e8fab849db2209b3e15bec2f59c2412c.ppt
- Количество слайдов: 13
 OWASP Israel 2010 Conference Ofer Maor CTO, Hacktics Chairman, OWASP Israel Sep 2010 http: //www. webappsec. org/ Copyright © 2009 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the Creative Commons Attribution-Share. Alike 2. 5 License. To view this license, visit http: //creativecommons. org/licenses/by-sa/2. 5/ The OWASP Foundation http: //www. owasp. org/
OWASP Israel 2010 Conference Ofer Maor CTO, Hacktics Chairman, OWASP Israel Sep 2010 http: //www. webappsec. org/ Copyright © 2009 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the Creative Commons Attribution-Share. Alike 2. 5 License. To view this license, visit http: //creativecommons. org/licenses/by-sa/2. 5/ The OWASP Foundation http: //www. owasp. org/
 OWASP Israel 2010 Conference
OWASP Israel 2010 Conference
 OWASP World OWASP is a worldwide free and open community focused on improving the security of application software. Our mission is to make application security visible so that people and organizations can make informed decisions about application security risks. Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. The OWASP Foundation is a 501 c 3 not -for-profit charitable organization that ensures the ongoing availability and support for our work. OWASP Israel – Sep 2010
OWASP World OWASP is a worldwide free and open community focused on improving the security of application software. Our mission is to make application security visible so that people and organizations can make informed decisions about application security risks. Everyone is free to participate in OWASP and all of our materials are available under a free and open software license. The OWASP Foundation is a 501 c 3 not -for-profit charitable organization that ensures the ongoing availability and support for our work. OWASP Israel – Sep 2010
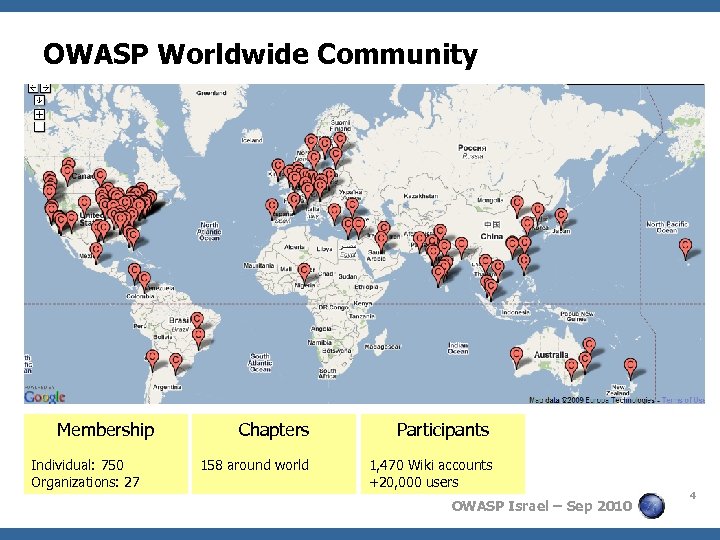 OWASP Worldwide Community Membership Individual: 750 Organizations: 27 Chapters Participants 158 around world 1, 470 Wiki accounts +20, 000 users OWASP Israel – Sep 2010 4
OWASP Worldwide Community Membership Individual: 750 Organizations: 27 Chapters Participants 158 around world 1, 470 Wiki accounts +20, 000 users OWASP Israel – Sep 2010 4
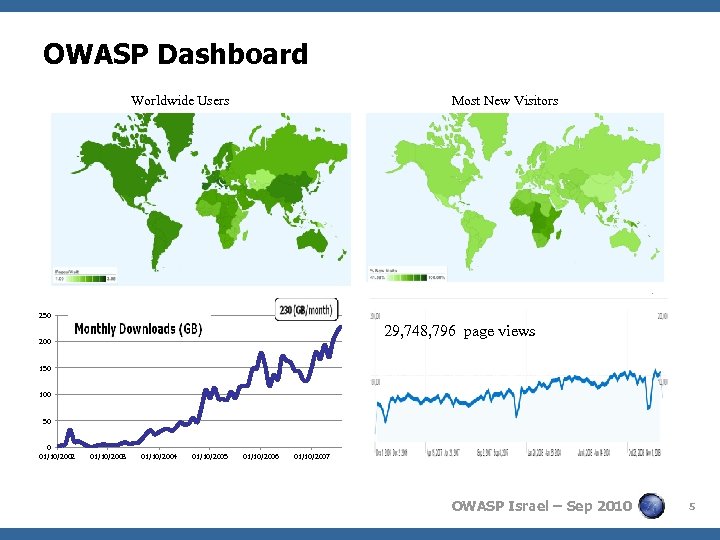 OWASP Dashboard Worldwide Users Most New Visitors 250 29, 748, 796 page views 200 150 100 50 0 01/10/2002 01/10/2003 01/10/2004 01/10/2005 01/10/2006 01/10/2007 OWASP Israel – Sep 2010 5
OWASP Dashboard Worldwide Users Most New Visitors 250 29, 748, 796 page views 200 150 100 50 0 01/10/2002 01/10/2003 01/10/2004 01/10/2005 01/10/2006 01/10/2007 OWASP Israel – Sep 2010 5
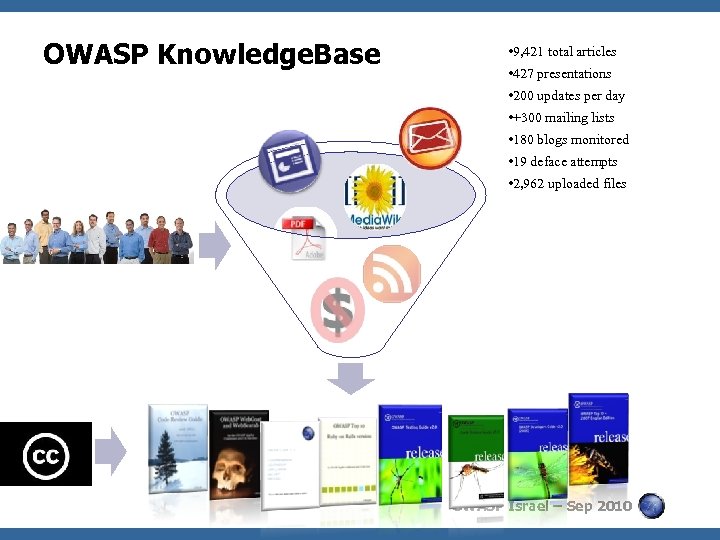 OWASP Knowledge. Base • 9, 421 total articles • 427 presentations • 200 updates per day • +300 mailing lists • 180 blogs monitored • 19 deface attempts • 2, 962 uploaded files OWASP Israel – Sep 2010
OWASP Knowledge. Base • 9, 421 total articles • 427 presentations • 200 updates per day • +300 mailing lists • 180 blogs monitored • 19 deface attempts • 2, 962 uploaded files OWASP Israel – Sep 2010
 OWASP Top 10 Critical Vulnerabilities - 2010 A 1: Injection A 5: Cross Site Request Forgery (CSRF) A 2: Cross Site Scripting (XSS) A 3: Broken Authentication and Session Management A 4: Insecure Direct Object Reference A 6: Security Misconfiguration A 7: Failure to Restrict URL Access A 8: Unvalidated Redirects and Forwards A 9: Insecure Cryptographic Storage A 10: Insufficient Transport Layer Protection www. owasp. org/index. php/Category: OWASP_Top_Ten_Project OWASP Israel – Sep 2010 7
OWASP Top 10 Critical Vulnerabilities - 2010 A 1: Injection A 5: Cross Site Request Forgery (CSRF) A 2: Cross Site Scripting (XSS) A 3: Broken Authentication and Session Management A 4: Insecure Direct Object Reference A 6: Security Misconfiguration A 7: Failure to Restrict URL Access A 8: Unvalidated Redirects and Forwards A 9: Insecure Cryptographic Storage A 10: Insufficient Transport Layer Protection www. owasp. org/index. php/Category: OWASP_Top_Ten_Project OWASP Israel – Sep 2010 7
 OWASP App. Sec Guides
OWASP App. Sec Guides
 Many Other Projects…
Many Other Projects…
 About OWASP Israel
About OWASP Israel
 What do we Need?
What do we Need?
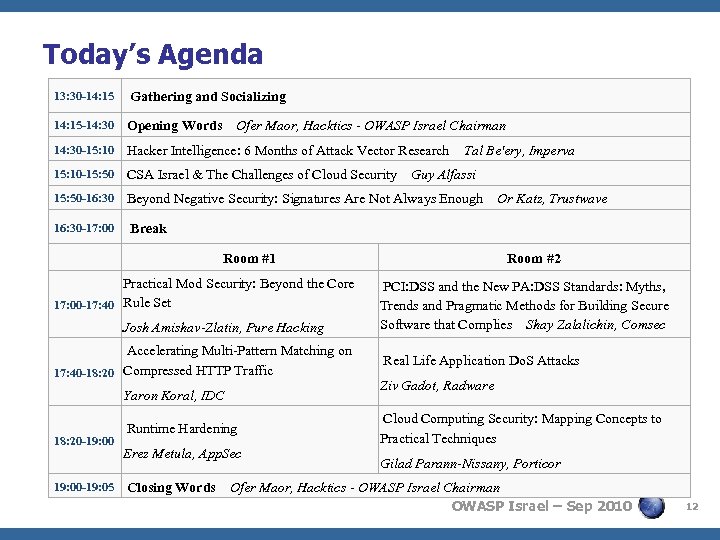 Today’s Agenda 13: 30 -14: 15 Gathering and Socializing 14: 15 -14: 30 Opening Words Ofer Maor, Hacktics - OWASP Israel Chairman 14: 30 -15: 10 Hacker Intelligence: 6 Months of Attack Vector Research Tal Be'ery, Imperva 15: 10 -15: 50 CSA Israel & The Challenges of Cloud Security Guy Alfassi 15: 50 -16: 30 Beyond Negative Security: Signatures Are Not Always Enough Or Katz, Trustwave 16: 30 -17: 00 Break Room #1 Practical Mod Security: Beyond the Core 17: 00 -17: 40 Rule Set Josh Amishav-Zlatin, Pure Hacking Accelerating Multi-Pattern Matching on 17: 40 -18: 20 Compressed HTTP Traffic Yaron Koral, IDC 18: 20 -19: 00 Runtime Hardening Erez Metula, App. Sec Room #2 PCI: DSS and the New PA: DSS Standards: Myths, Trends and Pragmatic Methods for Building Secure Software that Complies Shay Zalalichin, Comsec Real Life Application Do. S Attacks Ziv Gadot, Radware Cloud Computing Security: Mapping Concepts to Practical Techniques Gilad Parann-Nissany, Porticor 19: 00 -19: 05 Closing Words Ofer Maor, Hacktics - OWASP Israel Chairman OWASP Israel – Sep 2010 12
Today’s Agenda 13: 30 -14: 15 Gathering and Socializing 14: 15 -14: 30 Opening Words Ofer Maor, Hacktics - OWASP Israel Chairman 14: 30 -15: 10 Hacker Intelligence: 6 Months of Attack Vector Research Tal Be'ery, Imperva 15: 10 -15: 50 CSA Israel & The Challenges of Cloud Security Guy Alfassi 15: 50 -16: 30 Beyond Negative Security: Signatures Are Not Always Enough Or Katz, Trustwave 16: 30 -17: 00 Break Room #1 Practical Mod Security: Beyond the Core 17: 00 -17: 40 Rule Set Josh Amishav-Zlatin, Pure Hacking Accelerating Multi-Pattern Matching on 17: 40 -18: 20 Compressed HTTP Traffic Yaron Koral, IDC 18: 20 -19: 00 Runtime Hardening Erez Metula, App. Sec Room #2 PCI: DSS and the New PA: DSS Standards: Myths, Trends and Pragmatic Methods for Building Secure Software that Complies Shay Zalalichin, Comsec Real Life Application Do. S Attacks Ziv Gadot, Radware Cloud Computing Security: Mapping Concepts to Practical Techniques Gilad Parann-Nissany, Porticor 19: 00 -19: 05 Closing Words Ofer Maor, Hacktics - OWASP Israel Chairman OWASP Israel – Sep 2010 12
 Thank You! Questions? OWASP Israel – Sep 2010 13
Thank You! Questions? OWASP Israel – Sep 2010 13


