a0b3a2d7005bf483171f9f1d484b9600.ppt
- Количество слайдов: 32

Overview of Modern Web Architectures, Standards, Security, and Future Directions Zhenhua Guo 1

Outline n n n Web App Case Study Modern Web Characteristics Modern Web Architecture : Open Social q q q Architecture Components Security n n Background Authorization Out of Scope: Authentication Future Directions 2
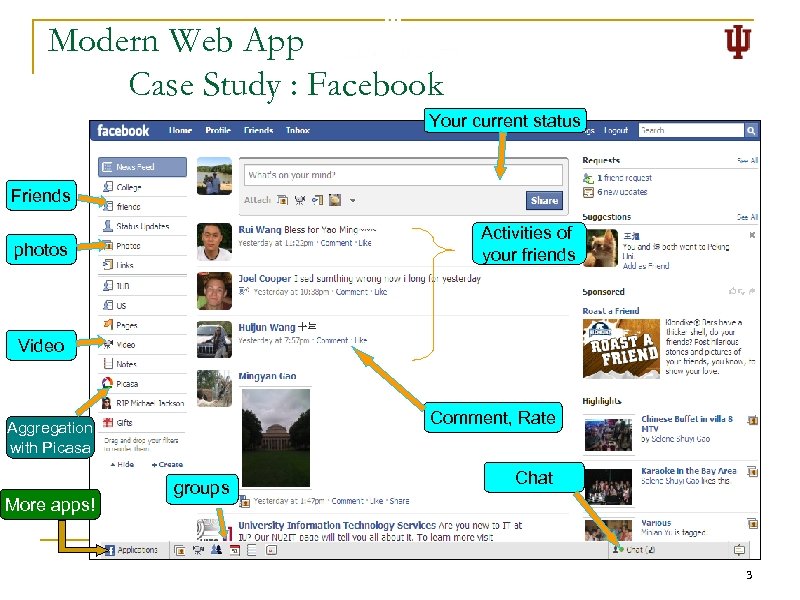
Modern Web App Case Study : Facebook Your current status n Friends photos Facebook q q More than 200 million active users Activities of MS paid $240 million foryour friends 1. 6 percent Video Comment, Rate Aggregation with Picasa More apps! groups Chat 3
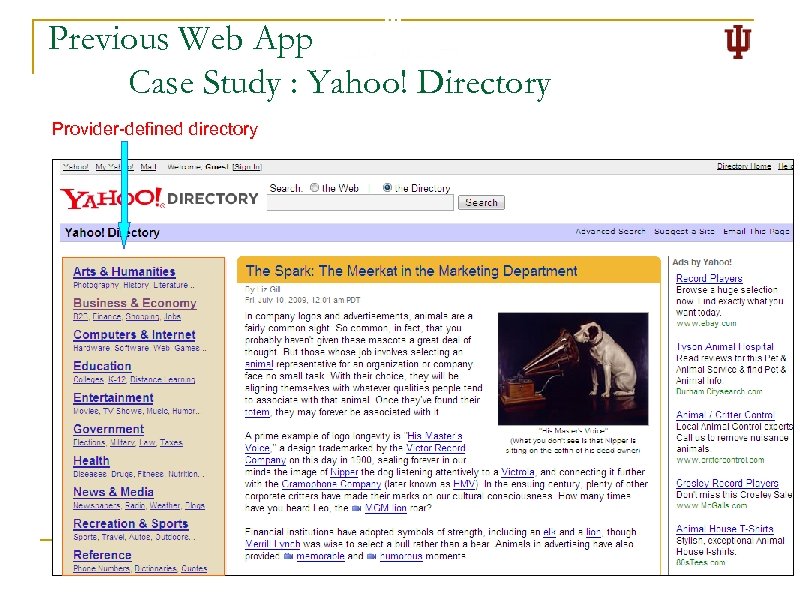
Previous Web App Case Study : Yahoo! Directory Provider-defined directory 4
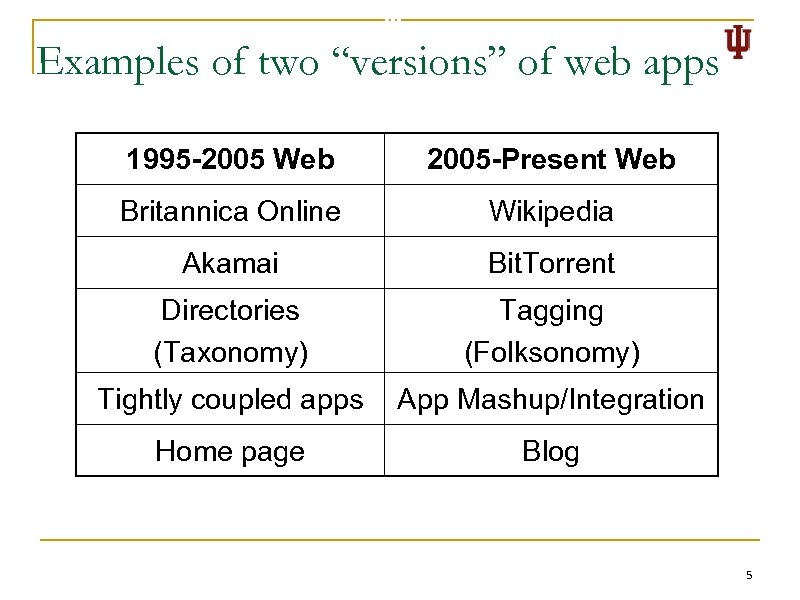
Examples of two “versions” of web apps 1995 -2005 Web 2005 -Present Web Britannica Online Wikipedia Akamai Bit. Torrent Directories (Taxonomy) Tagging (Folksonomy) Tightly coupled apps App Mashup/Integration Home page Blog 5
Web 2. 0 n n “Second generation of web development and web design” Web 2. 0 vs. Web 1. 0 q Technical point of view n n q Similar technologies as Web 1. 0: HTML, Javascript, XML, HTTP, etc. Web 2. 0 makes the web programmable User’s point of view n Read-write collaborative web q n Participatory nature q n Blogging, commenting, rating Cooperate, not control q n Sharing, creation of data Facebook interoperates with Google Picasa, Yahoo! Flickr, Blogs, etc User centric q Web is a platform. Users add content (“value”) 6
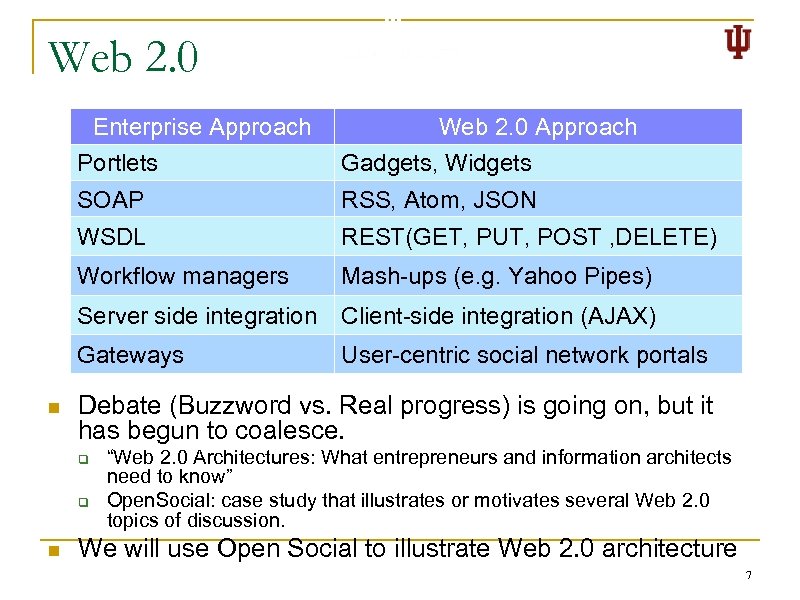
Web 2. 0 Enterprise Approach Web 2. 0 Approach Portlets SOAP RSS, Atom, JSON WSDL REST(GET, PUT, POST , DELETE) Workflow managers Mash-ups (e. g. Yahoo Pipes) Server side integration Client-side integration (AJAX) Gateways n Gadgets, Widgets User-centric social network portals Debate (Buzzword vs. Real progress) is going on, but it has begun to coalesce. q q n “Web 2. 0 Architectures: What entrepreneurs and information architects need to know” Open. Social: case study that illustrates or motivates several Web 2. 0 topics of discussion. We will use Open Social to illustrate Web 2. 0 architecture 7
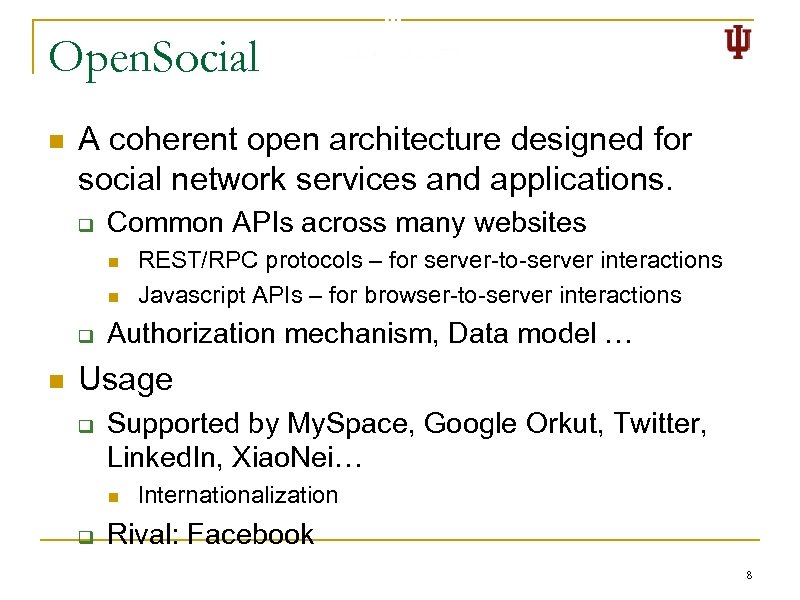
Open. Social n A coherent open architecture designed for social network services and applications. q Common APIs across many websites n n q n REST/RPC protocols – for server-to-server interactions Javascript APIs – for browser-to-server interactions Authorization mechanism, Data model … Usage q Supported by My. Space, Google Orkut, Twitter, Linked. In, Xiao. Nei… n q Internationalization Rival: Facebook 8
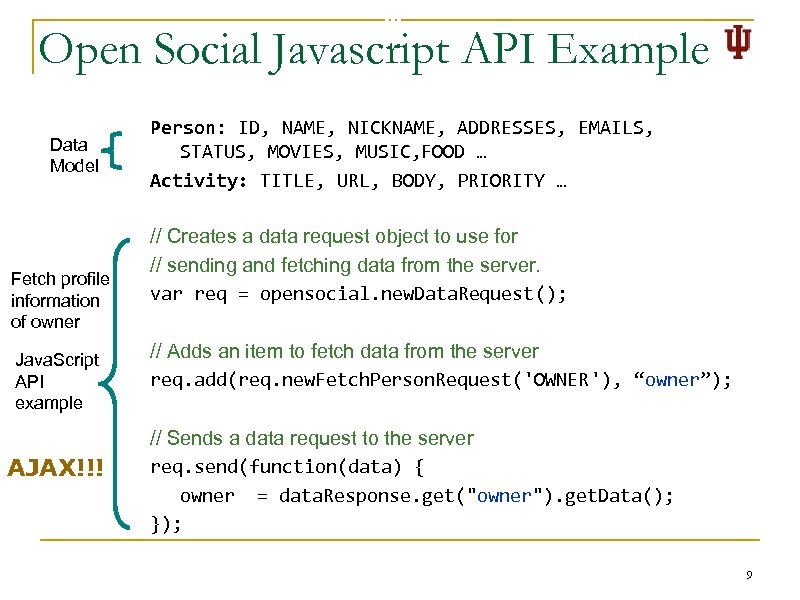
Open Social Javascript API Example Data Model Fetch profile information of owner Java. Script API example AJAX!!! Person: ID, NAME, NICKNAME, ADDRESSES, EMAILS, STATUS, MOVIES, MUSIC, FOOD … Activity: TITLE, URL, BODY, PRIORITY … // Creates a data request object to use for // sending and fetching data from the server. var req = opensocial. new. Data. Request(); // Adds an item to fetch data from the server req. add(req. new. Fetch. Person. Request('OWNER'), “owner”); // Sends a data request to the server req. send(function(data) { owner = data. Response. get("owner"). get. Data(); }); 9
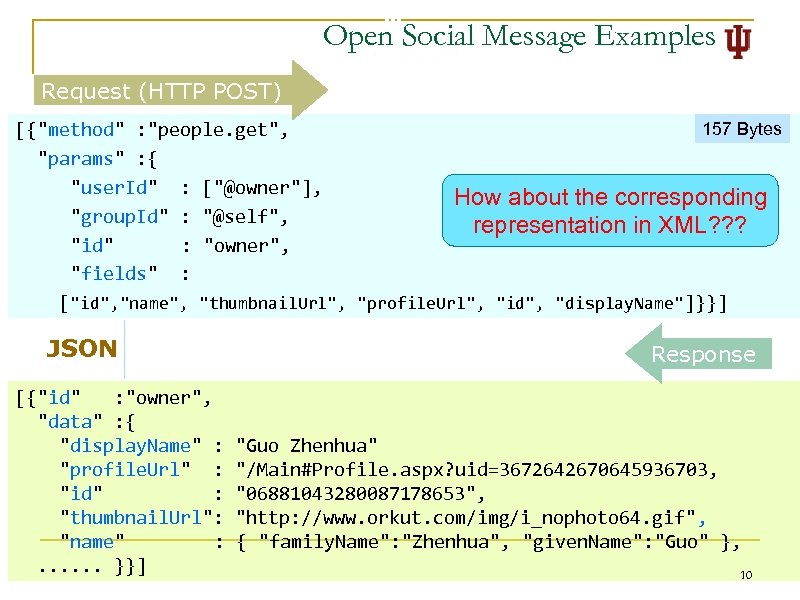
Open Social Message Examples Request (HTTP POST) 157 Bytes [{"method" : "people. get", "params" : { "user. Id" : ["@owner"], How about the corresponding "group. Id" : "@self", representation in XML? ? ? "id" : "owner", "fields" : ["id", "name", "thumbnail. Url", "profile. Url", "id", "display. Name"]}}] JSON [{"id" : "owner", "data" : { "display. Name" : "profile. Url" : "id" : "thumbnail. Url": "name" : . . . }}] Response "Guo Zhenhua" "/Main#Profile. aspx? uid=3672642670645936703, "06881043280087178653", "http: //www. orkut. com/img/i_nophoto 64. gif", { "family. Name": "Zhenhua", "given. Name": "Guo" }, 10
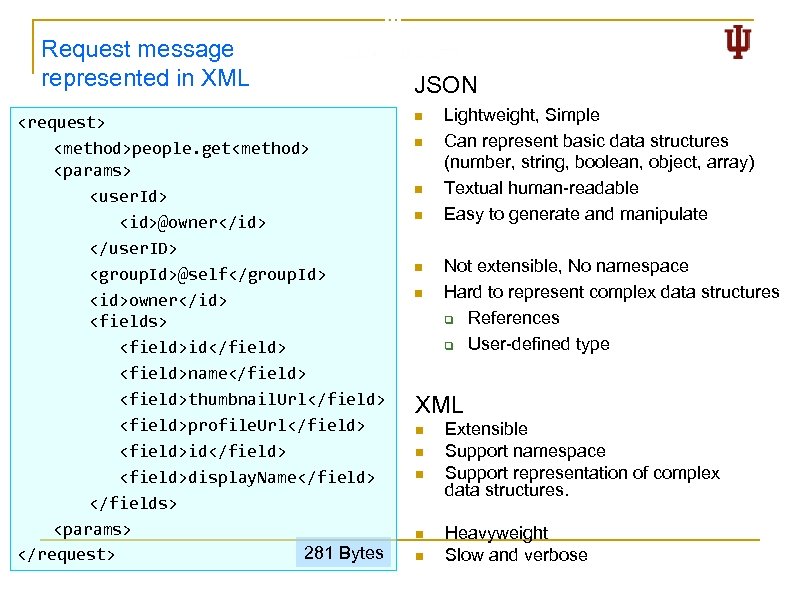
Request message represented in XML <request> <method>people. get<method> <params> <user. Id> <id>@owner</id> </user. ID> <group. Id>@self</group. Id> <id>owner</id> <fields> <field>id</field> <field>name</field> <field>thumbnail. Url</field> <field>profile. Url</field> <field>id</field> <field>display. Name</field> </fields> <params> 281 Bytes </request> JSON n n n Lightweight, Simple Can represent basic data structures (number, string, boolean, object, array) Textual human-readable Easy to generate and manipulate Not extensible, No namespace Hard to represent complex data structures q References q User-defined type XML n n n Extensible Support namespace Support representation of complex data structures. Heavyweight Slow and verbose
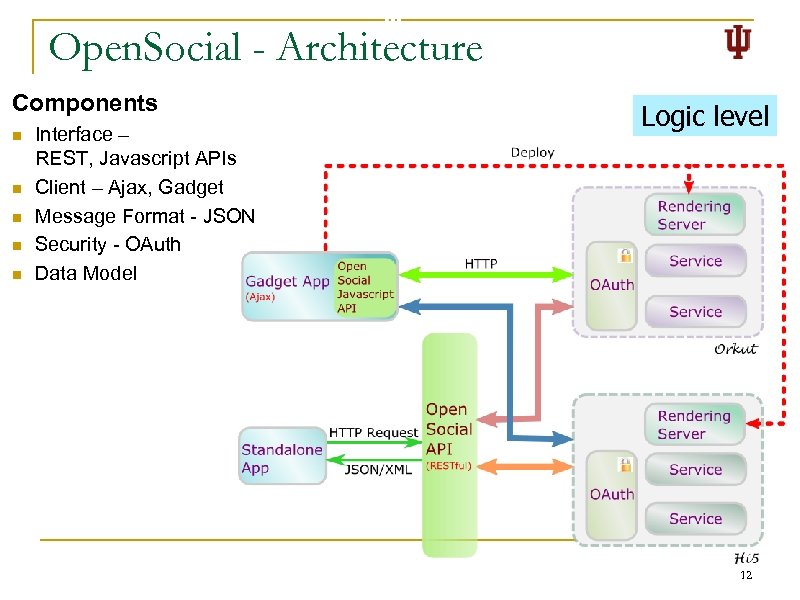
Open. Social - Architecture Components n n n Interface – REST, Javascript APIs Client – Ajax, Gadget Message Format - JSON Security - OAuth Data Model Logic level 12
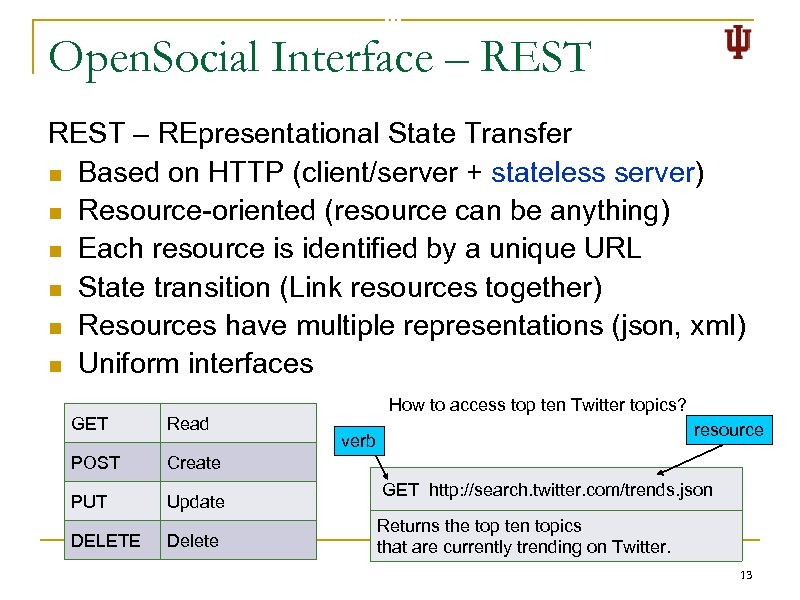
Open. Social Interface – REST – REpresentational State Transfer n Based on HTTP (client/server + stateless server) n Resource-oriented (resource can be anything) n Each resource is identified by a unique URL n State transition (Link resources together) n Resources have multiple representations (json, xml) n Uniform interfaces GET Read POST How to access top ten Twitter topics? Create PUT DELETE Update Delete resource verb GET http: //search. twitter. com/trends. json Returns the top ten topics that are currently trending on Twitter. 13
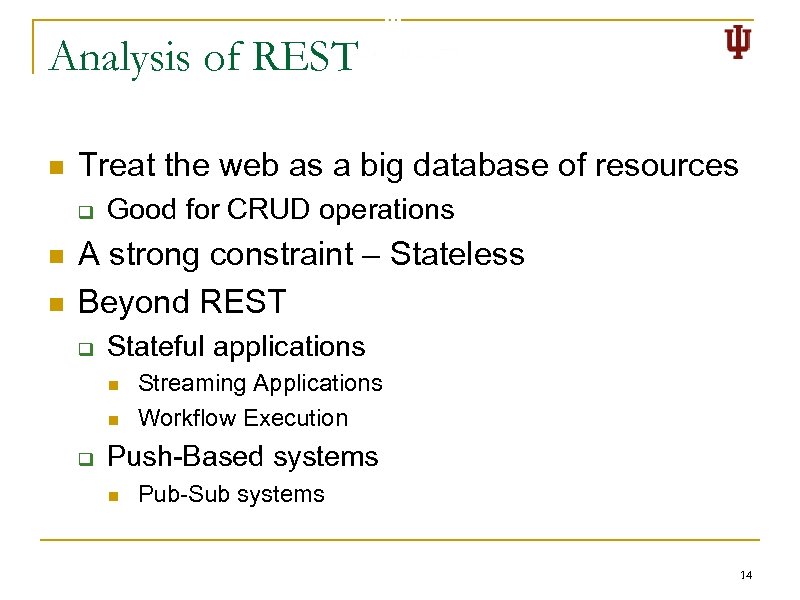
Analysis of REST n Treat the web as a big database of resources q n n Good for CRUD operations A strong constraint – Stateless Beyond REST q Stateful applications n n q Streaming Applications Workflow Execution Push-Based systems n Pub-Sub systems 14
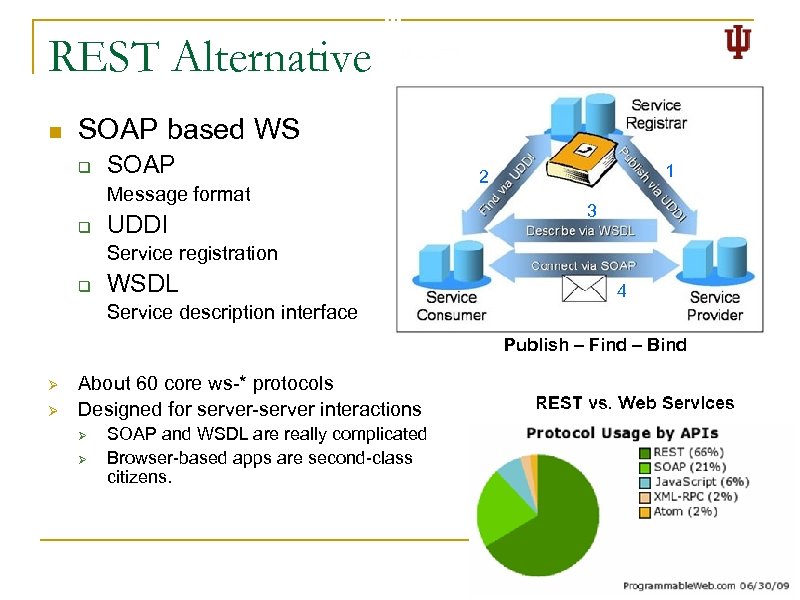
REST Alternative n SOAP based WS q SOAP Message format q UDDI 1 2 3 Service registration q WSDL 4 Service description interface Publish – Find – Bind Ø Ø About 60 core ws-* protocols Designed for server-server interactions Ø Ø SOAP and WSDL are really complicated Browser-based apps are second-class citizens. 15
AJAX

Open. Social Client Tech – AJAX n Rationale Update sections without refreshing the whole page q More interactive q More responsive q Less bandwidth usage n Asynchronous Java. Script and XML q q q HTML + CSS Presentation DOM Document model (for dynamic manipulation) XMLHttp. Request Asynchronous Communication JSON/XML Data format Javascript Bring these together 17
Data Model
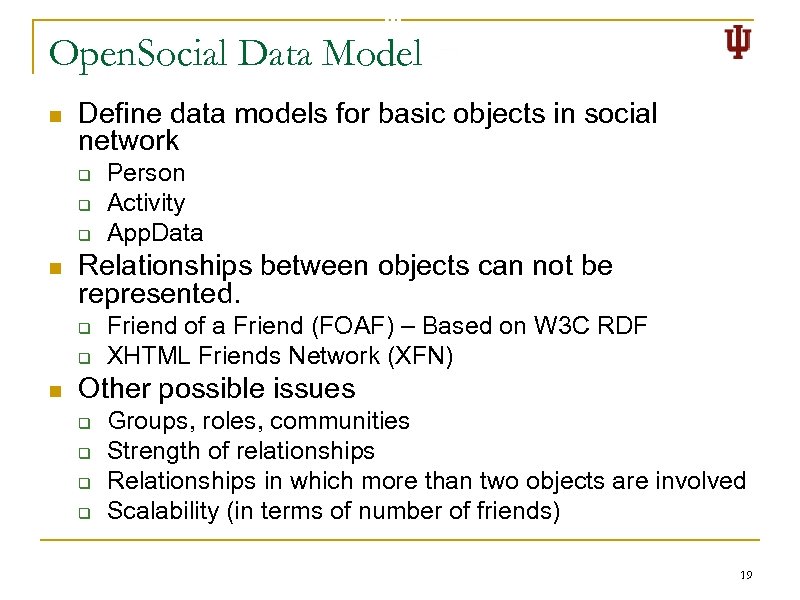
Open. Social Data Model n Define data models for basic objects in social network q q q n Relationships between objects can not be represented. q q n Person Activity App. Data Friend of a Friend (FOAF) – Based on W 3 C RDF XHTML Friends Network (XFN) Other possible issues q q Groups, roles, communities Strength of relationships Relationships in which more than two objects are involved Scalability (in terms of number of friends) 19

Security in Open. Social 20
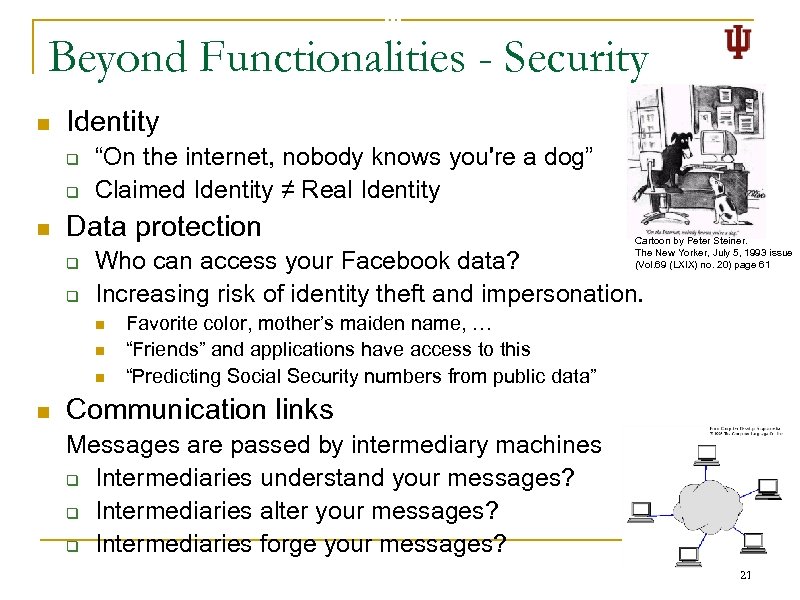
Beyond Functionalities - Security n Identity q q n “On the internet, nobody knows you're a dog” Claimed Identity ≠ Real Identity Data protection q q Who can access your Facebook data? Increasing risk of identity theft and impersonation. n n Cartoon by Peter Steiner. The New Yorker, July 5, 1993 issue (Vol. 69 (LXIX) no. 20) page 61 Favorite color, mother’s maiden name, … “Friends” and applications have access to this “Predicting Social Security numbers from public data” Communication links Messages are passed by intermediary machines q Intermediaries understand your messages? q Intermediaries alter your messages? q Intermediaries forge your messages? 21
Security Requirements (in Web) n Connection level q q n SSL/TLS System Implementation level q q q n Confidentiality Integrity Non-repudiation Prevention of replay attack Redirect Session stealing (cookie) Cross-site scripting, Cross-site request forgery Securer programs + User education Architecture level q Authentication n q Single Sign-On Authorization n Delegation 22

Challenges n Technical Challenges q q n Loosely coupled components No single, isolated trusted base Domain-specific policies Separation of security policies and security mechanisms. Possible solutions q Authentication n q Central Authentication Service Cosign Open. ID Authorization n n Shibboleth OAuth 23
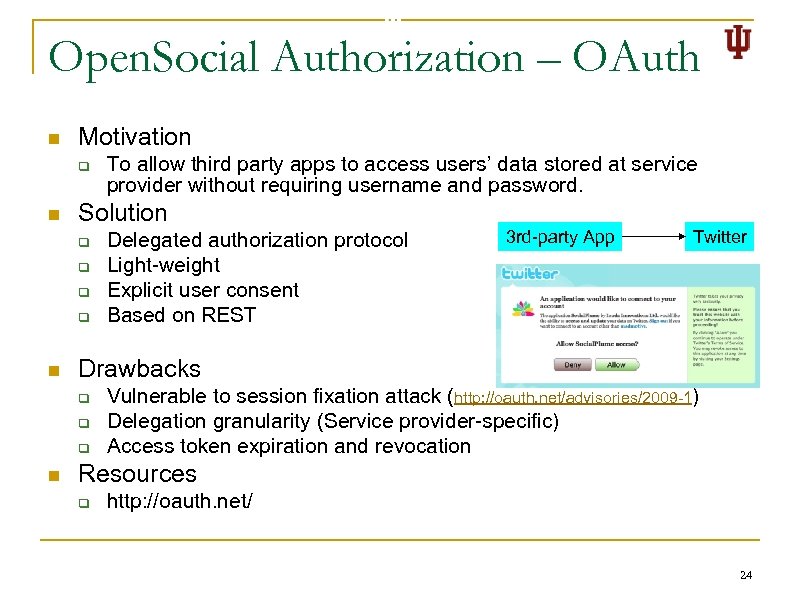
Open. Social Authorization – OAuth n Motivation q n Solution q q n Delegated authorization protocol Light-weight Explicit user consent Based on REST 3 rd-party App Twitter Drawbacks q q q n To allow third party apps to access users’ data stored at service provider without requiring username and password. Vulnerable to session fixation attack (http: //oauth. net/advisories/2009 -1) Delegation granularity (Service provider-specific) Access token expiration and revocation Resources q http: //oauth. net/ 24
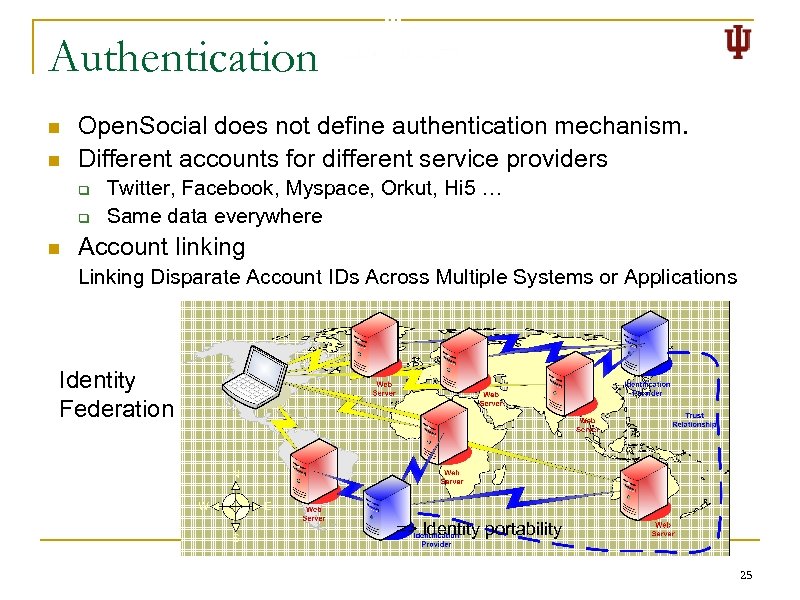
Authentication n n Open. Social does not define authentication mechanism. Different accounts for different service providers q q n Twitter, Facebook, Myspace, Orkut, Hi 5 … Same data everywhere Account linking Linking Disparate Account IDs Across Multiple Systems or Applications Identity Federation => Identity portability 25
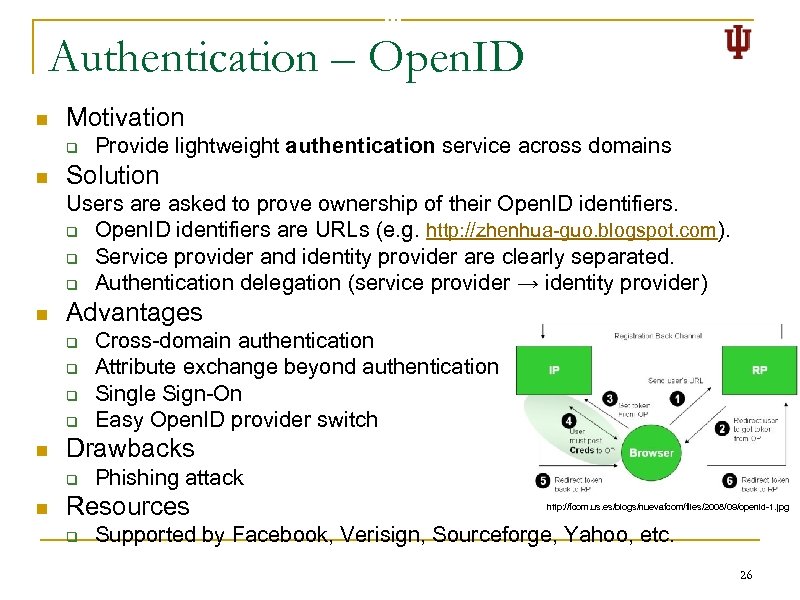
Authentication – Open. ID n Motivation q n Provide lightweight authentication service across domains Solution Users are asked to prove ownership of their Open. ID identifiers. q Open. ID identifiers are URLs (e. g. http: //zhenhua-guo. blogspot. com). q Service provider and identity provider are clearly separated. q Authentication delegation (service provider → identity provider) n Advantages q q n Drawbacks q n Cross-domain authentication Attribute exchange beyond authentication Single Sign-On Easy Open. ID provider switch Phishing attack Resources q http: //fcom. us. es/blogs/nuevafcom/files/2008/09/openid-1. jpg Supported by Facebook, Verisign, Sourceforge, Yahoo, etc. 26
OAuth and Open. ID n n Based on relaxed REST Use SSL/TLS to guarantee confidentiality, integrity and non-repudiation. Scalability Vulnerable to q q q Phishing Cross-site scripting Cross-site forgery request 27
Conclusions n n n Adoption of web 2. 0 Services, not packaged software Open Architecture and Open Standards q q q n n Interoperability Flexibility Integration Security Adoption in scientific communities q Traditional gateways n q LEAD, Earth System Grid Gateways that integrate web 2. 0 technologies n n n my. Experiment, Sci. Vee, Sakai Open Life Science Gateway Polar. Grid Portal

Future Directions n Semantic Web (Web 3. 0? ) q n Machine-readable representations of resources and relationships Artificial Intelligence, Data Mining q Search Engine n q Recommendation System n q Scaling Question Answering n q Information search Information retrieval Social Network Analysis n n Flow pattern recognition Strength of connections 29
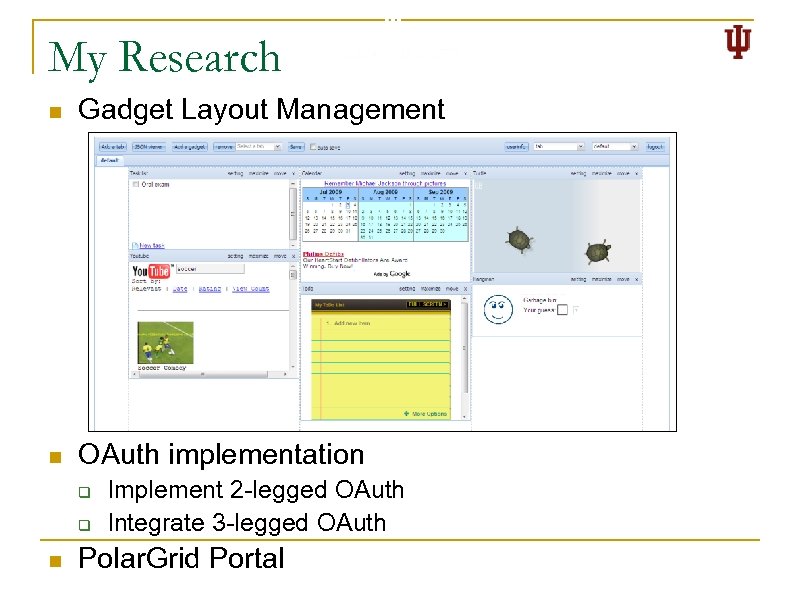
My Research n Gadget Layout Management n OAuth implementation q q n Implement 2 -legged OAuth Integrate 3 -legged OAuth Polar. Grid Portal


Questions?
a0b3a2d7005bf483171f9f1d484b9600.ppt