717518622817367b58e1251d5547c203.ppt
- Количество слайдов: 106
 Packet Manuplation
Packet Manuplation
 Topics Covered
Topics Covered
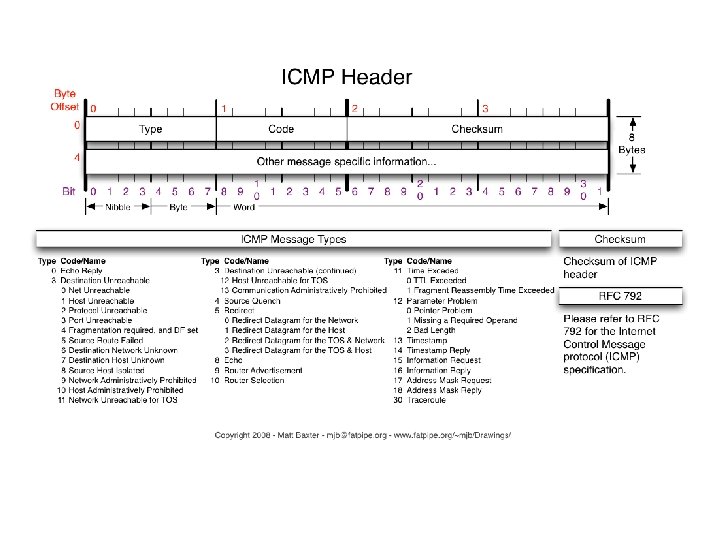
 Network Protocol Headers: TCP, IP, UDP, ICMP, MAC
Network Protocol Headers: TCP, IP, UDP, ICMP, MAC
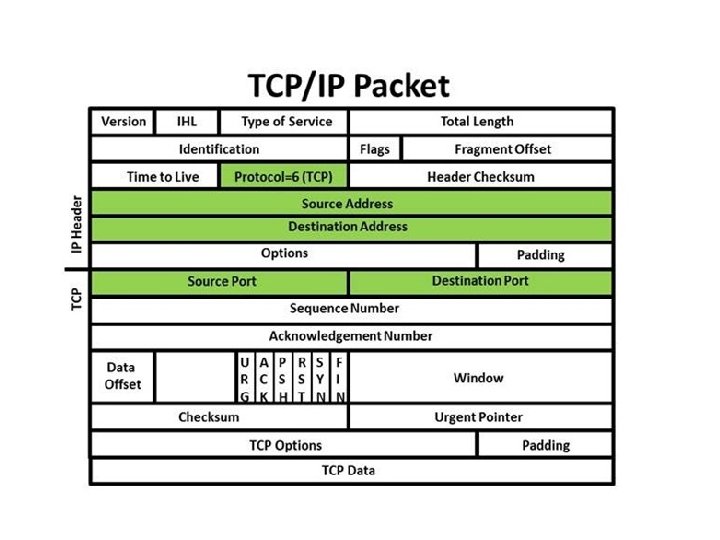
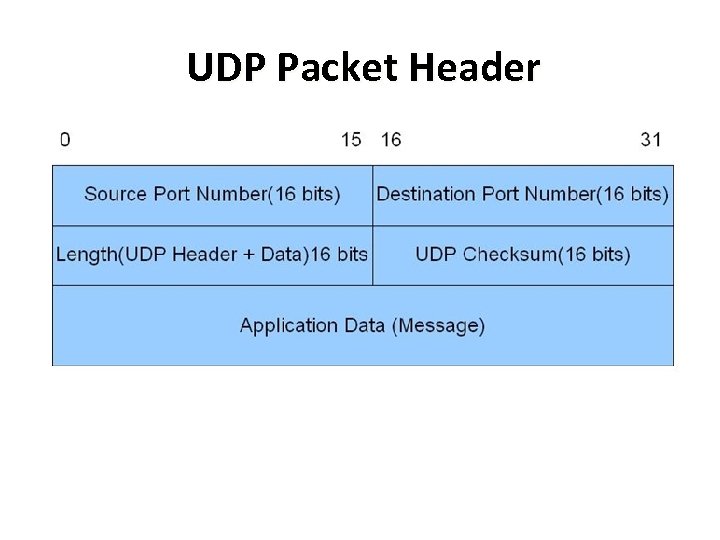 UDP Packet Header
UDP Packet Header
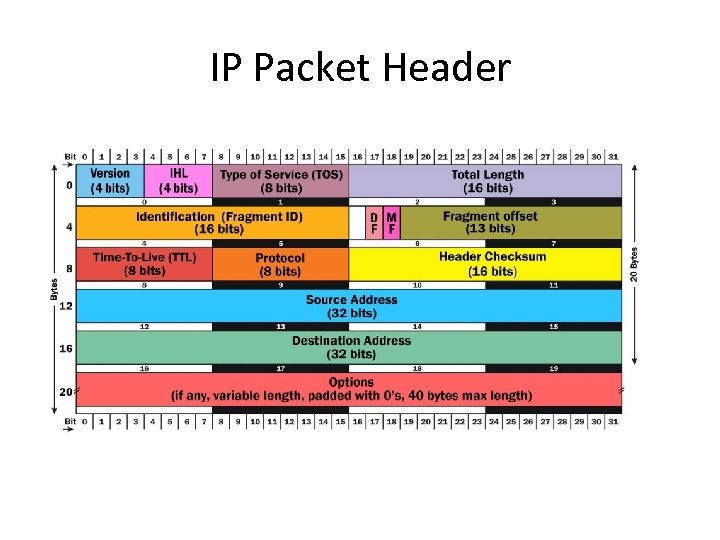 IP Packet Header
IP Packet Header
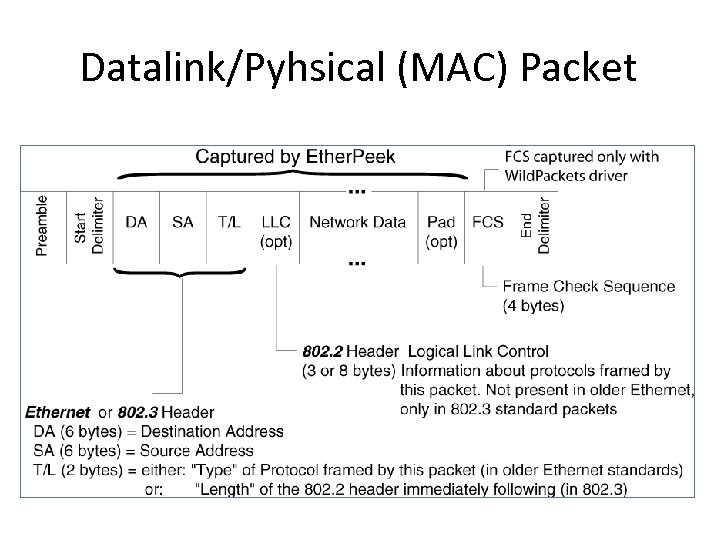 Datalink/Pyhsical (MAC) Packet
Datalink/Pyhsical (MAC) Packet
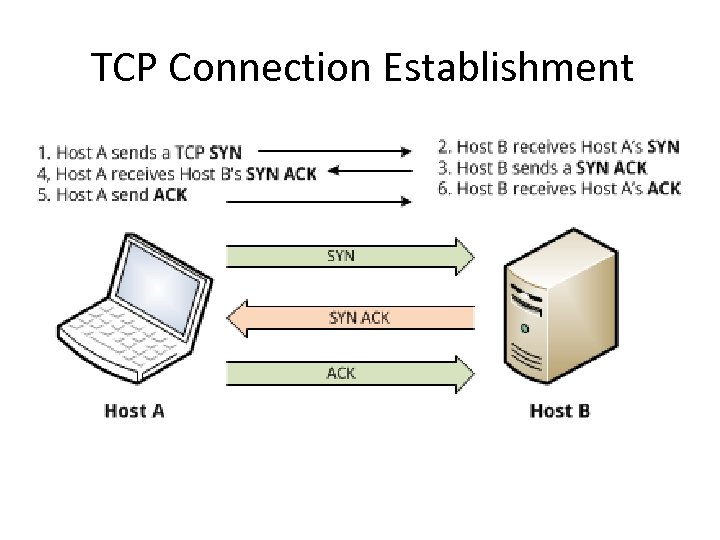 TCP Connection Establishment
TCP Connection Establishment
 Normal TCP Handshake
Normal TCP Handshake
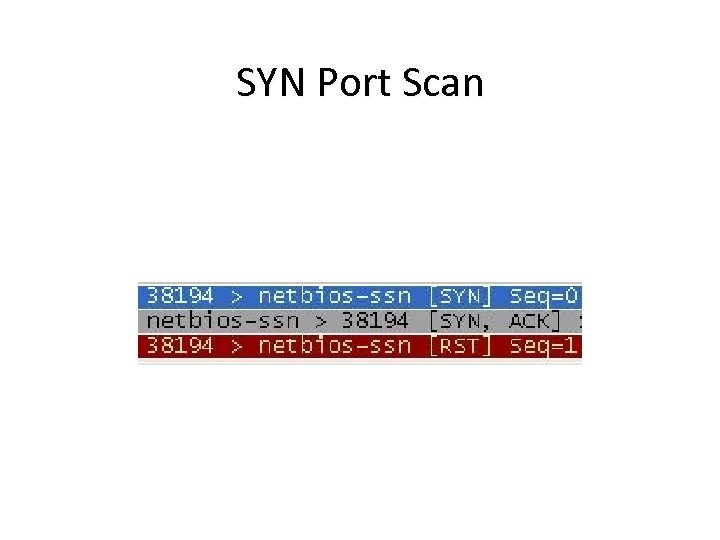 SYN Port Scan
SYN Port Scan
 Scapy Packet Manipulation
Scapy Packet Manipulation
 The First Step 1. Install Python 3. 5+ 2. Download and install Scapy 3. (Optional): Install additional software for special features. 4. Run Scapy with root privileges.
The First Step 1. Install Python 3. 5+ 2. Download and install Scapy 3. (Optional): Install additional software for special features. 4. Run Scapy with root privileges.
 Hello World
Hello World
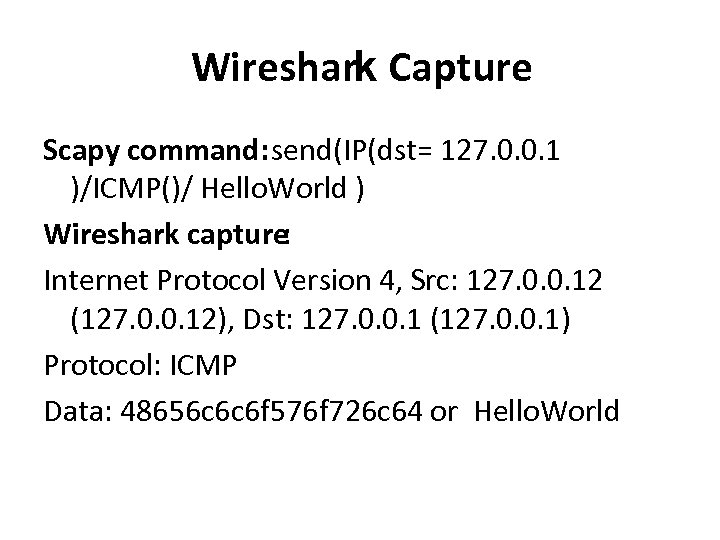 Wireshark Capture Scapy command: send(IP(dst= 127. 0. 0. 1 )/ICMP()/ Hello. World ) Wireshark capture: Internet Protocol Version 4, Src: 127. 0. 0. 12 (127. 0. 0. 12), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Protocol: ICMP Data: 48656 c 6 c 6 f 576 f 726 c 64 or Hello. World
Wireshark Capture Scapy command: send(IP(dst= 127. 0. 0. 1 )/ICMP()/ Hello. World ) Wireshark capture: Internet Protocol Version 4, Src: 127. 0. 0. 12 (127. 0. 0. 12), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Protocol: ICMP Data: 48656 c 6 c 6 f 576 f 726 c 64 or Hello. World
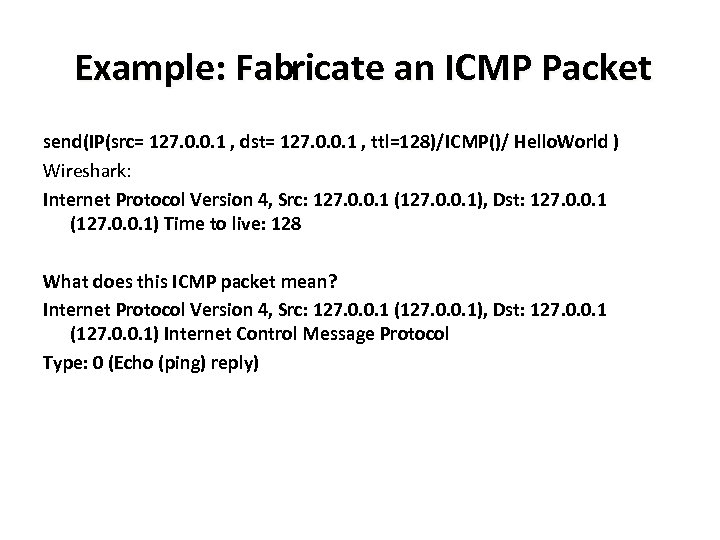 Example: Fabricate an ICMP Packet send(IP(src= 127. 0. 0. 1 , dst= 127. 0. 0. 1 , ttl=128)/ICMP()/ Hello. World ) Wireshark: Internet Protocol Version 4, Src: 127. 0. 0. 1 (127. 0. 0. 1), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Time to live: 128 What does this ICMP packet mean? Internet Protocol Version 4, Src: 127. 0. 0. 1 (127. 0. 0. 1), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Internet Control Message Protocol Type: 0 (Echo (ping) reply)
Example: Fabricate an ICMP Packet send(IP(src= 127. 0. 0. 1 , dst= 127. 0. 0. 1 , ttl=128)/ICMP()/ Hello. World ) Wireshark: Internet Protocol Version 4, Src: 127. 0. 0. 1 (127. 0. 0. 1), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Time to live: 128 What does this ICMP packet mean? Internet Protocol Version 4, Src: 127. 0. 0. 1 (127. 0. 0. 1), Dst: 127. 0. 0. 1 (127. 0. 0. 1) Internet Control Message Protocol Type: 0 (Echo (ping) reply)
 Sending a ping packet
Sending a ping packet
 Sending a ping packet with random source IP
Sending a ping packet with random source IP
 Sending & Receiving Layer 3 and 2 Packets
Sending & Receiving Layer 3 and 2 Packets
![Show the Packet Contents ###[ IP ]### version= 4 L ihl= 5 L tos= Show the Packet Contents ###[ IP ]### version= 4 L ihl= 5 L tos=](https://present5.com/presentation/717518622817367b58e1251d5547c203/image-20.jpg) Show the Packet Contents ###[ IP ]### version= 4 L ihl= 5 L tos= 0 x 0 len= 38 id= 7395 flags= frag= 0 L ttl= 64 proto= icmp chksum= 0 x 83 d 7 src= 127. 0. 0. 1 dst= 127. 0. 0. 1 options ###[ ICMP ]### type= echo-reply code= 0 chksum= 0 x 0 id= 0 x 0 seq= 0 x 0 ###[ Raw ]### load= 'Hello. World' ###[ Padding ]### load= 'x 00xe 7x 03 Nx 99' >>>
Show the Packet Contents ###[ IP ]### version= 4 L ihl= 5 L tos= 0 x 0 len= 38 id= 7395 flags= frag= 0 L ttl= 64 proto= icmp chksum= 0 x 83 d 7 src= 127. 0. 0. 1 dst= 127. 0. 0. 1 options ###[ ICMP ]### type= echo-reply code= 0 chksum= 0 x 0 id= 0 x 0 seq= 0 x 0 ###[ Raw ]### load= 'Hello. World' ###[ Padding ]### load= 'x 00xe 7x 03 Nx 99' >>>
 Show the TTL of the ICMP reply packet
Show the TTL of the ICMP reply packet
 Create an ARP request
Create an ARP request
 UDP Scanning
UDP Scanning
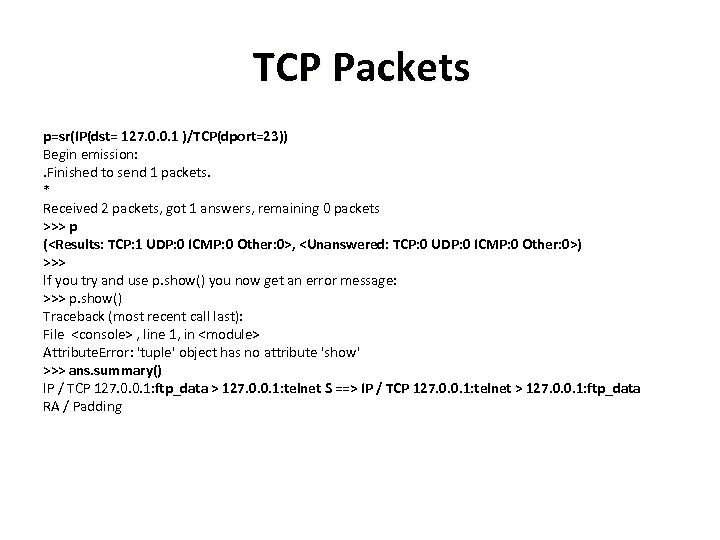 TCP Packets p=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=23)) Begin emission: . Finished to send 1 packets. * Received 2 packets, got 1 answers, remaining 0 packets >>> p (
TCP Packets p=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=23)) Begin emission: . Finished to send 1 packets. * Received 2 packets, got 1 answers, remaining 0 packets >>> p (
![TCP Packets a=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=[23, 80, 53])) Begin emission: . **Finished TCP Packets a=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=[23, 80, 53])) Begin emission: . **Finished](https://present5.com/presentation/717518622817367b58e1251d5547c203/image-25.jpg) TCP Packets a=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=[23, 80, 53])) Begin emission: . **Finished to send 3 packets. * Received 4 packets, got 3 answers, remaining 0 packets >>> a (
TCP Packets a=sr(IP(dst= 127. 0. 0. 1 )/TCP(dport=[23, 80, 53])) Begin emission: . **Finished to send 3 packets. * Received 4 packets, got 3 answers, remaining 0 packets >>> a (
 TCP SYN to port 80
TCP SYN to port 80
 Details of the TCP packet >>> p (
Details of the TCP packet >>> p (
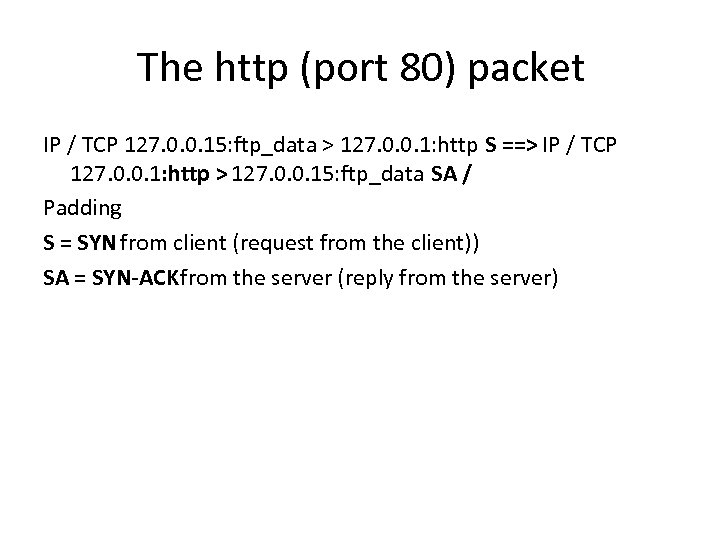 The http (port 80) packet IP / TCP 127. 0. 0. 15: ftp_data > 127. 0. 0. 1: http S ==> IP / TCP 127. 0. 0. 1: http > 127. 0. 0. 15: ftp_data SA / Padding S = SYN from client (request from the client)) SA = SYN-ACK from the server (reply from the server)
The http (port 80) packet IP / TCP 127. 0. 0. 15: ftp_data > 127. 0. 0. 1: http S ==> IP / TCP 127. 0. 0. 1: http > 127. 0. 0. 15: ftp_data SA / Padding S = SYN from client (request from the client)) SA = SYN-ACK from the server (reply from the server)
 The telnet (port 23) Packet IP / TCP 127. 0. 0. 1: ftp_data > 127. 0. 0. 1: telnet S ==> IP / TCP 127. 0. 0. 1: telnet > 127. 0. 0. 1: ftp_data RA / Padding SYN Sent from the source Destination responded with a RSTACK (RA) which is a RESet & ACKnowledgeflag in the TCP packet telling the source to reset the connection
The telnet (port 23) Packet IP / TCP 127. 0. 0. 1: ftp_data > 127. 0. 0. 1: telnet S ==> IP / TCP 127. 0. 0. 1: telnet > 127. 0. 0. 1: ftp_data RA / Padding SYN Sent from the source Destination responded with a RSTACK (RA) which is a RESet & ACKnowledgeflag in the TCP packet telling the source to reset the connection
![Port Scan (TCP-SYN Scan) a=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443], Port Scan (TCP-SYN Scan) a=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443],](https://present5.com/presentation/717518622817367b58e1251d5547c203/image-30.jpg) Port Scan (TCP-SYN Scan) a=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443], flags= S )) Source port=666 Destination ports: 22, 80, 21, and 443 flags= S = SYN scan
Port Scan (TCP-SYN Scan) a=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443], flags= S )) Source port=666 Destination ports: 22, 80, 21, and 443 flags= S = SYN scan
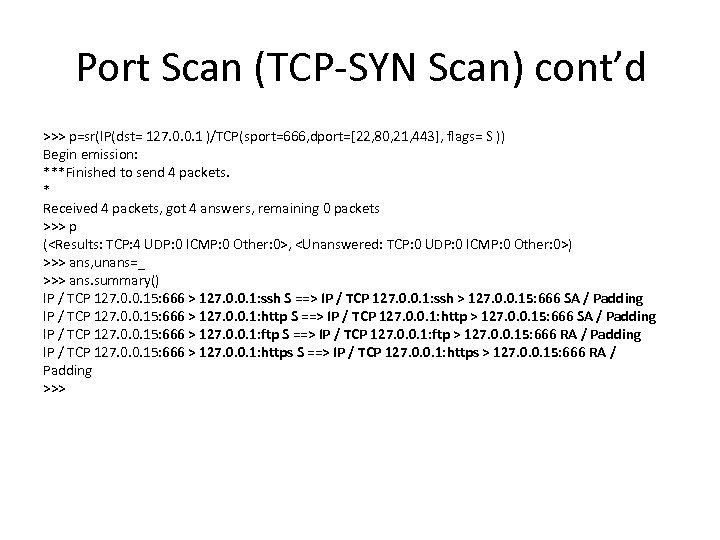 Port Scan (TCP-SYN Scan) cont’d >>> p=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443], flags= S )) Begin emission: ***Finished to send 4 packets. * Received 4 packets, got 4 answers, remaining 0 packets >>> p (
Port Scan (TCP-SYN Scan) cont’d >>> p=sr(IP(dst= 127. 0. 0. 1 )/TCP(sport=666, dport=[22, 80, 21, 443], flags= S )) Begin emission: ***Finished to send 4 packets. * Received 4 packets, got 4 answers, remaining 0 packets >>> p (
 TCP ACK flag sent after SYN flag
TCP ACK flag sent after SYN flag
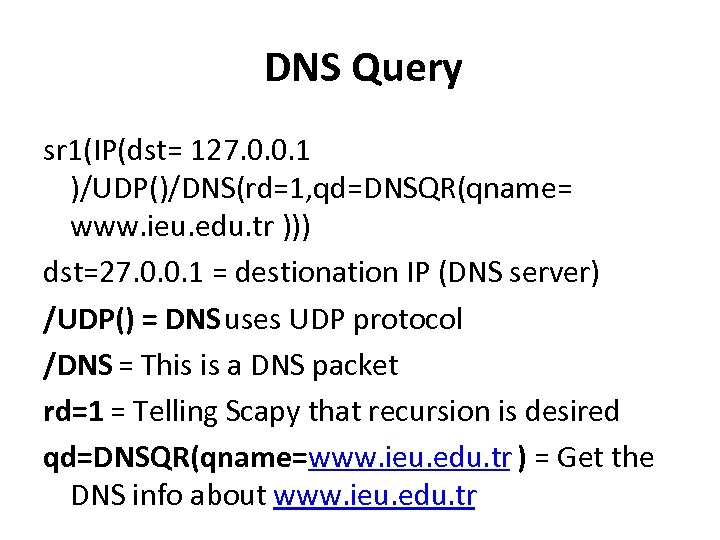 DNS Query sr 1(IP(dst= 127. 0. 0. 1 )/UDP()/DNS(rd=1, qd=DNSQR(qname= www. ieu. edu. tr ))) dst=27. 0. 0. 1 = destionation IP (DNS server) /UDP() = DNS uses UDP protocol /DNS = This is a DNS packet rd=1 = Telling Scapy that recursion is desired qd=DNSQR(qname=www. ieu. edu. tr ) = Get the DNS info about www. ieu. edu. tr
DNS Query sr 1(IP(dst= 127. 0. 0. 1 )/UDP()/DNS(rd=1, qd=DNSQR(qname= www. ieu. edu. tr ))) dst=27. 0. 0. 1 = destionation IP (DNS server) /UDP() = DNS uses UDP protocol /DNS = This is a DNS packet rd=1 = Telling Scapy that recursion is desired qd=DNSQR(qname=www. ieu. edu. tr ) = Get the DNS info about www. ieu. edu. tr
![Traceroute traceroute ([ www. google. com ], maxttl=20) Begin emission: . . *Finished to Traceroute traceroute ([ www. google. com ], maxttl=20) Begin emission: . . *Finished to](https://present5.com/presentation/717518622817367b58e1251d5547c203/image-34.jpg) Traceroute traceroute ([ www. google. com ], maxttl=20) Begin emission: . . *Finished to send 20 packets. ********* Received 20 packets, got 18 answers, remaining 2 packets 74. 125. 132. 99: tcp 80 1 172. 1. 16. 2 11 3 80. 3. 129. 161 11 4 212. 43. 163. 221 11 5 62. 252. 192. 157 11 6 62. 253. 187. 178 11 17 74. 125. 132. 99 SA 18 74. 125. 132. 99 SA 19 74. 125. 132. 99 SA 20 74. 125. 132. 99 SA (
Traceroute traceroute ([ www. google. com ], maxttl=20) Begin emission: . . *Finished to send 20 packets. ********* Received 20 packets, got 18 answers, remaining 2 packets 74. 125. 132. 99: tcp 80 1 172. 1. 16. 2 11 3 80. 3. 129. 161 11 4 212. 43. 163. 221 11 5 62. 252. 192. 157 11 6 62. 253. 187. 178 11 17 74. 125. 132. 99 SA 18 74. 125. 132. 99 SA 19 74. 125. 132. 99 SA 20 74. 125. 132. 99 SA (
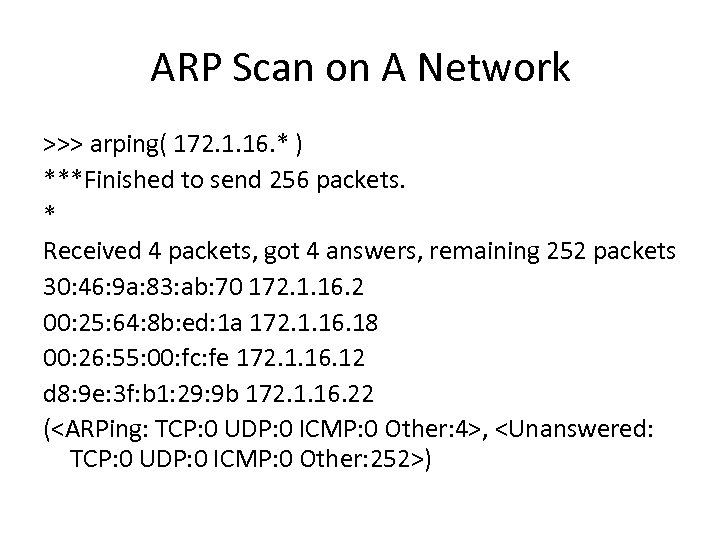 ARP Scan on A Network >>> arping( 172. 1. 16. * ) ***Finished to send 256 packets. * Received 4 packets, got 4 answers, remaining 252 packets 30: 46: 9 a: 83: ab: 70 172. 1. 16. 2 00: 25: 64: 8 b: ed: 1 a 172. 1. 16. 18 00: 26: 55: 00: fc: fe 172. 1. 16. 12 d 8: 9 e: 3 f: b 1: 29: 9 b 172. 1. 16. 22 (
ARP Scan on A Network >>> arping( 172. 1. 16. * ) ***Finished to send 256 packets. * Received 4 packets, got 4 answers, remaining 252 packets 30: 46: 9 a: 83: ab: 70 172. 1. 16. 2 00: 25: 64: 8 b: ed: 1 a 172. 1. 16. 18 00: 26: 55: 00: fc: fe 172. 1. 16. 12 d 8: 9 e: 3 f: b 1: 29: 9 b 172. 1. 16. 22 (
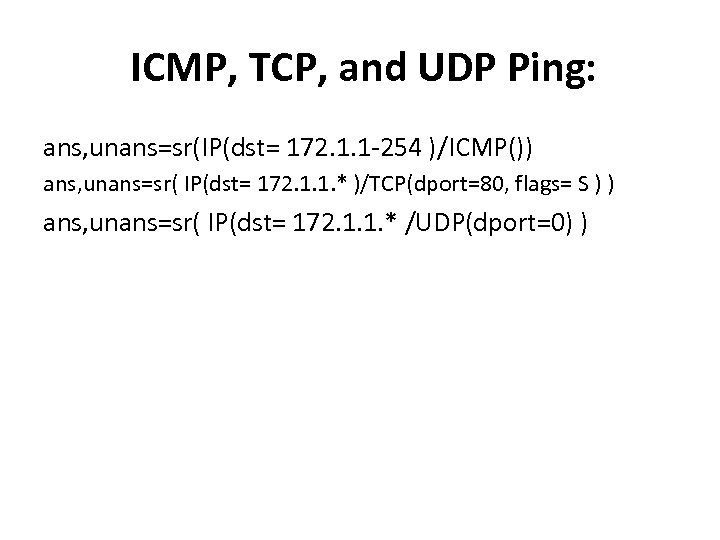 ICMP, TCP, and UDP Ping: ans, unans=sr(IP(dst= 172. 1. 1 -254 )/ICMP()) ans, unans=sr( IP(dst= 172. 1. 1. * )/TCP(dport=80, flags= S ) ) ans, unans=sr( IP(dst= 172. 1. 1. * /UDP(dport=0) )
ICMP, TCP, and UDP Ping: ans, unans=sr(IP(dst= 172. 1. 1 -254 )/ICMP()) ans, unans=sr( IP(dst= 172. 1. 1. * )/TCP(dport=80, flags= S ) ) ans, unans=sr( IP(dst= 172. 1. 1. * /UDP(dport=0) )
 Packet Sniffing sniff() CTRL-C (to stop sniffing) get something like
Packet Sniffing sniff() CTRL-C (to stop sniffing) get something like
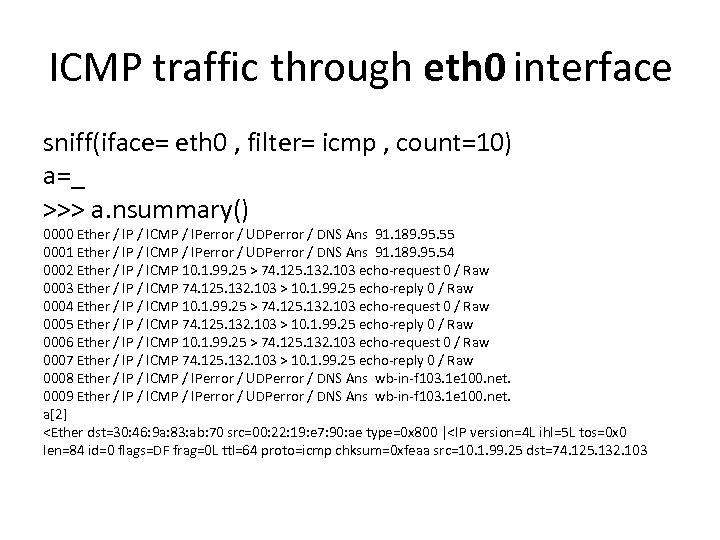 ICMP traffic through eth 0 interface sniff(iface= eth 0 , filter= icmp , count=10) a=_ >>> a. nsummary() 0000 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans 91. 189. 95. 55 0001 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans 91. 189. 95. 54 0002 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0003 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0004 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0005 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0006 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0007 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0008 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans wb-in-f 103. 1 e 100. net. 0009 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans wb-in-f 103. 1 e 100. net. a[2]
ICMP traffic through eth 0 interface sniff(iface= eth 0 , filter= icmp , count=10) a=_ >>> a. nsummary() 0000 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans 91. 189. 95. 55 0001 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans 91. 189. 95. 54 0002 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0003 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0004 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0005 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0006 Ether / IP / ICMP 10. 1. 99. 25 > 74. 125. 132. 103 echo-request 0 / Raw 0007 Ether / IP / ICMP 74. 125. 132. 103 > 10. 1. 99. 25 echo-reply 0 / Raw 0008 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans wb-in-f 103. 1 e 100. net. 0009 Ether / IP / ICMP / IPerror / UDPerror / DNS Ans wb-in-f 103. 1 e 100. net. a[2]
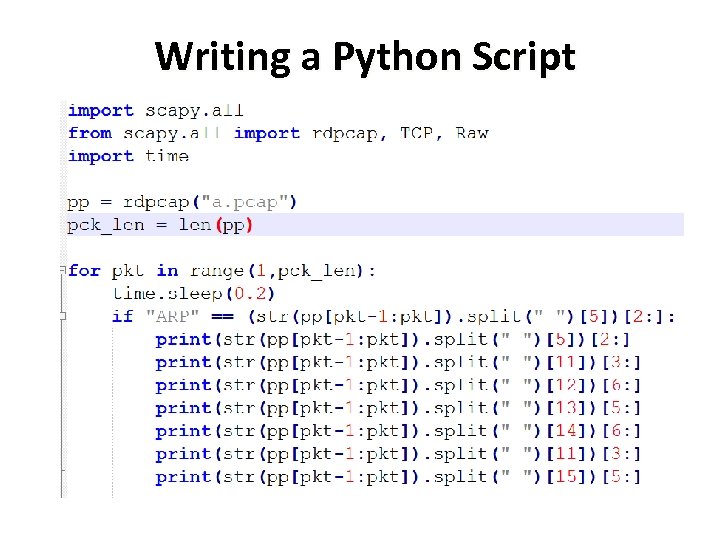 Writing a Python Script
Writing a Python Script
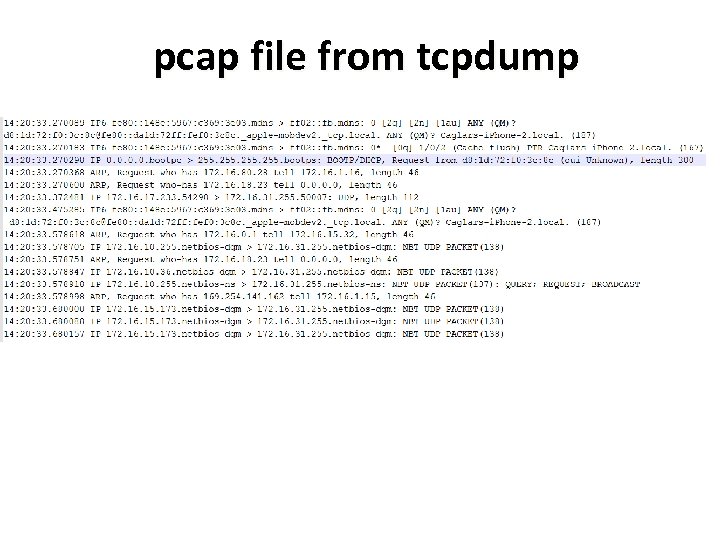 pcap file from tcpdump
pcap file from tcpdump
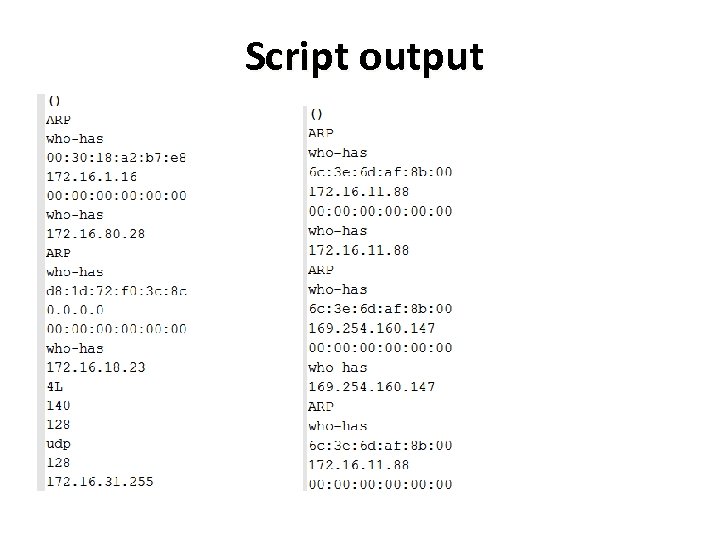 Script output
Script output
 Nmap (network mapper) is an open source tool for network traffic analysis and security auditing. It uses raw network packets to determine:
Nmap (network mapper) is an open source tool for network traffic analysis and security auditing. It uses raw network packets to determine:
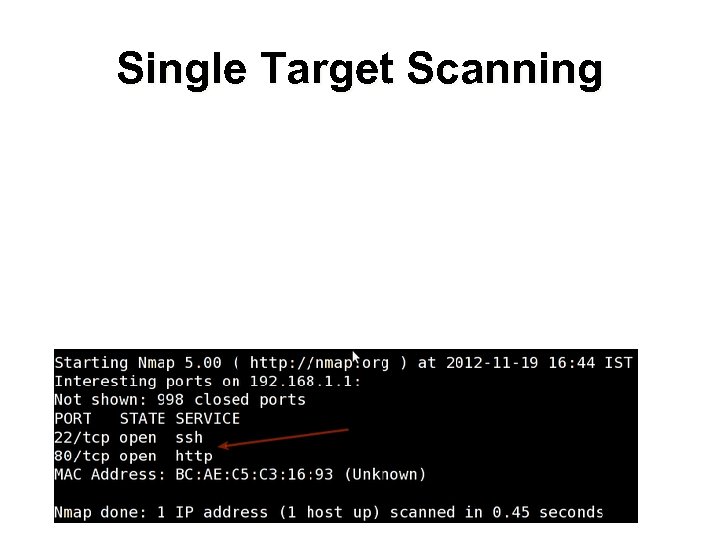 Single Target Scanning
Single Target Scanning
 Multiple Target Scanning
Multiple Target Scanning
 More Nmap Commands
More Nmap Commands
 More Nmap Commands
More Nmap Commands
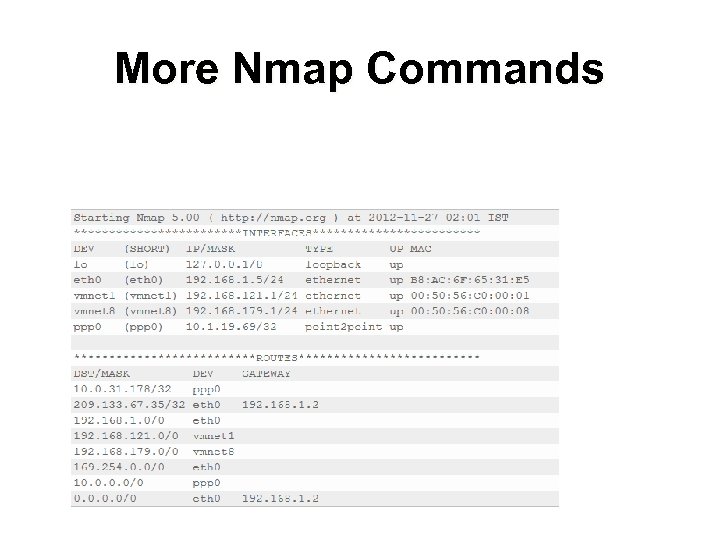 More Nmap Commands
More Nmap Commands
 Scan Specific ports
Scan Specific ports
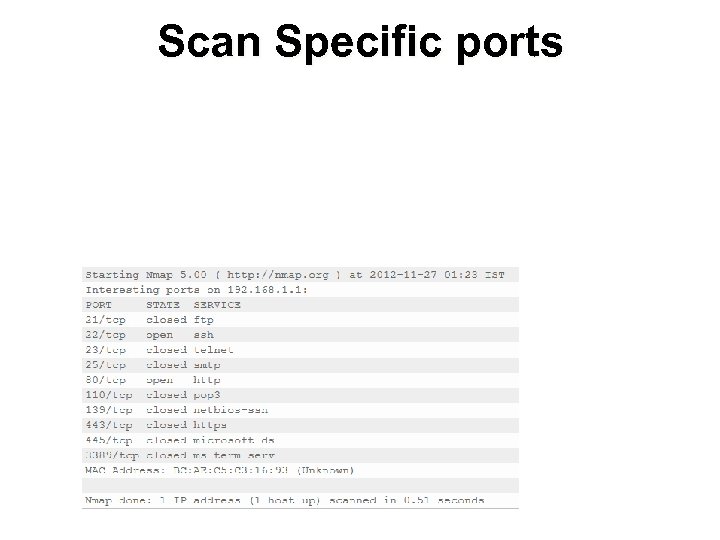 Scan Specific ports
Scan Specific ports
 Host Discovery (1)
Host Discovery (1)
 Host Discovery (2) nmap -O 192. 168. 1. 1 nmap -O --osscan-guess 192. 168. 1. 1 nmap -v -O --osscan-guess 192. 168. 1. 1 Starting Nmap 5. 00 ( http: //nmap. org ) at 2012 -11 -27 01: 29 IST NSE: Loaded 0 scripts for scanning. Initiating ARP Ping Scan at 01: 29 Scanning 192. 168. 1. 1 [1 port] Completed ARP Ping Scan at 01: 29, 0. 01 s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 01: 29 Completed Parallel DNS resolution of 1 host. at 01: 29, 0. 22 s elapsed Initiating SYN Stealth Scan at 01: 29 Scanning 192. 168. 1. 1 [1000 ports] Discovered open port 80/tcp on 192. 168. 1. 1 Discovered open port 22/tcp on 192. 168. 1. 1 Completed SYN Stealth Scan at 01: 29, 0. 16 s elapsed (1000 total ports) Initiating OS detection (try #1) against 192. 168. 1. 1 Retrying OS detection (try #2) against 192. 168. 1. 1 Retrying OS detection (try #3) against 192. 168. 1. 1 Retrying OS detection (try #4) against 192. 168. 1. 1 Retrying OS detection (try #5) against 192. 168. 1. 1 Host 192. 168. 1. 1 is up (0. 00049 s latency). Interesting ports on 192. 168. 1. 1: Not shown: 998 closed ports
Host Discovery (2) nmap -O 192. 168. 1. 1 nmap -O --osscan-guess 192. 168. 1. 1 nmap -v -O --osscan-guess 192. 168. 1. 1 Starting Nmap 5. 00 ( http: //nmap. org ) at 2012 -11 -27 01: 29 IST NSE: Loaded 0 scripts for scanning. Initiating ARP Ping Scan at 01: 29 Scanning 192. 168. 1. 1 [1 port] Completed ARP Ping Scan at 01: 29, 0. 01 s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 01: 29 Completed Parallel DNS resolution of 1 host. at 01: 29, 0. 22 s elapsed Initiating SYN Stealth Scan at 01: 29 Scanning 192. 168. 1. 1 [1000 ports] Discovered open port 80/tcp on 192. 168. 1. 1 Discovered open port 22/tcp on 192. 168. 1. 1 Completed SYN Stealth Scan at 01: 29, 0. 16 s elapsed (1000 total ports) Initiating OS detection (try #1) against 192. 168. 1. 1 Retrying OS detection (try #2) against 192. 168. 1. 1 Retrying OS detection (try #3) against 192. 168. 1. 1 Retrying OS detection (try #4) against 192. 168. 1. 1 Retrying OS detection (try #5) against 192. 168. 1. 1 Host 192. 168. 1. 1 is up (0. 00049 s latency). Interesting ports on 192. 168. 1. 1: Not shown: 998 closed ports
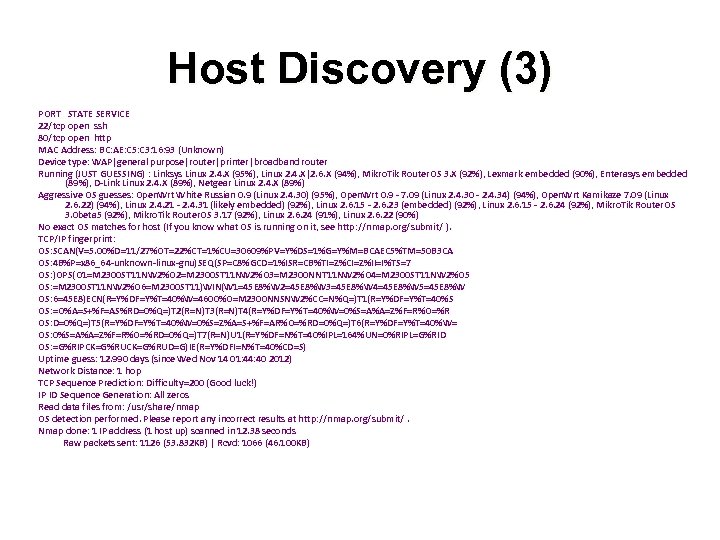 Host Discovery (3) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: BC: AE: C 5: C 3: 16: 93 (Unknown) Device type: WAP|general purpose|router|printer|broadband router Running (JUST GUESSING) : Linksys Linux 2. 4. X (95%), Linux 2. 4. X|2. 6. X (94%), Mikro. Tik Router. OS 3. X (92%), Lexmark embedded (90%), Enterasys embedded (89%), D-Link Linux 2. 4. X (89%), Netgear Linux 2. 4. X (89%) Aggressive OS guesses: Open. Wrt White Russian 0. 9 (Linux 2. 4. 30) (95%), Open. Wrt 0. 9 - 7. 09 (Linux 2. 4. 30 - 2. 4. 34) (94%), Open. Wrt Kamikaze 7. 09 (Linux 2. 6. 22) (94%), Linux 2. 4. 21 - 2. 4. 31 (likely embedded) (92%), Linux 2. 6. 15 - 2. 6. 23 (embedded) (92%), Linux 2. 6. 15 - 2. 6. 24 (92%), Mikro. Tik Router. OS 3. 0 beta 5 (92%), Mikro. Tik Router. OS 3. 17 (92%), Linux 2. 6. 24 (91%), Linux 2. 6. 22 (90%) No exact OS matches for host (If you know what OS is running on it, see http: //nmap. org/submit/ ). TCP/IP fingerprint: OS: SCAN(V=5. 00%D=11/27%OT=22%CT=1%CU=30609%PV=Y%DS=1%G=Y%M=BCAEC 5%TM=50 B 3 CA OS: 4 B%P=x 86_64 -unknown-linux-gnu)SEQ(SP=C 8%GCD=1%ISR=CB%TI=Z%CI=Z%II=I%TS=7 OS: )OPS(O 1=M 2300 ST 11 NW 2%O 2=M 2300 ST 11 NW 2%O 3=M 2300 NNT 11 NW 2%O 4=M 2300 ST 11 NW 2%O 5 OS: =M 2300 ST 11 NW 2%O 6=M 2300 ST 11)WIN(W 1=45 E 8%W 2=45 E 8%W 3=45 E 8%W 4=45 E 8%W 5=45 E 8%W OS: 6=45 E 8)ECN(R=Y%DF=Y%T=40%W=4600%O=M 2300 NNSNW 2%CC=N%Q=)T 1(R=Y%DF=Y%T=40%S OS: =O%A=S+%F=AS%RD=0%Q=)T 2(R=N)T 3(R=N)T 4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%R OS: D=0%Q=)T 5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T 6(R=Y%DF=Y%T=40%W= OS: 0%S=A%A=Z%F=R%O=%RD=0%Q=)T 7(R=N)U 1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID OS: =G%RIPCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Uptime guess: 12. 990 days (since Wed Nov 14 01: 44: 40 2012) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=200 (Good luck!) IP ID Sequence Generation: All zeros Read data files from: /usr/share/nmap OS detection performed. Please report any incorrect results at http: //nmap. org/submit/. Nmap done: 1 IP address (1 host up) scanned in 12. 38 seconds Raw packets sent: 1126 (53. 832 KB) | Rcvd: 1066 (46. 100 KB)
Host Discovery (3) PORT STATE SERVICE 22/tcp open ssh 80/tcp open http MAC Address: BC: AE: C 5: C 3: 16: 93 (Unknown) Device type: WAP|general purpose|router|printer|broadband router Running (JUST GUESSING) : Linksys Linux 2. 4. X (95%), Linux 2. 4. X|2. 6. X (94%), Mikro. Tik Router. OS 3. X (92%), Lexmark embedded (90%), Enterasys embedded (89%), D-Link Linux 2. 4. X (89%), Netgear Linux 2. 4. X (89%) Aggressive OS guesses: Open. Wrt White Russian 0. 9 (Linux 2. 4. 30) (95%), Open. Wrt 0. 9 - 7. 09 (Linux 2. 4. 30 - 2. 4. 34) (94%), Open. Wrt Kamikaze 7. 09 (Linux 2. 6. 22) (94%), Linux 2. 4. 21 - 2. 4. 31 (likely embedded) (92%), Linux 2. 6. 15 - 2. 6. 23 (embedded) (92%), Linux 2. 6. 15 - 2. 6. 24 (92%), Mikro. Tik Router. OS 3. 0 beta 5 (92%), Mikro. Tik Router. OS 3. 17 (92%), Linux 2. 6. 24 (91%), Linux 2. 6. 22 (90%) No exact OS matches for host (If you know what OS is running on it, see http: //nmap. org/submit/ ). TCP/IP fingerprint: OS: SCAN(V=5. 00%D=11/27%OT=22%CT=1%CU=30609%PV=Y%DS=1%G=Y%M=BCAEC 5%TM=50 B 3 CA OS: 4 B%P=x 86_64 -unknown-linux-gnu)SEQ(SP=C 8%GCD=1%ISR=CB%TI=Z%CI=Z%II=I%TS=7 OS: )OPS(O 1=M 2300 ST 11 NW 2%O 2=M 2300 ST 11 NW 2%O 3=M 2300 NNT 11 NW 2%O 4=M 2300 ST 11 NW 2%O 5 OS: =M 2300 ST 11 NW 2%O 6=M 2300 ST 11)WIN(W 1=45 E 8%W 2=45 E 8%W 3=45 E 8%W 4=45 E 8%W 5=45 E 8%W OS: 6=45 E 8)ECN(R=Y%DF=Y%T=40%W=4600%O=M 2300 NNSNW 2%CC=N%Q=)T 1(R=Y%DF=Y%T=40%S OS: =O%A=S+%F=AS%RD=0%Q=)T 2(R=N)T 3(R=N)T 4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%R OS: D=0%Q=)T 5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T 6(R=Y%DF=Y%T=40%W= OS: 0%S=A%A=Z%F=R%O=%RD=0%Q=)T 7(R=N)U 1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID OS: =G%RIPCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) Uptime guess: 12. 990 days (since Wed Nov 14 01: 44: 40 2012) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=200 (Good luck!) IP ID Sequence Generation: All zeros Read data files from: /usr/share/nmap OS detection performed. Please report any incorrect results at http: //nmap. org/submit/. Nmap done: 1 IP address (1 host up) scanned in 12. 38 seconds Raw packets sent: 1126 (53. 832 KB) | Rcvd: 1066 (46. 100 KB)
 Nping
Nping
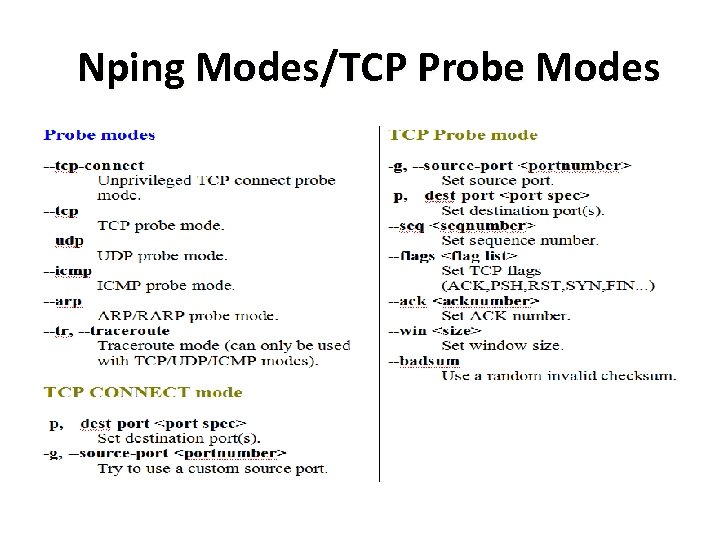 Nping Modes/TCP Probe Modes
Nping Modes/TCP Probe Modes
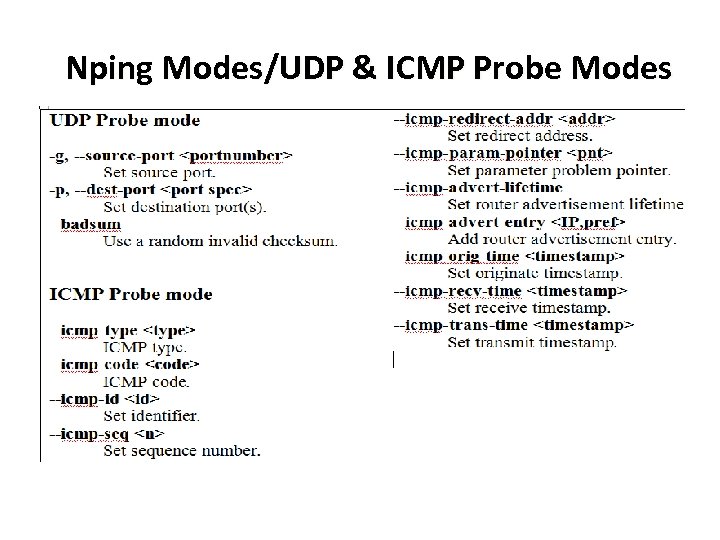 Nping Modes/UDP & ICMP Probe Modes
Nping Modes/UDP & ICMP Probe Modes
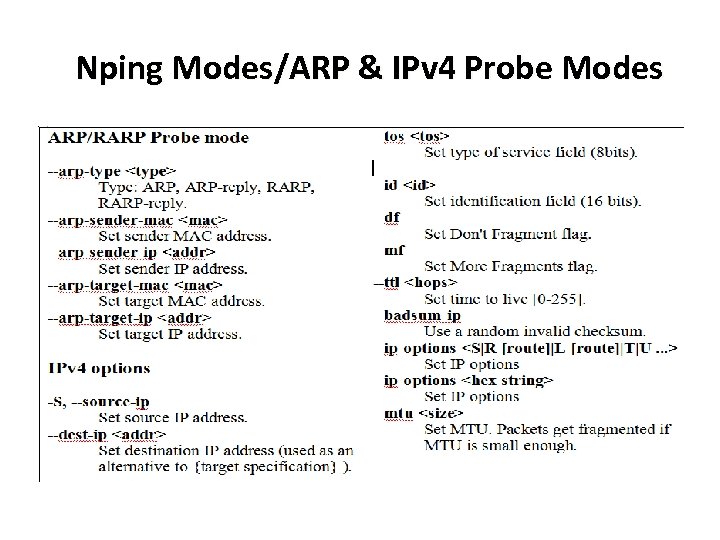 Nping Modes/ARP & IPv 4 Probe Modes
Nping Modes/ARP & IPv 4 Probe Modes
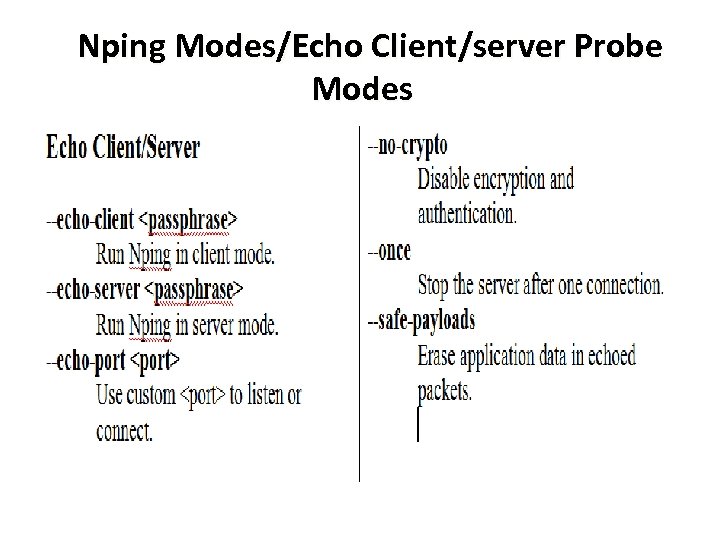 Nping Modes/Echo Client/server Probe Modes
Nping Modes/Echo Client/server Probe Modes
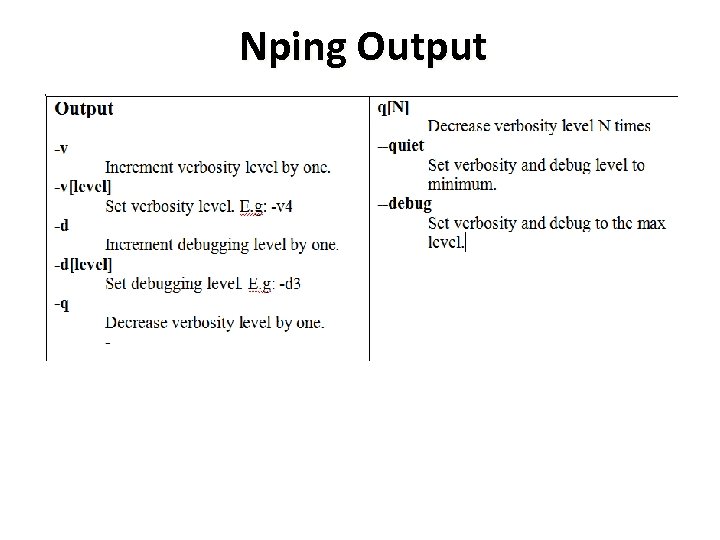 Nping Output
Nping Output
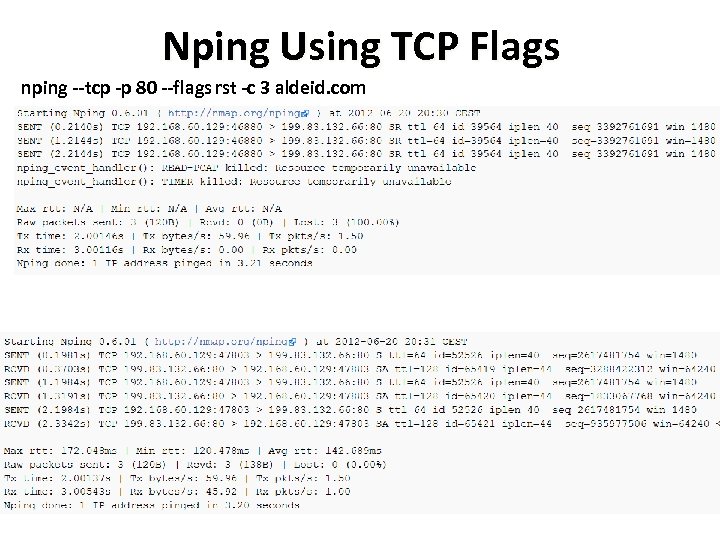 Nping Using TCP Flags nping --tcp -p 80 --flags rst -c 3 aldeid. com
Nping Using TCP Flags nping --tcp -p 80 --flags rst -c 3 aldeid. com
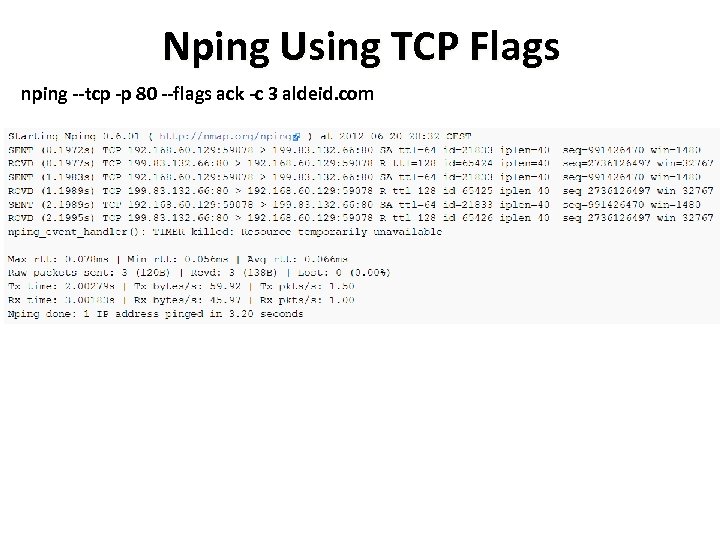 Nping Using TCP Flags nping --tcp -p 80 --flags ack -c 3 aldeid. com
Nping Using TCP Flags nping --tcp -p 80 --flags ack -c 3 aldeid. com
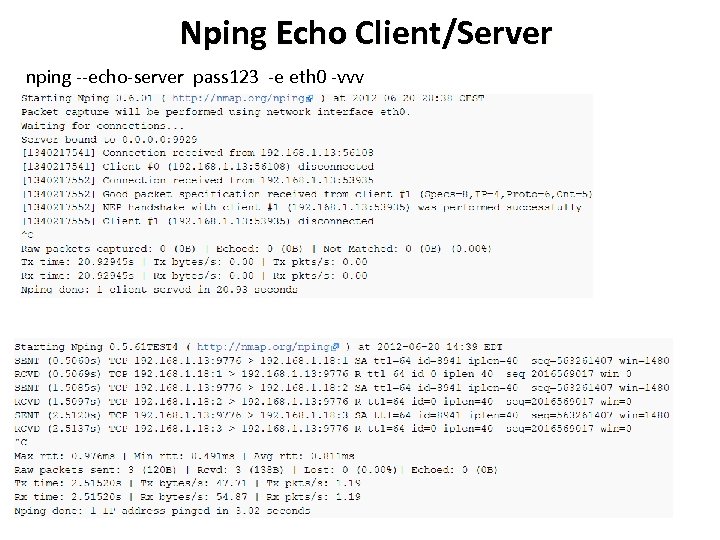 Nping Echo Client/Server nping --echo-server pass 123 -e eth 0 -vvv
Nping Echo Client/Server nping --echo-server pass 123 -e eth 0 -vvv
 tcpdump
tcpdump
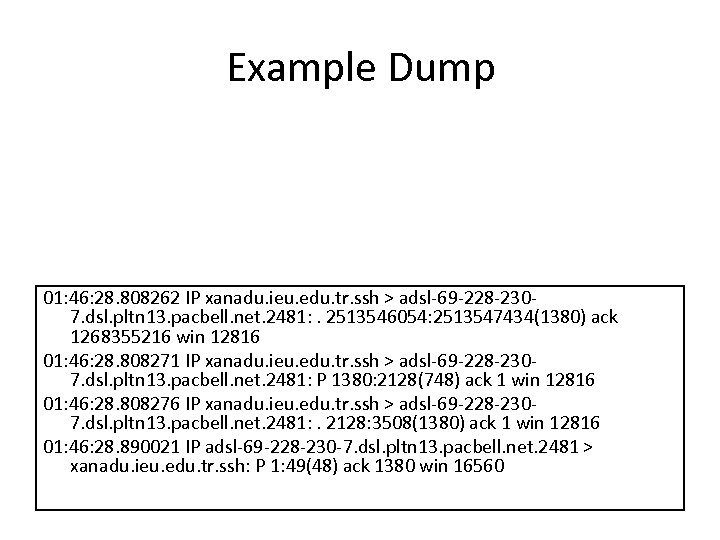 Example Dump 01: 46: 28. 808262 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: . 2513546054: 2513547434(1380) ack 1268355216 win 12816 01: 46: 28. 808271 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: P 1380: 2128(748) ack 1 win 12816 01: 46: 28. 808276 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: . 2128: 3508(1380) ack 1 win 12816 01: 46: 28. 890021 IP adsl-69 -228 -230 -7. dsl. pltn 13. pacbell. net. 2481 > xanadu. ieu. edu. tr. ssh: P 1: 49(48) ack 1380 win 16560
Example Dump 01: 46: 28. 808262 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: . 2513546054: 2513547434(1380) ack 1268355216 win 12816 01: 46: 28. 808271 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: P 1380: 2128(748) ack 1 win 12816 01: 46: 28. 808276 IP xanadu. ieu. edu. tr. ssh > adsl-69 -228 -2307. dsl. pltn 13. pacbell. net. 2481: . 2128: 3508(1380) ack 1 win 12816 01: 46: 28. 890021 IP adsl-69 -228 -230 -7. dsl. pltn 13. pacbell. net. 2481 > xanadu. ieu. edu. tr. ssh: P 1: 49(48) ack 1380 win 16560
 Closer look at a tcpdump line ? 01: 46: 28. 808262 IP xanadu. ieu. edu. tr. ssh> adsl-69 -228 -230 -7. dsl. pltn 13. pacbell. net. 2481. : 2513546054: 2513547434(1380) ack 1268355216 win 12816
Closer look at a tcpdump line ? 01: 46: 28. 808262 IP xanadu. ieu. edu. tr. ssh> adsl-69 -228 -230 -7. dsl. pltn 13. pacbell. net. 2481. : 2513546054: 2513547434(1380) ack 1268355216 win 12816
 Command line use
Command line use
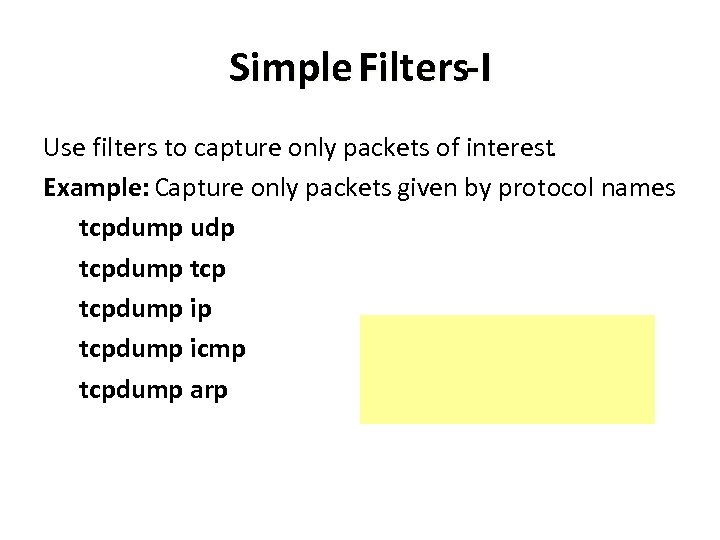 Simple Filters-I Use filters to capture only packets of interest. Example: Capture only packets given by protocol names tcpdump udp tcpdump ip tcpdump icmp tcpdump arp
Simple Filters-I Use filters to capture only packets of interest. Example: Capture only packets given by protocol names tcpdump udp tcpdump ip tcpdump icmp tcpdump arp
 Filters-II
Filters-II
 Filters -III
Filters -III
 Writing Filters
Writing Filters
 Combining Filters Options
Combining Filters Options
 Some Useful Options
Some Useful Options
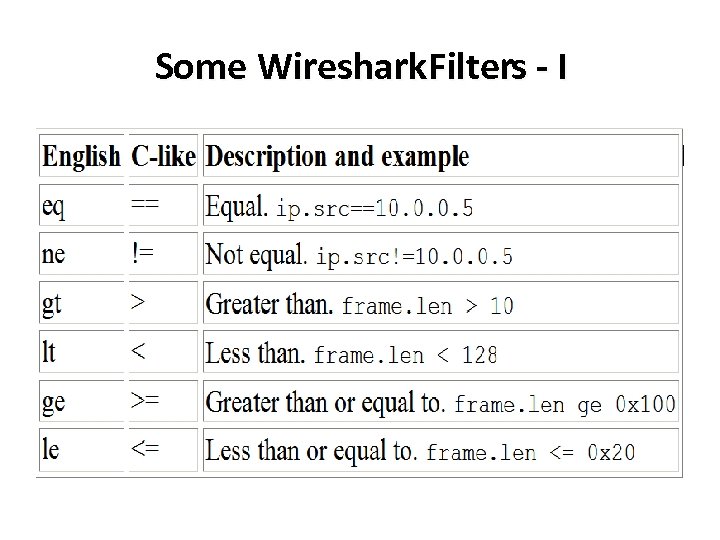 Some Wireshark. Filters - I
Some Wireshark. Filters - I
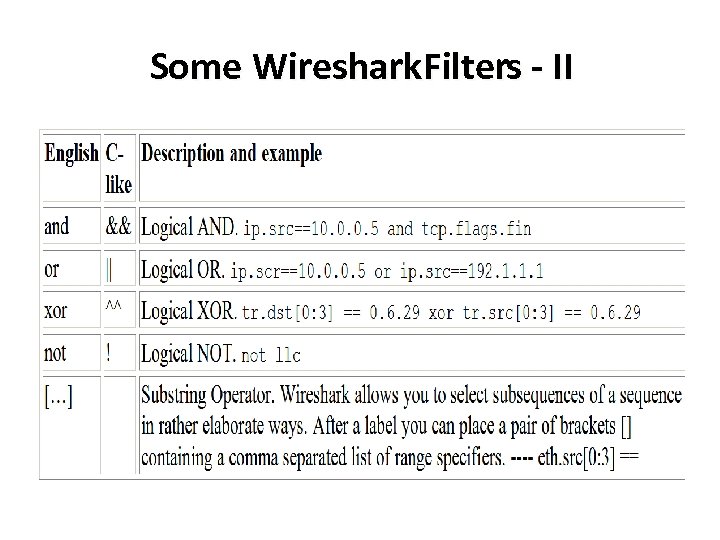 Some Wireshark. Filters - II
Some Wireshark. Filters - II
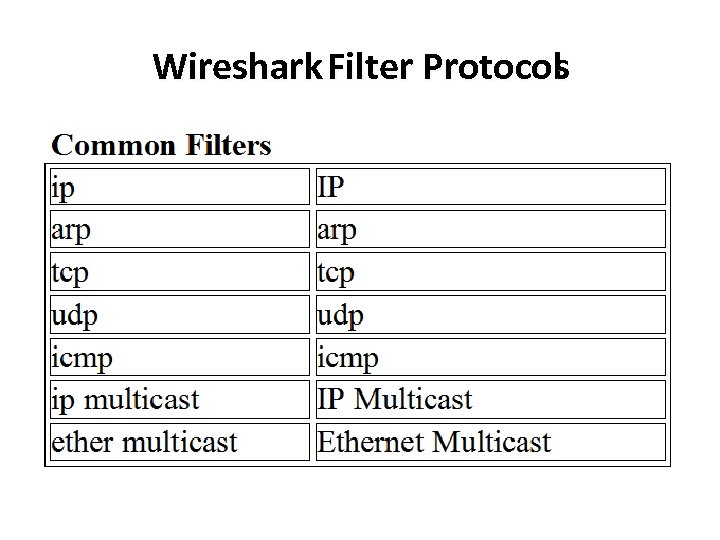 Wireshark Filter Protocol s
Wireshark Filter Protocol s
 Wireshark IP Filters
Wireshark IP Filters
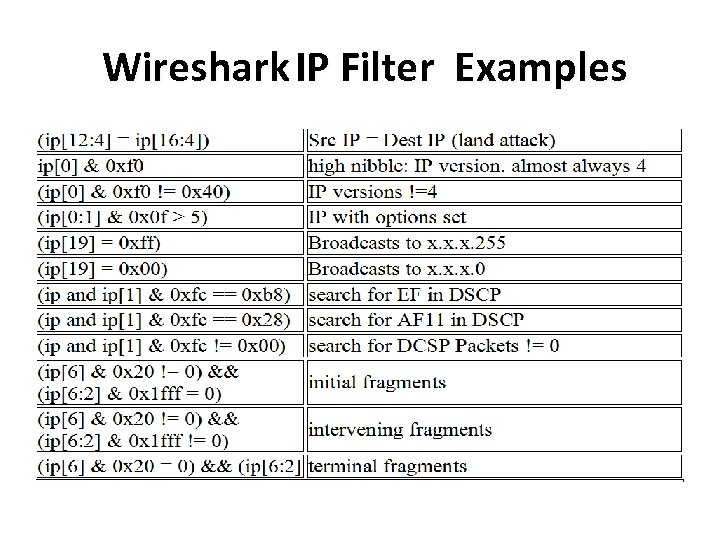 Wireshark IP Filter Examples
Wireshark IP Filter Examples
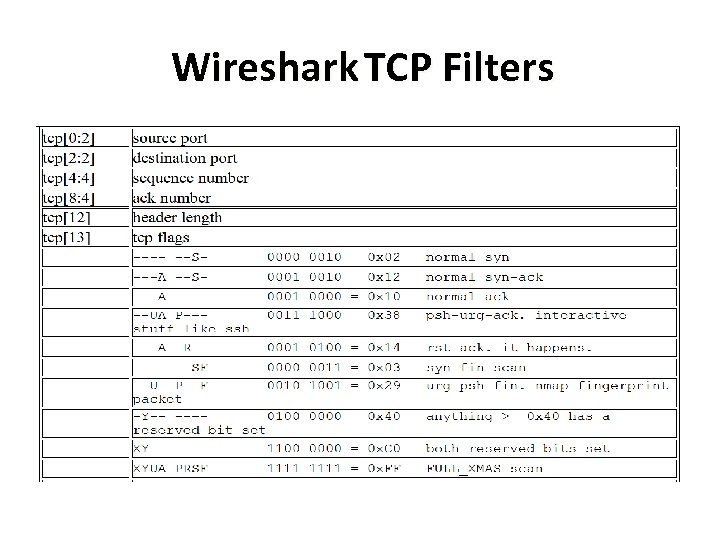 Wireshark TCP Filters
Wireshark TCP Filters
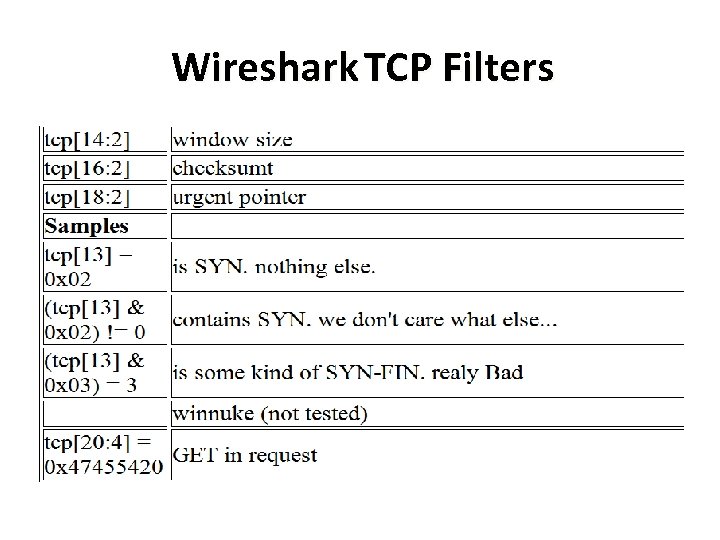 Wireshark TCP Filters
Wireshark TCP Filters
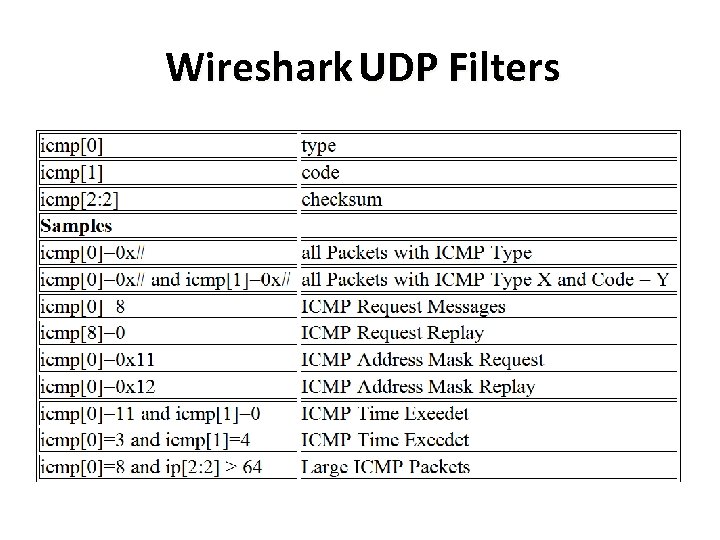 Wireshark UDP Filters
Wireshark UDP Filters
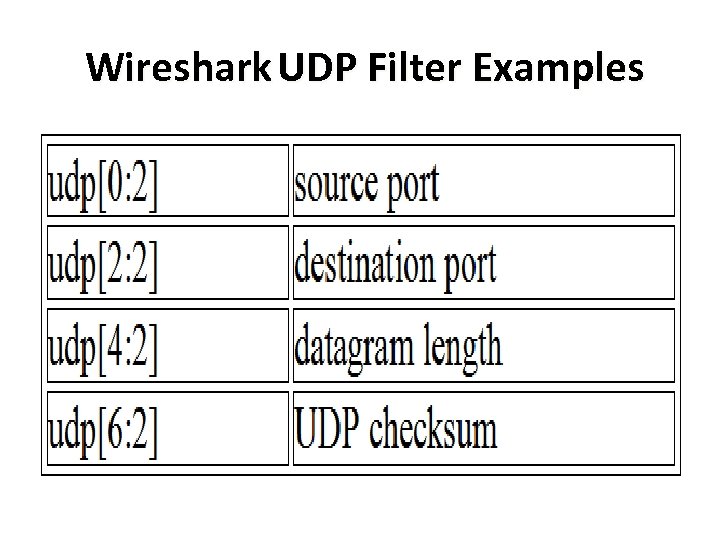 Wireshark UDP Filter Examples
Wireshark UDP Filter Examples
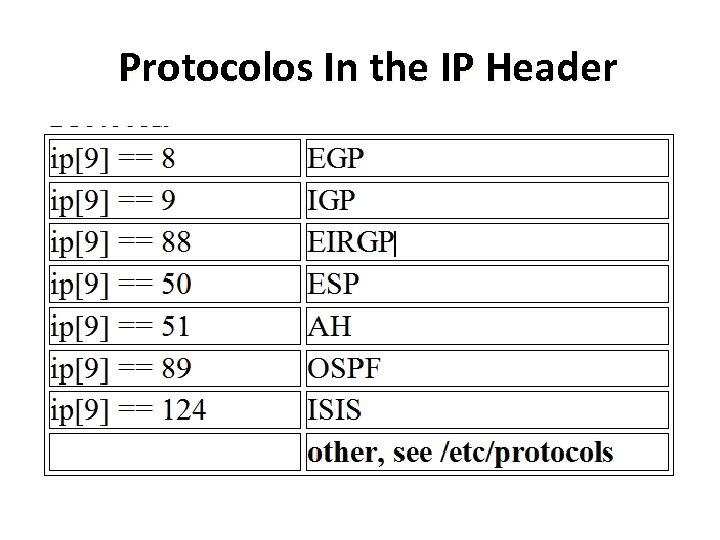 Protocolos In the IP Header
Protocolos In the IP Header
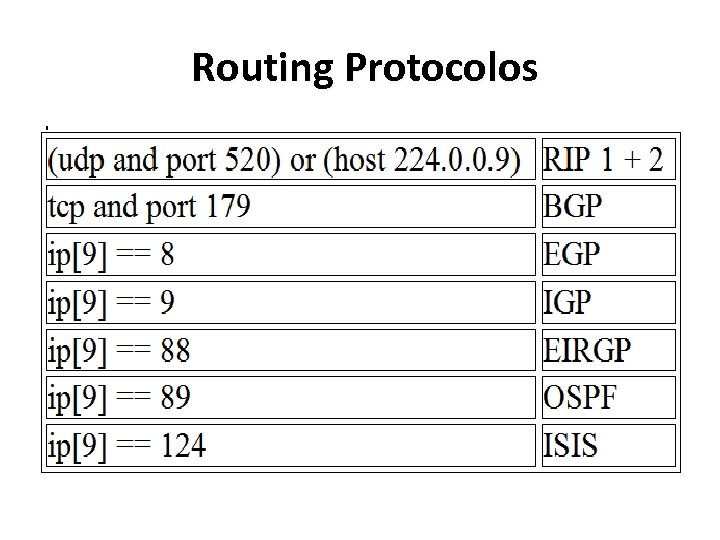 Routing Protocolos
Routing Protocolos
 More on Scanning
More on Scanning
 Determining if system is alive - Purpose
Determining if system is alive - Purpose
 ARP Host discovery - 1
ARP Host discovery - 1
 ARP Host discovery - 2
ARP Host discovery - 2
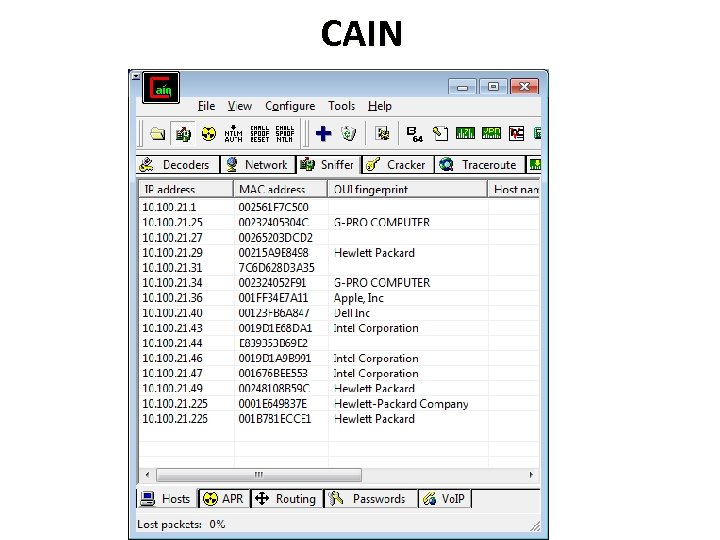 CAIN
CAIN
 ICMP Host discovery - 1
ICMP Host discovery - 1
 ICMP Host discovery - 2
ICMP Host discovery - 2
 Network discovery tools - 1
Network discovery tools - 1
 Network discovery tools - 2
Network discovery tools - 2
 TCP/UDP Host discovery - 1 - Especially useful when ICMP responses are limited - Servers provide services over network
TCP/UDP Host discovery - 1 - Especially useful when ICMP responses are limited - Servers provide services over network
 TCP/UDP Host discovery - 2
TCP/UDP Host discovery - 2
 Determining services that are up
Determining services that are up
 Scan Types - 1 - TCP connect scan
Scan Types - 1 - TCP connect scan
 Scan Types - 2
Scan Types - 2
 Scan Types - 3
Scan Types - 3
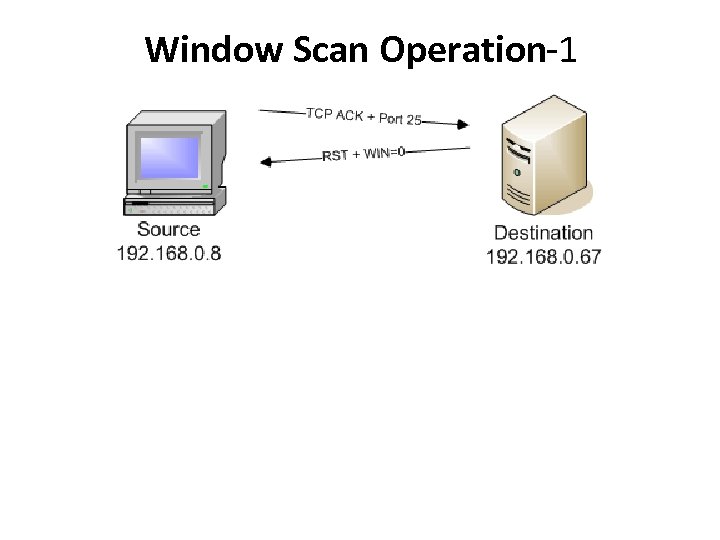 Window Scan Operation-1
Window Scan Operation-1
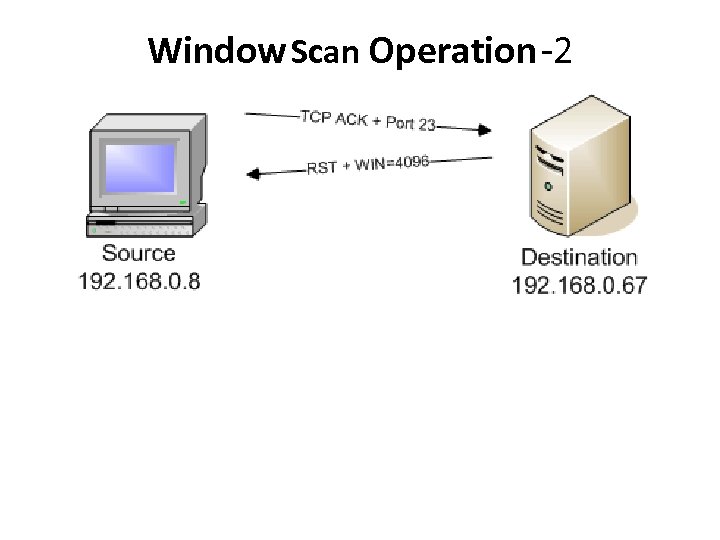 Window Scan Operation -2
Window Scan Operation -2
 Identifying Services - 1
Identifying Services - 1
 Identifying Services - 2
Identifying Services - 2
 Detecting the OS - 1
Detecting the OS - 1
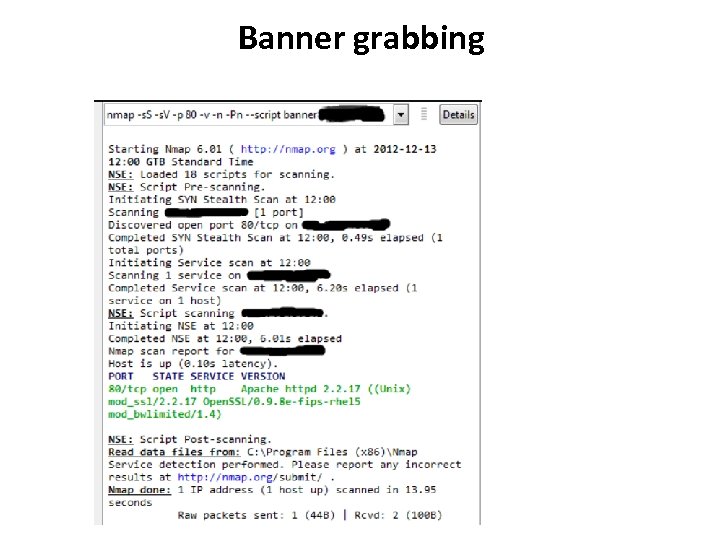 Banner grabbing
Banner grabbing
 Detecting the OS - 2
Detecting the OS - 2
 Detecting the OS - 3
Detecting the OS - 3
 Detecting the OS - 4
Detecting the OS - 4


