e0b44fe65e4b8255df99ea5ea0781c3f.ppt
- Количество слайдов: 16
 Overview of AEEC Information Security CONOPS Vic Patel, FAA/ATO-P WJHTC Security Engineering Simon Blake-Wilson, BCI and FAA April 19, 2004
Overview of AEEC Information Security CONOPS Vic Patel, FAA/ATO-P WJHTC Security Engineering Simon Blake-Wilson, BCI and FAA April 19, 2004
 AEEC Information Security Background • • • AEEC is an association of airlines, organized by ARINC, that develop standards for avionics AEEC Information Security (SEC) Working Group formed to address increasing interest from airlines AEEC SEC participation includes airlines, airframers, avionics, IFE vendors, comms service providers FAA/ATO-P WJHTC Security Engineering Group participating in AEEC SEC initial product is an Information Security Concept of Operations (CONOPS)
AEEC Information Security Background • • • AEEC is an association of airlines, organized by ARINC, that develop standards for avionics AEEC Information Security (SEC) Working Group formed to address increasing interest from airlines AEEC SEC participation includes airlines, airframers, avionics, IFE vendors, comms service providers FAA/ATO-P WJHTC Security Engineering Group participating in AEEC SEC initial product is an Information Security Concept of Operations (CONOPS)
 AEEC Info Sec CONOPS Goals of the Info Sec CONOPS include: • • Provide background in info sec for airline departments who have not dealt with it before Emphasize sound security practice Assist other AEEC groups thinking about information security Discuss issues that arise as the aircraft becomes part of the corporate LAN, and there is more connectivity between domains on the aircraft CONOPS is expected to be approved in mid 2005.
AEEC Info Sec CONOPS Goals of the Info Sec CONOPS include: • • Provide background in info sec for airline departments who have not dealt with it before Emphasize sound security practice Assist other AEEC groups thinking about information security Discuss issues that arise as the aircraft becomes part of the corporate LAN, and there is more connectivity between domains on the aircraft CONOPS is expected to be approved in mid 2005.
 CONOPS Information Security Process The CONOPS emphasizes the importance of following an overall information security process to secure a system: • • Risk-based approach High-level to allow each step to be performed at an appropriate level of detail Strangely there are no existing standards for overall approach. Common Criteria and Federal Information Security Management Act (FISMA) provide pieces but are not coordinated. FAA’s Security Certification and Authorization Package (SCAP) process includes FISMA requirements
CONOPS Information Security Process The CONOPS emphasizes the importance of following an overall information security process to secure a system: • • Risk-based approach High-level to allow each step to be performed at an appropriate level of detail Strangely there are no existing standards for overall approach. Common Criteria and Federal Information Security Management Act (FISMA) provide pieces but are not coordinated. FAA’s Security Certification and Authorization Package (SCAP) process includes FISMA requirements
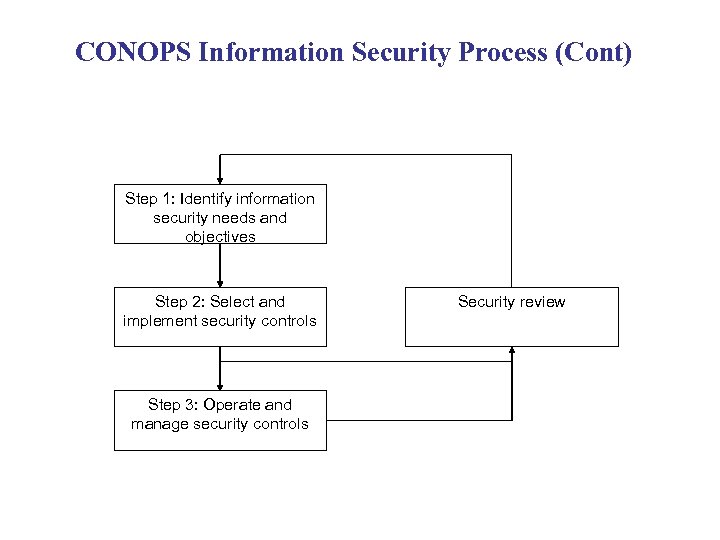 CONOPS Information Security Process (Cont) Step 1: Identify information security needs and objectives Step 2: Select and implement security controls Step 3: Operate and manage security controls Security review
CONOPS Information Security Process (Cont) Step 1: Identify information security needs and objectives Step 2: Select and implement security controls Step 3: Operate and manage security controls Security review
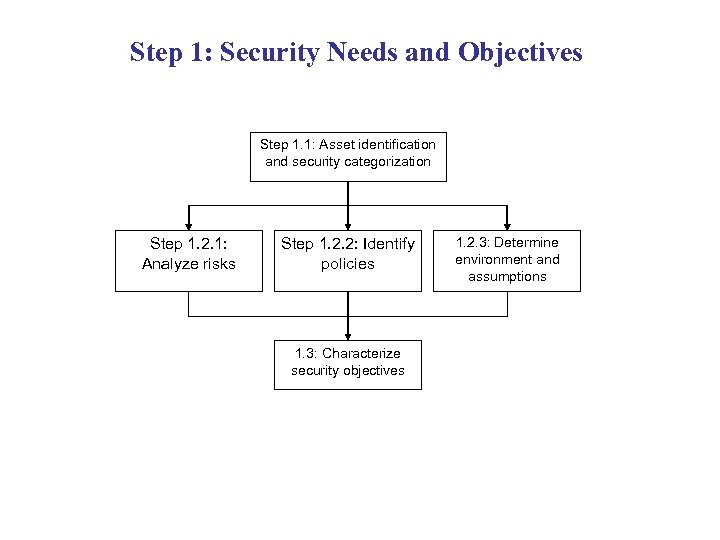 Step 1: Security Needs and Objectives Step 1. 1: Asset identification and security categorization Step 1. 2. 1: Analyze risks Step 1. 2. 2: Identify policies 1. 3: Characterize security objectives 1. 2. 3: Determine environment and assumptions
Step 1: Security Needs and Objectives Step 1. 1: Asset identification and security categorization Step 1. 2. 1: Analyze risks Step 1. 2. 2: Identify policies 1. 3: Characterize security objectives 1. 2. 3: Determine environment and assumptions
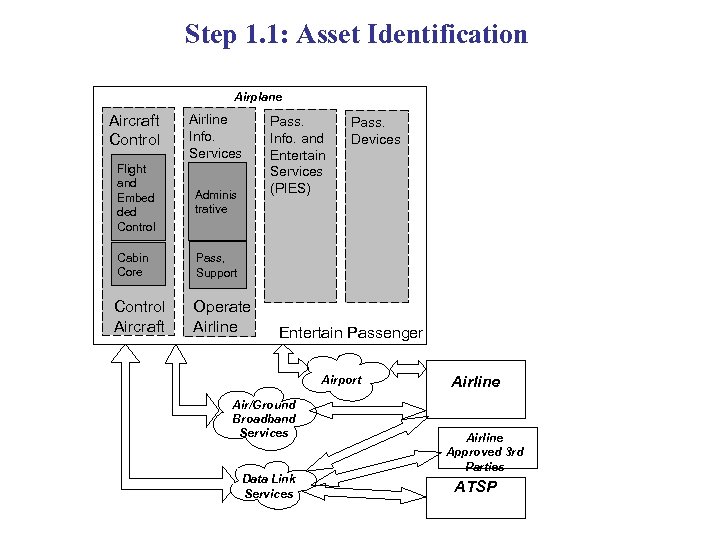 Step 1. 1: Asset Identification Airplane Aircraft Control Airline Info. Services Flight and Embed ded Control Adminis trative Cabin Core Operate Airline Pass. Devices Pass, Support Control Aircraft Pass. Info. and Entertain Services (PIES) Entertain Passenger Airport Air/Ground Broadband Services Data Link Services Airline Approved 3 rd Parties ATSP
Step 1. 1: Asset Identification Airplane Aircraft Control Airline Info. Services Flight and Embed ded Control Adminis trative Cabin Core Operate Airline Pass. Devices Pass, Support Control Aircraft Pass. Info. and Entertain Services (PIES) Entertain Passenger Airport Air/Ground Broadband Services Data Link Services Airline Approved 3 rd Parties ATSP
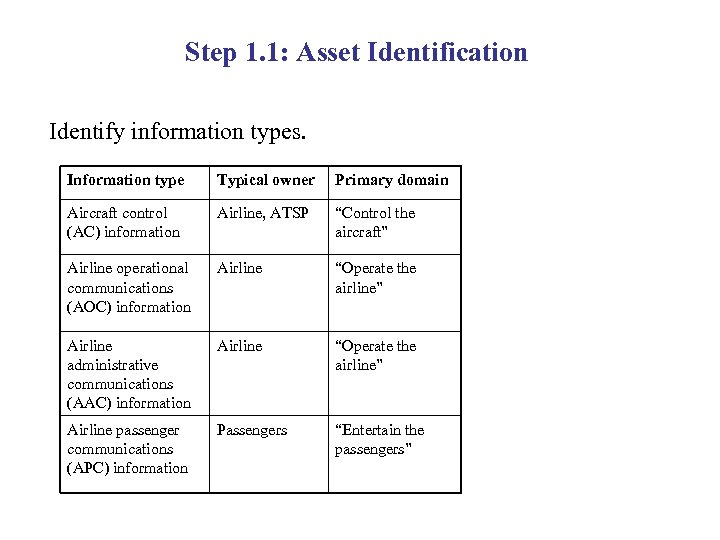 Step 1. 1: Asset Identification Identify information types. Information type Typical owner Primary domain Aircraft control (AC) information Airline, ATSP “Control the aircraft” Airline operational communications (AOC) information Airline “Operate the airline” Airline administrative communications (AAC) information Airline “Operate the airline” Airline passenger communications (APC) information Passengers “Entertain the passengers”
Step 1. 1: Asset Identification Identify information types. Information type Typical owner Primary domain Aircraft control (AC) information Airline, ATSP “Control the aircraft” Airline operational communications (AOC) information Airline “Operate the airline” Airline administrative communications (AAC) information Airline “Operate the airline” Airline passenger communications (APC) information Passengers “Entertain the passengers”
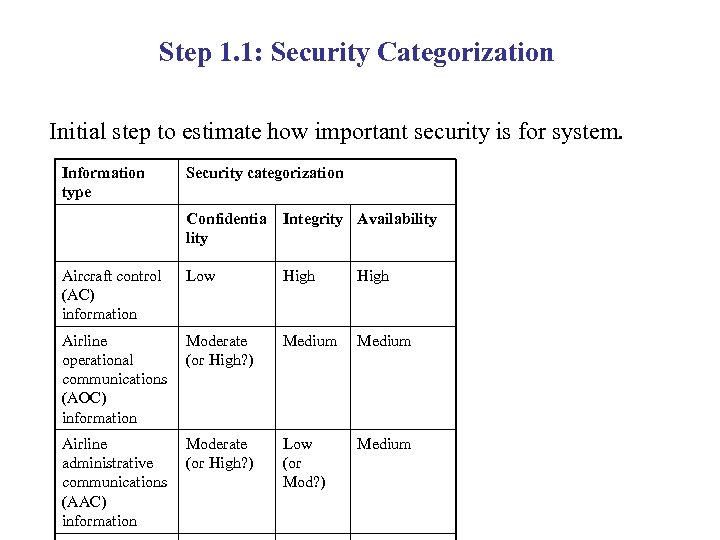 Step 1. 1: Security Categorization Initial step to estimate how important security is for system. Information type Security categorization Confidentia lity Integrity Availability Aircraft control (AC) information Low High Airline operational communications (AOC) information Moderate (or High? ) Medium Airline administrative communications (AAC) information Moderate (or High? ) Low (or Mod? ) Medium
Step 1. 1: Security Categorization Initial step to estimate how important security is for system. Information type Security categorization Confidentia lity Integrity Availability Aircraft control (AC) information Low High Airline operational communications (AOC) information Moderate (or High? ) Medium Airline administrative communications (AAC) information Moderate (or High? ) Low (or Mod? ) Medium
 Step 1. 2. 1: Analyze Risks Identify threats based on high-level framework. Threat Identifier Threat description T. ACCESS An authorized user may gain unauthorized access to the aircraft system or to information controlled by the aircraft system via user error, system error, or an attack for malicious or nonmalicious purposes. T. DEVELOP Security failures may occur as the result of problems introduced during implementation of the aircraft system. T. ENTRY An individual other than an authorized user may gain access to the aircraft system or to information controlled by the aircraft system via system error or an attack for malicious purposes. T. MAINTAI N The security of the aircraft system may be reduced or defeated due to errors or omissions in the administration and maintenance of the
Step 1. 2. 1: Analyze Risks Identify threats based on high-level framework. Threat Identifier Threat description T. ACCESS An authorized user may gain unauthorized access to the aircraft system or to information controlled by the aircraft system via user error, system error, or an attack for malicious or nonmalicious purposes. T. DEVELOP Security failures may occur as the result of problems introduced during implementation of the aircraft system. T. ENTRY An individual other than an authorized user may gain access to the aircraft system or to information controlled by the aircraft system via system error or an attack for malicious purposes. T. MAINTAI N The security of the aircraft system may be reduced or defeated due to errors or omissions in the administration and maintenance of the
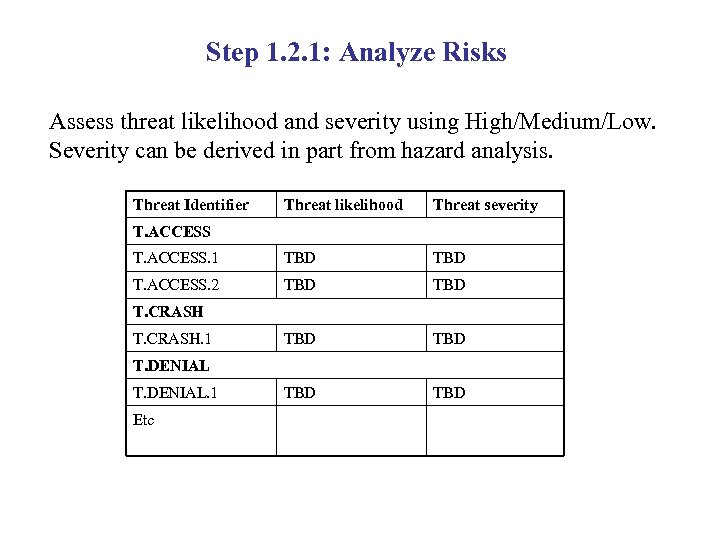 Step 1. 2. 1: Analyze Risks Assess threat likelihood and severity using High/Medium/Low. Severity can be derived in part from hazard analysis. Threat Identifier Threat likelihood Threat severity T. ACCESS. 1 TBD T. ACCESS. 2 TBD TBD TBD T. ACCESS T. CRASH. 1 T. DENIAL. 1 Etc
Step 1. 2. 1: Analyze Risks Assess threat likelihood and severity using High/Medium/Low. Severity can be derived in part from hazard analysis. Threat Identifier Threat likelihood Threat severity T. ACCESS. 1 TBD T. ACCESS. 2 TBD TBD TBD T. ACCESS T. CRASH. 1 T. DENIAL. 1 Etc
 Step 1. 2. 2: Identify Policies Identify policies that may affect security choices. Policy Identifier Policy Description P. AIRLINE This policy area covers applicable airline information security policies. P. EXPORT This policy area covers applicable national and international export laws concerning cryptography and security controls. P. PRIVACY This policy area covers applicable national and international laws concerning privacy. P. REGULATI This policy area covers applicable national ON and international regulations concerning development and implementation of aircraft systems.
Step 1. 2. 2: Identify Policies Identify policies that may affect security choices. Policy Identifier Policy Description P. AIRLINE This policy area covers applicable airline information security policies. P. EXPORT This policy area covers applicable national and international export laws concerning cryptography and security controls. P. PRIVACY This policy area covers applicable national and international laws concerning privacy. P. REGULATI This policy area covers applicable national ON and international regulations concerning development and implementation of aircraft systems.
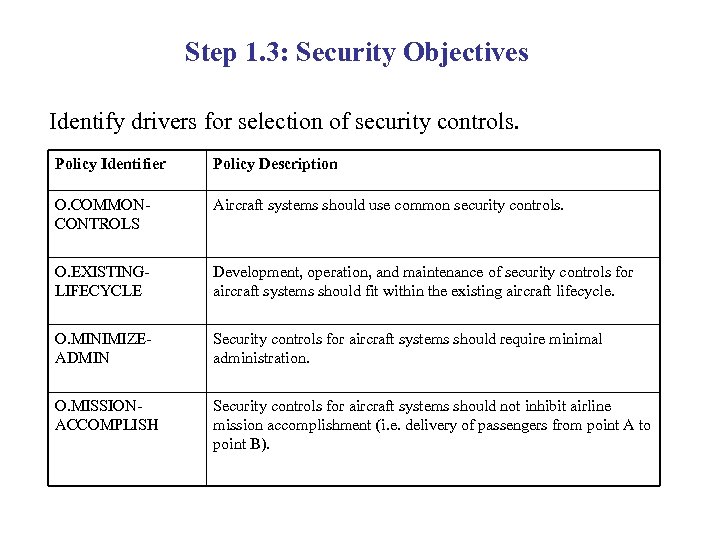 Step 1. 3: Security Objectives Identify drivers for selection of security controls. Policy Identifier Policy Description O. COMMONCONTROLS Aircraft systems should use common security controls. O. EXISTINGLIFECYCLE Development, operation, and maintenance of security controls for aircraft systems should fit within the existing aircraft lifecycle. O. MINIMIZEADMIN Security controls for aircraft systems should require minimal administration. O. MISSIONACCOMPLISH Security controls for aircraft systems should not inhibit airline mission accomplishment (i. e. delivery of passengers from point A to point B).
Step 1. 3: Security Objectives Identify drivers for selection of security controls. Policy Identifier Policy Description O. COMMONCONTROLS Aircraft systems should use common security controls. O. EXISTINGLIFECYCLE Development, operation, and maintenance of security controls for aircraft systems should fit within the existing aircraft lifecycle. O. MINIMIZEADMIN Security controls for aircraft systems should require minimal administration. O. MISSIONACCOMPLISH Security controls for aircraft systems should not inhibit airline mission accomplishment (i. e. delivery of passengers from point A to point B).
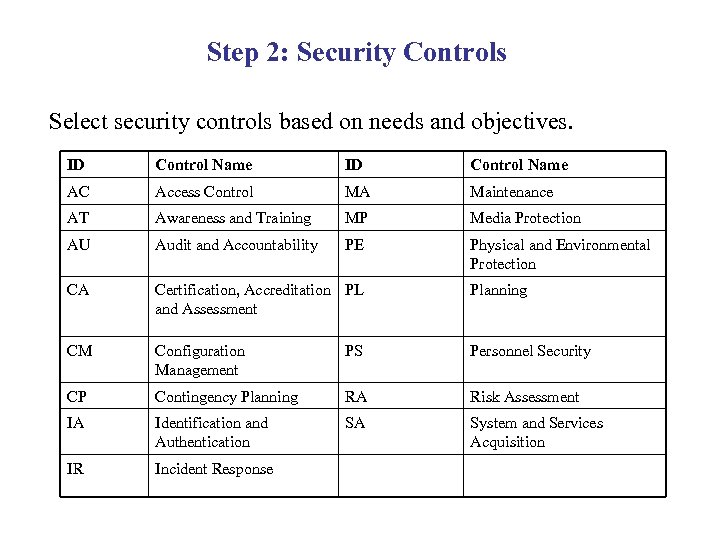 Step 2: Security Controls Select security controls based on needs and objectives. ID Control Name AC Access Control MA Maintenance AT Awareness and Training MP Media Protection AU Audit and Accountability PE Physical and Environmental Protection CA Certification, Accreditation PL and Assessment Planning CM Configuration Management PS Personnel Security CP Contingency Planning RA Risk Assessment IA Identification and Authentication SA System and Services Acquisition IR Incident Response
Step 2: Security Controls Select security controls based on needs and objectives. ID Control Name AC Access Control MA Maintenance AT Awareness and Training MP Media Protection AU Audit and Accountability PE Physical and Environmental Protection CA Certification, Accreditation PL and Assessment Planning CM Configuration Management PS Personnel Security CP Contingency Planning RA Risk Assessment IA Identification and Authentication SA System and Services Acquisition IR Incident Response
 Aeronautical Issues with Security Controls The CONOPS touches on many issues specific to the aeronautical industry: • • • Airline IT and maintenance have traditionally been separate Security patches and certification Lack of IT support on aircraft Long lifecycles from design to deployment and use Security and safety Etc.
Aeronautical Issues with Security Controls The CONOPS touches on many issues specific to the aeronautical industry: • • • Airline IT and maintenance have traditionally been separate Security patches and certification Lack of IT support on aircraft Long lifecycles from design to deployment and use Security and safety Etc.
 Summary • • The AEEC CONOPS identifies security process for airlines and discusses many aeronautical security issues Only known standard for overall security process – but can exploit Common Criteria, FISMA, and SCAP Process potentially applicable throughout the aeronautical industry FAA WJHTC Information Security Group is using the process within programs such as NEXCOM, Future Comms Study, CPDLC
Summary • • The AEEC CONOPS identifies security process for airlines and discusses many aeronautical security issues Only known standard for overall security process – but can exploit Common Criteria, FISMA, and SCAP Process potentially applicable throughout the aeronautical industry FAA WJHTC Information Security Group is using the process within programs such as NEXCOM, Future Comms Study, CPDLC


