 Phases of Hackers
Phases of Hackers
 Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
 Module Insights Identify how hackers behave in realworld when they chaise targets and gain access.
Module Insights Identify how hackers behave in realworld when they chaise targets and gain access.
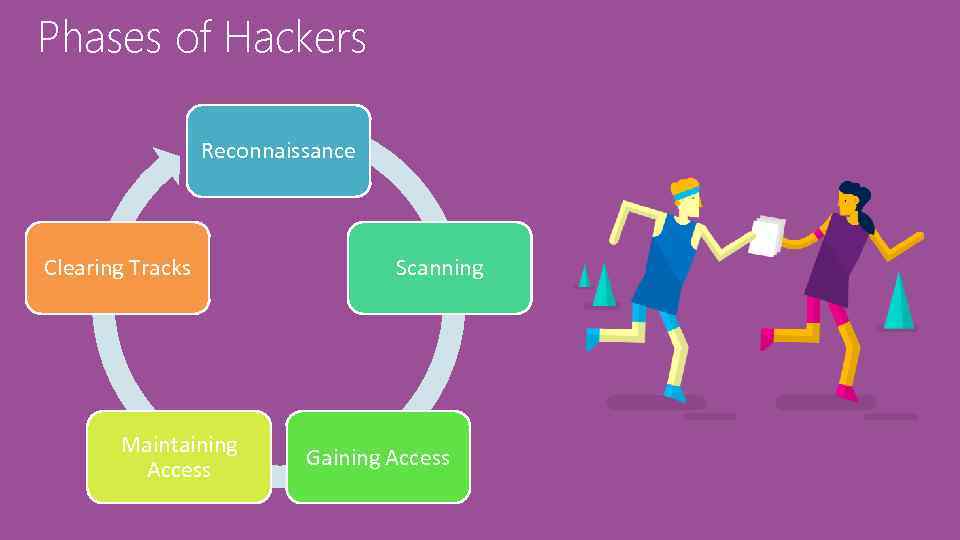 Phases of Hackers Reconnaissance Clearing Tracks Maintaining Access Scanning Gaining Access
Phases of Hackers Reconnaissance Clearing Tracks Maintaining Access Scanning Gaining Access
 Reconnaissance Refers to phase where attacker gathers as much information as possible. Learn About Target: 1) Active Recon 2) Passive Recon
Reconnaissance Refers to phase where attacker gathers as much information as possible. Learn About Target: 1) Active Recon 2) Passive Recon
 DEMO Gaining fast personal information's
DEMO Gaining fast personal information's
 Scanning Types Port Scanning Vulnerability Scanning Network Scanning
Scanning Types Port Scanning Vulnerability Scanning Network Scanning
 DEMO How do they find us?
DEMO How do they find us?
 Gaining Access The Key Point of hacking: • This phase of the attack occurs when the hacker moves from simply probing the network to actually attacking it. • After the hacker has gained access, he can begin to move from system to system, spreading his damage as he progresses. • Comes down to his skill level, amount of access he achieves, network architecture, and configuration of the victim's network.
Gaining Access The Key Point of hacking: • This phase of the attack occurs when the hacker moves from simply probing the network to actually attacking it. • After the hacker has gained access, he can begin to move from system to system, spreading his damage as he progresses. • Comes down to his skill level, amount of access he achieves, network architecture, and configuration of the victim's network.
 DEMO How do they gain access?
DEMO How do they gain access?
 Maintaining Access • Refers to the phase when attacker tries to retain ownership of the system • The attacker may compromise the system • This where Backdoors, Root. Kits or Trojans prevents your systems • An Attacker can upload, download or manipulate data, applications & configurations of your systems
Maintaining Access • Refers to the phase when attacker tries to retain ownership of the system • The attacker may compromise the system • This where Backdoors, Root. Kits or Trojans prevents your systems • An Attacker can upload, download or manipulate data, applications & configurations of your systems
 Clearing Tracks • Refer to activates carried out by an attacker to hide the misdeeds • Reasons Inc. the need for prolonged stay, continued use of resource, remove evidence of hacking
Clearing Tracks • Refer to activates carried out by an attacker to hide the misdeeds • Reasons Inc. the need for prolonged stay, continued use of resource, remove evidence of hacking
 Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
 Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
 © 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
© 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.