4285ae37c3075a2942bd90258c82ff11.ppt
- Количество слайдов: 13
 Palo Alto Networks Product Overview Karsten Dindorp, Computerlinks
Palo Alto Networks Product Overview Karsten Dindorp, Computerlinks
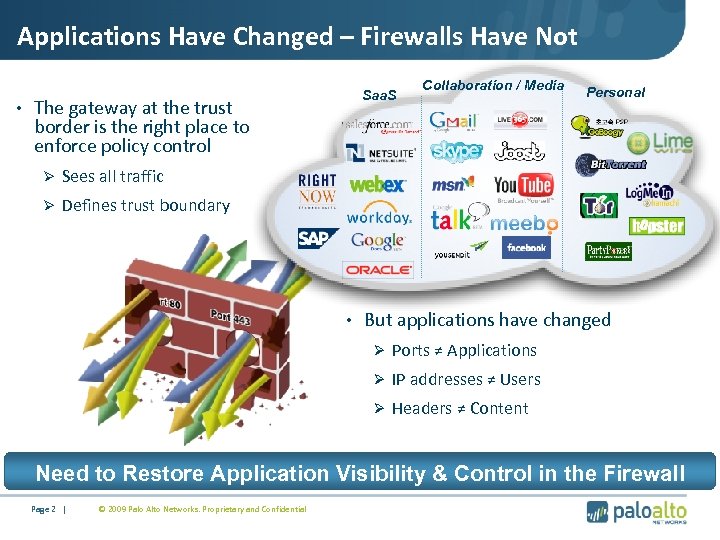 Applications Have Changed – Firewalls Have Not • The gateway at the trust Saa. S Collaboration / Media Personal border is the right place to enforce policy control Ø Sees all traffic Ø Defines trust boundary • But applications have changed Ø Ports ≠ Applications Ø IP addresses ≠ Users Ø Headers ≠ Content Need to Restore Application Visibility & Control in the Firewall Page 2 | © 2009 Palo Alto Networks. Proprietary and Confidential
Applications Have Changed – Firewalls Have Not • The gateway at the trust Saa. S Collaboration / Media Personal border is the right place to enforce policy control Ø Sees all traffic Ø Defines trust boundary • But applications have changed Ø Ports ≠ Applications Ø IP addresses ≠ Users Ø Headers ≠ Content Need to Restore Application Visibility & Control in the Firewall Page 2 | © 2009 Palo Alto Networks. Proprietary and Confidential
 Stateful Inspection Classification The Common Foundation of Nearly All Firewalls • Stateful Inspection classifies traffic by looking at the IP header - source IP - source port - destination IP - destination port - protocol • Internal table creates mapping to well-known protocols/ports - HTTP = TCP port 80 - SMTP = TCP port 25 - SSL = TCP port 443 - etc, etc… Page 3 | © 2009 Palo Alto Networks. Proprietary and Confidential
Stateful Inspection Classification The Common Foundation of Nearly All Firewalls • Stateful Inspection classifies traffic by looking at the IP header - source IP - source port - destination IP - destination port - protocol • Internal table creates mapping to well-known protocols/ports - HTTP = TCP port 80 - SMTP = TCP port 25 - SSL = TCP port 443 - etc, etc… Page 3 | © 2009 Palo Alto Networks. Proprietary and Confidential
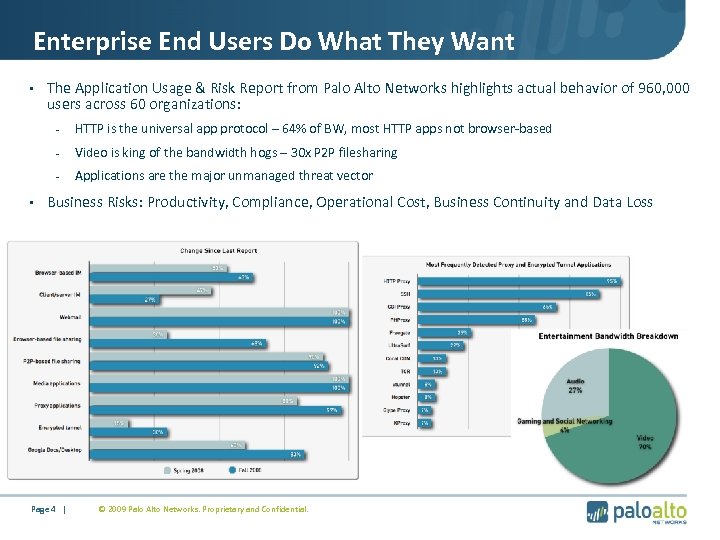 Enterprise End Users Do What They Want • The Application Usage & Risk Report from Palo Alto Networks highlights actual behavior of 960, 000 users across 60 organizations: - HTTP is the universal app protocol – 64% of BW, most HTTP apps not browser-based - Video is king of the bandwidth hogs – 30 x P 2 P filesharing - Applications are the major unmanaged threat vector • Business Risks: Productivity, Compliance, Operational Cost, Business Continuity and Data Loss Page 4 | © 2009 Palo Alto Networks. Proprietary and Confidential.
Enterprise End Users Do What They Want • The Application Usage & Risk Report from Palo Alto Networks highlights actual behavior of 960, 000 users across 60 organizations: - HTTP is the universal app protocol – 64% of BW, most HTTP apps not browser-based - Video is king of the bandwidth hogs – 30 x P 2 P filesharing - Applications are the major unmanaged threat vector • Business Risks: Productivity, Compliance, Operational Cost, Business Continuity and Data Loss Page 4 | © 2009 Palo Alto Networks. Proprietary and Confidential.
 Firewall “helpers” Is Not The Answer Internet • Complex to manage • Expensive to buy and maintain • Firewall “helpers” have limited view of traffic • Ultimately, doesn’t solve the problem Page 5 | © 2009 Palo Alto Networks. Proprietary and Confidential
Firewall “helpers” Is Not The Answer Internet • Complex to manage • Expensive to buy and maintain • Firewall “helpers” have limited view of traffic • Ultimately, doesn’t solve the problem Page 5 | © 2009 Palo Alto Networks. Proprietary and Confidential
 The Right Answer: Make the Firewall Do Its Job New Requirements for the Firewall 1. Identify applications regardless of port, protocol, evasive tactic or SSL 2. Identify users regardless of IP address 3. Scan application content in real-time (prevent threats and data leaks) 4. Granular visibility and policy control over application access / functionality 5. Multi-gigabit, in-line deployment with no performance degradation Page 6 | © 2009 Palo Alto Networks. Proprietary and Confidential
The Right Answer: Make the Firewall Do Its Job New Requirements for the Firewall 1. Identify applications regardless of port, protocol, evasive tactic or SSL 2. Identify users regardless of IP address 3. Scan application content in real-time (prevent threats and data leaks) 4. Granular visibility and policy control over application access / functionality 5. Multi-gigabit, in-line deployment with no performance degradation Page 6 | © 2009 Palo Alto Networks. Proprietary and Confidential
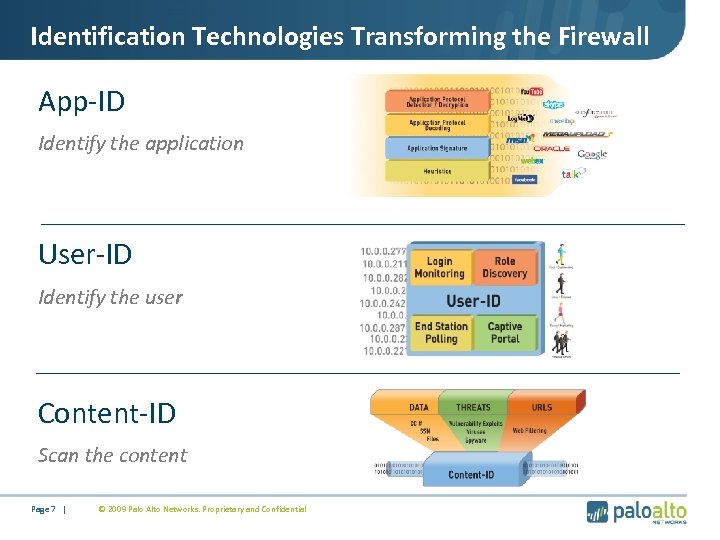 Identification Technologies Transforming the Firewall App-ID Identify the application User-ID Identify the user Content-ID Scan the content Page 7 | © 2009 Palo Alto Networks. Proprietary and Confidential
Identification Technologies Transforming the Firewall App-ID Identify the application User-ID Identify the user Content-ID Scan the content Page 7 | © 2009 Palo Alto Networks. Proprietary and Confidential
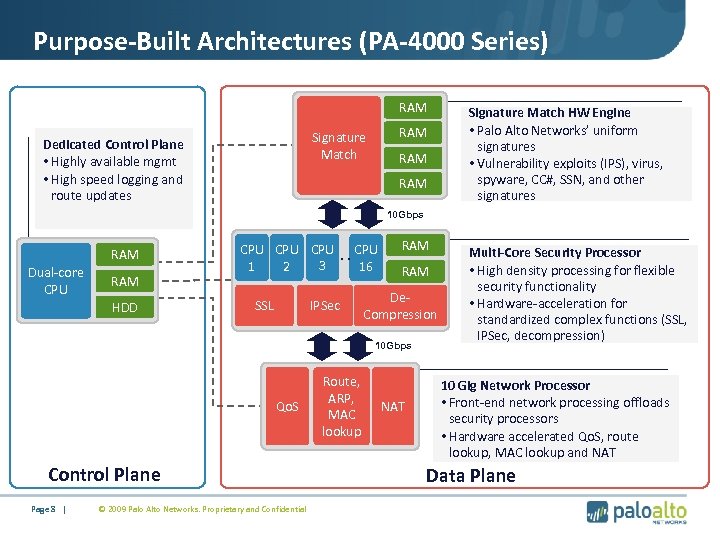 Purpose-Built Architectures (PA-4000 Series) RAM Signature Match Dedicated Control Plane • Highly available mgmt • High speed logging and route updates RAM Signature Match HW Engine • Palo Alto Networks’ uniform signatures • Vulnerability exploits (IPS), virus, spyware, CC#, SSN, and other signatures 10 Gbps RAM Dual-core CPU RAM HDD CPU CPU. . CPU 3 1 2 16 SSL IPSec RAM De. Compression 10 Gbps Qo. S Control Plane Page 8 | © 2009 Palo Alto Networks. Proprietary and Confidential Route, ARP, MAC lookup NAT Multi-Core Security Processor • High density processing for flexible security functionality • Hardware-acceleration for standardized complex functions (SSL, IPSec, decompression) 10 Gig Network Processor • Front-end network processing offloads security processors • Hardware accelerated Qo. S, route lookup, MAC lookup and NAT Data Plane
Purpose-Built Architectures (PA-4000 Series) RAM Signature Match Dedicated Control Plane • Highly available mgmt • High speed logging and route updates RAM Signature Match HW Engine • Palo Alto Networks’ uniform signatures • Vulnerability exploits (IPS), virus, spyware, CC#, SSN, and other signatures 10 Gbps RAM Dual-core CPU RAM HDD CPU CPU. . CPU 3 1 2 16 SSL IPSec RAM De. Compression 10 Gbps Qo. S Control Plane Page 8 | © 2009 Palo Alto Networks. Proprietary and Confidential Route, ARP, MAC lookup NAT Multi-Core Security Processor • High density processing for flexible security functionality • Hardware-acceleration for standardized complex functions (SSL, IPSec, decompression) 10 Gig Network Processor • Front-end network processing offloads security processors • Hardware accelerated Qo. S, route lookup, MAC lookup and NAT Data Plane
 PAN-OS Core Features • Strong networking foundation: • High Availability: - Active / passive - Configuration and session synchronization - Path, link, and HA monitoring - Dynamic routing (OSPF, RIPv 2) - Site-to-site IPSec VPN - SSL VPN - Tap mode – connect to SPAN port - Virtual wire (“Layer 1”) for true transparent in-line deployment - All interfaces (physical or logical) assigned to security zones - L 2/L 3 switching foundation - Establish multiple virtual systems to fully virtualized the device (PA-4000 & PA-2000 only) • Virtualization: • Qo. S traffic shaping - Max, guaranteed and priority - By user, app, interface, zone, and more Page 9 | © 2009 Palo Alto Networks. Proprietary and Confidential • Intuitive and flexible management - CLI, Web, Panorama, SNMP, Syslog
PAN-OS Core Features • Strong networking foundation: • High Availability: - Active / passive - Configuration and session synchronization - Path, link, and HA monitoring - Dynamic routing (OSPF, RIPv 2) - Site-to-site IPSec VPN - SSL VPN - Tap mode – connect to SPAN port - Virtual wire (“Layer 1”) for true transparent in-line deployment - All interfaces (physical or logical) assigned to security zones - L 2/L 3 switching foundation - Establish multiple virtual systems to fully virtualized the device (PA-4000 & PA-2000 only) • Virtualization: • Qo. S traffic shaping - Max, guaranteed and priority - By user, app, interface, zone, and more Page 9 | © 2009 Palo Alto Networks. Proprietary and Confidential • Intuitive and flexible management - CLI, Web, Panorama, SNMP, Syslog
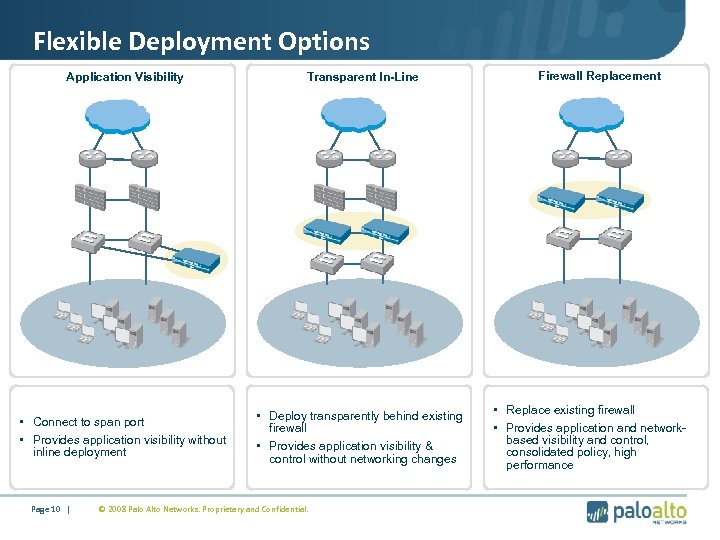 Flexible Deployment Options Application Visibility Transparent In-Line • Connect to span port • Provides application visibility without inline deployment • Deploy transparently behind existing firewall • Provides application visibility & control without networking changes Page 10 | © 2008 Palo Alto Networks. Proprietary and Confidential. Firewall Replacement • Replace existing firewall • Provides application and networkbased visibility and control, consolidated policy, high performance
Flexible Deployment Options Application Visibility Transparent In-Line • Connect to span port • Provides application visibility without inline deployment • Deploy transparently behind existing firewall • Provides application visibility & control without networking changes Page 10 | © 2008 Palo Alto Networks. Proprietary and Confidential. Firewall Replacement • Replace existing firewall • Provides application and networkbased visibility and control, consolidated policy, high performance
 Palo Alto Networks Next-Gen Firewalls PA-4060 • • • PA-4050 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 4 XFP (10 Gig) I/O 4 SFP (1 Gig) I/O PA-2050 • • • 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 16 copper gigabit 8 SFP interfaces PA-2020 1 Gbps FW 500 Mbps threat prevention 250, 000 sessions 16 copper gigabit 4 SFP interfaces Page 11 | • • • 500 Mbps FW 200 Mbps threat prevention 125, 000 sessions 12 copper gigabit 2 SFP interfaces © 2009 Palo Alto Networks. Proprietary and Confidential PA-4020 • • • 2 Gbps FW 2 Gbps threat prevention 500, 000 sessions 16 copper gigabit 8 SFP interfaces PA-500 • • 250 Mbps FW 100 Mbps threat prevention 50, 000 sessions 8 copper gigabit
Palo Alto Networks Next-Gen Firewalls PA-4060 • • • PA-4050 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 4 XFP (10 Gig) I/O 4 SFP (1 Gig) I/O PA-2050 • • • 10 Gbps FW 5 Gbps threat prevention 2, 000 sessions 16 copper gigabit 8 SFP interfaces PA-2020 1 Gbps FW 500 Mbps threat prevention 250, 000 sessions 16 copper gigabit 4 SFP interfaces Page 11 | • • • 500 Mbps FW 200 Mbps threat prevention 125, 000 sessions 12 copper gigabit 2 SFP interfaces © 2009 Palo Alto Networks. Proprietary and Confidential PA-4020 • • • 2 Gbps FW 2 Gbps threat prevention 500, 000 sessions 16 copper gigabit 8 SFP interfaces PA-500 • • 250 Mbps FW 100 Mbps threat prevention 50, 000 sessions 8 copper gigabit
 PAN-OS 3. 0 Summary of Features • Networking - Quality of Service Enforcement SSL VPN IPv 6 Firewall (Virtual Wire) IPsec Multiple Phase 2 SAs 802. 3 ad link aggregation PA-2000 virtual systems licenses (+5) • App-ID • Visibility and Reporting - • Management - Custom Web-based App-IDs - Custom App-ID Risk and Timeouts - CRL checking within SSL forward proxy - • Threat Prevention & URL Filtering - - Dynamic URL Filtering DB - Increased signature capacity - Threat Exception List - CVE in Threat Profiles - - • User Identification Citrix/Terminal Server User ID © 2009 Palo Alto Networks. Proprietary and Confidential Page 12 - | Proxy X-Forwarded-For Support - User Activity Report - Multi-zone Rules Automated Config Backup in Panorama Role-based admins in Panorama SNMP Enhancements Ø Custom community string Ø Extended MIB support XML-based REST API Ability to Duplicate Objects Log Export Enhancements Ø Support for FTP Ø Scheduler Custom Admin Login Banner Web-based Tech Support Export Database indexing Configurable management I/O settings
PAN-OS 3. 0 Summary of Features • Networking - Quality of Service Enforcement SSL VPN IPv 6 Firewall (Virtual Wire) IPsec Multiple Phase 2 SAs 802. 3 ad link aggregation PA-2000 virtual systems licenses (+5) • App-ID • Visibility and Reporting - • Management - Custom Web-based App-IDs - Custom App-ID Risk and Timeouts - CRL checking within SSL forward proxy - • Threat Prevention & URL Filtering - - Dynamic URL Filtering DB - Increased signature capacity - Threat Exception List - CVE in Threat Profiles - - • User Identification Citrix/Terminal Server User ID © 2009 Palo Alto Networks. Proprietary and Confidential Page 12 - | Proxy X-Forwarded-For Support - User Activity Report - Multi-zone Rules Automated Config Backup in Panorama Role-based admins in Panorama SNMP Enhancements Ø Custom community string Ø Extended MIB support XML-based REST API Ability to Duplicate Objects Log Export Enhancements Ø Support for FTP Ø Scheduler Custom Admin Login Banner Web-based Tech Support Export Database indexing Configurable management I/O settings
 Demo Page 13 | © 2007 Palo Alto Networks. Proprietary and Confidential 2009 Palo Alto Networks. Proprietary and Confidential
Demo Page 13 | © 2007 Palo Alto Networks. Proprietary and Confidential 2009 Palo Alto Networks. Proprietary and Confidential


