ef8bf70965212b9a155f68a133bb58e4.ppt
- Количество слайдов: 34
 PCI: DSS What is it, and what does it mean to you? Dale Pearson 17 th November 2009
PCI: DSS What is it, and what does it mean to you? Dale Pearson 17 th November 2009
 Today’s Presentation • • • Security Stats Why PCI: DSS What does PCI: DSS mean to you Steps to becoming compliant Tips and Take Aways Question Time
Today’s Presentation • • • Security Stats Why PCI: DSS What does PCI: DSS mean to you Steps to becoming compliant Tips and Take Aways Question Time
 About Me • • Founder – Security Active Security Manager – Atos Origin Senior Security and Risk Consultant – Zurich Global Network & Security Architect – GE • • Security Research Presenting / Lecturing Security Bloggers Meet Up Blogging / Podcasting / Twittering Consulting / Education / Awareness Ethical Hacker. Net Board of Advisors Hackers for Charity / i. T 4 Communities
About Me • • Founder – Security Active Security Manager – Atos Origin Senior Security and Risk Consultant – Zurich Global Network & Security Architect – GE • • Security Research Presenting / Lecturing Security Bloggers Meet Up Blogging / Podcasting / Twittering Consulting / Education / Awareness Ethical Hacker. Net Board of Advisors Hackers for Charity / i. T 4 Communities
 Security Stats are from the Verizon Business Data Breach Investigations Report http: //www. verizonbusiness. com/resources/security/databreachreport. pdf
Security Stats are from the Verizon Business Data Breach Investigations Report http: //www. verizonbusiness. com/resources/security/databreachreport. pdf
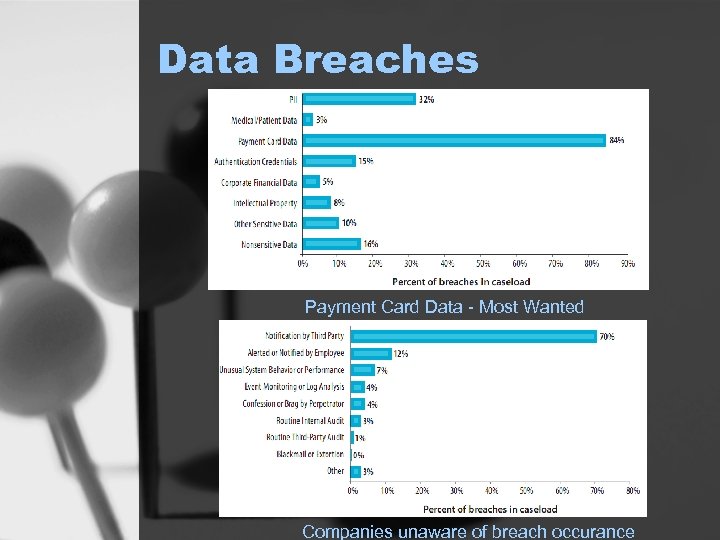 Data Breaches Payment Card Data - Most Wanted Companies unaware of breach occurance
Data Breaches Payment Card Data - Most Wanted Companies unaware of breach occurance
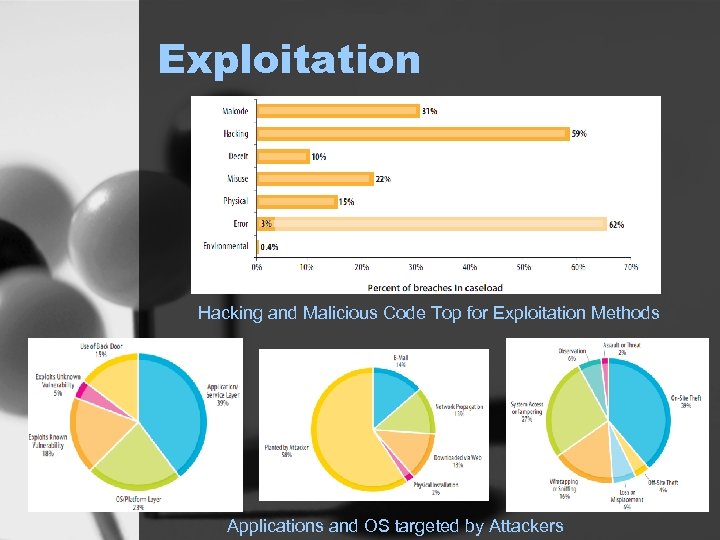 Exploitation Hacking and Malicious Code Top for Exploitation Methods Applications and OS targeted by Attackers
Exploitation Hacking and Malicious Code Top for Exploitation Methods Applications and OS targeted by Attackers
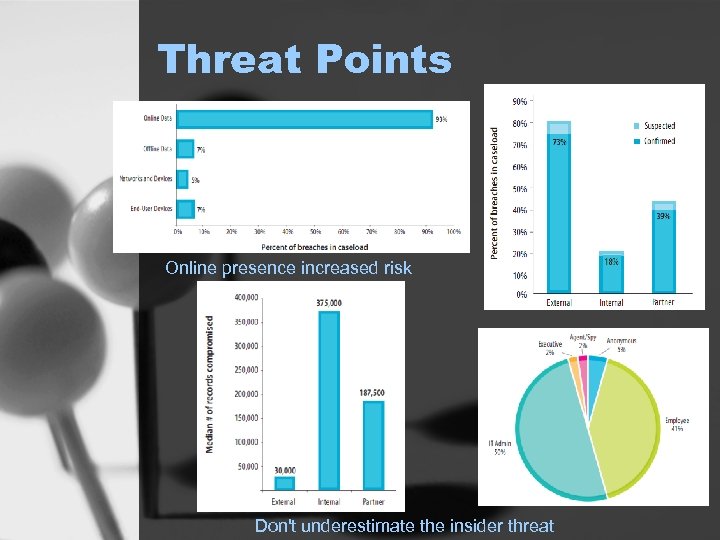 Threat Points Online presence increased risk Don't underestimate the insider threat
Threat Points Online presence increased risk Don't underestimate the insider threat
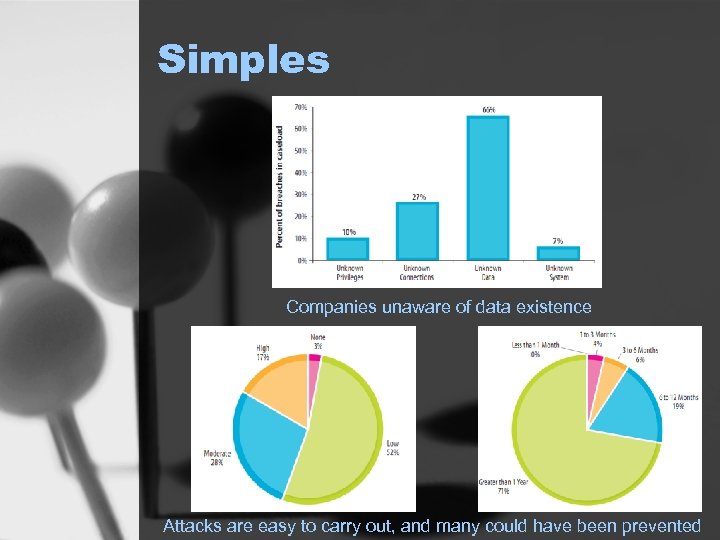 Simples Companies unaware of data existence Attacks are easy to carry out, and many could have been prevented
Simples Companies unaware of data existence Attacks are easy to carry out, and many could have been prevented
 Why PCI: DSS ? ?
Why PCI: DSS ? ?
 In the Media
In the Media
 The Creation of PCI: DSS • Payment Card Industry : Data Security Standard • Card Fraud pushed to an unsustainable level • Security of information is an important factor to protect against financial loss, as well as reputational loss • PCI: DSS is the card schemes response • Secure transmission, storage and processing of card holder data. • Coverage of systems, policies, and procedures
The Creation of PCI: DSS • Payment Card Industry : Data Security Standard • Card Fraud pushed to an unsustainable level • Security of information is an important factor to protect against financial loss, as well as reputational loss • PCI: DSS is the card schemes response • Secure transmission, storage and processing of card holder data. • Coverage of systems, policies, and procedures
 What's it all about? • • • Increase security of card holder data Coverage of entire payments process Backing from the card schemes and banks Compliance is mandatory Based on best practice Over 232 controls in 12 areas • June 2005 Deadline • July 2007 Deadline • All merchants to define a compliance date • 18% of companies in the UK are compliant
What's it all about? • • • Increase security of card holder data Coverage of entire payments process Backing from the card schemes and banks Compliance is mandatory Based on best practice Over 232 controls in 12 areas • June 2005 Deadline • July 2007 Deadline • All merchants to define a compliance date • 18% of companies in the UK are compliant
 What can PCI: DSS Do For You? • • • Brand reputation protection Framework to build upon Understanding of information in your business Improved security controls Documented and formalised process and policy Acceptance and reduction of risk Competitive edge Reduced processing costs Avoid fines and legal costs Continue accepting cards Safe Harbour
What can PCI: DSS Do For You? • • • Brand reputation protection Framework to build upon Understanding of information in your business Improved security controls Documented and formalised process and policy Acceptance and reduction of risk Competitive edge Reduced processing costs Avoid fines and legal costs Continue accepting cards Safe Harbour
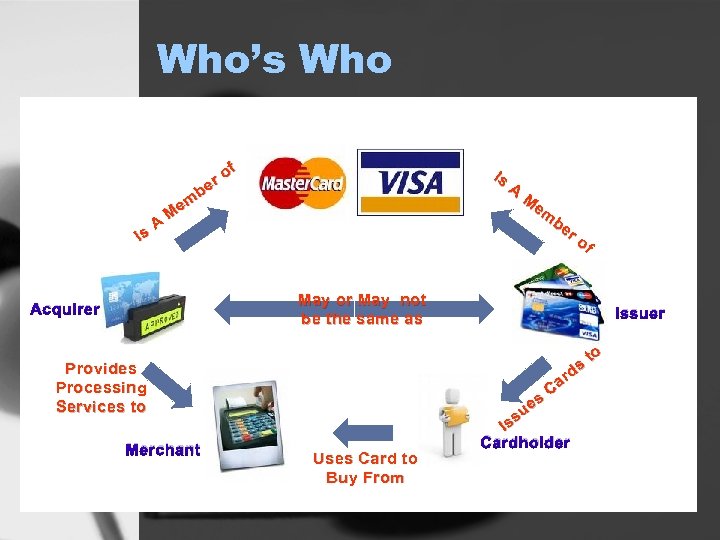 Who’s Who Is A f ro be em M Is A M em be ro f May or May not be the same as Acquirer s rd Ca Provides Processing Services to Merchant Issuer Uses Card to Buy From s ue s Is Cardholder to
Who’s Who Is A f ro be em M Is A M em be ro f May or May not be the same as Acquirer s rd Ca Provides Processing Services to Merchant Issuer Uses Card to Buy From s ue s Is Cardholder to
 What does PCI: DSS mean to you?
What does PCI: DSS mean to you?
 PCI: SS Requirements Build and Maintain a Secure Network • Install and maintain a firewall configuration to protect cardholder data • Do not use vendor-supplied defaults for system passwords and other parameters Protect Cardholder Data • Protect stored cardholder data • Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program • Use and regularly update anti-virus software • Develop and maintain secure systems and applications
PCI: SS Requirements Build and Maintain a Secure Network • Install and maintain a firewall configuration to protect cardholder data • Do not use vendor-supplied defaults for system passwords and other parameters Protect Cardholder Data • Protect stored cardholder data • Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program • Use and regularly update anti-virus software • Develop and maintain secure systems and applications
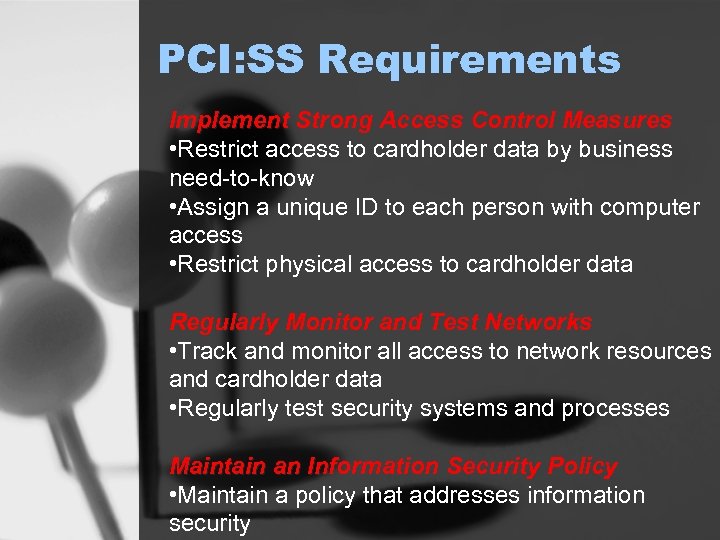 PCI: SS Requirements Implement Strong Access Control Measures • Restrict access to cardholder data by business need-to-know • Assign a unique ID to each person with computer access • Restrict physical access to cardholder data Regularly Monitor and Test Networks • Track and monitor all access to network resources and cardholder data • Regularly test security systems and processes Maintain an Information Security Policy • Maintain a policy that addresses information security
PCI: SS Requirements Implement Strong Access Control Measures • Restrict access to cardholder data by business need-to-know • Assign a unique ID to each person with computer access • Restrict physical access to cardholder data Regularly Monitor and Test Networks • Track and monitor all access to network resources and cardholder data • Regularly test security systems and processes Maintain an Information Security Policy • Maintain a policy that addresses information security
 Steps to becoming Compliant
Steps to becoming Compliant
 Merchant Requirements
Merchant Requirements
 Self Assessment Questionnaire • • Subset of the full Onsite Audit Criteria Completed by the merchant Submitted to the Acquirer Made up of Yes / Not Applicable responses • Broken up into the six sections of requirement
Self Assessment Questionnaire • • Subset of the full Onsite Audit Criteria Completed by the merchant Submitted to the Acquirer Made up of Yes / Not Applicable responses • Broken up into the six sections of requirement
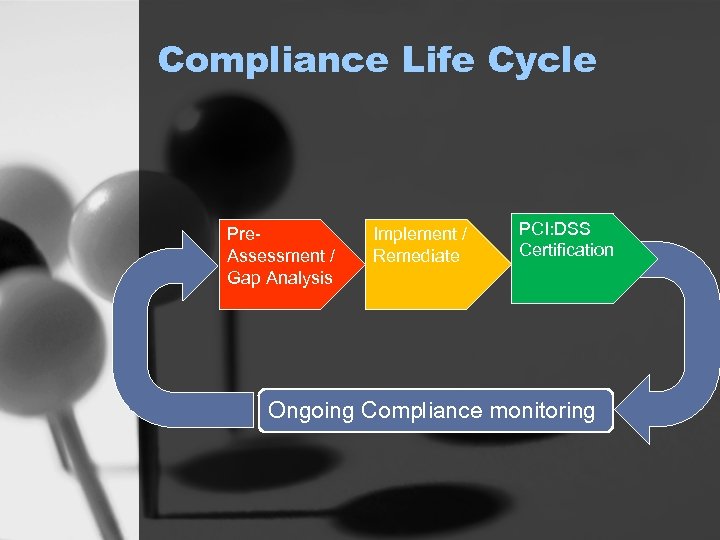 Compliance Life Cycle Pre. Assessment / Gap Analysis Implement / Remediate PCI: DSS Certification Ongoing Compliance monitoring
Compliance Life Cycle Pre. Assessment / Gap Analysis Implement / Remediate PCI: DSS Certification Ongoing Compliance monitoring
 Road to compliance • Senior Manager Support • Understand the task at hand • Identify applications and locations of cardholder data • Produce network diagrams and data flows • Identify compliance gaps to the 12 requirements • Obtain required expertise • Establish the scope for compliance • Engage with 3 rd parties • Conduct vulnerability scans • Prioritise remediation activities • Clarify compliance on submission of SAQ
Road to compliance • Senior Manager Support • Understand the task at hand • Identify applications and locations of cardholder data • Produce network diagrams and data flows • Identify compliance gaps to the 12 requirements • Obtain required expertise • Establish the scope for compliance • Engage with 3 rd parties • Conduct vulnerability scans • Prioritise remediation activities • Clarify compliance on submission of SAQ
 Key Controls Systems / Technology • Network Segmentation • System Hardening • Encryption • Anti-Virus / Anti-Malware • Access Controls • Password Controls • Physical Access Controls • Centralized Logging • File Integrity Monitoring • IDS / IPS • Scanning (Wireless & Vulnerabilities)
Key Controls Systems / Technology • Network Segmentation • System Hardening • Encryption • Anti-Virus / Anti-Malware • Access Controls • Password Controls • Physical Access Controls • Centralized Logging • File Integrity Monitoring • IDS / IPS • Scanning (Wireless & Vulnerabilities)
 Key Controls Procedures • Systems Build • Encryption Key Management • Secure Applications Development • Security Testing (Vuln Scanning & Pen Tests) • Log Review • Annual Risk Assessment • Policies / Procedures Annual Review & Issue • Security Awareness • Incident Response Annual Testing People • Background Checks, Security Awareness
Key Controls Procedures • Systems Build • Encryption Key Management • Secure Applications Development • Security Testing (Vuln Scanning & Pen Tests) • Log Review • Annual Risk Assessment • Policies / Procedures Annual Review & Issue • Security Awareness • Incident Response Annual Testing People • Background Checks, Security Awareness
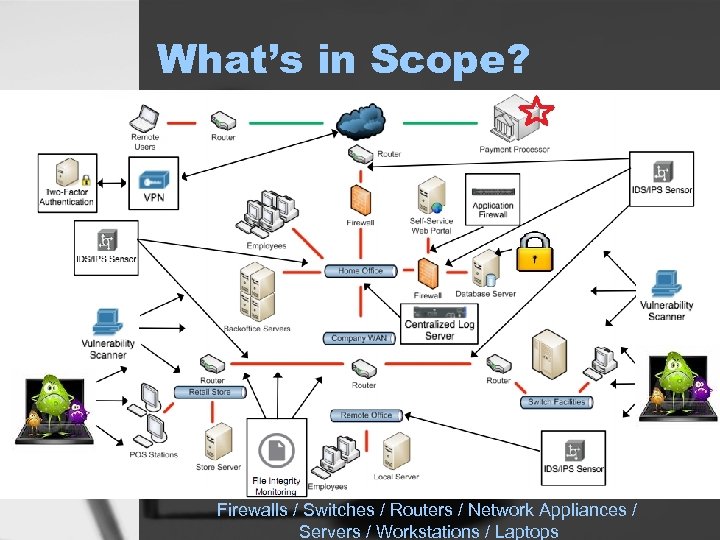 What’s in Scope? Firewalls / Switches / Routers / Network Appliances / Servers / Workstations / Laptops
What’s in Scope? Firewalls / Switches / Routers / Network Appliances / Servers / Workstations / Laptops
 PA-DSS Payment Application Data Security Standard • Based on Visa’s (Payment Application Best Practices) Required 1 st July 2010 Purpose and scope • Payment applications must facilitate (not prevent) PCI: DSS compliance • Applies only to payment applications developed by 3 rd parties Goals for Software Development • Application must not retain mag stripe data • Application must encrypt cardholder data • Guidance for PCI: DSS compliant implementation
PA-DSS Payment Application Data Security Standard • Based on Visa’s (Payment Application Best Practices) Required 1 st July 2010 Purpose and scope • Payment applications must facilitate (not prevent) PCI: DSS compliance • Applies only to payment applications developed by 3 rd parties Goals for Software Development • Application must not retain mag stripe data • Application must encrypt cardholder data • Guidance for PCI: DSS compliant implementation
 QSA Review / Assessment • Detailed audit against PCI: DSS • Targets all systems and networks storing, processing or transmitting cardholder data • Review of contractual relationships • Performed by a VISA certified provider (QSA) • Report on compliance submitted to Acquirer
QSA Review / Assessment • Detailed audit against PCI: DSS • Targets all systems and networks storing, processing or transmitting cardholder data • Review of contractual relationships • Performed by a VISA certified provider (QSA) • Report on compliance submitted to Acquirer
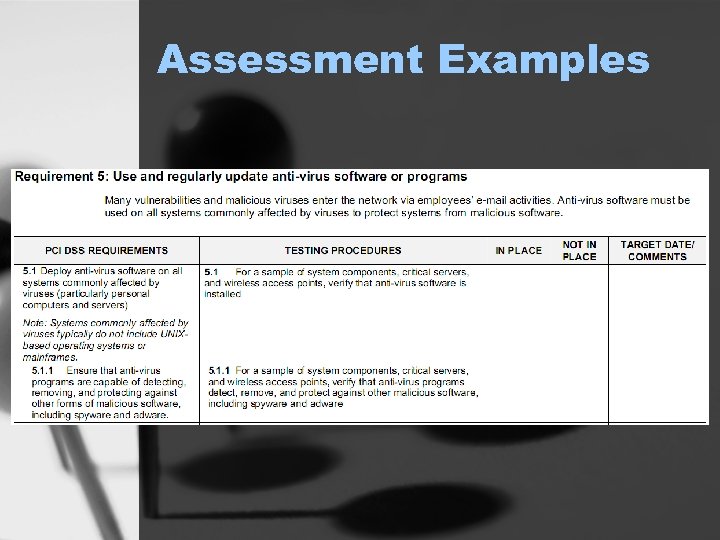 Assessment Examples
Assessment Examples
 Common Compliance Issues • • • Scoping of project is to large Flat network and no segmentation Legacy systems, and non compliant software Lack of knowledge to interpret controls Lack of formal processes and procedures Confusion of systems scoping Storage, processing and transmitting of data with no business requirement Non compliant 3 rd parties Significant cost to full compliance Evaluation of compensating controls
Common Compliance Issues • • • Scoping of project is to large Flat network and no segmentation Legacy systems, and non compliant software Lack of knowledge to interpret controls Lack of formal processes and procedures Confusion of systems scoping Storage, processing and transmitting of data with no business requirement Non compliant 3 rd parties Significant cost to full compliance Evaluation of compensating controls
 Consequence of non compliance • • Monthly fine for non compliance Increased cost for processing cards Damage to brand reputation Customers sue for negligence Increased risk of security breach Costly investigative charges No safe harbour Acquirer refuses to allow card processing
Consequence of non compliance • • Monthly fine for non compliance Increased cost for processing cards Damage to brand reputation Customers sue for negligence Increased risk of security breach Costly investigative charges No safe harbour Acquirer refuses to allow card processing
 Misconceptions • Self assessment means your compliant • Compliance means you wont suffer a breach • Outsourcing takes away your need for compliance • PCI: DSS is just about IT • A single product can make you compliant • Compliance can be automated
Misconceptions • Self assessment means your compliant • Compliance means you wont suffer a breach • Outsourcing takes away your need for compliance • PCI: DSS is just about IT • A single product can make you compliant • Compliance can be automated
 Tips and Take Aways • • • Reduce your scope Ensure senior buy in Prioritise Tasks – High Medium Low Be honest and open about card holder data existence Maintain the good security practices Go beyond card data systems Be proactive with checks and controls No single product equals compliance Make someone responsible for managing compliance
Tips and Take Aways • • • Reduce your scope Ensure senior buy in Prioritise Tasks – High Medium Low Be honest and open about card holder data existence Maintain the good security practices Go beyond card data systems Be proactive with checks and controls No single product equals compliance Make someone responsible for managing compliance
 Online Documentation • PCI: DSS Standard v 1. 2 https: //www. pcisecuritystandards. org/saq/docs/aoc_saq_d_merchants. doc • Approved QSA List https: //www. pcisecuritystandards. org/pdfs/pci_qsa_list. pdf • PCI Prioritized Approach https: //www. pcisecuritystandards. org/education/prioritized. shtml
Online Documentation • PCI: DSS Standard v 1. 2 https: //www. pcisecuritystandards. org/saq/docs/aoc_saq_d_merchants. doc • Approved QSA List https: //www. pcisecuritystandards. org/pdfs/pci_qsa_list. pdf • PCI Prioritized Approach https: //www. pcisecuritystandards. org/education/prioritized. shtml
 Q&A Thank You. Dale Pearson 07770 373 586 dale. pearson@securityactive. co. uk
Q&A Thank You. Dale Pearson 07770 373 586 dale. pearson@securityactive. co. uk


