777e15c6a1e87012ef358ce888a16b0f.ppt
- Количество слайдов: 19

PKI in the Small A Public Key Infrastructure for Advanced Network Technologies Workshop April 27– 28, 2000, NIST James A. Rome Executive Secretary, IST Center for Information Infrastructure Technology DOE Y 12, Advanced Technology Directorate Oak Ridge, Tennessee 37830 -8027 (865) 574 -1306 jar@y 12. doe. gov http: //www. ornl. gov/~jar

Center for Information Infrastructure Technology Some uses of PKI l Authentication of people, resources, places l Encrypt and/or digitally sign w E-mail w Code objects w Communication channels l Basis for strong authorization l Keystone of secure applications What issues arise when you actually want to use PKI in an application-based infrastructure?

Center for Information Infrastructure Technology What does an X. 509 certificate do? PKI X. 509 certificates bind an identity to a public key The person with the distinguished name E=jar@y 12. doe. gov, CN=James A. Rome, UID=jar, L=Oak Ridge, TN, ST=Administrator, OU=Center for Information Infrastructure Technology, O=Materials Microcharacterization Collaboratory, C=US is known by the public key 30: 81: 89: 02: 81: 00: B 1: FC: D 0: D 8: 6 F: B 3: 71: 73: 36: 6 B: 5 F: 1 C: 9 F: 9 B: 5 B: E 9: 35: 84: 95: A 1: C 0: 2 D: B 2: E 5: 5 D: 0 F: 8 C: B 8: 4 E: 78: 69: B 8: BB: E 3: 71: B 5: C 2: AB: 08: 8 A: 8 F: 47: 3 C: 51: CB: AC: F 2: F 3: D 0: B 4: 2 F: 34: F 7: E 1: 1 D: 30: D 5: 51: F 1: 72: F 9: 3 D: AE: C 1: 5 D: 5 B: 26: 39: 5 A: DA: 10: CF: A 3: 3 E: 95: 99: 7 A: F 3: 27: 79: 88: 7 A: BC: E 4: 9 A: F 6: 39: 87: 9 A: 49: E 0: 70: 9 A: E 4: B 4: 29: 93: 33: C 0: 41: 59: FB: 41: B 6: D 8: B 1: A 7: 39: FC: 5 D: 17: 1 B: 75: AF: B 2: 81: EC: EE: E 7: A 7: FB: 85: 17: B 1: 33: 02: 03: 01: 00: 01

Center for Information Infrastructure Technology Is this enough? l There is at least one more James A. Rome (I own his paintings!) l Is the information in the DN enough to pin down which James A. Rome you want to deal with in a large trust realm? How about John Smith? l Do you accept the assurances of the authority that issued my certificate? (Issuer: CN=MMC CA, OU=Center for Information Infrastructure Technology, O=Materials Microcharacterization Collaboratory, L=Oak Ridge, TN, ST=Administrator, C=US) l Is my certificate valid right now? l Do you want to trust me for everything?

Center for Information Infrastructure Technology It suffices in some situations A bank, the IRS (One-way trust) l They only care that you identified yourself with a valid social security number (your “identity”) l As long as there is money in the account the PKI certificate from a bank identifies its customer for its purposes w If you are a crook, it is someone else’s problem l Your social security number is a unique government identifier, but you may have many certificates w What information do you want in your certificate? w What information does the issuer want in it? w What ever happened to privacy?

Certificates may only be a first step in others. . . Center for Information Infrastructure Technology The whole Canadian government has Entrust certificates l Can you use the certificates to really identify the person you want? l Should they be trusted? (Two-way trust) In general, an out-of-band method is needed to really identify someone to your satisfaction l You know someone who knows him (PGP) l You met them at a meeting and have their e-mail l The owner of a resource says “OK”

Center for Information Infrastructure Technology Size of the trust realm matters l. A collaboratory works well w ~100 people w PGP model of trust works w Members unlikely to become criminals overnight l. A National Laboratory is kind of big w Everyone has a government badge, including – grad students from India – janitors, guards, secretaries, scientists w Can you tell which is which? w For some things it matters The applications using PKI must enforce restrictions

Center for Information Infrastructure Technology Authorization is what counts PKI can provide strong authentication, but only the owners of resources can authorize their use l How do you use certificates in the authorization process? l Can you guarantee that stakeholder rights are enforced? (See Akenti in my other talk) l Is their an audit trail for legal action in case of criminal activity? l Who determines and maintains the security policies?

Center for Information Infrastructure Technology Security and networking With million-$ instruments on line, security is a necessity. l Fast, transparent encryption l Secure multicast for conferencing and group collaboration l Accurate and fast knowledge of who is accessing our devices from across the net Certificates are the key to achieving above

Center for Information Infrastructure Technology So you want to set up PKI? . . A PKI infrastructure is the most mature solution available for implementing security l SSL-based Web servers l SSL hooks in Java, CORBA, Entrust toolkits l Client certificate management in Netscape and IE l S/MIME e-mail l Signed Java and Java. Script applets (override security of sandbox) l Server-side programs l Stand-alone applications So, what is involved in deploying these tools?

Center for Information Infrastructure Technology Which certificates to use? Certificates issued by agency or Laboratory: l Users may already have certificates to support other applications l Organization accepts cost of maintaining infrastructure l Probably will be part of FPKI l Certificates are fairly generic Certificates issued by collaboratory or project: l Local control over certificate content l Easier to identify authorized users l May not be recognized by FPKI

Center for Information Infrastructure Technology SSL Web servers Netscape, IIS, and Apache (Stronghold) all support SSL encrypted channels. l It is easy to configure a Web server to require certificates and to only accept those from one CA l You need a server certificate w Minimum cost is ~$300 w You may need a Dunn and Bradstreet report and letter from the company President, … l ORNL uses Thawte server certificates l You probably want to issue your own server certificates. . .

Center for Information Infrastructure Technology Certificate Authorities (CAs) Certificate Authority software allows you to issue server and client PKI certificates l Roll your own with SSLeahy or newer toolkits w Bad idea. No tools, no user interfaces, etc. l Buy one from Netscape, Entrust, … w Netscape cost ~$31 (internal), $8 (external) per certificate l You want your CA to be on a secure machine (locked room, not a lot of other things on it). l What should the Federal policy on recognizing these CAs be?
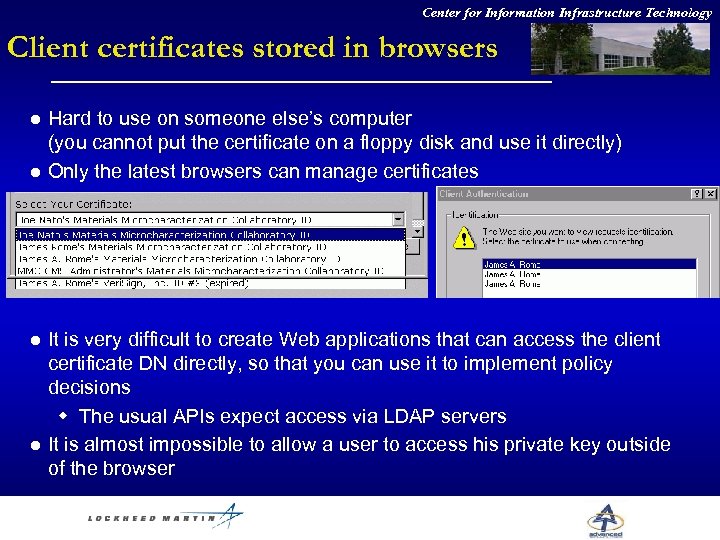
Center for Information Infrastructure Technology Client certificates stored in browsers l l Hard to use on someone else’s computer (you cannot put the certificate on a floppy disk and use it directly) Only the latest browsers can manage certificates It is very difficult to create Web applications that can access the client certificate DN directly, so that you can use it to implement policy decisions w The usual APIs expect access via LDAP servers It is almost impossible to allow a user to access his private key outside of the browser

Center for Information Infrastructure Technology Browsers and certificates l How do they handle multiple certificates? w 1 certificate/e-mail address. l Must use Netscape or. IE 5. IE 4 never worked properly. l Can certificates be spoofed? — Yes w NS accepts every certificate in signed E-mail and overwrites existing certificate entry. w Only stores user certificates by e-mail address.

Center for Information Infrastructure Technology CA issues l No obvious “accept CA” mechanism w Certificate is invalid if the CA not on your “approved” list. But no info on how to get the CA certificate. l Most certificates do not contain CRL URL l Generally no ip address for the CA or LDAP server in the presented certificate l What does “certificate is valid” mean? w CA on approved list w Today is in the certificate validity range w Netscape 6 will allow you to designate a place to verify certificates (all or nothing)
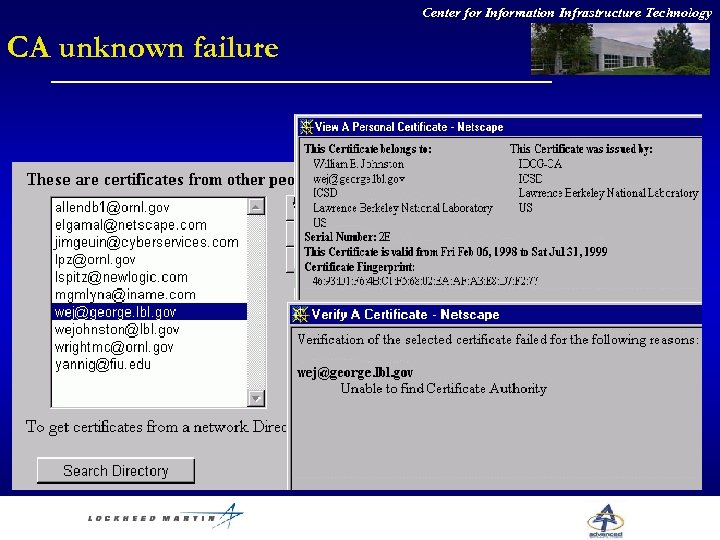
Center for Information Infrastructure Technology CA unknown failure
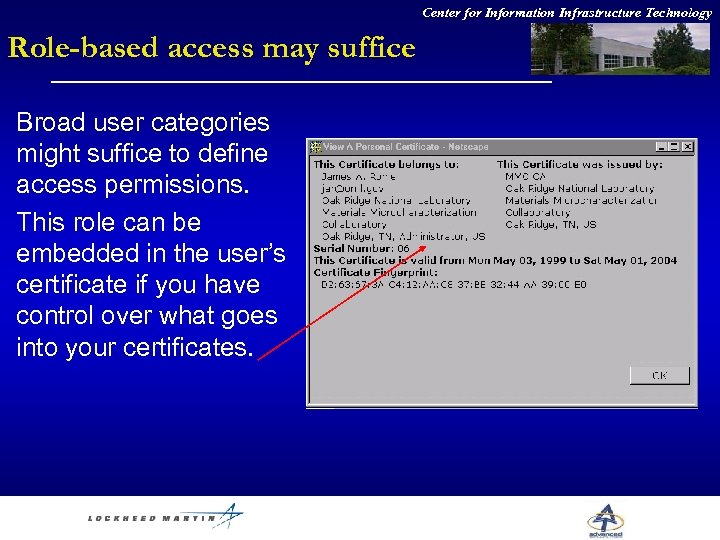
Center for Information Infrastructure Technology Role-based access may suffice Broad user categories might suffice to define access permissions. This role can be embedded in the user’s certificate if you have control over what goes into your certificates.

Center for Information Infrastructure Technology Summary Getting PKI certificates is only a small part of the process. Many issues must be resolved: l Which certificates and CA will you use? l What sort of PKI-enabled applications will you support? l How will the “out-of-band” information about the certificate holder be obtained? If it is not made easy and advantageous for the user, it will not be used
777e15c6a1e87012ef358ce888a16b0f.ppt