d1b0d261576b0c5cda1ecea1da14cb7e.ppt
- Количество слайдов: 40
 Peer-to-Peer Network Security 1 st March 2013 Symposium on Privacy & Security 2013, IIT, Kanpur BITS Pilani Hyderabad Campus Chittaranjan Hota Dept. of Computer Sc. & Information Systems hota@hyderabad. bits-pilani. ac. in
Peer-to-Peer Network Security 1 st March 2013 Symposium on Privacy & Security 2013, IIT, Kanpur BITS Pilani Hyderabad Campus Chittaranjan Hota Dept. of Computer Sc. & Information Systems hota@hyderabad. bits-pilani. ac. in
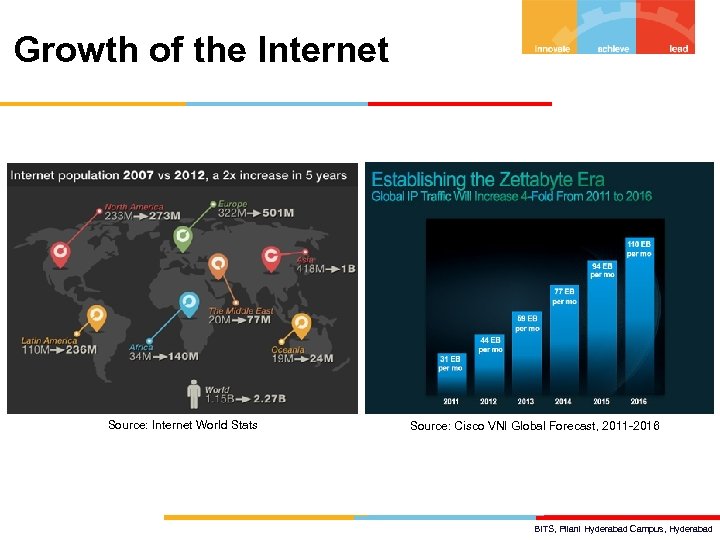 Growth of the Internet Source: Internet World Stats Source: Cisco VNI Global Forecast, 2011 -2016 BITS, Pilani Hyderabad Campus, Hyderabad
Growth of the Internet Source: Internet World Stats Source: Cisco VNI Global Forecast, 2011 -2016 BITS, Pilani Hyderabad Campus, Hyderabad
 Leading Applications Source: Sandvine Global Internet Phenomena Report, 2012 Internet bandwidth usage estimation report, 2011 BITS, Pilani Hyderabad Campus, Hyderabad
Leading Applications Source: Sandvine Global Internet Phenomena Report, 2012 Internet bandwidth usage estimation report, 2011 BITS, Pilani Hyderabad Campus, Hyderabad
 Pirate Bay Indian ISPs Unblock Torrent Sites After Madras High Court Order Consortium of internet providers win fight to access legitimate content on the P 2 P file-sharing sites. Finally its a sigh of relief from millions of Bit. Torrent users across India as the Madras High Court has ruled that Indian ISPs should not block the entire website for preventing a single content to be shared online. July 2012 May 2012 BITS, Pilani Hyderabad Campus, Hyderabad
Pirate Bay Indian ISPs Unblock Torrent Sites After Madras High Court Order Consortium of internet providers win fight to access legitimate content on the P 2 P file-sharing sites. Finally its a sigh of relief from millions of Bit. Torrent users across India as the Madras High Court has ruled that Indian ISPs should not block the entire website for preventing a single content to be shared online. July 2012 May 2012 BITS, Pilani Hyderabad Campus, Hyderabad
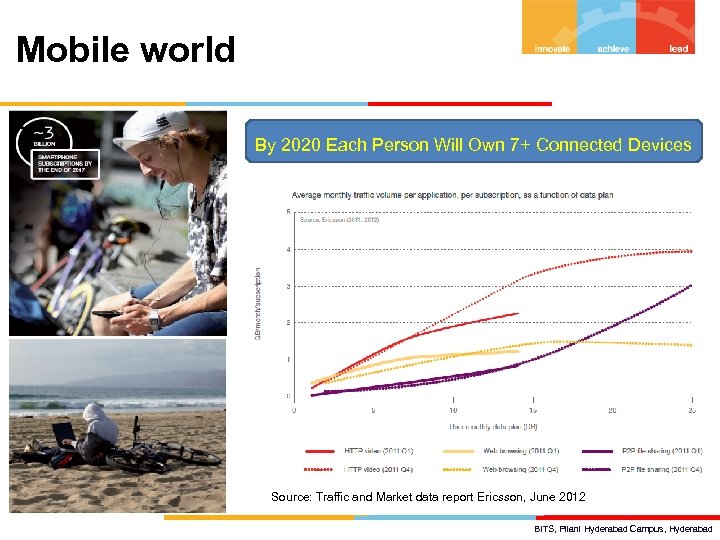 Mobile world By 2020 Each Person Will Own 7+ Connected Devices Source: Traffic and Market data report Ericsson, June 2012 BITS, Pilani Hyderabad Campus, Hyderabad
Mobile world By 2020 Each Person Will Own 7+ Connected Devices Source: Traffic and Market data report Ericsson, June 2012 BITS, Pilani Hyderabad Campus, Hyderabad
 Have you ever wondered? • 966 million P 2 P searches every day. • 800, 000 of which include terms like credit cards, tax returns, bank accounts, medical insurance, and passwords. Source: www. idtheftcenter. org BITS, Pilani Hyderabad Campus, Hyderabad
Have you ever wondered? • 966 million P 2 P searches every day. • 800, 000 of which include terms like credit cards, tax returns, bank accounts, medical insurance, and passwords. Source: www. idtheftcenter. org BITS, Pilani Hyderabad Campus, Hyderabad
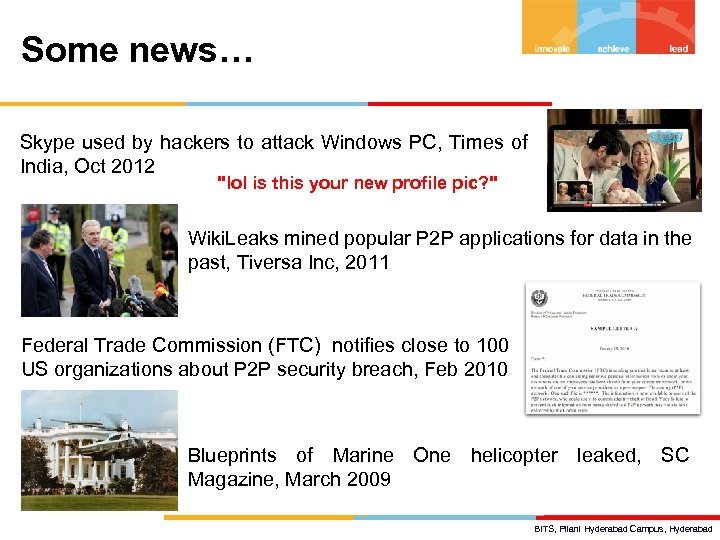 Some news… Skype used by hackers to attack Windows PC, Times of India, Oct 2012 "lol is this your new profile pic? " Wiki. Leaks mined popular P 2 P applications for data in the past, Tiversa Inc, 2011 Federal Trade Commission (FTC) notifies close to 100 US organizations about P 2 P security breach, Feb 2010 Blueprints of Marine One helicopter leaked, SC Magazine, March 2009 BITS, Pilani Hyderabad Campus, Hyderabad
Some news… Skype used by hackers to attack Windows PC, Times of India, Oct 2012 "lol is this your new profile pic? " Wiki. Leaks mined popular P 2 P applications for data in the past, Tiversa Inc, 2011 Federal Trade Commission (FTC) notifies close to 100 US organizations about P 2 P security breach, Feb 2010 Blueprints of Marine One helicopter leaked, SC Magazine, March 2009 BITS, Pilani Hyderabad Campus, Hyderabad
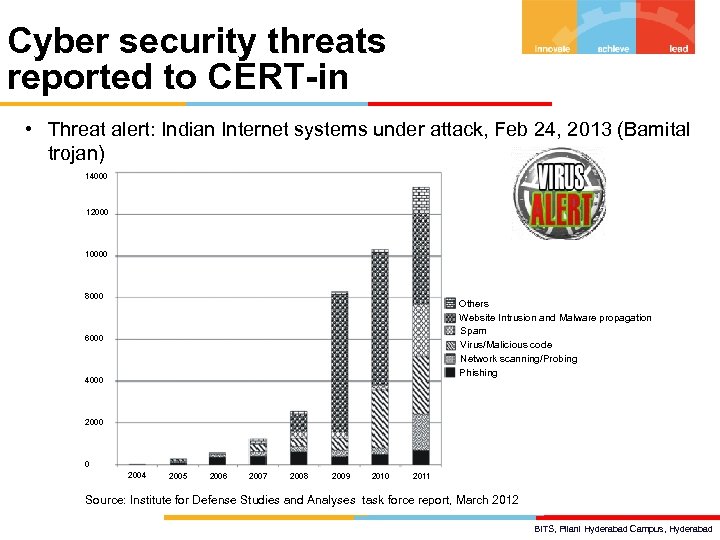 Cyber security threats reported to CERT-in • Threat alert: Indian Internet systems under attack, Feb 24, 2013 (Bamital trojan) 14000 12000 10000 8000 Others Website Intrusion and Malware propagation Spam Virus/Malicious code Network scanning/Probing Phishing 6000 4000 2000 0 2004 2005 2006 2007 2008 2009 2010 2011 Source: Institute for Defense Studies and Analyses task force report, March 2012 BITS, Pilani Hyderabad Campus, Hyderabad
Cyber security threats reported to CERT-in • Threat alert: Indian Internet systems under attack, Feb 24, 2013 (Bamital trojan) 14000 12000 10000 8000 Others Website Intrusion and Malware propagation Spam Virus/Malicious code Network scanning/Probing Phishing 6000 4000 2000 0 2004 2005 2006 2007 2008 2009 2010 2011 Source: Institute for Defense Studies and Analyses task force report, March 2012 BITS, Pilani Hyderabad Campus, Hyderabad
 What is a P 2 P Network? C P 2 P overlay layer A F H G D B A E C E F H AS 1 AS 4 B AS 2 AS 6 D AS 3 G AS 5 Native IP layer BITS, Pilani Hyderabad Campus, Hyderabad
What is a P 2 P Network? C P 2 P overlay layer A F H G D B A E C E F H AS 1 AS 4 B AS 2 AS 6 D AS 3 G AS 5 Native IP layer BITS, Pilani Hyderabad Campus, Hyderabad
 Generic P 2 P Architecture Search API Overlay Messaging API Peer Role Selection Capability & Configuration Routing and Forwarding Neighbor Discovery Join/Leave Bootstrap Content Storage NAT/ Firewall Traversal Operating System BITS, Pilani Hyderabad Campus, Hyderabad
Generic P 2 P Architecture Search API Overlay Messaging API Peer Role Selection Capability & Configuration Routing and Forwarding Neighbor Discovery Join/Leave Bootstrap Content Storage NAT/ Firewall Traversal Operating System BITS, Pilani Hyderabad Campus, Hyderabad
 Examples of P 2 P Networks BITS, Pilani Hyderabad Campus, Hyderabad
Examples of P 2 P Networks BITS, Pilani Hyderabad Campus, Hyderabad
 DC++ BITS, Pilani Hyderabad Campus, Hyderabad
DC++ BITS, Pilani Hyderabad Campus, Hyderabad
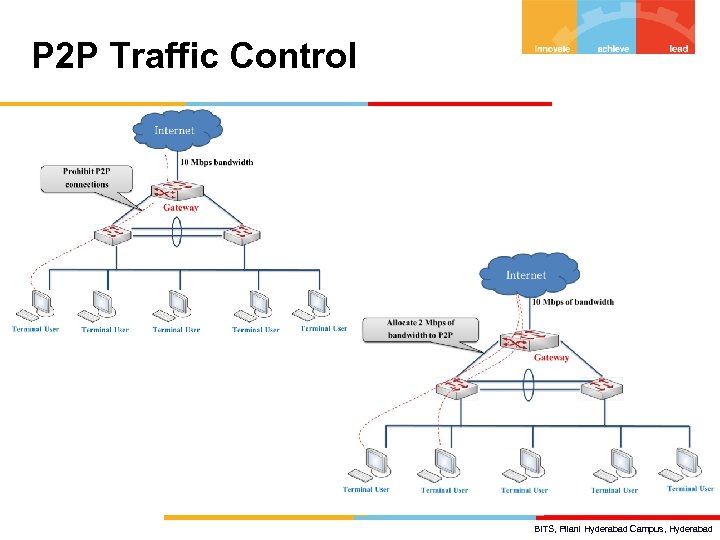 P 2 P Traffic Control BITS, Pilani Hyderabad Campus, Hyderabad
P 2 P Traffic Control BITS, Pilani Hyderabad Campus, Hyderabad
 Security Gap in P 2 P Peer A Peer B Protected Network Internet A TCP Port Peer X Malicious Peer C Firewall BITS, Pilani Hyderabad Campus, Hyderabad
Security Gap in P 2 P Peer A Peer B Protected Network Internet A TCP Port Peer X Malicious Peer C Firewall BITS, Pilani Hyderabad Campus, Hyderabad
 Effect of NATing on P 2 P Server Internet NAT P 2 P Application Private IP Addresses Public IP Addresses BITS, Pilani Hyderabad Campus, Hyderabad
Effect of NATing on P 2 P Server Internet NAT P 2 P Application Private IP Addresses Public IP Addresses BITS, Pilani Hyderabad Campus, Hyderabad
 NAT Traversal Application Relay Internet Private IP Addresses Public IP Addresses Private IP Addresses BITS, Pilani Hyderabad Campus, Hyderabad
NAT Traversal Application Relay Internet Private IP Addresses Public IP Addresses Private IP Addresses BITS, Pilani Hyderabad Campus, Hyderabad
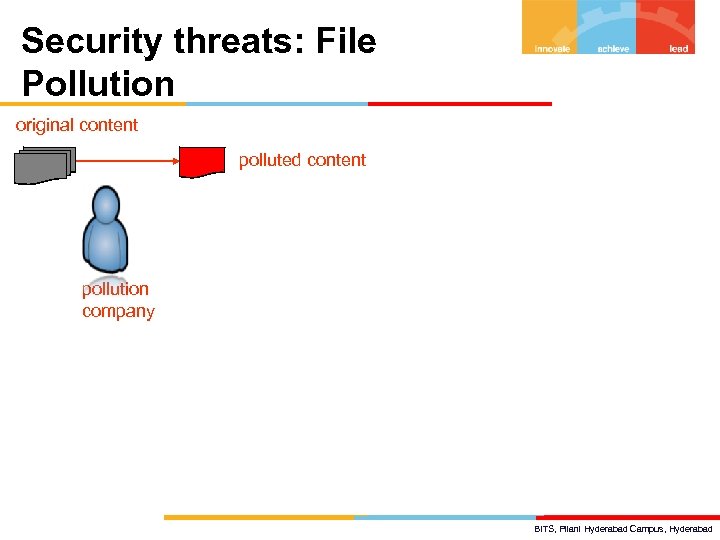 Security threats: File Pollution original content polluted content pollution company BITS, Pilani Hyderabad Campus, Hyderabad
Security threats: File Pollution original content polluted content pollution company BITS, Pilani Hyderabad Campus, Hyderabad
 File Pollution pollution server pollution company File sharing network pollution server BITS, Pilani Hyderabad Campus, Hyderabad
File Pollution pollution server pollution company File sharing network pollution server BITS, Pilani Hyderabad Campus, Hyderabad
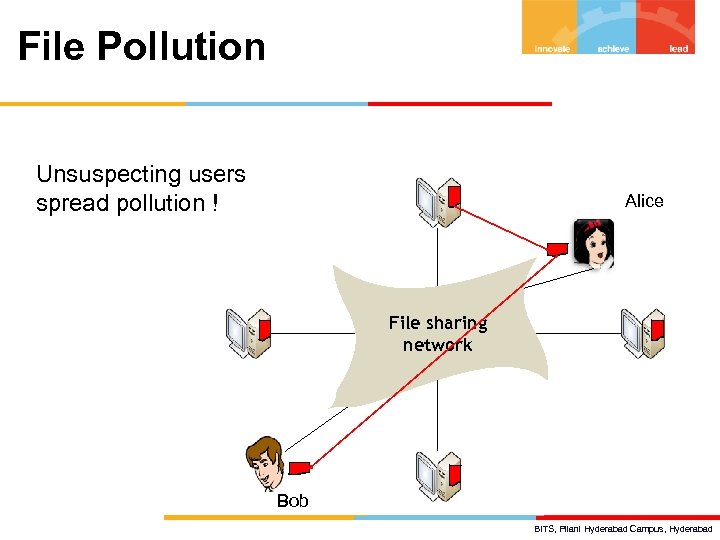 File Pollution Unsuspecting users spread pollution ! Alice File sharing network Bob BITS, Pilani Hyderabad Campus, Hyderabad
File Pollution Unsuspecting users spread pollution ! Alice File sharing network Bob BITS, Pilani Hyderabad Campus, Hyderabad
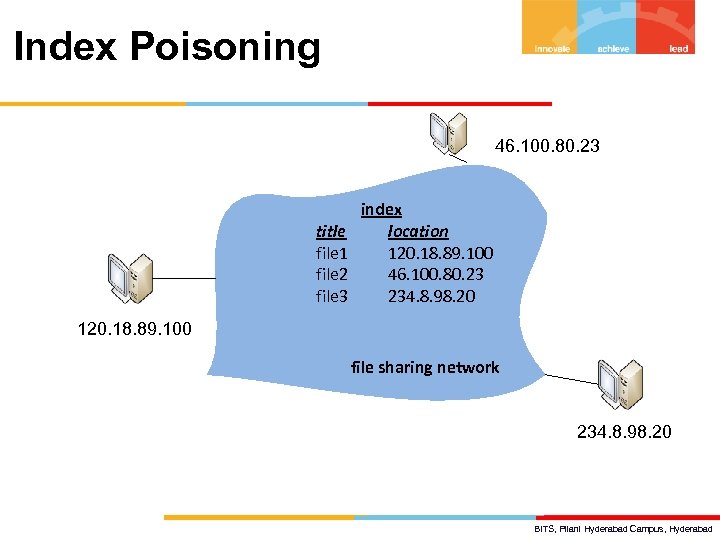 Index Poisoning 46. 100. 80. 23 title file 1 file 2 file 3 index location 120. 18. 89. 100 46. 100. 80. 23 234. 8. 98. 20 120. 18. 89. 100 file sharing network 234. 8. 98. 20 BITS, Pilani Hyderabad Campus, Hyderabad
Index Poisoning 46. 100. 80. 23 title file 1 file 2 file 3 index location 120. 18. 89. 100 46. 100. 80. 23 234. 8. 98. 20 120. 18. 89. 100 file sharing network 234. 8. 98. 20 BITS, Pilani Hyderabad Campus, Hyderabad
 Index Poisoning 46. 100. 80. 23 120. 18. 89. 100 title file 1 file 2 file 3 file 4 index location 120. 18. 89. 100 46. 100. 80. 23 234. 8. 98. 20 111. 22. 22 file sharing network 234. 8. 98. 20 111. 22. 22 BITS, Pilani Hyderabad Campus, Hyderabad
Index Poisoning 46. 100. 80. 23 120. 18. 89. 100 title file 1 file 2 file 3 file 4 index location 120. 18. 89. 100 46. 100. 80. 23 234. 8. 98. 20 111. 22. 22 file sharing network 234. 8. 98. 20 111. 22. 22 BITS, Pilani Hyderabad Campus, Hyderabad
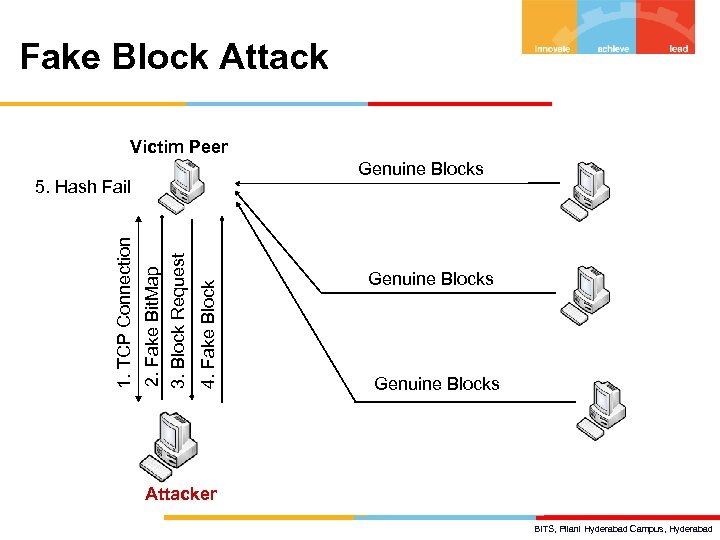 Fake Block Attack Victim Peer Genuine Blocks 4. Fake Block 2. Fake Bit. Map 3. Block Request 1. TCP Connection 5. Hash Fail Genuine Blocks Attacker BITS, Pilani Hyderabad Campus, Hyderabad
Fake Block Attack Victim Peer Genuine Blocks 4. Fake Block 2. Fake Bit. Map 3. Block Request 1. TCP Connection 5. Hash Fail Genuine Blocks Attacker BITS, Pilani Hyderabad Campus, Hyderabad
 Distributed Denial of Service BITS, Pilani Hyderabad Campus, Hyderabad
Distributed Denial of Service BITS, Pilani Hyderabad Campus, Hyderabad
 Node Insertion attack Victim peer A node insertion BITS, Pilani Hyderabad Campus, Hyderabad
Node Insertion attack Victim peer A node insertion BITS, Pilani Hyderabad Campus, Hyderabad
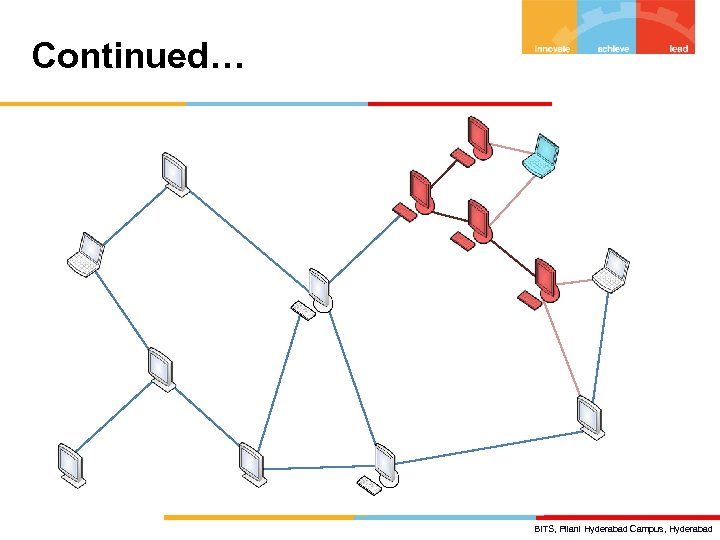 Continued… BITS, Pilani Hyderabad Campus, Hyderabad
Continued… BITS, Pilani Hyderabad Campus, Hyderabad
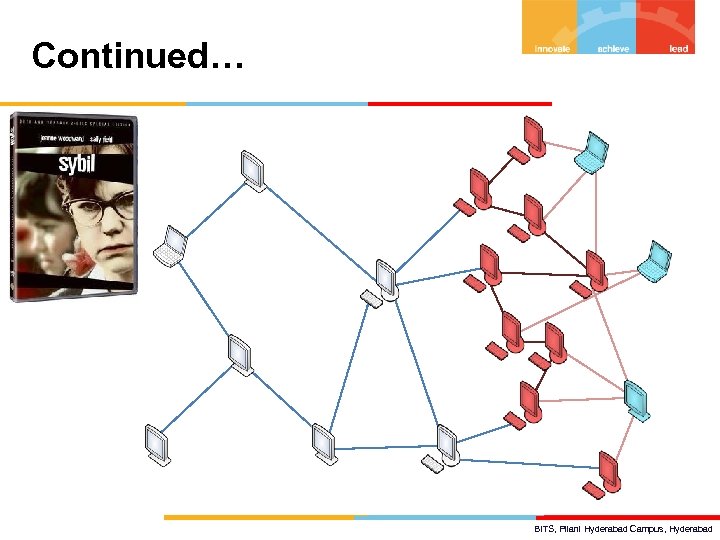 Continued… BITS, Pilani Hyderabad Campus, Hyderabad
Continued… BITS, Pilani Hyderabad Campus, Hyderabad
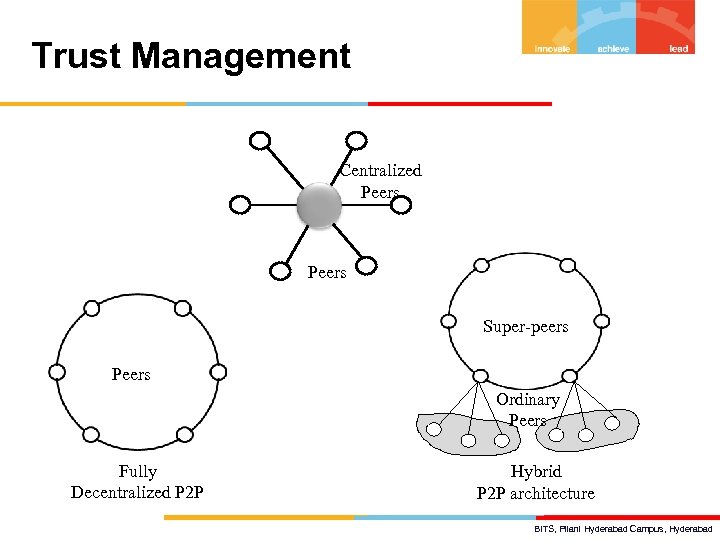 Trust Management Centralized Peers Super-peers Peers Ordinary Peers Fully Decentralized P 2 P Hybrid P 2 P architecture BITS, Pilani Hyderabad Campus, Hyderabad
Trust Management Centralized Peers Super-peers Peers Ordinary Peers Fully Decentralized P 2 P Hybrid P 2 P architecture BITS, Pilani Hyderabad Campus, Hyderabad
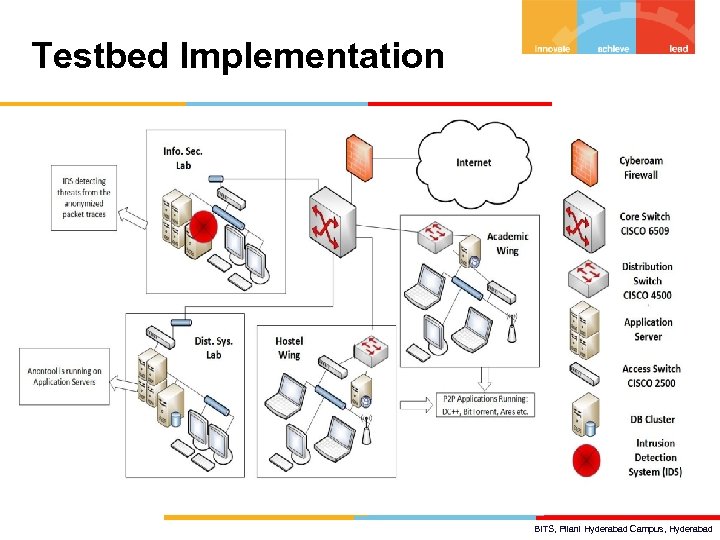 Testbed Implementation BITS, Pilani Hyderabad Campus, Hyderabad
Testbed Implementation BITS, Pilani Hyderabad Campus, Hyderabad
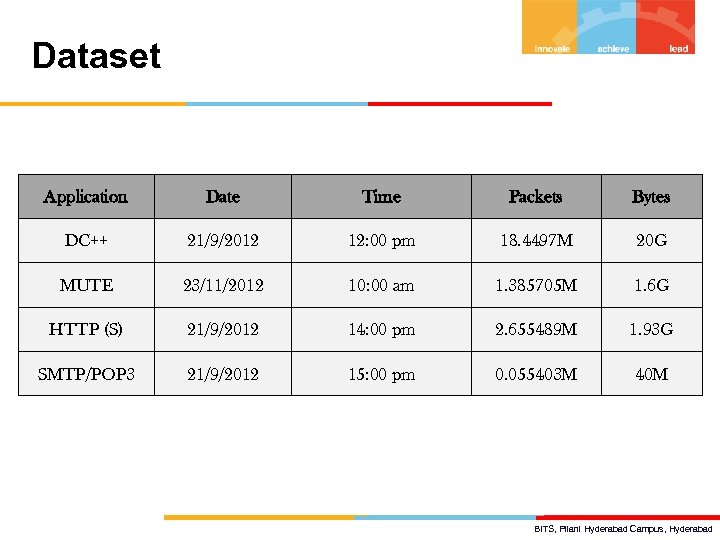 Dataset Application Date Time Packets Bytes DC++ 21/9/2012 12: 00 pm 18. 4497 M 20 G MUTE 23/11/2012 10: 00 am 1. 385705 M 1. 6 G HTTP (S) 21/9/2012 14: 00 pm 2. 655489 M 1. 93 G SMTP/POP 3 21/9/2012 15: 00 pm 0. 055403 M 40 M BITS, Pilani Hyderabad Campus, Hyderabad
Dataset Application Date Time Packets Bytes DC++ 21/9/2012 12: 00 pm 18. 4497 M 20 G MUTE 23/11/2012 10: 00 am 1. 385705 M 1. 6 G HTTP (S) 21/9/2012 14: 00 pm 2. 655489 M 1. 93 G SMTP/POP 3 21/9/2012 15: 00 pm 0. 055403 M 40 M BITS, Pilani Hyderabad Campus, Hyderabad
 Portscan using Metasploit BITS, Pilani Hyderabad Campus, Hyderabad
Portscan using Metasploit BITS, Pilani Hyderabad Campus, Hyderabad
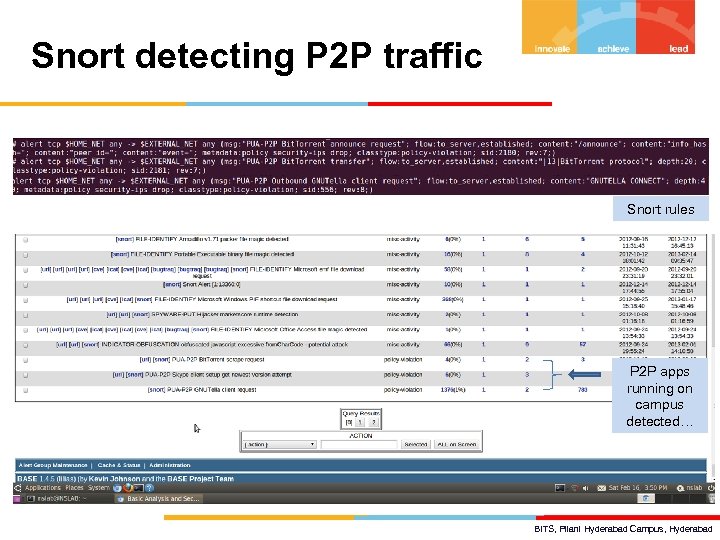 Snort detecting P 2 P traffic Snort rules P 2 P apps running on campus detected… BITS, Pilani Hyderabad Campus, Hyderabad
Snort detecting P 2 P traffic Snort rules P 2 P apps running on campus detected… BITS, Pilani Hyderabad Campus, Hyderabad
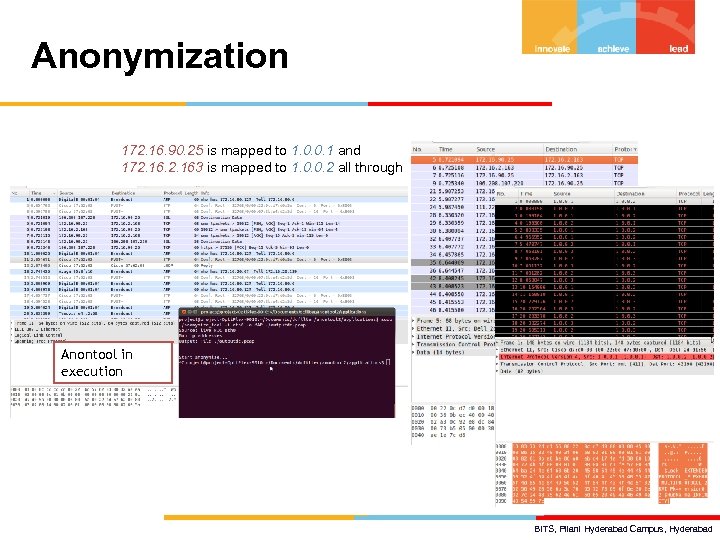 Anonymization 172. 16. 90. 25 is mapped to 1. 0. 0. 1 and 172. 163 is mapped to 1. 0. 0. 2 all through Anontool in execution BITS, Pilani Hyderabad Campus, Hyderabad
Anonymization 172. 16. 90. 25 is mapped to 1. 0. 0. 1 and 172. 163 is mapped to 1. 0. 0. 2 all through Anontool in execution BITS, Pilani Hyderabad Campus, Hyderabad
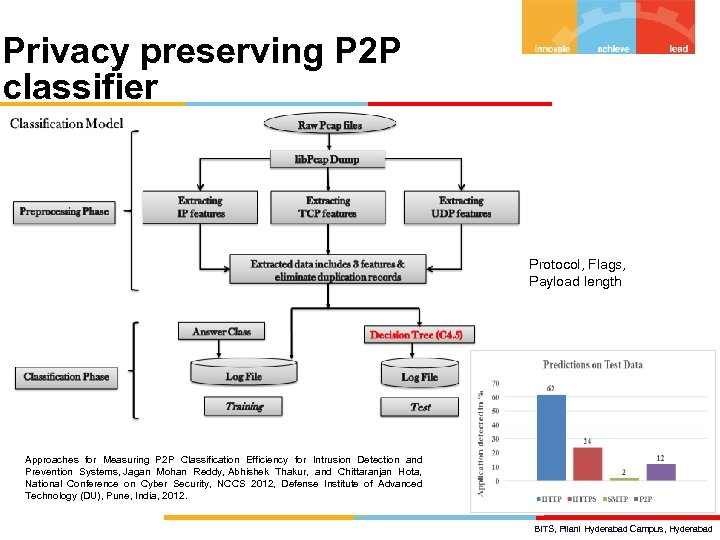 Privacy preserving P 2 P classifier Protocol, Flags, Payload length Approaches for Measuring P 2 P Classification Efficiency for Intrusion Detection and Prevention Systems, Jagan Mohan Reddy, Abhishek Thakur, and Chittaranjan Hota, National Conference on Cyber Security, NCCS 2012, Defense Institute of Advanced Technology (DU), Pune, India, 2012. BITS, Pilani Hyderabad Campus, Hyderabad
Privacy preserving P 2 P classifier Protocol, Flags, Payload length Approaches for Measuring P 2 P Classification Efficiency for Intrusion Detection and Prevention Systems, Jagan Mohan Reddy, Abhishek Thakur, and Chittaranjan Hota, National Conference on Cyber Security, NCCS 2012, Defense Institute of Advanced Technology (DU), Pune, India, 2012. BITS, Pilani Hyderabad Campus, Hyderabad
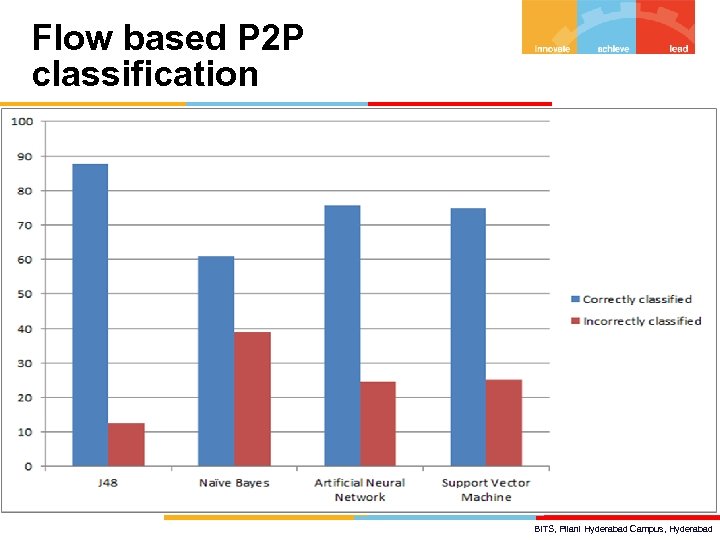 Flow based P 2 P classification Feature calculation BITS, Pilani Hyderabad Campus, Hyderabad
Flow based P 2 P classification Feature calculation BITS, Pilani Hyderabad Campus, Hyderabad
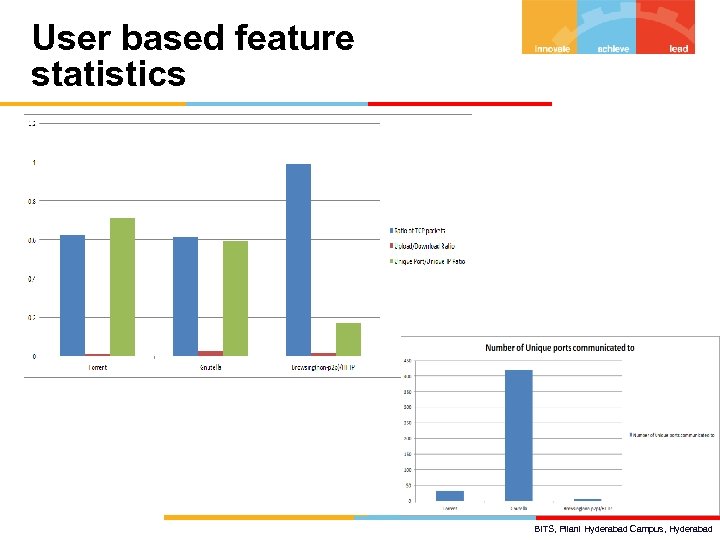 User based feature statistics BITS, Pilani Hyderabad Campus, Hyderabad
User based feature statistics BITS, Pilani Hyderabad Campus, Hyderabad
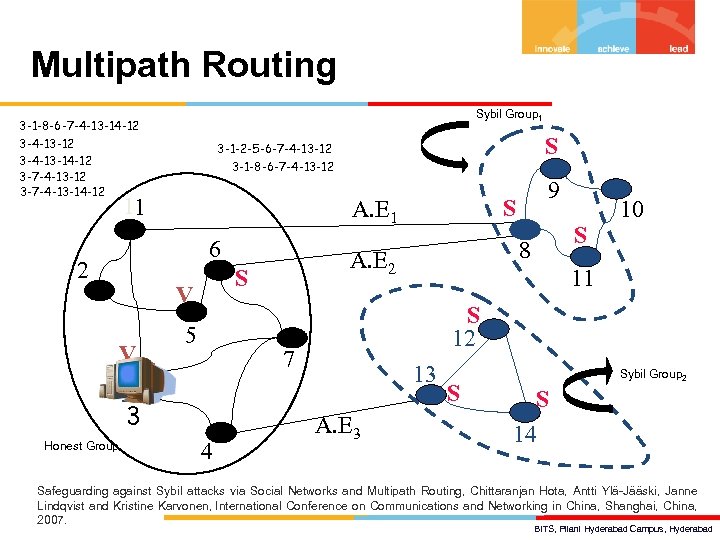 Multipath Routing Sybil Group 1 3 -1 -8 -6 -7 -4 -13 -14 -12 3 -4 -13 -14 -12 3 -7 -4 -13 -14 -12 11 V . V 5 Honest Group 4 10 11 S 12 7 3 3 S 8 A. E 2 S 9 S A. E 1 6 2 S 3 -1 -2 -5 -6 -7 -4 -13 -12 3 -1 -8 -6 -7 -4 -13 -12 13 A. E 3 S Sybil Group 2 S 14 Safeguarding against Sybil attacks via Social Networks and Multipath Routing, Chittaranjan Hota, Antti Ylä-Jääski, Janne Lindqvist and Kristine Karvonen, International Conference on Communications and Networking in China, Shanghai, China, 2007. BITS, Pilani Hyderabad Campus, Hyderabad
Multipath Routing Sybil Group 1 3 -1 -8 -6 -7 -4 -13 -14 -12 3 -4 -13 -14 -12 3 -7 -4 -13 -14 -12 11 V . V 5 Honest Group 4 10 11 S 12 7 3 3 S 8 A. E 2 S 9 S A. E 1 6 2 S 3 -1 -2 -5 -6 -7 -4 -13 -12 3 -1 -8 -6 -7 -4 -13 -12 13 A. E 3 S Sybil Group 2 S 14 Safeguarding against Sybil attacks via Social Networks and Multipath Routing, Chittaranjan Hota, Antti Ylä-Jääski, Janne Lindqvist and Kristine Karvonen, International Conference on Communications and Networking in China, Shanghai, China, 2007. BITS, Pilani Hyderabad Campus, Hyderabad
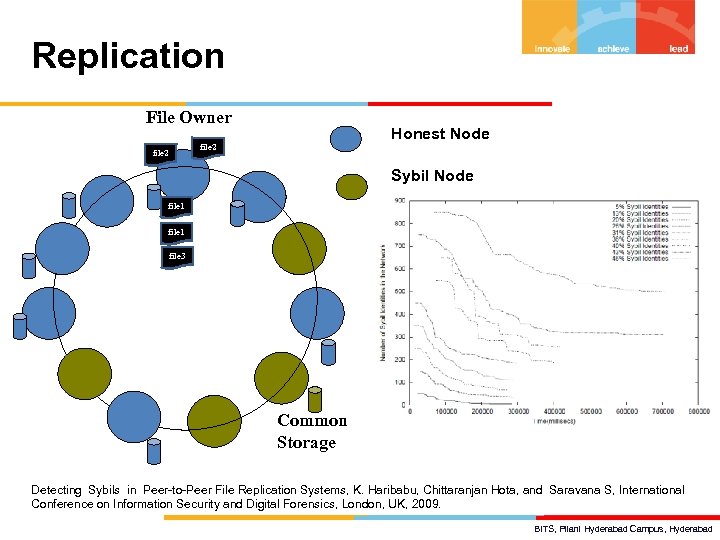 Replication File Owner file 2 Honest Node file 2 Sybil Node file 1 file 3 Common Storage Detecting Sybils in Peer-to-Peer File Replication Systems, K. Haribabu, Chittaranjan Hota, and Saravana S, International Conference on Information Security and Digital Forensics, London, UK, 2009. BITS, Pilani Hyderabad Campus, Hyderabad
Replication File Owner file 2 Honest Node file 2 Sybil Node file 1 file 3 Common Storage Detecting Sybils in Peer-to-Peer File Replication Systems, K. Haribabu, Chittaranjan Hota, and Saravana S, International Conference on Information Security and Digital Forensics, London, UK, 2009. BITS, Pilani Hyderabad Campus, Hyderabad
 Psychometric Analysis Detecting Sybils in P 2 P Overlays using Psychometric Analysis Methods, K Haribabu, Arindam Pal, Chittaranjan Hota, IEEE International Conference on Advanced Information Networking and Applications (AINA), Singapore, 2011. GAUR: A method to detect Sybil groups in Peer-to-Peer overlays, Haribabu K, Chittaranjan Hota, and A Paul, Int. J. Grid and Utility Computing, IJGUC, Vol. 3, Nos. 2/3, Inderscience, 2012. BITS Pilani, Hyderabad Campus
Psychometric Analysis Detecting Sybils in P 2 P Overlays using Psychometric Analysis Methods, K Haribabu, Arindam Pal, Chittaranjan Hota, IEEE International Conference on Advanced Information Networking and Applications (AINA), Singapore, 2011. GAUR: A method to detect Sybil groups in Peer-to-Peer overlays, Haribabu K, Chittaranjan Hota, and A Paul, Int. J. Grid and Utility Computing, IJGUC, Vol. 3, Nos. 2/3, Inderscience, 2012. BITS Pilani, Hyderabad Campus
 References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 19. 20. 21. 22. 23. 24. 25. 26. 27. 28. 29. 30. http: //news. netcraft. com/archives/2007/05/23/p 2 p_networks_hijacked_for_ddos_attacks. htm S Mcbride, and G A Flower, Estimate of Film-piracy cost soars: Hollywood loss is put at $6. 1 b a year, The Wall Street Journal Europe, may 4 th, 2006. Thomas Karagiannis, Andre Broido, Michalis Faloutsos, Kc claffy, Transport Layer Identification of P 2 P Traffic, in Proc. 4 th ACM SIGCOMM conference on Internet measurement, pp. 121 -134, 2004. Subhabrata Sen, Oliver Spatscheck, and Dongmei Wang, Accurate, Scalable In. Network Identification of P 2 P Traffic Using Application Signatures, WWW 2004, May 2004. S Sen, Jia Wang, Analyzing Peer-To-Peer Traffic Across Large Networks, IEEE/ACM Transactions on Networking, Vol. 12, No. 2, April 2004. Thuy T T N, and G Armitage, A survey of Techniques for Internet Traffic Classification using Machine Learning, IEEE Communications Surveys & Tutorials, Vol. 10, No. 4, 2008. Hassan Khan, S A Khayam, L Golubchik, M. Rajarajan, and Michael Orr, Wirespeed, Privacy-Preserving P 2 P Traffic Detection on Commodity Switches, Available Online at www. xflowresearch. com Intrusion detection system: At: http: //en. wikipedia. org/wiki/Intrusion_detection_system. P. Garcia-Teodoroa, J. Diaz-Verdejo, G. Macia-Fernandeza, and E. Vazquezb, Anomaly-based network intrusion detection: Techniques, systems and challenges, Computers and Security, vol. 28, Issue: 1 -2, pp. 18 -28, 2009. Gupta R, and Somani A K, Game theory as a tool to strategize as well as predict node’s behavior in peer-to-peer networks , International conf. on PDS, 2005, pp. 244 -249. Roberto G Cascella, 2 nd ENISA Workshop on Authentication Interoperability Languages held at the ENISA/EEMA European e. Identity conference, Paris, France, June 12 -13, 2007. C Wang, Li Chen, H Chen, and K Zhou, Incentive Mechanism Based on Game Theory in P 2 P Networks, ITCS 2010, pp. 190 -193. Sarraute, C. , et al. , Simulation of Computer Network Attacks, Core. Labs, Core Security Technologies, 2010. http: //www. metasploit. com/modules/exploit/multi/browser/java_atomicreferencearray www. metasploit. com/modules/auxiliary/dos/windows/rdp/ms 12_020_maxchannelids http: //www. metasploit. com/modules/exploit/windows/smb/ms 08_067_netapi Quinlan, J. R, C 4. 5: Programs for Machine Learning, Morgan Kaufmann Publishers, 1993. http: //www. cs. waikato. ac. nz/ml/weka/ http: //pytbull. sourceforge. net/ http: //www. secdev. org/projects/scapy Massicotte, F. and Labiche, Y, An analysis of signature overlaps in Intrusion Detection Systems, Dependable Systems & Networks (DSN) IEEE/IFIP 41 st International Conference, pp. 109 -120, 2011. Cheng-Yuan Ho, Yuan-Cheng Lai, I-Wei Chen, Fu-Yu Wang, and Wei-Hsuan Tai, Statistical analysis of false positives and false negatives from real traffic with intrusion detection/prevention systems, Communication Magazine, IEEE, pp. 146 -154, 2012. Sardar Ali, Hassan Khan, and Syed Ali Khayam, What is the Impact of P 2 P Traffic on Anomaly Detection? , Proceeding of 13 th International symposium, Recent Advances in Intrusion Detection (RAID) 2010, pp. 1 -7, 2010. Jeffrey Erman, et al. Identifying and Discriminating Between Web and Peer-to-Peer in the Network Core, WWW 2007, ACM, pp. 883 -892. Genevieve B, et al. , Estimating P 2 P traffic volume at USC, Technical Report, USC, June 2007. Alok Madhukar, Carey W, A Longitudinal Study of P 2 P Traffic Classification, IEEE International Symposium on Modeling, Analysis, and Simulation, CA, 2006, pp. 179 -188. Hongwei C, et al. , A SVM method for P 2 P traffic identification based on multiple traffic mode, Journal of Networks, Nov 2010, pp. 1381 -1388. K Ilgun, et al, State transition analysis: A rule based intrusion detection approach, IEEE transactions on software engineering, Vol 21, 1995. F Jemili, et al, A framework for an adaptive intrusion detection system using bayesian network, IEEE Intelligence and Security Informatics, May 2007, pp. 66 -70. BITS, Pilani Hyderabad Campus, Hyderabad
References 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. 16. 17. 18. 19. 20. 21. 22. 23. 24. 25. 26. 27. 28. 29. 30. http: //news. netcraft. com/archives/2007/05/23/p 2 p_networks_hijacked_for_ddos_attacks. htm S Mcbride, and G A Flower, Estimate of Film-piracy cost soars: Hollywood loss is put at $6. 1 b a year, The Wall Street Journal Europe, may 4 th, 2006. Thomas Karagiannis, Andre Broido, Michalis Faloutsos, Kc claffy, Transport Layer Identification of P 2 P Traffic, in Proc. 4 th ACM SIGCOMM conference on Internet measurement, pp. 121 -134, 2004. Subhabrata Sen, Oliver Spatscheck, and Dongmei Wang, Accurate, Scalable In. Network Identification of P 2 P Traffic Using Application Signatures, WWW 2004, May 2004. S Sen, Jia Wang, Analyzing Peer-To-Peer Traffic Across Large Networks, IEEE/ACM Transactions on Networking, Vol. 12, No. 2, April 2004. Thuy T T N, and G Armitage, A survey of Techniques for Internet Traffic Classification using Machine Learning, IEEE Communications Surveys & Tutorials, Vol. 10, No. 4, 2008. Hassan Khan, S A Khayam, L Golubchik, M. Rajarajan, and Michael Orr, Wirespeed, Privacy-Preserving P 2 P Traffic Detection on Commodity Switches, Available Online at www. xflowresearch. com Intrusion detection system: At: http: //en. wikipedia. org/wiki/Intrusion_detection_system. P. Garcia-Teodoroa, J. Diaz-Verdejo, G. Macia-Fernandeza, and E. Vazquezb, Anomaly-based network intrusion detection: Techniques, systems and challenges, Computers and Security, vol. 28, Issue: 1 -2, pp. 18 -28, 2009. Gupta R, and Somani A K, Game theory as a tool to strategize as well as predict node’s behavior in peer-to-peer networks , International conf. on PDS, 2005, pp. 244 -249. Roberto G Cascella, 2 nd ENISA Workshop on Authentication Interoperability Languages held at the ENISA/EEMA European e. Identity conference, Paris, France, June 12 -13, 2007. C Wang, Li Chen, H Chen, and K Zhou, Incentive Mechanism Based on Game Theory in P 2 P Networks, ITCS 2010, pp. 190 -193. Sarraute, C. , et al. , Simulation of Computer Network Attacks, Core. Labs, Core Security Technologies, 2010. http: //www. metasploit. com/modules/exploit/multi/browser/java_atomicreferencearray www. metasploit. com/modules/auxiliary/dos/windows/rdp/ms 12_020_maxchannelids http: //www. metasploit. com/modules/exploit/windows/smb/ms 08_067_netapi Quinlan, J. R, C 4. 5: Programs for Machine Learning, Morgan Kaufmann Publishers, 1993. http: //www. cs. waikato. ac. nz/ml/weka/ http: //pytbull. sourceforge. net/ http: //www. secdev. org/projects/scapy Massicotte, F. and Labiche, Y, An analysis of signature overlaps in Intrusion Detection Systems, Dependable Systems & Networks (DSN) IEEE/IFIP 41 st International Conference, pp. 109 -120, 2011. Cheng-Yuan Ho, Yuan-Cheng Lai, I-Wei Chen, Fu-Yu Wang, and Wei-Hsuan Tai, Statistical analysis of false positives and false negatives from real traffic with intrusion detection/prevention systems, Communication Magazine, IEEE, pp. 146 -154, 2012. Sardar Ali, Hassan Khan, and Syed Ali Khayam, What is the Impact of P 2 P Traffic on Anomaly Detection? , Proceeding of 13 th International symposium, Recent Advances in Intrusion Detection (RAID) 2010, pp. 1 -7, 2010. Jeffrey Erman, et al. Identifying and Discriminating Between Web and Peer-to-Peer in the Network Core, WWW 2007, ACM, pp. 883 -892. Genevieve B, et al. , Estimating P 2 P traffic volume at USC, Technical Report, USC, June 2007. Alok Madhukar, Carey W, A Longitudinal Study of P 2 P Traffic Classification, IEEE International Symposium on Modeling, Analysis, and Simulation, CA, 2006, pp. 179 -188. Hongwei C, et al. , A SVM method for P 2 P traffic identification based on multiple traffic mode, Journal of Networks, Nov 2010, pp. 1381 -1388. K Ilgun, et al, State transition analysis: A rule based intrusion detection approach, IEEE transactions on software engineering, Vol 21, 1995. F Jemili, et al, A framework for an adaptive intrusion detection system using bayesian network, IEEE Intelligence and Security Informatics, May 2007, pp. 66 -70. BITS, Pilani Hyderabad Campus, Hyderabad
 Thank You! BITS, Pilani Hyderabad Campus, Hyderabad
Thank You! BITS, Pilani Hyderabad Campus, Hyderabad


