5ed66b1758bfe2ca3382a6672bb7e6f0.ppt
- Количество слайдов: 15

PAPI: Simple and Ubiquitous Access to Internet Information Services JISC/CNI Conference - Edinburgh, 27 June 2002

Outline • Requirements on AA (Authentication and Authorization) technologies • The PAPI components • The PAPI protocol • Application scenarios • Current status and ongoing work 2

Requirements on AA technologies • Preserve user privacy • Do not interfere with provider rights and accounting procedures • Do not impose management burdens either to providers or consumers • Fully permit user mobility • Transparency to the user • Compatibility with other access control systems • Web based, although extensible to other access technologies 3
What is PAPI • PAPI enables distributed access control to information resources accross the Internet § Authentication is locally performed at the organization the user belongs to § Authorization is fully controlled by the provider • Based on standard HTTP procedures and public key cryptography § Does not require specific hardware or software 4
The components of PAPI • The Authentication Server (AS) § Provides users with a (local) single authentication point • The Point of Access (Po. A) § Performs actual access control by means of temporary cryptographic tokens, encoded as HTTP cookies • The Group-wide Point of Access (GPo. A) § Combines a group of Po. As with similar access policies § Intended to simplify AS-Po. A interactions 5
The Authentication Server • Verifies user identity and rights § Each of these verifications is independently performed § Directories play a key role in rights management • Builds a set of digitally signed assertions about the user § According to privacy preservation rules • Sends the assertions to the appropriate (G)Po. As § By means of references to objects embedded in HTML 6

The Point of Access • Evaluates assertions received from the AS § Verifying the signature and matching against any defined filter § If the assertion is acceptable, produces a initial couple of access tokens • If the request comes with access tokens, evaluates them § Access is granted only to requests carrying valid tokens § Two classes of tokens (long- and shortlived) to avoid unauthorized access by cookie copying 7

The Group-wide Point of Access • A Po. A that receives a request without access tokens can redirect it to a GPo. A • The GPo. A analyzes these requests § If valid, the Po. A receives a signed assertion from its GPo. A § The Po. A process it as coming from any other AS § The hierarchy may be indefinitely extended • Trust management is simplified § An AS needs only to know about the GPo. A § Po. As may be added under a GPo. A without configuring them for valid ASes 8
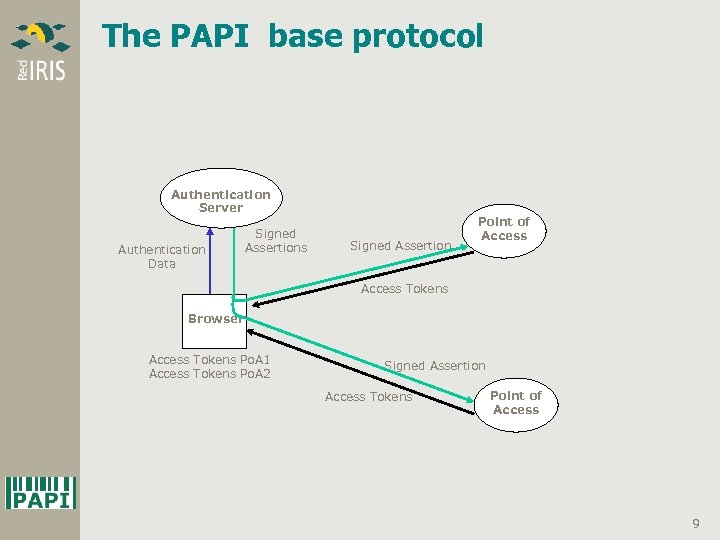
The PAPI base protocol Authentication Server Authentication Data Signed Assertions Signed Assertion Point of Access Tokens Browser Access Tokens Po. A 1 Access Tokens Po. A 2 Signed Assertion Access Tokens Point of Access 9
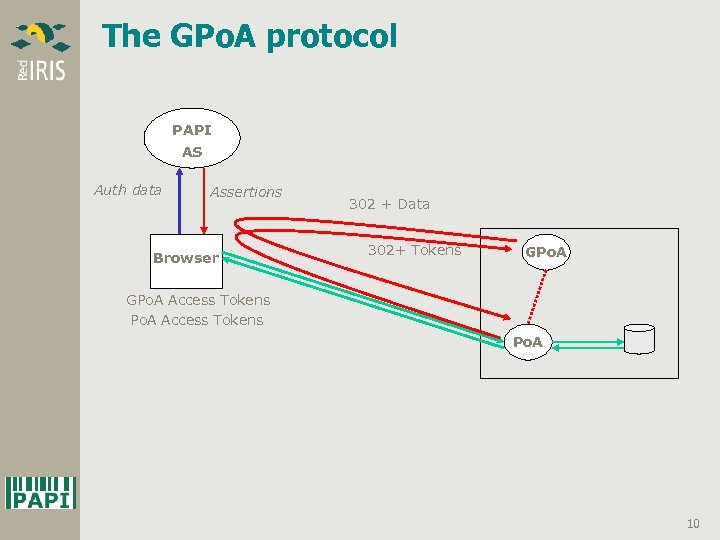
The GPo. A protocol PAPI AS Auth data Assertions Browser 302 + Data 302+ Tokens GPo. A Access Tokens Po. A 10
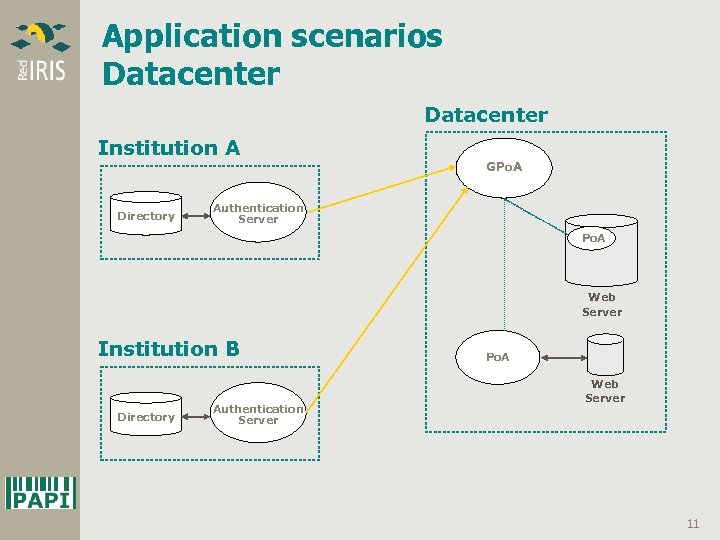
Application scenarios Datacenter Institution A Directory GPo. A Authentication Server Po. A Web Server Institution B Directory Authentication Server Po. A Web Server 11
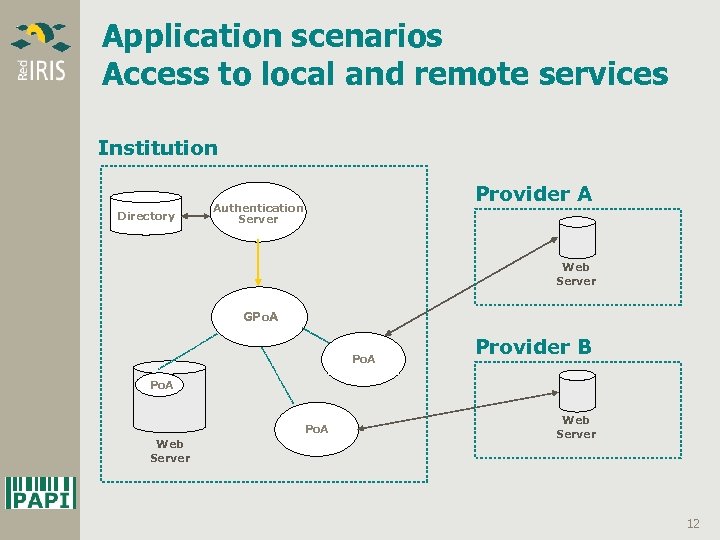
Application scenarios Access to local and remote services Institution Directory Provider A Authentication Server Web Server GPo. A Provider B Po. A Web Server 12
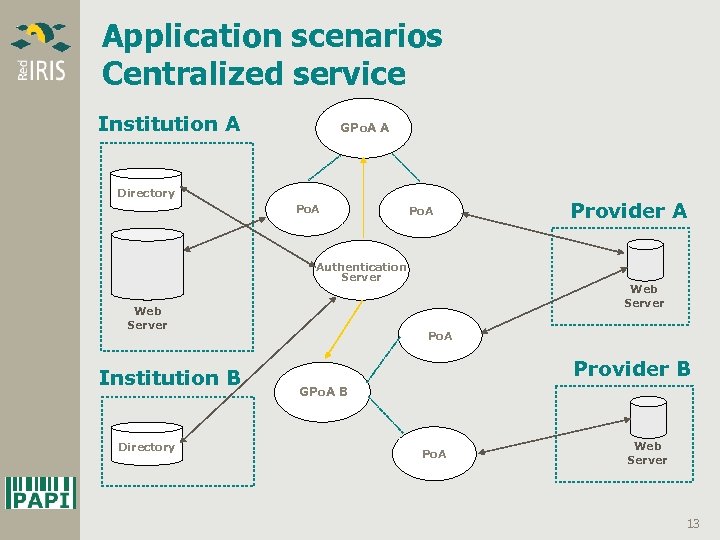
Application scenarios Centralized service Institution A GPo. A A Directory Po. A Authentication Server Web Server Institution B Directory Provider A Web Server Po. A Provider B GPo. A B Po. A Web Server 13
Current status • Version 1. 1 in production § Available in open source from http: //www. rediris. es/app/papi/ § Runs on Apache servers § Authentication modules based on POP 3, LDAP and index files • Version 1. 2 nearly to be released § Includes ISAPI (Microsoft IIS) support § Enhanced proxy functionality § Simpler configuration • Growing installed base § Gaining experience on requirements and applicability 14

Ongoing work • Alignment with other AA initiatives § Use of standard languages (SAML) for assertions and normalization of attributes § In the framework of the TF-AACE group • In collaboration with Internet 2 (Shibboleth) • Dynamic assertion evaluation § Based on attribute queries made by (G)Po. As and answered by the AS § Running on top of Web. Services (SOAP) • Performance enhancements • Going beyond the Web § Use of the AA model for other applications: videoconferencing, Grid services, . . . 15
5ed66b1758bfe2ca3382a6672bb7e6f0.ppt