8e94f338ecae265901fdf463451ac75f.ppt
- Количество слайдов: 24
 OUHSC Information Security Update IT, Information Security Services Randy Moore Mike Waller Nathan Gibson Greg Bostic
OUHSC Information Security Update IT, Information Security Services Randy Moore Mike Waller Nathan Gibson Greg Bostic
 Security Project Update (the three Ps) • Policy baseline completed – See http: //it. ouhsc. edu/policies/ • Perimeter firewall management project complete – – All externally accessible servers registered in db Firewall rules updated with db Servers scanned and vulnerabilities mitigated https: //www. ouhsc. edu/acl/admin 23/allacl. cfm • Private IPs for hosts on new network
Security Project Update (the three Ps) • Policy baseline completed – See http: //it. ouhsc. edu/policies/ • Perimeter firewall management project complete – – All externally accessible servers registered in db Firewall rules updated with db Servers scanned and vulnerabilities mitigated https: //www. ouhsc. edu/acl/admin 23/allacl. cfm • Private IPs for hosts on new network
 Security Personnel Update • • Kenneth Reed: moved to Engineering Nathan Gibson: moving on risk assessments Mike Waller is moving on to Charlotte Greg Bostic is moving into security
Security Personnel Update • • Kenneth Reed: moved to Engineering Nathan Gibson: moving on risk assessments Mike Waller is moving on to Charlotte Greg Bostic is moving into security
 New Projects • • Payment Card Industry Data Security Standard Risk Assessments Security policy implementation Active Directory Baseline Security Configuration
New Projects • • Payment Card Industry Data Security Standard Risk Assessments Security policy implementation Active Directory Baseline Security Configuration
 OUHSC Group Policy Objects
OUHSC Group Policy Objects
 Purpose • • • Compliance Security Ease administrative overhead High level Polices Only Tier 1 s can still apply organizational preferred settings • User “buy-in”
Purpose • • • Compliance Security Ease administrative overhead High level Polices Only Tier 1 s can still apply organizational preferred settings • User “buy-in”
 Time Line • 4 Week Implementation Life Cycle – Week 1: IT will create and test the AD GP settings. – Week 2 -4: Tier 1 s will apply and test each GP to their respective AD Organizational Unit (OU) and present feedback to IT. For settings that present a change for their end-users Tier 1’s should communicate those changes in advance to their user community. IT will assist in developing appropriate communications. – Week 5: IT will evaluate any feedback given and make necessary modification before applying the settings at the campus wide level.
Time Line • 4 Week Implementation Life Cycle – Week 1: IT will create and test the AD GP settings. – Week 2 -4: Tier 1 s will apply and test each GP to their respective AD Organizational Unit (OU) and present feedback to IT. For settings that present a change for their end-users Tier 1’s should communicate those changes in advance to their user community. IT will assist in developing appropriate communications. – Week 5: IT will evaluate any feedback given and make necessary modification before applying the settings at the campus wide level.
 Time Line(cont) • 20 Settings – Will be separate into 4 separate groups containing at most 3 sets of related settings to limit impact. Example:
Time Line(cont) • 20 Settings – Will be separate into 4 separate groups containing at most 3 sets of related settings to limit impact. Example:
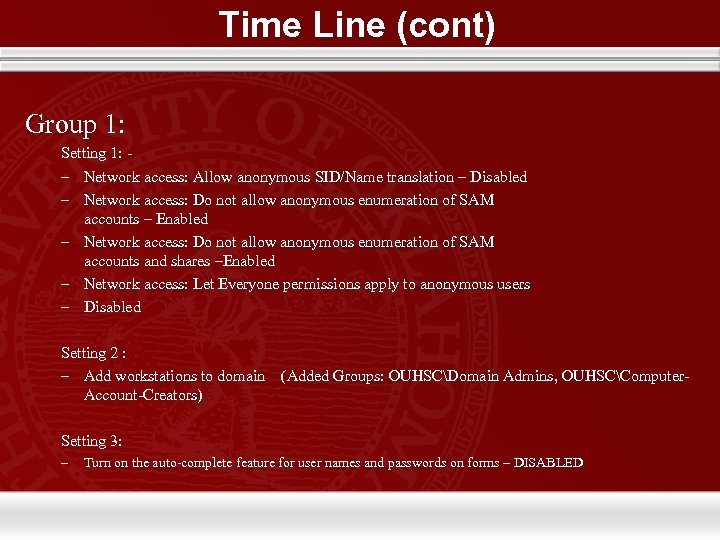 Time Line (cont) Group 1: Setting 1: – Network access: Allow anonymous SID/Name translation – Disabled – Network access: Do not allow anonymous enumeration of SAM accounts – Enabled – Network access: Do not allow anonymous enumeration of SAM accounts and shares –Enabled – Network access: Let Everyone permissions apply to anonymous users – Disabled Setting 2 : – Add workstations to domain Account-Creators) (Added Groups: OUHSCDomain Admins, OUHSCComputer- Setting 3: – Turn on the auto-complete feature for user names and passwords on forms – DISABLED
Time Line (cont) Group 1: Setting 1: – Network access: Allow anonymous SID/Name translation – Disabled – Network access: Do not allow anonymous enumeration of SAM accounts – Enabled – Network access: Do not allow anonymous enumeration of SAM accounts and shares –Enabled – Network access: Let Everyone permissions apply to anonymous users – Disabled Setting 2 : – Add workstations to domain Account-Creators) (Added Groups: OUHSCDomain Admins, OUHSCComputer- Setting 3: – Turn on the auto-complete feature for user names and passwords on forms – DISABLED
 IT Responsibilities • Create GPOs and configure settings • Assist Tier 1 s in communicating GPO results to users • Receive feedback from Tier 1 s and assist in resolving problems • Apply GPO settings at the Domain level after testing phase
IT Responsibilities • Create GPOs and configure settings • Assist Tier 1 s in communicating GPO results to users • Receive feedback from Tier 1 s and assist in resolving problems • Apply GPO settings at the Domain level after testing phase
 Tier 1 Responsibilities • Advise Users • Apply GPOs to Active Directory Organization Units • Give feedback to IT-OPS and IT-ISS
Tier 1 Responsibilities • Advise Users • Apply GPOs to Active Directory Organization Units • Give feedback to IT-OPS and IT-ISS
 GPO Review • Group Policy Objects: 1. Allows you to configure baseline settings to ensure all resources have them same settings 2. Ease the administrative overhead in applying and modifying end user device and servers. 3. “One-Stop-Shop” for demonstrating policy compliance
GPO Review • Group Policy Objects: 1. Allows you to configure baseline settings to ensure all resources have them same settings 2. Ease the administrative overhead in applying and modifying end user device and servers. 3. “One-Stop-Shop” for demonstrating policy compliance
 GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) 1. Start > Run > gpmc. msc
GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) 1. Start > Run > gpmc. msc
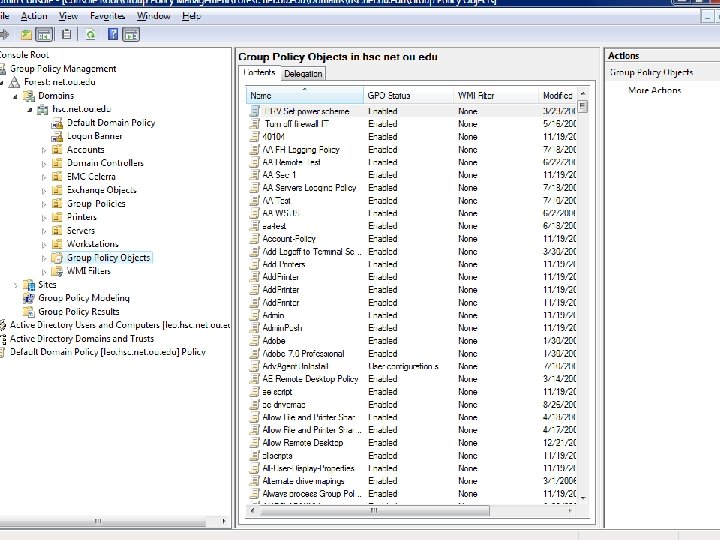
 GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU.
GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU.
 GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU 3. To apply the GPOs you right click on your OU and choose “Link an existing GPO”
GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU 3. To apply the GPOs you right click on your OU and choose “Link an existing GPO”
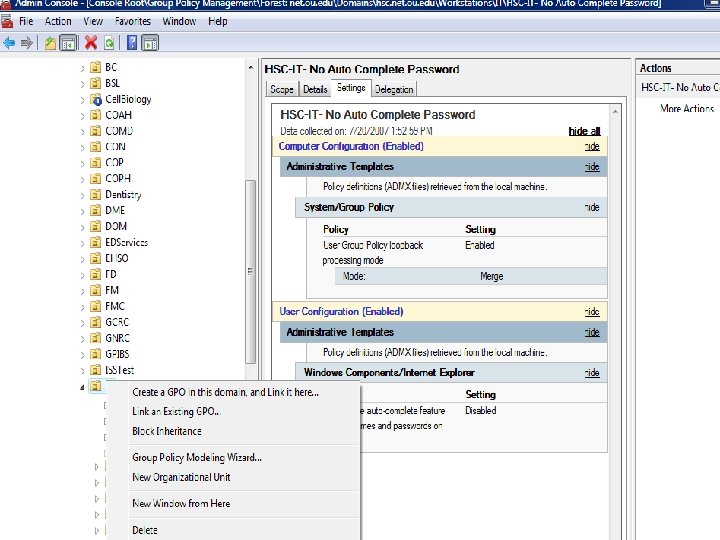
 GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU 3. To apply the GPOs you right click on your OU and choose “Link an existing GPO” 4. All GPOs that are in this project will have a common naming convention
GPO Review (cont) • Applying Group Policy Objects 1. Use MS built in Group Policy Management Console (gpmc. msc) a. Start > Run > gpmc. msc 2. Apply GPOs to your Workstations OU 3. To apply the GPOs you right click on your OU and choose “Link an existing GPO” 4. All GPOs that are in this project will have a common naming convention
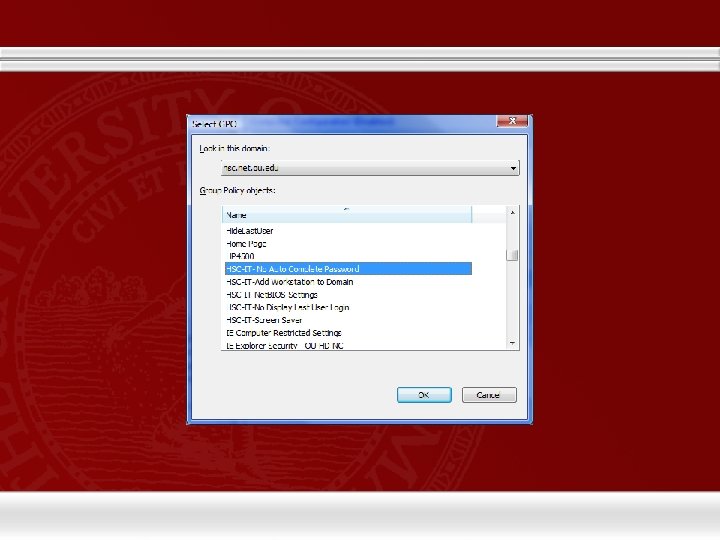
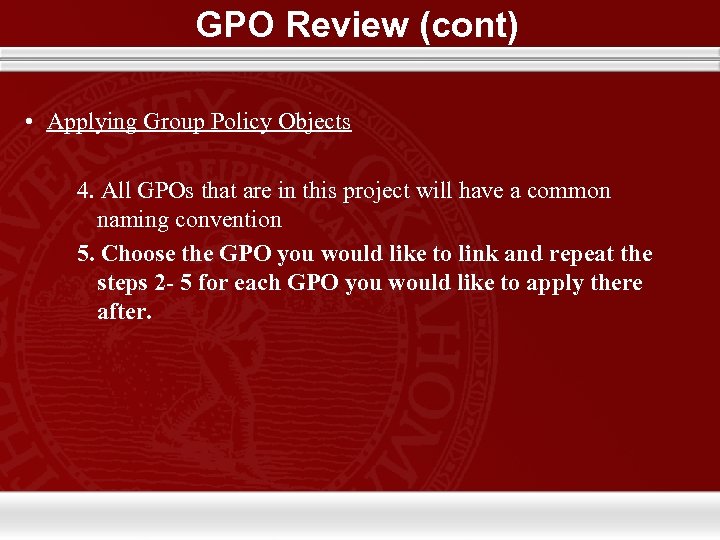 GPO Review (cont) • Applying Group Policy Objects 4. All GPOs that are in this project will have a common naming convention 5. Choose the GPO you would like to link and repeat the steps 2 - 5 for each GPO you would like to apply there after.
GPO Review (cont) • Applying Group Policy Objects 4. All GPOs that are in this project will have a common naming convention 5. Choose the GPO you would like to link and repeat the steps 2 - 5 for each GPO you would like to apply there after.
 House Cleaning Help • Clean up Computers OU • Standardize GPO naming scheme – – HSC-Dept-XXXX Delete Old GPOs Combine GPOs If possible Remove GPOs with settings applies at higher lever
House Cleaning Help • Clean up Computers OU • Standardize GPO naming scheme – – HSC-Dept-XXXX Delete Old GPOs Combine GPOs If possible Remove GPOs with settings applies at higher lever
 House Cleaning Help (cont)
House Cleaning Help (cont)
 Let’s Talk Questions & Concerns ? ? ?
Let’s Talk Questions & Concerns ? ? ?


