processes Certificate status information services (CRL/OCSP) Keeping the records for certification operations Time stamping services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 4
Electronic Certificate Service Provider (ECSP) Article 8 (Turkish Electronic Signature Law no. 5070) Electronic certificate service providers shall be public entities and establishments and natural persons or private law legal entities that provide electronic certificates, time-stamping and other services related to electronic signatures Related services Management of electronic certificate application, generation, dissemination, revocation and renewal processes Certificate status information services (CRL/OCSP) Keeping the records for certification operations Time stamping services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 4
 Electronic Certificate Service Provider (ECSP) It is indispensable for an ECSP to own the following principles in order to be able to maintain its processes appropriately: Trust and reliability Capability and expertise Stability and continuity Impartiality Technical and physical infrastructure Quality focused customer services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 5
Electronic Certificate Service Provider (ECSP) It is indispensable for an ECSP to own the following principles in order to be able to maintain its processes appropriately: Trust and reliability Capability and expertise Stability and continuity Impartiality Technical and physical infrastructure Quality focused customer services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 5
 “Electronic Signature” Definition EU Directive 1999/93/EC ‘electronic signature’ means data in electronic form which are attached to or logically associated with other electronic data and which serve as a method of authentication; (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 6
“Electronic Signature” Definition EU Directive 1999/93/EC ‘electronic signature’ means data in electronic form which are attached to or logically associated with other electronic data and which serve as a method of authentication; (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 6
 “Advanced Electronic Signature” Definition EU Directive 1999/93/EC ‘Advanced electronic signature’ means an electronic signature which meets the following requirements: (a) it is uniquely linked to the signatory; (b) it is capable of identifying the signatory; (c) it is created using means that the signatory can maintain under his sole control; and (d) it is linked to the data to which it relates in such a manner that any subsequent change of the data is detectable. (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 7
“Advanced Electronic Signature” Definition EU Directive 1999/93/EC ‘Advanced electronic signature’ means an electronic signature which meets the following requirements: (a) it is uniquely linked to the signatory; (b) it is capable of identifying the signatory; (c) it is created using means that the signatory can maintain under his sole control; and (d) it is linked to the data to which it relates in such a manner that any subsequent change of the data is detectable. (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 7
 “Qualified Electronic Signature” Definition EU Directive 1999/93/EC Qualified Electronic Signature: Advanced electronic signature which is based on a qualified certificate and which is created by a secure-signature-creation device. (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 8
“Qualified Electronic Signature” Definition EU Directive 1999/93/EC Qualified Electronic Signature: Advanced electronic signature which is based on a qualified certificate and which is created by a secure-signature-creation device. (also ETSI TS 101 456 definition) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 8
 Electronic Signature in Turkish Legislation Turkish Electronic Signature Law (No. 5070) has been put into effect on July 23, 2005. Regulations have been published by Turkish Telecommunications Authority on January 6, 2005. Electronic Signature Law (no. 5070) – TURKEY Article 3. b – Electronic Signature Data in electronic form that are attached to other electronic data or logically linked to that electronic data and used for authentication. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 9
Electronic Signature in Turkish Legislation Turkish Electronic Signature Law (No. 5070) has been put into effect on July 23, 2005. Regulations have been published by Turkish Telecommunications Authority on January 6, 2005. Electronic Signature Law (no. 5070) – TURKEY Article 3. b – Electronic Signature Data in electronic form that are attached to other electronic data or logically linked to that electronic data and used for authentication. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 9
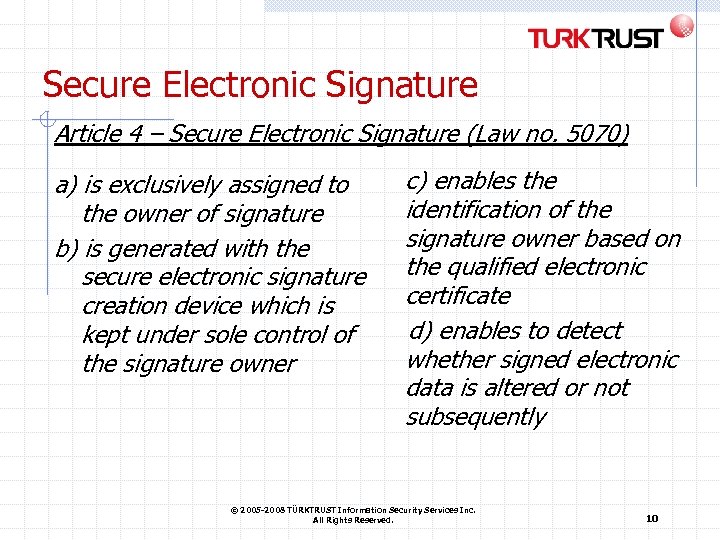 Secure Electronic Signature Article 4 – Secure Electronic Signature (Law no. 5070) a) is exclusively assigned to the owner of signature b) is generated with the secure electronic signature creation device which is kept under sole control of the signature owner c) enables the identification of the signature owner based on the qualified electronic certificate d) enables to detect whether signed electronic data is altered or not subsequently © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 10
Secure Electronic Signature Article 4 – Secure Electronic Signature (Law no. 5070) a) is exclusively assigned to the owner of signature b) is generated with the secure electronic signature creation device which is kept under sole control of the signature owner c) enables the identification of the signature owner based on the qualified electronic certificate d) enables to detect whether signed electronic data is altered or not subsequently © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 10
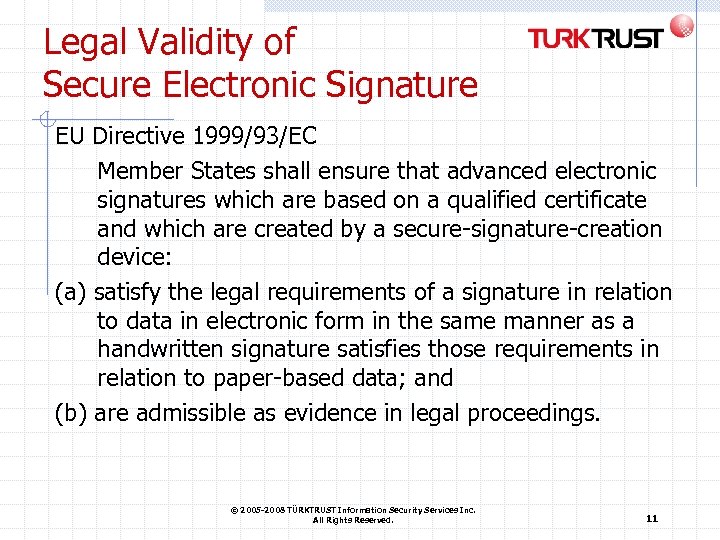 Legal Validity of Secure Electronic Signature EU Directive 1999/93/EC Member States shall ensure that advanced electronic signatures which are based on a qualified certificate and which are created by a secure-signature-creation device: (a) satisfy the legal requirements of a signature in relation to data in electronic form in the same manner as a handwritten signature satisfies those requirements in relation to paper-based data; and (b) are admissible as evidence in legal proceedings. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 11
Legal Validity of Secure Electronic Signature EU Directive 1999/93/EC Member States shall ensure that advanced electronic signatures which are based on a qualified certificate and which are created by a secure-signature-creation device: (a) satisfy the legal requirements of a signature in relation to data in electronic form in the same manner as a handwritten signature satisfies those requirements in relation to paper-based data; and (b) are admissible as evidence in legal proceedings. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 11
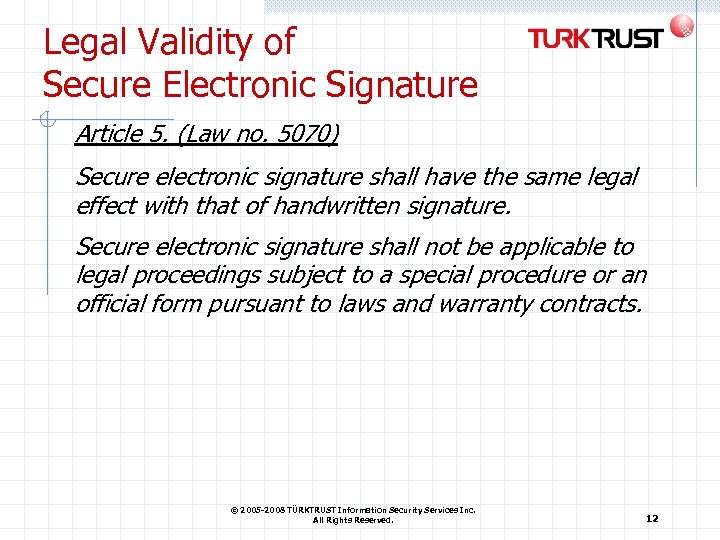 Legal Validity of Secure Electronic Signature Article 5. (Law no. 5070) Secure electronic signature shall have the same legal effect with that of handwritten signature. Secure electronic signature shall not be applicable to legal proceedings subject to a special procedure or an official form pursuant to laws and warranty contracts. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 12
Legal Validity of Secure Electronic Signature Article 5. (Law no. 5070) Secure electronic signature shall have the same legal effect with that of handwritten signature. Secure electronic signature shall not be applicable to legal proceedings subject to a special procedure or an official form pursuant to laws and warranty contracts. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 12
 “Certificate” Definition EU Directive 1999/93/EC ‘Certificate’ means an electronic attestation which links signature-verification data to a person and confirms the identity of that person. ETSI TS 101 456 Certificate: Public key of a user, together with some other information, rendered un-forgeable by encipherment with the private key of the certification authority which issued it (see ITU-T Recommendation X. 509). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 13
“Certificate” Definition EU Directive 1999/93/EC ‘Certificate’ means an electronic attestation which links signature-verification data to a person and confirms the identity of that person. ETSI TS 101 456 Certificate: Public key of a user, together with some other information, rendered un-forgeable by encipherment with the private key of the certification authority which issued it (see ITU-T Recommendation X. 509). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 13
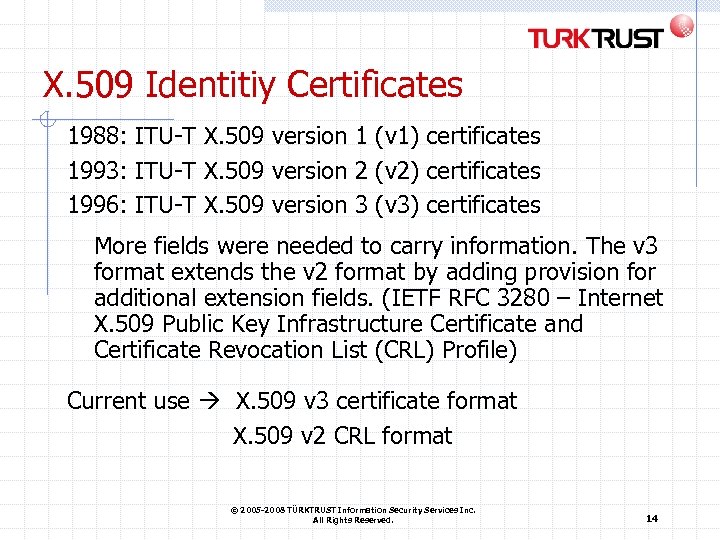 X. 509 Identitiy Certificates 1988: ITU-T X. 509 version 1 (v 1) certificates 1993: ITU-T X. 509 version 2 (v 2) certificates 1996: ITU-T X. 509 version 3 (v 3) certificates More fields were needed to carry information. The v 3 format extends the v 2 format by adding provision for additional extension fields. (IETF RFC 3280 – Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile) Current use X. 509 v 3 certificate format X. 509 v 2 CRL format © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 14
X. 509 Identitiy Certificates 1988: ITU-T X. 509 version 1 (v 1) certificates 1993: ITU-T X. 509 version 2 (v 2) certificates 1996: ITU-T X. 509 version 3 (v 3) certificates More fields were needed to carry information. The v 3 format extends the v 2 format by adding provision for additional extension fields. (IETF RFC 3280 – Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile) Current use X. 509 v 3 certificate format X. 509 v 2 CRL format © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 14
 “Qualified Certificate” Profile IETF RFC 3739 – Internet X. 509 Public Key Infrastructure Qualified Certificates Profile It is based on [X. 509] and [RFC 3280], which defines underlying certificate formats and semantics needed for a full implementation of this standard. This profile includes specific mechanisms intended for use with Qualified Certificates. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 15
“Qualified Certificate” Profile IETF RFC 3739 – Internet X. 509 Public Key Infrastructure Qualified Certificates Profile It is based on [X. 509] and [RFC 3280], which defines underlying certificate formats and semantics needed for a full implementation of this standard. This profile includes specific mechanisms intended for use with Qualified Certificates. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 15
 “Qualified Certificate” Profile ETSI TS 101 862 – Qualified Certificate Profile The following statements are defined in the document: Statement claiming that the certificate is issued as a Qualified Certificate; Statement regarding limits on the value of transactions for which the certificate can be used; Statement indicating the duration of the retention period during which registration information is archived; Statement claiming that the private key associated with the public key in the certificate resides within a Secure Signature Creation Device. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 16
“Qualified Certificate” Profile ETSI TS 101 862 – Qualified Certificate Profile The following statements are defined in the document: Statement claiming that the certificate is issued as a Qualified Certificate; Statement regarding limits on the value of transactions for which the certificate can be used; Statement indicating the duration of the retention period during which registration information is archived; Statement claiming that the private key associated with the public key in the certificate resides within a Secure Signature Creation Device. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 16
 Electronic Certificate X. 509 Name Surname Article 3. i – Electronic Certificate Electronic data binding the signature verification data of the signature owner to identity data of that person © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 17
Electronic Certificate X. 509 Name Surname Article 3. i – Electronic Certificate Electronic data binding the signature verification data of the signature owner to identity data of that person © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 17
 Qualified Electronic Certificate Article 9 (Law no. 5070) Signature Verification Data (Public Key) Certificate serial number Issuer and country information A statement identifying the certificate as qualified Certificate owner’s identification information Proof of authority to act on behalf of someone else Occupation information Certificate usage conditions Certificate validity period © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. ECSP’s Electronic Signature 18
Qualified Electronic Certificate Article 9 (Law no. 5070) Signature Verification Data (Public Key) Certificate serial number Issuer and country information A statement identifying the certificate as qualified Certificate owner’s identification information Proof of authority to act on behalf of someone else Occupation information Certificate usage conditions Certificate validity period © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. ECSP’s Electronic Signature 18
 Common Certificate Types Qualified Electronic Certificates (QEC) SSL Server Certificates Object Signing Certificates Security Certificates / Simple Electronic Certificates Root Certificates © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 19
Common Certificate Types Qualified Electronic Certificates (QEC) SSL Server Certificates Object Signing Certificates Security Certificates / Simple Electronic Certificates Root Certificates © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 19
 Why Electronic Signature? Electronic signature allows secure transactions through electronic media in the following applications while enabling time, money and human resources savings. Electronic correspondence and agreements Legal processes Financial and banking applications Electronic transactions with governmental bodies Insurance applications Business processes running on ERP or document management applications E-government, e-commerce, e-business applications © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 20
Why Electronic Signature? Electronic signature allows secure transactions through electronic media in the following applications while enabling time, money and human resources savings. Electronic correspondence and agreements Legal processes Financial and banking applications Electronic transactions with governmental bodies Insurance applications Business processes running on ERP or document management applications E-government, e-commerce, e-business applications © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 20
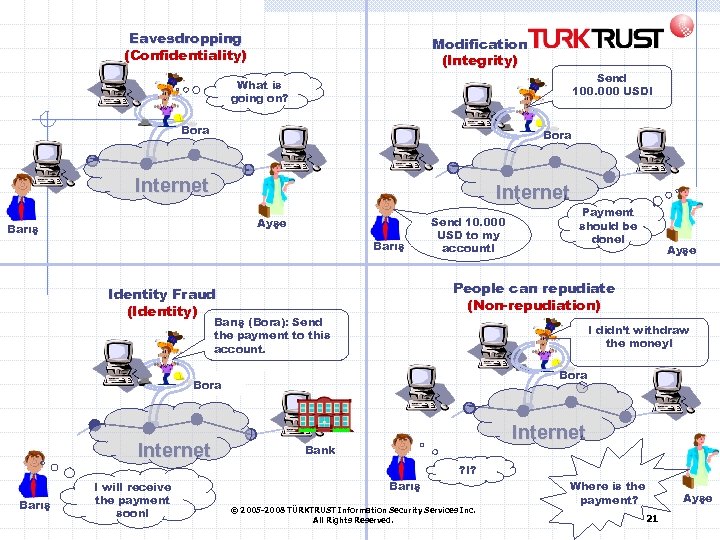 Eavesdropping (Confidentiality) Modification (Integrity) Send 100. 000 USD! What is going on? Bora Internet Ayşe Barış Send 10. 000 USD to my account! Ayşe People can repudiate (Non-repudiation) Identity Fraud (Identity) Barış (Bora): Send the payment to this account. I didn’t withdraw the money! Bora Internet Payment should be done! Internet Bank ? !? Barış I will receive the payment soon! Barış © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. Where is the payment? Ayşe 21
Eavesdropping (Confidentiality) Modification (Integrity) Send 100. 000 USD! What is going on? Bora Internet Ayşe Barış Send 10. 000 USD to my account! Ayşe People can repudiate (Non-repudiation) Identity Fraud (Identity) Barış (Bora): Send the payment to this account. I didn’t withdraw the money! Bora Internet Payment should be done! Internet Bank ? !? Barış I will receive the payment soon! Barış © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. Where is the payment? Ayşe 21
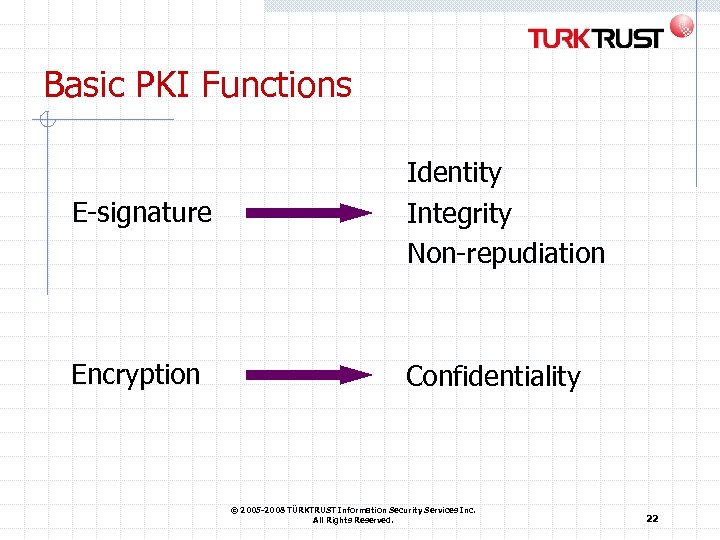 Basic PKI Functions E-signature Identity Integrity Non-repudiation Encryption Confidentiality © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 22
Basic PKI Functions E-signature Identity Integrity Non-repudiation Encryption Confidentiality © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 22
 Key Pair Article 3. d – Signature Creation Data (Law no. 5070) Unique data such as password and cryptographic keys belonging to signature owners and being used by signature owner in order to create electronic signatures Article 3. f – Signature Verification Data (Law no. 5070) Data such as passwords and cryptographic public keys used for the verification of electronic signatures © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 23
Key Pair Article 3. d – Signature Creation Data (Law no. 5070) Unique data such as password and cryptographic keys belonging to signature owners and being used by signature owner in order to create electronic signatures Article 3. f – Signature Verification Data (Law no. 5070) Data such as passwords and cryptographic public keys used for the verification of electronic signatures © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 23
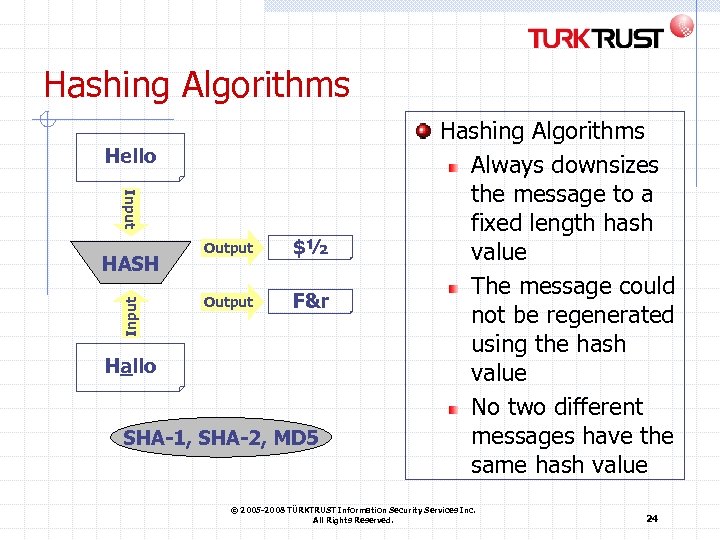 Hashing Algorithms Hello Input HASH Output $½ Output F&r Hallo SHA-1, SHA-2, MD 5 Hashing Algorithms Always downsizes the message to a fixed length hash value The message could not be regenerated using the hash value No two different messages have the same hash value © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 24
Hashing Algorithms Hello Input HASH Output $½ Output F&r Hallo SHA-1, SHA-2, MD 5 Hashing Algorithms Always downsizes the message to a fixed length hash value The message could not be regenerated using the hash value No two different messages have the same hash value © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 24
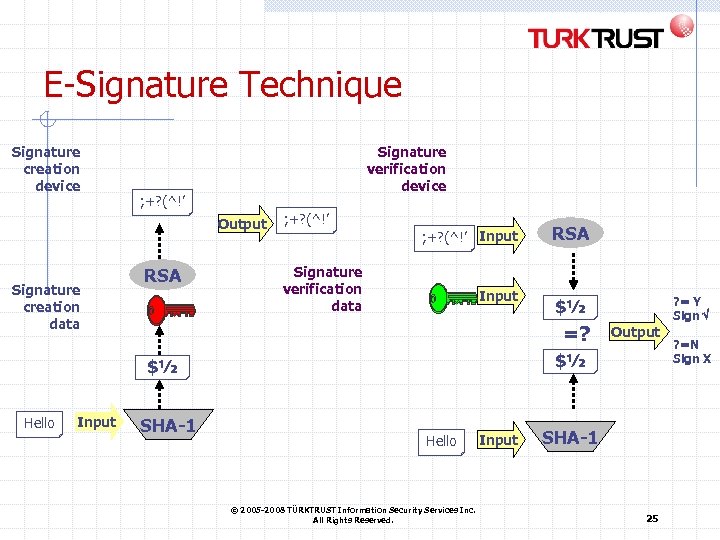 E-Signature Technique Signature creation device Signature verification device ; +? (^!’ Output Signature creation data RSA ; +? (^!’ Input Signature verification data Input SHA-1 ? = Y Sign $½ =? Output $½ $½ Hello RSA Hello © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. Input SHA-1 25 ? =N Sign X
E-Signature Technique Signature creation device Signature verification device ; +? (^!’ Output Signature creation data RSA ; +? (^!’ Input Signature verification data Input SHA-1 ? = Y Sign $½ =? Output $½ $½ Hello RSA Hello © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. Input SHA-1 25 ? =N Sign X
 Secure Electronic Signature Creation Devices Article 6 (Law no. 5070) a) Electronic signature creation data produced by those devices are unique b) Electronic signature creation data recorded in those devices cannot be derived in any means and their secrecy is assured c) Electronic signature creation data recorded in those devices can not be obtained or used by third parties and electronic signatures are protected against forgery d) The data to be signed can not be altered by anyone except the signature owner and can be seen by the signature owner before the generation of signature © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 26
Secure Electronic Signature Creation Devices Article 6 (Law no. 5070) a) Electronic signature creation data produced by those devices are unique b) Electronic signature creation data recorded in those devices cannot be derived in any means and their secrecy is assured c) Electronic signature creation data recorded in those devices can not be obtained or used by third parties and electronic signatures are protected against forgery d) The data to be signed can not be altered by anyone except the signature owner and can be seen by the signature owner before the generation of signature © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 26
 Secure Electronic Signature Creation Devices According to technical and legal requirements, secure electronic signature creation devices are selected as smart cards and tokens that possess specific security standards (EAL 4+). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 27
Secure Electronic Signature Creation Devices According to technical and legal requirements, secure electronic signature creation devices are selected as smart cards and tokens that possess specific security standards (EAL 4+). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 27
 Administrative Security Which key pair belongs to whom Key pair generation True identification Declaration of someone’s possession of the public key (signature verification data) by a trusted third party Electronic certificate Electronic Certificate Service Provider – ECSP (Certification Authority – CA) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 28
Administrative Security Which key pair belongs to whom Key pair generation True identification Declaration of someone’s possession of the public key (signature verification data) by a trusted third party Electronic certificate Electronic Certificate Service Provider – ECSP (Certification Authority – CA) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 28
 Repository of an ECSP End user certificates issued by the ECSP Certificate Revocation Lists (CRL) Root certificates of the ECSP Certificate Policy (CP) Certification Practice Statement (CPS) Time Stamping Policies Time Stamping Practice Statement Agreements (subscriber, relying party, etc. ) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 29
Repository of an ECSP End user certificates issued by the ECSP Certificate Revocation Lists (CRL) Root certificates of the ECSP Certificate Policy (CP) Certification Practice Statement (CPS) Time Stamping Policies Time Stamping Practice Statement Agreements (subscriber, relying party, etc. ) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 29
 PKI Components PKI components are the elements that comprise a public key infrastructure, including entities (such as CAs and RAs) and individuals (such as subscribers and relying parties) participating within the system, technologies (such as algorithms and key generation software), processes (such as key management procedures and directives), records (such as digital certificates, operational logs), and policy instruments (such as CPs, CPSs and agreements). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 30
PKI Components PKI components are the elements that comprise a public key infrastructure, including entities (such as CAs and RAs) and individuals (such as subscribers and relying parties) participating within the system, technologies (such as algorithms and key generation software), processes (such as key management procedures and directives), records (such as digital certificates, operational logs), and policy instruments (such as CPs, CPSs and agreements). © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 30
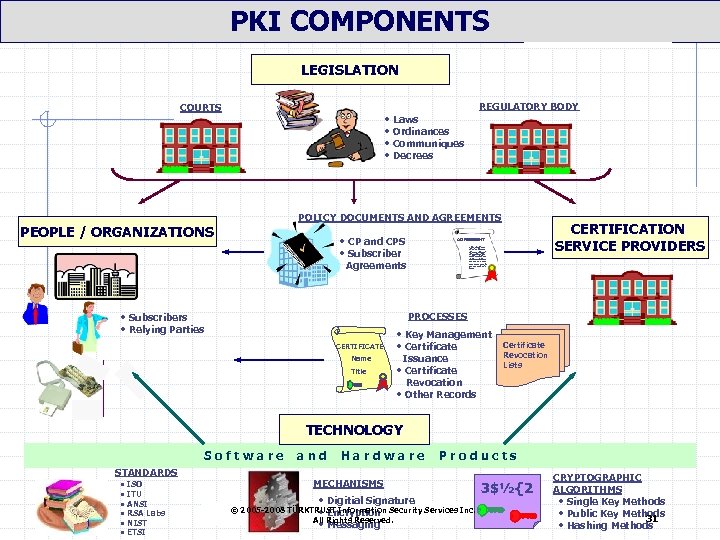 PKI COMPONENTS LEGISLATION REGULATORY BODY COURTS • Laws • Ordinances • Communiques • Decrees POLICY DOCUMENTS AND AGREEMENTS PEOPLE / ORGANIZATIONS • CP and CPS • Subscriber Agreements CERTIFICATION SERVICE PROVIDERS AGREEMENT ASDLFKJSDLK FSDFKJSDLKJ FSLDKJFSDKF JSLDFSDLFSK DFHSKDFHSDK FHSKDJFHSDK IUTYITYTIYIYIYTIYITYITYR ITYIUTYIETYEI RTYT PROCESSES • Subscribers • Relying Parties CERTIFICATE Name Title • Key Management • Certificate Issuance • Certificate Revocation • Other Records Certificate Revocation Lists TECHNOLOGY Software STANDARDS • ISO • ITU • ANSI • RSA Labs • NIST • ETSI and Hardware Products MECHANISMS • Digitial Signature © 2005 -2008 TÜRKTRUST Information Security Services Inc. • Encryption All Rights Reserved. • Messaging 3$½{2 CRYPTOGRAPHIC ALGORITHMS • Single Key Methods • Public Key Methods 31 • Hashing Methods
PKI COMPONENTS LEGISLATION REGULATORY BODY COURTS • Laws • Ordinances • Communiques • Decrees POLICY DOCUMENTS AND AGREEMENTS PEOPLE / ORGANIZATIONS • CP and CPS • Subscriber Agreements CERTIFICATION SERVICE PROVIDERS AGREEMENT ASDLFKJSDLK FSDFKJSDLKJ FSLDKJFSDKF JSLDFSDLFSK DFHSKDFHSDK FHSKDJFHSDK IUTYITYTIYIYIYTIYITYITYR ITYIUTYIETYEI RTYT PROCESSES • Subscribers • Relying Parties CERTIFICATE Name Title • Key Management • Certificate Issuance • Certificate Revocation • Other Records Certificate Revocation Lists TECHNOLOGY Software STANDARDS • ISO • ITU • ANSI • RSA Labs • NIST • ETSI and Hardware Products MECHANISMS • Digitial Signature © 2005 -2008 TÜRKTRUST Information Security Services Inc. • Encryption All Rights Reserved. • Messaging 3$½{2 CRYPTOGRAPHIC ALGORITHMS • Single Key Methods • Public Key Methods 31 • Hashing Methods
 PKI Business Models Organizational (Closed) PKI Models The ECSP itself is the relying party The relying party can outsource the PKI services to third parties for issuing certificates for the subscribers on its behalf Provides offering PKI services and certificates to the personnel, clients, suppliers, etc. of organizations. The PKI service provider forms a legal bond via a contract with the users and the relying parties of the system. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 32
PKI Business Models Organizational (Closed) PKI Models The ECSP itself is the relying party The relying party can outsource the PKI services to third parties for issuing certificates for the subscribers on its behalf Provides offering PKI services and certificates to the personnel, clients, suppliers, etc. of organizations. The PKI service provider forms a legal bond via a contract with the users and the relying parties of the system. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 32
 PKI Business Models Public (Open) PKI Models More than one ECSP Open to public usage for general purposes ECSPs stand as a trusted third party against the subscribers (certificate users) and relying parties Legislation guarantees the service quality of the ECSPs and protects the subscribers and relying parties © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 33
PKI Business Models Public (Open) PKI Models More than one ECSP Open to public usage for general purposes ECSPs stand as a trusted third party against the subscribers (certificate users) and relying parties Legislation guarantees the service quality of the ECSPs and protects the subscribers and relying parties © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 33
 Trust Models and PKI Architectures Hierarchy A central Certification Authority recognises each CA Relying parties just trust the central CA Mesh CAs directly recognise each other Each relying party just trusts its own CA that in turn trusts the remote CA Web / trust model A repository of trusted Certification Authorities Each relying party trusts all distributed certificates of the list Bridge infrastructure A central technical infrastructure cross-recognises each concerned CA Each relying party just trusts its own CA that trusts the bridge that in turn trusts the remote CA © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 34
Trust Models and PKI Architectures Hierarchy A central Certification Authority recognises each CA Relying parties just trust the central CA Mesh CAs directly recognise each other Each relying party just trusts its own CA that in turn trusts the remote CA Web / trust model A repository of trusted Certification Authorities Each relying party trusts all distributed certificates of the list Bridge infrastructure A central technical infrastructure cross-recognises each concerned CA Each relying party just trusts its own CA that trusts the bridge that in turn trusts the remote CA © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 34
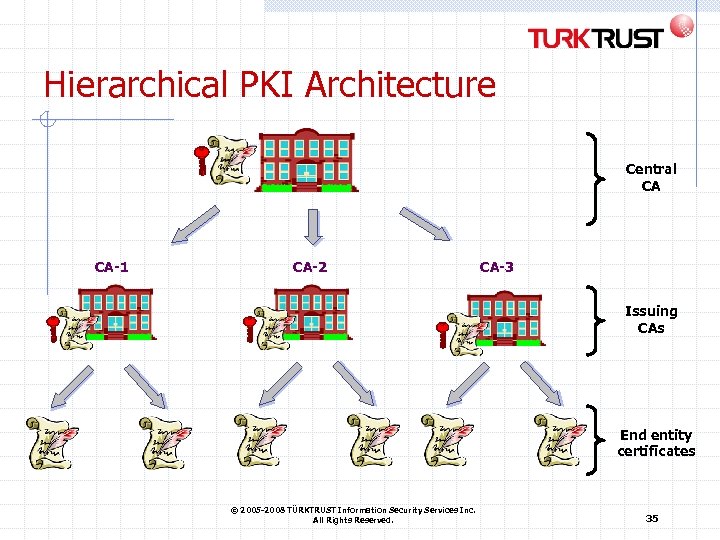 Hierarchical PKI Architecture Central CA CA-1 CA-2 CA-3 Issuing CAs End entity certificates © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 35
Hierarchical PKI Architecture Central CA CA-1 CA-2 CA-3 Issuing CAs End entity certificates © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 35
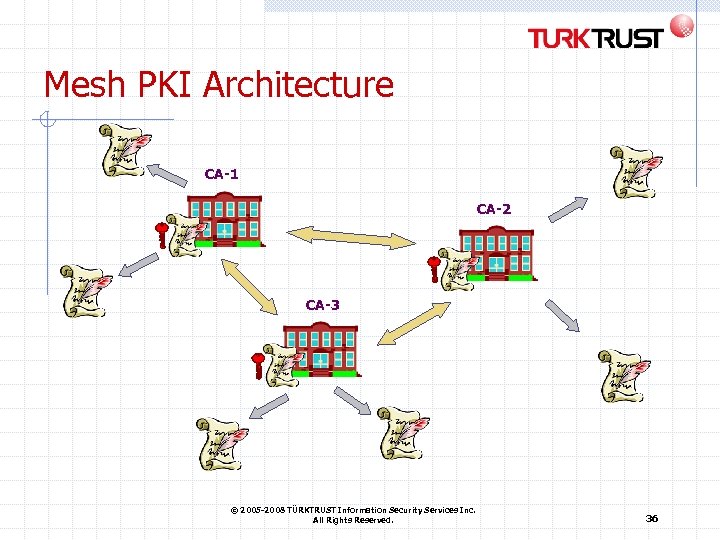 Mesh PKI Architecture CA-1 CA-2 CA-3 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 36
Mesh PKI Architecture CA-1 CA-2 CA-3 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 36
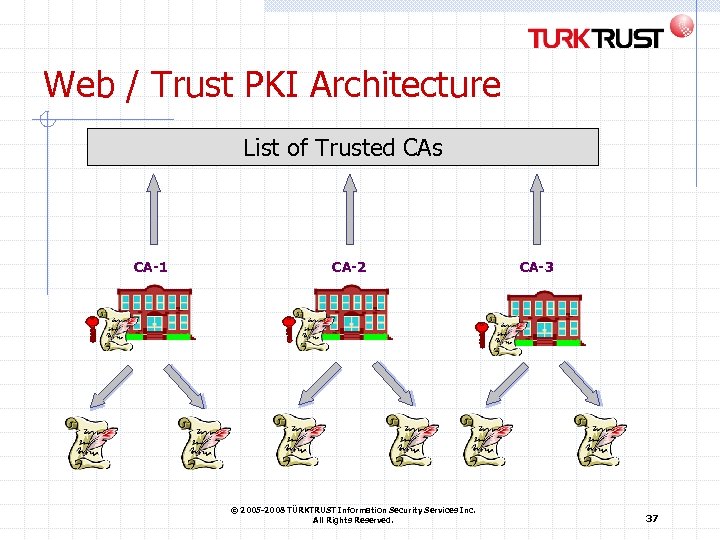 Web / Trust PKI Architecture List of Trusted CAs CA-1 CA-2 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. CA-3 37
Web / Trust PKI Architecture List of Trusted CAs CA-1 CA-2 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. CA-3 37
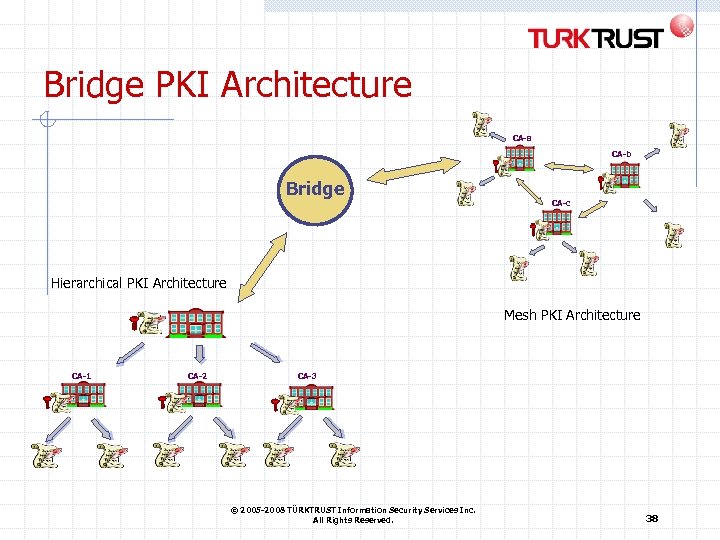 Bridge PKI Architecture CA-a CA-b Bridge CA-c Hierarchical PKI Architecture Mesh PKI Architecture CA-1 CA-2 CA-3 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 38
Bridge PKI Architecture CA-a CA-b Bridge CA-c Hierarchical PKI Architecture Mesh PKI Architecture CA-1 CA-2 CA-3 © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 38
 Certificate Life Cycle Certificate application and registration Certificate issuance, delivery and dissemination Certificate renewal and rekey Certificate revocation and suspension Certificate status services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 39
Certificate Life Cycle Certificate application and registration Certificate issuance, delivery and dissemination Certificate renewal and rekey Certificate revocation and suspension Certificate status services © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 39
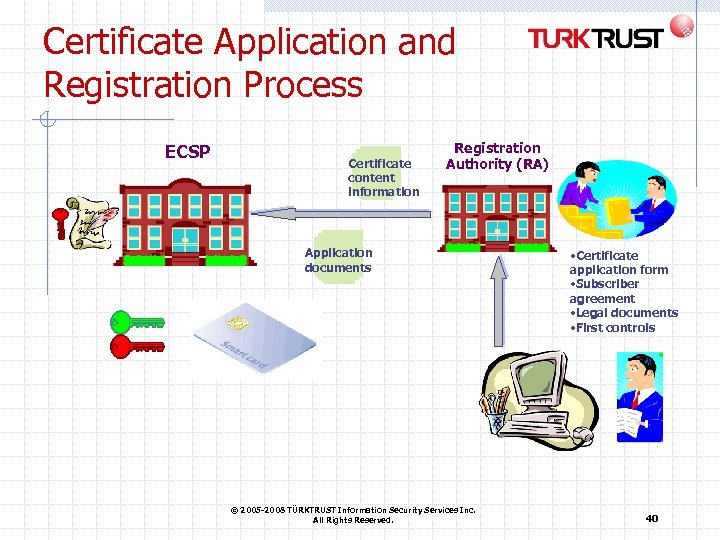 Certificate Application and Registration Process ECSP Certificate content information Registration Authority (RA) Application documents © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. • Certificate application form • Subscriber agreement • Legal documents • First controls 40
Certificate Application and Registration Process ECSP Certificate content information Registration Authority (RA) Application documents © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. • Certificate application form • Subscriber agreement • Legal documents • First controls 40
 Critical Issues about Application and Registration People who wish to obtain qualified electronic certificates or other personal certificates can apply personally Companies that wish to obtain certificates on behalf of their employees can file applications provided that personal application documents exist Server administrators or authorized representatives may apply for server certificates Personal or organizational identity validation should be done appropriately by the ECSP Application documents should be collected by the ECSP and the applicant should be registered accordingly © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 41
Critical Issues about Application and Registration People who wish to obtain qualified electronic certificates or other personal certificates can apply personally Companies that wish to obtain certificates on behalf of their employees can file applications provided that personal application documents exist Server administrators or authorized representatives may apply for server certificates Personal or organizational identity validation should be done appropriately by the ECSP Application documents should be collected by the ECSP and the applicant should be registered accordingly © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 41
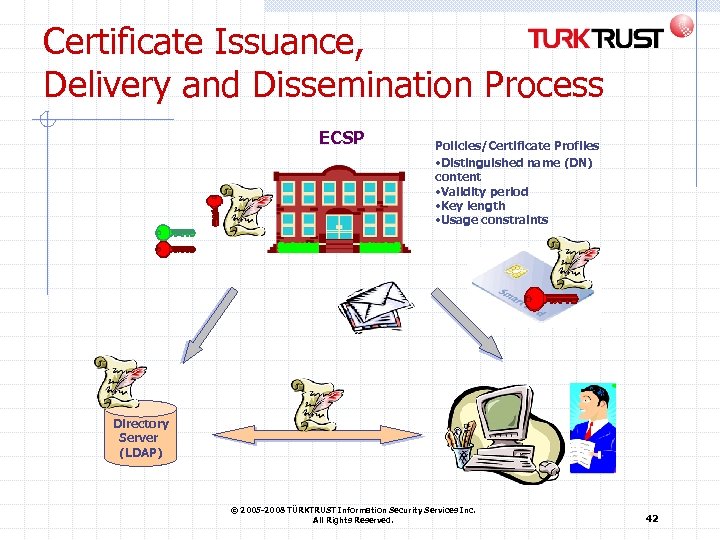 Certificate Issuance, Delivery and Dissemination Process ECSP Policies/Certificate Profiles • Distinguished name (DN) content • Validity period • Key length • Usage constraints Directory Server (LDAP) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 42
Certificate Issuance, Delivery and Dissemination Process ECSP Policies/Certificate Profiles • Distinguished name (DN) content • Validity period • Key length • Usage constraints Directory Server (LDAP) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 42
 Critical Issues about Generation and Dissemination Certificate generation is done under appropriate security procedures Suitable certificate profiles are used according to the applicant’s certificate request Smart cards or tokens that contain the generated certificates and the signature creation data are prepared for delivery under strict security conditions Smart cards, tokens and the access codes are sent to the subscriber separately and delivered by identity validation Certificates are published for public access if the subscriber has given written consent © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 43
Critical Issues about Generation and Dissemination Certificate generation is done under appropriate security procedures Suitable certificate profiles are used according to the applicant’s certificate request Smart cards or tokens that contain the generated certificates and the signature creation data are prepared for delivery under strict security conditions Smart cards, tokens and the access codes are sent to the subscriber separately and delivered by identity validation Certificates are published for public access if the subscriber has given written consent © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 43
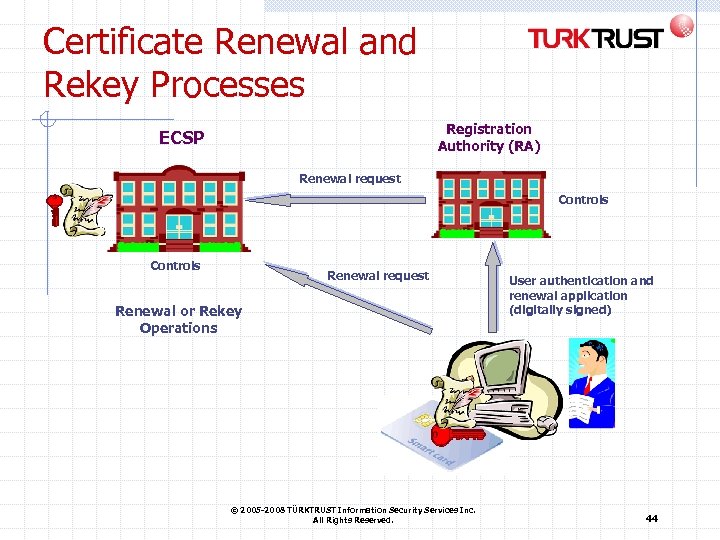 Certificate Renewal and Rekey Processes Registration Authority (RA) ECSP Renewal request Controls Renewal request Renewal or Rekey Operations © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. User authentication and renewal application (digitally signed) 44
Certificate Renewal and Rekey Processes Registration Authority (RA) ECSP Renewal request Controls Renewal request Renewal or Rekey Operations © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. User authentication and renewal application (digitally signed) 44
 Critical Issues about Renewal and Rekey Certificates can be renewed before the end of their expiry date Certificates are not renewed beyond 3 (three) years with the same key pair Proper identity checks are done during renewal and rekey If certificate content changes, the certificate can not be renewed but it can only be rekeyed with new personal information © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 45
Critical Issues about Renewal and Rekey Certificates can be renewed before the end of their expiry date Certificates are not renewed beyond 3 (three) years with the same key pair Proper identity checks are done during renewal and rekey If certificate content changes, the certificate can not be renewed but it can only be rekeyed with new personal information © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 45
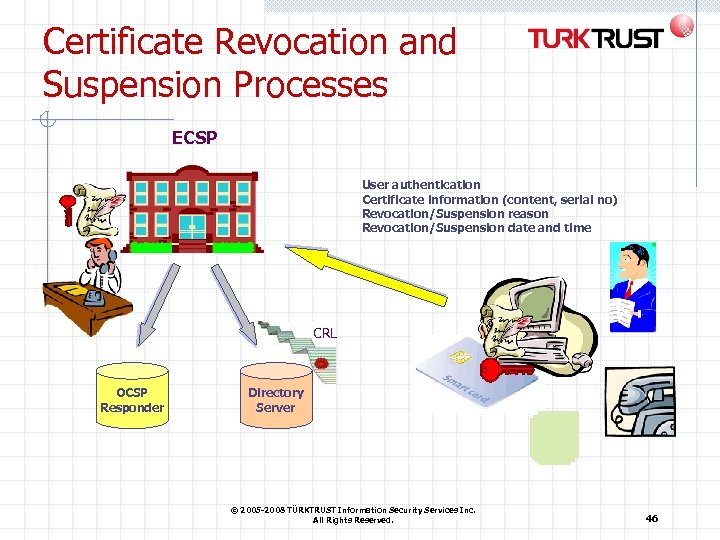 Certificate Revocation and Suspension Processes ECSP User authentication Certificate information (content, serial no) Revocation/Suspension reason Revocation/Suspension date and time CRL OCSP Responder Directory Server © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 46
Certificate Revocation and Suspension Processes ECSP User authentication Certificate information (content, serial no) Revocation/Suspension reason Revocation/Suspension date and time CRL OCSP Responder Directory Server © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 46
 Critical Issues about Suspension and Revocation Circumstances for revocation: Upon request by the subscriber Information within the certificate is false or incorrect, A change occurs in the information regarding the subject included in a certificate’s content It is learned that the subject’s legal capacity is restricted, or the subject is bankrupt or lost in danger of death, or died, The private key has been lost, stolen, disclosed or a risk of access or use by a third party arises, The secure electronic signature creation device in which the private key is located has been lost, broken down or compromised, It is understood that the certificate has been used in contradiction to the provisions of the CP and CPS documents and the Subscriber’s Agreement, ECSP suspends provision of certification services. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 47
Critical Issues about Suspension and Revocation Circumstances for revocation: Upon request by the subscriber Information within the certificate is false or incorrect, A change occurs in the information regarding the subject included in a certificate’s content It is learned that the subject’s legal capacity is restricted, or the subject is bankrupt or lost in danger of death, or died, The private key has been lost, stolen, disclosed or a risk of access or use by a third party arises, The secure electronic signature creation device in which the private key is located has been lost, broken down or compromised, It is understood that the certificate has been used in contradiction to the provisions of the CP and CPS documents and the Subscriber’s Agreement, ECSP suspends provision of certification services. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 47
 Critical Issues about Suspension and Revocation Circumstances for suspension: Where the source of a certificate revocation request could not be verified, ECSP shall suspend, rather than revoke, the certificate in question until the verification is finalized, or upon a request where the end user is unsure whether any circumstance that requires revocation does exist. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 48
Critical Issues about Suspension and Revocation Circumstances for suspension: Where the source of a certificate revocation request could not be verified, ECSP shall suspend, rather than revoke, the certificate in question until the verification is finalized, or upon a request where the end user is unsure whether any circumstance that requires revocation does exist. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 48
 Critical Issues about Suspension and Revocation Who can request revocation or suspension? The subject himself, for personal certificates, The server administrator, for server certificates, An authorized person of a company or an institution to which the subject or server is associated, for certificates in organizational use, ECSP’s authorized personnel for end user certificates and root and subroot certificates where security concerns with respect to the ECSP necessitate. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 49
Critical Issues about Suspension and Revocation Who can request revocation or suspension? The subject himself, for personal certificates, The server administrator, for server certificates, An authorized person of a company or an institution to which the subject or server is associated, for certificates in organizational use, ECSP’s authorized personnel for end user certificates and root and subroot certificates where security concerns with respect to the ECSP necessitate. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 49
 Critical Issues about Suspension and Revocation The certificate owner (subscriber): during the course of certificate registration process or until the end of the certificate life time, shall notify the ECSP as soon as possible to ensure that the certificate is revoked for the changes of any kind in his/her personal information that is contained in the certificate itself in cases where there is a risk of usage by other person or persons of the signature creation device or the data required for accessing the device or even the conditions which may bring about such a risk emerge, shall immediately notify the ECSP in order the certificate to be revoked (from the “TURKTRUST Letter Of Commitment by the Qualified Certificate Owner – Subscriber Agreement”) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 50
Critical Issues about Suspension and Revocation The certificate owner (subscriber): during the course of certificate registration process or until the end of the certificate life time, shall notify the ECSP as soon as possible to ensure that the certificate is revoked for the changes of any kind in his/her personal information that is contained in the certificate itself in cases where there is a risk of usage by other person or persons of the signature creation device or the data required for accessing the device or even the conditions which may bring about such a risk emerge, shall immediately notify the ECSP in order the certificate to be revoked (from the “TURKTRUST Letter Of Commitment by the Qualified Certificate Owner – Subscriber Agreement”) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 50
 Critical Issues about Suspension and Revocation The ECSP should immediately resolve all certificate revocation requests transmitted over the web, by telephone or on paper, following the approval of the request and authentication of the request. Relying parties are under obligation to verify the related certificate to rely on an electronic signature transmitted. To verify a certificate’s status, updated CRLs published by the ECSP or the on-line certificate status inquiry service OCSP should be used. It is recommended that relying parties should use secure signature verification devices when verifying electronic signatures The duration of suspension may not exceed a certain period. Those still in suspension at the end of this period shall be automatically revoked for security reasons © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 51
Critical Issues about Suspension and Revocation The ECSP should immediately resolve all certificate revocation requests transmitted over the web, by telephone or on paper, following the approval of the request and authentication of the request. Relying parties are under obligation to verify the related certificate to rely on an electronic signature transmitted. To verify a certificate’s status, updated CRLs published by the ECSP or the on-line certificate status inquiry service OCSP should be used. It is recommended that relying parties should use secure signature verification devices when verifying electronic signatures The duration of suspension may not exceed a certain period. Those still in suspension at the end of this period shall be automatically revoked for security reasons © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 51
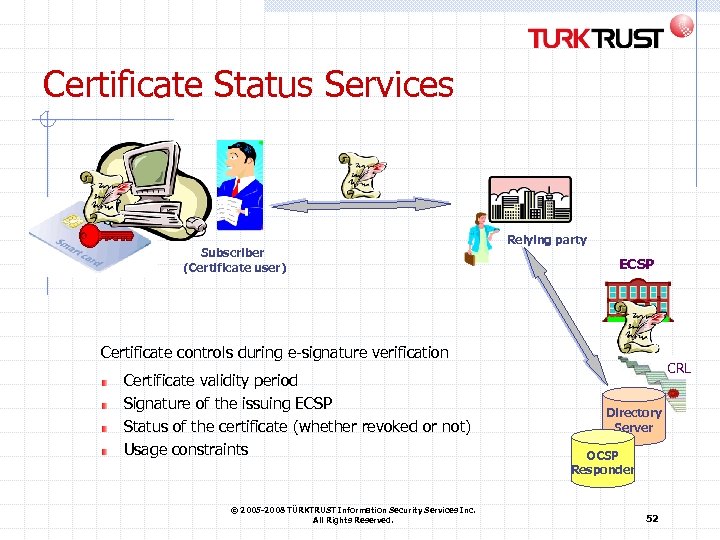 Certificate Status Services Subscriber (Certificate user) Relying party ECSP Certificate controls during e-signature verification Certificate validity period Signature of the issuing ECSP Status of the certificate (whether revoked or not) Usage constraints © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. CRL Directory Server OCSP Responder 52
Certificate Status Services Subscriber (Certificate user) Relying party ECSP Certificate controls during e-signature verification Certificate validity period Signature of the issuing ECSP Status of the certificate (whether revoked or not) Usage constraints © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. CRL Directory Server OCSP Responder 52
 Critical Issues about Certificate Status Services ECSPs should issue a new CRL periodically even if there is no change in the status of current certificates. Generally, the CRLs are published daily. ECSPs have to provide uninterrupted on-line certificate status protocol OCSP support. By the real time certificate status inquiry that is more reliable than CRLs, customers may inquire the status of certificates online and get immediate status response by using appropriate software on the customer side. It is recommended that relying parties when inquiring the status of certificates should prefer OCSP if their technical capabilities allow and opt for CRL as a second alternative. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 53
Critical Issues about Certificate Status Services ECSPs should issue a new CRL periodically even if there is no change in the status of current certificates. Generally, the CRLs are published daily. ECSPs have to provide uninterrupted on-line certificate status protocol OCSP support. By the real time certificate status inquiry that is more reliable than CRLs, customers may inquire the status of certificates online and get immediate status response by using appropriate software on the customer side. It is recommended that relying parties when inquiring the status of certificates should prefer OCSP if their technical capabilities allow and opt for CRL as a second alternative. © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 53
 Directory Services A directory service is a software application that makes resources on a network accessible to users and other applications Almost all directory services are based on the X. 500 ITU standard Usually more than one namespace (trees of objects) are used to form the directory service A directory service is highly optimized for reads and provides advanced search possibilities on many different attributes that can be associated with objects in a directory © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 54
Directory Services A directory service is a software application that makes resources on a network accessible to users and other applications Almost all directory services are based on the X. 500 ITU standard Usually more than one namespace (trees of objects) are used to form the directory service A directory service is highly optimized for reads and provides advanced search possibilities on many different attributes that can be associated with objects in a directory © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 54
 Directory Service Application Protocol Common directory services used by ECSPs enabling effective certificate search utilize Lightweight Directory Access Protocol (LDAP) Based on X. 500 standard Supports TCP/IP An open protocol IETF RFC 4510 specifies LDAPv 3 The Lightweight Directory Access Protocol (LDAP) is an Internet protocol for accessing distributed directory services that act in accordance with X. 500 data and service models © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 55
Directory Service Application Protocol Common directory services used by ECSPs enabling effective certificate search utilize Lightweight Directory Access Protocol (LDAP) Based on X. 500 standard Supports TCP/IP An open protocol IETF RFC 4510 specifies LDAPv 3 The Lightweight Directory Access Protocol (LDAP) is an Internet protocol for accessing distributed directory services that act in accordance with X. 500 data and service models © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 55
 Bibliography CWA 14167 -1 – Security Requirements for Trustworthy Systems Managing Certificates for Electronic Signatures - Part 1: System Security Requirements (June 2003) CWA 14169 – Secure Signature-Creation Devices "EAL 4+“ (March 2002) Digitial Signature Law Survey (https: //dsls. rechten. uvt. nl) ETSI TS 101 456 – Policy requirements for certification authorities issuing qualified certificates (April 2002) ETSI TS 101 733 – Electronic Signatures and Infrastructures (ESI); Electronic Signature Formats (December 2003) ETSI TS 101 862 – Qualified Certificate Profile (January 2006) EU Directive 1999/93/EC on a Community framework for electronic signatures (December 1999) FIPS PUB 140 -2 – Security Requirements for Cryptographic Modules (March 2002) (Supercedes FIPS PUB 140 -1, January 1994) IETF RFC 2634 – Enhanced Security Services for S/MIME (June 1999) IETF RFC 3161 – Internet X. 509 Public Key Infrastructure Time-Stamp Protocol (TSP) (August 2001) IETF RFC 3280 – Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile (April 2002) IETF RFC 3369 – Cryptographic Message Syntax (CMS) (August 2002) IETF RFC 3647 – Internet X. 509 Public Key Infrastructure Certificate Policy and Certification Practices Framework (November 2003) IETF RFC 3739 – Internet X. 509 Public Key Infrastructure Qualified Certificates Profile (March 2004) IETF RFC 4510 – Lightweight Directory Access Protocol (LDAP): Technical Specification Road Map (June 2006) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 56
Bibliography CWA 14167 -1 – Security Requirements for Trustworthy Systems Managing Certificates for Electronic Signatures - Part 1: System Security Requirements (June 2003) CWA 14169 – Secure Signature-Creation Devices "EAL 4+“ (March 2002) Digitial Signature Law Survey (https: //dsls. rechten. uvt. nl) ETSI TS 101 456 – Policy requirements for certification authorities issuing qualified certificates (April 2002) ETSI TS 101 733 – Electronic Signatures and Infrastructures (ESI); Electronic Signature Formats (December 2003) ETSI TS 101 862 – Qualified Certificate Profile (January 2006) EU Directive 1999/93/EC on a Community framework for electronic signatures (December 1999) FIPS PUB 140 -2 – Security Requirements for Cryptographic Modules (March 2002) (Supercedes FIPS PUB 140 -1, January 1994) IETF RFC 2634 – Enhanced Security Services for S/MIME (June 1999) IETF RFC 3161 – Internet X. 509 Public Key Infrastructure Time-Stamp Protocol (TSP) (August 2001) IETF RFC 3280 – Internet X. 509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile (April 2002) IETF RFC 3369 – Cryptographic Message Syntax (CMS) (August 2002) IETF RFC 3647 – Internet X. 509 Public Key Infrastructure Certificate Policy and Certification Practices Framework (November 2003) IETF RFC 3739 – Internet X. 509 Public Key Infrastructure Qualified Certificates Profile (March 2004) IETF RFC 4510 – Lightweight Directory Access Protocol (LDAP): Technical Specification Road Map (June 2006) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 56
 Bibliography ISO 15408 Part 1 – Information technology — Security techniques — Evaluation criteria for IT security — Part 1: Introduction and general model (October 2005) ISO 15408 Part 2 – Information technology — Security techniques — Evaluation criteria for IT security — Part 2: Security functional requirements (October 2005) ISO 15408 Part 3 – Information technology — Security techniques — Evaluation criteria for IT security — Part 3: Security assurance requirements (October 2005) ISO/IEC 27001: 2005 – Information technology – Security techniques – Information security management systems – Requirements (former BS 7799 -2: 2002 – Information security management systems — Specification with guidance for use) ISO/IEC 27002: 2005 – Information technology – Security techniques – Code of practice for information security management (former ISO/IEC 17799: 2005 – Information technology — Security techniques — Code of practice for information security management) ISO/IEC 17025, EN 45001 – General requirements for the competence of testing and calibration laboratories ISO/IEC Guide 62, EN 45012 – General requirements for bodies operating assessment and certification/registration of quality systems ISO/IEC Guide 65, EN 45011 – General requirements for bodies operating product certification systems © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 57
Bibliography ISO 15408 Part 1 – Information technology — Security techniques — Evaluation criteria for IT security — Part 1: Introduction and general model (October 2005) ISO 15408 Part 2 – Information technology — Security techniques — Evaluation criteria for IT security — Part 2: Security functional requirements (October 2005) ISO 15408 Part 3 – Information technology — Security techniques — Evaluation criteria for IT security — Part 3: Security assurance requirements (October 2005) ISO/IEC 27001: 2005 – Information technology – Security techniques – Information security management systems – Requirements (former BS 7799 -2: 2002 – Information security management systems — Specification with guidance for use) ISO/IEC 27002: 2005 – Information technology – Security techniques – Code of practice for information security management (former ISO/IEC 17799: 2005 – Information technology — Security techniques — Code of practice for information security management) ISO/IEC 17025, EN 45001 – General requirements for the competence of testing and calibration laboratories ISO/IEC Guide 62, EN 45012 – General requirements for bodies operating assessment and certification/registration of quality systems ISO/IEC Guide 65, EN 45011 – General requirements for bodies operating product certification systems © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 57
 Bibliography ITU-T Recommendation X. 500 – Information technology - Open Systems Interconnection The Directory: Overview of concepts, models and services ITU-T Recommendation X. 509 – Information technology - Open systems interconnection The directory: Authentication framework European Electronic Signature Standardisation Initiative (EESSI) – Final Report of the EESSI Expert Team (July 1999) PKI Assessement Guidelines – American Bar Association – Guidelines to Help Assess and Facilitate Interoperable Trustworthy Public Key Infrastructures (June 2001) TURKEY - Electronic Signature Law no. 5070 (January 2004) TURKEY - Ordinance on the Procedures and Principles Pertaining to the Implementation of Electronic Signature Law (January 2005) TURKEY - Communiqué on Processes and Technical Criteria Regarding Electronic Signatures (January 2005) TÜRKTRUST Certificate Policies (CP) Version 01 (May 2005) TÜRKTRUST Certification Practice Statement (CPS) Version 01 (May 2005) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 58
Bibliography ITU-T Recommendation X. 500 – Information technology - Open Systems Interconnection The Directory: Overview of concepts, models and services ITU-T Recommendation X. 509 – Information technology - Open systems interconnection The directory: Authentication framework European Electronic Signature Standardisation Initiative (EESSI) – Final Report of the EESSI Expert Team (July 1999) PKI Assessement Guidelines – American Bar Association – Guidelines to Help Assess and Facilitate Interoperable Trustworthy Public Key Infrastructures (June 2001) TURKEY - Electronic Signature Law no. 5070 (January 2004) TURKEY - Ordinance on the Procedures and Principles Pertaining to the Implementation of Electronic Signature Law (January 2005) TURKEY - Communiqué on Processes and Technical Criteria Regarding Electronic Signatures (January 2005) TÜRKTRUST Certificate Policies (CP) Version 01 (May 2005) TÜRKTRUST Certification Practice Statement (CPS) Version 01 (May 2005) © 2005 -2008 TÜRKTRUST Information Security Services Inc. All Rights Reserved. 58
 PKI SYSTEMS Concepts, Processes, Components Mert ÖZARAR Project Senior Engineer mert. ozarar@turktrust. com. tr TÜRKTRUST Information Security Services Inc. 59
PKI SYSTEMS Concepts, Processes, Components Mert ÖZARAR Project Senior Engineer mert. ozarar@turktrust. com. tr TÜRKTRUST Information Security Services Inc. 59


