2b8537b0ac2ebf5493bfae3f34db4e90.ppt
- Количество слайдов: 27
 PKI ASSESSMENT The process of evaluating, verifying, and certifying your PKI Presented by: Randy V. Sabett Vanguard Enterprise Security Expo 2001 June 5, 2001 © Cooley Godward 2001 1
PKI ASSESSMENT The process of evaluating, verifying, and certifying your PKI Presented by: Randy V. Sabett Vanguard Enterprise Security Expo 2001 June 5, 2001 © Cooley Godward 2001 1
 Introduction l l l Dichotomy Challenges Models Mechanisms and criteria Path forward © Cooley Godward 2001 2
Introduction l l l Dichotomy Challenges Models Mechanisms and criteria Path forward © Cooley Godward 2001 2
 Dichotomy l l “UBIQUITOUS PKI!!!!!” …but many barriers è Need: common recognition mechanism © Cooley Godward 2001 3
Dichotomy l l “UBIQUITOUS PKI!!!!!” …but many barriers è Need: common recognition mechanism © Cooley Godward 2001 3
 Challenges - traditional technology vs. PKI l Traditional technology © Cooley Godward 2001 4
Challenges - traditional technology vs. PKI l Traditional technology © Cooley Godward 2001 4
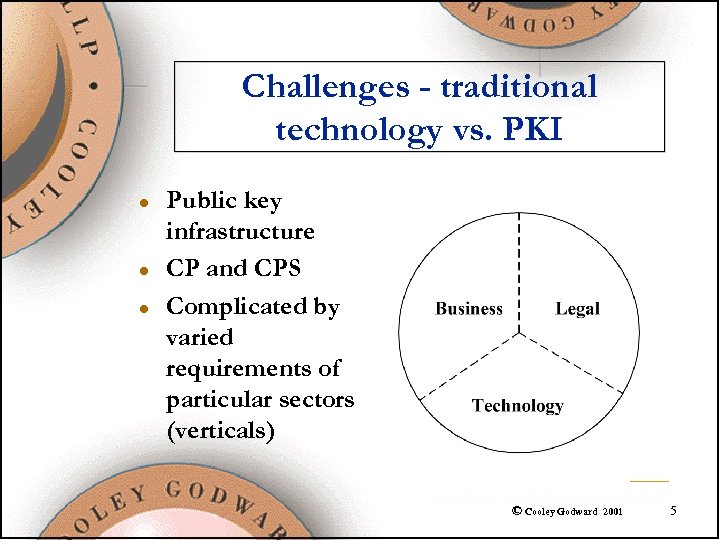 Challenges - traditional technology vs. PKI l l l Public key infrastructure CP and CPS Complicated by varied requirements of particular sectors (verticals) © Cooley Godward 2001 5
Challenges - traditional technology vs. PKI l l l Public key infrastructure CP and CPS Complicated by varied requirements of particular sectors (verticals) © Cooley Godward 2001 5
 Challenges - recognition l l No universally acceptable mechanism for recognizing the sufficiency of a PKI deployment Uncharted legal waters Several efforts and proposals - most focus on technical and business General model © Cooley Godward 2001 6
Challenges - recognition l l No universally acceptable mechanism for recognizing the sufficiency of a PKI deployment Uncharted legal waters Several efforts and proposals - most focus on technical and business General model © Cooley Godward 2001 6
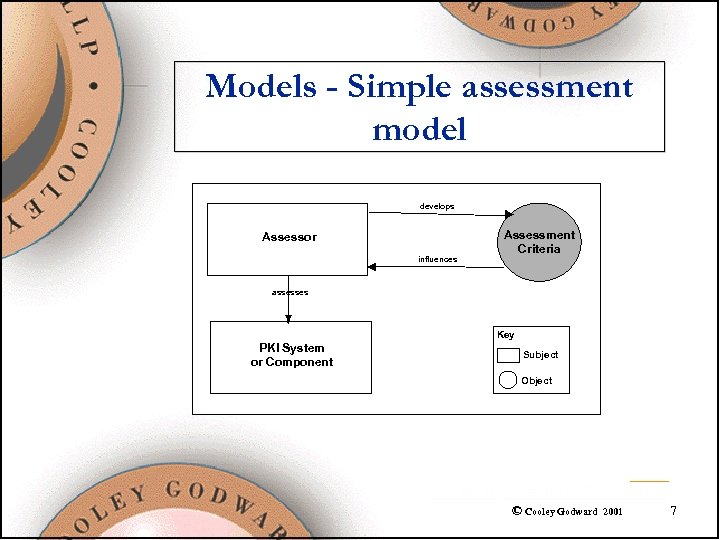 Models - Simple assessment model develops Assessor influences Assessment Criteria assesses Key PKI System or Component Subject Object © Cooley Godward 2001 7
Models - Simple assessment model develops Assessor influences Assessment Criteria assesses Key PKI System or Component Subject Object © Cooley Godward 2001 7
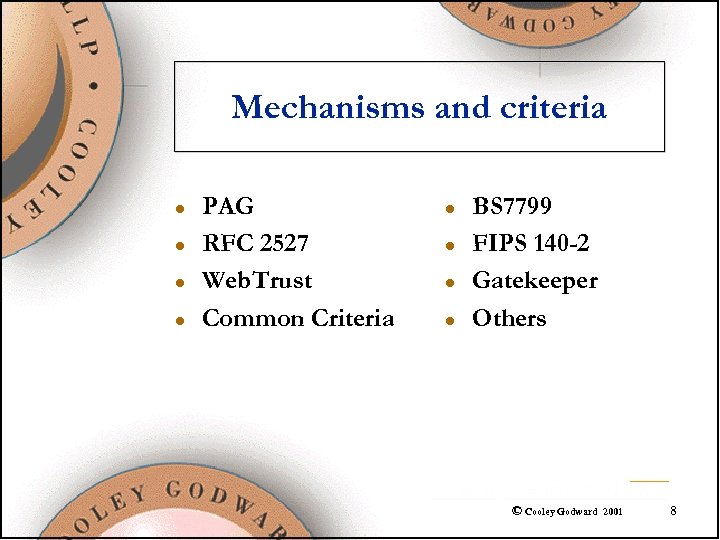 Mechanisms and criteria l l PAG RFC 2527 Web. Trust Common Criteria l l BS 7799 FIPS 140 -2 Gatekeeper Others © Cooley Godward 2001 8
Mechanisms and criteria l l PAG RFC 2527 Web. Trust Common Criteria l l BS 7799 FIPS 140 -2 Gatekeeper Others © Cooley Godward 2001 8
 PKI Assessment Guidelines (PAG) l l l Five year project of the Information Security Committee of the American Bar Association Follow up work to the Digital Signature Guidelines (1996) Participation by over 400 legal, technical, and business people © Cooley Godward 2001 9
PKI Assessment Guidelines (PAG) l l l Five year project of the Information Security Committee of the American Bar Association Follow up work to the Digital Signature Guidelines (1996) Participation by over 400 legal, technical, and business people © Cooley Godward 2001 9
 PAG (cont’d) l l D. 2. 1. 4. 1 The Effect of Contractual Privity Upon Relying Party’s Responsibilities Expressed as Covenants or Imposed by Law Issue Summary. This section discusses the issue of whether the relying party is in privity of contract with the other PKI participants… Relevant Considerations. Threshold question is whether the PKI attempts to create contractual privity between the CA and the relying party… Appropriate Requirements and Practices. It is necessary for the PKI to decide how to present relying party covenants; unlike other participants, however, relying party covenants tend to be small enough in number to make it feasible to list in this section, or perhaps cross reference. © Cooley Godward 2001 10
PAG (cont’d) l l D. 2. 1. 4. 1 The Effect of Contractual Privity Upon Relying Party’s Responsibilities Expressed as Covenants or Imposed by Law Issue Summary. This section discusses the issue of whether the relying party is in privity of contract with the other PKI participants… Relevant Considerations. Threshold question is whether the PKI attempts to create contractual privity between the CA and the relying party… Appropriate Requirements and Practices. It is necessary for the PKI to decide how to present relying party covenants; unlike other participants, however, relying party covenants tend to be small enough in number to make it feasible to list in this section, or perhaps cross reference. © Cooley Godward 2001 10
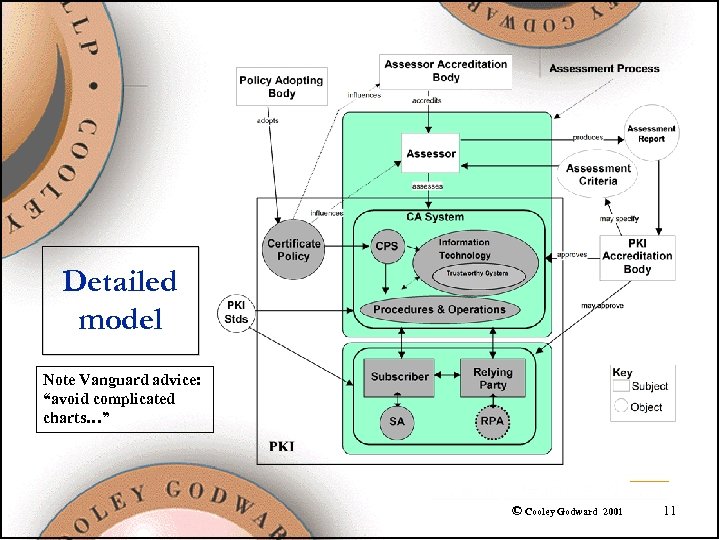 Detailed model Note Vanguard advice: “avoid complicated charts…” © Cooley Godward 2001 11
Detailed model Note Vanguard advice: “avoid complicated charts…” © Cooley Godward 2001 11
 RFC 2527 l l l Framework for PKI policy documents Certificate Policies Certification Practice Statements © Cooley Godward 2001 12
RFC 2527 l l l Framework for PKI policy documents Certificate Policies Certification Practice Statements © Cooley Godward 2001 12
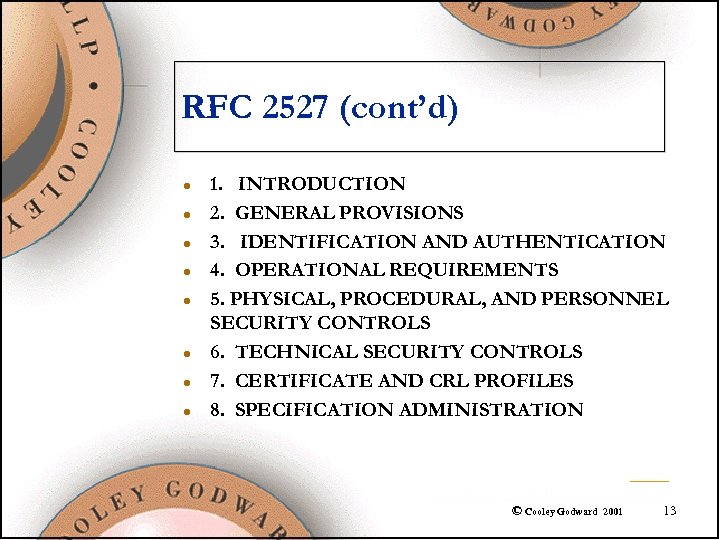 RFC 2527 (cont’d) l l l l 1. INTRODUCTION 2. GENERAL PROVISIONS 3. IDENTIFICATION AND AUTHENTICATION 4. OPERATIONAL REQUIREMENTS 5. PHYSICAL, PROCEDURAL, AND PERSONNEL SECURITY CONTROLS 6. TECHNICAL SECURITY CONTROLS 7. CERTIFICATE AND CRL PROFILES 8. SPECIFICATION ADMINISTRATION © Cooley Godward 2001 13
RFC 2527 (cont’d) l l l l 1. INTRODUCTION 2. GENERAL PROVISIONS 3. IDENTIFICATION AND AUTHENTICATION 4. OPERATIONAL REQUIREMENTS 5. PHYSICAL, PROCEDURAL, AND PERSONNEL SECURITY CONTROLS 6. TECHNICAL SECURITY CONTROLS 7. CERTIFICATE AND CRL PROFILES 8. SPECIFICATION ADMINISTRATION © Cooley Godward 2001 13
 Web. Trust l l l Framework to assess adequacy and effectiveness of controls employed by CAs Designed specifically for the examinations of CA business activities Builds on X 9. 79 work of the American Banker’s Association © Cooley Godward 2001 14
Web. Trust l l l Framework to assess adequacy and effectiveness of controls employed by CAs Designed specifically for the examinations of CA business activities Builds on X 9. 79 work of the American Banker’s Association © Cooley Godward 2001 14
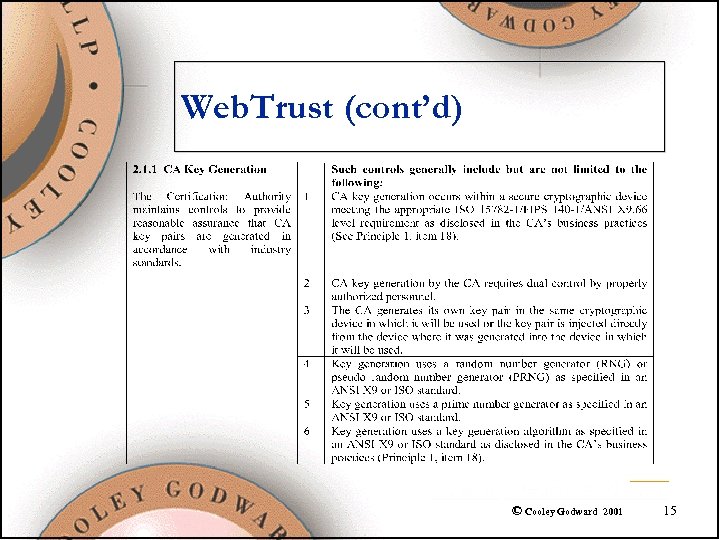 Web. Trust (cont’d) © Cooley Godward 2001 15
Web. Trust (cont’d) © Cooley Godward 2001 15
 X 9. 79 - CA Control Objectives l l National standard - approved by ABA (the other ABA - American Banker’s Association) and ANSI Being proposed to ISO TC 68 as an international work item © Cooley Godward 2001 16
X 9. 79 - CA Control Objectives l l National standard - approved by ABA (the other ABA - American Banker’s Association) and ANSI Being proposed to ISO TC 68 as an international work item © Cooley Godward 2001 16
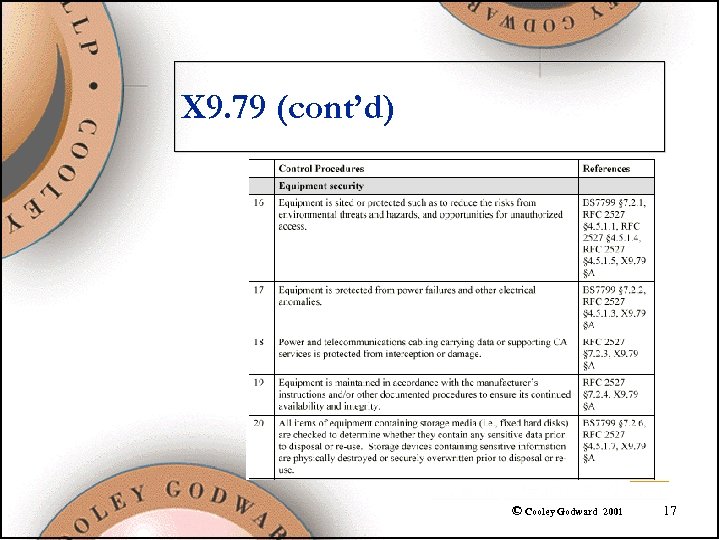 X 9. 79 (cont’d) © Cooley Godward 2001 17
X 9. 79 (cont’d) © Cooley Godward 2001 17
 Common Criteria l l l Some view as replacement for the Orange Book, ITSEC, etc. International acceptance Focus on protection profile © Cooley Godward 2001 18
Common Criteria l l l Some view as replacement for the Orange Book, ITSEC, etc. International acceptance Focus on protection profile © Cooley Godward 2001 18
 BS 7799 - Code of Practice for Information Security Management l l British Standard being used in several other European countries General Information Security standard, not focussed on PKI Certification scheme called c: cure similar to ISO 9000 Now ISO/IEC 17799: 2000 © Cooley Godward 2001 19
BS 7799 - Code of Practice for Information Security Management l l British Standard being used in several other European countries General Information Security standard, not focussed on PKI Certification scheme called c: cure similar to ISO 9000 Now ISO/IEC 17799: 2000 © Cooley Godward 2001 19
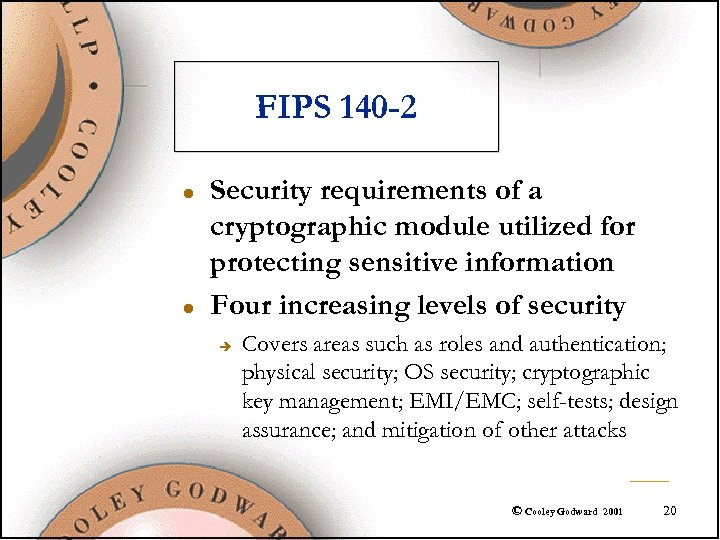 FIPS 140 -2 l l Security requirements of a cryptographic module utilized for protecting sensitive information Four increasing levels of security è Covers areas such as roles and authentication; physical security; OS security; cryptographic key management; EMI/EMC; self-tests; design assurance; and mitigation of other attacks © Cooley Godward 2001 20
FIPS 140 -2 l l Security requirements of a cryptographic module utilized for protecting sensitive information Four increasing levels of security è Covers areas such as roles and authentication; physical security; OS security; cryptographic key management; EMI/EMC; self-tests; design assurance; and mitigation of other attacks © Cooley Godward 2001 20
 FIPS 140 -2 (cont’d) l 4. 5. 2 Single-Chip Cryptographic Modules l SECURITY LEVEL 2 - All Level 1 requirements plus: è è l chip covered with tamper-evident coating or contained in a tamper-evident enclosure coating or enclosure shall be opaque within the visible spectrum. SECURITY LEVEL 3 - All Level 2 requirements plus: è è è Either: chip covered with hard opaque tamper-evident coating, or the chip shall be contained within a strong enclosure. The enclosure shall be such that attempts at removal or penetration shall have a high probability of causing serious damage to the cryptographic module (i. e. , the module will not function). © Cooley Godward 2001 21
FIPS 140 -2 (cont’d) l 4. 5. 2 Single-Chip Cryptographic Modules l SECURITY LEVEL 2 - All Level 1 requirements plus: è è l chip covered with tamper-evident coating or contained in a tamper-evident enclosure coating or enclosure shall be opaque within the visible spectrum. SECURITY LEVEL 3 - All Level 2 requirements plus: è è è Either: chip covered with hard opaque tamper-evident coating, or the chip shall be contained within a strong enclosure. The enclosure shall be such that attempts at removal or penetration shall have a high probability of causing serious damage to the cryptographic module (i. e. , the module will not function). © Cooley Godward 2001 21
 Gatekeeper l l l Australian PKI strategy and enabler for the delivery of Government online Accreditation Criteria published Covers procurement, security policy/planning, physical security, technology evaluation, personnel vetting, legal issues, and privacy considerations © Cooley Godward 2001 22
Gatekeeper l l l Australian PKI strategy and enabler for the delivery of Government online Accreditation Criteria published Covers procurement, security policy/planning, physical security, technology evaluation, personnel vetting, legal issues, and privacy considerations © Cooley Godward 2001 22
 Path forward l l Development of internationally acceptable suite of criteria, NOT development of an international approach to PKI Common Criteria, Web. Trust, & PAG promising Common Criteria è Industry specific protection profiles è Global recognition Web. Trust è PKI-specific set of criteria © Cooley Godward 2001 23
Path forward l l Development of internationally acceptable suite of criteria, NOT development of an international approach to PKI Common Criteria, Web. Trust, & PAG promising Common Criteria è Industry specific protection profiles è Global recognition Web. Trust è PKI-specific set of criteria © Cooley Godward 2001 23
 On going activities l l l Update to RFC 2527 Industry specific protection profiles Other industry and governmental activities è PAG out for public comment è X 9. 79 into ISO © Cooley Godward 2001 24
On going activities l l l Update to RFC 2527 Industry specific protection profiles Other industry and governmental activities è PAG out for public comment è X 9. 79 into ISO © Cooley Godward 2001 24
 Resources for more info l l l l ABA - http: //www. abanet. org/scitech/ec/isc/ RFC 2527 - http: //www. ietf. org/rfc. html Web. Trust - http: //www. aicpa. org/webtrust/princrit. htm X 9. 79 - http: //webstore. ansi. org/ansidocstore/ Common Criteria - http: //www. commoncriteria. org/ FIPS 140 - http: //csrc. nist. gov/cryptval/140 -1. htm Gatekeeper http: //www. govonline. gov. au/projects/publickey/ © Cooley Godward 2001 25
Resources for more info l l l l ABA - http: //www. abanet. org/scitech/ec/isc/ RFC 2527 - http: //www. ietf. org/rfc. html Web. Trust - http: //www. aicpa. org/webtrust/princrit. htm X 9. 79 - http: //webstore. ansi. org/ansidocstore/ Common Criteria - http: //www. commoncriteria. org/ FIPS 140 - http: //csrc. nist. gov/cryptval/140 -1. htm Gatekeeper http: //www. govonline. gov. au/projects/publickey/ © Cooley Godward 2001 25
 Questions? © Cooley Godward 2001 26
Questions? © Cooley Godward 2001 26
 PKI ASSESSMENT The process of evaluating, verifying, and certifying your PKI Presented by: Randy V. Sabett Cooley Godward LLP 703. 456. 8137 (phone) - 703. 456. 8100 (fax) rsabett@cooley. com www. cooley. com © Cooley Godward 2001 27
PKI ASSESSMENT The process of evaluating, verifying, and certifying your PKI Presented by: Randy V. Sabett Cooley Godward LLP 703. 456. 8137 (phone) - 703. 456. 8100 (fax) rsabett@cooley. com www. cooley. com © Cooley Godward 2001 27


