b8ca7b7f6254745ebb25824117c83b38.ppt
- Количество слайдов: 32
 Payment Card Industry (PCI) Data Security Standards (DSS) Challenges and Issues for z. Series Systems Vanguard Integrity Professionals www. go 2 vanguard. com October 2012 1
Payment Card Industry (PCI) Data Security Standards (DSS) Challenges and Issues for z. Series Systems Vanguard Integrity Professionals www. go 2 vanguard. com October 2012 1
 Overview Session Overview The PCI Data Security Standards apply to any company that transmits, processes or stores credit card “cardholder” data. While many companies are exempt from PCI, companies are not exempt from protecting their sensitive data which includes customer, company confidential and Personally Identifiable Information (PII). This presentation provides an overview of the PCI Data Security Requirements, why they evolved, why they are important and how the requirements can leveraged by all companies to improve their overall compliance program. Several of the requirements will be discussed in detail, the “hidden meaning” of the requirement will be revealed, and examples will be provided showing how RACF controls can be implemented, and supporting evidence collected, to demonstrate compliance. 2
Overview Session Overview The PCI Data Security Standards apply to any company that transmits, processes or stores credit card “cardholder” data. While many companies are exempt from PCI, companies are not exempt from protecting their sensitive data which includes customer, company confidential and Personally Identifiable Information (PII). This presentation provides an overview of the PCI Data Security Requirements, why they evolved, why they are important and how the requirements can leveraged by all companies to improve their overall compliance program. Several of the requirements will be discussed in detail, the “hidden meaning” of the requirement will be revealed, and examples will be provided showing how RACF controls can be implemented, and supporting evidence collected, to demonstrate compliance. 2
 The Problem: Credit Card Breaches As long as we have a Black Market for Credit Cards, we’ll continue to have Cardholder Breaches Albert Gonzalez, dubbed his operation: “Operation Get Rich or Die Tryin’” Convicted for breaches at: TJX Corp (45 M) Heartland Payment Systems (100 M) Hannaford Bros Co (4. 2 M) 7 -Eleven (TBD) 2 Unidentified Companies (TBD) Albert also infiltrated these companies for over 40 million cards: BJ's Wholesale Club Barnes & Noble Inc Office Max Dave & Buster's DSW shoe stores Forever 21 3
The Problem: Credit Card Breaches As long as we have a Black Market for Credit Cards, we’ll continue to have Cardholder Breaches Albert Gonzalez, dubbed his operation: “Operation Get Rich or Die Tryin’” Convicted for breaches at: TJX Corp (45 M) Heartland Payment Systems (100 M) Hannaford Bros Co (4. 2 M) 7 -Eleven (TBD) 2 Unidentified Companies (TBD) Albert also infiltrated these companies for over 40 million cards: BJ's Wholesale Club Barnes & Noble Inc Office Max Dave & Buster's DSW shoe stores Forever 21 3
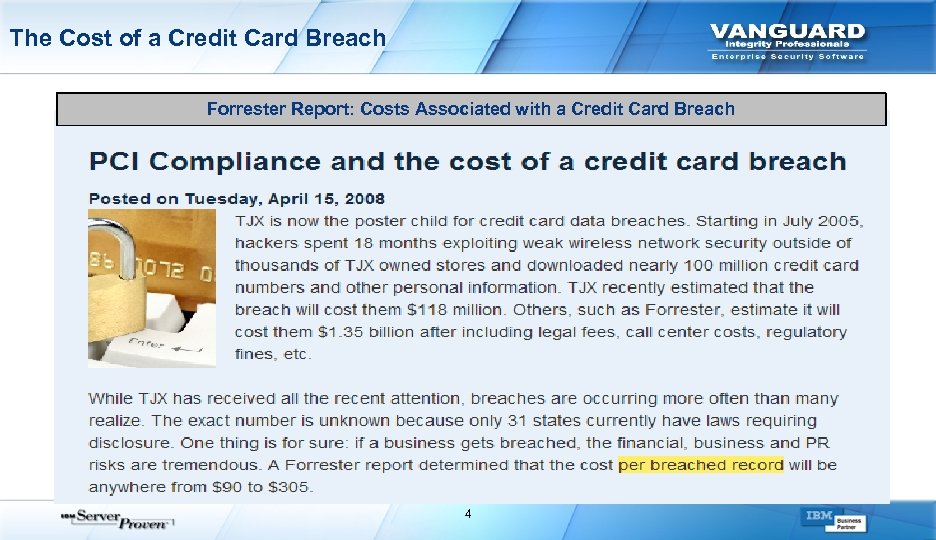 The Cost of a Credit Card Breach Forrester Report: Costs Associated with a Credit Card Breach 4
The Cost of a Credit Card Breach Forrester Report: Costs Associated with a Credit Card Breach 4
 The PCI DSS Infrastructure The PCI Security Council, Sponsoring Organizations, QSA’s and PFI’s PCI Security Council & Sponsoring Organizations: Qualified Security Assessor (QSA): (264 companies as of August 2011) PCI Forensic Investigator (PFI): (15 companies as of August 2011) 5
The PCI DSS Infrastructure The PCI Security Council, Sponsoring Organizations, QSA’s and PFI’s PCI Security Council & Sponsoring Organizations: Qualified Security Assessor (QSA): (264 companies as of August 2011) PCI Forensic Investigator (PFI): (15 companies as of August 2011) 5
 Top PCI Challenges for z. Series Systems Challenges 1. Interpreting PCI DSS for z. Series Systems 6
Top PCI Challenges for z. Series Systems Challenges 1. Interpreting PCI DSS for z. Series Systems 6
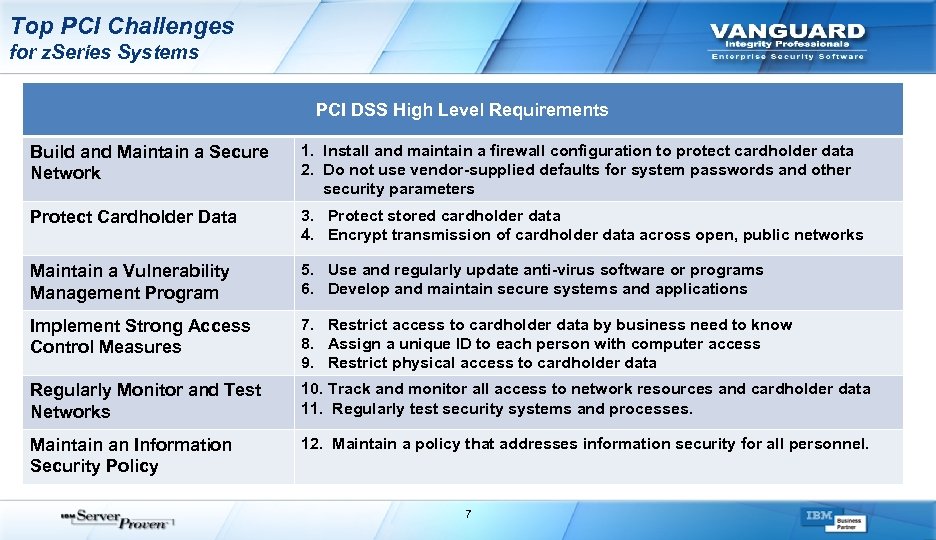 Top PCI Challenges for z. Series Systems PCI DSS High Level Requirements Build and Maintain a Secure Network 1. Install and maintain a firewall configuration to protect cardholder data 2. Do not use vendor-supplied defaults for system passwords and other security parameters Protect Cardholder Data 3. Protect stored cardholder data 4. Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program 5. Use and regularly update anti-virus software or programs 6. Develop and maintain secure systems and applications Implement Strong Access Control Measures 7. Restrict access to cardholder data by business need to know 8. Assign a unique ID to each person with computer access 9. Restrict physical access to cardholder data Regularly Monitor and Test Networks 10. Track and monitor all access to network resources and cardholder data 11. Regularly test security systems and processes. Maintain an Information Security Policy 12. Maintain a policy that addresses information security for all personnel. 7
Top PCI Challenges for z. Series Systems PCI DSS High Level Requirements Build and Maintain a Secure Network 1. Install and maintain a firewall configuration to protect cardholder data 2. Do not use vendor-supplied defaults for system passwords and other security parameters Protect Cardholder Data 3. Protect stored cardholder data 4. Encrypt transmission of cardholder data across open, public networks Maintain a Vulnerability Management Program 5. Use and regularly update anti-virus software or programs 6. Develop and maintain secure systems and applications Implement Strong Access Control Measures 7. Restrict access to cardholder data by business need to know 8. Assign a unique ID to each person with computer access 9. Restrict physical access to cardholder data Regularly Monitor and Test Networks 10. Track and monitor all access to network resources and cardholder data 11. Regularly test security systems and processes. Maintain an Information Security Policy 12. Maintain a policy that addresses information security for all personnel. 7
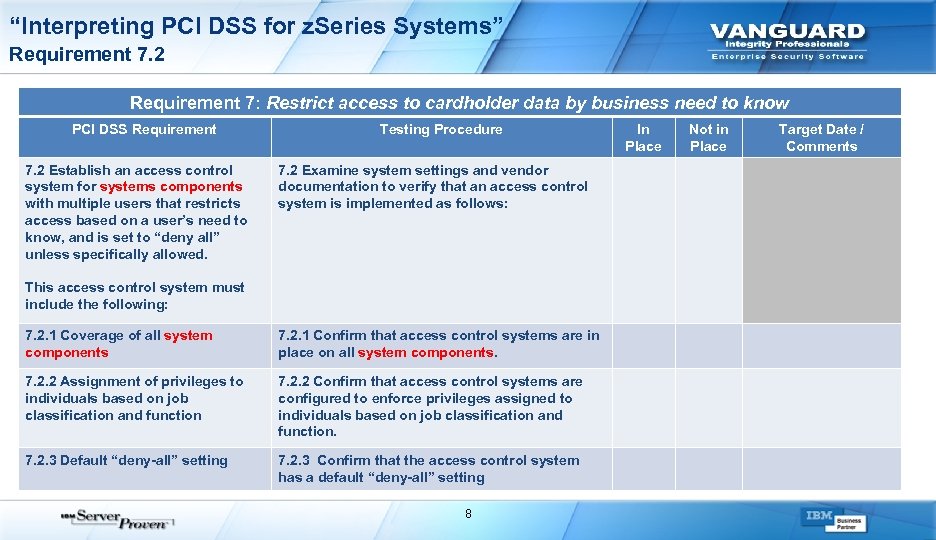 “Interpreting PCI DSS for z. Series Systems” Requirement 7. 2 Requirement 7: Restrict access to cardholder data by business need to know PCI DSS Requirement 7. 2 Establish an access control system for systems components with multiple users that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed. Testing Procedure 7. 2 Examine system settings and vendor documentation to verify that an access control system is implemented as follows: This access control system must include the following: 7. 2. 1 Coverage of all system components 7. 2. 1 Confirm that access control systems are in place on all system components. 7. 2. 2 Assignment of privileges to individuals based on job classification and function 7. 2. 2 Confirm that access control systems are configured to enforce privileges assigned to individuals based on job classification and function. 7. 2. 3 Default “deny-all” setting 7. 2. 3 Confirm that the access control system has a default “deny-all” setting 8 In Place Not in Place Target Date / Comments
“Interpreting PCI DSS for z. Series Systems” Requirement 7. 2 Requirement 7: Restrict access to cardholder data by business need to know PCI DSS Requirement 7. 2 Establish an access control system for systems components with multiple users that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed. Testing Procedure 7. 2 Examine system settings and vendor documentation to verify that an access control system is implemented as follows: This access control system must include the following: 7. 2. 1 Coverage of all system components 7. 2. 1 Confirm that access control systems are in place on all system components. 7. 2. 2 Assignment of privileges to individuals based on job classification and function 7. 2. 2 Confirm that access control systems are configured to enforce privileges assigned to individuals based on job classification and function. 7. 2. 3 Default “deny-all” setting 7. 2. 3 Confirm that the access control system has a default “deny-all” setting 8 In Place Not in Place Target Date / Comments
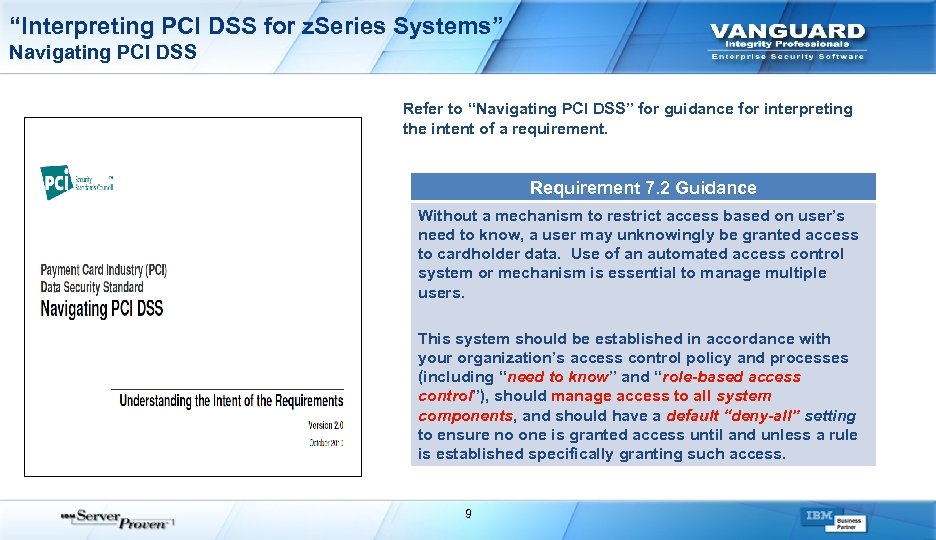 “Interpreting PCI DSS for z. Series Systems” Navigating PCI DSS Refer to “Navigating PCI DSS” for guidance for interpreting the intent of a requirement. Requirement 7. 2 Guidance Without a mechanism to restrict access based on user’s need to know, a user may unknowingly be granted access to cardholder data. Use of an automated access control system or mechanism is essential to manage multiple users. This system should be established in accordance with your organization’s access control policy and processes (including “need to know” and “role-based access control”), should manage access to all system components, and should have a default “deny-all” setting to ensure no one is granted access until and unless a rule is established specifically granting such access. 9
“Interpreting PCI DSS for z. Series Systems” Navigating PCI DSS Refer to “Navigating PCI DSS” for guidance for interpreting the intent of a requirement. Requirement 7. 2 Guidance Without a mechanism to restrict access based on user’s need to know, a user may unknowingly be granted access to cardholder data. Use of an automated access control system or mechanism is essential to manage multiple users. This system should be established in accordance with your organization’s access control policy and processes (including “need to know” and “role-based access control”), should manage access to all system components, and should have a default “deny-all” setting to ensure no one is granted access until and unless a rule is established specifically granting such access. 9
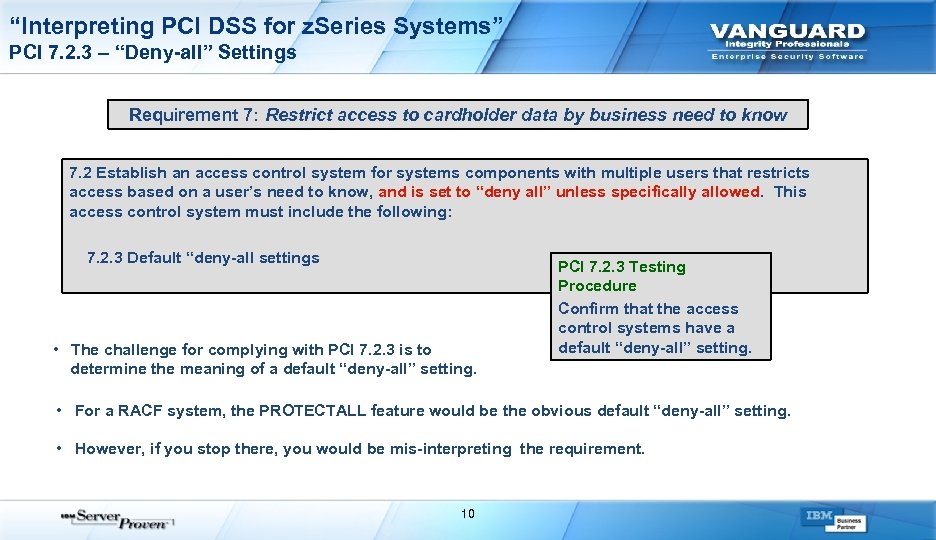 “Interpreting PCI DSS for z. Series Systems” PCI 7. 2. 3 – “Deny-all” Settings Requirement 7: Restrict access to cardholder data by business need to know 7. 2 Establish an access control system for systems components with multiple users that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed. This access control system must include the following: 7. 2. 3 Default “deny-all settings • The challenge for complying with PCI 7. 2. 3 is to determine the meaning of a default “deny-all” setting. PCI 7. 2. 3 Testing Procedure Confirm that the access control systems have a default “deny-all” setting. • For a RACF system, the PROTECTALL feature would be the obvious default “deny-all” setting. • However, if you stop there, you would be mis-interpreting the requirement. 10
“Interpreting PCI DSS for z. Series Systems” PCI 7. 2. 3 – “Deny-all” Settings Requirement 7: Restrict access to cardholder data by business need to know 7. 2 Establish an access control system for systems components with multiple users that restricts access based on a user’s need to know, and is set to “deny all” unless specifically allowed. This access control system must include the following: 7. 2. 3 Default “deny-all settings • The challenge for complying with PCI 7. 2. 3 is to determine the meaning of a default “deny-all” setting. PCI 7. 2. 3 Testing Procedure Confirm that the access control systems have a default “deny-all” setting. • For a RACF system, the PROTECTALL feature would be the obvious default “deny-all” setting. • However, if you stop there, you would be mis-interpreting the requirement. 10
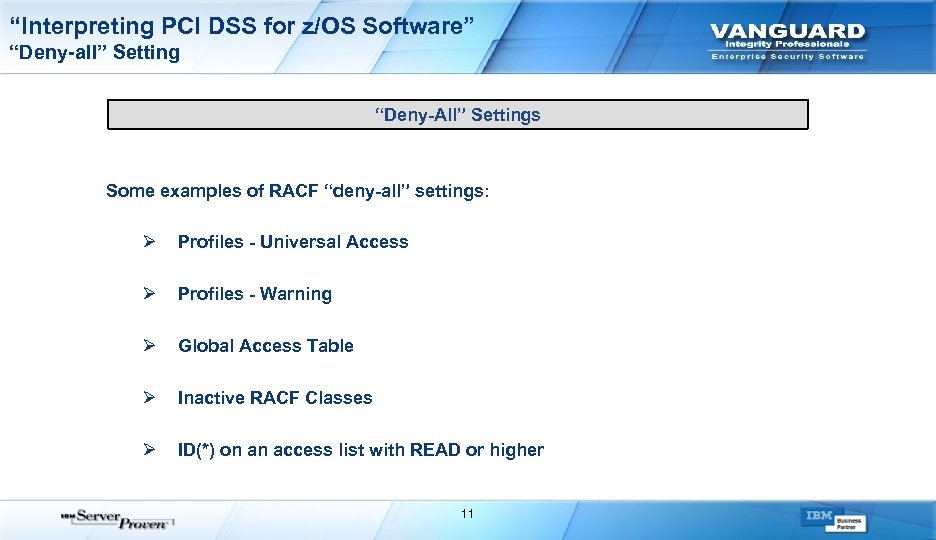 “Interpreting PCI DSS for z/OS Software” “Deny-all” Setting “Deny-All” Settings Some examples of RACF “deny-all” settings: Ø Ø Profiles - Universal Access Ø Global Access Table Ø Inactive RACF Classes Ø ID(*) on an access list with READ or higher Profiles - Warning 11
“Interpreting PCI DSS for z/OS Software” “Deny-all” Setting “Deny-All” Settings Some examples of RACF “deny-all” settings: Ø Ø Profiles - Universal Access Ø Global Access Table Ø Inactive RACF Classes Ø ID(*) on an access list with READ or higher Profiles - Warning 11
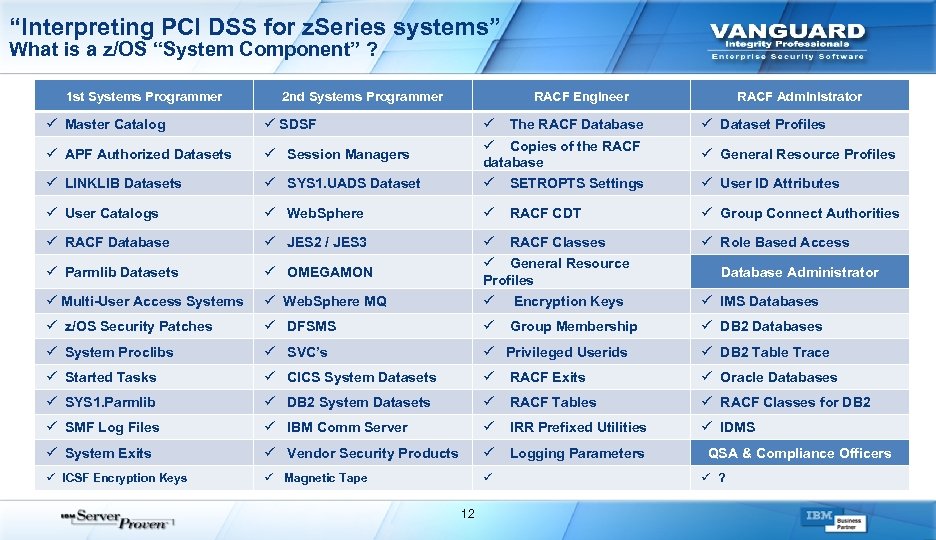 “Interpreting PCI DSS for z. Series systems” What is a z/OS “System Component” ? 1 st Systems Programmer 2 nd Systems Programmer ü Master Catalog ü SDSF ü APF Authorized Datasets ü Session Managers ü LINKLIB Datasets RACF Engineer RACF Administrator ü Dataset Profiles ü SYS 1. UADS Dataset ü The RACF Database ü Copies of the RACF database ü SETROPTS Settings ü User Catalogs ü Web. Sphere ü RACF CDT ü Group Connect Authorities ü RACF Database ü JES 2 / JES 3 ü Role Based Access ü Parmlib Datasets ü OMEGAMON ü Multi-User Access Systems ü Web. Sphere MQ ü RACF Classes ü General Resource Profiles ü Encryption Keys ü z/OS Security Patches ü DFSMS ü Group Membership ü DB 2 Databases ü System Proclibs ü SVC’s ü Privileged Userids ü DB 2 Table Trace ü Started Tasks ü CICS System Datasets ü RACF Exits ü Oracle Databases ü SYS 1. Parmlib ü DB 2 System Datasets ü RACF Tables ü RACF Classes for DB 2 ü SMF Log Files ü IBM Comm Server ü IRR Prefixed Utilities ü IDMS ü System Exits ü Vendor Security Products ü Logging Parameters ü ICSF Encryption Keys ü Magnetic Tape ü 12 ü General Resource Profiles ü User ID Attributes Database Administrator ü IMS Databases QSA & Compliance Officers ü ?
“Interpreting PCI DSS for z. Series systems” What is a z/OS “System Component” ? 1 st Systems Programmer 2 nd Systems Programmer ü Master Catalog ü SDSF ü APF Authorized Datasets ü Session Managers ü LINKLIB Datasets RACF Engineer RACF Administrator ü Dataset Profiles ü SYS 1. UADS Dataset ü The RACF Database ü Copies of the RACF database ü SETROPTS Settings ü User Catalogs ü Web. Sphere ü RACF CDT ü Group Connect Authorities ü RACF Database ü JES 2 / JES 3 ü Role Based Access ü Parmlib Datasets ü OMEGAMON ü Multi-User Access Systems ü Web. Sphere MQ ü RACF Classes ü General Resource Profiles ü Encryption Keys ü z/OS Security Patches ü DFSMS ü Group Membership ü DB 2 Databases ü System Proclibs ü SVC’s ü Privileged Userids ü DB 2 Table Trace ü Started Tasks ü CICS System Datasets ü RACF Exits ü Oracle Databases ü SYS 1. Parmlib ü DB 2 System Datasets ü RACF Tables ü RACF Classes for DB 2 ü SMF Log Files ü IBM Comm Server ü IRR Prefixed Utilities ü IDMS ü System Exits ü Vendor Security Products ü Logging Parameters ü ICSF Encryption Keys ü Magnetic Tape ü 12 ü General Resource Profiles ü User ID Attributes Database Administrator ü IMS Databases QSA & Compliance Officers ü ?
 Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 13
Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 13
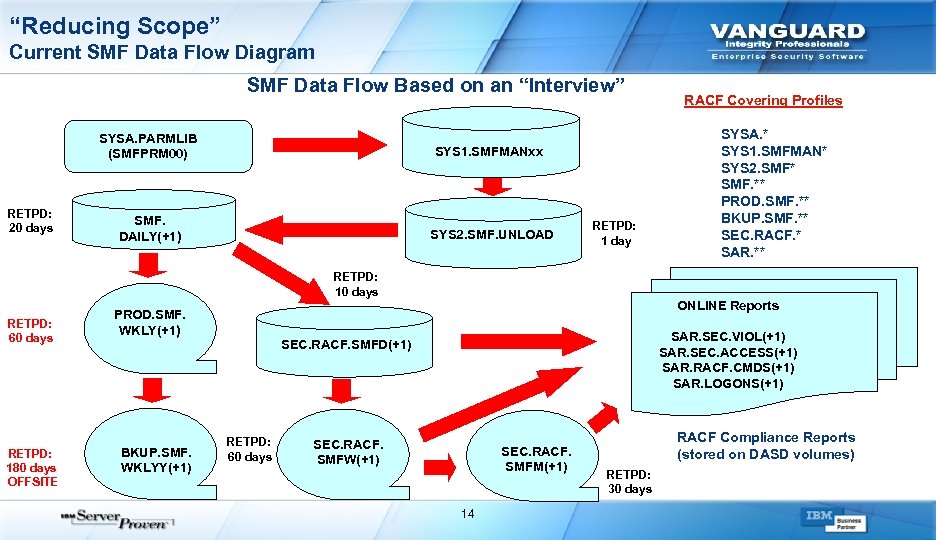 “Reducing Scope” Current SMF Data Flow Diagram SMF Data Flow Based on an “Interview” SYSA. PARMLIB (SMFPRM 00) RETPD: 20 days SYS 2. SMF. UNLOAD SYSA. * SYS 1. SMFMAN* SYS 2. SMF* SMF. ** PROD. SMF. ** BKUP. SMF. ** SEC. RACF. * SAR. ** SYS 1. SMFMANxx SMF. DAILY(+1) RACF Covering Profiles RETPD: 1 day RETPD: 10 days RETPD: 60 days RETPD: 180 days OFFSITE ONLINE Reports PROD. SMF. WKLY(+1) BKUP. SMF. WKLYY(+1) SAR. SEC. VIOL(+1) SAR. SEC. ACCESS(+1) SAR. RACF. CMDS(+1) SAR. LOGONS(+1) SEC. RACF. SMFD(+1) RETPD: 60 days SEC. RACF. SMFW(+1) SEC. RACF. SMFM(+1) 14 RACF Compliance Reports (stored on DASD volumes) RETPD: 30 days
“Reducing Scope” Current SMF Data Flow Diagram SMF Data Flow Based on an “Interview” SYSA. PARMLIB (SMFPRM 00) RETPD: 20 days SYS 2. SMF. UNLOAD SYSA. * SYS 1. SMFMAN* SYS 2. SMF* SMF. ** PROD. SMF. ** BKUP. SMF. ** SEC. RACF. * SAR. ** SYS 1. SMFMANxx SMF. DAILY(+1) RACF Covering Profiles RETPD: 1 day RETPD: 10 days RETPD: 60 days RETPD: 180 days OFFSITE ONLINE Reports PROD. SMF. WKLY(+1) BKUP. SMF. WKLYY(+1) SAR. SEC. VIOL(+1) SAR. SEC. ACCESS(+1) SAR. RACF. CMDS(+1) SAR. LOGONS(+1) SEC. RACF. SMFD(+1) RETPD: 60 days SEC. RACF. SMFW(+1) SEC. RACF. SMFM(+1) 14 RACF Compliance Reports (stored on DASD volumes) RETPD: 30 days
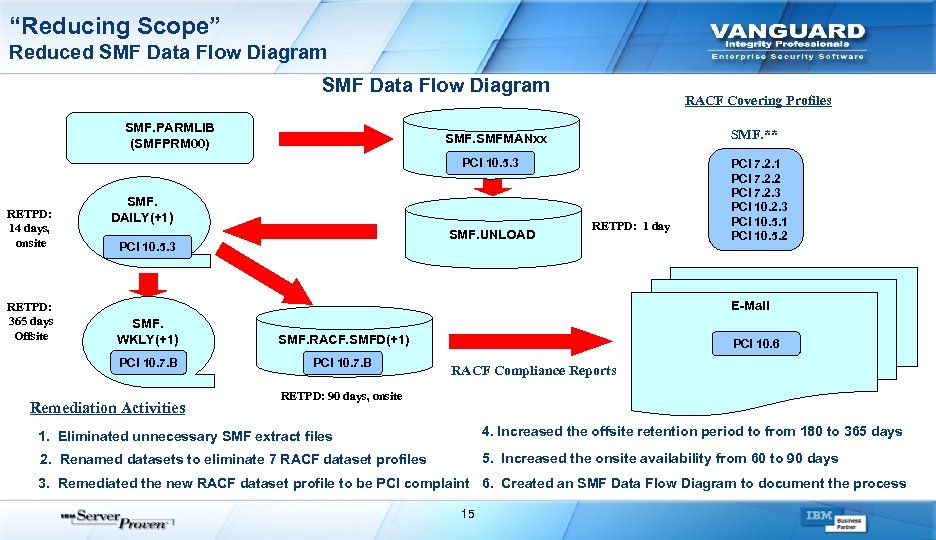 “Reducing Scope” Reduced SMF Data Flow Diagram SMF. PARMLIB (SMFPRM 00) RACF Covering Profiles SMF. ** SMFMANxx PCI 10. 5. 3 RETPD: 14 days, onsite RETPD: 365 days Offsite SMF. DAILY(+1) SMF. UNLOAD PCI 10. 5. 3 RETPD: 1 day PCI 7. 2. 1 PCI 7. 2. 2 PCI 7. 2. 3 PCI 10. 5. 1 PCI 10. 5. 2 E-Mail SMF. WKLY(+1) SMF. RACF. SMFD(+1) PCI 10. 7. B Remediation Activities PCI 10. 6 RACF Compliance Reports RETPD: 90 days, onsite 1. Eliminated unnecessary SMF extract files 4. Increased the offsite retention period to from 180 to 365 days 2. Renamed datasets to eliminate 7 RACF dataset profiles 5. Increased the onsite availability from 60 to 90 days 3. Remediated the new RACF dataset profile to be PCI complaint 6. Created an SMF Data Flow Diagram to document the process 15
“Reducing Scope” Reduced SMF Data Flow Diagram SMF. PARMLIB (SMFPRM 00) RACF Covering Profiles SMF. ** SMFMANxx PCI 10. 5. 3 RETPD: 14 days, onsite RETPD: 365 days Offsite SMF. DAILY(+1) SMF. UNLOAD PCI 10. 5. 3 RETPD: 1 day PCI 7. 2. 1 PCI 7. 2. 2 PCI 7. 2. 3 PCI 10. 5. 1 PCI 10. 5. 2 E-Mail SMF. WKLY(+1) SMF. RACF. SMFD(+1) PCI 10. 7. B Remediation Activities PCI 10. 6 RACF Compliance Reports RETPD: 90 days, onsite 1. Eliminated unnecessary SMF extract files 4. Increased the offsite retention period to from 180 to 365 days 2. Renamed datasets to eliminate 7 RACF dataset profiles 5. Increased the onsite availability from 60 to 90 days 3. Remediated the new RACF dataset profile to be PCI complaint 6. Created an SMF Data Flow Diagram to document the process 15
 Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 16
Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 16
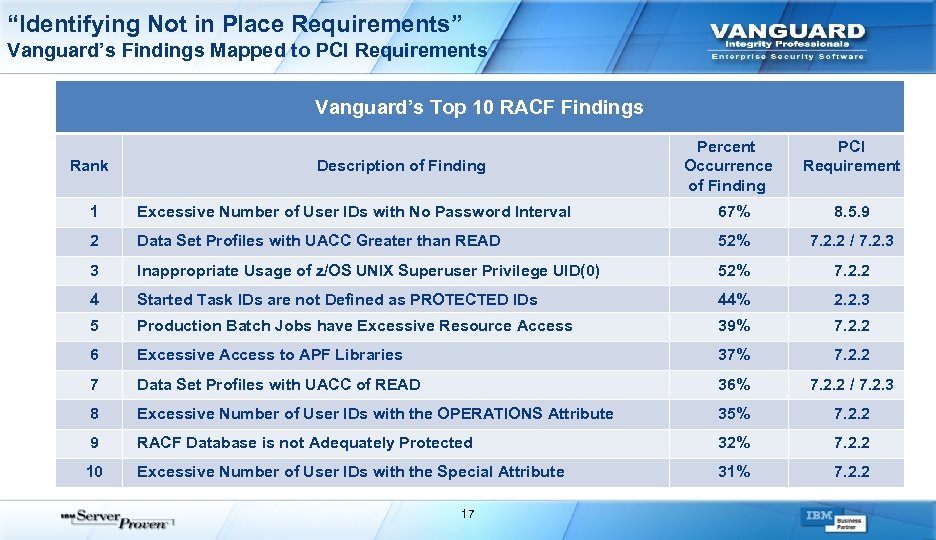 “Identifying Not in Place Requirements” Vanguard’s Findings Mapped to PCI Requirements Vanguard’s Top 10 RACF Findings Rank Description of Finding Percent Occurrence of Finding PCI Requirement 1 Excessive Number of User IDs with No Password Interval 67% 8. 5. 9 2 Data Set Profiles with UACC Greater than READ 52% 7. 2. 2 / 7. 2. 3 3 Inappropriate Usage of z/OS UNIX Superuser Privilege UID(0) 52% 7. 2. 2 4 Started Task IDs are not Defined as PROTECTED IDs 44% 2. 2. 3 5 Production Batch Jobs have Excessive Resource Access 39% 7. 2. 2 6 Excessive Access to APF Libraries 37% 7. 2. 2 7 Data Set Profiles with UACC of READ 36% 7. 2. 2 / 7. 2. 3 8 Excessive Number of User IDs with the OPERATIONS Attribute 35% 7. 2. 2 9 RACF Database is not Adequately Protected 32% 7. 2. 2 10 Excessive Number of User IDs with the Special Attribute 31% 7. 2. 2 17
“Identifying Not in Place Requirements” Vanguard’s Findings Mapped to PCI Requirements Vanguard’s Top 10 RACF Findings Rank Description of Finding Percent Occurrence of Finding PCI Requirement 1 Excessive Number of User IDs with No Password Interval 67% 8. 5. 9 2 Data Set Profiles with UACC Greater than READ 52% 7. 2. 2 / 7. 2. 3 3 Inappropriate Usage of z/OS UNIX Superuser Privilege UID(0) 52% 7. 2. 2 4 Started Task IDs are not Defined as PROTECTED IDs 44% 2. 2. 3 5 Production Batch Jobs have Excessive Resource Access 39% 7. 2. 2 6 Excessive Access to APF Libraries 37% 7. 2. 2 7 Data Set Profiles with UACC of READ 36% 7. 2. 2 / 7. 2. 3 8 Excessive Number of User IDs with the OPERATIONS Attribute 35% 7. 2. 2 9 RACF Database is not Adequately Protected 32% 7. 2. 2 10 Excessive Number of User IDs with the Special Attribute 31% 7. 2. 2 17
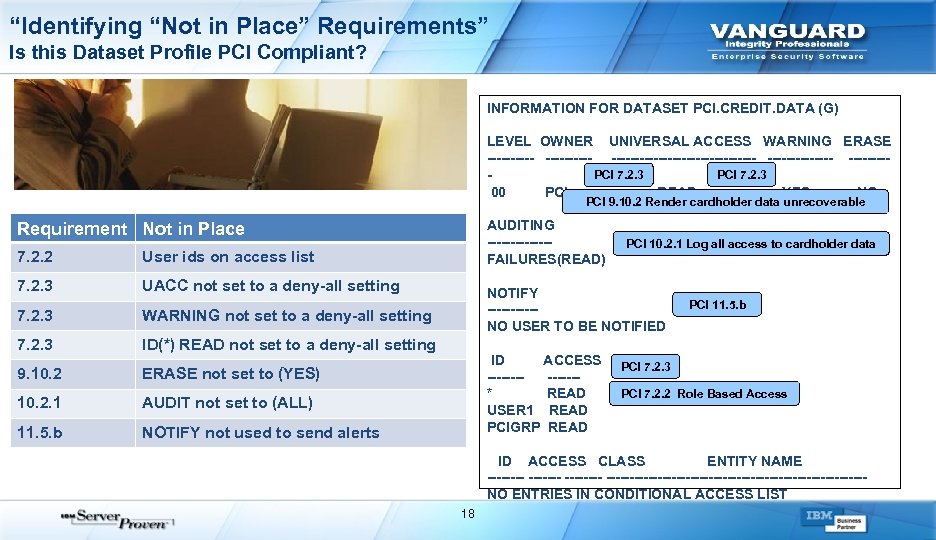 “Identifying “Not in Place” Requirements” Is this Dataset Profile PCI Compliant? INFORMATION FOR DATASET PCI. CREDIT. DATA (G) LEVEL OWNER UNIVERSAL ACCESS WARNING ERASE ---------------- ------- ----PCI 7. 2. 3 - 00 PCI READ YES NO PCI 9. 10. 2 Render cardholder data unrecoverable AUDITING ------- PCI 10. 2. 1 Log all access to cardholder data FAILURES(READ) NOTIFY PCI 11. 5. b ------ NO USER TO BE NOTIFIED Requirement Not in Place 7. 2. 2 User ids on access list 7. 2. 3 UACC not set to a deny-all setting 7. 2. 3 WARNING not set to a deny-all setting 7. 2. 3 ID(*) READ not set to a deny-all setting 9. 10. 2 ERASE not set to (YES) 10. 2. 1 AUDIT not set to (ALL) 11. 5. b NOTIFY not used to send alerts ID ACCESS PCI 7. 2. 3 ------- PCI 7. 2. 2 Role Based Access * READ USER 1 READ PCIGRP READ ID ACCESS CLASS ENTITY NAME -------------------------------NO ENTRIES IN CONDITIONAL ACCESS LIST 18
“Identifying “Not in Place” Requirements” Is this Dataset Profile PCI Compliant? INFORMATION FOR DATASET PCI. CREDIT. DATA (G) LEVEL OWNER UNIVERSAL ACCESS WARNING ERASE ---------------- ------- ----PCI 7. 2. 3 - 00 PCI READ YES NO PCI 9. 10. 2 Render cardholder data unrecoverable AUDITING ------- PCI 10. 2. 1 Log all access to cardholder data FAILURES(READ) NOTIFY PCI 11. 5. b ------ NO USER TO BE NOTIFIED Requirement Not in Place 7. 2. 2 User ids on access list 7. 2. 3 UACC not set to a deny-all setting 7. 2. 3 WARNING not set to a deny-all setting 7. 2. 3 ID(*) READ not set to a deny-all setting 9. 10. 2 ERASE not set to (YES) 10. 2. 1 AUDIT not set to (ALL) 11. 5. b NOTIFY not used to send alerts ID ACCESS PCI 7. 2. 3 ------- PCI 7. 2. 2 Role Based Access * READ USER 1 READ PCIGRP READ ID ACCESS CLASS ENTITY NAME -------------------------------NO ENTRIES IN CONDITIONAL ACCESS LIST 18
 “Identifying “Not in Place” Requirements” PCI RACF Mini-Review Making Management aware. Why do I need a PCI z/OS RACF Mini Readiness Review? The mini assessment is designed to give the administrator and their management a real-time view (health check) of the integrity of their system. The Mini assessment is an engagement that investigates areas in which we frequently find problems. Each problem is then mapped to the applicable PCI requirement. This no charge offering, with an investment of only a few hours time, provides you with insight that there are z/OS RACF “Not in Place” conditions that need to be addressed. Mini Readiness Reviews can help you develop the justification management needs to allocate resources to address the issues identified. 19
“Identifying “Not in Place” Requirements” PCI RACF Mini-Review Making Management aware. Why do I need a PCI z/OS RACF Mini Readiness Review? The mini assessment is designed to give the administrator and their management a real-time view (health check) of the integrity of their system. The Mini assessment is an engagement that investigates areas in which we frequently find problems. Each problem is then mapped to the applicable PCI requirement. This no charge offering, with an investment of only a few hours time, provides you with insight that there are z/OS RACF “Not in Place” conditions that need to be addressed. Mini Readiness Reviews can help you develop the justification management needs to allocate resources to address the issues identified. 19
 Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 4. Proving Compliance 20
Top PCI Challenges for z. Series Systems Challenges 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 4. Proving Compliance 20
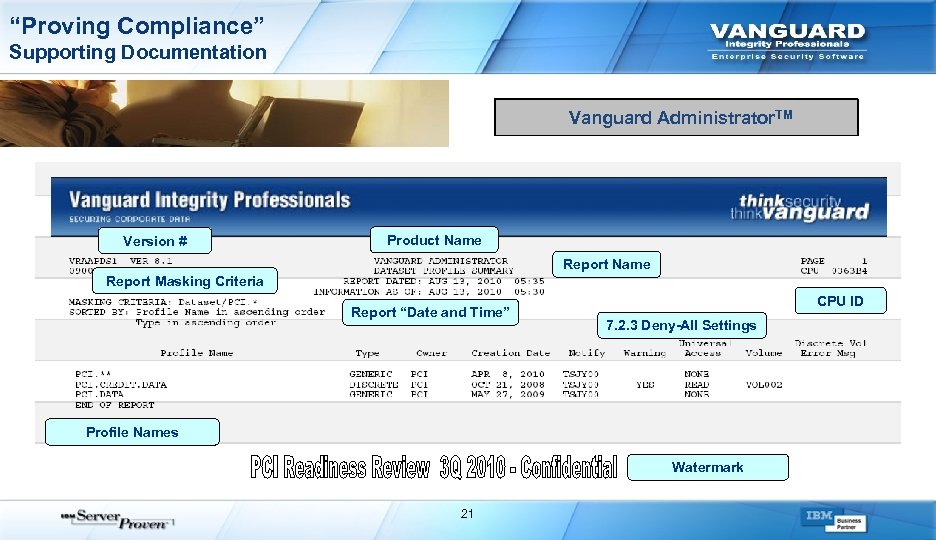 “Proving Compliance” Supporting Documentation Vanguard Administrator. TM Version # Product Name Report Masking Criteria Report “Date and Time” CPU ID 7. 2. 3 Deny-All Settings Profile Names Watermark 21
“Proving Compliance” Supporting Documentation Vanguard Administrator. TM Version # Product Name Report Masking Criteria Report “Date and Time” CPU ID 7. 2. 3 Deny-All Settings Profile Names Watermark 21
 “Proving Compliance” Supporting Documentation 7. 2 Establish an access control system for systems components Exhibit 7. 2 – Cardholder Data Flow Diagram Exhibit 7. 2 – RACF Data Flow Diagram Exhibit 7. 2 – SMF Data Flow Diagram 7. 2. 1 Coverage of all system components Exhibit 7. 2. 1 – RACF Databases 7. 2. 2 Assignment of privileges based on job classification and function RACF Group Profiles Exhibit 7. 2. 2 – RBAC Supporting Documentation RACF User ID Profiles Exhibit 7. 2. 2 – User IDs with System Level Administrative Privileges Exhibit 7. 2. 2 – User IDs on Access Lists RACF Dataset Profiles Exhibit 7. 2. 2 – Cardholder Dataset Profiles System Data Set Profiles Exhibit 7. 2. 2 – Authorized Program Facility (APF) Data Sets Exhibit 7. 2. 2 – DASD Volume Backup Data Sets Exhibit 7. 2. 2 – LINKLIST Data Sets 22
“Proving Compliance” Supporting Documentation 7. 2 Establish an access control system for systems components Exhibit 7. 2 – Cardholder Data Flow Diagram Exhibit 7. 2 – RACF Data Flow Diagram Exhibit 7. 2 – SMF Data Flow Diagram 7. 2. 1 Coverage of all system components Exhibit 7. 2. 1 – RACF Databases 7. 2. 2 Assignment of privileges based on job classification and function RACF Group Profiles Exhibit 7. 2. 2 – RBAC Supporting Documentation RACF User ID Profiles Exhibit 7. 2. 2 – User IDs with System Level Administrative Privileges Exhibit 7. 2. 2 – User IDs on Access Lists RACF Dataset Profiles Exhibit 7. 2. 2 – Cardholder Dataset Profiles System Data Set Profiles Exhibit 7. 2. 2 – Authorized Program Facility (APF) Data Sets Exhibit 7. 2. 2 – DASD Volume Backup Data Sets Exhibit 7. 2. 2 – LINKLIST Data Sets 22
 Top PCI Challenges for z. Series Systems Challenges and Solutions 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 4. Proving Compliance 5. Staying Compliant 23
Top PCI Challenges for z. Series Systems Challenges and Solutions 1. Proper Interpretation of the Requirements 2. Reducing Scope 3. Identifying “Not in Place” Requirements 4. Proving Compliance 5. Staying Compliant 23
 “Staying Compliant” Ongoing Readiness Reviews Requirement 7. 2. 3 System Settings PROTECTALL Feature Profile Settings WARNING Attribute Universal Access – UACC(NONE) Attribute ID(*) on an Access List Global Access Settings (GAC) General Resource Back-Stop Profiles Inactive General Resource Classes Profiles that can bypass a “deny-all” Setting TAPEDSN Feature ICHBLP Profile RACF Dataset Conversion Table RACF Exits 24
“Staying Compliant” Ongoing Readiness Reviews Requirement 7. 2. 3 System Settings PROTECTALL Feature Profile Settings WARNING Attribute Universal Access – UACC(NONE) Attribute ID(*) on an Access List Global Access Settings (GAC) General Resource Back-Stop Profiles Inactive General Resource Classes Profiles that can bypass a “deny-all” Setting TAPEDSN Feature ICHBLP Profile RACF Dataset Conversion Table RACF Exits 24
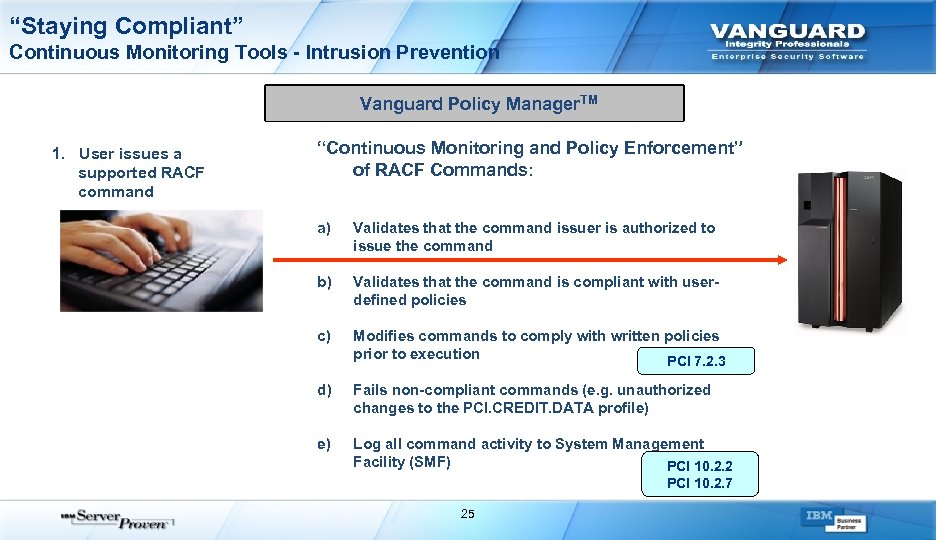 “Staying Compliant” Continuous Monitoring Tools - Intrusion Prevention Vanguard Policy Manager. TM 1. User issues a supported RACF command “Continuous Monitoring and Policy Enforcement” of RACF Commands: a) Validates that the command issuer is authorized to issue the command b) Validates that the command is compliant with userdefined policies c) Modifies commands to comply with written policies prior to execution PCI 7. 2. 3 d) Fails non-compliant commands (e. g. unauthorized changes to the PCI. CREDIT. DATA profile) e) Log all command activity to System Management Facility (SMF) PCI 10. 2. 2 PCI 10. 2. 7 25
“Staying Compliant” Continuous Monitoring Tools - Intrusion Prevention Vanguard Policy Manager. TM 1. User issues a supported RACF command “Continuous Monitoring and Policy Enforcement” of RACF Commands: a) Validates that the command issuer is authorized to issue the command b) Validates that the command is compliant with userdefined policies c) Modifies commands to comply with written policies prior to execution PCI 7. 2. 3 d) Fails non-compliant commands (e. g. unauthorized changes to the PCI. CREDIT. DATA profile) e) Log all command activity to System Management Facility (SMF) PCI 10. 2. 2 PCI 10. 2. 7 25
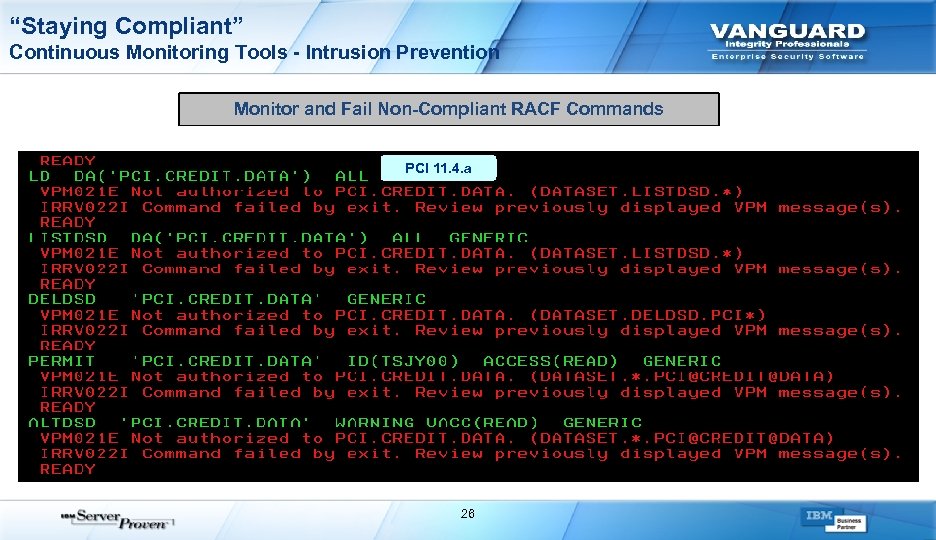 “Staying Compliant” Continuous Monitoring Tools - Intrusion Prevention Monitor and Fail Non-Compliant RACF Commands PCI 11. 4. a 26
“Staying Compliant” Continuous Monitoring Tools - Intrusion Prevention Monitor and Fail Non-Compliant RACF Commands PCI 11. 4. a 26
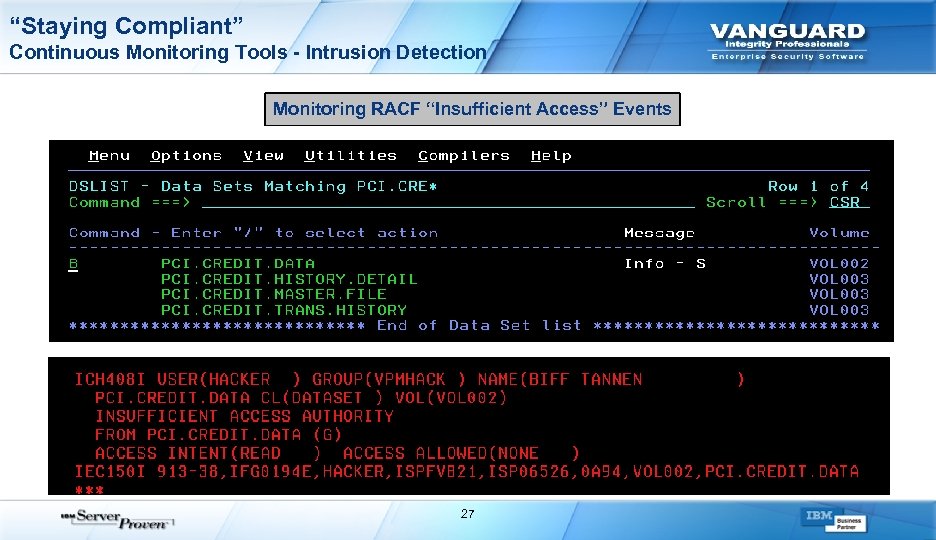 “Staying Compliant” Continuous Monitoring Tools - Intrusion Detection Monitoring RACF “Insufficient Access” Events 27
“Staying Compliant” Continuous Monitoring Tools - Intrusion Detection Monitoring RACF “Insufficient Access” Events 27
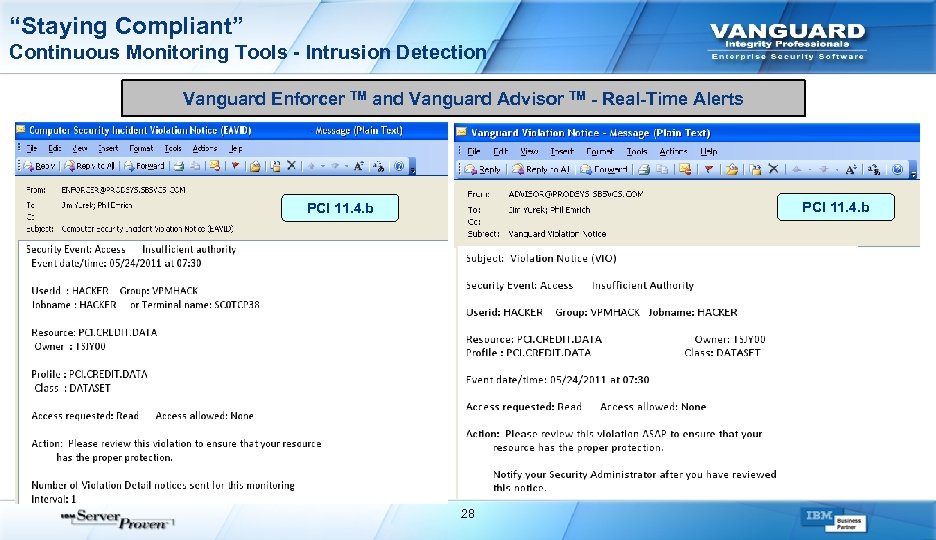 “Staying Compliant” Continuous Monitoring Tools - Intrusion Detection Vanguard Enforcer TM and Vanguard Advisor TM - Real-Time Alerts PCI 11. 4. b 28
“Staying Compliant” Continuous Monitoring Tools - Intrusion Detection Vanguard Enforcer TM and Vanguard Advisor TM - Real-Time Alerts PCI 11. 4. b 28
 References PCI Security Standards Council Payment Card Industry (PCI) Data Security Standards and Navigating PCI DSS 2. 0 https: //www. pcisecuritystandards. org/ NIST - National Checklist Program Repository, z. Series RACF STIG http: //web. nvd. nist. gov/view/ncp/repository? page_num=1 x. Bridge Systems - Achieving PCI Compliance on the Mainframe – White Paper http: //www. xbridgesystems. com/products/whitepapers/Xbridge_White_Paper_Achieving_PCI_Compliance_on_the_Mainframe_Ap ril_2011. pdf Verizon Business - Verizon 2010 Payment Card Industry Compliance Report http: //www. verizonbusiness. com/resources/reports/rp_2010 -payment-card-industry-compliance-report_en_xg. pdf Gartner Research Note - "Why Your IBM z. Series Mainframe May Not Be as Secure as You Think It Is and What You Can Do About It. " http: //www. go 2 vanguard. com/gartner_request. php Verisign Global Security Consulting Services - Compliance and the cost of a credit card breach http: //www. verisign. com/static/PCI_REASONS. pdf COMPUTERWORLD - January 6, 2010 Update: Heartland breach shows why compliance is not enough http: //www. computerworld. com/s/article/9143158/Update_Heartland_breach_shows_why_compliance_is_not_enough Ponemon Institute - PCI DSS Trends 2010: QSA Insights Report http: //www. ponemon. org/data-security 29
References PCI Security Standards Council Payment Card Industry (PCI) Data Security Standards and Navigating PCI DSS 2. 0 https: //www. pcisecuritystandards. org/ NIST - National Checklist Program Repository, z. Series RACF STIG http: //web. nvd. nist. gov/view/ncp/repository? page_num=1 x. Bridge Systems - Achieving PCI Compliance on the Mainframe – White Paper http: //www. xbridgesystems. com/products/whitepapers/Xbridge_White_Paper_Achieving_PCI_Compliance_on_the_Mainframe_Ap ril_2011. pdf Verizon Business - Verizon 2010 Payment Card Industry Compliance Report http: //www. verizonbusiness. com/resources/reports/rp_2010 -payment-card-industry-compliance-report_en_xg. pdf Gartner Research Note - "Why Your IBM z. Series Mainframe May Not Be as Secure as You Think It Is and What You Can Do About It. " http: //www. go 2 vanguard. com/gartner_request. php Verisign Global Security Consulting Services - Compliance and the cost of a credit card breach http: //www. verisign. com/static/PCI_REASONS. pdf COMPUTERWORLD - January 6, 2010 Update: Heartland breach shows why compliance is not enough http: //www. computerworld. com/s/article/9143158/Update_Heartland_breach_shows_why_compliance_is_not_enough Ponemon Institute - PCI DSS Trends 2010: QSA Insights Report http: //www. ponemon. org/data-security 29
 References PCI Testing Procedures Referenced in this Presentation 7. 2. 1 Confirm that access control systems are in place on all system components. 7. 2. 2 Confirm that access control systems are configured to enforce privileges assigned to individuals based on job classification and function. 7. 2. 3 Confirm that the access control systems have a default “deny-all” setting. 10. 2. 2 Verify actions taken by any individual with root or administrative privileges are logged 10. 2. 3 Verify access to all audit trails is logged. 10. 2. 7 Verify creation and deletion of system level objects are logged. 10. 5. 1 Verify that only individuals who have a job-related need can view audit trail files. 10. 5. 2 Verify that current audit trail files are protected from unauthorized modifications via access control mechanisms 10. 5. 3 Verify that current audit trail files are promptly backed up to a centralized log server or media that is difficult to alter. 10. 6 Through observation and interviews, verify that regular log reviews are performed for all system components. 10. 7. b Verify that audit logs are available for at least one year and processes are in place to immediately restore at least the last three months’ logs for analysis. 10. 2. 3 Verify access to all audit trails is logged. 11. 4. a Verify the use of intrusion-detection systems and/or intrusion-prevention systems and that all traffic at the perimeter of the cardholder data environment as well as at critical points in the cardholder data environment is monitored. 11. 4. b Confirm IDS and/or IPS are configured to alert personnel of suspected compromises. 30
References PCI Testing Procedures Referenced in this Presentation 7. 2. 1 Confirm that access control systems are in place on all system components. 7. 2. 2 Confirm that access control systems are configured to enforce privileges assigned to individuals based on job classification and function. 7. 2. 3 Confirm that the access control systems have a default “deny-all” setting. 10. 2. 2 Verify actions taken by any individual with root or administrative privileges are logged 10. 2. 3 Verify access to all audit trails is logged. 10. 2. 7 Verify creation and deletion of system level objects are logged. 10. 5. 1 Verify that only individuals who have a job-related need can view audit trail files. 10. 5. 2 Verify that current audit trail files are protected from unauthorized modifications via access control mechanisms 10. 5. 3 Verify that current audit trail files are promptly backed up to a centralized log server or media that is difficult to alter. 10. 6 Through observation and interviews, verify that regular log reviews are performed for all system components. 10. 7. b Verify that audit logs are available for at least one year and processes are in place to immediately restore at least the last three months’ logs for analysis. 10. 2. 3 Verify access to all audit trails is logged. 11. 4. a Verify the use of intrusion-detection systems and/or intrusion-prevention systems and that all traffic at the perimeter of the cardholder data environment as well as at critical points in the cardholder data environment is monitored. 11. 4. b Confirm IDS and/or IPS are configured to alert personnel of suspected compromises. 30
 Thank You Tamil Hindi Thai Danke Arabic German Russian Simplified Chinese Traditional Chinese Korean Japanese Obrigado Brazilian Portuguese Gracias Merci French Spanish Grazie Italian 31 © 2011 Vanguard Integrity Professionals, Inc.
Thank You Tamil Hindi Thai Danke Arabic German Russian Simplified Chinese Traditional Chinese Korean Japanese Obrigado Brazilian Portuguese Gracias Merci French Spanish Grazie Italian 31 © 2011 Vanguard Integrity Professionals, Inc.
 About Vanguard Integrity Professionals is the world’s leading solutions provider in the field of RACF®. Leveraging its robust suite of security administration and auditing tools, a development and professional services team comprised of more than 30 of the top RACF experts in the world, and a proven history of providing market leading solutions for over 20 years, Vanguard has established a reputation as the best in the industry. Vanguard offers the most comprehensive suite of security software solutions, professional services, and training of any vendor in the world. More than 500 customers have partnered with Vanguard to ensure and protect the integrity of Information Systems and the confidentiality of sensitive production data in the nation's largest financial, healthcare, retail organizations and government agencies. Vanguard is also the developer and sponsor of Vanguard Security and Compliance™ (formerly, the Vanguard Enterprise Security Expo), the most prominent and insightful security conference in the industry, which has trained more than 8, 000 security experts since 1987. Vanguard Professional Services provides customers with the industry's most comprehensive set of enterprise professional service offerings in the RACF z/OS®, distributed and Network/Internet markets. Vanguard consultants, with an average of 25 years experience, offer strategic consulting and training tailored to meet an organization’s unique business requirements, and can assist in the process of managing risks to protect the integrity of information systems and confidentiality of your data. Vanguard consultants are highly regarded and considered the best-of-the-best in their field. Vanguard’s Software Solutions offer a robust set of tools for z/OS Security Server and Resource Access Control Facility (RACF) that dramatically improve the efficiency of security administration and management, and address the demands of regulatory compliance and reporting. The Security Server is transformed into a real-time intrusion detection and policy enforcement platform, extending System z® security and audit capabilities across the enterprise. With Vanguard's solutions users are empowered to make immediate and informed security decisions. 32
About Vanguard Integrity Professionals is the world’s leading solutions provider in the field of RACF®. Leveraging its robust suite of security administration and auditing tools, a development and professional services team comprised of more than 30 of the top RACF experts in the world, and a proven history of providing market leading solutions for over 20 years, Vanguard has established a reputation as the best in the industry. Vanguard offers the most comprehensive suite of security software solutions, professional services, and training of any vendor in the world. More than 500 customers have partnered with Vanguard to ensure and protect the integrity of Information Systems and the confidentiality of sensitive production data in the nation's largest financial, healthcare, retail organizations and government agencies. Vanguard is also the developer and sponsor of Vanguard Security and Compliance™ (formerly, the Vanguard Enterprise Security Expo), the most prominent and insightful security conference in the industry, which has trained more than 8, 000 security experts since 1987. Vanguard Professional Services provides customers with the industry's most comprehensive set of enterprise professional service offerings in the RACF z/OS®, distributed and Network/Internet markets. Vanguard consultants, with an average of 25 years experience, offer strategic consulting and training tailored to meet an organization’s unique business requirements, and can assist in the process of managing risks to protect the integrity of information systems and confidentiality of your data. Vanguard consultants are highly regarded and considered the best-of-the-best in their field. Vanguard’s Software Solutions offer a robust set of tools for z/OS Security Server and Resource Access Control Facility (RACF) that dramatically improve the efficiency of security administration and management, and address the demands of regulatory compliance and reporting. The Security Server is transformed into a real-time intrusion detection and policy enforcement platform, extending System z® security and audit capabilities across the enterprise. With Vanguard's solutions users are empowered to make immediate and informed security decisions. 32


