52f60ad81a8e14c6cc7047cd4c00ea39.ppt
- Количество слайдов: 72
 Pirates and Protocols: Trademark Use and Protection on the Internet Wednesday, March 18, 2009 7: 00 p. m. New York City Bar Association 42 West 44 th Street New York, NY
Pirates and Protocols: Trademark Use and Protection on the Internet Wednesday, March 18, 2009 7: 00 p. m. New York City Bar Association 42 West 44 th Street New York, NY
 Pirates and Protocols: Trademark Use and Protection on the Internet Moderator Monica Richman, Partner Sonnenschein Nath & Rosenthal LLP Speakers Mark Fiore Weil, Gotshal & Manges LLP Erik Walsh Arnold & Porter LLP Heather Greenberg Associate General Counsel The Topps Company, Inc. Mitchell Stein Partner Sullivan & Worcester LLP Jonathan Sirota Secretary & Director of Legal Affairs Smart. Money Kevin Taylor Partner Taylor & Mrsich, LLP Counsel for e. Bay, Tiffany v. e. Bay Counsel for Tiffany, Tiffany v. e. Bay
Pirates and Protocols: Trademark Use and Protection on the Internet Moderator Monica Richman, Partner Sonnenschein Nath & Rosenthal LLP Speakers Mark Fiore Weil, Gotshal & Manges LLP Erik Walsh Arnold & Porter LLP Heather Greenberg Associate General Counsel The Topps Company, Inc. Mitchell Stein Partner Sullivan & Worcester LLP Jonathan Sirota Secretary & Director of Legal Affairs Smart. Money Kevin Taylor Partner Taylor & Mrsich, LLP Counsel for e. Bay, Tiffany v. e. Bay Counsel for Tiffany, Tiffany v. e. Bay
 Pirates and Protocols: Trademark Use and Protection on the Internet The format for the discussion will be as follows: (1) Strategies for enforcement of trademark rights against online infringers and counterfeiters - a discussion of Tiffany (NJ), Inc. and Tiffany and Company v. e. Bay, Inc. , 2008 U. S. Dist. LEXIS 53359 (S. D. N. Y. , July 14, 2008). (2) Guidelines for using ‘adwords’ and behavioral advertising on the Internet - what is happening right now? (3) Recent developments regarding intellectual property and use on the Internet.
Pirates and Protocols: Trademark Use and Protection on the Internet The format for the discussion will be as follows: (1) Strategies for enforcement of trademark rights against online infringers and counterfeiters - a discussion of Tiffany (NJ), Inc. and Tiffany and Company v. e. Bay, Inc. , 2008 U. S. Dist. LEXIS 53359 (S. D. N. Y. , July 14, 2008). (2) Guidelines for using ‘adwords’ and behavioral advertising on the Internet - what is happening right now? (3) Recent developments regarding intellectual property and use on the Internet.
 Pirates and Protocols: Trademark Use and Protection on the Internet TIFFANY & CO. v. e. Bay Inc.
Pirates and Protocols: Trademark Use and Protection on the Internet TIFFANY & CO. v. e. Bay Inc.
 Pirates and Protocols: Trademark Use and Protection on the Internet Counterfeiting of the Tiffany Marks § Greatest threat to the Tiffany brand § Until the early-mid 2000’s, anticounterfeiting efforts focused on streetlevel § Customs Seizures § Raids § Canal St. § Litigation against Individual Vendors/Manufacturers
Pirates and Protocols: Trademark Use and Protection on the Internet Counterfeiting of the Tiffany Marks § Greatest threat to the Tiffany brand § Until the early-mid 2000’s, anticounterfeiting efforts focused on streetlevel § Customs Seizures § Raids § Canal St. § Litigation against Individual Vendors/Manufacturers
 Pirates and Protocols: Trademark Use and Protection on the Internet Counterfeit Trade Explodes on the Internet § Early 2003, Tiffany observes significant number of counterfeit Tiffany items available on e. Bay. § Tiffany initially pursues legal action against individual counterfeiters selling on e. Bay. § Pursuing legal action against individual e. Bay sellers does not stem the tide. § Too many § Relative anonymity § Many located abroad § Little likelihood of enforcing judgment
Pirates and Protocols: Trademark Use and Protection on the Internet Counterfeit Trade Explodes on the Internet § Early 2003, Tiffany observes significant number of counterfeit Tiffany items available on e. Bay. § Tiffany initially pursues legal action against individual counterfeiters selling on e. Bay. § Pursuing legal action against individual e. Bay sellers does not stem the tide. § Too many § Relative anonymity § Many located abroad § Little likelihood of enforcing judgment
 Pirates and Protocols: Trademark Use and Protection on the Internet Why Sue e. Bay?
Pirates and Protocols: Trademark Use and Protection on the Internet Why Sue e. Bay?
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Active Role in the Sales § e. Bay takes a fee at: § § § § Listing Sale Payment (if through Pay. Pal) Business advice Marketing calendars Advertising assistance (reimbursements) § § § Inform sellers that “Tiffany” is a top seller “Hot Lists” Sponsored links to advertise “Tiffany” on e. Bay assists its sellers to help grow their sales e. Bay focuses on Luxury Brands
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Active Role in the Sales § e. Bay takes a fee at: § § § § Listing Sale Payment (if through Pay. Pal) Business advice Marketing calendars Advertising assistance (reimbursements) § § § Inform sellers that “Tiffany” is a top seller “Hot Lists” Sponsored links to advertise “Tiffany” on e. Bay assists its sellers to help grow their sales e. Bay focuses on Luxury Brands
 Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Chain of Distribution n No sale/discounted merchandise n No liquidation n Controlled Chain (No Wholesalers) n No Overruns Allowed by Manufacturers n Full Refund on Returns n Nevertheless, e. Bay sellers observed offering hundreds of “Tiffany” items at a time
Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Chain of Distribution n No sale/discounted merchandise n No liquidation n Controlled Chain (No Wholesalers) n No Overruns Allowed by Manufacturers n Full Refund on Returns n Nevertheless, e. Bay sellers observed offering hundreds of “Tiffany” items at a time
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits Ineffective: § Ve. RO Program and its Deficiencies § Rights owners submit a Notice of Claimed Infringement (“NOCI”) § Good faith basis (under penalty of perjury) that listing is infringing § e. Bay will remove upon receipt § § Burden on rights owner Not proactive Too many listings to review Dynamic nature of e. Bay § Timing: Items can be sold between searching, reporting and removal § Clever counterfeiters
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits Ineffective: § Ve. RO Program and its Deficiencies § Rights owners submit a Notice of Claimed Infringement (“NOCI”) § Good faith basis (under penalty of perjury) that listing is infringing § e. Bay will remove upon receipt § § Burden on rights owner Not proactive Too many listings to review Dynamic nature of e. Bay § Timing: Items can be sold between searching, reporting and removal § Clever counterfeiters
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits Ineffective: Fraud Engine n e. Bay system that flags listings for e. Bay employees to review n Most of the filters flag only those items that are blatantly counterfeit – e. g. , “faux Tiffany”; “counterfeit Tiffany”
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits Ineffective: Fraud Engine n e. Bay system that flags listings for e. Bay employees to review n Most of the filters flag only those items that are blatantly counterfeit – e. g. , “faux Tiffany”; “counterfeit Tiffany”
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits: Repeat Offenders n Tiffany has identified dozens of repeat offenders – Identified numerous sellers that it reported on 3 or more occasions – Identifies repeat offenders who come back listing dozens, sometimes hundreds of “Tiffany” items
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Efforts to Prevent Counterfeits: Repeat Offenders n Tiffany has identified dozens of repeat offenders – Identified numerous sellers that it reported on 3 or more occasions – Identifies repeat offenders who come back listing dozens, sometimes hundreds of “Tiffany” items
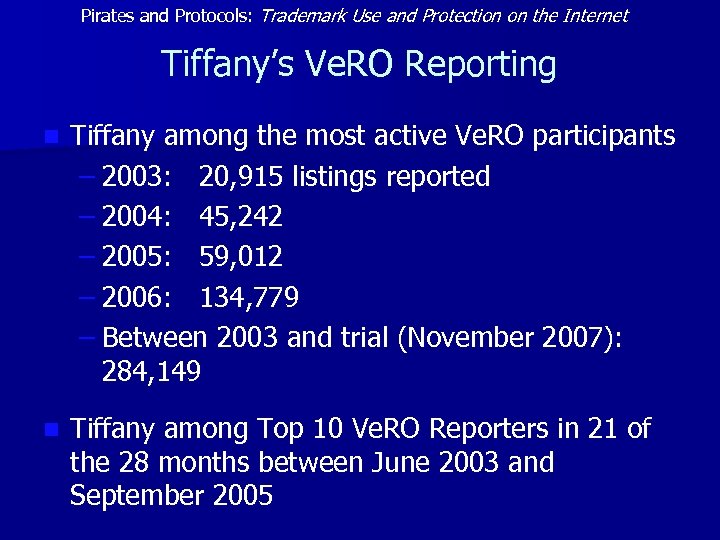 Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Ve. RO Reporting n Tiffany among the most active Ve. RO participants – 2003: 20, 915 listings reported – 2004: 45, 242 – 2005: 59, 012 – 2006: 134, 779 – Between 2003 and trial (November 2007): 284, 149 n Tiffany among Top 10 Ve. RO Reporters in 21 of the 28 months between June 2003 and September 2005
Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Ve. RO Reporting n Tiffany among the most active Ve. RO participants – 2003: 20, 915 listings reported – 2004: 45, 242 – 2005: 59, 012 – 2006: 134, 779 – Between 2003 and trial (November 2007): 284, 149 n Tiffany among Top 10 Ve. RO Reporters in 21 of the 28 months between June 2003 and September 2005
 Pirates and Protocols: Trademark Use and Protection on the Internet Summary of Tiffany’s Claims at Trial n Contributory Infringement n Direct Infringement n False Advertising n Dilution
Pirates and Protocols: Trademark Use and Protection on the Internet Summary of Tiffany’s Claims at Trial n Contributory Infringement n Direct Infringement n False Advertising n Dilution
 Pirates and Protocols: Trademark Use and Protection on the Internet Arguments on Appeal n Inwood – General vs. Specific Knowledge § Snow Crest, Inwood, Fonovisa n Comparative burden analysis n Applicability of Nominative Fair Use doctrine n Public Policy implications of District Court’s decision
Pirates and Protocols: Trademark Use and Protection on the Internet Arguments on Appeal n Inwood – General vs. Specific Knowledge § Snow Crest, Inwood, Fonovisa n Comparative burden analysis n Applicability of Nominative Fair Use doctrine n Public Policy implications of District Court’s decision
 Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Allegations • Tiffany’s central allegation: e. Bay knowingly facilitated the sale of counterfeit Tiffany silver jewelry items by sellers on the e. Bay website • Tiffany’s ancillary allegations: e. Bay advertised the availability of Tiffany goods via promotions on its website and via “sponsored links” on search engines such as Google and Yahoo
Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Allegations • Tiffany’s central allegation: e. Bay knowingly facilitated the sale of counterfeit Tiffany silver jewelry items by sellers on the e. Bay website • Tiffany’s ancillary allegations: e. Bay advertised the availability of Tiffany goods via promotions on its website and via “sponsored links” on search engines such as Google and Yahoo
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Anti-Infringement Measures Context: e. Bay’s Website • • • More than 200 million registered users worldwide At least 100 million listings on e. Bay at any given time Approximately 6 million new listings posted each day e. Bay itself does not sell any items e. Bay never possesses nor inspects items listed on its website Subject to e. Bay policies, sellers are responsible for creating their own listings
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Anti-Infringement Measures Context: e. Bay’s Website • • • More than 200 million registered users worldwide At least 100 million listings on e. Bay at any given time Approximately 6 million new listings posted each day e. Bay itself does not sell any items e. Bay never possesses nor inspects items listed on its website Subject to e. Bay policies, sellers are responsible for creating their own listings
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Ve. RO Program • • e. Bay’s “Notice-and-Takedown” System e. Bay allows rights owners to report listings through Ve. RO e. Bay automatically removes reported listings More than 14, 000 rights owners participate in Ve. RO Thousands of listings are removed each week All fees associated with removed listings are refunded Listings are removed within 24 hours, usually in under 4 hours
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Ve. RO Program • • e. Bay’s “Notice-and-Takedown” System e. Bay allows rights owners to report listings through Ve. RO e. Bay automatically removes reported listings More than 14, 000 rights owners participate in Ve. RO Thousands of listings are removed each week All fees associated with removed listings are refunded Listings are removed within 24 hours, usually in under 4 hours
 Pirates and Protocols: Trademark Use and Protection on the Internet Notice of Claimed Infringement
Pirates and Protocols: Trademark Use and Protection on the Internet Notice of Claimed Infringement
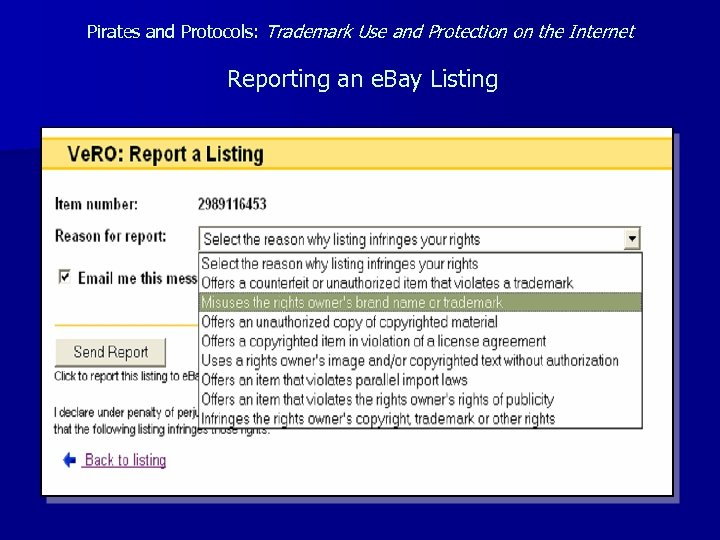 Pirates and Protocols: Trademark Use and Protection on the Internet Reporting an e. Bay Listing
Pirates and Protocols: Trademark Use and Protection on the Internet Reporting an e. Bay Listing
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Responses to Tiffany’s Reports • The trial record showed that e. Bay routinely removed listings that Tiffany reported to it • e. Bay never refused to remove a reported listing • Evidence showed that e. Bay’s response rate was close to 100 percent • Tiffany could point to only 15 instances in which e. Bay allegedly did not respond to a report and thus required Tiffany to follow up (based on nearly 300, 000 reported listings)
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Responses to Tiffany’s Reports • The trial record showed that e. Bay routinely removed listings that Tiffany reported to it • e. Bay never refused to remove a reported listing • Evidence showed that e. Bay’s response rate was close to 100 percent • Tiffany could point to only 15 instances in which e. Bay allegedly did not respond to a report and thus required Tiffany to follow up (based on nearly 300, 000 reported listings)
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Additional Key Anti-Infringement Measures • • More than 4, 000 e. Bay and Pay. Pal employees are devoted to anti-infringement/anti-fraud activities e. Bay requires users to abide by its User Agreement and has implemented policies that forbid infringing items e. Bay uses pop-up warning messages and undertakes efforts to educate users about intellectual property rights e. Bay allows rights owners to create “About Me” webpages to provide information about themselves
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Additional Key Anti-Infringement Measures • • More than 4, 000 e. Bay and Pay. Pal employees are devoted to anti-infringement/anti-fraud activities e. Bay requires users to abide by its User Agreement and has implemented policies that forbid infringing items e. Bay uses pop-up warning messages and undertakes efforts to educate users about intellectual property rights e. Bay allows rights owners to create “About Me” webpages to provide information about themselves
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Fraud Engine e. Bay proactively monitors listings on its site via a “fraud engine” consisting of tens of thousands of search rules • The fraud engine automatically flags for further review and removal listings that may be offering infringing items • Listings are flagged if they explicitly offer “knock -off” items or meet other criteria of suspiciousness • Thousands of listings are flagged each day •
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Fraud Engine e. Bay proactively monitors listings on its site via a “fraud engine” consisting of tens of thousands of search rules • The fraud engine automatically flags for further review and removal listings that may be offering infringing items • Listings are flagged if they explicitly offer “knock -off” items or meet other criteria of suspiciousness • Thousands of listings are flagged each day •
 Pirates and Protocols: Trademark Use and Protection on the Internet Suspensions of e. Bay Users e. Bay suspends users, on both temporary and permanent bases, based on willful or repeat violations • e. Bay suspends hundreds of thousands of sellers each year, including tens of thousands for infringing conduct • Tiffany could point to only a handful of instances where users were alleged to have not been suspended, and the District Court did not credit those instances •
Pirates and Protocols: Trademark Use and Protection on the Internet Suspensions of e. Bay Users e. Bay suspends users, on both temporary and permanent bases, based on willful or repeat violations • e. Bay suspends hundreds of thousands of sellers each year, including tens of thousands for infringing conduct • Tiffany could point to only a handful of instances where users were alleged to have not been suspended, and the District Court did not credit those instances •
 Pirates and Protocols: Trademark Use and Protection on the Internet District Court’s Application of Inwood • The Legal Standard: “[I]f a manufacturer or distributor intentionally induces another to infringe a trademark, or if it continues to supply its product to one whom it knows or has reason to know is engaging in trademark infringement, the manufacturer or distributor is contributorially responsible for any harm done as a result of the deceit. ” Inwood Labs. , Inc. v. Ives Labs. , Inc. , 456 U. S. 844, 854 (1982).
Pirates and Protocols: Trademark Use and Protection on the Internet District Court’s Application of Inwood • The Legal Standard: “[I]f a manufacturer or distributor intentionally induces another to infringe a trademark, or if it continues to supply its product to one whom it knows or has reason to know is engaging in trademark infringement, the manufacturer or distributor is contributorially responsible for any harm done as a result of the deceit. ” Inwood Labs. , Inc. v. Ives Labs. , Inc. , 456 U. S. 844, 854 (1982).
 Pirates and Protocols: Trademark Use and Protection on the Internet Specific Versus Generalized Knowledge • The District Court held that generalized knowledge of infringing activity is insufficient under Inwood: “[C]ompanies like e. Bay cannot be held liable for trademark infringement based solely on their generalized knowledge that trademark infringement might be occurring on their websites. ” • “[T]rademark plaintiffs bear a high burden in establishing ‘knowledge. ’” Gucci Am. , Inc. v. Hall & Assocs. , 135 F. Supp. 2 d 409, 420 (S. D. N. Y. 2001). • Drawing support from copyright law, the District Court noted that “generalized knowledge that copyright infringement may take place in an Internet venue is insufficient to impose contributory liability. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Specific Versus Generalized Knowledge • The District Court held that generalized knowledge of infringing activity is insufficient under Inwood: “[C]ompanies like e. Bay cannot be held liable for trademark infringement based solely on their generalized knowledge that trademark infringement might be occurring on their websites. ” • “[T]rademark plaintiffs bear a high burden in establishing ‘knowledge. ’” Gucci Am. , Inc. v. Hall & Assocs. , 135 F. Supp. 2 d 409, 420 (S. D. N. Y. 2001). • Drawing support from copyright law, the District Court noted that “generalized knowledge that copyright infringement may take place in an Internet venue is insufficient to impose contributory liability. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Rejection of Restatement § The Restatement (Third) of Unfair Competition states that contributory infringement occurs where a defendant “fails to take reasonable precautions” against infringing activity in circumstances in which that activity “can be reasonably anticipated. ” • Noting that the Supreme Court in Inwood called the “reasonable anticipation” standard “watered down and incorrect, ” the District Court held that the Restatement did not govern: “Tiffany’s argument is foreclosed by Inwood itself. ” • “In determining whether e. Bay is liable, the standard is not whether e. Bay could reasonably anticipate possible infringement, but rather whether e. Bay continued to supply its services to sellers when it knew or had reason to know of infringement by those sellers. ” • The rejection of the “reasonable anticipation” standard is consistent with the principle that generalized knowledge is insufficient for contributory liability.
Pirates and Protocols: Trademark Use and Protection on the Internet Rejection of Restatement § The Restatement (Third) of Unfair Competition states that contributory infringement occurs where a defendant “fails to take reasonable precautions” against infringing activity in circumstances in which that activity “can be reasonably anticipated. ” • Noting that the Supreme Court in Inwood called the “reasonable anticipation” standard “watered down and incorrect, ” the District Court held that the Restatement did not govern: “Tiffany’s argument is foreclosed by Inwood itself. ” • “In determining whether e. Bay is liable, the standard is not whether e. Bay could reasonably anticipate possible infringement, but rather whether e. Bay continued to supply its services to sellers when it knew or had reason to know of infringement by those sellers. ” • The rejection of the “reasonable anticipation” standard is consistent with the principle that generalized knowledge is insufficient for contributory liability.
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Alleged Knowledge n The District Court: • rejected Tiffany’s demand letters as a basis for knowledge, concluding that demand letters generally “are insufficient to impute knowledge as to instances not specifically identified in such notices, particularly in cases where the activity at issue is not always infringing. ” • rejected Tiffany’s “five-or-more” rule, by which Tiffany alleged that any seller of “five or more” Tiffany items is “almost certainly” selling counterfeit items: “Tiffany’s own CEO disavowed the importance of the five-or-more rule. ” • declined to credit the “buying programs” Tiffany conducted in an attempt to determine the amount of counterfeit Tiffany items on e. Bay: “Tiffany entirely suspended its normal policing procedures during the programs. ”
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Alleged Knowledge n The District Court: • rejected Tiffany’s demand letters as a basis for knowledge, concluding that demand letters generally “are insufficient to impute knowledge as to instances not specifically identified in such notices, particularly in cases where the activity at issue is not always infringing. ” • rejected Tiffany’s “five-or-more” rule, by which Tiffany alleged that any seller of “five or more” Tiffany items is “almost certainly” selling counterfeit items: “Tiffany’s own CEO disavowed the importance of the five-or-more rule. ” • declined to credit the “buying programs” Tiffany conducted in an attempt to determine the amount of counterfeit Tiffany items on e. Bay: “Tiffany entirely suspended its normal policing procedures during the programs. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Responses When It Had Knowledge n When advised of specific instances of infringement, “e. Bay responded appropriately. ” • Even if a defendant has knowledge of infringing activity, contributory liability only attaches if the defendant fails to take steps to remedy it, that is, if the defendant “continues to supply” its product or service. • “Here, when Tiffany put e. Bay on notice of specific items that Tiffany believed to be infringing, e. Bay immediately removed those listings. ” • Tiffany conceded at trial “that e. Bay always acted in good faith and never refused to remove a listing after a NOCI had been filed. ” • In addition, “when e. Bay had knowledge that a seller was repeatedly engaging in counterfeit activity, e. Bay’s pattern was to suspend that seller and then take further corrective action. ”
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Responses When It Had Knowledge n When advised of specific instances of infringement, “e. Bay responded appropriately. ” • Even if a defendant has knowledge of infringing activity, contributory liability only attaches if the defendant fails to take steps to remedy it, that is, if the defendant “continues to supply” its product or service. • “Here, when Tiffany put e. Bay on notice of specific items that Tiffany believed to be infringing, e. Bay immediately removed those listings. ” • Tiffany conceded at trial “that e. Bay always acted in good faith and never refused to remove a listing after a NOCI had been filed. ” • In addition, “when e. Bay had knowledge that a seller was repeatedly engaging in counterfeit activity, e. Bay’s pattern was to suspend that seller and then take further corrective action. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Authentic Tiffany Items on e. Bay n Relevant to the District Court’s conclusion was evidence showing that authentic Tiffany items are sold on e. Bay. • “[A] substantial number of authentic Tiffany goods are sold on e. Bay, including both new and vintage silver jewelry, sometimes in lots of five or more. ” • The doctrine of contributory trademark infringement “cannot be used as a sword to cut off resale of authentic Tiffany items. ” • “e. Bay and other online market websites may properly promote and facilitate the growth of legitimate secondary markets in brand-name goods. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Authentic Tiffany Items on e. Bay n Relevant to the District Court’s conclusion was evidence showing that authentic Tiffany items are sold on e. Bay. • “[A] substantial number of authentic Tiffany goods are sold on e. Bay, including both new and vintage silver jewelry, sometimes in lots of five or more. ” • The doctrine of contributory trademark infringement “cannot be used as a sword to cut off resale of authentic Tiffany items. ” • “e. Bay and other online market websites may properly promote and facilitate the growth of legitimate secondary markets in brand-name goods. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Trademark Owner’s Policing Duty • “Tiffany and e. Bay alike have an interest in eliminating counterfeit Tiffany merchandise from e. Bay. ” • “[T]he heart of this dispute is. . . who should bear the burden of policing Tiffany’s valuable trademarks in Internet commerce. ” • “The law is clear: it is the trademark owner’s burden to police its mark”; “Tiffany must ultimately bear the burden of protecting its trademark. ” • See also, e. g. , Standing Stone Media, Inc. v. Indiancountrytoday. com, 193 F. Supp. 2 d 528, 532 (N. D. N. Y. 2002) (trademark owners have duty to “police and enforce their trademark rights”); Mc. Carthy on Trademarks and Unfair Competition (“[C]orporate owners of trademarks have a duty to protect and preserve the corporation’s trademark assets through vigilant policing and appropriate acts of enforcement. ”).
Pirates and Protocols: Trademark Use and Protection on the Internet Trademark Owner’s Policing Duty • “Tiffany and e. Bay alike have an interest in eliminating counterfeit Tiffany merchandise from e. Bay. ” • “[T]he heart of this dispute is. . . who should bear the burden of policing Tiffany’s valuable trademarks in Internet commerce. ” • “The law is clear: it is the trademark owner’s burden to police its mark”; “Tiffany must ultimately bear the burden of protecting its trademark. ” • See also, e. g. , Standing Stone Media, Inc. v. Indiancountrytoday. com, 193 F. Supp. 2 d 528, 532 (N. D. N. Y. 2002) (trademark owners have duty to “police and enforce their trademark rights”); Mc. Carthy on Trademarks and Unfair Competition (“[C]orporate owners of trademarks have a duty to protect and preserve the corporation’s trademark assets through vigilant policing and appropriate acts of enforcement. ”).
 Pirates and Protocols: Trademark Use and Protection on the Internet Willful Blindness in Trademark Law • As a corollary to the knowledge requirement for contributory trademark liability, courts have recognized the concept of “willful blindness. ” • “To be willfully blind, a person must suspect wrongdoing and deliberately fail to investigate. ” Hard Rock Cafe Licensing Corp. v. Concession Servs. , Inc. , 955 F. 2 d 1143, 1149 (7 th Cir. 1992). • But a defendant “has no affirmative duty to take precautions against the sale of counterfeits. ” Hard Rock, 955 F. 2 d at 1149.
Pirates and Protocols: Trademark Use and Protection on the Internet Willful Blindness in Trademark Law • As a corollary to the knowledge requirement for contributory trademark liability, courts have recognized the concept of “willful blindness. ” • “To be willfully blind, a person must suspect wrongdoing and deliberately fail to investigate. ” Hard Rock Cafe Licensing Corp. v. Concession Servs. , Inc. , 955 F. 2 d 1143, 1149 (7 th Cir. 1992). • But a defendant “has no affirmative duty to take precautions against the sale of counterfeits. ” Hard Rock, 955 F. 2 d at 1149.
 Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Alleged Willful Blindness n n The District Court held that the evidence did not support a finding of willful blindness by e. Bay. The court instead found, among other things, that: • e. Bay had committed as much as $20 million each year to tools to promote trust and safety on its site. • one quarter of e. Bay’s workforce was devoted to trust and safety. • e. Bay proactively searched listings on its site for indications of fraudulent activity. n “Put simply, ” the court concluded, “it cannot be said that e. Bay purposefully contrived to avoid learning of counterfeiting on its website, or that e. Bay failed to investigate once it learned of such counterfeiting. ”
Pirates and Protocols: Trademark Use and Protection on the Internet e. Bay’s Alleged Willful Blindness n n The District Court held that the evidence did not support a finding of willful blindness by e. Bay. The court instead found, among other things, that: • e. Bay had committed as much as $20 million each year to tools to promote trust and safety on its site. • one quarter of e. Bay’s workforce was devoted to trust and safety. • e. Bay proactively searched listings on its site for indications of fraudulent activity. n “Put simply, ” the court concluded, “it cannot be said that e. Bay purposefully contrived to avoid learning of counterfeiting on its website, or that e. Bay failed to investigate once it learned of such counterfeiting. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Remaining Claims n The District Court rejected Tiffany’s remaining claims of direct trademark infringement and false advertising, direct and contributory dilution, unfair competition, and analogous state-law claims. n Tiffany challenged e. Bay’s use of Tiffany’s trademarks on its website and its purchases of “sponsored links” on Google and Yahoo to advertise the availability of Tiffany jewelry on e. Bay. • These practices are protected by the doctrine of “nominative fair use, ” pursuant to which “trademark owners cannot prevent others from making a descriptive use of their trademark. ” • The doctrine “is essential because it is undisputed that trademark owners cannot use trademark law to prevent the resale of authentic, trademarked goods. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Tiffany’s Remaining Claims n The District Court rejected Tiffany’s remaining claims of direct trademark infringement and false advertising, direct and contributory dilution, unfair competition, and analogous state-law claims. n Tiffany challenged e. Bay’s use of Tiffany’s trademarks on its website and its purchases of “sponsored links” on Google and Yahoo to advertise the availability of Tiffany jewelry on e. Bay. • These practices are protected by the doctrine of “nominative fair use, ” pursuant to which “trademark owners cannot prevent others from making a descriptive use of their trademark. ” • The doctrine “is essential because it is undisputed that trademark owners cannot use trademark law to prevent the resale of authentic, trademarked goods. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising targeted to a specific individual based on that person’s web-surfing behavior. With behavioral advertising, this means that two people could see vastly different ads when viewing the identical webpage at the same time.
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising targeted to a specific individual based on that person’s web-surfing behavior. With behavioral advertising, this means that two people could see vastly different ads when viewing the identical webpage at the same time.
 Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising What is contextual advertising? • “Keywords” are pre-identified relevant terms that are used to trigger appropriate “contextual advertising. ” • Keywords can be either generic terms or trademarks (e. g. , “cars” and “insurance”; “Ford” and “GEICO”).
Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising What is contextual advertising? • “Keywords” are pre-identified relevant terms that are used to trigger appropriate “contextual advertising. ” • Keywords can be either generic terms or trademarks (e. g. , “cars” and “insurance”; “Ford” and “GEICO”).
 Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising • Contextual advertising providers, such as adware companies and search engine providers, program their systems to match interested consumers to contextual advertising based on keywords. • Under the contextual advertising model, advertisers bid on “keywords” that an Internet user might enter in a search query. The search engine then matches the advertisement and sponsored hyperlink to the keyword the advertiser purchased. When an Internet user enters the keyword as a search, it triggers the sponsored link to appear on the search results page either to the right or immediately above the natural search results.
Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising • Contextual advertising providers, such as adware companies and search engine providers, program their systems to match interested consumers to contextual advertising based on keywords. • Under the contextual advertising model, advertisers bid on “keywords” that an Internet user might enter in a search query. The search engine then matches the advertisement and sponsored hyperlink to the keyword the advertiser purchased. When an Internet user enters the keyword as a search, it triggers the sponsored link to appear on the search results page either to the right or immediately above the natural search results.
 Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising Advertisers’ Position: The practice should be considered a permissible noncommercial use or fair use of a trademark that places an advertisement in front of a potential purchaser, which is no different from other types of competitive / comparative advertising.
Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising Advertisers’ Position: The practice should be considered a permissible noncommercial use or fair use of a trademark that places an advertisement in front of a potential purchaser, which is no different from other types of competitive / comparative advertising.
 Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising Trademark Owners’ Position: Many trademark owners consider the use of their marks as keywords to constitute infringement or unfair competition that improperly diverts Internet traffic from their sites and confuses consumers about the source of the products they encounter via pop-up ads, banners and sponsored search results. But does the sale of trademarks as keywords to trigger ads represent “use” in commerce, a prerequisite to an infringement cause of action under the Lanham Act?
Pirates and Protocols: Trademark Use and Protection on the Internet Contextual Advertising Trademark Owners’ Position: Many trademark owners consider the use of their marks as keywords to constitute infringement or unfair competition that improperly diverts Internet traffic from their sites and confuses consumers about the source of the products they encounter via pop-up ads, banners and sponsored search results. But does the sale of trademarks as keywords to trigger ads represent “use” in commerce, a prerequisite to an infringement cause of action under the Lanham Act?
 Pirates and Protocols: Trademark Use and Protection on the Internet Statutory Requirements Trademark infringement claims under § 32(1) of the Lanham Act, 15 U. S. C. § 1114(1)2, require that the plaintiff establishes that (1) it has a valid mark that is entitled to protection under the Lanham Act; and that (2) the defendant used the mark, (3) in commerce, (4) ‘in connection with the sale. . . or advertising of goods or services, ’ 15 U. S. C. § 1114(1)(a), (5), without the plaintiff's consent. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Statutory Requirements Trademark infringement claims under § 32(1) of the Lanham Act, 15 U. S. C. § 1114(1)2, require that the plaintiff establishes that (1) it has a valid mark that is entitled to protection under the Lanham Act; and that (2) the defendant used the mark, (3) in commerce, (4) ‘in connection with the sale. . . or advertising of goods or services, ’ 15 U. S. C. § 1114(1)(a), (5), without the plaintiff's consent. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Statutory Requirements The plaintiff must also show that the defendant's use of that mark “is likely to cause confusion. . . as to the affiliation, connection, or association of [the defendant] with [the plaintiff], or as to the origin, sponsorship, or approval of [the defendant's] goods, services, or commercial activities by [the plaintiff]. ” 15 U. S. C. § 1125(a)(1)(A).
Pirates and Protocols: Trademark Use and Protection on the Internet Statutory Requirements The plaintiff must also show that the defendant's use of that mark “is likely to cause confusion. . . as to the affiliation, connection, or association of [the defendant] with [the plaintiff], or as to the origin, sponsorship, or approval of [the defendant's] goods, services, or commercial activities by [the plaintiff]. ” 15 U. S. C. § 1125(a)(1)(A).
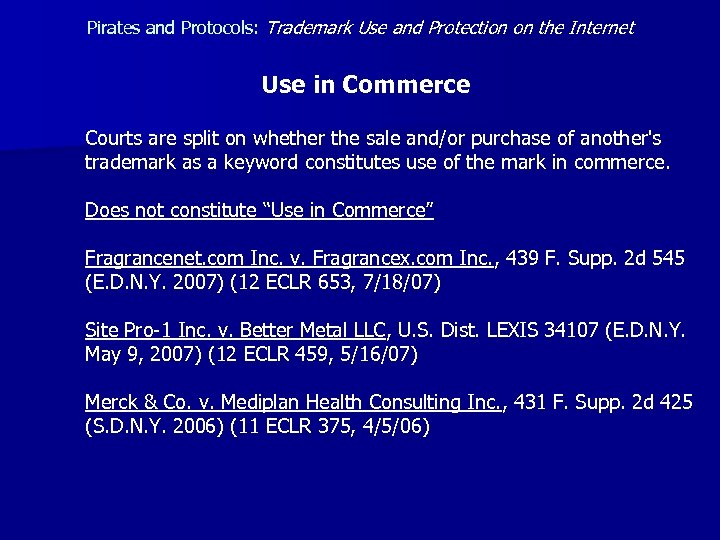 Pirates and Protocols: Trademark Use and Protection on the Internet Use in Commerce Courts are split on whether the sale and/or purchase of another's trademark as a keyword constitutes use of the mark in commerce. Does not constitute “Use in Commerce” Fragrancenet. com Inc. v. Fragrancex. com Inc. , 439 F. Supp. 2 d 545 (E. D. N. Y. 2007) (12 ECLR 653, 7/18/07) Site Pro-1 Inc. v. Better Metal LLC, U. S. Dist. LEXIS 34107 (E. D. N. Y. May 9, 2007) (12 ECLR 459, 5/16/07) Merck & Co. v. Mediplan Health Consulting Inc. , 431 F. Supp. 2 d 425 (S. D. N. Y. 2006) (11 ECLR 375, 4/5/06)
Pirates and Protocols: Trademark Use and Protection on the Internet Use in Commerce Courts are split on whether the sale and/or purchase of another's trademark as a keyword constitutes use of the mark in commerce. Does not constitute “Use in Commerce” Fragrancenet. com Inc. v. Fragrancex. com Inc. , 439 F. Supp. 2 d 545 (E. D. N. Y. 2007) (12 ECLR 653, 7/18/07) Site Pro-1 Inc. v. Better Metal LLC, U. S. Dist. LEXIS 34107 (E. D. N. Y. May 9, 2007) (12 ECLR 459, 5/16/07) Merck & Co. v. Mediplan Health Consulting Inc. , 431 F. Supp. 2 d 425 (S. D. N. Y. 2006) (11 ECLR 375, 4/5/06)
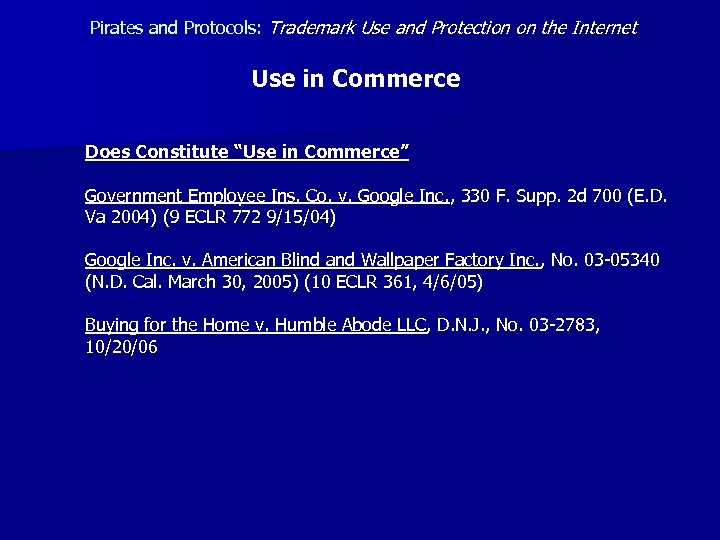 Pirates and Protocols: Trademark Use and Protection on the Internet Use in Commerce Does Constitute “Use in Commerce” Government Employee Ins. Co. v. Google Inc. , 330 F. Supp. 2 d 700 (E. D. Va 2004) (9 ECLR 772 9/15/04) Google Inc. v. American Blind and Wallpaper Factory Inc. , No. 03 -05340 (N. D. Cal. March 30, 2005) (10 ECLR 361, 4/6/05) Buying for the Home v. Humble Abode LLC, D. N. J. , No. 03 -2783, 10/20/06
Pirates and Protocols: Trademark Use and Protection on the Internet Use in Commerce Does Constitute “Use in Commerce” Government Employee Ins. Co. v. Google Inc. , 330 F. Supp. 2 d 700 (E. D. Va 2004) (9 ECLR 772 9/15/04) Google Inc. v. American Blind and Wallpaper Factory Inc. , No. 03 -05340 (N. D. Cal. March 30, 2005) (10 ECLR 361, 4/6/05) Buying for the Home v. Humble Abode LLC, D. N. J. , No. 03 -2783, 10/20/06
 Pirates and Protocols: Trademark Use and Protection on the Internet Initial Interest Confusion In 2004 the Ninth Circuit held - without addressing the "use in commerce" question - that the use of trademarks to trigger the display of banner advertising creates initial interest confusion (Playboy Enter. Inc. v. Netscape Communications Corp. , 354 F. 3 d 1020 (9 th Cir. 2004) (9 ECLR 55 1/21/04) International Profit Associates, Inc. v. Paisola, 461 F. Supp. 2 d 273 (D. N. J. 2006) Edina Realty Inc. v. MLSonline. com, Civ. 04 -4371, 2006, WL 737064 (D. Minn. March 20, 2006) Storus Corp. v. Aroa Marketing Inc. , 2008 WL 449835 (N. D. Cal. Feb. 15, 2008)
Pirates and Protocols: Trademark Use and Protection on the Internet Initial Interest Confusion In 2004 the Ninth Circuit held - without addressing the "use in commerce" question - that the use of trademarks to trigger the display of banner advertising creates initial interest confusion (Playboy Enter. Inc. v. Netscape Communications Corp. , 354 F. 3 d 1020 (9 th Cir. 2004) (9 ECLR 55 1/21/04) International Profit Associates, Inc. v. Paisola, 461 F. Supp. 2 d 273 (D. N. J. 2006) Edina Realty Inc. v. MLSonline. com, Civ. 04 -4371, 2006, WL 737064 (D. Minn. March 20, 2006) Storus Corp. v. Aroa Marketing Inc. , 2008 WL 449835 (N. D. Cal. Feb. 15, 2008)
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • Self-Regulatory Principles For Online Behavioral Advertising (“Principles”) - Federal Trade Commission staff report issues on February 12, 2009. • Online Behavioral Advertising “means the practice of tracking a consumer’s online activities over time – including searches the consumer has conducted, the web pages visited, and the content viewed - in order to deliver advertising targeted to the individual consumer’s interests”
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • Self-Regulatory Principles For Online Behavioral Advertising (“Principles”) - Federal Trade Commission staff report issues on February 12, 2009. • Online Behavioral Advertising “means the practice of tracking a consumer’s online activities over time – including searches the consumer has conducted, the web pages visited, and the content viewed - in order to deliver advertising targeted to the individual consumer’s interests”
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • FTC – First Party Behavioral Advertising “is behavioral advertising by and at a single website, which practice is more likely consistent with consumer expectations, and less likely to lead to harm than other forms of behavioral advertising” • FTC – Contextual Advertising is “advertising based on a consumer’s current visit to a single web page or single search query that involves no retention of data about the consumer’s online activities - beyond that necessary for the immediate delivery of an ad or search result – is likely to be less invasive than other forms of behavioral advertising. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • FTC – First Party Behavioral Advertising “is behavioral advertising by and at a single website, which practice is more likely consistent with consumer expectations, and less likely to lead to harm than other forms of behavioral advertising” • FTC – Contextual Advertising is “advertising based on a consumer’s current visit to a single web page or single search query that involves no retention of data about the consumer’s online activities - beyond that necessary for the immediate delivery of an ad or search result – is likely to be less invasive than other forms of behavioral advertising. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • First Party and Contextual Advertising: • Fall outside the scope of the Principles • Still subject to other laws and policies that impose obligations regarding the collection of data
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • First Party and Contextual Advertising: • Fall outside the scope of the Principles • Still subject to other laws and policies that impose obligations regarding the collection of data
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • FTC – Personally Identifiable Information and Non. Personally Identifiable Information “in context of behavioral advertising, rapidly changing technology and other factors have made the line between personally identifiable and non-personally identifiable information increasingly unclear. ” • The Principles are designed to serve as the basis for industry self regulatory efforts to address privacy concerns regarding the following four (4) aspects of online consumer data collection:
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines • FTC – Personally Identifiable Information and Non. Personally Identifiable Information “in context of behavioral advertising, rapidly changing technology and other factors have made the line between personally identifiable and non-personally identifiable information increasingly unclear. ” • The Principles are designed to serve as the basis for industry self regulatory efforts to address privacy concerns regarding the following four (4) aspects of online consumer data collection:
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines First Aspect: Transparency and Consumer Control • Meaningful disclosure to consumers about the practice of behavioral advertising • Disclosures within a privacy policy/terms of use is no longer considered “best practice” • Disclosure via a prominent link attached to each targeted advertisement served or that is placed on the home page linking to a page describing behavioral advertising practices • A choice to opt out should be easily accessible
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines First Aspect: Transparency and Consumer Control • Meaningful disclosure to consumers about the practice of behavioral advertising • Disclosures within a privacy policy/terms of use is no longer considered “best practice” • Disclosure via a prominent link attached to each targeted advertisement served or that is placed on the home page linking to a page describing behavioral advertising practices • A choice to opt out should be easily accessible
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Second Aspect: Reasonable Security and Limited Data Retention for Consumer Data • Reasonable data security measures so that behavioral data does not fall into the wrong hands • Retain data only as long as necessary for legitimate business or law enforcement needs
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Second Aspect: Reasonable Security and Limited Data Retention for Consumer Data • Reasonable data security measures so that behavioral data does not fall into the wrong hands • Retain data only as long as necessary for legitimate business or law enforcement needs
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Third Aspect: Affirmative Express Consent Before For Material Changes To Existing Privacy Promises • FTC understands that businesses have a legitimate need to change their privacy policies on a prospective basis to engage in new advertising practices • Prospective changes - affirmative express consent is not required when changes only relate to the use of newly collected data in accordance with a changed privacy policy. However, prominent disclosure of the changed privacy policy as well as an easily accessible choice to opt out is expected • Companies are bound by promises made to consumers at the time of data collection regarding how such data is collected, used, and shared
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Third Aspect: Affirmative Express Consent Before For Material Changes To Existing Privacy Promises • FTC understands that businesses have a legitimate need to change their privacy policies on a prospective basis to engage in new advertising practices • Prospective changes - affirmative express consent is not required when changes only relate to the use of newly collected data in accordance with a changed privacy policy. However, prominent disclosure of the changed privacy policy as well as an easily accessible choice to opt out is expected • Companies are bound by promises made to consumers at the time of data collection regarding how such data is collected, used, and shared
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Third Aspect Continued • “Material” refers to uses of behavioral data that are materially different from promises made at the time the data was collected • “Retroactive” and “Material” changes to privacy policies require affirmative express consent • “Affirmative express consent” - pre-checked boxes, disclosures buried in a privacy policy, and other similar mechanisms are not sufficient to constitute affirmative consent. • However, the Principles do not list any specific mechanisms that are sufficient to constitute affirmative consent
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Third Aspect Continued • “Material” refers to uses of behavioral data that are materially different from promises made at the time the data was collected • “Retroactive” and “Material” changes to privacy policies require affirmative express consent • “Affirmative express consent” - pre-checked boxes, disclosures buried in a privacy policy, and other similar mechanisms are not sufficient to constitute affirmative consent. • However, the Principles do not list any specific mechanisms that are sufficient to constitute affirmative consent
 Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Fourth Aspect: Affirmative Express Consent To (Or Prohibition Against) Using Sensitive Data For Behavioral Advertising • “Sensitive Data” – is data such as information about children, medical information, account numbers, sexual orientation, or finances • Note: Certain data may also be subject to obligations under other policies or laws, such as children’s data (COPPA), health data (HIPAA), and financial data (GLB). Source – February 2009 FTC Staff report titled “Self-regulatory Principles For Online Behavioral Advertising”
Pirates and Protocols: Trademark Use and Protection on the Internet Behavioral Advertising Guidelines Fourth Aspect: Affirmative Express Consent To (Or Prohibition Against) Using Sensitive Data For Behavioral Advertising • “Sensitive Data” – is data such as information about children, medical information, account numbers, sexual orientation, or finances • Note: Certain data may also be subject to obligations under other policies or laws, such as children’s data (COPPA), health data (HIPAA), and financial data (GLB). Source – February 2009 FTC Staff report titled “Self-regulatory Principles For Online Behavioral Advertising”
 Pirates and Protocols: Trademark Use and Protection on the Internet IAB Advertising Addendum • IAB's Board of Directors Adopts Privacy Guidelines for Interactive Advertising • Applicable to Internet media companies, ad serving organizations and rich media vendors • Meant to be an addendum to the existing IAB standard terms and conditions
Pirates and Protocols: Trademark Use and Protection on the Internet IAB Advertising Addendum • IAB's Board of Directors Adopts Privacy Guidelines for Interactive Advertising • Applicable to Internet media companies, ad serving organizations and rich media vendors • Meant to be an addendum to the existing IAB standard terms and conditions
 Pirates and Protocols: Trademark Use and Protection on the Internet Case Law Round-up
Pirates and Protocols: Trademark Use and Protection on the Internet Case Law Round-up
 Pirates and Protocols: Trademark Use and Protection on the Internet ISP “Secondary Liability” § ISPs can be contributorily liable for trademark infringement – Factors: § Defendant intentionally induced the infringement; or either § Defendant continued to supply an infringing product to a third party after learning that the product was infringing; OR § For on-line services, that defendant had knowledge of and direct control over the infringing activity.
Pirates and Protocols: Trademark Use and Protection on the Internet ISP “Secondary Liability” § ISPs can be contributorily liable for trademark infringement – Factors: § Defendant intentionally induced the infringement; or either § Defendant continued to supply an infringing product to a third party after learning that the product was infringing; OR § For on-line services, that defendant had knowledge of and direct control over the infringing activity.
 Pirates and Protocols: Trademark Use and Protection on the Internet ISPs can be vicariously liable for trademark infringement § To establish vicarious liability, defendant and infringer must have either: § – a partnership, or authority to bind one another; or – otherwise exercise joint ownership or control over the infringing product.
Pirates and Protocols: Trademark Use and Protection on the Internet ISPs can be vicariously liable for trademark infringement § To establish vicarious liability, defendant and infringer must have either: § – a partnership, or authority to bind one another; or – otherwise exercise joint ownership or control over the infringing product.
 Pirates and Protocols: Trademark Use and Protection on the Internet § Contributory and Vicarious Liability claims have generally failed against: – Credit card companies. see e. g. , Perfect 10, Inc. v. Visa Int’l Serv. Ass’n, 2004 WL 1773349 (N. D. Cal. Aug. 5, 2004); – Search engines, see, e. g. , Newborn v. Yahoo, Inc. , 391 F. Supp. 2 d 181 (D. D. C. 2005); and – Domain name registrars, see, e. g. , Lockheed Martin Corp. v. Network Solutions, Inc. , 194 F. 3 d 980 (9 th Cir. 1999).
Pirates and Protocols: Trademark Use and Protection on the Internet § Contributory and Vicarious Liability claims have generally failed against: – Credit card companies. see e. g. , Perfect 10, Inc. v. Visa Int’l Serv. Ass’n, 2004 WL 1773349 (N. D. Cal. Aug. 5, 2004); – Search engines, see, e. g. , Newborn v. Yahoo, Inc. , 391 F. Supp. 2 d 181 (D. D. C. 2005); and – Domain name registrars, see, e. g. , Lockheed Martin Corp. v. Network Solutions, Inc. , 194 F. 3 d 980 (9 th Cir. 1999).
 Pirates and Protocols: Trademark Use and Protection on the Internet § Secondary liability claims have succeeded against ISPs on basis that ISPs are analogous to brick-and-mortar “landlords” who are aware of, and benefit from, the infringer’s legal activities – See, e. g. , Gucci Am. V. Hall & Assocs. , 135 F. Supp. 2 d 409 (S. D. N. Y. 2001)
Pirates and Protocols: Trademark Use and Protection on the Internet § Secondary liability claims have succeeded against ISPs on basis that ISPs are analogous to brick-and-mortar “landlords” who are aware of, and benefit from, the infringer’s legal activities – See, e. g. , Gucci Am. V. Hall & Assocs. , 135 F. Supp. 2 d 409 (S. D. N. Y. 2001)
 Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Louis Vuitton Malletier SA v. Akanoc Solutions, Inc. , 591 F. Supp. 2 d 1098 (ND Cal. Dec. 23, 2008) (claims of ISP contributory and vicarious liability survive motion for SJ) – Heartland Beef Inc. v. Lobel’s of New York LLC, (S. D. Tex. Feb. 5, 2009) 2009 WL 311087 (Yahoo not liable under LA for causing sponsored link to trigger based on user-inputted term) – Voyageurs du Monde, Terres d’Aventure v. Google, (TGI Paris, Jan. 7, 2009) (Google liable for failing to establish means to verify advertisers had right to use ad words and failing to make clear that ad words were advertisements)
Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Louis Vuitton Malletier SA v. Akanoc Solutions, Inc. , 591 F. Supp. 2 d 1098 (ND Cal. Dec. 23, 2008) (claims of ISP contributory and vicarious liability survive motion for SJ) – Heartland Beef Inc. v. Lobel’s of New York LLC, (S. D. Tex. Feb. 5, 2009) 2009 WL 311087 (Yahoo not liable under LA for causing sponsored link to trigger based on user-inputted term) – Voyageurs du Monde, Terres d’Aventure v. Google, (TGI Paris, Jan. 7, 2009) (Google liable for failing to establish means to verify advertisers had right to use ad words and failing to make clear that ad words were advertisements)
 Pirates and Protocols: Trademark Use and Protection on the Internet Using Marks on or in Web Pages § Risk of Liability arises from unauthorized use of other’s trademarks on: § Web Pages § Hyperlinks § Metatags § Liability can arise from “initial interest confusion. ”
Pirates and Protocols: Trademark Use and Protection on the Internet Using Marks on or in Web Pages § Risk of Liability arises from unauthorized use of other’s trademarks on: § Web Pages § Hyperlinks § Metatags § Liability can arise from “initial interest confusion. ”
 Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Baby. Age. com Inc. v. Leachco Inc. , 2009 WL 82552 (M. D. Pa. Jan. 12, 2009) (on-line company may be liable for providing links to its products on web page despite listing other company as “featured brand”) – Indiaweekly. com LLC v. Nehaflix. com Inc. , 2009 WL 189867 (D. Conn. Jan. 27, 2009) (on-line use of competitor’s tm on web site in order to appear in search engine hits states actionable claim under LA)
Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Baby. Age. com Inc. v. Leachco Inc. , 2009 WL 82552 (M. D. Pa. Jan. 12, 2009) (on-line company may be liable for providing links to its products on web page despite listing other company as “featured brand”) – Indiaweekly. com LLC v. Nehaflix. com Inc. , 2009 WL 189867 (D. Conn. Jan. 27, 2009) (on-line use of competitor’s tm on web site in order to appear in search engine hits states actionable claim under LA)
 Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases (cont. ) – Market America v. Optihealth Products, Inc. , 2008 WL 5069802 (M. D. N. C. Nov. 21, 2008) (use of competitor’s tm in metatags and as trigger for sponsored links constituted “use in commerce” under LA) – Suarez Corp. Indus. V. Earthwise Technologies, Inc. , 2008 WL 4934055 (W. D. Wash. Nov. 14, 2008) (use of competitor’s tm in domain names and metatags likely caused confusion, despite disclaimer)
Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases (cont. ) – Market America v. Optihealth Products, Inc. , 2008 WL 5069802 (M. D. N. C. Nov. 21, 2008) (use of competitor’s tm in metatags and as trigger for sponsored links constituted “use in commerce” under LA) – Suarez Corp. Indus. V. Earthwise Technologies, Inc. , 2008 WL 4934055 (W. D. Wash. Nov. 14, 2008) (use of competitor’s tm in domain names and metatags likely caused confusion, despite disclaimer)
 Pirates and Protocols: Trademark Use and Protection on the Internet Domain Names § Domain Names can be: – Hijacked, see 15 U. S. C. Sec 1125(d) (requires bad faith) – Reverse Hijacked, see 15 U. S. C. sec. 1114(2)(D)(v) (mark must be suspended, disabled or transferred) – Tasted – Kited
Pirates and Protocols: Trademark Use and Protection on the Internet Domain Names § Domain Names can be: – Hijacked, see 15 U. S. C. Sec 1125(d) (requires bad faith) – Reverse Hijacked, see 15 U. S. C. sec. 1114(2)(D)(v) (mark must be suspended, disabled or transferred) – Tasted – Kited
 Pirates and Protocols: Trademark Use and Protection on the Internet § Representative Domain Tasting Cases: – Neiman Marcus Group, Inc. v. Dotster, Inc. , C 06 -5292 RBL (W. D. Wash. May 30, 2006) – Neiman Marcus Group, Inc. v. Name. com, LLC, 07 -CV-00525 -WYD-BNB (D. Co. March 15, 2007) – Dell, Inc. v. Belgium. Domains, LLC, No. 0722764 (S. D. Fla. Nov. 2, 2007) (PI granted Nov. 20, 2007)
Pirates and Protocols: Trademark Use and Protection on the Internet § Representative Domain Tasting Cases: – Neiman Marcus Group, Inc. v. Dotster, Inc. , C 06 -5292 RBL (W. D. Wash. May 30, 2006) – Neiman Marcus Group, Inc. v. Name. com, LLC, 07 -CV-00525 -WYD-BNB (D. Co. March 15, 2007) – Dell, Inc. v. Belgium. Domains, LLC, No. 0722764 (S. D. Fla. Nov. 2, 2007) (PI granted Nov. 20, 2007)
 Pirates and Protocols: Trademark Use and Protection on the Internet § § Are domain names contract rights or property rights? If property, where are domain names located for jurisdictional purposes? Can domain names be seized or forfeited? See Kentucky v. 141 Domain Names, 08 -CI -1409 (Ky Cir. Court, Oct. 16, 2008), rev’d No. 2008 -CA-002000 -OA (Ky. Ct. App. Jan 20, 2009).
Pirates and Protocols: Trademark Use and Protection on the Internet § § Are domain names contract rights or property rights? If property, where are domain names located for jurisdictional purposes? Can domain names be seized or forfeited? See Kentucky v. 141 Domain Names, 08 -CI -1409 (Ky Cir. Court, Oct. 16, 2008), rev’d No. 2008 -CA-002000 -OA (Ky. Ct. App. Jan 20, 2009).
 Pirates and Protocols: Trademark Use and Protection on the Internet Personal Jurisdiction n When does a web page create minimum contacts with a particular state? – Passive vs. Interactive Websites: a sliding scale – Interactively, however, may be insufficient: still need “purposeful availment” – Also, economic harm to in-state plaintiff may satisfy state long-arm statutes.
Pirates and Protocols: Trademark Use and Protection on the Internet Personal Jurisdiction n When does a web page create minimum contacts with a particular state? – Passive vs. Interactive Websites: a sliding scale – Interactively, however, may be insufficient: still need “purposeful availment” – Also, economic harm to in-state plaintiff may satisfy state long-arm statutes.
 Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Portfolio Solutions LLC v. ETF Portfolio Solutions, Inc. , 2009 WL 111908 (E. D. Mich. Jan. 15, 2009) (web site was basis for jurisdiction under federal and Michigan law) – Chanel, Inc. v. Guetae, 2009 WL 348501(D. N. J. Feb. 11, 2009) (“highly interactive” web site insufficient basis for jurisdiction absent purposeful availment)
Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases: – Portfolio Solutions LLC v. ETF Portfolio Solutions, Inc. , 2009 WL 111908 (E. D. Mich. Jan. 15, 2009) (web site was basis for jurisdiction under federal and Michigan law) – Chanel, Inc. v. Guetae, 2009 WL 348501(D. N. J. Feb. 11, 2009) (“highly interactive” web site insufficient basis for jurisdiction absent purposeful availment)
 Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases (cont. ) – Kruska v. Perverted Justice Foundations, Inc. , 2009 WL 577708 (D. Ariz. Feb. 2, 2009) (registration of domain name in AZ and location of server in AZ insufficient to establish personal jurisdiction over defendant) – Family Watchdog LLC v. Schweiss, 2009 WL 276856 (S. D. Ind. Feb. 5, 2009) (interactivity of web site insufficient by itself: there needs to be nexus between website and cause of action)
Pirates and Protocols: Trademark Use and Protection on the Internet § Recent Cases (cont. ) – Kruska v. Perverted Justice Foundations, Inc. , 2009 WL 577708 (D. Ariz. Feb. 2, 2009) (registration of domain name in AZ and location of server in AZ insufficient to establish personal jurisdiction over defendant) – Family Watchdog LLC v. Schweiss, 2009 WL 276856 (S. D. Ind. Feb. 5, 2009) (interactivity of web site insufficient by itself: there needs to be nexus between website and cause of action)
 Pirates and Protocols: Trademark Use and Protection on the Internet Virtual Trademarks: The Fight over SLART § The Lanham Act protects trademarks created and used in virtual worlds against real and virtual infringement. § Minsky v. Linden Research (N. D. N. Y. 2008) § What about protecting real world trademarks in virtual worlds?
Pirates and Protocols: Trademark Use and Protection on the Internet Virtual Trademarks: The Fight over SLART § The Lanham Act protects trademarks created and used in virtual worlds against real and virtual infringement. § Minsky v. Linden Research (N. D. N. Y. 2008) § What about protecting real world trademarks in virtual worlds?
 Pirates and Protocols: Trademark Use and Protection on the Internet Thank you to our speakers: Mark Fiore Mark. Fiore@weil. com Heather Greenberg HGreenberg@topps. com Jonathan Sirota jsirota@hearst. com Mitchell Stein mstein@sandw. com Kevin Taylor kevin. taylor@globaltechlaw. com Erik Walsh Erik_Walsh@aporter. com
Pirates and Protocols: Trademark Use and Protection on the Internet Thank you to our speakers: Mark Fiore Mark. Fiore@weil. com Heather Greenberg HGreenberg@topps. com Jonathan Sirota jsirota@hearst. com Mitchell Stein mstein@sandw. com Kevin Taylor kevin. taylor@globaltechlaw. com Erik Walsh Erik_Walsh@aporter. com


