Mod 6 - MVA Defense-in-Depth Windows Security.pptx
- Количество слайдов: 16
 Pass-the-Hash
Pass-the-Hash
 Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
 Module Insights Explore the major thread coming with pass-the-hash and the mitigation options available.
Module Insights Explore the major thread coming with pass-the-hash and the mitigation options available.
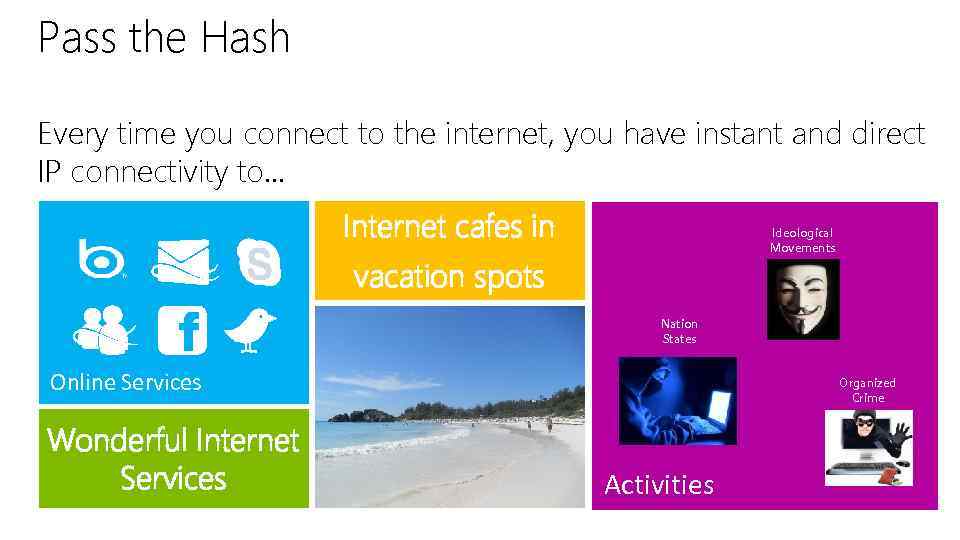 Pass the Hash Every time you connect to the internet, you have instant and direct IP connectivity to… Internet cafes in Ideological Movements vacation spots Nation States Online Services Wonderful Internet Services Organized Crime Activities
Pass the Hash Every time you connect to the internet, you have instant and direct IP connectivity to… Internet cafes in Ideological Movements vacation spots Nation States Online Services Wonderful Internet Services Organized Crime Activities
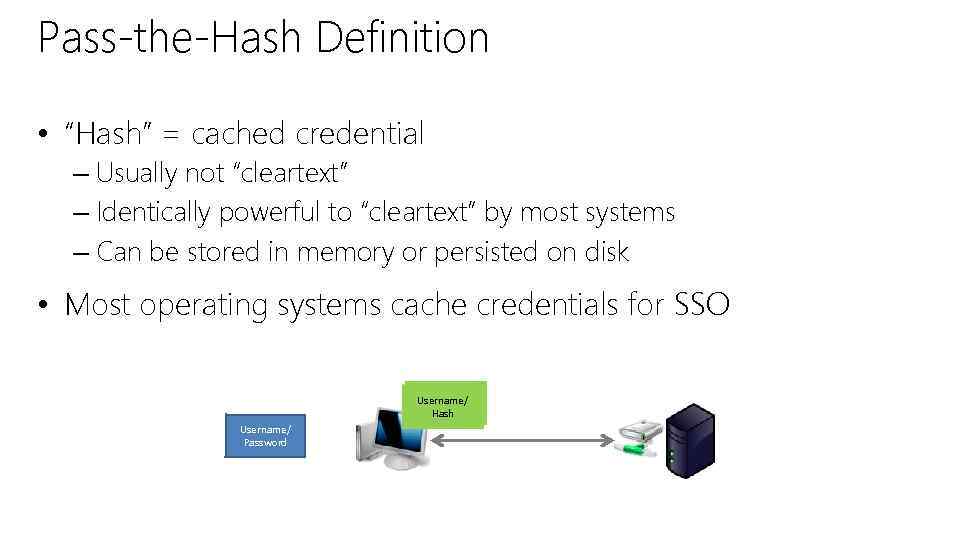 Pass-the-Hash Definition • “Hash” = cached credential – Usually not “cleartext” – Identically powerful to “cleartext” by most systems – Can be stored in memory or persisted on disk • Most operating systems cache credentials for SSO Username/ Hash Username/ Password
Pass-the-Hash Definition • “Hash” = cached credential – Usually not “cleartext” – Identically powerful to “cleartext” by most systems – Can be stored in memory or persisted on disk • Most operating systems cache credentials for SSO Username/ Hash Username/ Password
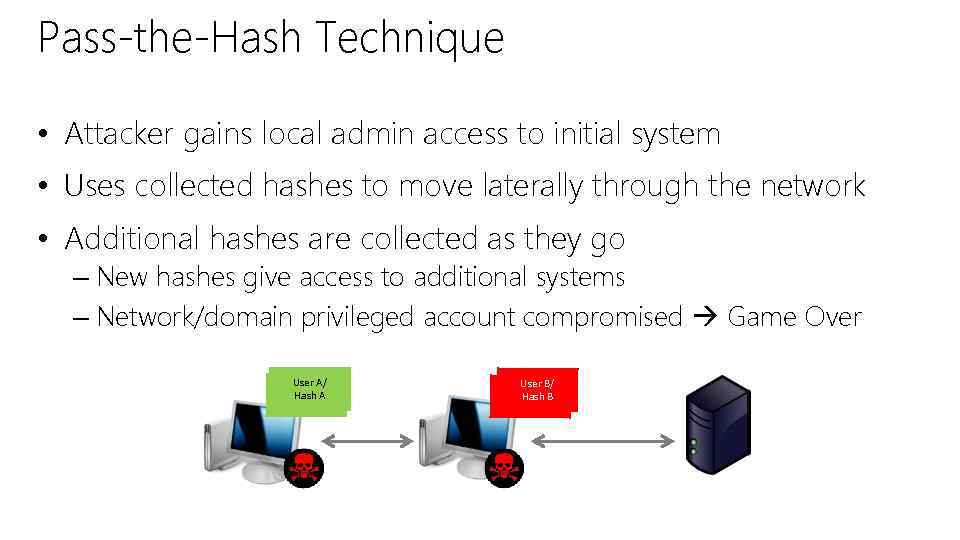 Pass-the-Hash Technique • Attacker gains local admin access to initial system • Uses collected hashes to move laterally through the network • Additional hashes are collected as they go – New hashes give access to additional systems – Network/domain privileged account compromised Game Over User A/ Hash A User B/ Hash B
Pass-the-Hash Technique • Attacker gains local admin access to initial system • Uses collected hashes to move laterally through the network • Additional hashes are collected as they go – New hashes give access to additional systems – Network/domain privileged account compromised Game Over User A/ Hash A User B/ Hash B
 Attack Scenario Attack activities Lateral movement Description In this activity, the attacker uses the credentials obtained from a compromised computer to gain access to another computer of the same value to the organization Privilege escalation In this activity, the attacker uses the credentials obtained from a compromised computer to gain access to another computer of a higher value to the organization.
Attack Scenario Attack activities Lateral movement Description In this activity, the attacker uses the credentials obtained from a compromised computer to gain access to another computer of the same value to the organization Privilege escalation In this activity, the attacker uses the credentials obtained from a compromised computer to gain access to another computer of a higher value to the organization.
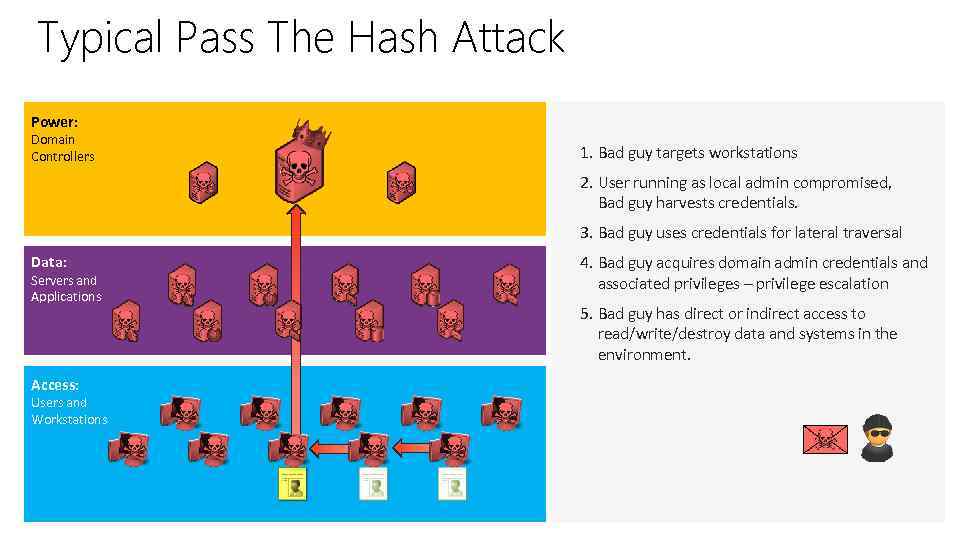 Typical Pass The Hash Attack Power: Domain Controllers 1. Bad guy targets workstations 2. User running as local admin compromised, Bad guy harvests credentials. 3. Bad guy uses credentials for lateral traversal Data: Servers and Applications Access: Users and Workstations 4. Bad guy acquires domain admin credentials and associated privileges – privilege escalation 5. Bad guy has direct or indirect access to read/write/destroy data and systems in the environment.
Typical Pass The Hash Attack Power: Domain Controllers 1. Bad guy targets workstations 2. User running as local admin compromised, Bad guy harvests credentials. 3. Bad guy uses credentials for lateral traversal Data: Servers and Applications Access: Users and Workstations 4. Bad guy acquires domain admin credentials and associated privileges – privilege escalation 5. Bad guy has direct or indirect access to read/write/destroy data and systems in the environment.
 DEMO Windows Credential Editor NTLM Pass-the-Hash
DEMO Windows Credential Editor NTLM Pass-the-Hash
 DEMO Crack the Hash
DEMO Crack the Hash
 Why can’t Microsoft release an update to fix it? Thesethe Hash and other credential theft attackscomputer’s memory, disks, Pass accounts have complete control over the exploit the access that an and processor resources. attacker gains by compromising an account in the local administrators group.
Why can’t Microsoft release an update to fix it? Thesethe Hash and other credential theft attackscomputer’s memory, disks, Pass accounts have complete control over the exploit the access that an and processor resources. attacker gains by compromising an account in the local administrators group.
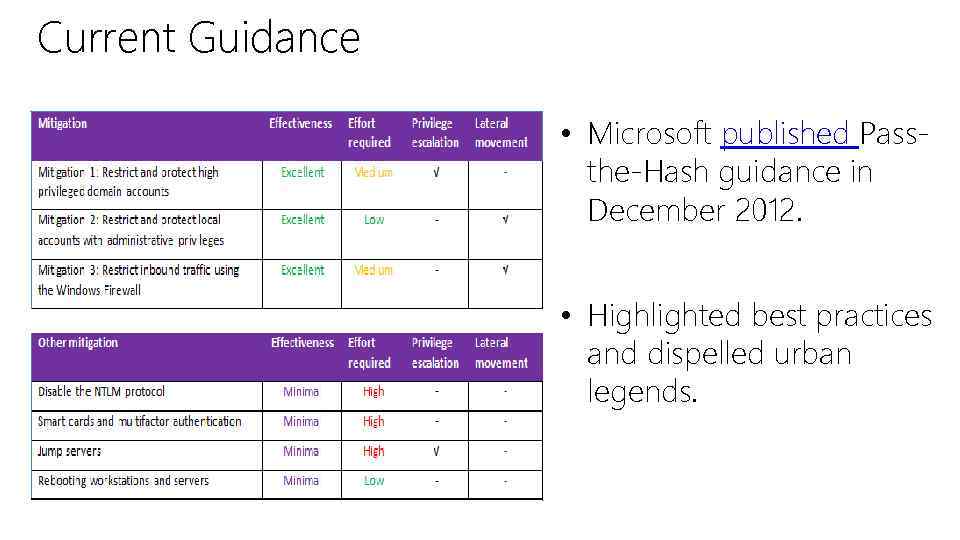 Current Guidance • Microsoft published Passthe-Hash guidance in December 2012. • Highlighted best practices and dispelled urban legends.
Current Guidance • Microsoft published Passthe-Hash guidance in December 2012. • Highlighted best practices and dispelled urban legends.
 Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
 Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
 © 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
© 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.


