a981a9668d52ecf92d3d5420fea62a71.ppt
- Количество слайдов: 86
 Part II : Computer Security and the VVSG October 15 -17, 2007 Barbara Guttman Nelson Hastings National Institute of Standards and Technology barbara. guttman@nist. gov nelson. hastings@nist. gov
Part II : Computer Security and the VVSG October 15 -17, 2007 Barbara Guttman Nelson Hastings National Institute of Standards and Technology barbara. guttman@nist. gov nelson. hastings@nist. gov
 Agenda n n n Security Requirements Overview Review of Chapter 4: Security and Audit Architecture Review of Chapter 5: General Security Requirements Next VVSG Training Oct 15 -17, 2007 Page 2
Agenda n n n Security Requirements Overview Review of Chapter 4: Security and Audit Architecture Review of Chapter 5: General Security Requirements Next VVSG Training Oct 15 -17, 2007 Page 2
 Security Requirements Overview n n The security requirements of the next VVSG work together to support equipment security Difficult to understand security provided by a single requirement or set of requirements without understanding how requirements relate to each other Next VVSG Training Oct 15 -17, 2007 Page 3
Security Requirements Overview n n The security requirements of the next VVSG work together to support equipment security Difficult to understand security provided by a single requirement or set of requirements without understanding how requirements relate to each other Next VVSG Training Oct 15 -17, 2007 Page 3
 Security Requirements Overview n For example, n n Cryptography section addresses how cryptography is implemented by equipment Software installation and electronic records sections address how cryptography, specifically digital signatures are use by equipment to support security Next VVSG Training Oct 15 -17, 2007 Page 4
Security Requirements Overview n For example, n n Cryptography section addresses how cryptography is implemented by equipment Software installation and electronic records sections address how cryptography, specifically digital signatures are use by equipment to support security Next VVSG Training Oct 15 -17, 2007 Page 4
 Security Requirements Overview n Documentation requirements related to security n n Part 2: Documentation Requirements System Security Specification n n Section 3. 5 of the Technical Data Package (TDP) Section 4. 3 of the user documentation Next VVSG Training Oct 15 -17, 2007 Page 5
Security Requirements Overview n Documentation requirements related to security n n Part 2: Documentation Requirements System Security Specification n n Section 3. 5 of the Technical Data Package (TDP) Section 4. 3 of the user documentation Next VVSG Training Oct 15 -17, 2007 Page 5
 Security Requirements Overview n Section 3. 5 System Security Specification (TDP) n n Provided to test lab to assist in the testing campaign General documentation about security including n n Security Architecture Security Threat Controls Security Testing and vulnerability analysis Detailed implementation specification for each security mechanism Next VVSG Training Oct 15 -17, 2007 Page 6
Security Requirements Overview n Section 3. 5 System Security Specification (TDP) n n Provided to test lab to assist in the testing campaign General documentation about security including n n Security Architecture Security Threat Controls Security Testing and vulnerability analysis Detailed implementation specification for each security mechanism Next VVSG Training Oct 15 -17, 2007 Page 6
 Security Requirements Overview n Section 4. 3: System Security Specification (User documentation) n n n Provided to user of the voting system including test labs How security mechanism are to be used Information needed to support a features use such as a list of software to be installed Next VVSG Training Oct 15 -17, 2007 Page 7
Security Requirements Overview n Section 4. 3: System Security Specification (User documentation) n n n Provided to user of the voting system including test labs How security mechanism are to be used Information needed to support a features use such as a list of software to be installed Next VVSG Training Oct 15 -17, 2007 Page 7
 Chapter 4: Security and Audit Architecture n n n Section 4. 2: Requirements to support auditing Section 4. 3: Electronic Records Section 4. 4 Independent Voter Verifiable Records (IVVR) n n VVPAT PCOS Next VVSG Training Oct 15 -17, 2007 Page 8
Chapter 4: Security and Audit Architecture n n n Section 4. 2: Requirements to support auditing Section 4. 3: Electronic Records Section 4. 4 Independent Voter Verifiable Records (IVVR) n n VVPAT PCOS Next VVSG Training Oct 15 -17, 2007 Page 8
 Software Independence n n n TGDC Resolution 06 -06 requires software independence (SI) Software Independence means that changes must be detectable Detectable, in practice, means auditable SI = Auditable Next VVSG Training Oct 15 -17, 2007 Page 9
Software Independence n n n TGDC Resolution 06 -06 requires software independence (SI) Software Independence means that changes must be detectable Detectable, in practice, means auditable SI = Auditable Next VVSG Training Oct 15 -17, 2007 Page 9
 Why Does the TGDC Want SI? n n With software, it is pretty easy to make a screen say one thing, but record another thing inside the computer. The hard part is making plausible, directed changes. Next VVSG Training Oct 15 -17, 2007 Page 10
Why Does the TGDC Want SI? n n With software, it is pretty easy to make a screen say one thing, but record another thing inside the computer. The hard part is making plausible, directed changes. Next VVSG Training Oct 15 -17, 2007 Page 10
 Auditing Records n n n Two types of records: Electronic & Independent 4. 3 address electronic records 4. 4 addresses independent records Next VVSG Training Oct 15 -17, 2007 Page 11
Auditing Records n n n Two types of records: Electronic & Independent 4. 3 address electronic records 4. 4 addresses independent records Next VVSG Training Oct 15 -17, 2007 Page 11
 Won’t a Test Lab Catch This? n No, software, especially the software that runs the user interface, is really complicated. Next VVSG Training Oct 15 -17, 2007 Page 12
Won’t a Test Lab Catch This? n No, software, especially the software that runs the user interface, is really complicated. Next VVSG Training Oct 15 -17, 2007 Page 12
 Famous Software that wasn’t doing what we thought it was doing n n Some trojan horse (or 2) NC voting example Therac 25 phishing Next VVSG Training Oct 15 -17, 2007 Page 13
Famous Software that wasn’t doing what we thought it was doing n n Some trojan horse (or 2) NC voting example Therac 25 phishing Next VVSG Training Oct 15 -17, 2007 Page 13
 Therac 25 n n After this second Tyler accident, the ETCC physicist immediately took the machine out of service and called AECL to alert the company to this second apparent overexposure. The Tyler physicist then began his own careful investigation. He worked with the operator, who remembered exactly what she had done on this occasion. After a great deal of effort, they were eventually able to elicit the Malfunction 54 message. They determined that data-entry speed during editing was the key factor in producing the error condition: If the prescription data was edited at a fast pace (as is natural for someone who has repeated the procedure a large number of times), the overdose occurred. http: //courses. cs. vt. edu/~cs 3604/lib/Therac_25/Therac_2. html Next VVSG Training Oct 15 -17, 2007 Page 14
Therac 25 n n After this second Tyler accident, the ETCC physicist immediately took the machine out of service and called AECL to alert the company to this second apparent overexposure. The Tyler physicist then began his own careful investigation. He worked with the operator, who remembered exactly what she had done on this occasion. After a great deal of effort, they were eventually able to elicit the Malfunction 54 message. They determined that data-entry speed during editing was the key factor in producing the error condition: If the prescription data was edited at a fast pace (as is natural for someone who has repeated the procedure a large number of times), the overdose occurred. http: //courses. cs. vt. edu/~cs 3604/lib/Therac_25/Therac_2. html Next VVSG Training Oct 15 -17, 2007 Page 14
 How Does the VVSG Address Auditability? n n n Requires equipment to have features that can be used for various types of audits Requires documentation NOTE – The VVSG itself does not require auditing – This is procedural and outside the scope. Next VVSG Training Oct 15 -17, 2007 Page 15
How Does the VVSG Address Auditability? n n n Requires equipment to have features that can be used for various types of audits Requires documentation NOTE – The VVSG itself does not require auditing – This is procedural and outside the scope. Next VVSG Training Oct 15 -17, 2007 Page 15
 4. 2 Requirements for Supporting Audits n Types of Audits n n n Pollbook Audit Hand Audit of Independent Record Ballot Count and Vote Total Audit Observational Testing Note: Parallel Testing is another type of audit, but it is not included because it does not levy requirements on the equipment Next VVSG Training Oct 15 -17, 2007 Page 16
4. 2 Requirements for Supporting Audits n Types of Audits n n n Pollbook Audit Hand Audit of Independent Record Ballot Count and Vote Total Audit Observational Testing Note: Parallel Testing is another type of audit, but it is not included because it does not levy requirements on the equipment Next VVSG Training Oct 15 -17, 2007 Page 16
 Audit Records n Two types of records: n n Electronic records Independent Voter Verifiable Records (IVVR) 4. 3 address electronic records 4. 4 addresses independent records Next VVSG Training Oct 15 -17, 2007 Page 17
Audit Records n Two types of records: n n Electronic records Independent Voter Verifiable Records (IVVR) 4. 3 address electronic records 4. 4 addresses independent records Next VVSG Training Oct 15 -17, 2007 Page 17
 4. 3 Electronic Records n General Requirements n n n Open Format Printable Digitally signed for Integrity & Authenticity Next VVSG Training Oct 15 -17, 2007 Page 18
4. 3 Electronic Records n General Requirements n n n Open Format Printable Digitally signed for Integrity & Authenticity Next VVSG Training Oct 15 -17, 2007 Page 18
 4. 3 Electronic Records n Information/data requirements n n Contain all relevant data List for Tabulator (4. 3. 2) List for EMS (4. 3. 3) Generally: n n n Totals Read ballots Counted ballots Rejected ballots Overvotes/undervotes Write-ins Next VVSG Training Oct 15 -17, 2007 Page 19
4. 3 Electronic Records n Information/data requirements n n Contain all relevant data List for Tabulator (4. 3. 2) List for EMS (4. 3. 3) Generally: n n n Totals Read ballots Counted ballots Rejected ballots Overvotes/undervotes Write-ins Next VVSG Training Oct 15 -17, 2007 Page 19
 4. 4 Independent Voter Verifiable Records (IVVR) n What is an independent voter verifiable record? (4. 4. 1) n n Direct verification by voter Support for hand auditing Various security and operational properties (can be rejected/durable) Doesn’t this mean paper? Next VVSG Training Oct 15 -17, 2007 Page 20
4. 4 Independent Voter Verifiable Records (IVVR) n What is an independent voter verifiable record? (4. 4. 1) n n Direct verification by voter Support for hand auditing Various security and operational properties (can be rejected/durable) Doesn’t this mean paper? Next VVSG Training Oct 15 -17, 2007 Page 20
 4. 4 Independent Voter Verifiable Records (IVVR) n n n Direct review (by voter & election official) Can support a hand audit Can support a recount Durable Tamper evidence Support for Privacy Next VVSG Training Oct 15 -17, 2007 Page 21
4. 4 Independent Voter Verifiable Records (IVVR) n n n Direct review (by voter & election official) Can support a hand audit Can support a recount Durable Tamper evidence Support for Privacy Next VVSG Training Oct 15 -17, 2007 Page 21
 4. 4 Independent Voter Verifiable Records (IVVR) n n n Public Format Sufficient Information (ballot configuration, not just selections) No codebook required Support for multiple physical media Able to be accepted or reject (per media) Non-human readable allowed (public format) Next VVSG Training Oct 15 -17, 2007 Page 22
4. 4 Independent Voter Verifiable Records (IVVR) n n n Public Format Sufficient Information (ballot configuration, not just selections) No codebook required Support for multiple physical media Able to be accepted or reject (per media) Non-human readable allowed (public format) Next VVSG Training Oct 15 -17, 2007 Page 22
 4. 4 Independent Voter Verifiable Records (IVVR) n Two current types of IVVR n n VVPAT Optical Scan Next VVSG Training Oct 15 -17, 2007 Page 23
4. 4 Independent Voter Verifiable Records (IVVR) n Two current types of IVVR n n VVPAT Optical Scan Next VVSG Training Oct 15 -17, 2007 Page 23
 4. 4. 2 VVPAT n n VVPAT & Accessibility addressed by Sharon. Note need for observational testing Many operational requirements Paper rolls allowed Next VVSG Training Oct 15 -17, 2007 Page 24
4. 4. 2 VVPAT n n VVPAT & Accessibility addressed by Sharon. Note need for observational testing Many operational requirements Paper rolls allowed Next VVSG Training Oct 15 -17, 2007 Page 24
 4. 4. 3 PCOS n n Few additional security requirements Allow non-human readable marks (record identifiers, batch information, integrity checks) Next VVSG Training Oct 15 -17, 2007 Page 25
4. 4. 3 PCOS n n Few additional security requirements Allow non-human readable marks (record identifiers, batch information, integrity checks) Next VVSG Training Oct 15 -17, 2007 Page 25
 Chapter 5: General Security Requirements n n n n Section 5. 1: Section 5. 2: Section 5. 3: Section 5. 4: Section 5. 5: Section 5. 6: Section 5. 7: Section 5. 8: Devices Next VVSG Training Cryptography Setup Inspection Software Installation Access Control System Integrity Management Communication Security System Event Logging Physical Security for Voting Oct 15 -17, 2007 Page 26
Chapter 5: General Security Requirements n n n n Section 5. 1: Section 5. 2: Section 5. 3: Section 5. 4: Section 5. 5: Section 5. 6: Section 5. 7: Section 5. 8: Devices Next VVSG Training Cryptography Setup Inspection Software Installation Access Control System Integrity Management Communication Security System Event Logging Physical Security for Voting Oct 15 -17, 2007 Page 26
 5. 1 Cryptography n Powerful basic security control n n Integrity of information Authentication of information Requirements developed to provide easy use and maintenance Use strength of existing federal standards Next VVSG Training Oct 15 -17, 2007 Page 27
5. 1 Cryptography n Powerful basic security control n n Integrity of information Authentication of information Requirements developed to provide easy use and maintenance Use strength of existing federal standards Next VVSG Training Oct 15 -17, 2007 Page 27
 5. 1 Cryptography n Implementation of cryptography n n n Public and Secret Key cryptography Not cryptographic voting protocols (a. k. a End-to-End voting systems) Many sections of the next VVSG leverage the security features supported by cryptography Next VVSG Training Oct 15 -17, 2007 Page 28
5. 1 Cryptography n Implementation of cryptography n n n Public and Secret Key cryptography Not cryptographic voting protocols (a. k. a End-to-End voting systems) Many sections of the next VVSG leverage the security features supported by cryptography Next VVSG Training Oct 15 -17, 2007 Page 28
 5. 1 Cryptography n FIPS 140 -2 validated cryptographic module n n A cryptographic module is hardware, firmware, and/or software that implements cryptographic functions (such as encryption, decryption, and key generation). Minimum strength of cryptography Next VVSG Training Oct 15 -17, 2007 Page 29
5. 1 Cryptography n FIPS 140 -2 validated cryptographic module n n A cryptographic module is hardware, firmware, and/or software that implements cryptographic functions (such as encryption, decryption, and key generation). Minimum strength of cryptography Next VVSG Training Oct 15 -17, 2007 Page 29
 5. 1 Cryptography n Signature Module n A hardware cryptographic module n n FIPS 140 -2 Level 2 (out of 4) with physical security being Level 3 Generates digital signatures Generates and stores private signature keys Permanently attached the equipment Next VVSG Training Oct 15 -17, 2007 Page 30
5. 1 Cryptography n Signature Module n A hardware cryptographic module n n FIPS 140 -2 Level 2 (out of 4) with physical security being Level 3 Generates digital signatures Generates and stores private signature keys Permanently attached the equipment Next VVSG Training Oct 15 -17, 2007 Page 30
 5. 1 Cryptography n Types of keys within a Signature Module (SM) n Device Signature Key (DSK) n n n Associated with a device for its lifetime Signatures traceable to specific pieces of equipment Election Signature Key (ESK) n n n Generated once per election cycle Associated with a device’s specific election cycle Signatures traceable to electronic records for a given election Next VVSG Training Oct 15 -17, 2007 Page 31
5. 1 Cryptography n Types of keys within a Signature Module (SM) n Device Signature Key (DSK) n n n Associated with a device for its lifetime Signatures traceable to specific pieces of equipment Election Signature Key (ESK) n n n Generated once per election cycle Associated with a device’s specific election cycle Signatures traceable to electronic records for a given election Next VVSG Training Oct 15 -17, 2007 Page 31
 5. 1 Cryptography n Device Signature Key (DSK) n n Generate using a nondeterministic random number generator Public Key certificate - self signed or CA Unique identifier on an external surface of the equipment and in certificate Signing of n n n Election signature key certificate Election key closeout records Device signature key certificates Next VVSG Training Oct 15 -17, 2007 Page 32
5. 1 Cryptography n Device Signature Key (DSK) n n Generate using a nondeterministic random number generator Public Key certificate - self signed or CA Unique identifier on an external surface of the equipment and in certificate Signing of n n n Election signature key certificate Election key closeout records Device signature key certificates Next VVSG Training Oct 15 -17, 2007 Page 32
 5. 1 Cryptography n Election Signature Key (ESK) n n Generate using a nondeterministic random number generator Used to digitally sign electronic records for an election cycle Destroyed as part of election close out Counters to keep track of the number of ESKs generated and signatures generated by a given ESK Next VVSG Training Oct 15 -17, 2007 Page 33
5. 1 Cryptography n Election Signature Key (ESK) n n Generate using a nondeterministic random number generator Used to digitally sign electronic records for an election cycle Destroyed as part of election close out Counters to keep track of the number of ESKs generated and signatures generated by a given ESK Next VVSG Training Oct 15 -17, 2007 Page 33
 5. 1 Cryptography n Election Signature Key (ESK) Certificates are signed by Device Signature Key (DSK) Device Signature (private) key Election Signature (Public) Key: Signature DSK Next VVSG Training Oct 15 -17, 2007 Page 34
5. 1 Cryptography n Election Signature Key (ESK) Certificates are signed by Device Signature Key (DSK) Device Signature (private) key Election Signature (Public) Key: Signature DSK Next VVSG Training Oct 15 -17, 2007 Page 34
 5. 1 Cryptography n Election key closeout record n n n Electronic record Public key of Election Signature Key (ESK) (certificate or message digest/hash? ? ? ) Number of signatures generated by Election Signature Key (ESK) number of the device Signed by the Device Signature Key (DSK) Next VVSG Training Oct 15 -17, 2007 Page 35
5. 1 Cryptography n Election key closeout record n n n Electronic record Public key of Election Signature Key (ESK) (certificate or message digest/hash? ? ? ) Number of signatures generated by Election Signature Key (ESK) number of the device Signed by the Device Signature Key (DSK) Next VVSG Training Oct 15 -17, 2007 Page 35
 5. 1 Cryptography n Technical Date Package (TDP) requirements n n n Certificate fields for Device Signature Key (DSK) and Election Signature Key (ESK) Specific cryptographic algorithms used Election Closeout Record format specification Next VVSG Training Oct 15 -17, 2007 Page 36
5. 1 Cryptography n Technical Date Package (TDP) requirements n n n Certificate fields for Device Signature Key (DSK) and Election Signature Key (ESK) Specific cryptographic algorithms used Election Closeout Record format specification Next VVSG Training Oct 15 -17, 2007 Page 36
 5. 2 Setup Inspection n Requirements related to the capabilities to inspect properties of voting devices n n Improves voting device management and maintenance Reflects new focus of requirements in light of software independence (SI) approach n Called Setup Validation in VVSG 2005 Next VVSG Training Oct 15 -17, 2007 Page 37
5. 2 Setup Inspection n Requirements related to the capabilities to inspect properties of voting devices n n Improves voting device management and maintenance Reflects new focus of requirements in light of software independence (SI) approach n Called Setup Validation in VVSG 2005 Next VVSG Training Oct 15 -17, 2007 Page 37
 5. 2 Setup Inspection n Inspections generate system event log entries n n Time and date Information related to the specific inspection n n Location of software files Component calibration Result of inspection Voting device unique identification Individual (or role) that performed inspection Next VVSG Training Oct 15 -17, 2007 Page 38
5. 2 Setup Inspection n Inspections generate system event log entries n n Time and date Information related to the specific inspection n n Location of software files Component calibration Result of inspection Voting device unique identification Individual (or role) that performed inspection Next VVSG Training Oct 15 -17, 2007 Page 38
 5. 2 Setup Inspections n Software identification verification n n Ability to query/inspect the voting device to determine what software is installed Software integrity verification n Using digital signatures and hash n n n Designated repositories such as National Software Reference Library (NSRL) Voting Device Owner - Jurisdiction SI approach allows for internal verification n NO external interface requirement like in VVSG 2005 Next VVSG Training Oct 15 -17, 2007 Page 39
5. 2 Setup Inspections n Software identification verification n n Ability to query/inspect the voting device to determine what software is installed Software integrity verification n Using digital signatures and hash n n n Designated repositories such as National Software Reference Library (NSRL) Voting Device Owner - Jurisdiction SI approach allows for internal verification n NO external interface requirement like in VVSG 2005 Next VVSG Training Oct 15 -17, 2007 Page 39
 5. 2 Setup Inspection n Voting device election information inspection n Ability to query/inspect the storage locations containing information that changes during an election n n Number of ballots cast Totals for a given contest Generalized register and variable terminology from VVSG 2005 Support zero total inspections prior to use in election Next VVSG Training Oct 15 -17, 2007 Page 40
5. 2 Setup Inspection n Voting device election information inspection n Ability to query/inspect the storage locations containing information that changes during an election n n Number of ballots cast Totals for a given contest Generalized register and variable terminology from VVSG 2005 Support zero total inspections prior to use in election Next VVSG Training Oct 15 -17, 2007 Page 40
 5. 2 Setup Inspection n Inspection of properties of voting device components n n n Backup power supply level Cabling connectivity indicator Communications operational status and on/off indicators Consumables remaining indicator Calibration determination and adjustments Next VVSG Training Oct 15 -17, 2007 Page 41
5. 2 Setup Inspection n Inspection of properties of voting device components n n n Backup power supply level Cabling connectivity indicator Communications operational status and on/off indicators Consumables remaining indicator Calibration determination and adjustments Next VVSG Training Oct 15 -17, 2007 Page 41
 5. 2 Setup Inspection n User documentation requirements n Model setup inspection process supported by voting device n n n Model inspection check list of other properties supported by the voting device n n Minimally includes items mentioned previously Manufacturer provided Risks related to not performing a given inspection Next VVSG Training Oct 15 -17, 2007 Page 42
5. 2 Setup Inspection n User documentation requirements n Model setup inspection process supported by voting device n n n Model inspection check list of other properties supported by the voting device n n Minimally includes items mentioned previously Manufacturer provided Risks related to not performing a given inspection Next VVSG Training Oct 15 -17, 2007 Page 42
 5. 3 Software Installation n Requirements related to the installation of software on voting devices n n Also covers access and modification of configuration files Uses digital signatures to provide the ability to verify the authentication and integrity of the software n n National Software Reference Library (NSRL) Designated repositories Next VVSG Training Oct 15 -17, 2007 Page 43
5. 3 Software Installation n Requirements related to the installation of software on voting devices n n Also covers access and modification of configuration files Uses digital signatures to provide the ability to verify the authentication and integrity of the software n n National Software Reference Library (NSRL) Designated repositories Next VVSG Training Oct 15 -17, 2007 Page 43
 5. 3 Software Installation n n Software installation only when in prevoting state Only individuals with an administrator or central election official role can install software n Central Election Officials limited to election specific software or data files Next VVSG Training Oct 15 -17, 2007 Page 44
5. 3 Software Installation n n Software installation only when in prevoting state Only individuals with an administrator or central election official role can install software n Central Election Officials limited to election specific software or data files Next VVSG Training Oct 15 -17, 2007 Page 44
 5. 3 Software Installation n Digital signature verification of software before installation Externally visible alert when software installation fails Software to only be able to be installed using documented procedures Next VVSG Training Oct 15 -17, 2007 Page 45
5. 3 Software Installation n Digital signature verification of software before installation Externally visible alert when software installation fails Software to only be able to be installed using documented procedures Next VVSG Training Oct 15 -17, 2007 Page 45
 5. 3 Software Installation n Software installation generates system event log entries n n n Time and date Software name and version Location of installation - directory path Digital signature verification - result and signature source Result of software installation Next VVSG Training Oct 15 -17, 2007 Page 46
5. 3 Software Installation n Software installation generates system event log entries n n n Time and date Software name and version Location of installation - directory path Digital signature verification - result and signature source Result of software installation Next VVSG Training Oct 15 -17, 2007 Page 46
 5. 3 Software Installation n Technical Data Package (TDP) requirements n List of all software to be installed on voting system n n n n Name and version Manufacturer contract information Type of software Software documentation Location software is to be installed Functionality provided by the software Dependences and interactions between the software Next VVSG Training Oct 15 -17, 2007 Page 47
5. 3 Software Installation n Technical Data Package (TDP) requirements n List of all software to be installed on voting system n n n n Name and version Manufacturer contract information Type of software Software documentation Location software is to be installed Functionality provided by the software Dependences and interactions between the software Next VVSG Training Oct 15 -17, 2007 Page 47
 5. 3 Software Installation n User documentation n n List of all software to be installed on voting system particularly election specific software Hardware and software need to install software Next VVSG Training Oct 15 -17, 2007 Page 48
5. 3 Software Installation n User documentation n n List of all software to be installed on voting system particularly election specific software Hardware and software need to install software Next VVSG Training Oct 15 -17, 2007 Page 48
 5. 3 Software Installation n Procedures used to perform software installation n n n No use of compilers COTS software to be obtained via open market How to create a baseline binary image for replication Preparations of erasable media Software from unalterable media - CDs Record resulting from the installation procedure Next VVSG Training Oct 15 -17, 2007 Page 49
5. 3 Software Installation n Procedures used to perform software installation n n n No use of compilers COTS software to be obtained via open market How to create a baseline binary image for replication Preparations of erasable media Software from unalterable media - CDs Record resulting from the installation procedure Next VVSG Training Oct 15 -17, 2007 Page 49
 5. 4 Access Control n The management of three basic elements n n Supports the ability of the voting system to n n n Identification Authentication Authorization Account for users actions Limits use of resources Applies to individuals, applications, and processes of the voting system Next VVSG Training Oct 15 -17, 2007 Page 50
5. 4 Access Control n The management of three basic elements n n Supports the ability of the voting system to n n n Identification Authentication Authorization Account for users actions Limits use of resources Applies to individuals, applications, and processes of the voting system Next VVSG Training Oct 15 -17, 2007 Page 50
 5. 4 Access Control n Management of identification information n n Creating and disabling identities or roles Failed attempts lock out n n Number of failures within in a time period Length of lockout time Next VVSG Training Oct 15 -17, 2007 Page 51
5. 4 Access Control n Management of identification information n n Creating and disabling identities or roles Failed attempts lock out n n Number of failures within in a time period Length of lockout time Next VVSG Training Oct 15 -17, 2007 Page 51
 5. 4 Access Control n Role identification n Required for voting devices and election management systems Roles specified: Voter, Election Judge, Poll Worker, Central Election Official, and Administrator Individual identification n Required by election management systems Next VVSG Training Oct 15 -17, 2007 Page 52
5. 4 Access Control n Role identification n Required for voting devices and election management systems Roles specified: Voter, Election Judge, Poll Worker, Central Election Official, and Administrator Individual identification n Required by election management systems Next VVSG Training Oct 15 -17, 2007 Page 52
 5. 4 Access Control n Management of authentication information n Setting and changing authentication information Protection of authentication data by system Password management - strength, reuse, and expiration. Next VVSG Training Oct 15 -17, 2007 Page 53
5. 4 Access Control n Management of authentication information n Setting and changing authentication information Protection of authentication data by system Password management - strength, reuse, and expiration. Next VVSG Training Oct 15 -17, 2007 Page 53
 5. 4 Access Control n Authentication requirements by role n n n Voter in Section 7. 5. 1 Issuance of voting credentials and ballot activation Poll Worker - N/A Election Judge and Central n n Administrator n n Something you know Multi-factor authentication - smartcard, biometric Application or Process - Digital certificate or signature - ? ? Next VVSG Training Oct 15 -17, 2007 Page 54
5. 4 Access Control n Authentication requirements by role n n n Voter in Section 7. 5. 1 Issuance of voting credentials and ballot activation Poll Worker - N/A Election Judge and Central n n Administrator n n Something you know Multi-factor authentication - smartcard, biometric Application or Process - Digital certificate or signature - ? ? Next VVSG Training Oct 15 -17, 2007 Page 54
 5. 4 Access Control n Authorization Management n n n By voting system state, time interval, or specific time Dual person control Separation of duties Type of functionality and data accessed Explicitly allowed or disallowed Least privilege, Privilege escalation, prevent modification or tampering of software/firmware ? ? ? Next VVSG Training Oct 15 -17, 2007 Page 55
5. 4 Access Control n Authorization Management n n n By voting system state, time interval, or specific time Dual person control Separation of duties Type of functionality and data accessed Explicitly allowed or disallowed Least privilege, Privilege escalation, prevent modification or tampering of software/firmware ? ? ? Next VVSG Training Oct 15 -17, 2007 Page 55
 5. 4 Access Control n Technical Date Package (TDP) requirements n n n Descriptions and specifications of all access control mechanisms used Descriptions and specification of all voting system mechanisms that rely on access control Mapping of all voting system operations and default roles with permissions to perform operations Next VVSG Training Oct 15 -17, 2007 Page 56
5. 4 Access Control n Technical Date Package (TDP) requirements n n n Descriptions and specifications of all access control mechanisms used Descriptions and specification of all voting system mechanisms that rely on access control Mapping of all voting system operations and default roles with permissions to perform operations Next VVSG Training Oct 15 -17, 2007 Page 56
 5. 4 Access Control n User documentation requirements n n Instructions for implementing, configuring, and managing Model access control policy Templates or instructions for custom access control policy creation Disclosure of all default privileged roles Next VVSG Training Oct 15 -17, 2007 Page 57
5. 4 Access Control n User documentation requirements n n Instructions for implementing, configuring, and managing Model access control policy Templates or instructions for custom access control policy creation Disclosure of all default privileged roles Next VVSG Training Oct 15 -17, 2007 Page 57
 5. 5 System Integrity Management n Security controls that do not fit into other sections of the VVSG n n Boot, load, and execute process protection Removable media interface protection Backup and recovery capabilities Malicious software protection Next VVSG Training Oct 15 -17, 2007 Page 58
5. 5 System Integrity Management n Security controls that do not fit into other sections of the VVSG n n Boot, load, and execute process protection Removable media interface protection Backup and recovery capabilities Malicious software protection Next VVSG Training Oct 15 -17, 2007 Page 58
 5. 5 System Integrity Management n Boot process protection n n Process used when a system is powered on Integrity verification of software initialization components n Hardware cryptographic module - digital signature/hashes Next VVSG Training Oct 15 -17, 2007 Page 59
5. 5 System Integrity Management n Boot process protection n n Process used when a system is powered on Integrity verification of software initialization components n Hardware cryptographic module - digital signature/hashes Next VVSG Training Oct 15 -17, 2007 Page 59
 5. 5 System Integrity Management n Load and execute process protection n n Process used to load software into memory for execution Integrity verification of any software before loading into memory for execution n Hardware cryptographic module - digital signature/hashes Next VVSG Training Oct 15 -17, 2007 Page 60
5. 5 System Integrity Management n Load and execute process protection n n Process used to load software into memory for execution Integrity verification of any software before loading into memory for execution n Hardware cryptographic module - digital signature/hashes Next VVSG Training Oct 15 -17, 2007 Page 60
 5. 5 System Integrity Management n Removable media interface protection n n Other than physical security mechanisms Ability to disable removable media interfaces when not required CDs, Flash memory, PCIMIA, etc. May only need a CDs interface to be enabled during software installation Next VVSG Training Oct 15 -17, 2007 Page 61
5. 5 System Integrity Management n Removable media interface protection n n Other than physical security mechanisms Ability to disable removable media interfaces when not required CDs, Flash memory, PCIMIA, etc. May only need a CDs interface to be enabled during software installation Next VVSG Training Oct 15 -17, 2007 Page 61
 5. 5 System Integrity Management n Backup and recovery mechanisms n n Limited to election management systems Permitted only when not capturing votes Integrity verification information (digital signatures, hashes, MACs) created with backup information Backup information authentication and integrity verification before used for recovery Next VVSG Training Oct 15 -17, 2007 Page 62
5. 5 System Integrity Management n Backup and recovery mechanisms n n Limited to election management systems Permitted only when not capturing votes Integrity verification information (digital signatures, hashes, MACs) created with backup information Backup information authentication and integrity verification before used for recovery Next VVSG Training Oct 15 -17, 2007 Page 62
 5. 5 System Integrity Management n Malicious software protection n n Limited to election management systems Use of malware detection software n n n Ability to update as new threats appear over time Executed at least once every 24 hours and before loading and execution of software Executed against removable media Next VVSG Training Oct 15 -17, 2007 Page 63
5. 5 System Integrity Management n Malicious software protection n n Limited to election management systems Use of malware detection software n n n Ability to update as new threats appear over time Executed at least once every 24 hours and before loading and execution of software Executed against removable media Next VVSG Training Oct 15 -17, 2007 Page 63
 5. 5 System Integrity Management n Technical Date Package (TDP) requirements n List of all software required to be executed Next VVSG Training Oct 15 -17, 2007 Page 64
5. 5 System Integrity Management n Technical Date Package (TDP) requirements n List of all software required to be executed Next VVSG Training Oct 15 -17, 2007 Page 64
 5. 6 Communication Security n Protection of voting system communications n n n Transmission of information Communications based threats No use of wireless technology n Except for infrared technology Next VVSG Training Oct 15 -17, 2007 Page 65
5. 6 Communication Security n Protection of voting system communications n n n Transmission of information Communications based threats No use of wireless technology n Except for infrared technology Next VVSG Training Oct 15 -17, 2007 Page 65
 5. 6 Communication Security n No remote communication to voting devices during election day n n Exceptions for devices used to transmit end of day results and communication with voter registration databases However, these devices cannot be connected to other polling place devices Next VVSG Training Oct 15 -17, 2007 Page 66
5. 6 Communication Security n No remote communication to voting devices during election day n n Exceptions for devices used to transmit end of day results and communication with voter registration databases However, these devices cannot be connected to other polling place devices Next VVSG Training Oct 15 -17, 2007 Page 66
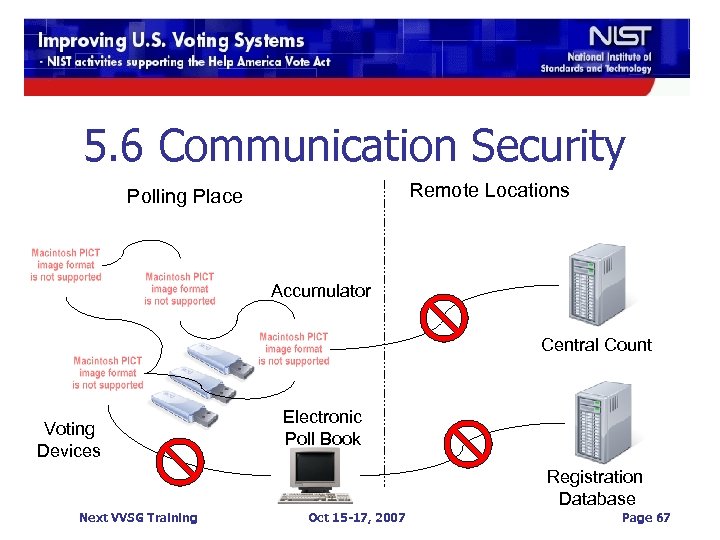 5. 6 Communication Security Remote Locations Polling Place Accumulator Central Count Voting Devices Electronic Poll Book Registration Database Next VVSG Training Oct 15 -17, 2007 Page 67
5. 6 Communication Security Remote Locations Polling Place Accumulator Central Count Voting Devices Electronic Poll Book Registration Database Next VVSG Training Oct 15 -17, 2007 Page 67
 5. 6 Communication Security n Network interface protection n Ability to disable physical network interfaces when not required Prohibit flow of network traffic from one interface to another on multiple interface devices Unique physical identifier (address) for each interface Next VVSG Training Oct 15 -17, 2007 Page 68
5. 6 Communication Security n Network interface protection n Ability to disable physical network interfaces when not required Prohibit flow of network traffic from one interface to another on multiple interface devices Unique physical identifier (address) for each interface Next VVSG Training Oct 15 -17, 2007 Page 68
 5. 6 Communication Security n n Limit communications to only devices that are required to communicate with each other Integrity information for data n n n Generate integrity information for data sent Verify integrity information for data received Digital signature, hashes, MACs Next VVSG Training Oct 15 -17, 2007 Page 69
5. 6 Communication Security n n Limit communications to only devices that are required to communicate with each other Integrity information for data n n n Generate integrity information for data sent Verify integrity information for data received Digital signature, hashes, MACs Next VVSG Training Oct 15 -17, 2007 Page 69
 5. 6 Communication Security n Mutual authentication between devices before exchange of information n n Part of connection establishment Unique identifier for devices Limit amount of information needed for authentication Limit devices to only required network ports, active shares, and services Next VVSG Training Oct 15 -17, 2007 Page 70
5. 6 Communication Security n Mutual authentication between devices before exchange of information n n Part of connection establishment Unique identifier for devices Limit amount of information needed for authentication Limit devices to only required network ports, active shares, and services Next VVSG Training Oct 15 -17, 2007 Page 70
 5. 6 Communication Security n Monitor network interfaces for evidence of attack n When attacks are detected, devices need to respond to stop attack n Shutting down network interface Next VVSG Training Oct 15 -17, 2007 Page 71
5. 6 Communication Security n Monitor network interfaces for evidence of attack n When attacks are detected, devices need to respond to stop attack n Shutting down network interface Next VVSG Training Oct 15 -17, 2007 Page 71
 5. 6 Communication Security n Documentation requirements n n List of all network communication processes and applications required for properation List of all network ports, shares, services, and protocols used Next VVSG Training Oct 15 -17, 2007 Page 72
5. 6 Communication Security n Documentation requirements n n List of all network communication processes and applications required for properation List of all network ports, shares, services, and protocols used Next VVSG Training Oct 15 -17, 2007 Page 72
 5. 7 System Event Logging n n Provides accountability and supports the ability to reconstruct events and detect intrusions Electronic audit trail n n n Information to be generated Integrity protection of the information Management of system event log Next VVSG Training Oct 15 -17, 2007 Page 73
5. 7 System Event Logging n n Provides accountability and supports the ability to reconstruct events and detect intrusions Electronic audit trail n n n Information to be generated Integrity protection of the information Management of system event log Next VVSG Training Oct 15 -17, 2007 Page 73
 5. 7 System Event Logging n n Log information must maintain voter privacy and ballot secrecy Basic log entry information n n System Identifier Event Identifier Time Stamp Result of event When applicable, user that triggered event and requested resource Next VVSG Training Oct 15 -17, 2007 Page 74
5. 7 System Event Logging n n Log information must maintain voter privacy and ballot secrecy Basic log entry information n n System Identifier Event Identifier Time Stamp Result of event When applicable, user that triggered event and requested resource Next VVSG Training Oct 15 -17, 2007 Page 74
 5. 7 System Event Logging n Time Stamp requirements n n Clock drift - 1 minute within 15 hours Format of time stamp - give example n n ISO 8601 Date Time - hours, minutes, and seconds Administrator role required to adjust clock Next VVSG Training Oct 15 -17, 2007 Page 75
5. 7 System Event Logging n Time Stamp requirements n n Clock drift - 1 minute within 15 hours Format of time stamp - give example n n ISO 8601 Date Time - hours, minutes, and seconds Administrator role required to adjust clock Next VVSG Training Oct 15 -17, 2007 Page 75
 5. 7 System Event Logging n Minimum list of events to be logged n General system functions events n n n Changes to configuration Device startup and shutdown Addition and deletion files System readiness results Authentication and access control events n n n Logon attempts Logout events Attempts to access system resources Next VVSG Training Oct 15 -17, 2007 Page 76
5. 7 System Event Logging n Minimum list of events to be logged n General system functions events n n n Changes to configuration Device startup and shutdown Addition and deletion files System readiness results Authentication and access control events n n n Logon attempts Logout events Attempts to access system resources Next VVSG Training Oct 15 -17, 2007 Page 76
 5. 7 System Event Logging n Software events n n Cryptographic events n n Installation, upgrades, and patches Changes to configuration settings Connection attempts to databases Changes to cryptographic keys Voting events n n n Opening and closing of polls Cast ballot Ballot definition and modification Next VVSG Training Oct 15 -17, 2007 Page 77
5. 7 System Event Logging n Software events n n Cryptographic events n n Installation, upgrades, and patches Changes to configuration settings Connection attempts to databases Changes to cryptographic keys Voting events n n n Opening and closing of polls Cast ballot Ballot definition and modification Next VVSG Training Oct 15 -17, 2007 Page 77
 5. 7 System Event Logging n Management of system event log n n Default setting of system event log Storage of log information in a publicly documented format such as XML Event logs separable on an election and device basis Retention of event log data from previous elections Next VVSG Training Oct 15 -17, 2007 Page 78
5. 7 System Event Logging n Management of system event log n n Default setting of system event log Storage of log information in a publicly documented format such as XML Event logs separable on an election and device basis Retention of event log data from previous elections Next VVSG Training Oct 15 -17, 2007 Page 78
 5. 7 System Event Logging n n Export of log information with digital signature Rotation of log information internally n n From primary file to new file Log capacity management n n Alert as it reaches configurable intervals Suspension of vote capturing when logs capacity reached Next VVSG Training Oct 15 -17, 2007 Page 79
5. 7 System Event Logging n n Export of log information with digital signature Rotation of log information internally n n From primary file to new file Log capacity management n n Alert as it reaches configurable intervals Suspension of vote capturing when logs capacity reached Next VVSG Training Oct 15 -17, 2007 Page 79
 5. 7 System Event Logging n n n Ability to view, analyze, and search system event log while on device Halt vote capturing when system log malfunctions or is disabled Administrator role required to configure system event log and clear previous election event logs prior to new election cycle Next VVSG Training Oct 15 -17, 2007 Page 80
5. 7 System Event Logging n n n Ability to view, analyze, and search system event log while on device Halt vote capturing when system log malfunctions or is disabled Administrator role required to configure system event log and clear previous election event logs prior to new election cycle Next VVSG Training Oct 15 -17, 2007 Page 80
 5. 7 System Event Logging n Protection of log information n Unauthorized access n n n Unauthorized modification n Read only for administrator roles Write or append only for processes Use of cryptography, append only media, operating system Unauthorized Deletion Integrity and [[availability]] protection of archived log information Next VVSG Training Oct 15 -17, 2007 Page 81
5. 7 System Event Logging n Protection of log information n Unauthorized access n n n Unauthorized modification n Read only for administrator roles Write or append only for processes Use of cryptography, append only media, operating system Unauthorized Deletion Integrity and [[availability]] protection of archived log information Next VVSG Training Oct 15 -17, 2007 Page 81
 5. 8 Physical Security for Voting Devices n Prevent undetected, unauthorized physical access n n n Must be able to differentiate authorized from unauthorized access Unauthorized access must leave physical evidence Requirements recognize use of a combination of procedures and physical countermeasures without prescribing either Next VVSG Training Oct 15 -17, 2007 Page 82
5. 8 Physical Security for Voting Devices n Prevent undetected, unauthorized physical access n n n Must be able to differentiate authorized from unauthorized access Unauthorized access must leave physical evidence Requirements recognize use of a combination of procedures and physical countermeasures without prescribing either Next VVSG Training Oct 15 -17, 2007 Page 82
 5. 8 Physical Security for Voting Devices n n Unauthorized physical access must leave physical evidence Physical port access and least functionality n n Essential to operations, testing and auditing Boundary protection n Broken connection → port automatically disabled, alarm, event log, authorization to re-enable Next VVSG Training Oct 15 -17, 2007 Page 83
5. 8 Physical Security for Voting Devices n n Unauthorized physical access must leave physical evidence Physical port access and least functionality n n Essential to operations, testing and auditing Boundary protection n Broken connection → port automatically disabled, alarm, event log, authorization to re-enable Next VVSG Training Oct 15 -17, 2007 Page 83
 5. 8 Physical Security for Voting Devices n Information flow n n Door covers and panels n n Restricted access to ports with removable media Tamper evidence Manually disable Monitor access Ballot boxes n Tamper evident Next VVSG Training Oct 15 -17, 2007 Page 84
5. 8 Physical Security for Voting Devices n Information flow n n Door covers and panels n n Restricted access to ports with removable media Tamper evidence Manually disable Monitor access Ballot boxes n Tamper evident Next VVSG Training Oct 15 -17, 2007 Page 84
 5. 8 Physical Security for Voting Devices n Secure physical locks and keys n n n Physical encasement locks (fasteners) n n Meet UL standards and be tamper evident Keyed per System Owner’s preference Must not compromise security Power supplies n If the power goes out, physical countermeasures should not fail Next VVSG Training Oct 15 -17, 2007 Page 85
5. 8 Physical Security for Voting Devices n Secure physical locks and keys n n n Physical encasement locks (fasteners) n n Meet UL standards and be tamper evident Keyed per System Owner’s preference Must not compromise security Power supplies n If the power goes out, physical countermeasures should not fail Next VVSG Training Oct 15 -17, 2007 Page 85
 Questions End of Day One? ? ? Next VVSG Training Oct 15 -17, 2007 Page 86
Questions End of Day One? ? ? Next VVSG Training Oct 15 -17, 2007 Page 86


