f7c6a215a09e98efee2d9a90c4be2e91.ppt
- Количество слайдов: 31

OZ Global Software, Inc. Bsafe Presentation 1

Company Vision To become the global security & monitoring solutions market leader on IBM platforms: IBM System i 5 IBM z. Series (Midrange) (Mainframe) Windows/UNIX Servers Management through One Windows like Management Console 2
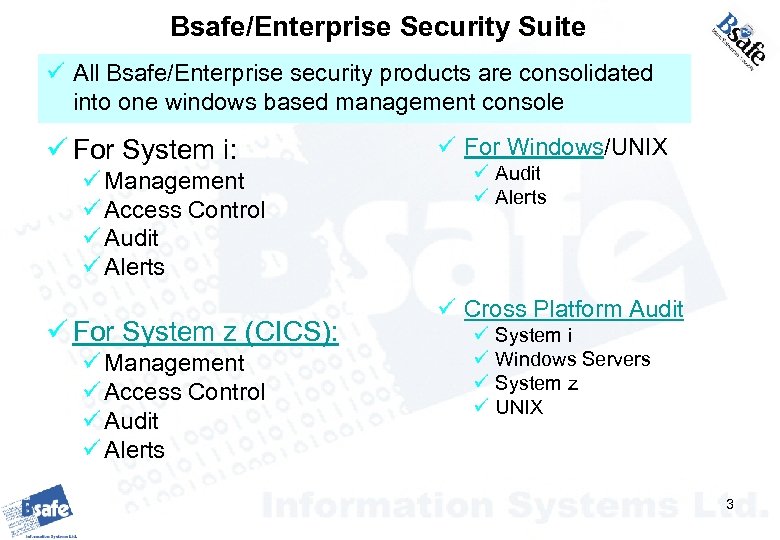
Bsafe/Enterprise Security Suite ü All Bsafe/Enterprise security products are consolidated into one windows based management console ü For System i: ü Management ü Access Control ü Audit ü Alerts ü For System z (CICS): ü Management ü Access Control ü Audit ü Alerts ü For Windows/UNIX ü Audit ü Alerts ü Cross Platform Audit ü ü System i Windows Servers System z UNIX 3

Bsafe Company Profile ü Founded in 1983 ü Locations: New Jersey, Toronto, Israel ü Over 20 years of experience developing security solutions for IBM System i 5/z. Series ü 80 resellers in 50 countries ü Global supplier agreement with IBM ü Few hundred customers incl. Fortune 500 companies 4

Sample Customers 5

The Challenges of Regulatory Compliance To be compliant, Security Officers must quantify that: Users with out a demonstrable need to access data should be prevented from accessing such data. A clear recognizable audit trail exists for transactions. A real-time intrusion alerting mechanism has been implemented. 6

The Problem The OS/400 was architected before the advent of PC connectivity. Therefore, it can not inherently track or secure all of a PC user’s transactions without additional assistance. Without such assistance a user is able to access the i. Series through the network, change or delete any data he wants without being detected 7
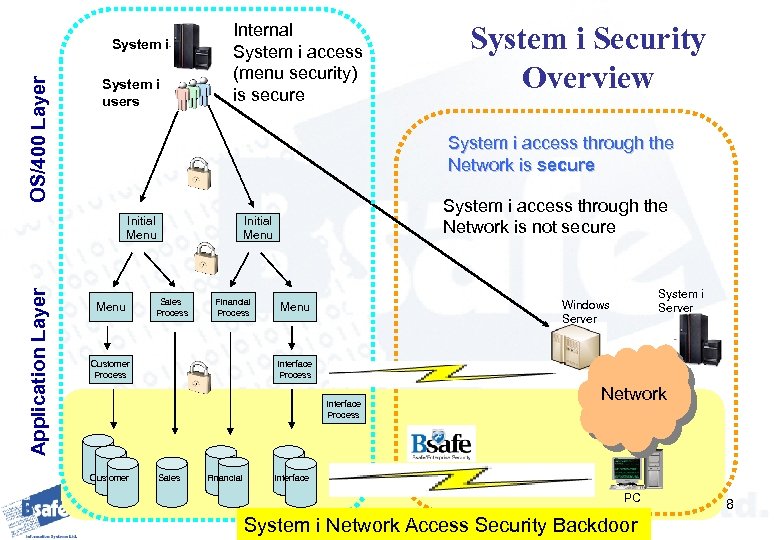
OS/400 Layer System i users Internal System i access (menu security) is secure System i access through the Network is secure Initial Menu Application Layer System i Security Overview Menu System i access through the Network is not secure Initial Menu Sales Process Financial Process Customer Process Interface Process Customer System i Server Windows Server Menu Sales Financial Network Interface PC System i Network Access Security Backdoor 8

System i Vulnerability System i does not differentiate if a user accesses through the network or through OS 400 internally For OS 400 internal access there are tools available to restrict access where required For access through the network this is not the situation as we can see in the following examples 9
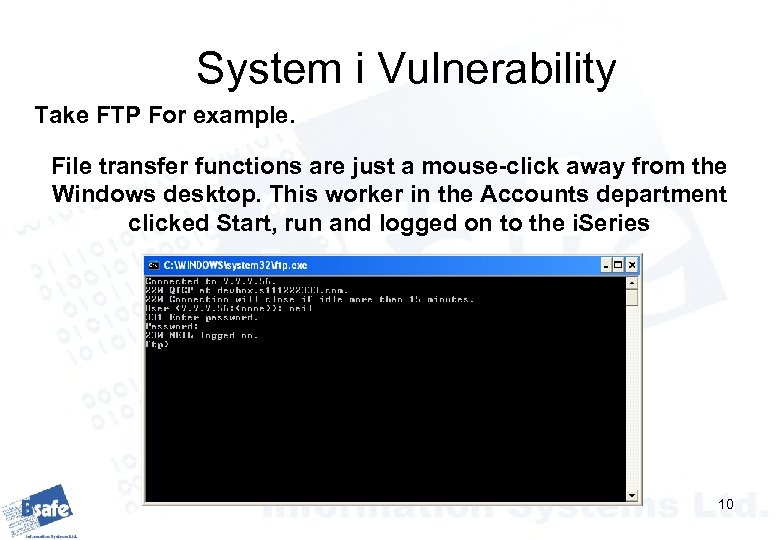
System i Vulnerability Take FTP For example. File transfer functions are just a mouse-click away from the Windows desktop. This worker in the Accounts department clicked Start, run and logged on to the i. Series 10
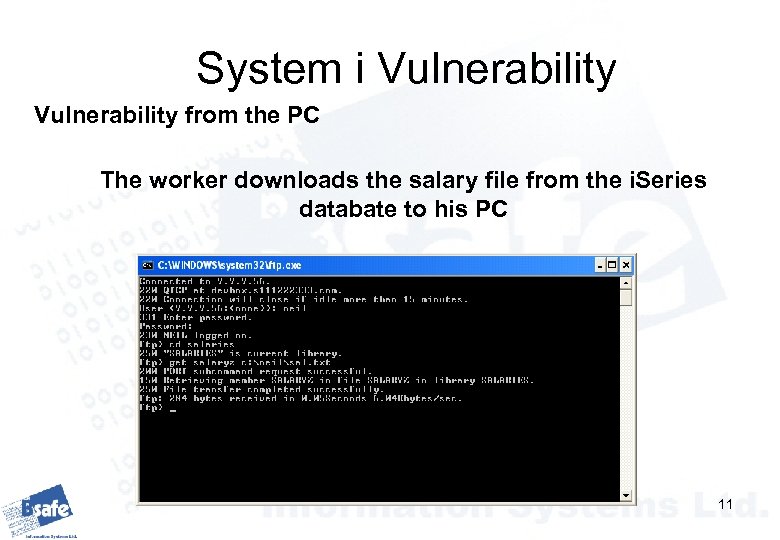
System i Vulnerability from the PC The worker downloads the salary file from the i. Series databate to his PC 11
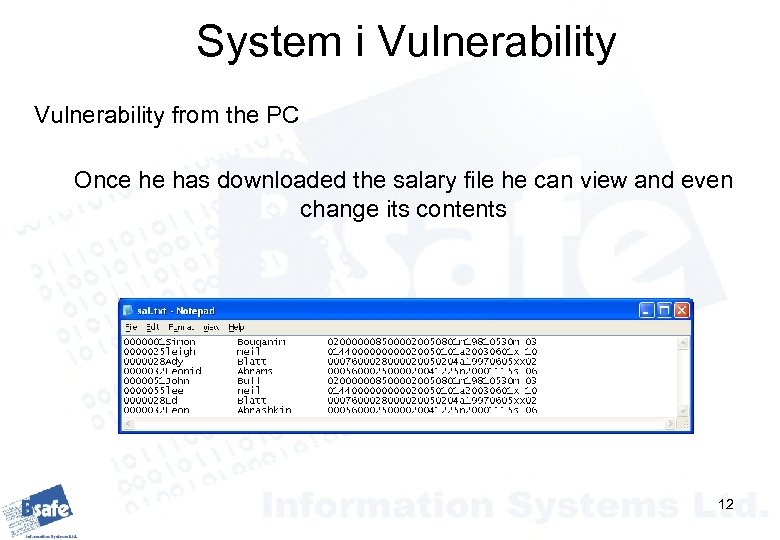
System i Vulnerability from the PC Once he has downloaded the salary file he can view and even change its contents 12
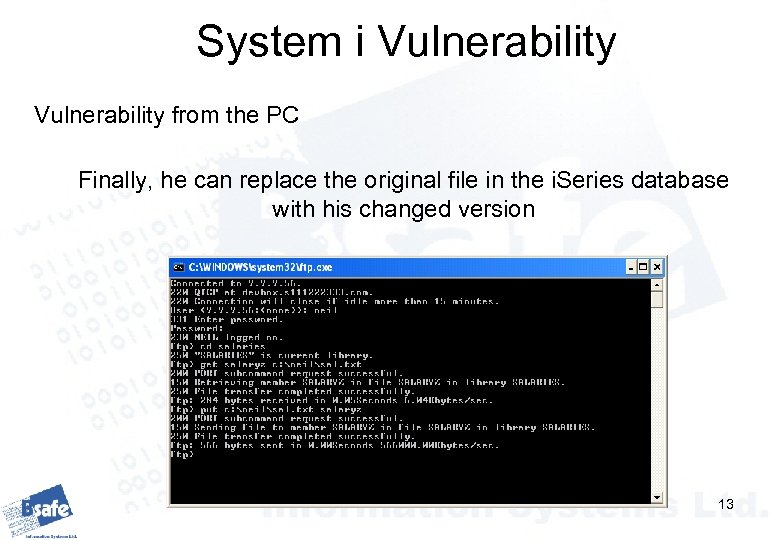
System i Vulnerability from the PC Finally, he can replace the original file in the i. Series database with his changed version 13
System i Vulnerability Another example… Ever heard of the IBM Operations Navigator? It provides many tools for accessing the i. Series from a PC 14
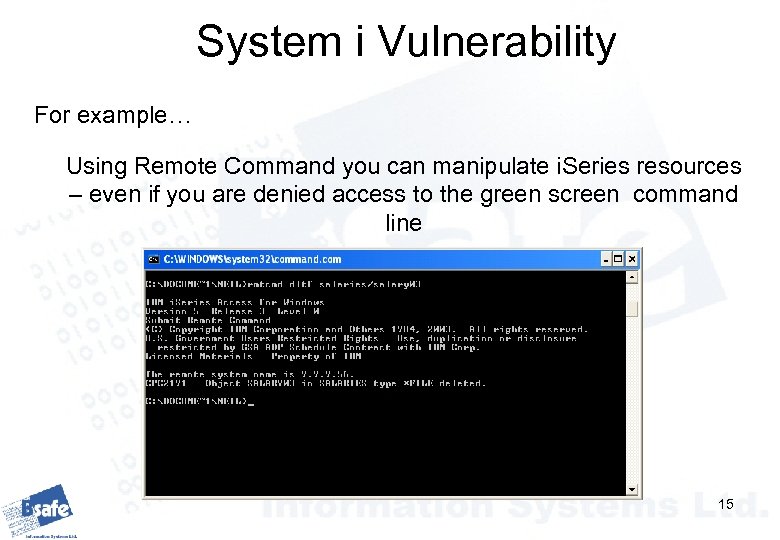
System i Vulnerability For example… Using Remote Command you can manipulate i. Series resources – even if you are denied access to the green screen command line 15
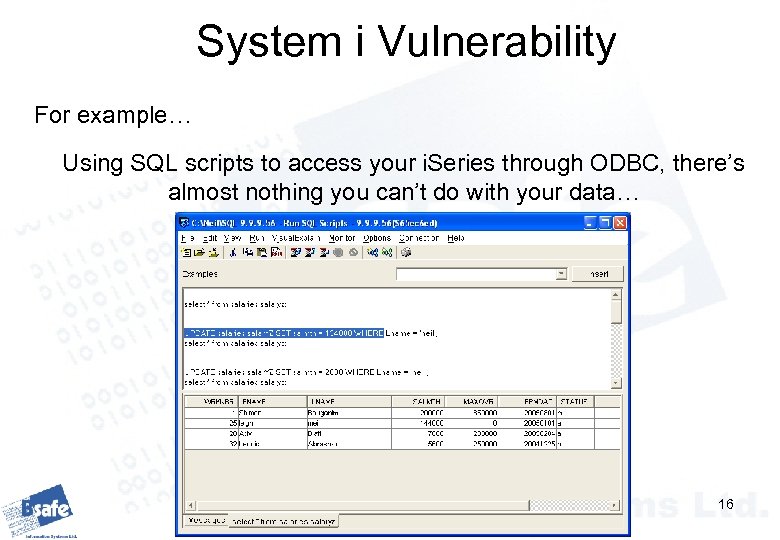
System i Vulnerability For example… Using SQL scripts to access your i. Series through ODBC, there’s almost nothing you can’t do with your data… 16
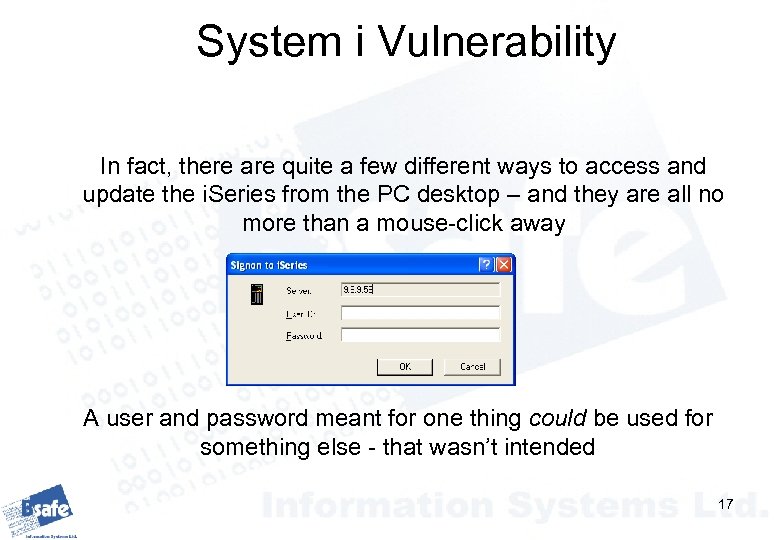
System i Vulnerability In fact, there are quite a few different ways to access and update the i. Series from the PC desktop – and they are all no more than a mouse-click away A user and password meant for one thing could be used for something else - that wasn’t intended 17

What Doesn’t Get Logged Earlier we saw how easily users can download sensitive files to their PCs via FTP The system journal doesn’t log FTP actions at all If the file is already journaled to a file journal it will log the opening of the file, but not the results of the FTP operations This is what you get… 18
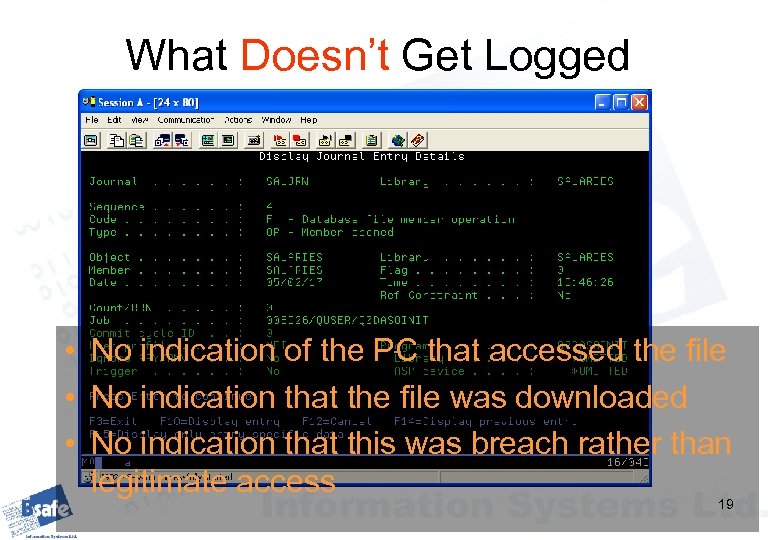
What Doesn’t Get Logged • No indication of the PC that accessed the file • No indication that the file was downloaded • No indication that this was breach rather than legitimate access 19

What Doesn’t Get Logged We saw also how easily users can update data via ODBC The system journal doesn’t log this action either If the file is journaled to a file journal it will log the record images, but little more This is what you get… 20
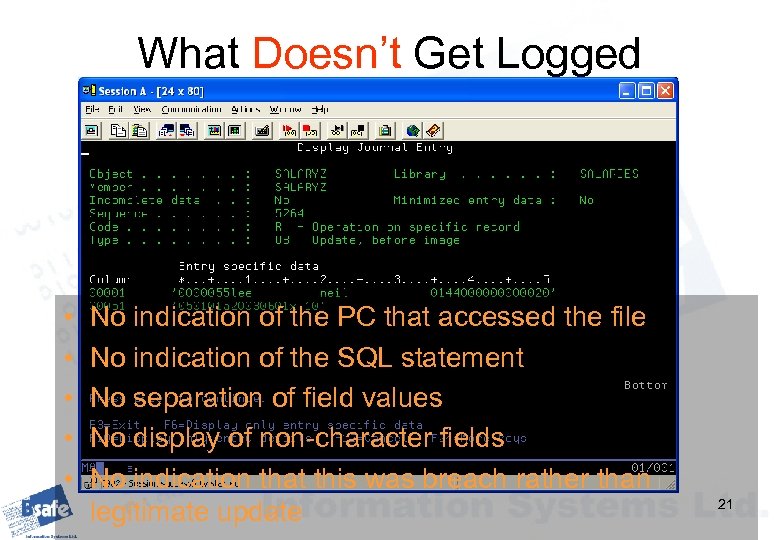
What Doesn’t Get Logged • • • No indication of the PC that accessed the file No indication of the SQL statement No separation of field values No display of non-character fields No indication that this was breach rather than legitimate update 21

The Challenges To be compliant, Security Officers must quantify that: Users with out a demonstrable need to access data should be prevented from accessing such data. A clear recognizable audit trail exists for transactions. A real-time intrusion alerting mechanism has been implemented. 22

The Result Companies will not be able to attain compliance without a vendor-supplied or inhouse created solution. 23

The Solution is Bsafe/Enterprise Security Bsafe enables Security Administrators and Auditors to: • Regulate (secure) users’ activities • Monitor users’ activities • Automate the creation of clear and concise audit reports • Receive real-time security and system related alerts Designed to be managed through Windows like Management Console 24
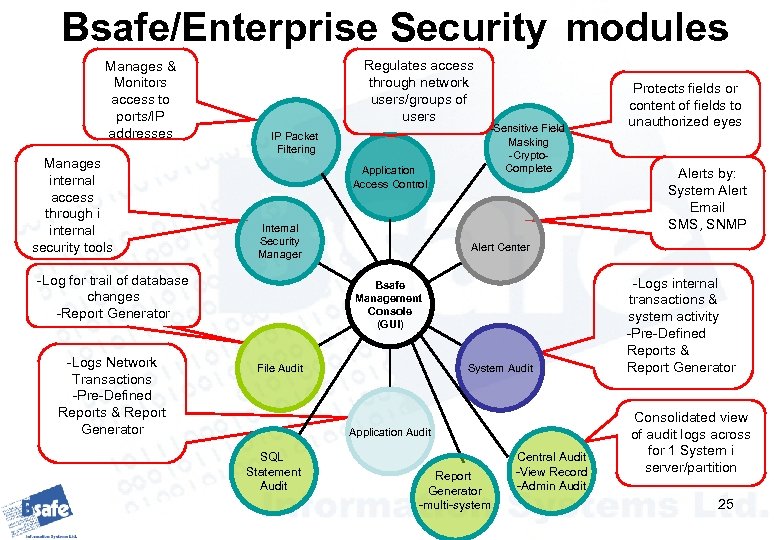
Bsafe/Enterprise Security modules Manages & Monitors access to ports/IP addresses Manages internal access through i internal security tools Regulates access through network users/groups of users IP Packet Filtering Application Access Control Internal Security Manager -Log for trail of database changes -Report Generator -Logs Network Transactions -Pre-Defined Reports & Report Generator -Sensitive Field Masking -Crypto. Complete Alerts by: System Alert Email SMS, SNMP Alert Center Bsafe Management Console (GUI) System Audit File Audit Application Audit SQL Statement Audit Protects fields or content of fields to unauthorized eyes Report Generator -multi-system Central Audit -View Record -Admin Audit -Logs internal transactions & system activity -Pre-Defined Reports & Report Generator Consolidated view of audit logs across for 1 System i server/partition 25
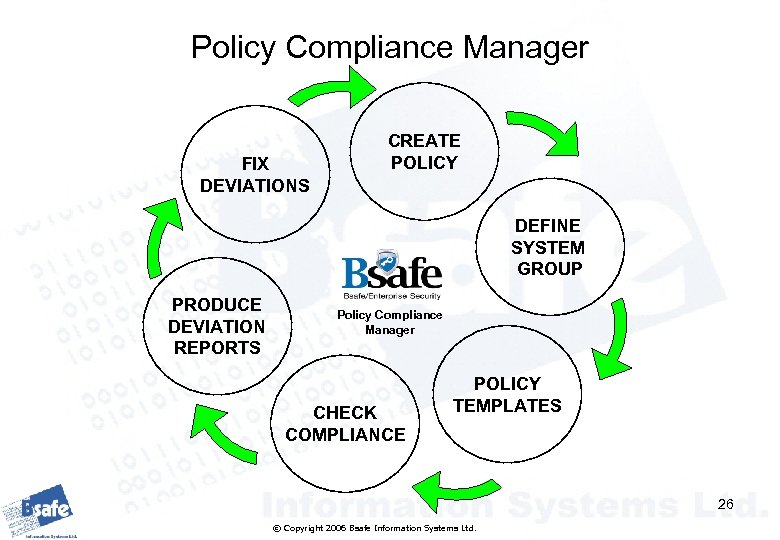
Policy Compliance Manager FIX DEVIATIONS CREATE POLICY DEFINE SYSTEM GROUP PRODUCE DEVIATION REPORTS Policy Compliance Manager CHECK COMPLIANCE POLICY TEMPLATES 26 © Copyright 2006 Bsafe Information Systems Ltd.
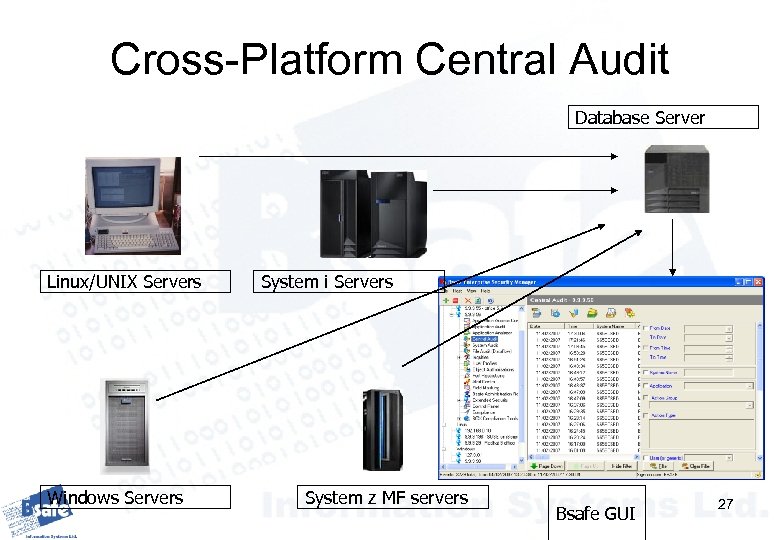
Cross-Platform Central Audit Database Server Linux/UNIX Servers Windows Servers System i Servers System z MF servers Bsafe GUI 27
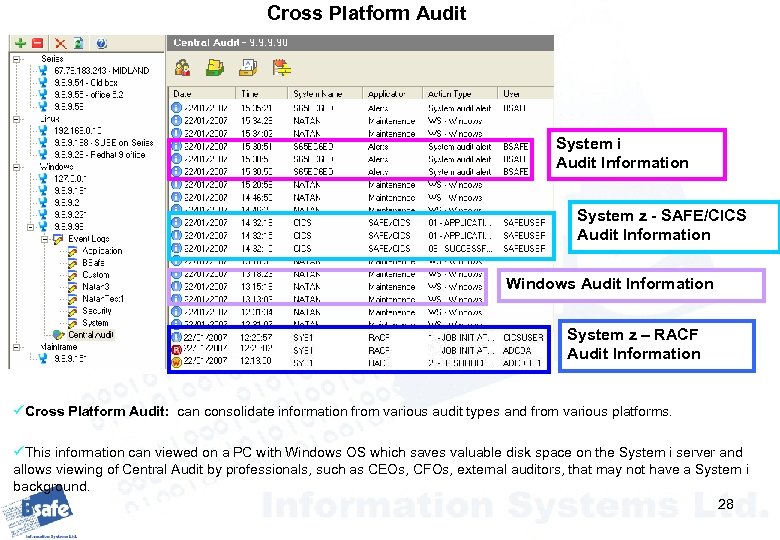
Cross Platform Audit System i Audit Information System z - SAFE/CICS Audit Information Windows Audit Information System z – RACF Audit Information üCross Platform Audit: can consolidate information from various audit types and from various platforms. üThis information can viewed on a PC with Windows OS which saves valuable disk space on the System i server and allows viewing of Central Audit by professionals, such as CEOs, CFOs, external auditors, that may not have a System i background. 28
Benefits ü Focus on customers which maintain System i and/or System z as their mission critical systems ü Comprehensive operating system and database security & monitoring suite ü Single console enabling central management for multiple server platforms ü Comprehensive Cross Platform Audit Trail ü GUI enabling green screen – empowering non-green screen personnel -Freeing up green-screen experts for mission critical tasks ü Highly granular functionality for securing and monitoring IBM platforms 29

Value Proposition ü Peace of Mind - Reduces Exposure – Enhances Security • • • Safeguards assets Reduces time spent on investigating suspicious events Prevents errors and mistakes from doing serious damage to mission critical systems and data ü Facilitates Formulation & Enforcement of Security Policy ü Simplifying Compliance • • Improves compliance with regulations by providing a full audit trail of end-user activity Reduces Auditing Time • Maintains separation of duties ü Automates previous manually conducted operations • • Ease of Use – non-expert can conduct security related- tasks Reduces Systems Management Time 30

Why a product like Bsafe is needed? ü Regulations & industry standards such as “Sarbanes-Oxley” ü Complex environments make security on the i 5 platform difficult to manage (networks, OS, hardware, applications) ü Constant changes in users, systems and the way users access applications ü New risks introduced by external partners, customers & remote employees accessing the i 5 network, using diverse platforms and devices ü Availability of experienced i 5 administrators 31
f7c6a215a09e98efee2d9a90c4be2e91.ppt