538cf97a4c54b87a5b20acef582a999a.ppt
- Количество слайдов: 110

Peer-to-Peer Networking and Networked Virtual Environments By Jehn-Ruey Jiang CSIE Department National Central University

P 2 P Networking
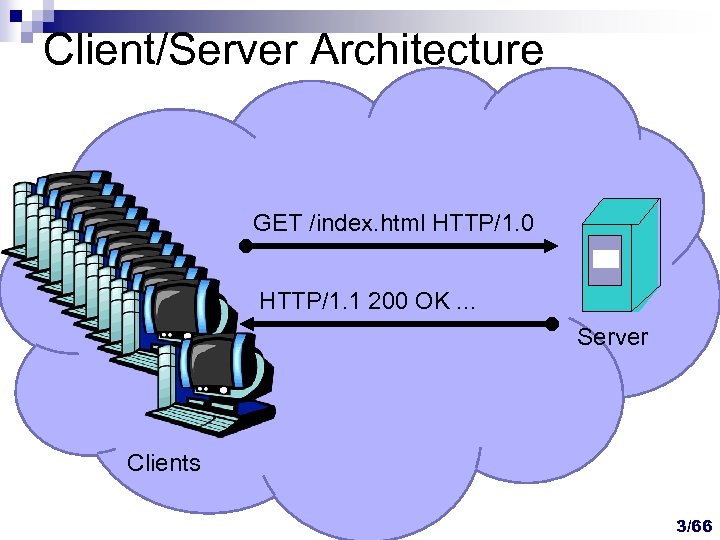
Client/Server Architecture GET /index. html HTTP/1. 0 HTTP/1. 1 200 OK. . . Server Clients 3/66

The Client Side Today’s clients can perform more roles than just forwarding users requests n Today’s clients have: n ¨ more computing power ¨ more storage space n Thin client Fat client 4/66
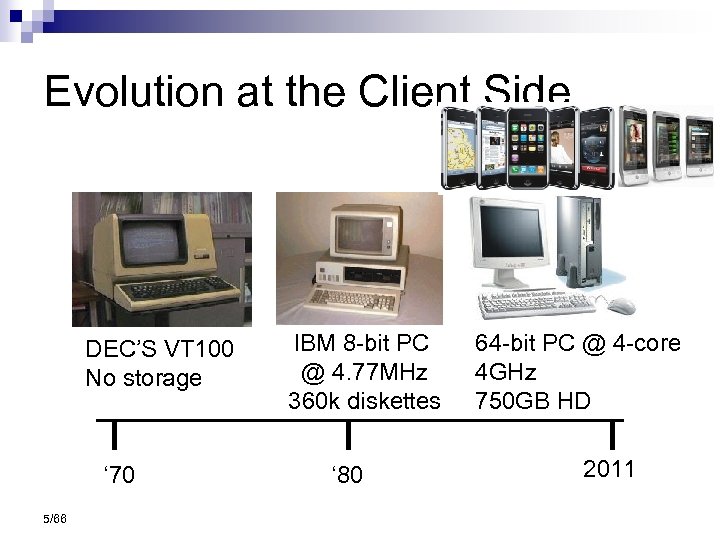
Evolution at the Client Side DEC’S VT 100 No storage ‘ 70 5/66 IBM 8 -bit PC @ 4. 77 MHz 360 k diskettes ‘ 80 64 -bit PC @ 4 -core 4 GHz 750 GB HD 2011

What Else Has Changed? n The number of home PCs is increasing rapidly Most of the PCs are “fat clients” As the Internet usage grow, more and more PCs are connecting to the global net Most of the time PCs are idle n How can we use all this? n n n Peer-to-Peer (P 2 P) 6/66
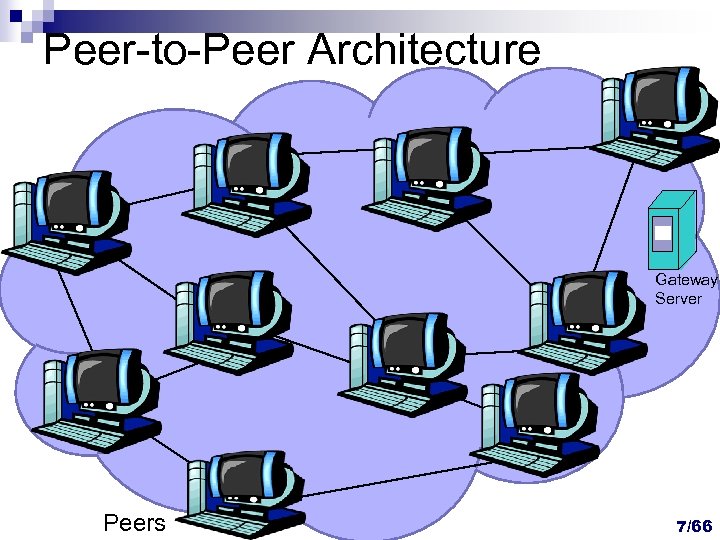
Peer-to-Peer Architecture Gateway Server Peers 7/66
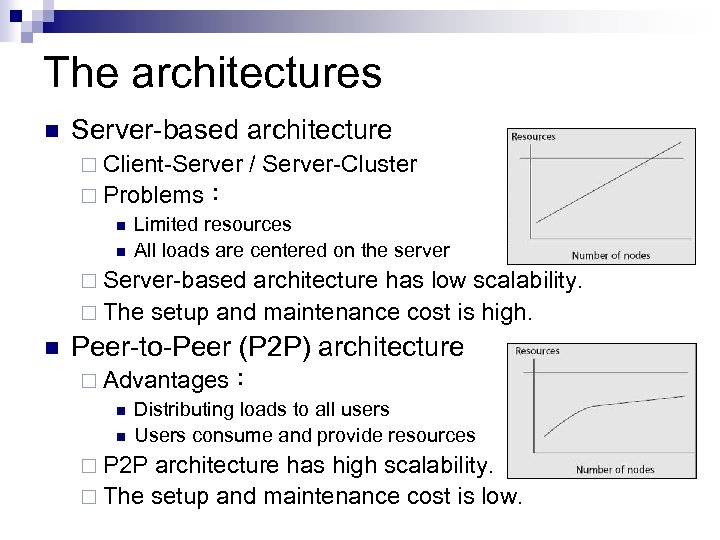
The architectures n Server-based architecture ¨ Client-Server / Server-Cluster ¨ Problems: n Limited resources n All loads are centered on the server ¨ Server-based architecture has low scalability. ¨ The setup and maintenance cost is high. n Peer-to-Peer (P 2 P) architecture ¨ Advantages: n Distributing loads to all users n Users consume and provide resources ¨ P 2 P architecture has high scalability. ¨ The setup and maintenance cost is low.

What is peer-to-peer (P 2 P)? n “Peer-to-peer is a way of structuring distributed applications such that the individual nodes have symmetric roles. Rather than being divided into clients and servers each with quite distinct roles, in P 2 P applications a node may act as both a client and a server. ” -- Charter of Peer-to-peer Research Group, IETF/IRTF, June 24, 2004 (http: //www. irtf. org/charters/p 2 prg. html) 9/66

Resources Sharing n What can we share? ¨ Computer-related n resources Shareable related-computer resources: ¨ CPU cycles - seti@home, GIMPS ¨ Bandwidth - PPLive, PPStream ¨ Storage Space - Ocean. Store, Murex ¨ Data - Napster, Gnutella ¨ People - Buddy Finder ¨ Camera, Microphone, Sensor, Service? ? ? 10/66
NVEs
Massively Multiplayer Online Games n MMOGs are growing quickly ¨ Multi-billion dollar industry ¨ 10 million subscribers for World of Warcraft ¨ 600, 000 concurrent users 12/66

13

Adaptive Computing and Networking Lab, CSIE, NCU 14

Adaptive Computing and Networking Lab, CSIE, NCU 15
16/66

NCU ACNLab
NASA World Wind
Google Earth
Zoom in…
To Hsin. Chu. . NCU ACNLab

and NTHU. .
It is going to be 3 D
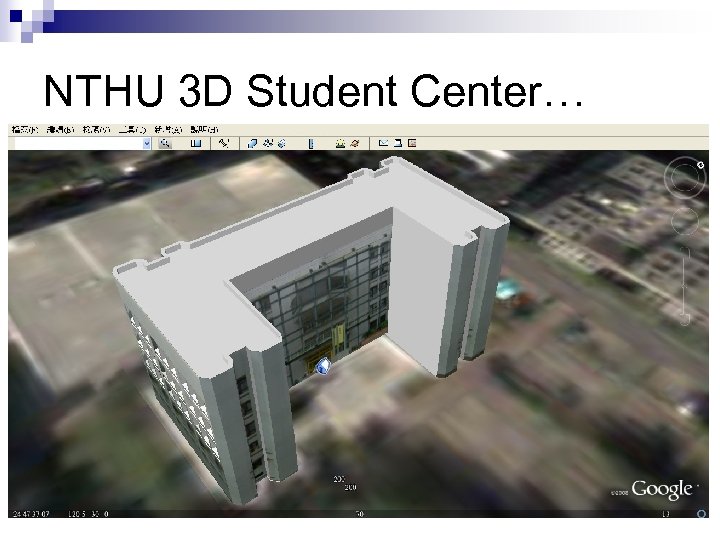
NTHU 3 D Student Center…

To the ground

3 -Dimensional Virtual Tourism n Google Earth n Virtual Earth 3 D (Micro. Soft) n NASA World Wind n X 3 D Earth NCU ACNLab
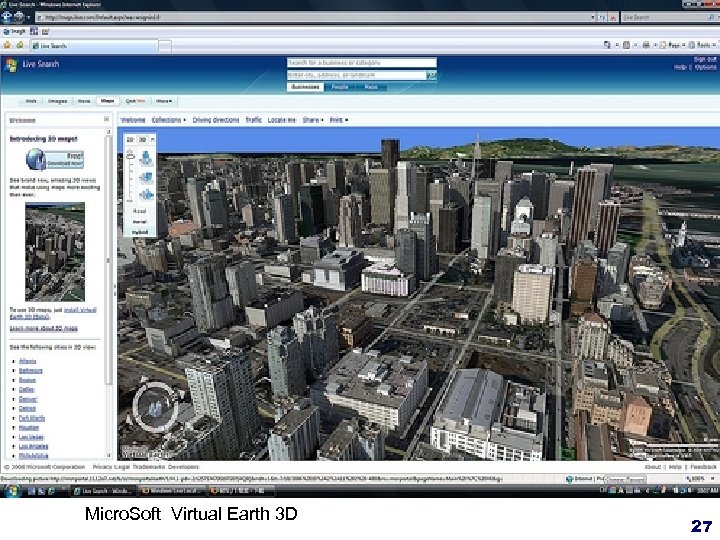
Micro. Soft Virtual Earth 3 D 27
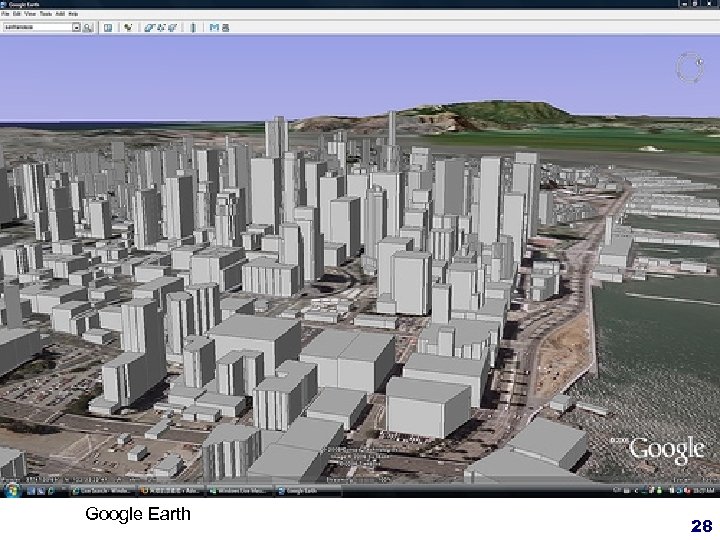
Google Earth 28
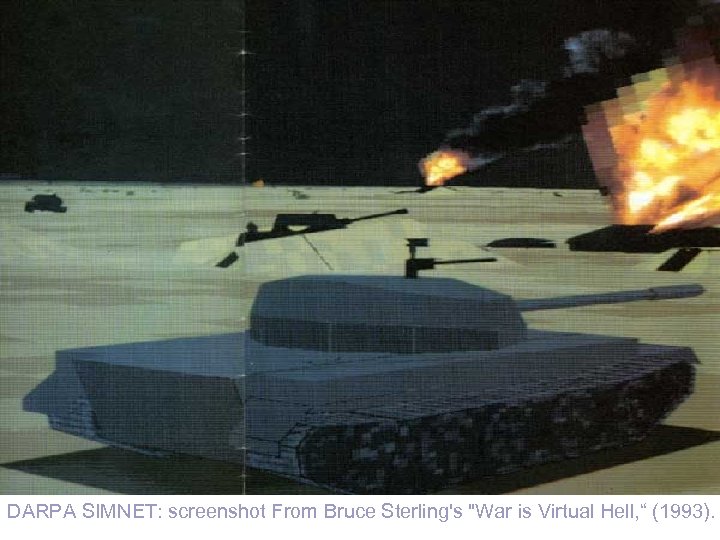
DARPA SIMNET: screenshot From Bruce Sterling's "War is Virtual Hell, “ (1993).

CALVIN: a distributed collaborative virtual environments for architectural layout designs (1996)

NVE A networked virtual environment (NVE) is a computer-generated virtual world where multiple geographically dispersed users can assume virtual representatives (or avatars) to concurrently interact with each other in real time through networked devices. n Also called a distributed virtual environment (DVE) or collaborative virtual environment (CVE) 31 n
NVE n Examples of NVEs include ¨early DARPA SIMNET and DIS systems ¨early distributed collaborative virtual environments ¨currently booming Massively Multiplayer Online Games (MMOGs) ¨future multi-user 3 DVTs ¨future multi-user Web 3 D browser 32

Question n n 33 Most VNEs, especially MMOGs, are server -based and thus suffer from the scalability problem. Can we apply the P 2 P concept to VNEs? YES!

P 2 P and NVEs
Questions How can we manage states of avatars, NPCs and objects of an NVE? n Answer: n ¨ Fully connected point-to-point ¨ Client/Server (C/S) ¨ Client/Server-cluster ¨ Peer-to-peer 35
![A simple solution (point-to-point) Source: [Funkhouser 95] But…too many irrelevant messages N * (N-1) A simple solution (point-to-point) Source: [Funkhouser 95] But…too many irrelevant messages N * (N-1)](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-36.jpg)
A simple solution (point-to-point) Source: [Funkhouser 95] But…too many irrelevant messages N * (N-1) connections ≈ O(N 2) Not scalable! 36
![A better solution (client-server) Source: [Funkhouser 95] Message filtering at server to reduce traffic A better solution (client-server) Source: [Funkhouser 95] Message filtering at server to reduce traffic](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-37.jpg)
A better solution (client-server) Source: [Funkhouser 95] Message filtering at server to reduce traffic N connections = O(N) server is bottleneck 37
![Current solution (server-cluster) Source: [Funkhouser 95] Still limited by servers. Expensive to deploy & Current solution (server-cluster) Source: [Funkhouser 95] Still limited by servers. Expensive to deploy &](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-38.jpg)
Current solution (server-cluster) Source: [Funkhouser 95] Still limited by servers. Expensive to deploy & maintain. 38
![The Problem n Client-server: resources limited by provisioning Resource limit [Funkhouser 95] The Problem n Client-server: resources limited by provisioning Resource limit [Funkhouser 95]](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-39.jpg)
The Problem n Client-server: resources limited by provisioning Resource limit [Funkhouser 95]
![The Solution n Peer-to-Peer: resources grow with demand Resource limit [Keller & Simon 2003] The Solution n Peer-to-Peer: resources grow with demand Resource limit [Keller & Simon 2003]](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-40.jpg)
The Solution n Peer-to-Peer: resources grow with demand Resource limit [Keller & Simon 2003]
![P 2 P Overlay for NVEs (1): DHT-based: Sim. MUD [Knutsson et al. 2004] P 2 P Overlay for NVEs (1): DHT-based: Sim. MUD [Knutsson et al. 2004]](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-41.jpg)
P 2 P Overlay for NVEs (1): DHT-based: Sim. MUD [Knutsson et al. 2004] (UPenn) n n Fixed-Sized Regions n 41 Pastry (DHT mapping) + Scribe (Multicast) Coordinators
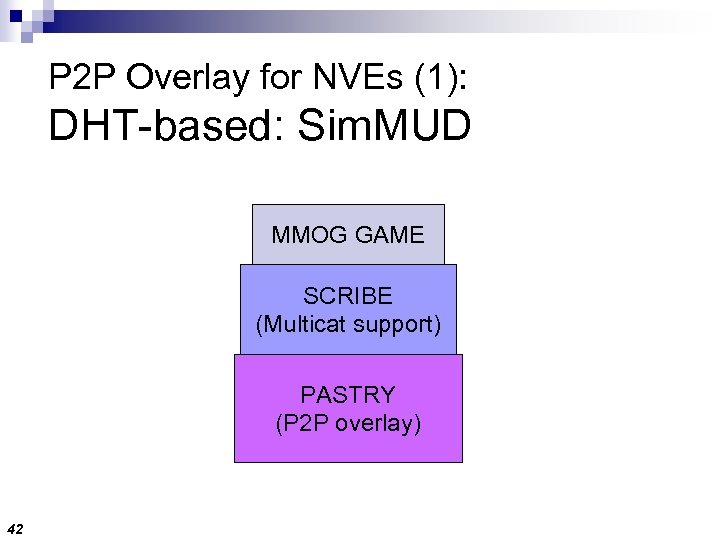
P 2 P Overlay for NVEs (1): DHT-based: Sim. MUD MMOG GAME SCRIBE (Multicat support) PASTRY (P 2 P overlay) 42
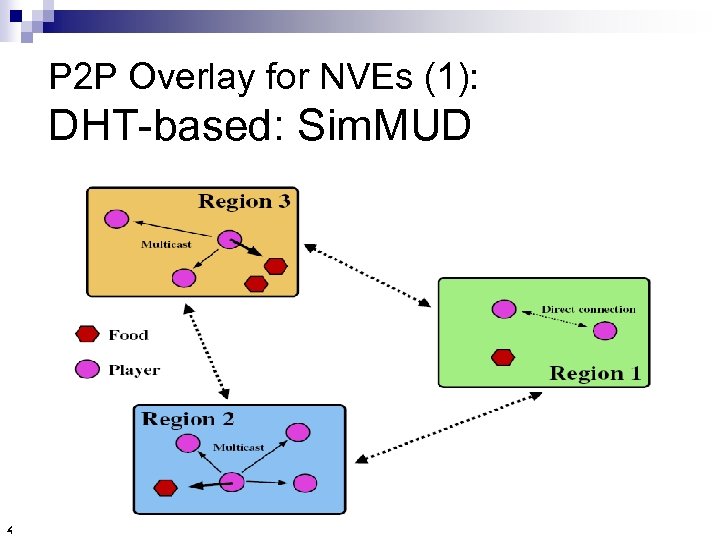
P 2 P Overlay for NVEs (1): DHT-based: Sim. MUD 43
![P 2 P Overlay for NVEs (2): Neighbor-list Exchange [Kawahara et al. 2004] (Univ. P 2 P Overlay for NVEs (2): Neighbor-list Exchange [Kawahara et al. 2004] (Univ.](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-44.jpg)
P 2 P Overlay for NVEs (2): Neighbor-list Exchange [Kawahara et al. 2004] (Univ. of Tokyo) n n 44 n Fully-distributed Nearest-neighbors List exchange High transmission Overlay partition
![P 2 P Overlay for NVEs (3): Mutual Notification: Solipsis [Keller & Simon 2003] P 2 P Overlay for NVEs (3): Mutual Notification: Solipsis [Keller & Simon 2003]](https://present5.com/presentation/538cf97a4c54b87a5b20acef582a999a/image-45.jpg)
P 2 P Overlay for NVEs (3): Mutual Notification: Solipsis [Keller & Simon 2003] (France Telecomm R&D) n n 45 n Links with AOI neighbor Mutual cooperation Inside convex hull Potentially slow discovery Inconsistent topology

P 2 P Overlay for NVEs (4) Voronoi-based Overlay Network : VON n Use Voronoi diagram to solve the neighbor discovery problem ¨Each node constructs a Voronoi diagram of its neighbors ¨Identify enclosing and boundary neighbors ¨Mutual collaboration in neighbor discovery
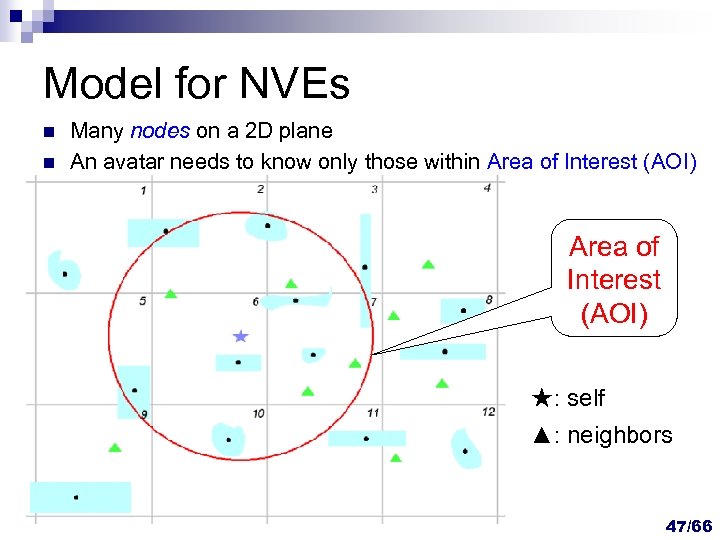
Model for NVEs n n Many nodes on a 2 D plane An avatar needs to know only those within Area of Interest (AOI) ★: self ▲: neighbors 47/66
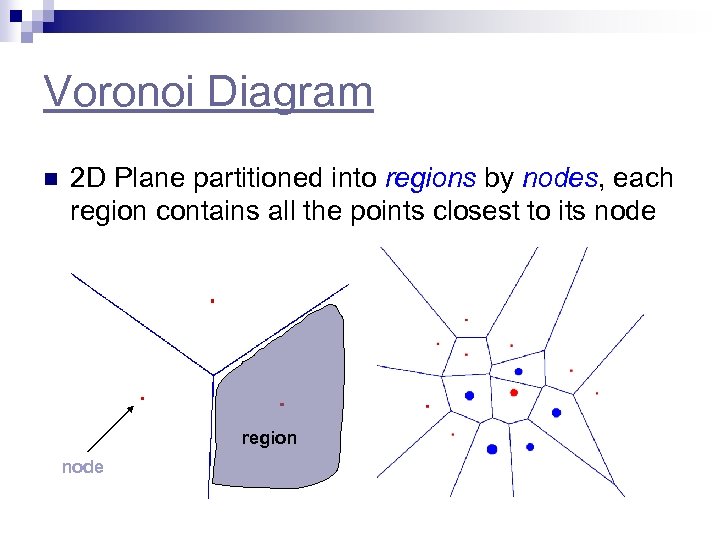
Voronoi Diagram n 2 D Plane partitioned into regions by nodes, each region contains all the points closest to its node region node
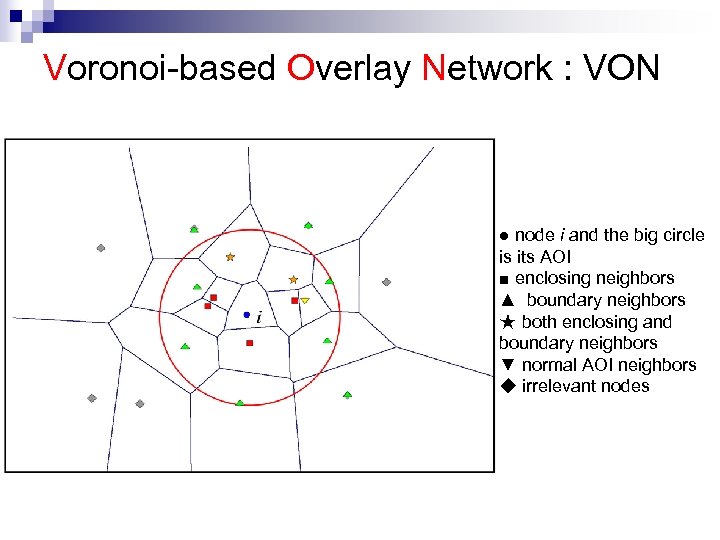
Voronoi-based Overlay Network : VON ● node i and the big circle is its AOI ■ enclosing neighbors ▲ boundary neighbors ★ both enclosing and boundary neighbors ▼ normal AOI neighbors ◆ irrelevant nodes
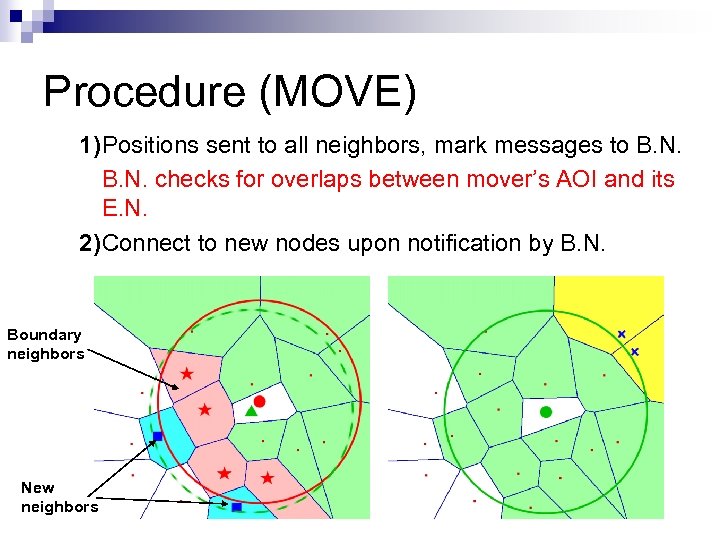
Procedure (MOVE) 1)Positions sent to all neighbors, mark messages to B. N. checks for overlaps between mover’s AOI and its E. N. 2)Connect to new nodes upon notification by B. N. Boundary neighbors New neighbors
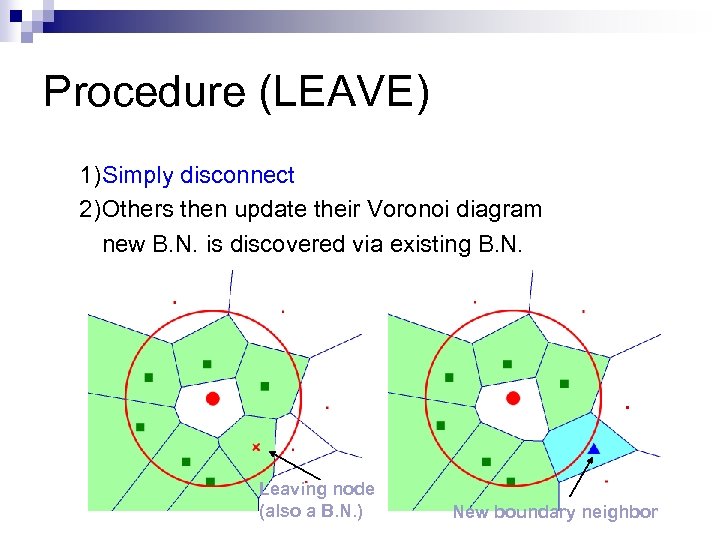
Procedure (LEAVE) 1)Simply disconnect 2)Others then update their Voronoi diagram new B. N. is discovered via existing B. N. Leaving node (also a B. N. ) New boundary neighbor
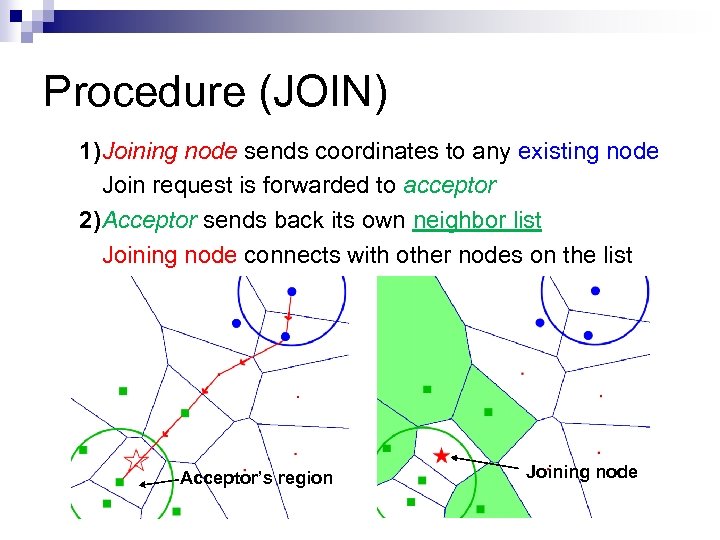
Procedure (JOIN) 1)Joining node sends coordinates to any existing node Join request is forwarded to acceptor 2)Acceptor sends back its own neighbor list Joining node connects with other nodes on the list Acceptor’s region Joining node

Neighborship Consistency (1) n Definition no. of current AOI neighbors observed no. of current actual AOI neighbors 53
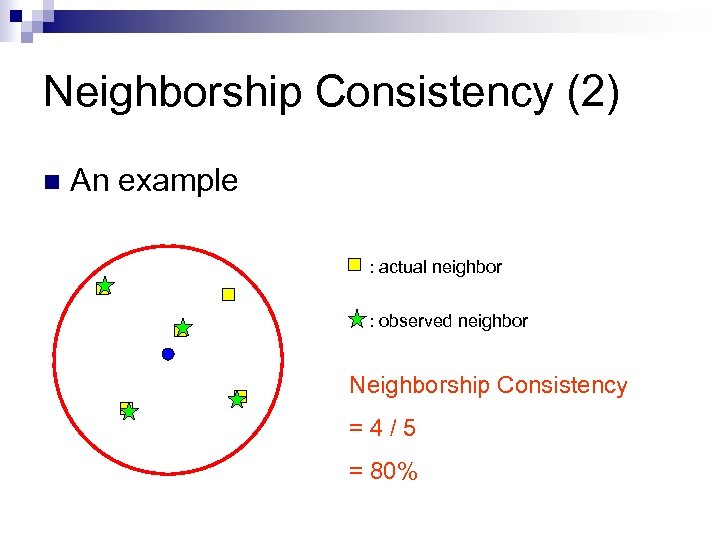
Neighborship Consistency (2) n An example : actual neighbor : observed neighbor Neighborship Consistency =4/5 = 80%
Factors affecting Neighborship Consistency n Mobility ¨ n Speed AOI-radius Node failure ¨ Possibly causes overlay partition 55
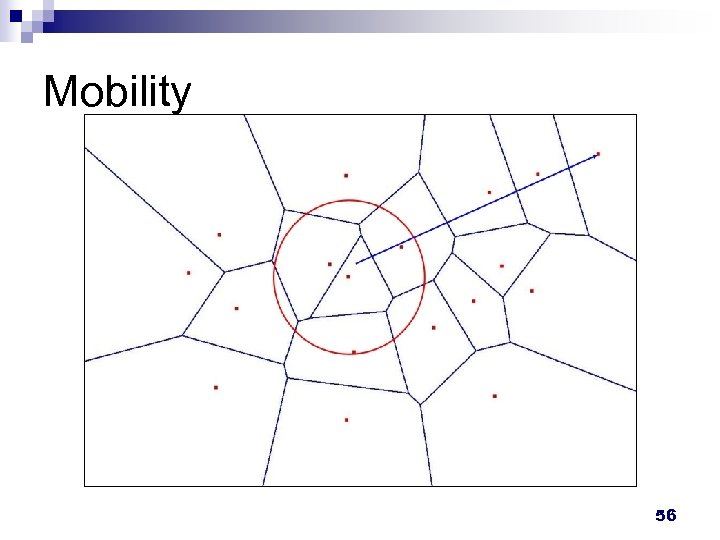
Mobility 56

Overlay Partition (1/2) Nodes divide into two or more groups n Each group can not be aware each other n May destroy neighborship consistency n In pure P 2 P NVE n ¨ May be impossible to detect and recover ¨ Have to avoid it 57
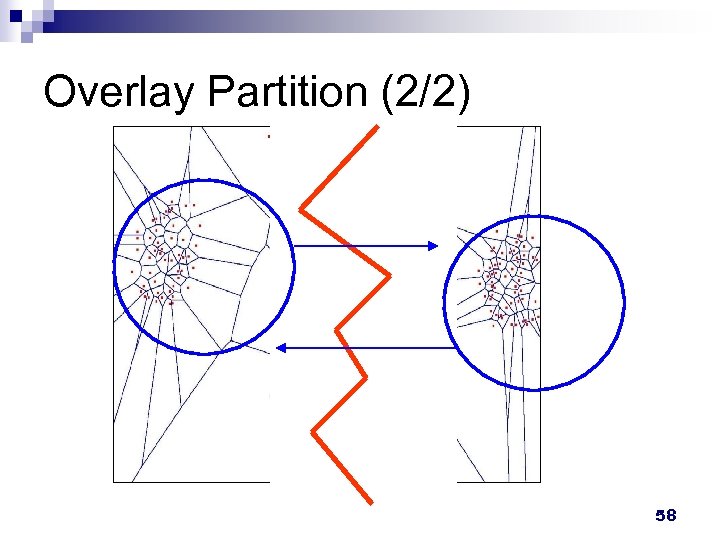
Overlay Partition (2/2) × × × 58

Proposed Solutions n Adaptive AOI ¨ AOI n radius increases with speed increasing Detecting critical nodes ¨ Critical nodes are the nodes in some regions where the density is low ¨ It is used to avoid overlay partition 59
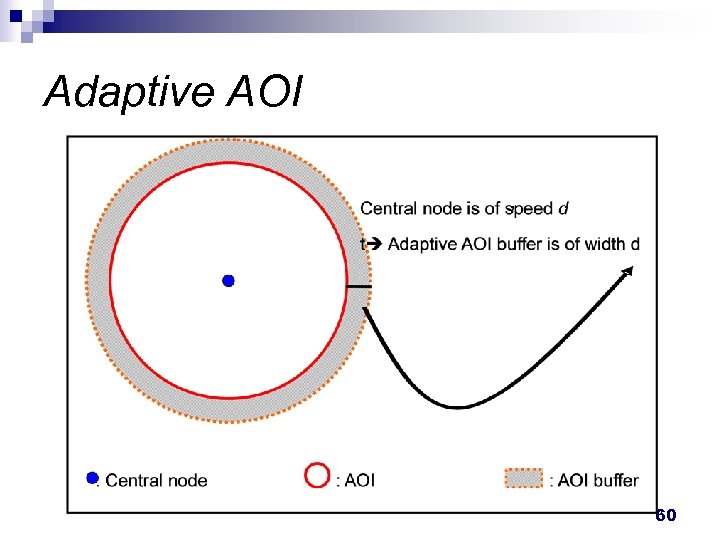
Adaptive AOI 60
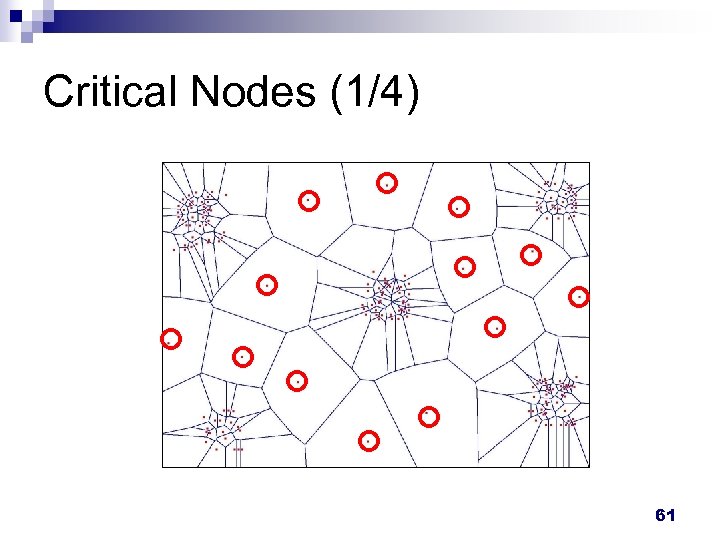
Critical Nodes (1/4) 61

Critical Nodes (2/4) n Periodically detect by node itself Neighbor_level = # AOI neighbors Average # AOI neighbors If a node detects that its neighbor level is lower than a pre-specified threshold, it regards itself as a critical node. n A critical node will perform the backup operation to send to all connected neighbors the backup message. n 62

Critical Nodes (3/4) n A Backup message ¨ Sent by critical nodes ¨ Contains a neighbor list n of the critical node Stock neighbor list ¨ Stores nodes from backup ¨ Uses to periodically check n message Check operation ¨ Check all nodes in its stock neighbor ¨ To discovery missed neighbors list periodically 63
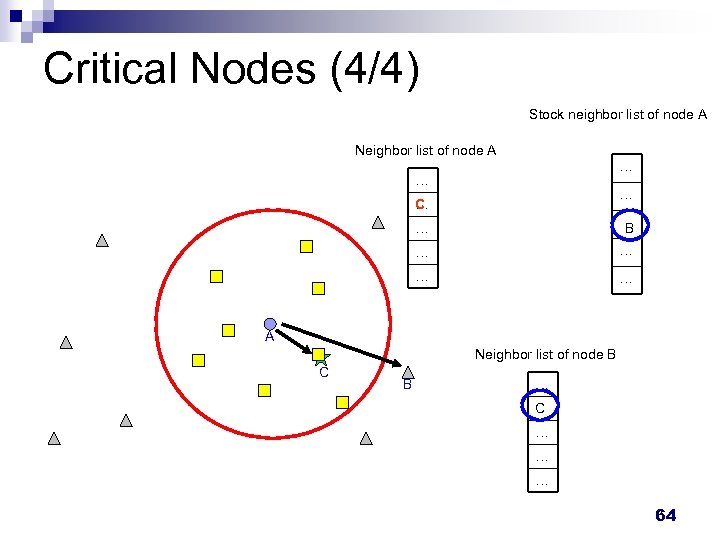
Critical Nodes (4/4) Stock neighbor list of node A Neighbor list of node A … … C … B … … A Neighbor list of node B C B … C … … … 64

3 D Streaming n Continuous and real-time delivery of 3 D contents over network connections to allow user interactions without a full download. n Contents are fragmented, transmitted, reconstructed, and then displayed.

3 D streaming vs. media streaming n Video / audio media streaming is very matured n User access patterns are different for 3 D content ¨ Highly interactive ¨ Behaviour-dependent Latency-sensitive Non-sequential

4 types of 3 D streaming n Object streaming n Scene streaming n Visualization streaming n Image-based streaming
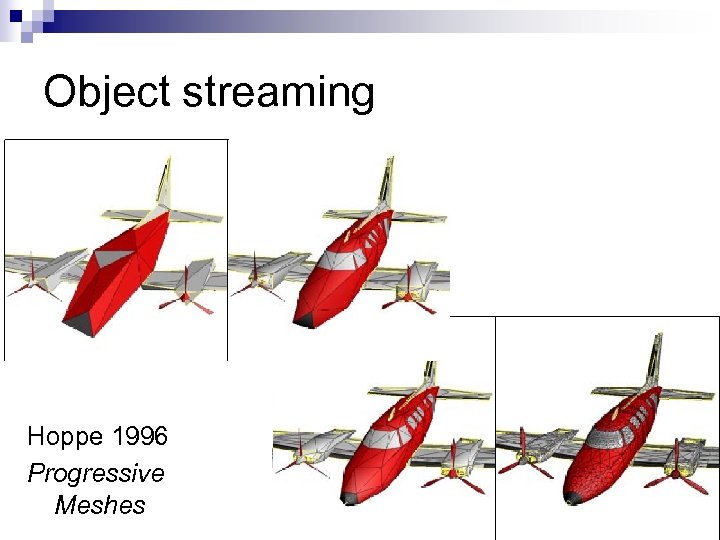
Object streaming Hoppe 1996 Progressive Meshes /
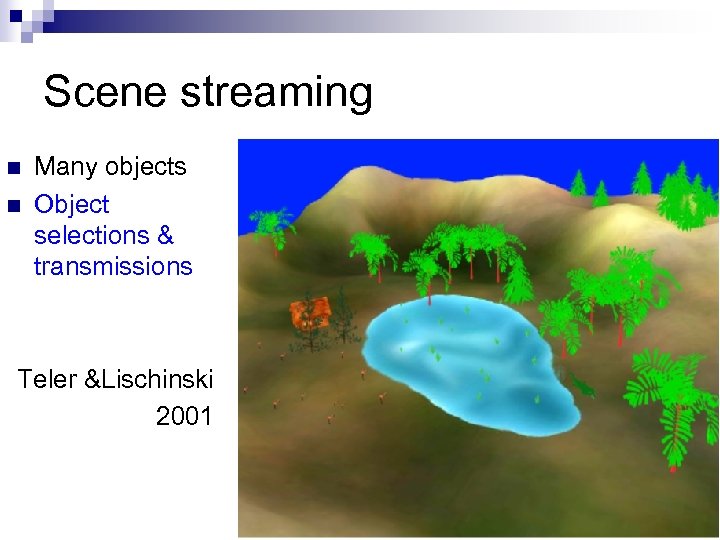
Scene streaming n n Many objects Object selections & transmissions Teler &Lischinski 2001 /
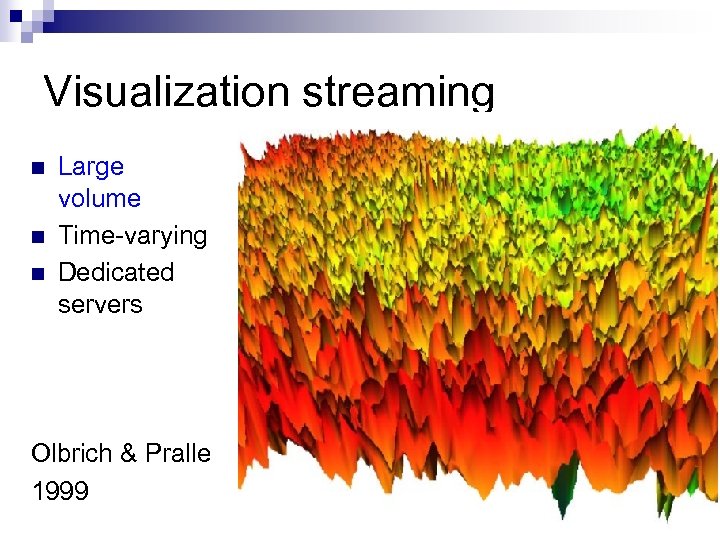
Visualization streaming n n n Large volume Time-varying Dedicated servers Olbrich & Pralle 1999 /
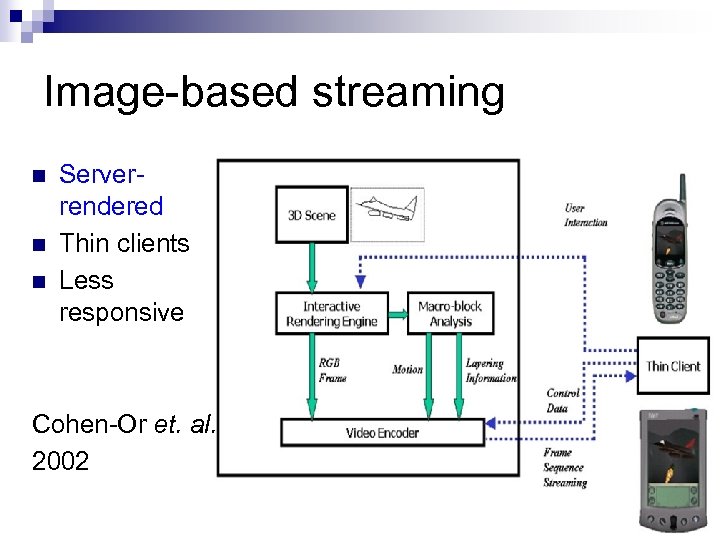
Image-based streaming n n n Serverrendered Thin clients Less responsive Cohen-Or et. al. 2002 /
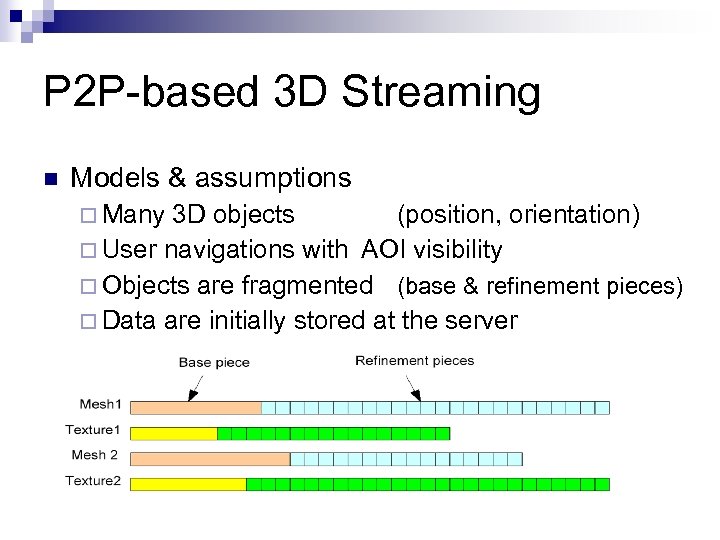
P 2 P-based 3 D Streaming n Models & assumptions ¨ Many 3 D objects (position, orientation) ¨ User navigations with AOI visibility ¨ Objects are fragmented (base & refinement pieces) ¨ Data are initially stored at the server
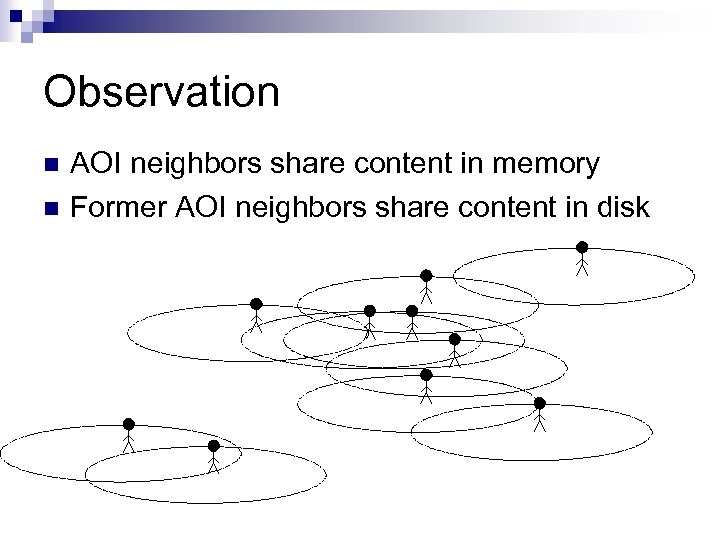
Observation n n AOI neighbors share content in memory Former AOI neighbors share content in disk
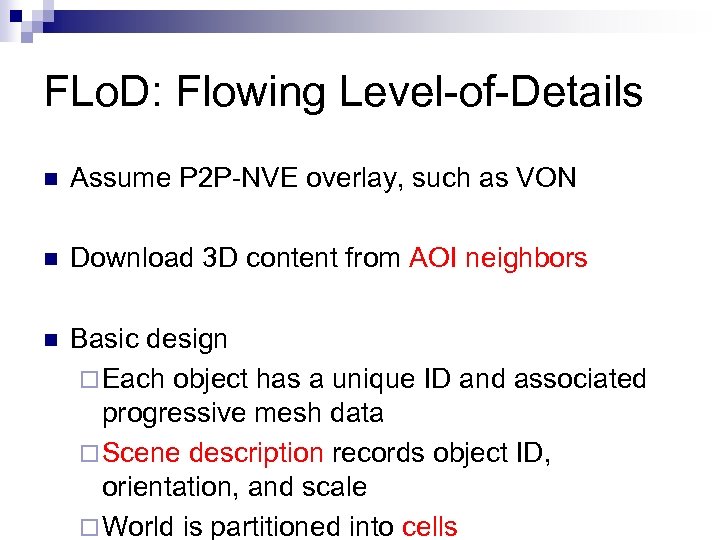
FLo. D: Flowing Level-of-Details n Assume P 2 P-NVE overlay, such as VON n Download 3 D content from AOI neighbors n Basic design ¨ Each object has a unique ID and associated progressive mesh data ¨ Scene description records object ID, orientation, and scale ¨ World is partitioned into cells

Steps of FLo. D 1. 2. 3. 4. Peers exchange incremental information of cached 3 D data periodically A peer sends requests for downloading scene descriptions A peer sends requests for downloading object data A peer asks the server if none of the peers responds
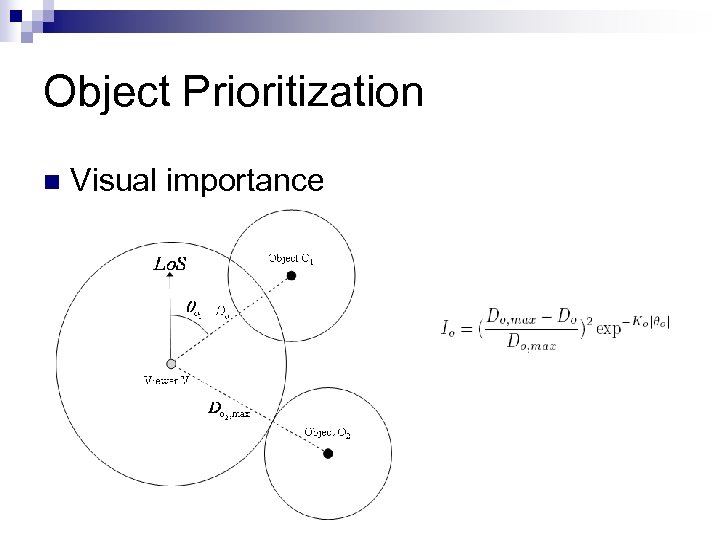
Object Prioritization n Visual importance
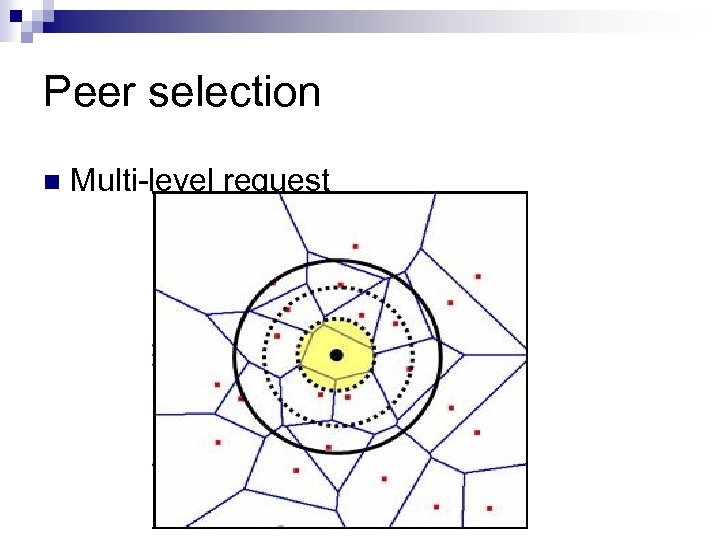
Peer selection n Multi-level request

Prototype experiment n n n Cell-based construction Use an actual game scene 100 x game scene (514 KB -> 51. 8 MB)
Fragmentation

Efficient AOI-Cast for Peer-to-Peer Networked Virtual Environments
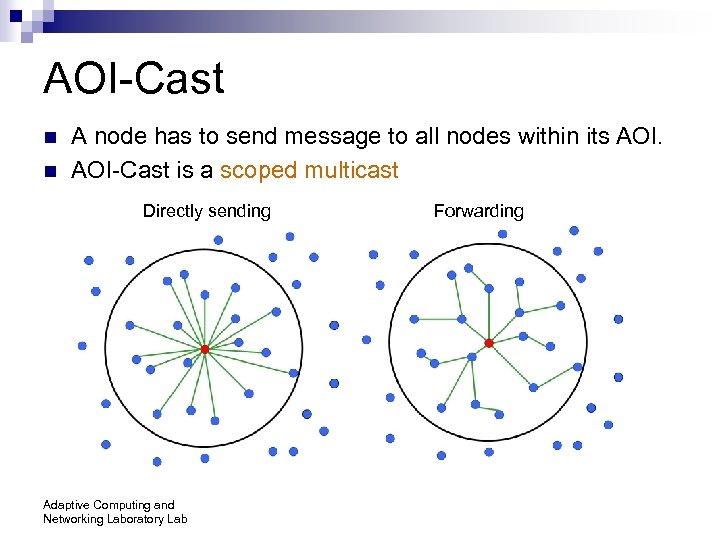
AOI-Cast n n A node has to send message to all nodes within its AOI-Cast is a scoped multicast Directly sending Adaptive Computing and Networking Laboratory Lab Forwarding
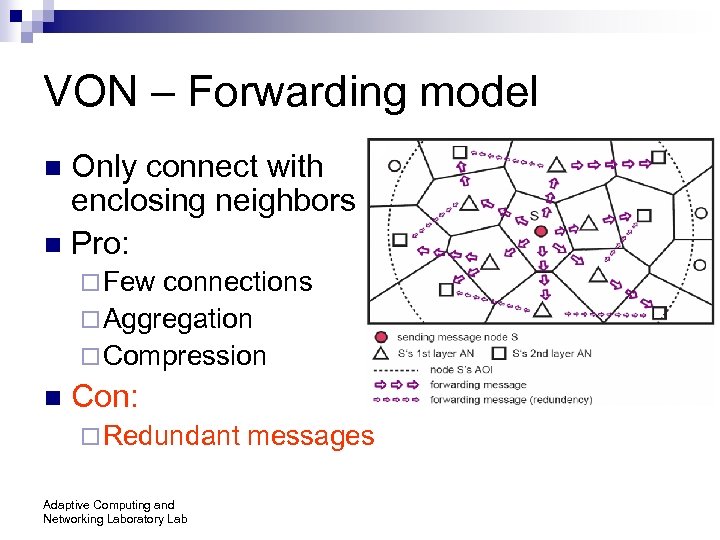
VON – Forwarding model Only connect with enclosing neighbors n Pro: n ¨ Few connections ¨ Aggregation ¨ Compression n Con: ¨ Redundant Adaptive Computing and Networking Laboratory Lab messages

Voro. Cast Adaptive Computing and Networking Laboratory Lab
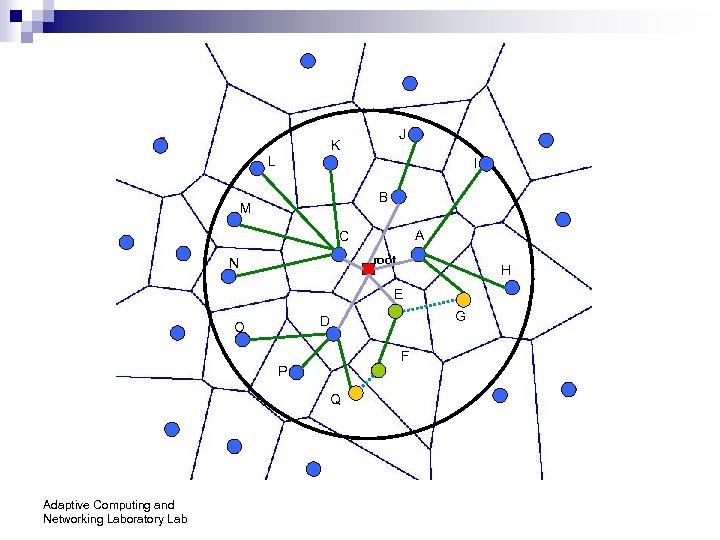
J K L I B M A C root N H E G D O F P Q Adaptive Computing and Networking Laboratory Lab
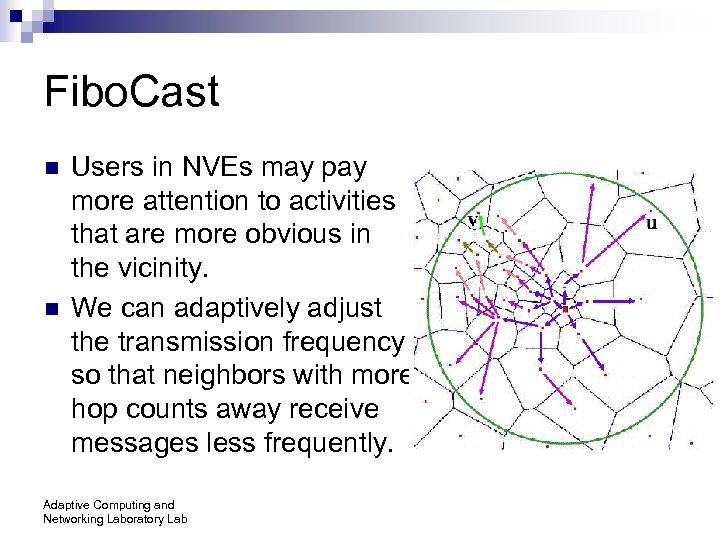
Fibo. Cast n n Users in NVEs may pay more attention to activities that are more obvious in the vicinity. We can adaptively adjust the transmission frequency so that neighbors with more hop counts away receive messages less frequently. Adaptive Computing and Networking Laboratory Lab

Fibo. Cast n Two variables in a message: ¨ current hop count (chc): increased each hop ¨ maximal hop count (mhp): set by a Fibonacci sequence with the last being infinite in a round-robin manner n The message is dropped when chc==mhp n E. G. : For a Fibonacci sequence <0, 1, 1, 2, 3, 5, 8, >, the maximal hop counts would be 2, 3, 3, 4, 5, 7, 10, , 1, 2, 3, 3, 4, 5, 7, etc. Adaptive Computing and Networking Laboratory Lab

Peer-to-Peer AOI Voice Chatting for Massively Multiplayer Online Games (P 2 P-NVE 2007 workshop) Jehn-Ruey Jiang and Hung-Shiang Chen Adaptive Computing and Networking Lab Dept. of CSIE, National Central University, Taiwan
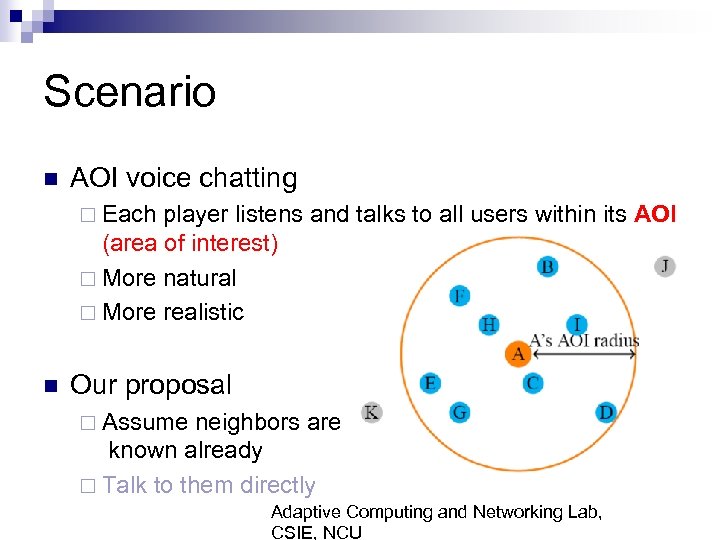
Scenario n AOI voice chatting ¨ Each player listens and talks to all users within its AOI (area of interest) ¨ More natural ¨ More realistic n Our proposal ¨ Assume neighbors are known already ¨ Talk to them directly Adaptive Computing and Networking Lab, CSIE, NCU
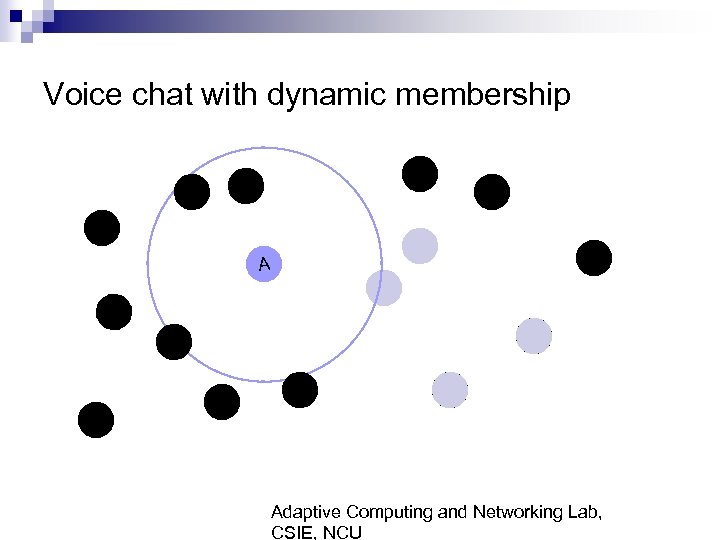
Voice chat with dynamic membership A Adaptive Computing and Networking Lab, CSIE, NCU

A simple approach n Nimbus. Cast: ¨ MMOG system first provides a list of AOI neighbors ¨ individual voice packets for all AOI neighbors Adaptive Computing and Networking Lab, CSIE, NCU
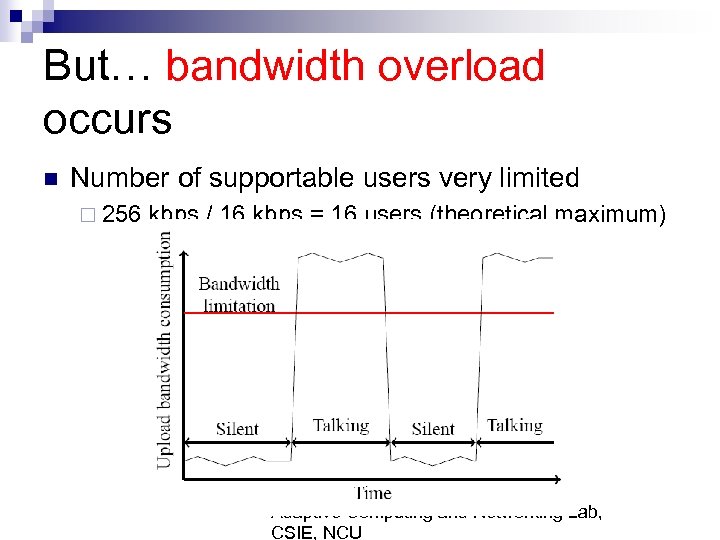
But… bandwidth overload occurs n Number of supportable users very limited ¨ 256 kbps / 16 kbps = 16 users (theoretical maximum) Adaptive Computing and Networking Lab, CSIE, NCU
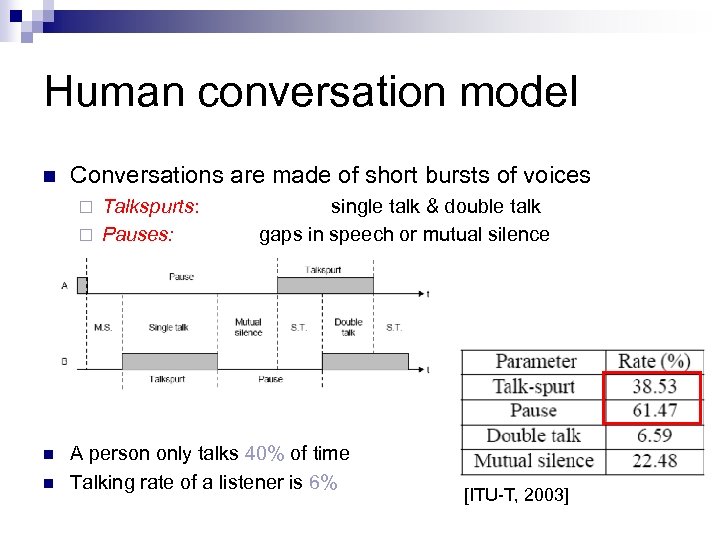
Human conversation model n Conversations are made of short bursts of voices Talkspurts: ¨ Pauses: ¨ n n single talk & double talk gaps in speech or mutual silence A person only talks 40% of time Talking rate of a listener is 6% [ITU-T, 2003]

Our proposal n Observation: idle bandwidth can be used to forward voice packets, supporting more users n Under two goals: ¨ Reasonable delay [ITU-T P. 59] 150~250 ms (good) ¨ No 400 ms (tolerable) bandwidth overload: Voice bursts should not exceed bandwidth limit Adaptive Computing and Networking Lab, CSIE, NCU
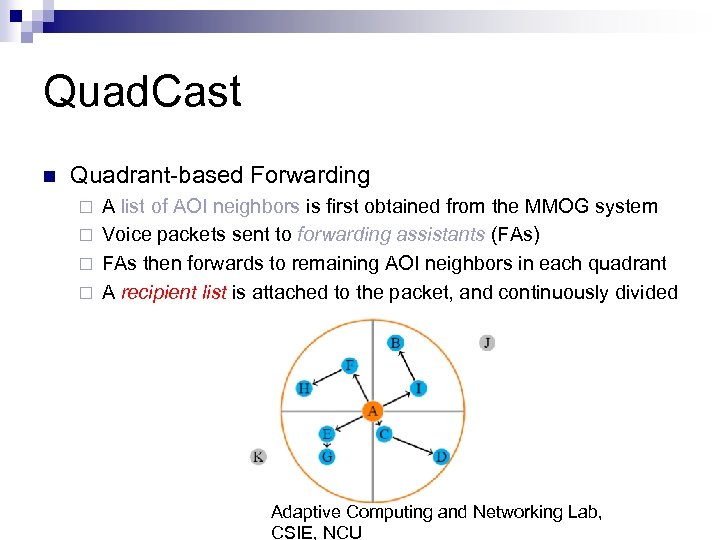
Quad. Cast n Quadrant-based Forwarding A list of AOI neighbors is first obtained from the MMOG system ¨ Voice packets sent to forwarding assistants (FAs) ¨ FAs then forwards to remaining AOI neighbors in each quadrant ¨ A recipient list is attached to the packet, and continuously divided ¨ Adaptive Computing and Networking Lab, CSIE, NCU
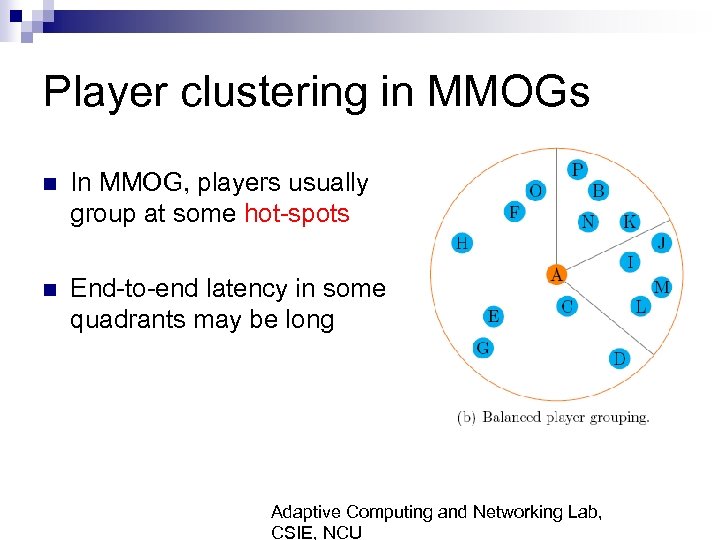
Player clustering in MMOGs n In MMOG, players usually group at some hot-spots n End-to-end latency in some quadrants may be long Adaptive Computing and Networking Lab, CSIE, NCU
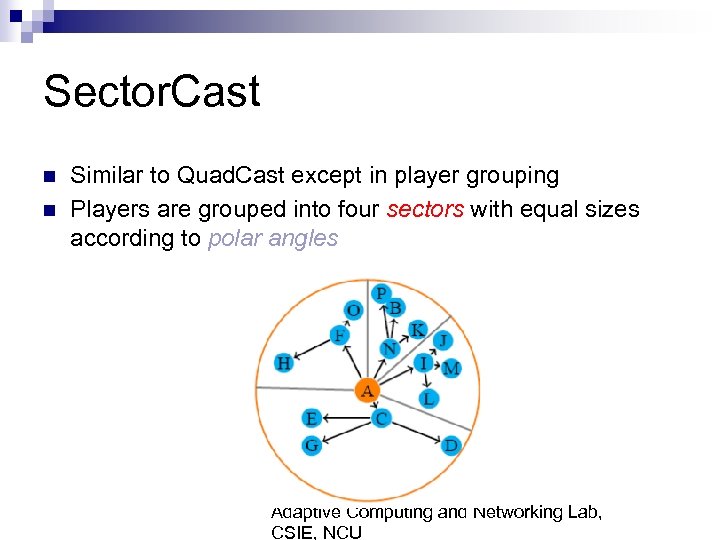
Sector. Cast n n Similar to Quad. Cast except in player grouping Players are grouped into four sectors with equal sizes according to polar angles Adaptive Computing and Networking Lab, CSIE, NCU
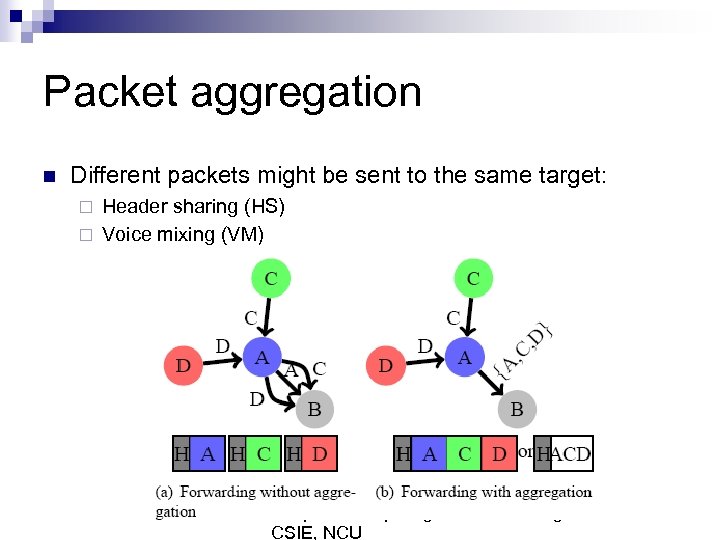
Packet aggregation n Different packets might be sent to the same target: Header sharing (HS) ¨ Voice mixing (VM) ¨ Adaptive Computing and Networking Lab, CSIE, NCU

P 2 P MMOG Topics n n n n Cheat Proof Reputation Management AOI Cast Mechanisms AOI Voice Chatting Secure P 2 P 3 D Streaming Behavior-Based P 2 P 3 D Streaming Incentive for P 2 P 3 D Streaming …

Related Journal Publication n Shun-Yun Hu, Jehn-Ruey Jiang and Bing-Yu Chen, “Peer-to -Peer 3 D Streaming, ” IEEE Internet Computing, Vol. 14, No. 2, pp. 54 -61, March/April 2010. Chien-Hao Chien, Shun-Yun Hu, Jehn-Ruey Jiang and Chuan-Wei Cheng, “Bandwidth-Aware Peer-to-Peer 3 D Streaming, ” International Journal of Advanced Media and Communication (IJAMC), Vol. 4, Issue 4, pp. 324 -342, 2010. Jehn-Ruey Jiang, Hung-Shiang Chen and Chao-Wei Hung, “Peer-to-Peer AOI Voice Chatting for Massively Multiplayer Online Games, ” International Journal of Electrical Engineering (IJEE), Vol. 17, No. 1, pp. 43 -54, 2010.

Related Journal Publication n n Mo-Che Chan, Shun-Yun Hu, and Jehn-Ruey Jiang, “Secure Peer-to-Peer 3 D Streaming, ” Multimedia Tools and Applications, Vol. 45, Issue 1, pp. 369 - 384, May 2009. Jehn-Ruey Jiang, Chung-Ta King, Chi-Shiang Liao and Ching-Hao Liu, “MUREX: A Mutable Replica Control Scheme for Structured Peer-to-Peer Storage Systems, ” International Journal of Pervasive Computing and Communications, Vol. 5, Issue 1, 2009. Jehn-Ruey Jiang, Jiun-Shiang Chiou and Shun-Yun Hu, “Enhancing Neighborship Consistency for Peer-to-Peer Networked Virtual Environments, ” Journal of Internet Technology, Vol. 10, No. 1, pp. 29 -36, 2009. Jehn-Ruey Jiang, Yu-Li Huang and Shun-Yun Hu, “Scalable AOI-cast for Peer-to-Peer Networked Virtual Environments, ” Journal of Internet Technology, Vol. 10, No. 2, pp. 119125, 2009.

Related Journal Publication n n Mo-Che Chan, Shun-Yun Hu, Jehn-Ruey Jiang, “An Efficient and Secure Event Signature (EASES) Protocol for Peer-to. Peer Massively Multiplayer Online Games, ” Computer Networks, Vol. 52, No. 9, pp. 1838 -1845, 2008. Guan-Yu Huang, Shun-Yun Hu and Jehn-Ruey Jiang, “Scalable Reputation Management with Trustworthy User Selection for P 2 P MMOGs, ” International Journal of Advanced Media and Communication (IJAMC), Vol. 2, Issue 4, 380 -401, 2008.
Q&A Thank you! Adaptive Computing and Networking Lab. http: //acnlab. csie. ncu. edu. tw
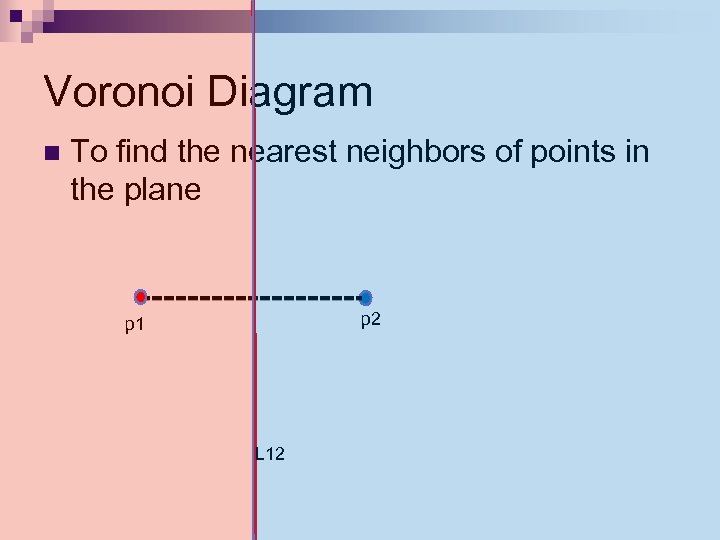
Voronoi Diagram n To find the nearest neighbors of points in the plane p 2 p 1 L 12
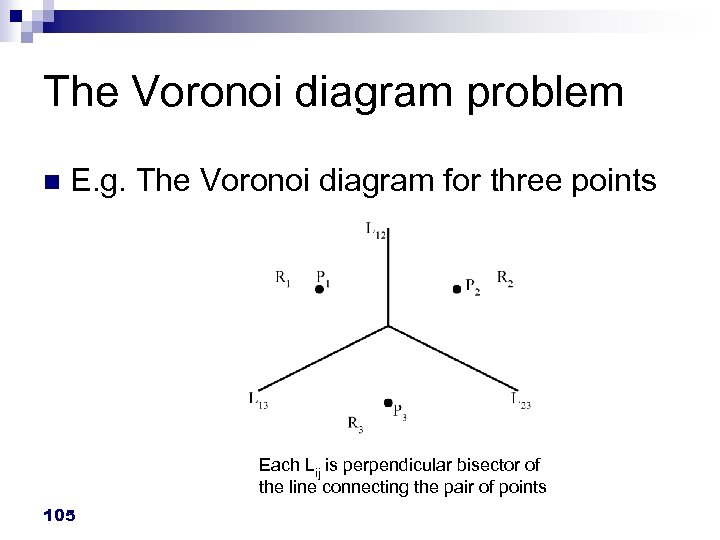
The Voronoi diagram problem n E. g. The Voronoi diagram for three points Each Lij is perpendicular bisector of the line connecting the pair of points 105

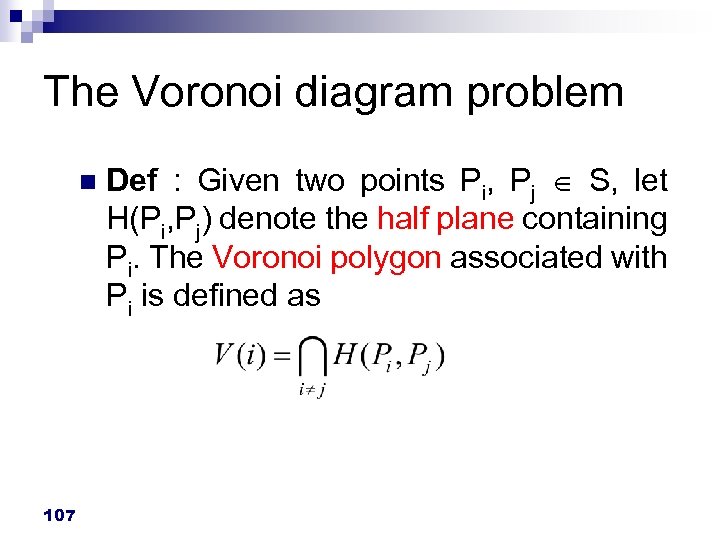
The Voronoi diagram problem n 107 Def : Given two points Pi, Pj S, let H(Pi, Pj) denote the half plane containing Pi. The Voronoi polygon associated with Pi is defined as
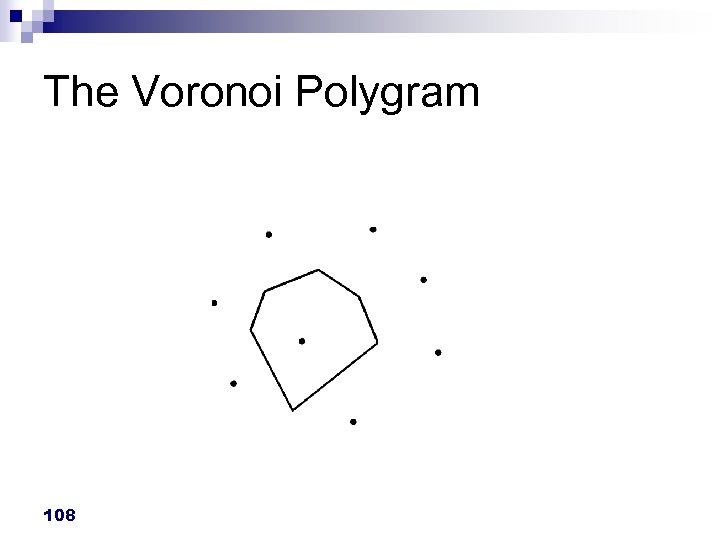
The Voronoi Polygram 108
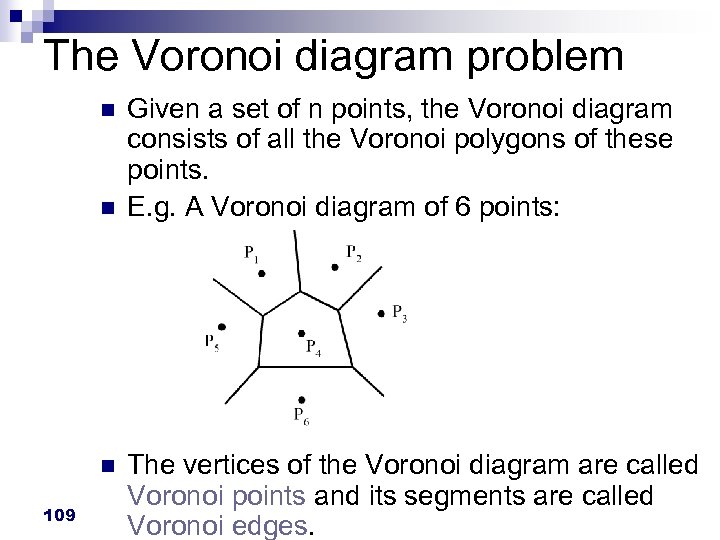
The Voronoi diagram problem n n n 109 Given a set of n points, the Voronoi diagram consists of all the Voronoi polygons of these points. E. g. A Voronoi diagram of 6 points: The vertices of the Voronoi diagram are called Voronoi points and its segments are called Voronoi edges.
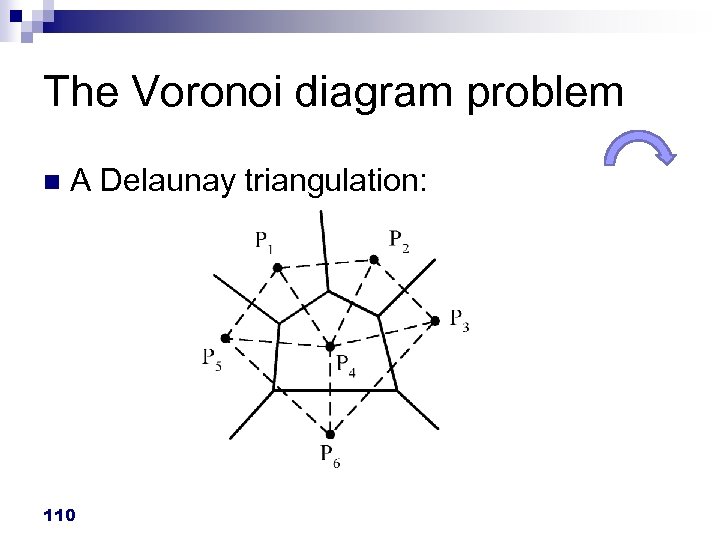
The Voronoi diagram problem n A Delaunay triangulation: 110
538cf97a4c54b87a5b20acef582a999a.ppt