454f776218a814701069021a26132c25.ppt
- Количество слайдов: 47
 Overview of Security Standards in the Grid CSE 225 High Performance and Computational Grids Spring 2000 Prepared By kwalsh@ucsd. edu
Overview of Security Standards in the Grid CSE 225 High Performance and Computational Grids Spring 2000 Prepared By kwalsh@ucsd. edu
 Objectives: • Gain familiarity with computer and network security standards. • Gain understanding of security requirements in Grid environments. • Gain understanding of some standards based security technologies present in Grid environments. • Learn about various Grid security models and system approaches to security. • Learn about some test bed implementations of security enabled Grid projects.
Objectives: • Gain familiarity with computer and network security standards. • Gain understanding of security requirements in Grid environments. • Gain understanding of some standards based security technologies present in Grid environments. • Learn about various Grid security models and system approaches to security. • Learn about some test bed implementations of security enabled Grid projects.
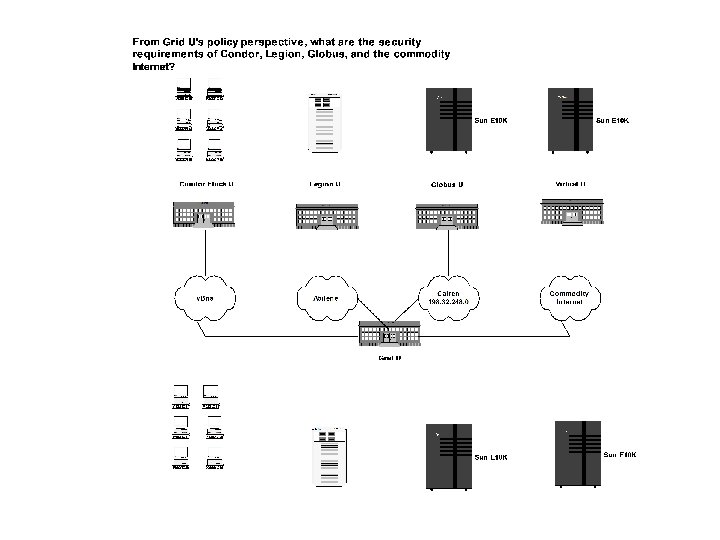
 Security Domains • Intradomain - internal to a given location or single organization. Contained security boundary. • Interdomain - encompasses two or more locations or organizations. Agreed on security boundaries and protocols between organizations.
Security Domains • Intradomain - internal to a given location or single organization. Contained security boundary. • Interdomain - encompasses two or more locations or organizations. Agreed on security boundaries and protocols between organizations.
 Security - The Protection of Assets • Prevention: take measure that protect your assets from damage • Detection: take measures that allow you to detect when an asset has been damaged, and who caused the damage. • Reaction: take measures that allow you to recover your assets or recover from damage to your assets.
Security - The Protection of Assets • Prevention: take measure that protect your assets from damage • Detection: take measures that allow you to detect when an asset has been damaged, and who caused the damage. • Reaction: take measures that allow you to recover your assets or recover from damage to your assets.
 Computer Security • Confidentiality: prevention of unauthorized disclosure of information. • Integrity: prevention of unauthorized withholding of information. • Availability: prevention of unauthorized withholding of information or resources.
Computer Security • Confidentiality: prevention of unauthorized disclosure of information. • Integrity: prevention of unauthorized withholding of information. • Availability: prevention of unauthorized withholding of information or resources.
 Network Security (1) • • • Trusted Networks Identification and Authentication Discretionary Access Control Labels and Mandatory Access Control Audit
Network Security (1) • • • Trusted Networks Identification and Authentication Discretionary Access Control Labels and Mandatory Access Control Audit
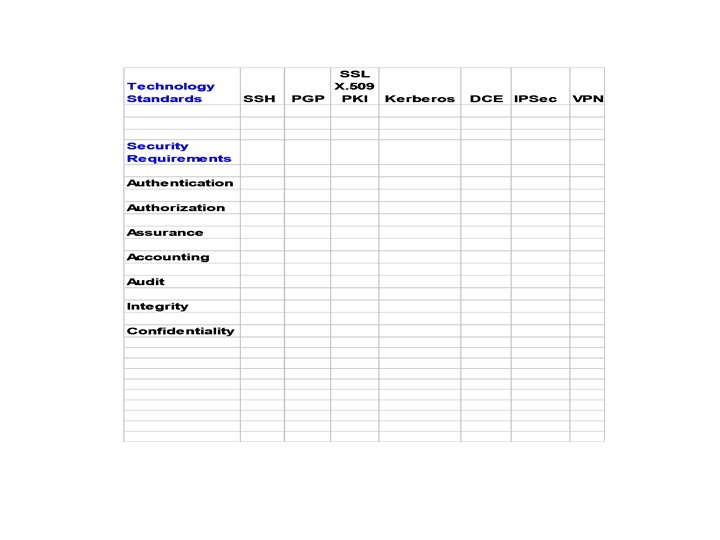
 Technology - Cryptography • • • DES (Data Encryption Standard) DSA (Digital Signature Algorithm) RSA (Rivest, Shamir, and Adelman) Blowfish IDEA (International Data Encryption Algorithm) AES (Advanced Encryption Standard)
Technology - Cryptography • • • DES (Data Encryption Standard) DSA (Digital Signature Algorithm) RSA (Rivest, Shamir, and Adelman) Blowfish IDEA (International Data Encryption Algorithm) AES (Advanced Encryption Standard)
 Technology - SSH (1) • SSH is a packet-based binary protocol that implements a transport layer security mechanism. • Encompasses authentication, key exchange, encryption, and integrity. • TCP/IP is used as the transport usually • Basically an end to end encrypted tunnel • SSH logins the most prevalent between domains.
Technology - SSH (1) • SSH is a packet-based binary protocol that implements a transport layer security mechanism. • Encompasses authentication, key exchange, encryption, and integrity. • TCP/IP is used as the transport usually • Basically an end to end encrypted tunnel • SSH logins the most prevalent between domains.
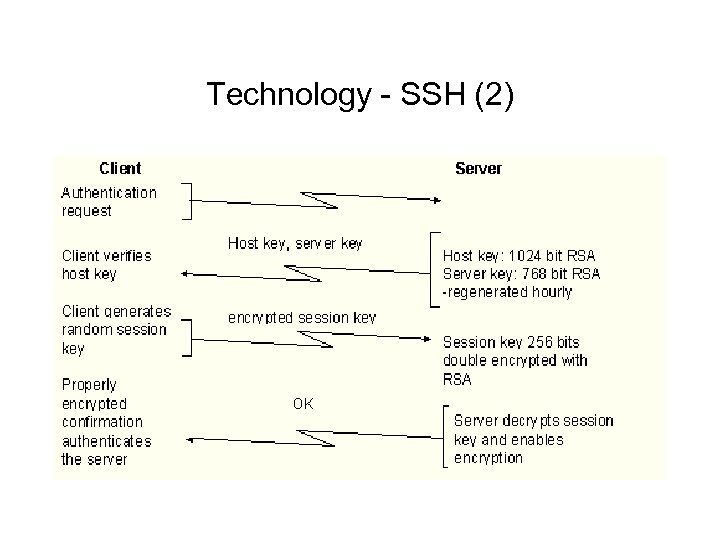 Technology - SSH (2)
Technology - SSH (2)
 Technology - PGP • • Pretty Good Privacy Public Domain Popular for email and email of files PGP user builds key ring of all public keys he has been given. • When message of file received from contact, can decrypt if key is on key ring
Technology - PGP • • Pretty Good Privacy Public Domain Popular for email and email of files PGP user builds key ring of all public keys he has been given. • When message of file received from contact, can decrypt if key is on key ring
 Shortcomings of PGP in distributed systems • Reasonable basis for key management among friends, but once it passes the bounds of direct friends, the credibility becomes strained. • Example – Carol’s key is P 1 signed with P 2 – Alice’s key is P 2 signed with P 4 – Carol’s key is P 1 signed with P 5 • What is the last certificate said Carol’s key is P 3 signed with P 5?
Shortcomings of PGP in distributed systems • Reasonable basis for key management among friends, but once it passes the bounds of direct friends, the credibility becomes strained. • Example – Carol’s key is P 1 signed with P 2 – Alice’s key is P 2 signed with P 4 – Carol’s key is P 1 signed with P 5 • What is the last certificate said Carol’s key is P 3 signed with P 5?
 Kerberos (1) • Supports authentication in distributed systems. • Used for authentication between intelligent processes, client to server tasks or workstation to other hosts. • Basis of Kerberos is central server that provides authenticated tokens, called tickets.
Kerberos (1) • Supports authentication in distributed systems. • Used for authentication between intelligent processes, client to server tasks or workstation to other hosts. • Basis of Kerberos is central server that provides authenticated tokens, called tickets.
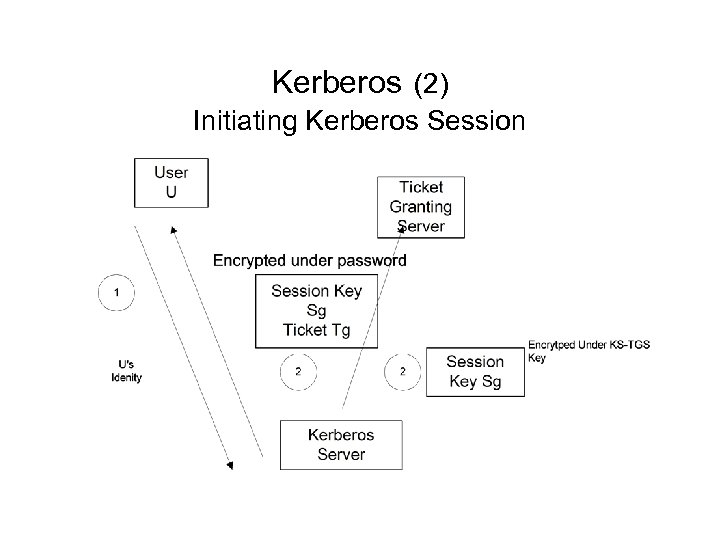 Kerberos (2) Initiating Kerberos Session
Kerberos (2) Initiating Kerberos Session
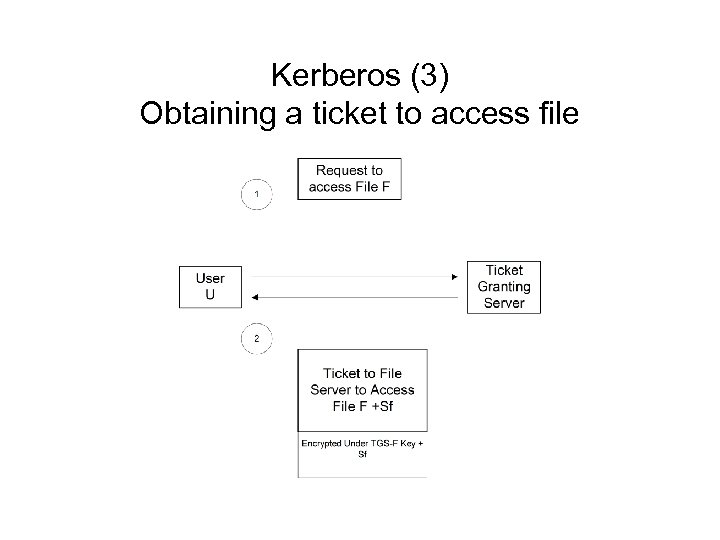 Kerberos (3) Obtaining a ticket to access file
Kerberos (3) Obtaining a ticket to access file
 Kerberos (4) Strengths • • • No password communicated on the network. Cryptographic protection against spoofing. Limited period of validity Time stamps to prevent replay attacks Mutual authentication
Kerberos (4) Strengths • • • No password communicated on the network. Cryptographic protection against spoofing. Limited period of validity Time stamps to prevent replay attacks Mutual authentication
 Kerberos (5) Shortcomings in distributed systems • Requires continuous availability of a trusted ticket granting service. • Authenticity of servers requires a trusted relationship between the ticket granting server and every server. • Requires timely transactions. • Subverted workstation can save and later replay user passwords. • Does not scale well.
Kerberos (5) Shortcomings in distributed systems • Requires continuous availability of a trusted ticket granting service. • Authenticity of servers requires a trusted relationship between the ticket granting server and every server. • Requires timely transactions. • Subverted workstation can save and later replay user passwords. • Does not scale well.
 Public Key Infrastructure (1) • PKI: consists of software and procedures put in place by an organization • Supports the use of Public Keys for authentication and identifying users, services, and confirming digital signatures. • Public keys usually conform to the X. 509 standard for certificates, and usually are based on the RSA public/private key encryption algorithm
Public Key Infrastructure (1) • PKI: consists of software and procedures put in place by an organization • Supports the use of Public Keys for authentication and identifying users, services, and confirming digital signatures. • Public keys usually conform to the X. 509 standard for certificates, and usually are based on the RSA public/private key encryption algorithm
 Public Key Infrastructure (2) Goals • Application enabler • Secure Sign-On – Secure “Single” Sign Security • End-User Transparency • Comprehensive Security
Public Key Infrastructure (2) Goals • Application enabler • Secure Sign-On – Secure “Single” Sign Security • End-User Transparency • Comprehensive Security
 Public Key Infrastructure (3) Components and Services • • • Certification Authority Certificate repository Certificate Revocation Key backup and recovery Automatic key update Key history management Cross-certification Support for non-repudiation Time stamping Client software
Public Key Infrastructure (3) Components and Services • • • Certification Authority Certificate repository Certificate Revocation Key backup and recovery Automatic key update Key history management Cross-certification Support for non-repudiation Time stamping Client software
 Public Key Infrastructure (4) Current Standards Activities • • X. 509 PKIX X. 500 LDAP S/MIME IPsec TLS
Public Key Infrastructure (4) Current Standards Activities • • X. 509 PKIX X. 500 LDAP S/MIME IPsec TLS
 Section Break • Security in Legion and Globus
Section Break • Security in Legion and Globus
 Security in Legion (1) Design Principals • 1 - As in the Hippocratic Oath, do no harm! • 2 - Caveat emptor - let the buyer beware. • 3 - Small is beautiful.
Security in Legion (1) Design Principals • 1 - As in the Hippocratic Oath, do no harm! • 2 - Caveat emptor - let the buyer beware. • 3 - Small is beautiful.
 Security in Legion Standards • X. 509 ? • Keberos ?
Security in Legion Standards • X. 509 ? • Keberos ?
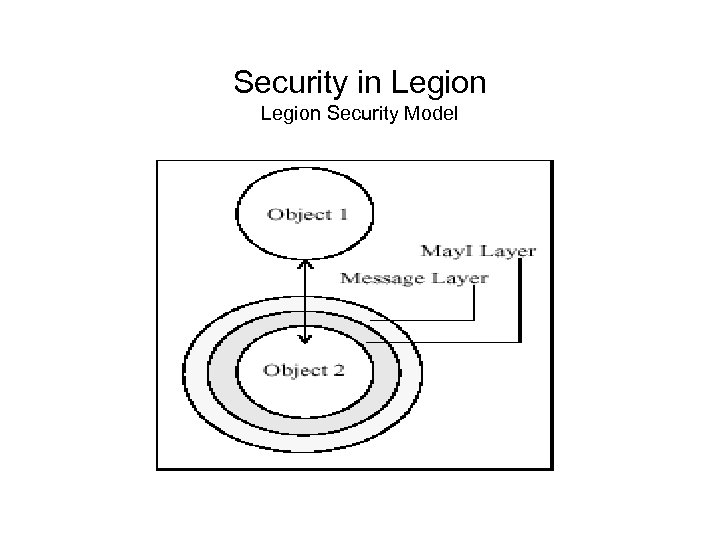 Security in Legion Security Model
Security in Legion Security Model
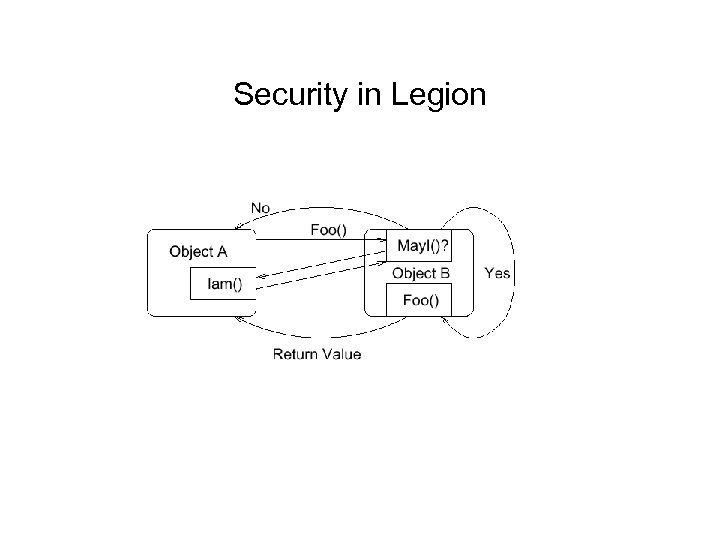
 Security in Legion (2) Basic Concepts • Every object provides certain known member functions - May. I, Can. I, Iam, and Delegate. (Can be defaulted to NIL. ) • Two objects associated with each operation: a responsible agent (RA) and a calling agent (CA) • Every invocation of member function is performed in the context of a certificate which contains the Legion Object ID. Certificate digitally signed by maker
Security in Legion (2) Basic Concepts • Every object provides certain known member functions - May. I, Can. I, Iam, and Delegate. (Can be defaulted to NIL. ) • Two objects associated with each operation: a responsible agent (RA) and a calling agent (CA) • Every invocation of member function is performed in the context of a certificate which contains the Legion Object ID. Certificate digitally signed by maker
 Security in Legion
Security in Legion
 Security in Legion • • • Legion users responsible for own security. Object might trust that the CA is correct. Policies defined by objects themselves. Every class defines a special member function, May. I defines the security objects for a class. Every member function invocation permitted only if May. I sanctions it.
Security in Legion • • • Legion users responsible for own security. Object might trust that the CA is correct. Policies defined by objects themselves. Every class defines a special member function, May. I defines the security objects for a class. Every member function invocation permitted only if May. I sanctions it.
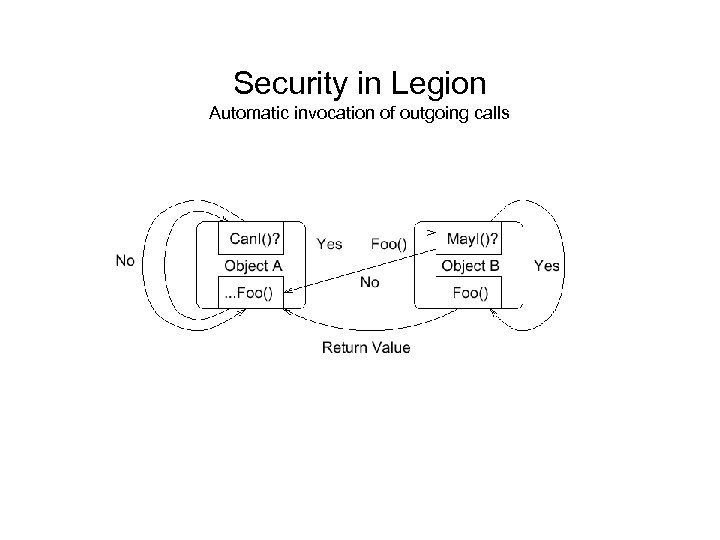 Security in Legion Automatic invocation of outgoing calls
Security in Legion Automatic invocation of outgoing calls
 Security in Legion • Authentication aided by use of Legion certificates based on public-key cryptography by default. Must know private key to authenticate. • May. I functions can code their own authentication protocols • Every Legion object required to supply special member function Iam for authentication purposes.
Security in Legion • Authentication aided by use of Legion certificates based on public-key cryptography by default. Must know private key to authenticate. • May. I functions can code their own authentication protocols • Every Legion object required to supply special member function Iam for authentication purposes.
 Security in Legion • Login establishes user identity and creates responsibility agent for user. • Login is building block for authentication and delegation. • Object can delegate new certificate to delegate rights. • Delegation policy defined by object.
Security in Legion • Login establishes user identity and creates responsibility agent for user. • Login is building block for authentication and delegation. • Object can delegate new certificate to delegate rights. • Delegation policy defined by object.
 Security in Legion Future Work • Legion does not specify any particular encryption. Future standardization? • Legion eschews distinguished trusted objects centralized key management server • Composition of a security policy
Security in Legion Future Work • Legion does not specify any particular encryption. Future standardization? • Legion eschews distinguished trusted objects centralized key management server • Composition of a security policy
 Security in Globus (1) Standards • Standards subscribed to: – Generic Security Services (GSS) RFC 2078 – Secure Socket Layer (SSL) • [SSleay] – Public Key Cryptography based on X. 509 certificates – Kerberos
Security in Globus (1) Standards • Standards subscribed to: – Generic Security Services (GSS) RFC 2078 – Secure Socket Layer (SSL) • [SSleay] – Public Key Cryptography based on X. 509 certificates – Kerberos
 Security in Globus (2)
Security in Globus (2)
 Security in Globus (3) Security Requirements • • Single sign-on Protection of credentials Interoperability with local security solutions Exportability Uniform credentials/certification infrastructure Support for secure group communication Support for multiple implementations
Security in Globus (3) Security Requirements • • Single sign-on Protection of credentials Interoperability with local security solutions Exportability Uniform credentials/certification infrastructure Support for secure group communication Support for multiple implementations
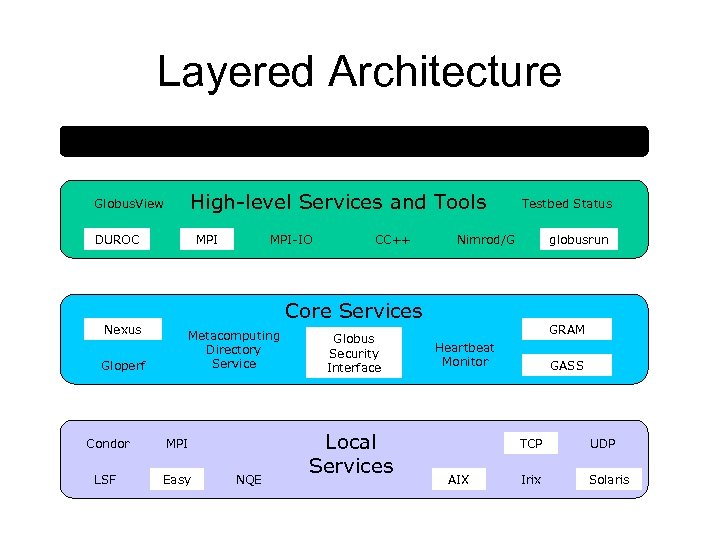 Layered Architecture Applications High-level Services and Tools Globus. View DUROC Nexus Gloperf MPI-IO CC++ Testbed Status Nimrod/G globusrun Core Services Metacomputing Directory Service Condor MPI LSF Easy NQE Globus Security Interface Local Services GRAM Heartbeat Monitor GASS TCP AIX UDP Irix Solaris
Layered Architecture Applications High-level Services and Tools Globus. View DUROC Nexus Gloperf MPI-IO CC++ Testbed Status Nimrod/G globusrun Core Services Metacomputing Directory Service Condor MPI LSF Easy NQE Globus Security Interface Local Services GRAM Heartbeat Monitor GASS TCP AIX UDP Irix Solaris
 Security in Globus (4) • assumes grid consists of multiple trust domains • assumes resource pool and user population are large and dynamic • interoperate with local security solutions - local security policies differ • authentication exportable - cannot directly or indirectly require use of bulk privacy
Security in Globus (4) • assumes grid consists of multiple trust domains • assumes resource pool and user population are large and dynamic • interoperate with local security solutions - local security policies differ • authentication exportable - cannot directly or indirectly require use of bulk privacy
 Security in Globus (5) • uniform credentials/certification - a user will be associated differently with site it has access to single logon - number of processes used in a computation will be dynamic access control
Security in Globus (5) • uniform credentials/certification - a user will be associated differently with site it has access to single logon - number of processes used in a computation will be dynamic access control
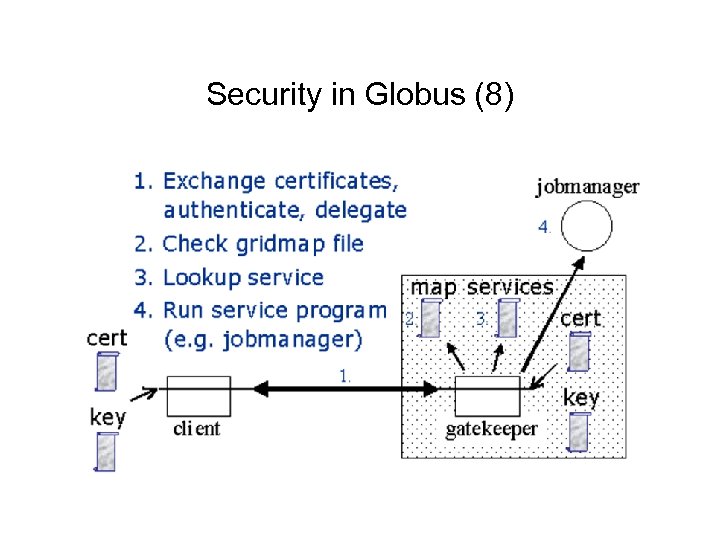 Security in Globus (8)
Security in Globus (8)
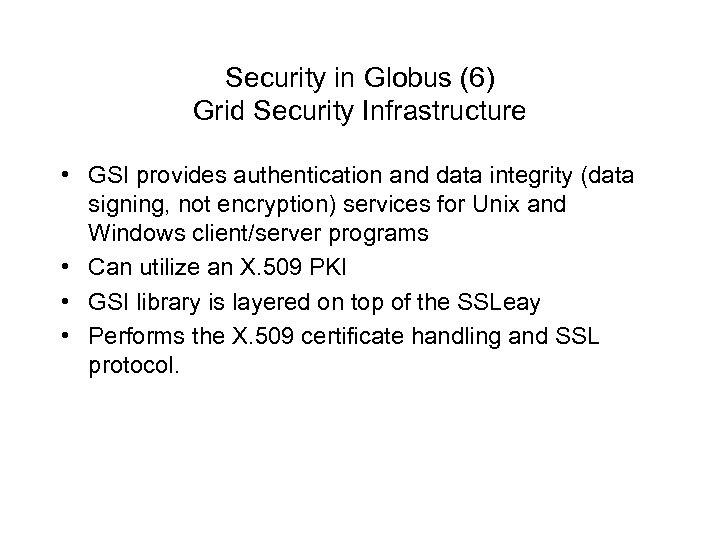 Security in Globus (6) Grid Security Infrastructure • GSI provides authentication and data integrity (data signing, not encryption) services for Unix and Windows client/server programs • Can utilize an X. 509 PKI • GSI library is layered on top of the SSLeay • Performs the X. 509 certificate handling and SSL protocol.
Security in Globus (6) Grid Security Infrastructure • GSI provides authentication and data integrity (data signing, not encryption) services for Unix and Windows client/server programs • Can utilize an X. 509 PKI • GSI library is layered on top of the SSLeay • Performs the X. 509 certificate handling and SSL protocol.
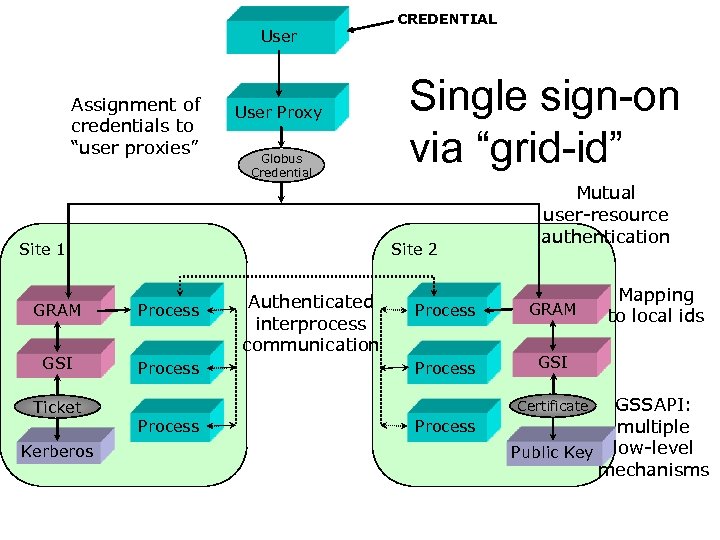 User Assignment of credentials to “user proxies” User Proxy Globus Credential GRAM Process GSI Process Kerberos Single sign-on via “grid-id” Site 2 Site 1 Ticket CREDENTIAL Authenticated interprocess communication Mutual user-resource authentication Process GRAM Process GSI GSSAPI: multiple Public Key low-level mechanisms Certificate Process Mapping to local ids Process
User Assignment of credentials to “user proxies” User Proxy Globus Credential GRAM Process GSI Process Kerberos Single sign-on via “grid-id” Site 2 Site 1 Ticket CREDENTIAL Authenticated interprocess communication Mutual user-resource authentication Process GRAM Process GSI GSSAPI: multiple Public Key low-level mechanisms Certificate Process Mapping to local ids Process
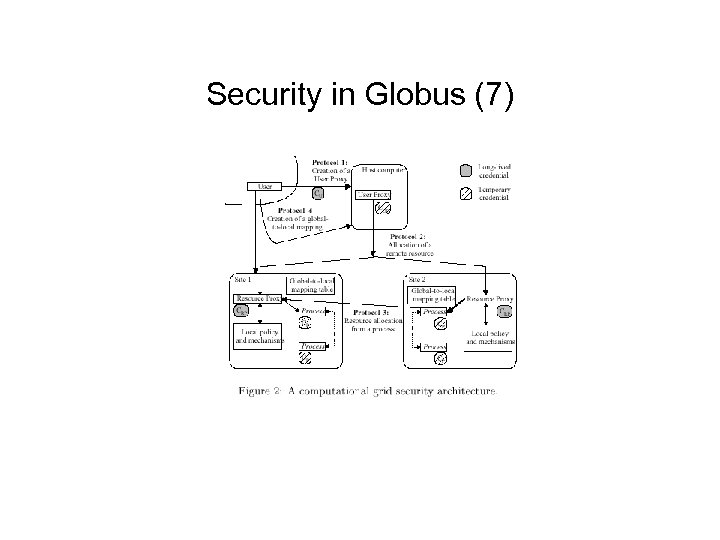 Security in Globus (7)
Security in Globus (7)
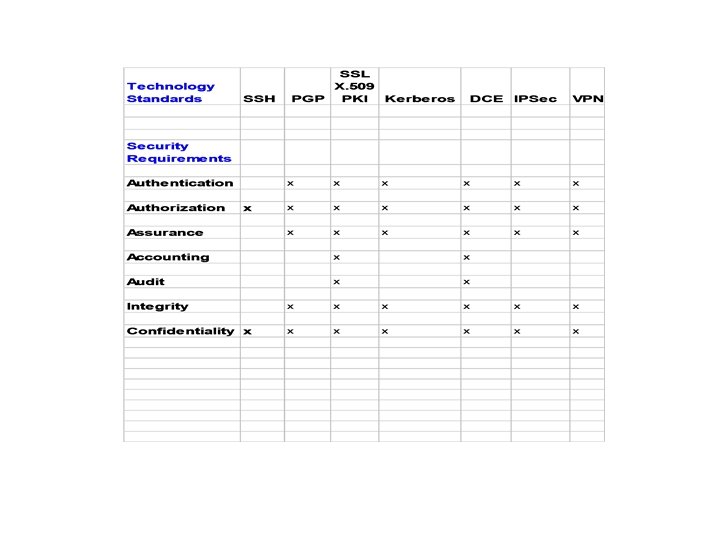
 Summary • • Computer security is machine access centric Network security is network access centric Grid security is application centric Inter-domain communications based upon common security standards such as PKI. • Metacomputing approach that embrace security standards will be more widely adopted.
Summary • • Computer security is machine access centric Network security is network access centric Grid security is application centric Inter-domain communications based upon common security standards such as PKI. • Metacomputing approach that embrace security standards will be more widely adopted.




