fdf6c51462346fd6e426a40f7b8dc991.ppt
- Количество слайдов: 29
 Passive Network Discovery Systems Martin Roesch
Passive Network Discovery Systems Martin Roesch
 The Current State of Intrusion Detection
The Current State of Intrusion Detection
 What is NIDS? A network intrusion detection system monitors traffic in real time and alerts when suspicious activity is detected 3
What is NIDS? A network intrusion detection system monitors traffic in real time and alerts when suspicious activity is detected 3
 Why is NIDS Important? Access control (firewalling) is only part of the security solution, you need network monitoring technology (Defense in Depth) to secure your enterprise effectively 4
Why is NIDS Important? Access control (firewalling) is only part of the security solution, you need network monitoring technology (Defense in Depth) to secure your enterprise effectively 4
 Complementary Security Measures 4 Network IDS complements and augments firewalls and other security infrastructure 6 Provides “assurance” in case firewall is bypassed or misconfigured 6 Protects against insider threats 6 Affords forensic analysis against changing environments and threat vectors 5
Complementary Security Measures 4 Network IDS complements and augments firewalls and other security infrastructure 6 Provides “assurance” in case firewall is bypassed or misconfigured 6 Protects against insider threats 6 Affords forensic analysis against changing environments and threat vectors 5
 What’s Wrong with NIDS? 4 IDS is not working as well as hoped 4 Industry has been its own worst enemy for years, over-hyped and under delivered 4 What are intrusion detection systems really for? 6 Awareness - How is my networking? How is my security infrastructure working? 6 Analysis - When things go wrong, what happened and how can I prevent it from happening again? 4 Classic IDS does not protect networks, it allows people to understand how/if their protection is working and what happened when it fails 6
What’s Wrong with NIDS? 4 IDS is not working as well as hoped 4 Industry has been its own worst enemy for years, over-hyped and under delivered 4 What are intrusion detection systems really for? 6 Awareness - How is my networking? How is my security infrastructure working? 6 Analysis - When things go wrong, what happened and how can I prevent it from happening again? 4 Classic IDS does not protect networks, it allows people to understand how/if their protection is working and what happened when it fails 6
 Problems With IDS Implementations 4 Implementational Issues 6 Some assembly required § IDSes traditionally require a great deal of tuning for the environment they’re monitoring § Most NIDS solutions are lacking a credible data management solution § Tuning is an ongoing process 6 “What do you mean you don’t know IP? !” § Proper training is required to get value from an IDS § Interpreting the output from an IDS requires a great deal of expertise 6 System policy management § Managing the distributed sensor detection configuration is a manual process 7
Problems With IDS Implementations 4 Implementational Issues 6 Some assembly required § IDSes traditionally require a great deal of tuning for the environment they’re monitoring § Most NIDS solutions are lacking a credible data management solution § Tuning is an ongoing process 6 “What do you mean you don’t know IP? !” § Proper training is required to get value from an IDS § Interpreting the output from an IDS requires a great deal of expertise 6 System policy management § Managing the distributed sensor detection configuration is a manual process 7
 Problems With IDS Implementations 4 Conceptual Problems 6 Detection Failures § Ptacek & Newsham paper, classic guide on how to defeat IDS by taking advantage of ambiguities that IDS cannot resolve – 6 Fundamental problem with the approach used by many (all? ) IDSes Data management § Once I’ve got my IDS tuned and my staff trained, I run into the next problem: data management § IDS generates huge amounts of information, this information must be managed § Data management is a very hard problem as well (on the order of difficulty with IDS in the first place) § Data coming from IDSes is subjective for a variety of reasons, users are left to add context 8
Problems With IDS Implementations 4 Conceptual Problems 6 Detection Failures § Ptacek & Newsham paper, classic guide on how to defeat IDS by taking advantage of ambiguities that IDS cannot resolve – 6 Fundamental problem with the approach used by many (all? ) IDSes Data management § Once I’ve got my IDS tuned and my staff trained, I run into the next problem: data management § IDS generates huge amounts of information, this information must be managed § Data management is a very hard problem as well (on the order of difficulty with IDS in the first place) § Data coming from IDSes is subjective for a variety of reasons, users are left to add context 8
 The Missing Link
The Missing Link
 What you don’t know can kill you 4 Intrusion detection systems operate in a contextual vacuum 6 No knowledge of the network topology 6 No knowledge of the network’s assets 6 No knowledge regarding asset criticality 4 Effective prioritization is impossible without context 6 Priority is in the eye of the beholder 6 Automated response is extremely risky 4 100% Effective detection is impossible without context 6 IDS must guess about network topology and composition, making assumptions frequently 6 Mistaken assumptions lead to false positives or false negatives 4 If the attacker has more information about the target than the NIDS, this can be leveraged 10
What you don’t know can kill you 4 Intrusion detection systems operate in a contextual vacuum 6 No knowledge of the network topology 6 No knowledge of the network’s assets 6 No knowledge regarding asset criticality 4 Effective prioritization is impossible without context 6 Priority is in the eye of the beholder 6 Automated response is extremely risky 4 100% Effective detection is impossible without context 6 IDS must guess about network topology and composition, making assumptions frequently 6 Mistaken assumptions lead to false positives or false negatives 4 If the attacker has more information about the target than the NIDS, this can be leveraged 10
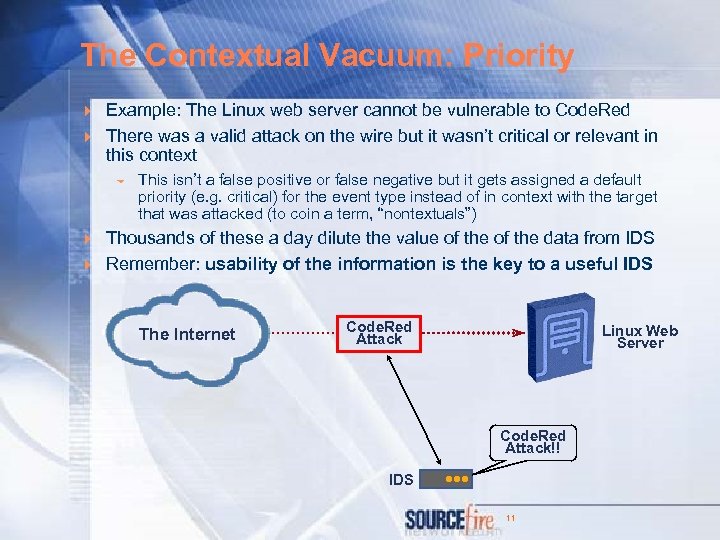 The Contextual Vacuum: Priority 4 Example: The Linux web server cannot be vulnerable to Code. Red 4 There was a valid attack on the wire but it wasn’t critical or relevant in this context 6 This isn’t a false positive or false negative but it gets assigned a default priority (e. g. critical) for the event type instead of in context with the target that was attacked (to coin a term, “nontextuals”) 4 Thousands of these a day dilute the value of the data from IDS 4 Remember: usability of the information is the key to a useful IDS The Internet Code. Red Attack Linux Web Server Code. Red Attack!! IDS • • • 11
The Contextual Vacuum: Priority 4 Example: The Linux web server cannot be vulnerable to Code. Red 4 There was a valid attack on the wire but it wasn’t critical or relevant in this context 6 This isn’t a false positive or false negative but it gets assigned a default priority (e. g. critical) for the event type instead of in context with the target that was attacked (to coin a term, “nontextuals”) 4 Thousands of these a day dilute the value of the data from IDS 4 Remember: usability of the information is the key to a useful IDS The Internet Code. Red Attack Linux Web Server Code. Red Attack!! IDS • • • 11
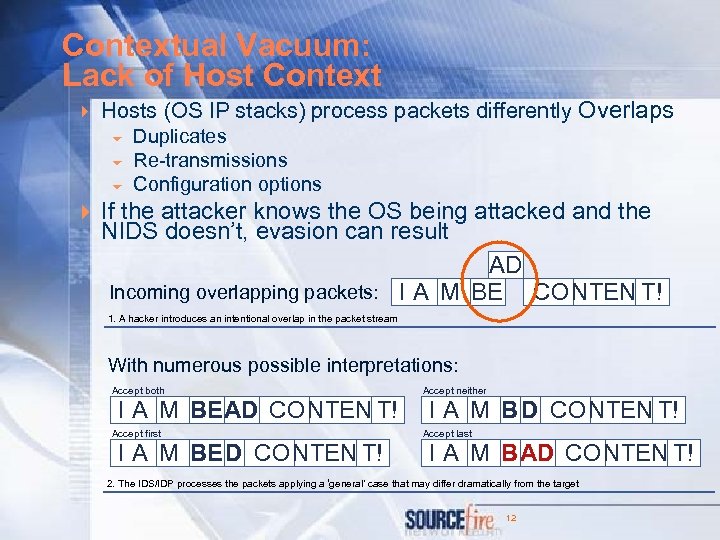 Contextual Vacuum: Lack of Host Context 4 Hosts (OS IP stacks) process packets differently Overlaps 6 Duplicates 6 Re-transmissions 6 Configuration options 4 If the attacker knows the OS being attacked and the NIDS doesn’t, evasion can result AD Incoming overlapping packets: I A M BE CO NTEN T! 1. A hacker introduces an intentional overlap in the packet stream With numerous possible interpretations: Accept both I A M BE AD CO NTEN T! Accept first I A M BE D CO NTEN T! Accept neither I A M B D CO NTEN T! Accept last I A M B AD CO NTEN T! 2. The IDS/IDP processes the packets applying a ‘general’ case that may differ dramatically from the target 12
Contextual Vacuum: Lack of Host Context 4 Hosts (OS IP stacks) process packets differently Overlaps 6 Duplicates 6 Re-transmissions 6 Configuration options 4 If the attacker knows the OS being attacked and the NIDS doesn’t, evasion can result AD Incoming overlapping packets: I A M BE CO NTEN T! 1. A hacker introduces an intentional overlap in the packet stream With numerous possible interpretations: Accept both I A M BE AD CO NTEN T! Accept first I A M BE D CO NTEN T! Accept neither I A M B D CO NTEN T! Accept last I A M B AD CO NTEN T! 2. The IDS/IDP processes the packets applying a ‘general’ case that may differ dramatically from the target 12
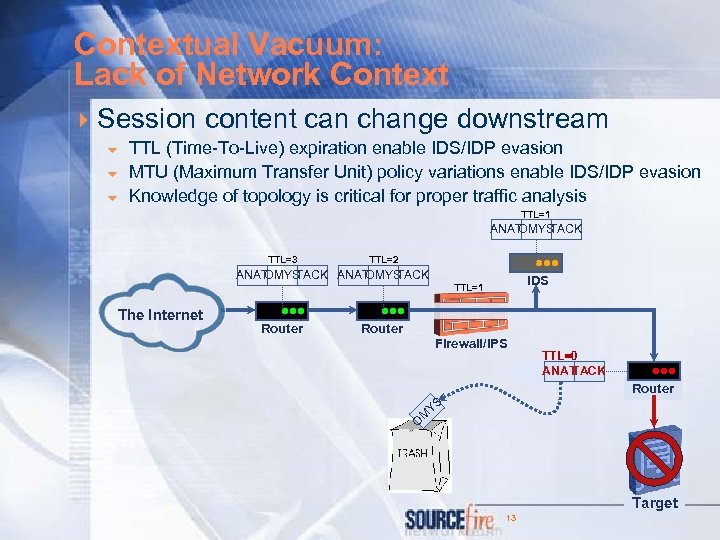 Contextual Vacuum: Lack of Network Context 4 Session content can change downstream 6 6 6 TTL (Time-To-Live) expiration enable IDS/IDP evasion MTU (Maximum Transfer Unit) policy variations enable IDS/IDP evasion Knowledge of topology is critical for proper traffic analysis TTL=1 ANAT OMYS TACK TTL=3 • • • TTL=2 ANAT OMYS TACK The Internet • • • Router IDS TTL=1 • • • Router Firewall/IPS TTL=0 ANAT AT OMYS AN TACK • • • Router YS M O Target 13
Contextual Vacuum: Lack of Network Context 4 Session content can change downstream 6 6 6 TTL (Time-To-Live) expiration enable IDS/IDP evasion MTU (Maximum Transfer Unit) policy variations enable IDS/IDP evasion Knowledge of topology is critical for proper traffic analysis TTL=1 ANAT OMYS TACK TTL=3 • • • TTL=2 ANAT OMYS TACK The Internet • • • Router IDS TTL=1 • • • Router Firewall/IPS TTL=0 ANAT AT OMYS AN TACK • • • Router YS M O Target 13
 How Can We Solve this Problem? 4 Context needs to be driven into network intrusion detection if it is going to get better 4 What elements of context are needed? 6 Network context § Topology 6 Host Context § Host OS § Host Services 6 Exposure Context § Vulnerability classes available against the network 14
How Can We Solve this Problem? 4 Context needs to be driven into network intrusion detection if it is going to get better 4 What elements of context are needed? 6 Network context § Topology 6 Host Context § Host OS § Host Services 6 Exposure Context § Vulnerability classes available against the network 14
 Current Tools for Building Context 4 Active scanners 6 Intermittent picture of network profile § Laptops are frequently disconnected from the network § Many machines run more than one operating system § Compromised servers are easily hidden from active scanners 6 Limited scope § Not all protocols § Not all ports § Not all assets 6 6 6 Strong potential for service disruption Consumption of network bandwidth Conclusions are binary in accuracy, either 100% right or 100% wrong 4 Host-based technologies 6 6 Cannot detect the unknown host or service Impose significant administrative burdens 15
Current Tools for Building Context 4 Active scanners 6 Intermittent picture of network profile § Laptops are frequently disconnected from the network § Many machines run more than one operating system § Compromised servers are easily hidden from active scanners 6 Limited scope § Not all protocols § Not all ports § Not all assets 6 6 6 Strong potential for service disruption Consumption of network bandwidth Conclusions are binary in accuracy, either 100% right or 100% wrong 4 Host-based technologies 6 6 Cannot detect the unknown host or service Impose significant administrative burdens 15
 The Ideal for Building Context 4 Passive network discovery systems (PNDS) are the only workable approach 6 All network participants are observed § All protocols § All ports § All assets 6 Information is persistent § Real-time § All of the time 6 Many techniques can be leveraged and combined § § 6 6 Packet analysis Flow analysis Protocol analysis Confidence model No disruption of network operations Minimal ‘moving parts’ 16
The Ideal for Building Context 4 Passive network discovery systems (PNDS) are the only workable approach 6 All network participants are observed § All protocols § All ports § All assets 6 Information is persistent § Real-time § All of the time 6 Many techniques can be leveraged and combined § § 6 6 Packet analysis Flow analysis Protocol analysis Confidence model No disruption of network operations Minimal ‘moving parts’ 16
 Vulnerability Analysis 4 VA by inference 6 Knowledge about the host and its profile is immediately associated with knowledge about vulnerabilities, exploits, and remediation processes 6 No packets are used to probe targets on the network, purely passive 6 Passive approach allows for constant vulnerability monitoring 4 Necessary to understand the exposure context 4 Confidence model is more appropriate to improving NIDS 17
Vulnerability Analysis 4 VA by inference 6 Knowledge about the host and its profile is immediately associated with knowledge about vulnerabilities, exploits, and remediation processes 6 No packets are used to probe targets on the network, purely passive 6 Passive approach allows for constant vulnerability monitoring 4 Necessary to understand the exposure context 4 Confidence model is more appropriate to improving NIDS 17
 Real-time Change Detection 4 New network assets (and vulnerabilities) 6 Laptops 6 Servers 6 Rogue devices § Wired § Wireless 6 Unauthorized users 4 New network services (and vulnerabilities) 6 Ports 6 Protocols 6 Services 4 Policy violations 6 Devices 6 Protocols 6 Operating systems 6 Services 6 Applications 4 Essential for understanding possible impact of attacks 18
Real-time Change Detection 4 New network assets (and vulnerabilities) 6 Laptops 6 Servers 6 Rogue devices § Wired § Wireless 6 Unauthorized users 4 New network services (and vulnerabilities) 6 Ports 6 Protocols 6 Services 4 Policy violations 6 Devices 6 Protocols 6 Operating systems 6 Services 6 Applications 4 Essential for understanding possible impact of attacks 18
 Benefits of Passive Network Discovery Systems
Benefits of Passive Network Discovery Systems
 IDS: Without Context 20
IDS: Without Context 20
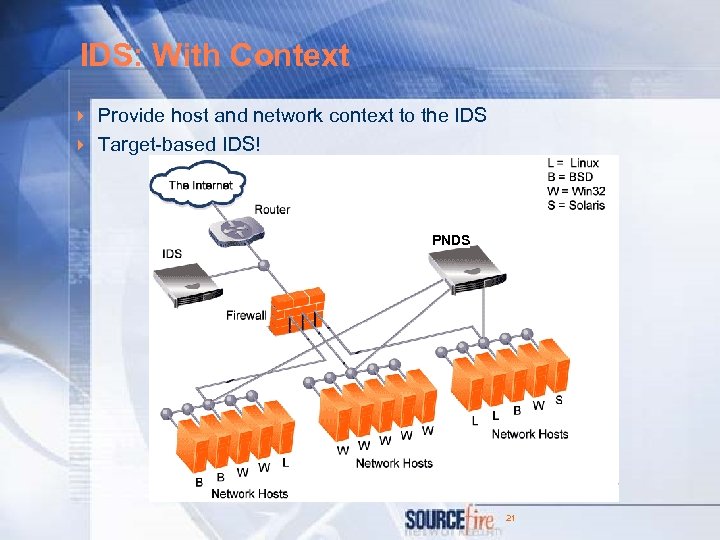 IDS: With Context 4 Provide host and network context to the IDS 4 Target-based IDS! PNDS 21
IDS: With Context 4 Provide host and network context to the IDS 4 Target-based IDS! PNDS 21
 Event->Vulnerability/Change Correlation 4 Prioritization based on potential impact 6 6 6 Events that correlate to nothing are not that interesting Events correlating to vulnerabilities are more interesting Events correlating to vulnerabilities and then affecting change are highly interesting 4 Tiered prioritization 6 6 Relevance Vulnerability Asset Sensitivity Attack Effectiveness 22
Event->Vulnerability/Change Correlation 4 Prioritization based on potential impact 6 6 6 Events that correlate to nothing are not that interesting Events correlating to vulnerabilities are more interesting Events correlating to vulnerabilities and then affecting change are highly interesting 4 Tiered prioritization 6 6 Relevance Vulnerability Asset Sensitivity Attack Effectiveness 22
 Automated Tuning 4 Dynamic implementation of security policies 6 6 Protocols Operating systems Services Applications 4 Protect the network instead of just trying to detect random attacks! 23
Automated Tuning 4 Dynamic implementation of security policies 6 6 Protocols Operating systems Services Applications 4 Protect the network instead of just trying to detect random attacks! 23
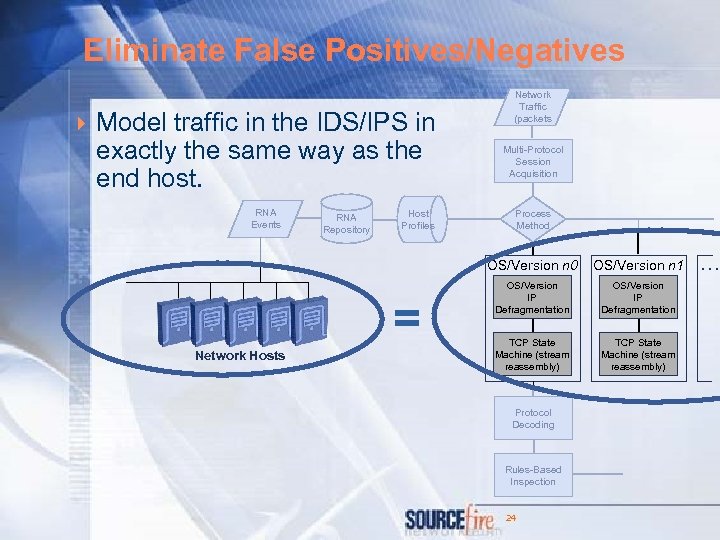 Eliminate False Positives/Negatives 4 Model traffic in the IDS/IPS in exactly the same way as the end host. RNA Events RNA Repository Host Profiles Network Traffic (packets Multi-Protocol Session Acquisition Process Method OS/Version n 0 = Network Hosts OS/Version n 1 OS/Version IP Defragmentation TCP State Machine (stream reassembly) Protocol Decoding Rules-Based Inspection 24 …
Eliminate False Positives/Negatives 4 Model traffic in the IDS/IPS in exactly the same way as the end host. RNA Events RNA Repository Host Profiles Network Traffic (packets Multi-Protocol Session Acquisition Process Method OS/Version n 0 = Network Hosts OS/Version n 1 OS/Version IP Defragmentation TCP State Machine (stream reassembly) Protocol Decoding Rules-Based Inspection 24 …
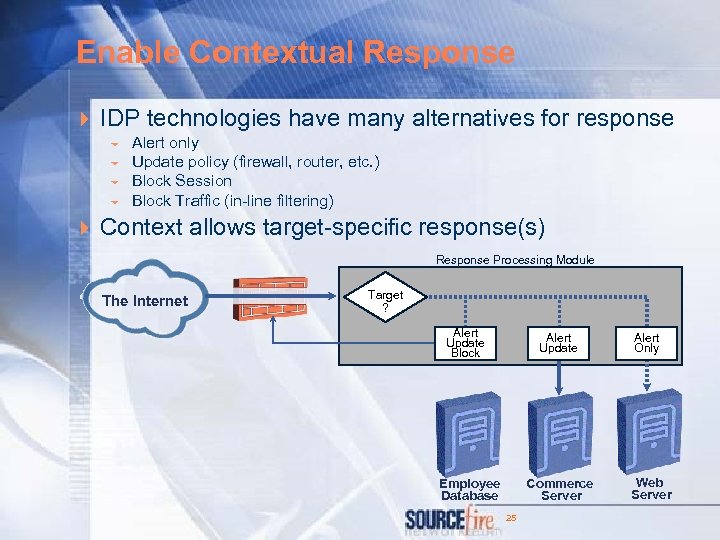 Enable Contextual Response 4 IDP technologies have many alternatives for response 6 6 Alert only Update policy (firewall, router, etc. ) Block Session Block Traffic (in-line filtering) 4 Context allows target-specific response(s) Response Processing Module The Internet Target ? Alert Update Block Alert Update Employee Database Commerce Server 25 Alert Only Web Server
Enable Contextual Response 4 IDP technologies have many alternatives for response 6 6 Alert only Update policy (firewall, router, etc. ) Block Session Block Traffic (in-line filtering) 4 Context allows target-specific response(s) Response Processing Module The Internet Target ? Alert Update Block Alert Update Employee Database Commerce Server 25 Alert Only Web Server
 Conclusions
Conclusions
 The Concept of NID Needs to Evolve 4 Algorithms are not enough 4 False positive picture has not improved dramatically in the past 10 years 4 Protecting the packets/protocols is a broken model 27
The Concept of NID Needs to Evolve 4 Algorithms are not enough 4 False positive picture has not improved dramatically in the past 10 years 4 Protecting the packets/protocols is a broken model 27
 PNDS Are the Right Answer 4 Vulnerability scanners still solve problems, they just don’t solve this one very well 4 We cannot expect to provide accurate intrusion detection in environments where attackers have better information about the targets than the defenders 4 PNDS address all the problems of context generation in a way that is appropriate for large, highly changeable environments 4 First commercial PNDS will be available in December (from Sourcefire) 28
PNDS Are the Right Answer 4 Vulnerability scanners still solve problems, they just don’t solve this one very well 4 We cannot expect to provide accurate intrusion detection in environments where attackers have better information about the targets than the defenders 4 PNDS address all the problems of context generation in a way that is appropriate for large, highly changeable environments 4 First commercial PNDS will be available in December (from Sourcefire) 28
 Questions & Answers
Questions & Answers


