 PKI Security in Map. Server using Apache FOSS 4 G 2006 EPFL-UNIL • Lausanne • Switzerland Michael Smith Engineer Research & Development Center - Remote Sensing/GIS Center US Army Corps of Engineers, Hanover, NH michael. smith@erdc. usace. army. mil
PKI Security in Map. Server using Apache FOSS 4 G 2006 EPFL-UNIL • Lausanne • Switzerland Michael Smith Engineer Research & Development Center - Remote Sensing/GIS Center US Army Corps of Engineers, Hanover, NH michael. smith@erdc. usace. army. mil
 About the Corps of Engineers ü 34, 600 civilian and 650 military personnel ü USACE provides responsive engineering services to the nation ü Civil Works: ü ü ü Plan, design, build and operate water resources projects Navigation Flood Control Environmental Protection Disaster Response ü Design and manage the construction of military facilities for the Army and Air Force. ü Provide design and construction management support for other Defense and federal agencies.
About the Corps of Engineers ü 34, 600 civilian and 650 military personnel ü USACE provides responsive engineering services to the nation ü Civil Works: ü ü ü Plan, design, build and operate water resources projects Navigation Flood Control Environmental Protection Disaster Response ü Design and manage the construction of military facilities for the Army and Air Force. ü Provide design and construction management support for other Defense and federal agencies.
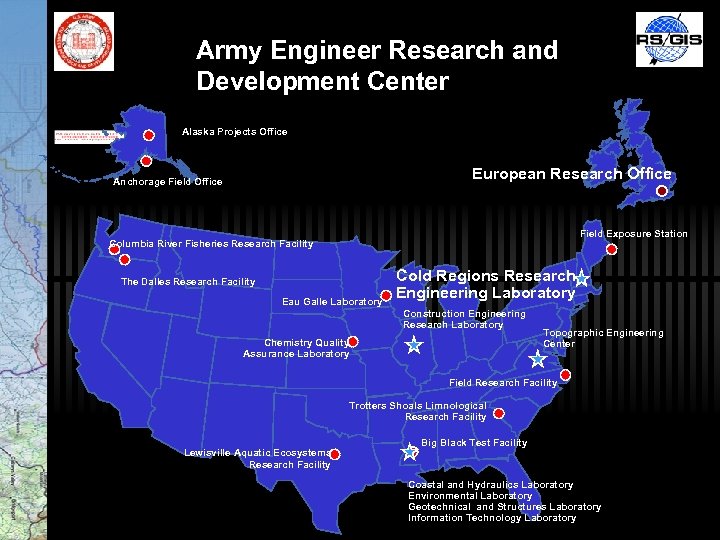 Army Engineer Research and Development Center Alaska Projects Office European Research Office Anchorage Field Office Field Exposure Station Columbia River Fisheries Research Facility The Dalles Research Facility Eau Galle Laboratory Cold Regions Research Engineering Laboratory Construction Engineering Research Laboratory Chemistry Quality Assurance Laboratory Topographic Engineering Center Field Research Facility Trotters Shoals Limnological Research Facility Lewisville Aquatic Ecosystems Research Facility Big Black Test Facility Coastal and Hydraulics Laboratory Environmental Laboratory Geotechnical and Structures Laboratory Information Technology Laboratory
Army Engineer Research and Development Center Alaska Projects Office European Research Office Anchorage Field Office Field Exposure Station Columbia River Fisheries Research Facility The Dalles Research Facility Eau Galle Laboratory Cold Regions Research Engineering Laboratory Construction Engineering Research Laboratory Chemistry Quality Assurance Laboratory Topographic Engineering Center Field Research Facility Trotters Shoals Limnological Research Facility Lewisville Aquatic Ecosystems Research Facility Big Black Test Facility Coastal and Hydraulics Laboratory Environmental Laboratory Geotechnical and Structures Laboratory Information Technology Laboratory
 RS/GIS Center Staff Skills & Background (32 Personnel) GIS enterprise applications Geospatial database organization and development GIS business practice applications development Image processing Sensor evaluation Spatial analysis Algorithm development/programming Emergency management Education and training Statistical analysis Watershed management Hydraulic engineering Geomorphology Forestry Computer programming Image processing Geography Database management Signal processing Electrical engineering Ecology Economics Hydrology Meteorology Statistics Water resources engineering
RS/GIS Center Staff Skills & Background (32 Personnel) GIS enterprise applications Geospatial database organization and development GIS business practice applications development Image processing Sensor evaluation Spatial analysis Algorithm development/programming Emergency management Education and training Statistical analysis Watershed management Hydraulic engineering Geomorphology Forestry Computer programming Image processing Geography Database management Signal processing Electrical engineering Ecology Economics Hydrology Meteorology Statistics Water resources engineering
 Business Requirements & Constraints ü Account/password management for thousands of users ü Support for PKI Infrastructure (Do. D Common Access Card) ü Strictly Defined Roles and Access ü Formal Release/Version Control & Reporting Mechanism ü 24 x 7 Systems with Fail-Over/Disaster Recovery ü Replication to Secure Networks ü Support Data Calls & Data Snapshots ü Formal Software Development Process ü Distributed Development Teams
Business Requirements & Constraints ü Account/password management for thousands of users ü Support for PKI Infrastructure (Do. D Common Access Card) ü Strictly Defined Roles and Access ü Formal Release/Version Control & Reporting Mechanism ü 24 x 7 Systems with Fail-Over/Disaster Recovery ü Replication to Secure Networks ü Support Data Calls & Data Snapshots ü Formal Software Development Process ü Distributed Development Teams
 What is PKI - Public Key Infrastructure ü PKI is a framework that enables secure transactions to be performed on otherwise non-secure platforms (i. e. , the Internet, etc. ). ü PKI provides security through the use of a private and public cryptographic key pair. ü The private key is unique to the individual. This private key is issued by a trusted third party known as the certificate authority (CA). ü The public key is freely distributed to other users to be matched with the private key to authenticate the transaction.
What is PKI - Public Key Infrastructure ü PKI is a framework that enables secure transactions to be performed on otherwise non-secure platforms (i. e. , the Internet, etc. ). ü PKI provides security through the use of a private and public cryptographic key pair. ü The private key is unique to the individual. This private key is issued by a trusted third party known as the certificate authority (CA). ü The public key is freely distributed to other users to be matched with the private key to authenticate the transaction.
 More on PKI ü Two factor authentication ü Something you know ü Something you have ü Passphrase not sent over net, just decrypts private key ü Since private key sent over net, only use string encryption https (TLS, 128 -bit ciphers etc)
More on PKI ü Two factor authentication ü Something you know ü Something you have ü Passphrase not sent over net, just decrypts private key ü Since private key sent over net, only use string encryption https (TLS, 128 -bit ciphers etc)
 PKI in the Do. D = CAC (Common Access Cards) ü The CAC will serve as the user's PKI token, which means that the ICC located on the CAC will be used to store the user's private key identity ü These certificates are used to access PKI on card key generation services and applications
PKI in the Do. D = CAC (Common Access Cards) ü The CAC will serve as the user's PKI token, which means that the ICC located on the CAC will be used to store the user's private key identity ü These certificates are used to access PKI on card key generation services and applications
 Basic Operation ü SSL used as the security/transport mechanism ü Server’s identity is verified browser root certificate ü User is authenticated by presenting a client certificate to the server ü Server verifies client by using a Certificate Authority (CA) root certificate
Basic Operation ü SSL used as the security/transport mechanism ü Server’s identity is verified browser root certificate ü User is authenticated by presenting a client certificate to the server ü Server verifies client by using a Certificate Authority (CA) root certificate
 Part of Normal Apache Setup ü Can be placed in a
Part of Normal Apache Setup ü Can be placed in a
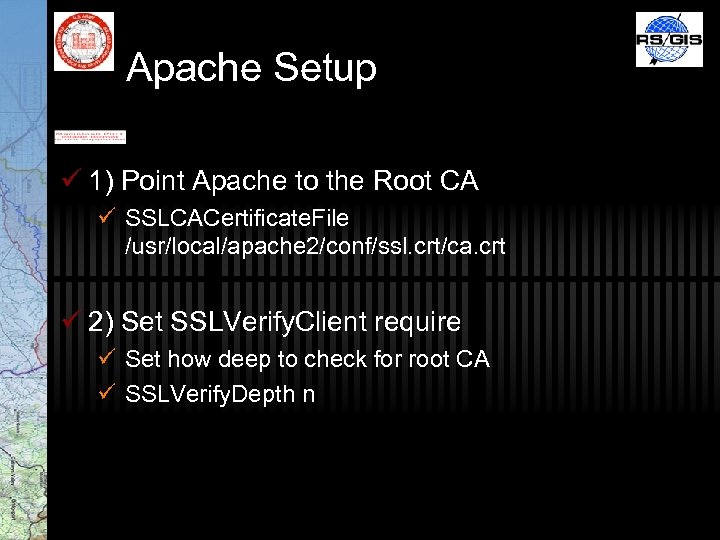 Apache Setup ü 1) Point Apache to the Root CA ü SSLCACertificate. File /usr/local/apache 2/conf/ssl. crt/ca. crt ü 2) Set SSLVerify. Client require ü Set how deep to check for root CA ü SSLVerify. Depth n
Apache Setup ü 1) Point Apache to the Root CA ü SSLCACertificate. File /usr/local/apache 2/conf/ssl. crt/ca. crt ü 2) Set SSLVerify. Client require ü Set how deep to check for root CA ü SSLVerify. Depth n
 SSL Environment Variables ü SSL_CLIENT_S_DN_CN ü The client supplied Common Name ü SMITH. MICHAEL. D. 1140324104 ü SSL_CLIENT_S_DN_OU ü The client supplied Organizational Unit ü Do. D ü SSL_CLIENT_S_V_END ü When the certificate expires ü Jul 19 23: 59 2009 GMT
SSL Environment Variables ü SSL_CLIENT_S_DN_CN ü The client supplied Common Name ü SMITH. MICHAEL. D. 1140324104 ü SSL_CLIENT_S_DN_OU ü The client supplied Organizational Unit ü Do. D ü SSL_CLIENT_S_V_END ü When the certificate expires ü Jul 19 23: 59 2009 GMT
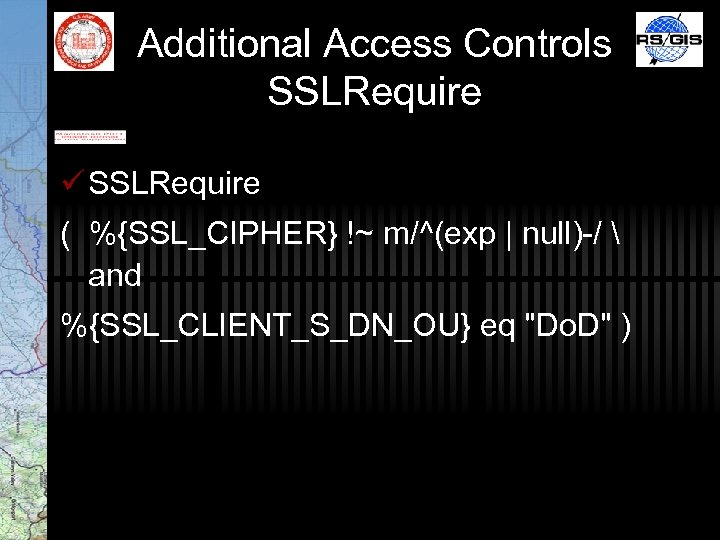 Additional Access Controls SSLRequire ü SSLRequire ( %{SSL_CIPHER} !~ m/^(exp | null)-/ and %{SSL_CLIENT_S_DN_OU} eq "Do. D" )
Additional Access Controls SSLRequire ü SSLRequire ( %{SSL_CIPHER} !~ m/^(exp | null)-/ and %{SSL_CLIENT_S_DN_OU} eq "Do. D" )
 Additional Access Controls Fake. Basic. Auth ü Passes SSL_CLIENT_S_DN_CN as basic authorization user name, sets password to “xxj 31 ZMTZzk. VA” encrypted version of password ü Use standard. htaccess files to limit to certain subsets of users
Additional Access Controls Fake. Basic. Auth ü Passes SSL_CLIENT_S_DN_CN as basic authorization user name, sets password to “xxj 31 ZMTZzk. VA” encrypted version of password ü Use standard. htaccess files to limit to certain subsets of users
 If using Reverse. Proxy ü Make sure you add the SSL Environment variables explicitly to the headers ü Request. Header set SSL_CLIENT_S_DN_CN %{SSL_CLIENT_S_DN_CN}e ü Request. Header set SSL_CLIENT_S_DN_OU %{SSL_CLIENT_S_DN_OU}e ü Request. Header set SSL_CLIENT_V_END %{SSL_CLIENT_V_END}e
If using Reverse. Proxy ü Make sure you add the SSL Environment variables explicitly to the headers ü Request. Header set SSL_CLIENT_S_DN_CN %{SSL_CLIENT_S_DN_CN}e ü Request. Header set SSL_CLIENT_S_DN_OU %{SSL_CLIENT_S_DN_OU}e ü Request. Header set SSL_CLIENT_V_END %{SSL_CLIENT_V_END}e
 Mapserver Integration ü Done at Environment or Cookie level for CGI or use Mapscript ü Only certain Map. Server parameters accept variable substitution ü Available for ü ü DATA TILEINDEX CONNECTION FILTER ü Remember to set DATAPATTERN properly
Mapserver Integration ü Done at Environment or Cookie level for CGI or use Mapscript ü Only certain Map. Server parameters accept variable substitution ü Available for ü ü DATA TILEINDEX CONNECTION FILTER ü Remember to set DATAPATTERN properly
 Map. Server Example ü DATA /data/%SSL_CLIENT_S_DN_OU%/nulldata. shp ü Status Default ü Unless Org name passed properly, map won’t draw ü Add error page to indicate security issue ü Use FILTER to display subsets of data to different groups
Map. Server Example ü DATA /data/%SSL_CLIENT_S_DN_OU%/nulldata. shp ü Status Default ü Unless Org name passed properly, map won’t draw ü Add error page to indicate security issue ü Use FILTER to display subsets of data to different groups
 To Summarize: Basic Steps ü Get a CA certificate ü Set SSLCertificate. File to point to your CA ü Set SSLVerify. Client to require ü Set SSLRequire as necessary to limit access ü Limit access using ü Fake. Basic. Auth and / or ü Setting SSL Environement Variables and / or ü Setting Session ID variables ü Add variables to Map. Server (as necessary)
To Summarize: Basic Steps ü Get a CA certificate ü Set SSLCertificate. File to point to your CA ü Set SSLVerify. Client to require ü Set SSLRequire as necessary to limit access ü Limit access using ü Fake. Basic. Auth and / or ü Setting SSL Environement Variables and / or ü Setting Session ID variables ü Add variables to Map. Server (as necessary)
 Questions?
Questions?
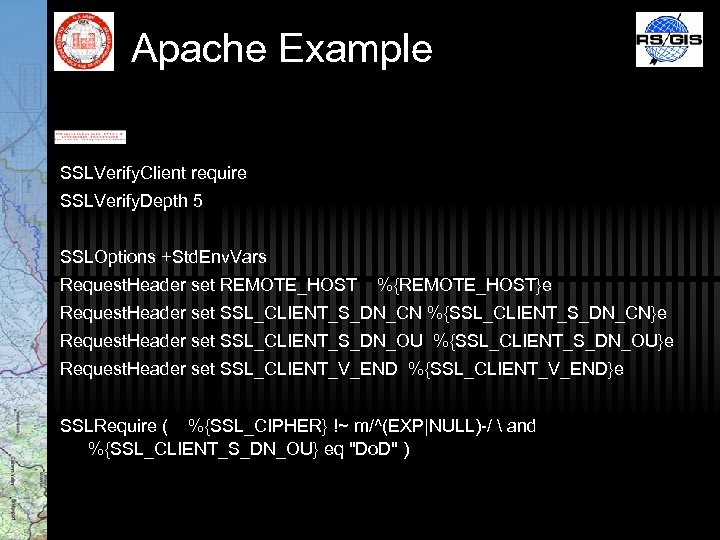 Apache Example SSLVerify. Client require SSLVerify. Depth 5 SSLOptions +Std. Env. Vars Request. Header set REMOTE_HOST %{REMOTE_HOST}e Request. Header set SSL_CLIENT_S_DN_CN %{SSL_CLIENT_S_DN_CN}e Request. Header set SSL_CLIENT_S_DN_OU %{SSL_CLIENT_S_DN_OU}e Request. Header set SSL_CLIENT_V_END %{SSL_CLIENT_V_END}e SSLRequire ( %{SSL_CIPHER} !~ m/^(EXP|NULL)-/ and %{SSL_CLIENT_S_DN_OU} eq "Do. D" )
Apache Example SSLVerify. Client require SSLVerify. Depth 5 SSLOptions +Std. Env. Vars Request. Header set REMOTE_HOST %{REMOTE_HOST}e Request. Header set SSL_CLIENT_S_DN_CN %{SSL_CLIENT_S_DN_CN}e Request. Header set SSL_CLIENT_S_DN_OU %{SSL_CLIENT_S_DN_OU}e Request. Header set SSL_CLIENT_V_END %{SSL_CLIENT_V_END}e SSLRequire ( %{SSL_CIPHER} !~ m/^(EXP|NULL)-/ and %{SSL_CLIENT_S_DN_OU} eq "Do. D" )


