dd2775ca94c35354868b0384c3b47d43.ppt
- Количество слайдов: 64
 Part 3. 1 Internet Applications Ch. 31, 32, 34 (DNS, E-mail, TELNET, FTP) FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 1
Part 3. 1 Internet Applications Ch. 31, 32, 34 (DNS, E-mail, TELNET, FTP) FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 1
 Functionality l Transport layer and layers below l l l Basic communication Reliability Application layer l Abstractions l l FALL 2005 Files Services Databases Names CSI 4118 – UNIVERSITY OF OTTAWA 2
Functionality l Transport layer and layers below l l l Basic communication Reliability Application layer l Abstractions l l FALL 2005 Files Services Databases Names CSI 4118 – UNIVERSITY OF OTTAWA 2
 Dichotomy of Duties l Network l l l Transfers bits Operates at application’s request Applications determine l l FALL 2005 What to send When to send Where to send Meaning of bits CSI 4118 – UNIVERSITY OF OTTAWA 3
Dichotomy of Duties l Network l l l Transfers bits Operates at application’s request Applications determine l l FALL 2005 What to send When to send Where to send Meaning of bits CSI 4118 – UNIVERSITY OF OTTAWA 3
 Important Point Although an internet system provides a basic communication service, the protocol software cannot initiate contact with, or accept contact from, a remote computer. Instead, two application programs must participate in any communication: one application initiates communication and the other accepts it. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 4
Important Point Although an internet system provides a basic communication service, the protocol software cannot initiate contact with, or accept contact from, a remote computer. Instead, two application programs must participate in any communication: one application initiates communication and the other accepts it. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 4
 How Two Application Programs Make Contact l One application l l l Another application l l l Begins execution first Waits passively at prearranged location Begins execution later Actively contacts first program Called client-server interaction FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 5
How Two Application Programs Make Contact l One application l l l Another application l l l Begins execution first Waits passively at prearranged location Begins execution later Actively contacts first program Called client-server interaction FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 5
 Client-Server Paradigm l l l Used by all network applications Passive program called a server Active program called a client FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 6
Client-Server Paradigm l l l Used by all network applications Passive program called a server Active program called a client FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 6
 Characteristics of a Client l l l l Arbitrary application program Becomes client temporarily Can also perform other computations Invoked directly by user Runs locally on user’s computer Actively initiates contact with a server Contacts one server at a time FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 7
Characteristics of a Client l l l l Arbitrary application program Becomes client temporarily Can also perform other computations Invoked directly by user Runs locally on user’s computer Actively initiates contact with a server Contacts one server at a time FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 7
 Characteristics of a Server l l l l Special-purpose, privileged program Dedicated to providing one service Can handle multiple remote clients simultaneously Invoked automatically when system boots Executes forever Needs powerful computer and operating system Waits passively for client contact Accepts requests from arbitrary clients FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 8
Characteristics of a Server l l l l Special-purpose, privileged program Dedicated to providing one service Can handle multiple remote clients simultaneously Invoked automatically when system boots Executes forever Needs powerful computer and operating system Waits passively for client contact Accepts requests from arbitrary clients FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 8
 Application Program Interface l l l Part of operating system Permits application to use protocols Defines l l FALL 2005 Operations allowed Arguments for each operation CSI 4118 – UNIVERSITY OF OTTAWA 9
Application Program Interface l l l Part of operating system Permits application to use protocols Defines l l FALL 2005 Operations allowed Arguments for each operation CSI 4118 – UNIVERSITY OF OTTAWA 9
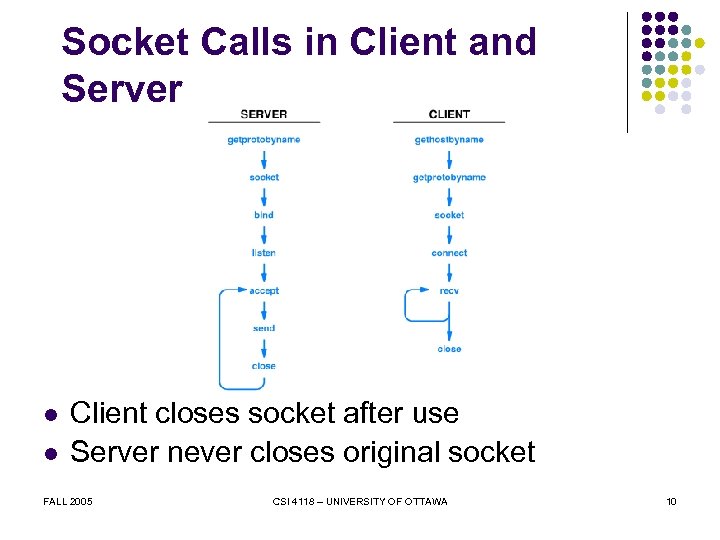 Socket Calls in Client and Server l l Client closes socket after use Server never closes original socket FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 10
Socket Calls in Client and Server l l Client closes socket after use Server never closes original socket FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 10
 Internet Applications l l l Domain Name System Electronic mail Remote login File transfer World Wide Web All use client-server model FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 11
Internet Applications l l l Domain Name System Electronic mail Remote login File transfer World Wide Web All use client-server model FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 11
 Names l l Internet communication requires IP addresses Humans prefer to use computer names Automated system available to translate names to addresses Known as Domain Name System (DNS) FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 12
Names l l Internet communication requires IP addresses Humans prefer to use computer names Automated system available to translate names to addresses Known as Domain Name System (DNS) FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 12
 DNS Functionality l Given l l Returns l l Name of a computer Computer’s internet address Method l l FALL 2005 Distributed lookup Client contacts server(s) as necessary CSI 4118 – UNIVERSITY OF OTTAWA 13
DNS Functionality l Given l l Returns l l Name of a computer Computer’s internet address Method l l FALL 2005 Distributed lookup Client contacts server(s) as necessary CSI 4118 – UNIVERSITY OF OTTAWA 13
 Domain Name Syntax l l Alphanumeric segments separated by dots Examples www. netbook. cs. purdue. edu www. eg. bucknell. edu l Most significant part on right FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 14
Domain Name Syntax l l Alphanumeric segments separated by dots Examples www. netbook. cs. purdue. edu www. eg. bucknell. edu l Most significant part on right FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 14
 Obtaining a Domain Name l Organization l l l Chooses a desired name Must be unique Registers with central authority Placed under one top-level domain Names subject to international law for l l FALL 2005 Trademarks Copyright CSI 4118 – UNIVERSITY OF OTTAWA 15
Obtaining a Domain Name l Organization l l l Chooses a desired name Must be unique Registers with central authority Placed under one top-level domain Names subject to international law for l l FALL 2005 Trademarks Copyright CSI 4118 – UNIVERSITY OF OTTAWA 15
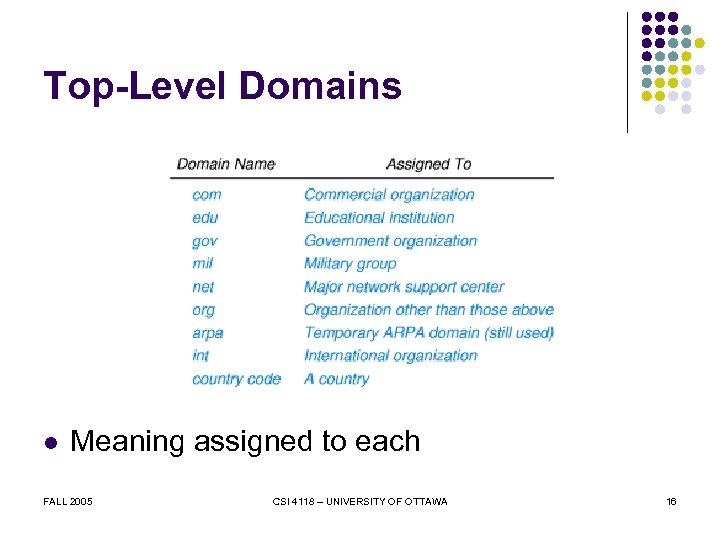 Top-Level Domains l Meaning assigned to each FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 16
Top-Level Domains l Meaning assigned to each FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 16
 Within Organization l l Subdivision possible Arbitrary levels possible Not standardized Controlled locally by organization FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 17
Within Organization l l Subdivision possible Arbitrary levels possible Not standardized Controlled locally by organization FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 17
 Example Name Structure l First level is. com l Second level is company name Third level is division within company Fourth level either l l FALL 2005 Company subdivision Individual computer CSI 4118 – UNIVERSITY OF OTTAWA 18
Example Name Structure l First level is. com l Second level is company name Third level is division within company Fourth level either l l FALL 2005 Company subdivision Individual computer CSI 4118 – UNIVERSITY OF OTTAWA 18
 An Example l Assume l l Company is Foobar Has two divisions Soap division l Candy division l l l FALL 2005 Candy division has subdivisions Soap Division has no subdivisions CSI 4118 – UNIVERSITY OF OTTAWA 19
An Example l Assume l l Company is Foobar Has two divisions Soap division l Candy division l l l FALL 2005 Candy division has subdivisions Soap Division has no subdivisions CSI 4118 – UNIVERSITY OF OTTAWA 19
 An Example (continued) l Names in soap division have form l computer. soap. foobar. com candy division have form Names in computer. subdivision. candy. foobar. com FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 20
An Example (continued) l Names in soap division have form l computer. soap. foobar. com candy division have form Names in computer. subdivision. candy. foobar. com FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 20
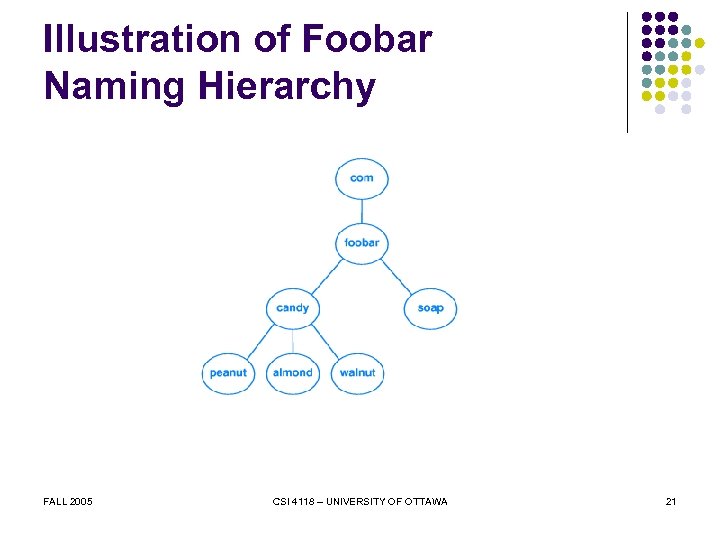 Illustration of Foobar Naming Hierarchy FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 21
Illustration of Foobar Naming Hierarchy FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 21
 The Point About Names The number of segments in a domain name corresponds to the naming hierarchy. There is no universal standard; each organization can choose how to structure names in its hierarchy. Furthermore, names within an organization do not need to follow a uniform pattern; individual groups within the organization can choose a hierarchical structure that is appropriate for the group. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 22
The Point About Names The number of segments in a domain name corresponds to the naming hierarchy. There is no universal standard; each organization can choose how to structure names in its hierarchy. Furthermore, names within an organization do not need to follow a uniform pattern; individual groups within the organization can choose a hierarchical structure that is appropriate for the group. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 22
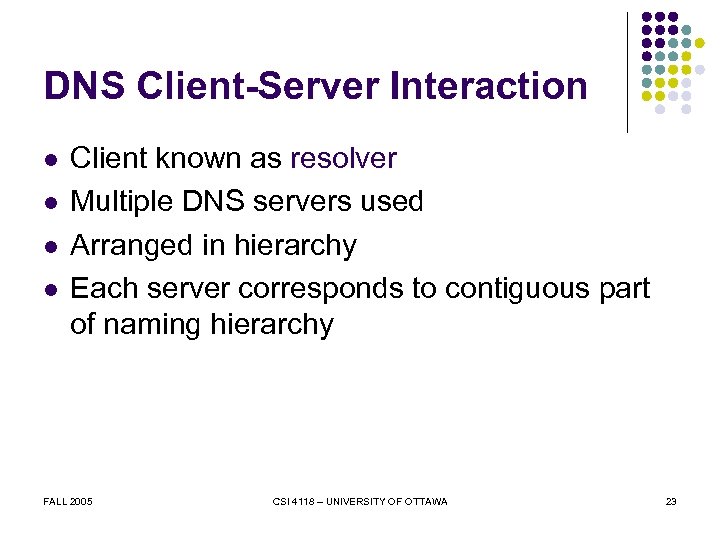 DNS Client-Server Interaction l l Client known as resolver Multiple DNS servers used Arranged in hierarchy Each server corresponds to contiguous part of naming hierarchy FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 23
DNS Client-Server Interaction l l Client known as resolver Multiple DNS servers used Arranged in hierarchy Each server corresponds to contiguous part of naming hierarchy FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 23
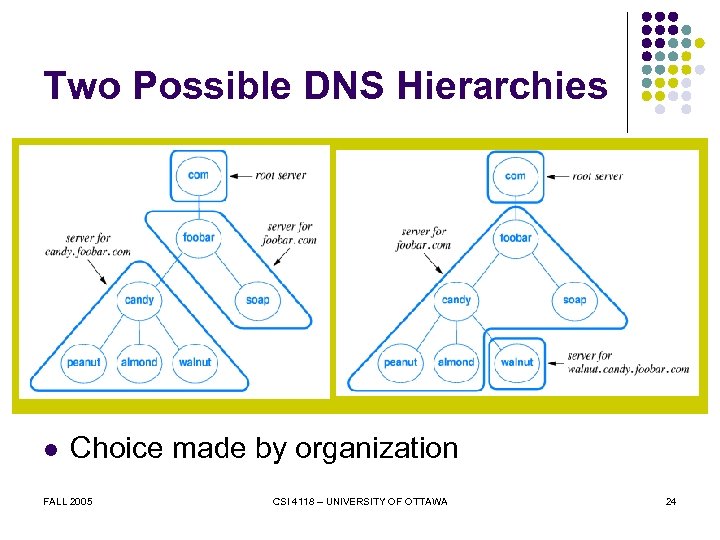 Two Possible DNS Hierarchies l Choice made by organization FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 24
Two Possible DNS Hierarchies l Choice made by organization FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 24
 Inter-Server Links All domain name servers are linked together to form a unified system. Each server knows how to reach a root server and how to reach servers that are authorities for names further down the hierarchy. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 25
Inter-Server Links All domain name servers are linked together to form a unified system. Each server knows how to reach a root server and how to reach servers that are authorities for names further down the hierarchy. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 25
 In Practice l l DNS uses backup server(s) ISPs and others l l Offer DNS service to subscribers Small organizations and individuals l l FALL 2005 Only need domain names for computers running servers Contract with an ISP for domain service CSI 4118 – UNIVERSITY OF OTTAWA 26
In Practice l l DNS uses backup server(s) ISPs and others l l Offer DNS service to subscribers Small organizations and individuals l l FALL 2005 Only need domain names for computers running servers Contract with an ISP for domain service CSI 4118 – UNIVERSITY OF OTTAWA 26
 DNS Lookup l Application l l l Becomes DNS client Sends request to local DNS server Local server l l l FALL 2005 If answer known, returns response If answer unknown l Starts at top-level server l Follows links l Returns response Called name resolution CSI 4118 – UNIVERSITY OF OTTAWA 27
DNS Lookup l Application l l l Becomes DNS client Sends request to local DNS server Local server l l l FALL 2005 If answer known, returns response If answer unknown l Starts at top-level server l Follows links l Returns response Called name resolution CSI 4118 – UNIVERSITY OF OTTAWA 27
 Caching in DNS l l l Server always caches answers Host can cache answers Caching l l l FALL 2005 Improves efficiency Eliminates unnecessary search Works well because high locality of reference CSI 4118 – UNIVERSITY OF OTTAWA 28
Caching in DNS l l l Server always caches answers Host can cache answers Caching l l l FALL 2005 Improves efficiency Eliminates unnecessary search Works well because high locality of reference CSI 4118 – UNIVERSITY OF OTTAWA 28
 DNS Types l Each entry in server consists of l l During lookup, client must supply l l l Domain name DNS type for name Value to which name corresponds Name Type Server l FALL 2005 Matches both name and type CSI 4118 – UNIVERSITY OF OTTAWA 29
DNS Types l Each entry in server consists of l l During lookup, client must supply l l l Domain name DNS type for name Value to which name corresponds Name Type Server l FALL 2005 Matches both name and type CSI 4118 – UNIVERSITY OF OTTAWA 29
 The Point About Types The domain name system stores a type with each entry. When a resolver looks up a name, the resolver must specify the type that is desired; a DNS server returns only entries that match the specified type. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 30
The Point About Types The domain name system stores a type with each entry. When a resolver looks up a name, the resolver must specify the type that is desired; a DNS server returns only entries that match the specified type. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 30
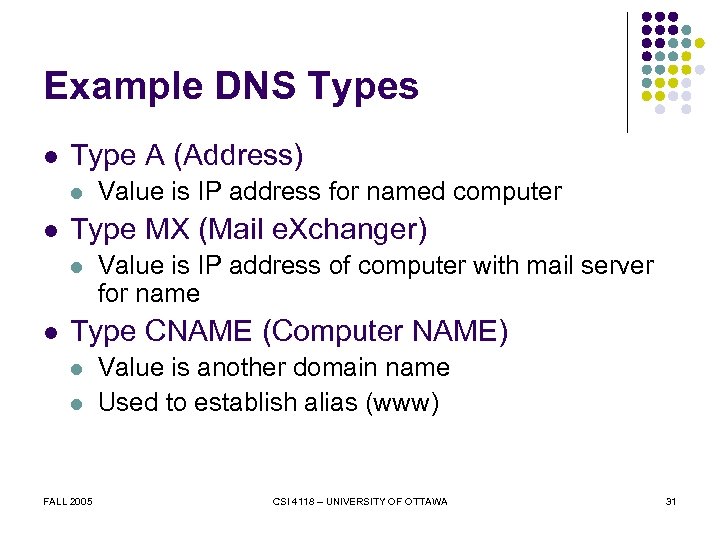 Example DNS Types l Type A (Address) l l Type MX (Mail e. Xchanger) l l Value is IP address for named computer Value is IP address of computer with mail server for name Type CNAME (Computer NAME) l l FALL 2005 Value is another domain name Used to establish alias (www) CSI 4118 – UNIVERSITY OF OTTAWA 31
Example DNS Types l Type A (Address) l l Type MX (Mail e. Xchanger) l l Value is IP address for named computer Value is IP address of computer with mail server for name Type CNAME (Computer NAME) l l FALL 2005 Value is another domain name Used to establish alias (www) CSI 4118 – UNIVERSITY OF OTTAWA 31
 Domain Name Abbreviation l l l DNS lookup uses full names Users desire abbreviations Technique l l FALL 2005 Configure resolver with list of suffixes Try suffixes one at a time CSI 4118 – UNIVERSITY OF OTTAWA 32
Domain Name Abbreviation l l l DNS lookup uses full names Users desire abbreviations Technique l l FALL 2005 Configure resolver with list of suffixes Try suffixes one at a time CSI 4118 – UNIVERSITY OF OTTAWA 32
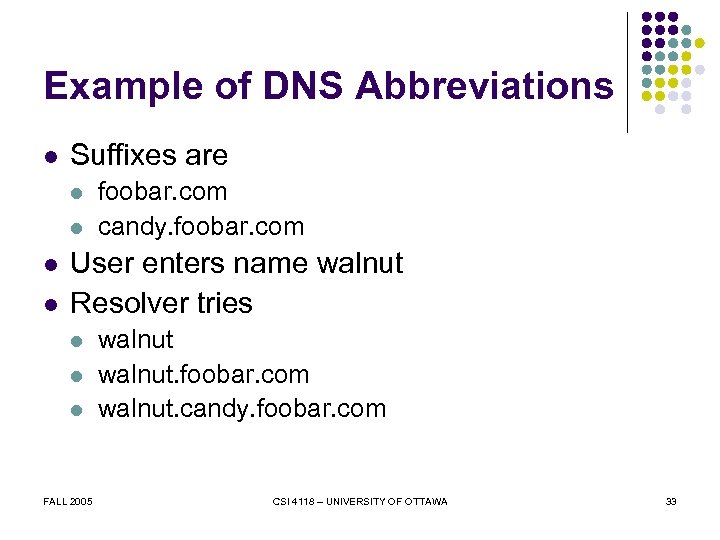 Example of DNS Abbreviations l Suffixes are l l foobar. com candy. foobar. com User enters name walnut Resolver tries l l l FALL 2005 walnut. foobar. com walnut. candy. foobar. com CSI 4118 – UNIVERSITY OF OTTAWA 33
Example of DNS Abbreviations l Suffixes are l l foobar. com candy. foobar. com User enters name walnut Resolver tries l l l FALL 2005 walnut. foobar. com walnut. candy. foobar. com CSI 4118 – UNIVERSITY OF OTTAWA 33
 Other Internet Applications l Invoked directly by user l l FALL 2005 E-mail Remote login File transfer Web browsing CSI 4118 – UNIVERSITY OF OTTAWA 34
Other Internet Applications l Invoked directly by user l l FALL 2005 E-mail Remote login File transfer Web browsing CSI 4118 – UNIVERSITY OF OTTAWA 34
 Electronic Mail l Originally l l Now l l Memo sent from one user to another Memo sent to one or more mailboxes Mailbox l l l FALL 2005 Destination point for messages Can be storage or program Given unique address CSI 4118 – UNIVERSITY OF OTTAWA 35
Electronic Mail l Originally l l Now l l Memo sent from one user to another Memo sent to one or more mailboxes Mailbox l l l FALL 2005 Destination point for messages Can be storage or program Given unique address CSI 4118 – UNIVERSITY OF OTTAWA 35
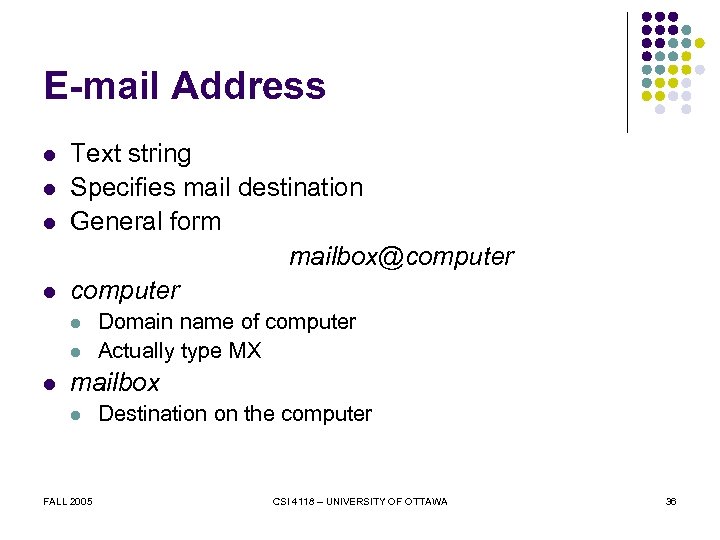 E-mail Address l l Text string Specifies mail destination General form mailbox@computer l l l Domain name of computer Actually type MX mailbox l FALL 2005 Destination on the computer CSI 4118 – UNIVERSITY OF OTTAWA 36
E-mail Address l l Text string Specifies mail destination General form mailbox@computer l l l Domain name of computer Actually type MX mailbox l FALL 2005 Destination on the computer CSI 4118 – UNIVERSITY OF OTTAWA 36
 Use of E-mail Address Each electronic mailbox has a unique address, which is divided into two parts: the first identifies a user’s mailbox, and the second identifies a computer on which the mailbox resides. E-mail software on the sender’s computer uses the second part to select a destination; e-mail software on the recipient’s computer uses the first part to select a particular mailbox. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 37
Use of E-mail Address Each electronic mailbox has a unique address, which is divided into two parts: the first identifies a user’s mailbox, and the second identifies a computer on which the mailbox resides. E-mail software on the sender’s computer uses the second part to select a destination; e-mail software on the recipient’s computer uses the first part to select a particular mailbox. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 37
 Mail Message Format l Header l l Identifies sender, recipient(s), memo contents Lines of form keyword: information Blank line Body l FALL 2005 Contains text of message CSI 4118 – UNIVERSITY OF OTTAWA 38
Mail Message Format l Header l l Identifies sender, recipient(s), memo contents Lines of form keyword: information Blank line Body l FALL 2005 Contains text of message CSI 4118 – UNIVERSITY OF OTTAWA 38
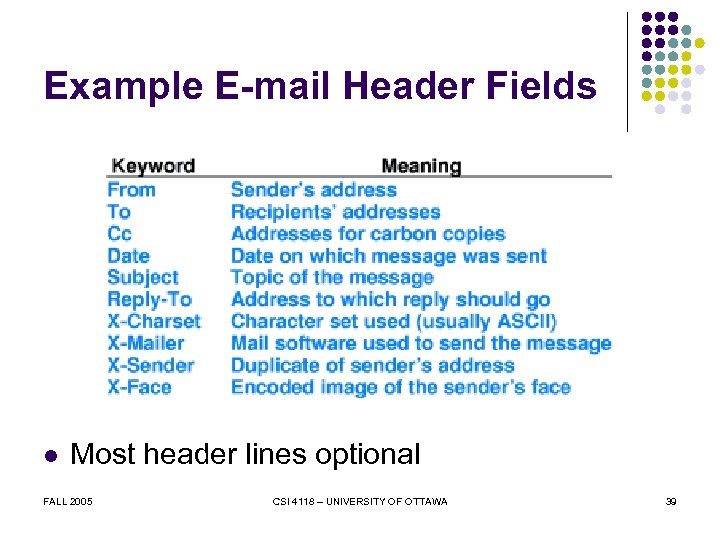 Example E-mail Header Fields l Most header lines optional FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 39
Example E-mail Header Fields l Most header lines optional FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 39
 Extending E-mail l Original e-mail l l Users desire to send l l SMTP - message restricted to ASCII text Image files Audio clips Compiled (binary) programs Solution l FALL 2005 Multi-purpose Internet Mail Extensions (MIME) CSI 4118 – UNIVERSITY OF OTTAWA 40
Extending E-mail l Original e-mail l l Users desire to send l l SMTP - message restricted to ASCII text Image files Audio clips Compiled (binary) programs Solution l FALL 2005 Multi-purpose Internet Mail Extensions (MIME) CSI 4118 – UNIVERSITY OF OTTAWA 40
 MIME l Allows transmission of l l l Binary data Multimedia files (video/audio clips) Multiple types in single message Mixed formats Backward compatible FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 41
MIME l Allows transmission of l l l Binary data Multimedia files (video/audio clips) Multiple types in single message Mixed formats Backward compatible FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 41
 MIME Encoding l Sender l l Sent like standard message Receiver l l l Inserts additional header lines Encodes binary data in (printable) ASCII Interprets header lines Extracts and decodes parts Separate standards for content and encoding FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 42
MIME Encoding l Sender l l Sent like standard message Receiver l l l Inserts additional header lines Encodes binary data in (printable) ASCII Interprets header lines Extracts and decodes parts Separate standards for content and encoding FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 42
 Example of MIME l Header lines added MIME-Version: 1. 0 Content-Type: Multipart/Mixed; Boundary=Mime_sep l Specifies l l FALL 2005 Using MIME version 1. 0 Line Mime_sep appears before each message part CSI 4118 – UNIVERSITY OF OTTAWA 43
Example of MIME l Header lines added MIME-Version: 1. 0 Content-Type: Multipart/Mixed; Boundary=Mime_sep l Specifies l l FALL 2005 Using MIME version 1. 0 Line Mime_sep appears before each message part CSI 4118 – UNIVERSITY OF OTTAWA 43
 MIME Although Internet e-mail only transfers text, MIME can be used to transport binary data by encoding it in printed characters. A MIME mail message includes additional information that a receiving application uses to decode the message. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 44
MIME Although Internet e-mail only transfers text, MIME can be used to transport binary data by encoding it in printed characters. A MIME mail message includes additional information that a receiving application uses to decode the message. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 44
 Mail Transfer l l l Protocol is Simple Mail Transfer Protocol (SMTP) Runs over TCP Used between l l l Mail transfer program on sender’s computer Mail server on recipient’s computer Specifies how l l l FALL 2005 Client interacts with server Recipients specified Message is transferred CSI 4118 – UNIVERSITY OF OTTAWA 45
Mail Transfer l l l Protocol is Simple Mail Transfer Protocol (SMTP) Runs over TCP Used between l l l Mail transfer program on sender’s computer Mail server on recipient’s computer Specifies how l l l FALL 2005 Client interacts with server Recipients specified Message is transferred CSI 4118 – UNIVERSITY OF OTTAWA 45
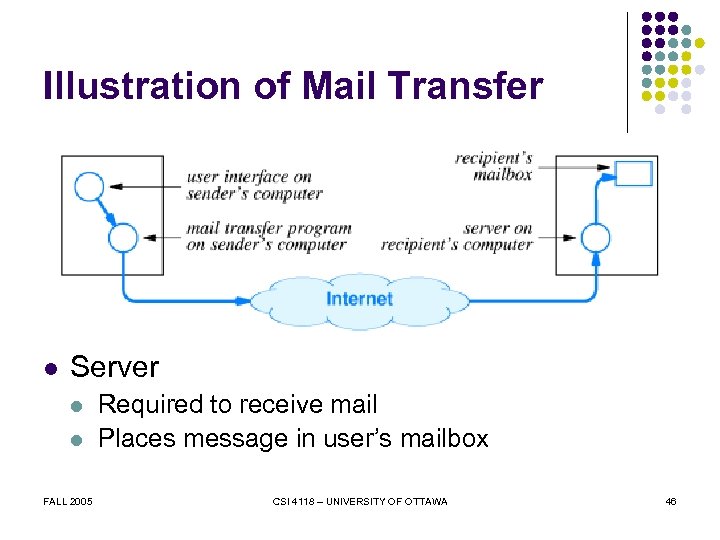 Illustration of Mail Transfer l Server l l FALL 2005 Required to receive mail Places message in user’s mailbox CSI 4118 – UNIVERSITY OF OTTAWA 46
Illustration of Mail Transfer l Server l l FALL 2005 Required to receive mail Places message in user’s mailbox CSI 4118 – UNIVERSITY OF OTTAWA 46
 Terminology l Mail exploder l l Mailing list l l l Program Accepts incoming message Delivers to multiple recipients Database Used by exploder Mail gateway l FALL 2005 Connects two mail systems CSI 4118 – UNIVERSITY OF OTTAWA 47
Terminology l Mail exploder l l Mailing list l l l Program Accepts incoming message Delivers to multiple recipients Database Used by exploder Mail gateway l FALL 2005 Connects two mail systems CSI 4118 – UNIVERSITY OF OTTAWA 47
 Illustration of a Mailing List l Separate permissions for l l Mailing to list Adding/deleting members l Public – anyone can join l FALL 2005 Private – access restricted by owner CSI 4118 – UNIVERSITY OF OTTAWA 48
Illustration of a Mailing List l Separate permissions for l l Mailing to list Adding/deleting members l Public – anyone can join l FALL 2005 Private – access restricted by owner CSI 4118 – UNIVERSITY OF OTTAWA 48
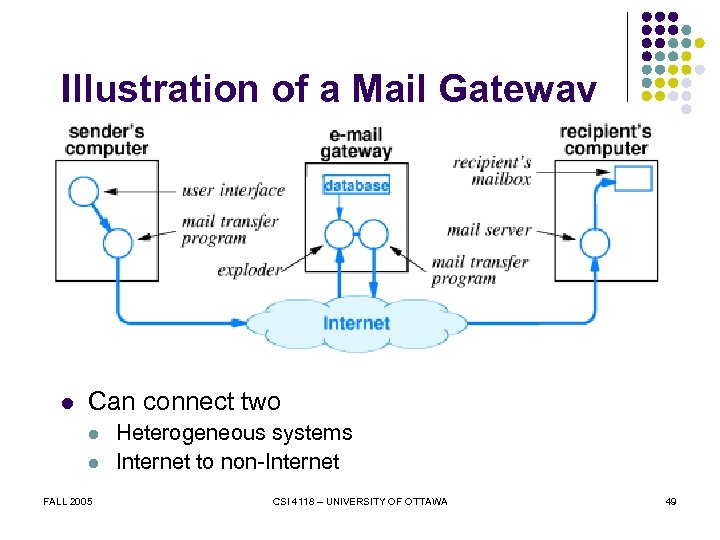 Illustration of a Mail Gateway l Can connect two l l FALL 2005 Heterogeneous systems Internet to non-Internet CSI 4118 – UNIVERSITY OF OTTAWA 49
Illustration of a Mail Gateway l Can connect two l l FALL 2005 Heterogeneous systems Internet to non-Internet CSI 4118 – UNIVERSITY OF OTTAWA 49
 Automated Mailing Lists l l l Automated program to handle routine chores of maintaining mailing list: list manager Used in conjunction with exploder Example expected command: add mailbox to list FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 50
Automated Mailing Lists l l l Automated program to handle routine chores of maintaining mailing list: list manager Used in conjunction with exploder Example expected command: add mailbox to list FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 50
 Computers Without Mail Servers l Typically l l l To receive e-mail, user must l l l Small, personal computer Not continuously connected to Internet Establish mailbox on large computer Access mailbox as necessary Post Office Protocol (POP) used FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 51
Computers Without Mail Servers l Typically l l l To receive e-mail, user must l l l Small, personal computer Not continuously connected to Internet Establish mailbox on large computer Access mailbox as necessary Post Office Protocol (POP) used FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 51
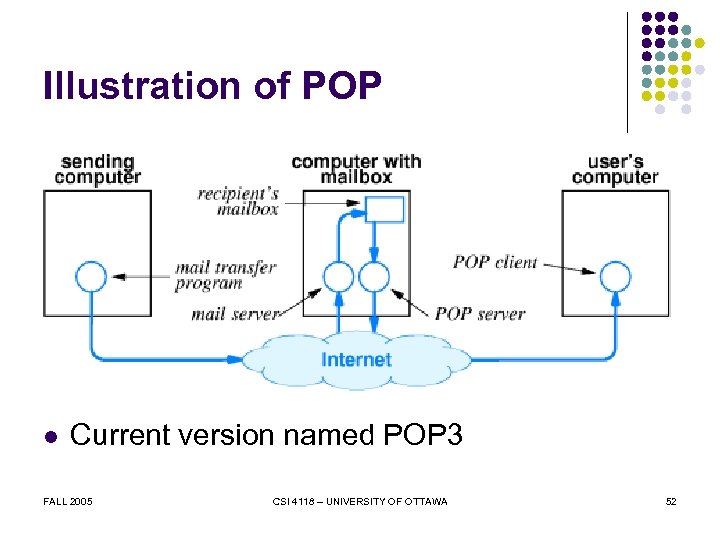 Illustration of POP l Current version named POP 3 FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 52
Illustration of POP l Current version named POP 3 FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 52
 Remote Login l l Provide interactive access to computer from remote site Standard protocol is TELNET FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 53
Remote Login l l Provide interactive access to computer from remote site Standard protocol is TELNET FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 53
 TELNET l l Text-oriented interface User l l l Invokes client Specifies remote computer Client l l l FALL 2005 Forms TCP connection to server Passes keystrokes over connection Displays output on screen CSI 4118 – UNIVERSITY OF OTTAWA 54
TELNET l l Text-oriented interface User l l l Invokes client Specifies remote computer Client l l l FALL 2005 Forms TCP connection to server Passes keystrokes over connection Displays output on screen CSI 4118 – UNIVERSITY OF OTTAWA 54
 File Transfer l l Complete file copy Major protocol is File Transfer Protocol (FTP) l l FALL 2005 Uses TCP Supports binary or text transfers Large set of commands Until 1995 was major source of packets in Internet CSI 4118 – UNIVERSITY OF OTTAWA 55
File Transfer l l Complete file copy Major protocol is File Transfer Protocol (FTP) l l FALL 2005 Uses TCP Supports binary or text transfers Large set of commands Until 1995 was major source of packets in Internet CSI 4118 – UNIVERSITY OF OTTAWA 55
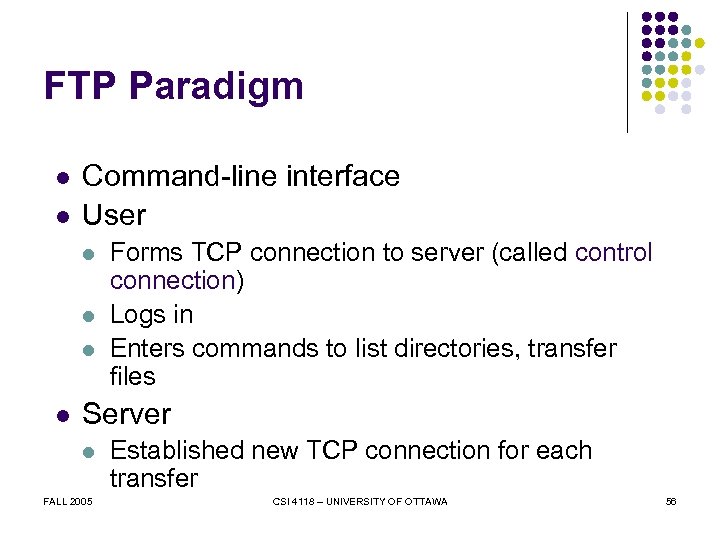 FTP Paradigm l l Command-line interface User l l Forms TCP connection to server (called control connection) Logs in Enters commands to list directories, transfer files Server l FALL 2005 Established new TCP connection for each transfer CSI 4118 – UNIVERSITY OF OTTAWA 56
FTP Paradigm l l Command-line interface User l l Forms TCP connection to server (called control connection) Logs in Enters commands to list directories, transfer files Server l FALL 2005 Established new TCP connection for each transfer CSI 4118 – UNIVERSITY OF OTTAWA 56
 Transfer Modes FTP has two basic transfer modes: one used for text files and the other for all nontext files. Although binary mode produces an exact copy of the bits, the resulting copy may be meaningless because does not convert values to the local representations. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 57
Transfer Modes FTP has two basic transfer modes: one used for text files and the other for all nontext files. Although binary mode produces an exact copy of the bits, the resulting copy may be meaningless because does not convert values to the local representations. FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 57
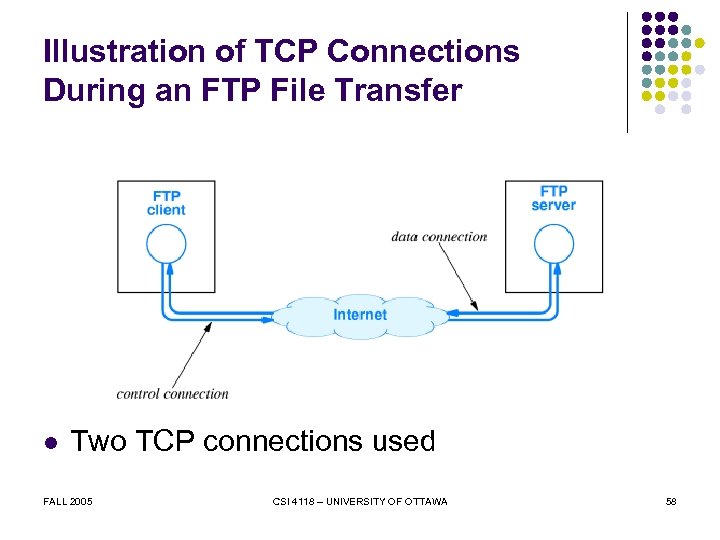 Illustration of TCP Connections During an FTP File Transfer l Two TCP connections used FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 58
Illustration of TCP Connections During an FTP File Transfer l Two TCP connections used FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 58
 TFTP l l Second file transfer service in TCP/IP: Trivial File Transfer Protocol (TFTP) Uses UDP instead of TCP Only supports file transfer Useful for bootstrapping a hardware device that has no disk for system software FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 59
TFTP l l Second file transfer service in TCP/IP: Trivial File Transfer Protocol (TFTP) Uses UDP instead of TCP Only supports file transfer Useful for bootstrapping a hardware device that has no disk for system software FALL 2005 CSI 4118 – UNIVERSITY OF OTTAWA 59
 Network File System l l l File transfer not needed for all data transfers File access service allows remote clients to copy or change small parts of file File access mechanism used with TCP/IP is Network File System (NSF) l l l FALL 2005 Allows client to copy or change pieces of file Allows shared file access Integrated into computer’s file system CSI 4118 – UNIVERSITY OF OTTAWA 60
Network File System l l l File transfer not needed for all data transfers File access service allows remote clients to copy or change small parts of file File access mechanism used with TCP/IP is Network File System (NSF) l l l FALL 2005 Allows client to copy or change pieces of file Allows shared file access Integrated into computer’s file system CSI 4118 – UNIVERSITY OF OTTAWA 60
 Summary l l Applications use client-server paradigm for interaction Client l l l Arbitrary application Actively initiates communication Must know server’s l l FALL 2005 IP address Protocol port number CSI 4118 – UNIVERSITY OF OTTAWA 61
Summary l l Applications use client-server paradigm for interaction Client l l l Arbitrary application Actively initiates communication Must know server’s l l FALL 2005 IP address Protocol port number CSI 4118 – UNIVERSITY OF OTTAWA 61
 Summary (continued) l Server l l l FALL 2005 Specialized program Runs forever Usually offers one service Passively waits for clients Can handle multiple clients simultaneously CSI 4118 – UNIVERSITY OF OTTAWA 62
Summary (continued) l Server l l l FALL 2005 Specialized program Runs forever Usually offers one service Passively waits for clients Can handle multiple clients simultaneously CSI 4118 – UNIVERSITY OF OTTAWA 62
 Summary (continued) l Domain Name System l l Maps name to IP address Uses on-line servers Uses caching for efficiency Two e-mail transfer protocols l l FALL 2005 SMTP POP 3 CSI 4118 – UNIVERSITY OF OTTAWA 63
Summary (continued) l Domain Name System l l Maps name to IP address Uses on-line servers Uses caching for efficiency Two e-mail transfer protocols l l FALL 2005 SMTP POP 3 CSI 4118 – UNIVERSITY OF OTTAWA 63
 Summary (continued) l Remote login l l l Remote, interactive use Protocol is TELNET File transfer l l FALL 2005 Copy of entire file Protocol is FTP CSI 4118 – UNIVERSITY OF OTTAWA 64
Summary (continued) l Remote login l l l Remote, interactive use Protocol is TELNET File transfer l l FALL 2005 Copy of entire file Protocol is FTP CSI 4118 – UNIVERSITY OF OTTAWA 64


