23030e8f6427d5affb7b67f2f37ddfa8.ppt
- Количество слайдов: 14
 Perceptions of Wi-Fi Security Requirements: A Stratified View Merrill Warkentin Xin (“Robert”) Luo Mississippi State University
Perceptions of Wi-Fi Security Requirements: A Stratified View Merrill Warkentin Xin (“Robert”) Luo Mississippi State University
 Overview Growth in Access Points – the problem Existing and emerging protocols Security threats Perception of Wi-Fi security threats Research plan Discussion
Overview Growth in Access Points – the problem Existing and emerging protocols Security threats Perception of Wi-Fi security threats Research plan Discussion
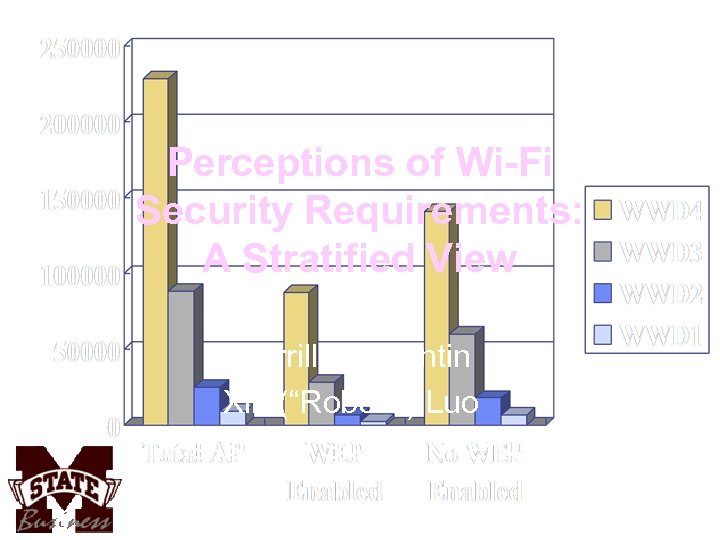
 Access Points Found 1 = Sept 2002 4 = June 2004 Total AP found in WWD 4: 228, 537 (Worldwide
Access Points Found 1 = Sept 2002 4 = June 2004 Total AP found in WWD 4: 228, 537 (Worldwide
 Existing & Emerging Protocols 802. 11, 802. 11 a, 802. 11 b, 802. 11 g n n n Four standards for Wireless LANs Ranging from 1 M to 54 M bit/sec. EAP – Extensible Authentication Protocol 802. 11 e n Qo. S (quality of service) 802. 11 h n Power usage and transmission power 802. 11 n n Improve the bandwidth 802. 11 f n inter access point 802. 11 s n Mesh networking 802. 11 r n fast roaming
Existing & Emerging Protocols 802. 11, 802. 11 a, 802. 11 b, 802. 11 g n n n Four standards for Wireless LANs Ranging from 1 M to 54 M bit/sec. EAP – Extensible Authentication Protocol 802. 11 e n Qo. S (quality of service) 802. 11 h n Power usage and transmission power 802. 11 n n Improve the bandwidth 802. 11 f n inter access point 802. 11 s n Mesh networking 802. 11 r n fast roaming
 Security Protocols: WEP and WPA WEP n n relies on unchanging, shared encryption keys addresses confidentiality instead of authentication WPA (early version of the 802. 11 i) n n n includes Temporal Key Integrity Protocol (TKIP) and 802. 1 x mechanisms provide dynamic key encryption and mutual authentication poorly chosen short human-readable passphrases can be cracked with a robust dictionary attack offline and without access to the network.
Security Protocols: WEP and WPA WEP n n relies on unchanging, shared encryption keys addresses confidentiality instead of authentication WPA (early version of the 802. 11 i) n n n includes Temporal Key Integrity Protocol (TKIP) and 802. 1 x mechanisms provide dynamic key encryption and mutual authentication poorly chosen short human-readable passphrases can be cracked with a robust dictionary attack offline and without access to the network.
 Interoperable Protocols Interoperability problem n Cisco’s proprietary version of 801. 1 x authentication--the Lightweight EAP (LEAP) w doesn’t function with a variety of hardware clients n Protected EAP (PEAP) w combining an administrator-specified authentication and confidentiality protocol with EAP Adoption problem n most organizations reluctant to embrace standards that have yet to be standardized
Interoperable Protocols Interoperability problem n Cisco’s proprietary version of 801. 1 x authentication--the Lightweight EAP (LEAP) w doesn’t function with a variety of hardware clients n Protected EAP (PEAP) w combining an administrator-specified authentication and confidentiality protocol with EAP Adoption problem n most organizations reluctant to embrace standards that have yet to be standardized
 Security Threats Viruses and Trojans Eavesdropping Man-in-the-middle attacks Denial of Service attacks
Security Threats Viruses and Trojans Eavesdropping Man-in-the-middle attacks Denial of Service attacks
 Top Seven 802. 11 Security Problems 1. 2. 3. 4. 5. 6. 7. Easy Access Rogue Access Points Unauthorized Use of Service/Performance Constraints MAC Spoofing, Session Highjacking Traffic Analysis and Eavesdropping Higher Level Attacks Source: Bitpipe
Top Seven 802. 11 Security Problems 1. 2. 3. 4. 5. 6. 7. Easy Access Rogue Access Points Unauthorized Use of Service/Performance Constraints MAC Spoofing, Session Highjacking Traffic Analysis and Eavesdropping Higher Level Attacks Source: Bitpipe
 IEEE 802. 11 i Security Protocol ratified in June 2004 WPA 2 with Advanced Encryption Standard (AES) address all known WEP deficiencies via a new mode called CCM provide confidentiality and integrity bring stronger encryption reduce key management overhead minimize the time spent computing key schedules (Cam-Winget, 2003)
IEEE 802. 11 i Security Protocol ratified in June 2004 WPA 2 with Advanced Encryption Standard (AES) address all known WEP deficiencies via a new mode called CCM provide confidentiality and integrity bring stronger encryption reduce key management overhead minimize the time spent computing key schedules (Cam-Winget, 2003)
 Wi-Max broadband wireless connections over long distances used for n n n "last mile" broadband connections hotspot and cellular backhaul high-speed enterprise connectivity based on IEEE 802. 16 standard provides metropolitan area network connectivity at speeds of up to 75 Mb/sec can transmit signals as far as 30 miles (average = 3 -5 miles) Source: Intel
Wi-Max broadband wireless connections over long distances used for n n n "last mile" broadband connections hotspot and cellular backhaul high-speed enterprise connectivity based on IEEE 802. 16 standard provides metropolitan area network connectivity at speeds of up to 75 Mb/sec can transmit signals as far as 30 miles (average = 3 -5 miles) Source: Intel
 Stakeholder Groups executive-level (top) management IT Directors (CIO, CSO, Netword Admins) staff, end users other stakeholders? (external) Research Question: “Do they have the same perceptions of Wi-Fi security? ”
Stakeholder Groups executive-level (top) management IT Directors (CIO, CSO, Netword Admins) staff, end users other stakeholders? (external) Research Question: “Do they have the same perceptions of Wi-Fi security? ”
 Perceptions of Wi-Fi Security Is it safe? Who can read? How to use? Each stakeholder group has influences. Who views as secure? How does this influence actions?
Perceptions of Wi-Fi Security Is it safe? Who can read? How to use? Each stakeholder group has influences. Who views as secure? How does this influence actions?
 Research Plan investigate similarities and dissimilarities in terms of perception of wireless security issues among stakeholder groups discuss implications of any differences research methodology n n lit review, develop research hypotheses survey – pilot study (at MSU) w deans, directors, IT directors, faculty, staff, students n survey – hospitals, hotels, cafes, etc.
Research Plan investigate similarities and dissimilarities in terms of perception of wireless security issues among stakeholder groups discuss implications of any differences research methodology n n lit review, develop research hypotheses survey – pilot study (at MSU) w deans, directors, IT directors, faculty, staff, students n survey – hospitals, hotels, cafes, etc.
 Stakeholder Discussion
Stakeholder Discussion


