f682f70c109238427b22954fd52b3c88.ppt
- Количество слайдов: 28
Packet Vaccine: Black-box Exploit Detection and Signature Generation Xiao. Feng Wang, Zhuowei Li Jun Xu, Mike Reiter Chongkyung Kil and Jong Youl Choi Dr. Xiao. Feng Wang Spring 2006
Automated Exploit Defense Dr. Xiao. Feng Wang Spring 2006
Expectations for Automated Defense? § A perfect fix to vulnerable software? § A reasonably secure and fast-generated fix seems more realistic Dr. Xiao. Feng Wang Spring 2006

Automatic Exploit Defense: the State of Art Source code instrument Static analysis of source code Monitor an application’s execution to the break point Static analysis of binary code Dr. Xiao. Feng Wang Spring 2006

Vaccine: a weakened viruses or bacteria for stimulating antibody production How about a black-box “packet vaccine” ? Dr. Xiao. Feng Wang Spring 2006
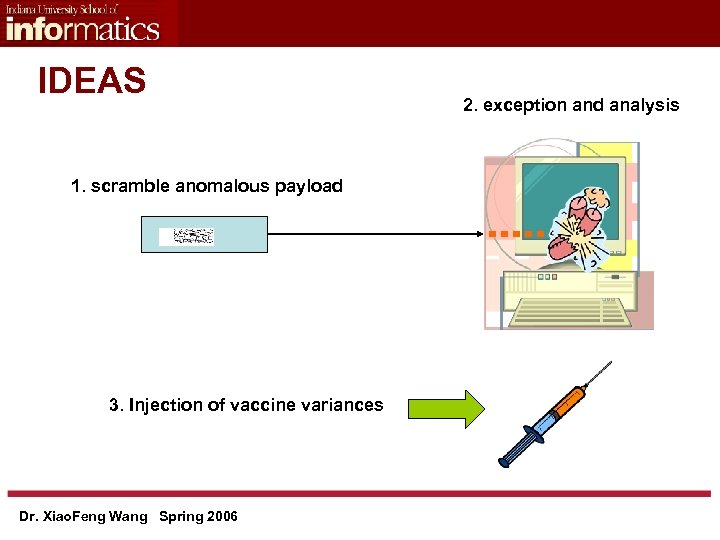
IDEAS 1. scramble anomalous payload 3. Injection of vaccine variances Dr. Xiao. Feng Wang Spring 2006 2. exception and analysis
Properties § Fast Exploit Detection § Black-box Signature Generation Ø Work on obfuscated code § Little or no modification to the protected system Dr. Xiao. Feng Wang Spring 2006
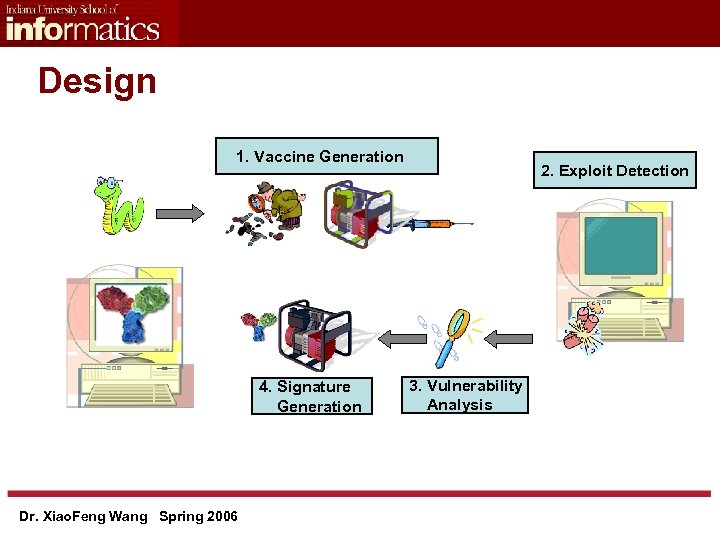
Design 1. Vaccine Generation 4. Signature Generation Dr. Xiao. Feng Wang Spring 2006 2. Exploit Detection 3. Vulnerability Analysis

Vaccine Generation § How to generate a weakened exploit? § Our approach 1. Identify an address-like byte token on a packet 2. Randomize it Dr. Xiao. Feng Wang Spring 2006

Address-like Tokens § Use address range Ø stack: 0 xc 0000000 Ø heap: 0 x 08048000 Ø entries of some libc functions § Where to get them? Ø Linux: /proc/pid/maps Ø Windows: debugging tools/memory monitoring tools Dr. Xiao. Feng Wang Spring 2006
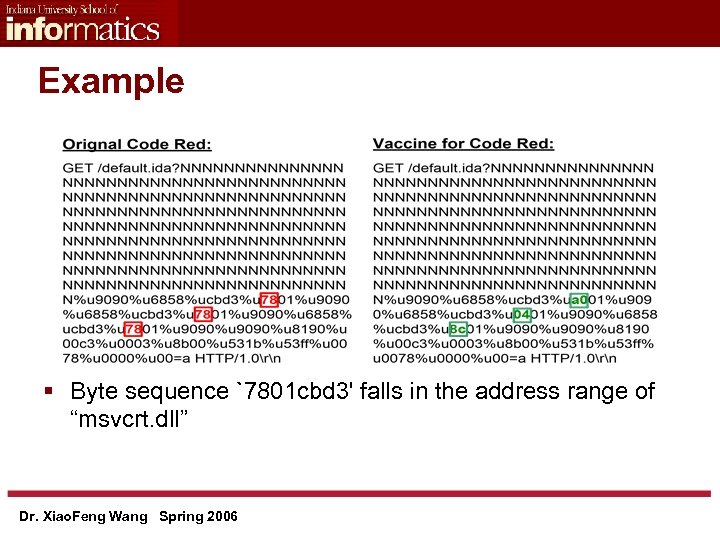
Example § Byte sequence `7801 cbd 3' falls in the address range of “msvcrt. dll” Dr. Xiao. Feng Wang Spring 2006
Exploit Detection and Vuln. Diagnosis § Detection: Ø Exception happens § Diagnosis Ø Pickup the contents from CR 2 and EIP Ø Match them to the scrambled byte sequences Ø Locate the corrupted pointer Dr. Xiao. Feng Wang Spring 2006
Signature Generation (1) § App-independent Signatures Ø Byte sequences § Byte-based Vaccine Injection (BVI) Ø Modify one byte and the jump address Ø Send to the application Ø not crash important byte Dr. Xiao. Feng Wang Spring 2006
Signature Generation (2) § Application-level Signatures Ø field length (buffer overrun) Ø special symbols (e. g, “%n” formate string) § App-based Vaccine Injection (AVI) Ø the minimal field length crash Ø remove special tokens no crash Dr. Xiao. Feng Wang Spring 2006
Performance § BVI is parallelizable Ø for multi-process application § AVI can be enhanced by binary search Dr. Xiao. Feng Wang Spring 2006
Implementation § Intercept application-level dataflow to detect suspicious tokens § Scramble them to generate vaccines § Signature generation (Red. Hat Linux 7. 3) Ø Verifier: implemented using ptrace Ø Prober: local/remote Ø Prober and verifier: a persistent connection Ø Verifier notifies Prober of exceptions Dr. Xiao. Feng Wang Spring 2006
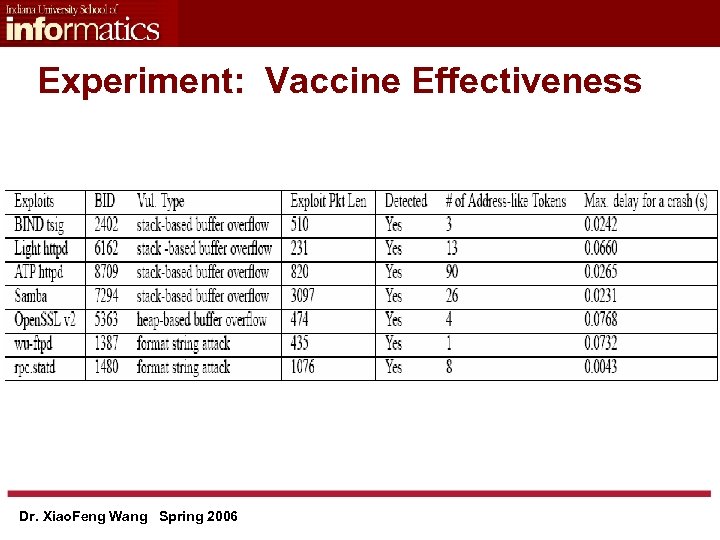
Experiment: Vaccine Effectiveness Dr. Xiao. Feng Wang Spring 2006
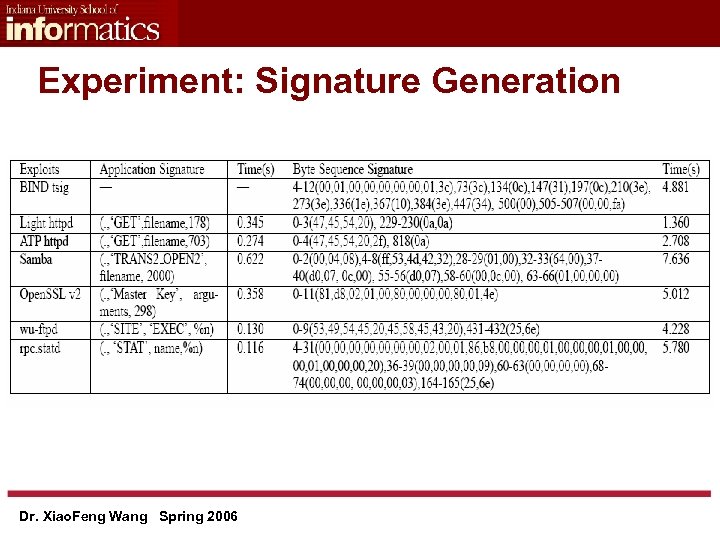
Experiment: Signature Generation Dr. Xiao. Feng Wang Spring 2006
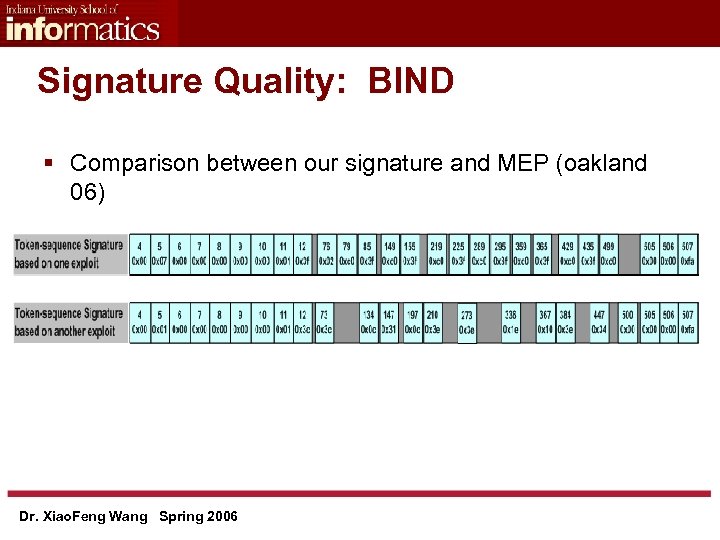
Signature Quality: BIND § Comparison between our signature and MEP (oakland 06) Dr. Xiao. Feng Wang Spring 2006
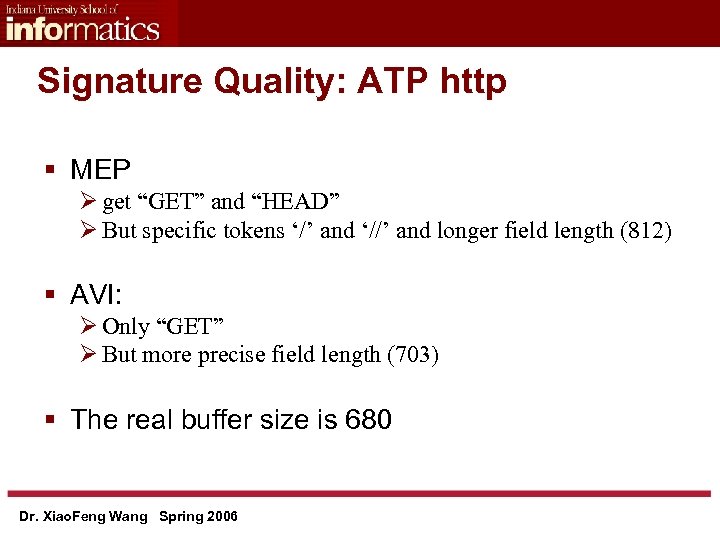
Signature Quality: ATP http § MEP Ø get “GET” and “HEAD” Ø But specific tokens ‘/’ and ‘//’ and longer field length (812) § AVI: Ø Only “GET” Ø But more precise field length (703) § The real buffer size is 680 Dr. Xiao. Feng Wang Spring 2006

False positives Dr. Xiao. Feng Wang Spring 2006
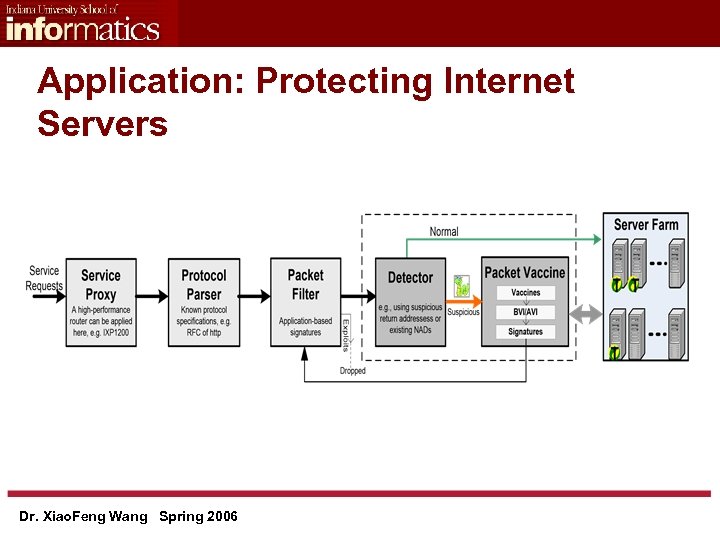
Application: Protecting Internet Servers Dr. Xiao. Feng Wang Spring 2006
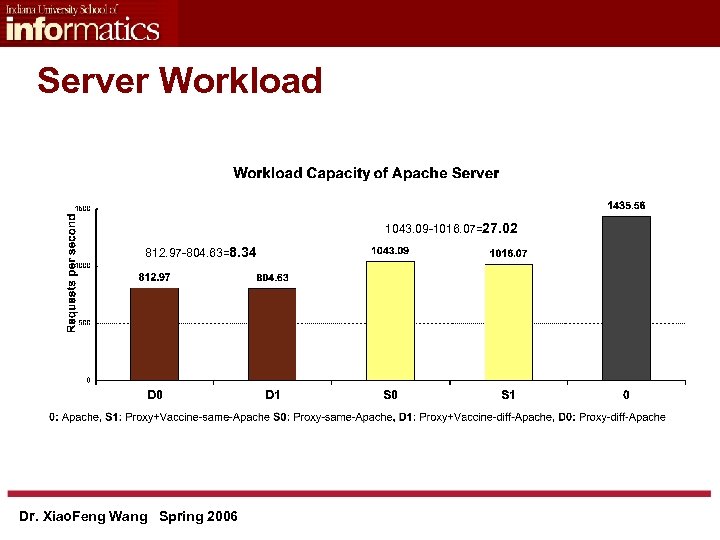
Server Workload 1043. 09 -1016. 07=27. 02 812. 97 -804. 63=8. 34 Dr. Xiao. Feng Wang Spring 2006
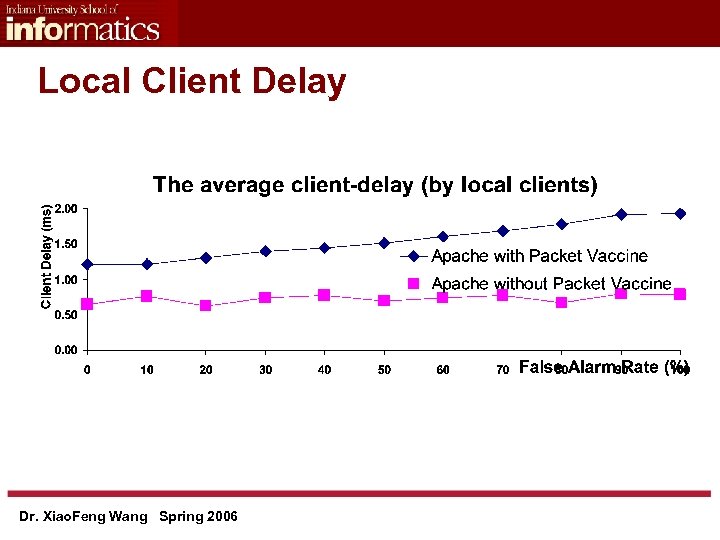
Local Client Delay Dr. Xiao. Feng Wang Spring 2006
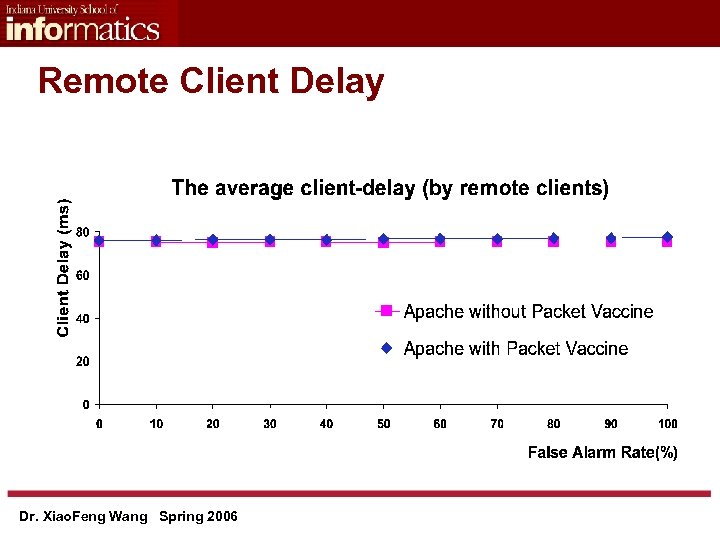
Remote Client Delay Dr. Xiao. Feng Wang Spring 2006
Other Applications § Vulnerability Scanner § A lightweight replacement for Grey-box approaches § Proactive discovery and fix of vulnerabilities Dr. Xiao. Feng Wang Spring 2006
Limitations § False negatives in exploit detection § Encrypted payload and checksums § Signature limitations in representation Dr. Xiao. Feng Wang Spring 2006
Future Work § Generation of more accurate signatures § Proactive detection of software vulnerabilities Dr. Xiao. Feng Wang Spring 2006
f682f70c109238427b22954fd52b3c88.ppt