06e4aa7fb2146543452637829cba56f3.ppt
- Количество слайдов: 13

PHISHING A Melbourne Athenaeum Library Cybersafety Information Guide Image source: http: //3 foldx. com/worriers-guide-to-identifying-phishing-e-mails

What is phishing? Phishing is the fraudulent practice of contacting people online, purporting to be from reputable companies, to induce individuals to reveal personal information, such as passwords and credit card numbers. Phishing is carried out with one goal in mind – identity theft. Providing your personal information online can lead to identity theft, draining of bank accounts or being signed up to programs without your consent.

Being vigilant • Phishing works because it is sent to large numbers of internet users. Studies suggest that even the least successful scams have approximately a 3% success rate. • To give you an idea of the numbers involved a moderate sized scam, sent to the equivalent of every email account in Australia, would have a success rate greater than the populations of Geelong and Canberra combined. • You could be targeted anywhere (or anytime) you’re using or connected to the internet – including when you’re using a computer, laptop, i. Pad or smartphone. • Vigilance against phishing is an important part of staying safe online. Rather than following links that are sent to you, it is best to use a search engine to find the official website for the organisation. • Phishing can seem relatively innocent, or inconsequential, or even appear to be a request for charity or aid. Make sure you verify the details of any unsolicited online contact using an independent source before donating money or otherwise interacting with them. Image source: https: //pixabay. com/en/internet-computer-screen-monitor-1593384
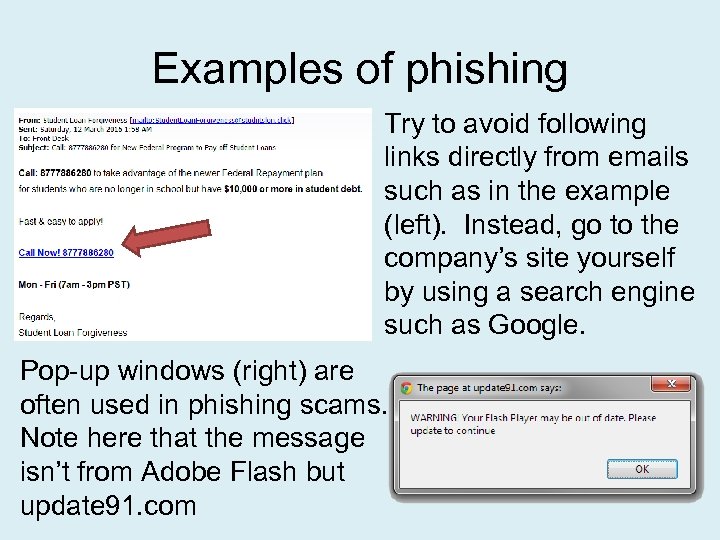
Examples of phishing Try to avoid following links directly from emails such as in the example (left). Instead, go to the company’s site yourself by using a search engine such as Google. Pop-up windows (right) are often used in phishing scams. Note here that the message isn’t from Adobe Flash but update 91. com
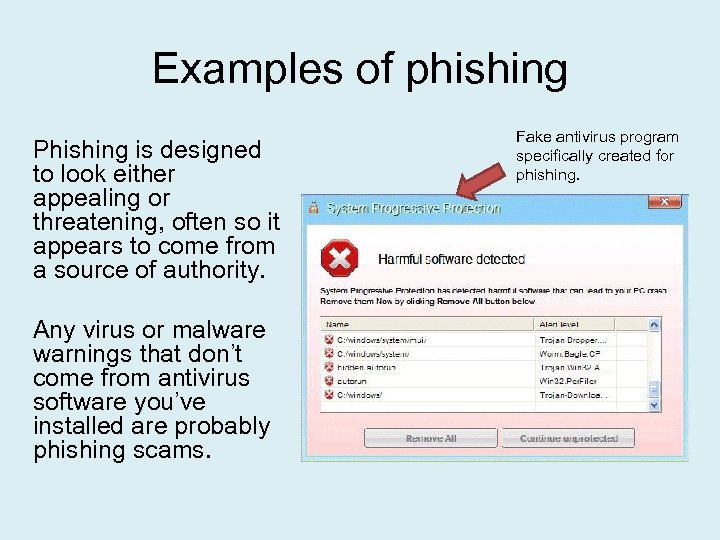
Examples of phishing Phishing is designed to look either appealing or threatening, often so it appears to come from a source of authority. Any virus or malware warnings that don’t come from antivirus software you’ve installed are probably phishing scams. Fake antivirus program specifically created for phishing.
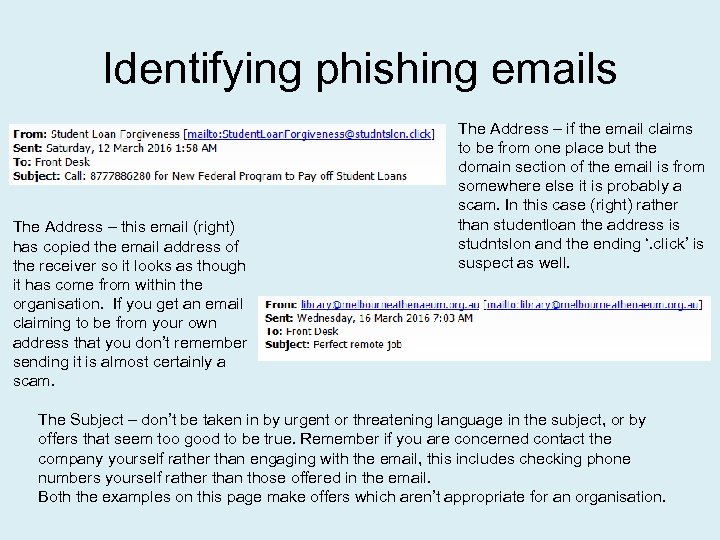
Identifying phishing emails The Address – this email (right) has copied the email address of the receiver so it looks as though it has come from within the organisation. If you get an email claiming to be from your own address that you don’t remember sending it is almost certainly a scam. The Address – if the email claims to be from one place but the domain section of the email is from somewhere else it is probably a scam. In this case (right) rather than studentloan the address is studntslon and the ending ‘. click’ is suspect as well. The Subject – don’t be taken in by urgent or threatening language in the subject, or by offers that seem too good to be true. Remember if you are concerned contact the company yourself rather than engaging with the email, this includes checking phone numbers yourself rather than those offered in the email. Both the examples on this page make offers which aren’t appropriate for an organisation.
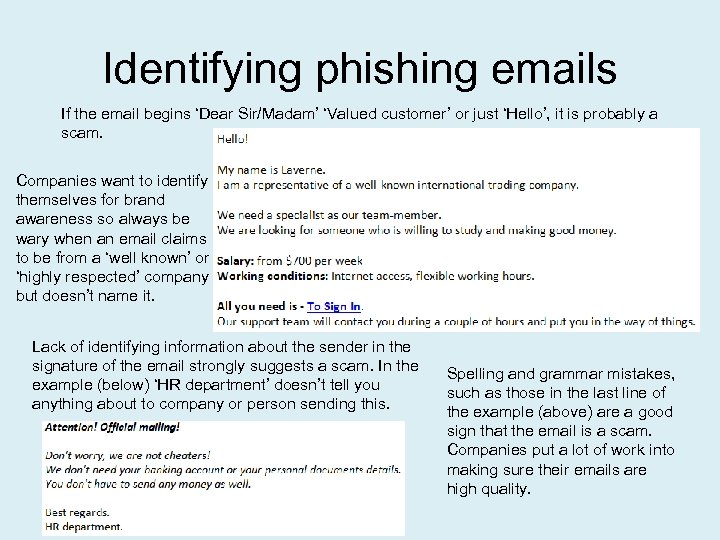
Identifying phishing emails If the email begins ‘Dear Sir/Madam’ ‘Valued customer’ or just ‘Hello’, it is probably a scam. Companies want to identify themselves for brand awareness so always be wary when an email claims to be from a ‘well known’ or ‘highly respected’ company but doesn’t name it. Lack of identifying information about the sender in the signature of the email strongly suggests a scam. In the example (below) ‘HR department’ doesn’t tell you anything about to company or person sending this. Spelling and grammar mistakes, such as those in the last line of the example (above) are a good sign that the email is a scam. Companies put a lot of work into making sure their emails are high quality.
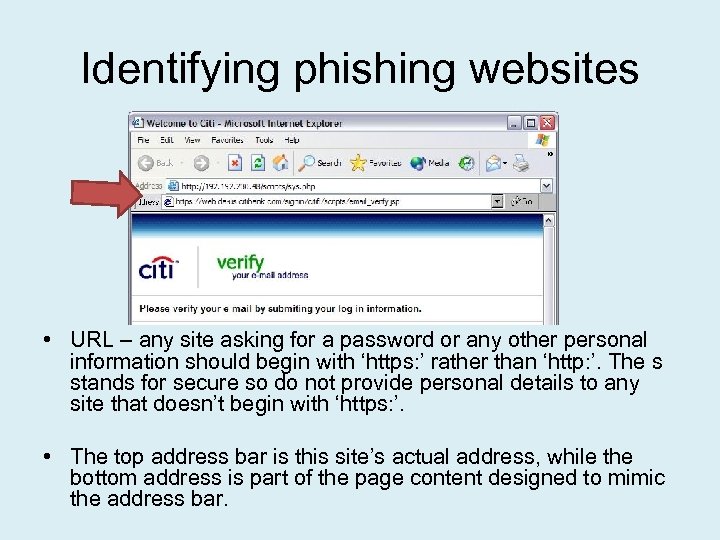
Identifying phishing websites • URL – any site asking for a password or any other personal information should begin with ‘https: ’ rather than ‘http: ’. The s stands for secure so do not provide personal details to any site that doesn’t begin with ‘https: ’. • The top address bar is this site’s actual address, while the bottom address is part of the page content designed to mimic the address bar.
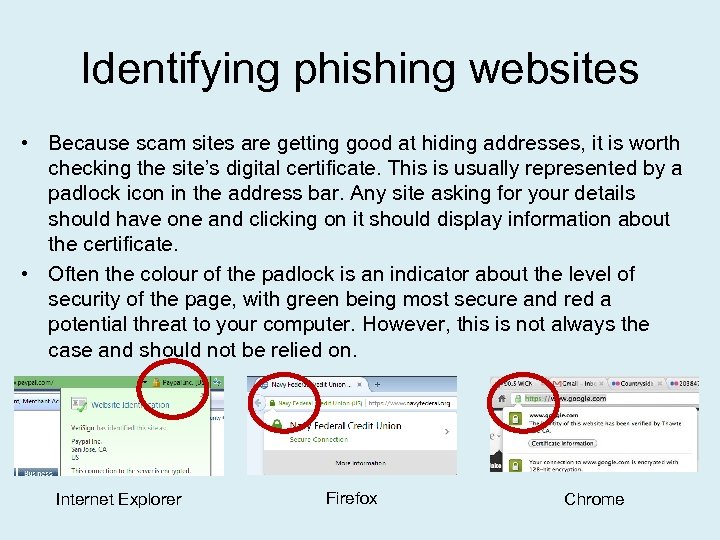
Identifying phishing websites • Because scam sites are getting good at hiding addresses, it is worth checking the site’s digital certificate. This is usually represented by a padlock icon in the address bar. Any site asking for your details should have one and clicking on it should display information about the certificate. • Often the colour of the padlock is an indicator about the level of security of the page, with green being most secure and red a potential threat to your computer. However, this is not always the case and should not be relied on. Internet Explorer Firefox Chrome
Identifying phishing websites • If the company name is misspelled or not included in the url this is probably not a legitimate site. A common trick is substitution (eg. replacing the letter ‘l’ with the numeral ‘ 1’). • Be wary of any site that immediately opens a pop-up window asking for login details. Sometimes phishing attempts direct you to a legitimate site but use a pop-up to get your account information. • If you are still unsure whether a site or email is a scam, check the Australian government website dedicated to finding and notifying people about them: https: //www. scamwatch. gov. au/

SMi. Shing Phishing can target any device connected to the internet. One form which is becoming increasingly common is smishing or SMi. Shing. This stands for SMS phishing. These attacks target smartphones rather than emails or websites and trick users into downloading malware onto their mobile device. Remember to be aware of this when downloading apps or opening attachments to messages on your phone. Image source: https: //pixabay. com/en/phone-scams-fraud-dishonest-crime-449836
What action to take If you or someone you know has been the victim of a scam: • Stop sending money. • Contact your bank and any organisation which is compromised. • Change your passwords, even ones which you don’t think have been compromised. • Recover your identity. • Report the scam to the authorities: Police, Scamwatch, etc. • Alert other people to the scam. • If needed, contact a support or counselling service. • Beware of being targeted with follow-up scams.

Thank you for taking the time to read this guide. If you have any further queries please don’t hesitate to ask library staff. Licensed under a Creative Commons Attribution-Non. Commercial-Share. Alike 4. 0 International License.
06e4aa7fb2146543452637829cba56f3.ppt