03064326c1217deeb7cc5e56d2fe1841.ppt
- Количество слайдов: 26

. ORG Public/Private Partnership for Netcentric Engineering Presentation to the Service Oriented Architecture for EGovernment Conference, May 1 -2, 2007 Chris. Gunderson@W 2 COG. org (o) 703 262 5332 (m) 831 224 5182 www. w 2 cog. org www. giglite. org


…(Lt Gen) Croom (Defense Information Systems Agency Director) said (military systems) should provide military information as easily as Travelocity …Croom invokes commercial success stories. . e. g. Google and Yahoo. . . said DISA would opt for a commercial approach* MYTH: Military Netcentric Operations is fundamentally different from commercial Ebusiness REALITY: “The world is flat!” (Tom Friedman NY Times)…. QUESTION: Is Google good enough? *FCW 7/11/05

Netcentric (i. e. , e-Gov) Biz Model: Flatten & Partner • Acquisition Community needs – – – • “Pointy End” Operational Communities need – – – • To efficiently survey possible solutions. To track operational community “market” trends Use-based contract incentives “Test drives” of live or downloadable use-case demos To pool resources for similar requirements Means to propagate investments in intellectual property To communicate via use-cases To Eliminate buffer between them and developers To collaborate on domain specific standards and schemas To integrate solutions through continuous low cost experimentation Hosting and inter-enterprise facilitation services Developer Communities need – To leverage and improve others’ solutions – To collaborate on technology standards and their uses. – Government certification to accelerate adoption and mitigate commercial risk

NR-KPP Challenge & Opportunity • CJCSI 6212. 01 D 8 Mar 06: “Net. Ready-KPP” (NR-KPP)/ NR-KPP Cert : “(Develop) …Verifiable performance measures …to assess information needs…” • DISA Joint Interoperability Test Command (JITC) directed to enforce the NR-KPP … But HOW? ? ?
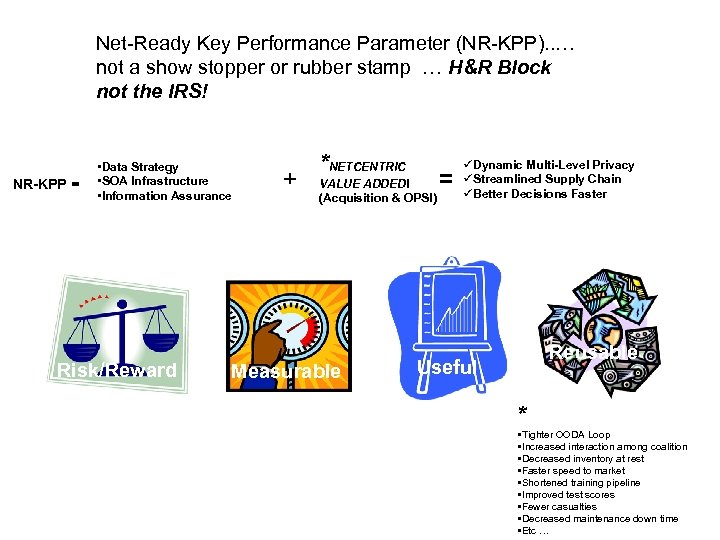
Net-Ready Key Performance Parameter (NR-KPP). . … not a show stopper or rubber stamp … H&R Block not the IRS! NR-KPP = • Data Strategy • SOA Infrastructure • Information Assurance Reward vs. Risk/Reward + *NETCENTRIC VALUE ADDED! (Acquisition & OPS!) Measurable = üDynamic Multi-Level Privacy üStreamlined Supply Chain üBetter Decisions Faster Useful Reusable Useful * • Tighter OODA Loop • Increased interaction among coalition • Decreased inventory at rest • Faster speed to market • Shortened training pipeline • Improved test scores • Fewer casualties • Decreased maintenance down time • Etc …
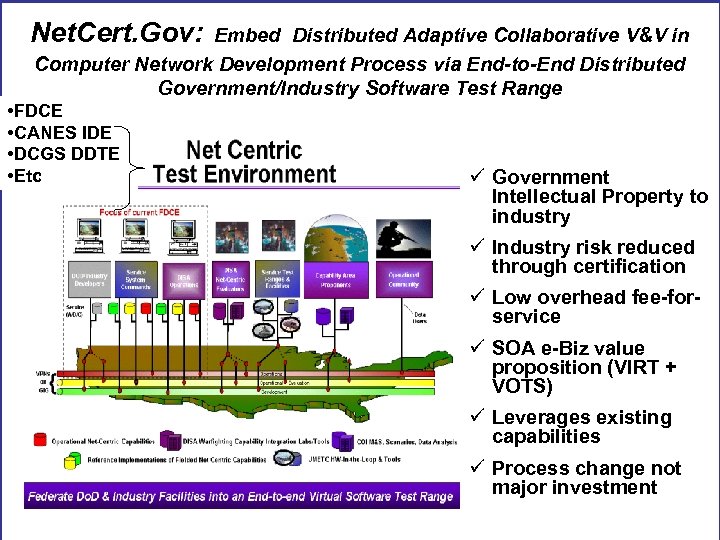
Net. Cert. Gov: Embed Distributed Adaptive Collaborative V&V in Computer Network Development Process via End-to-End Distributed Government/Industry Software Test Range • FDCE • CANES IDE • DCGS DDTE • Etc ü Government Intellectual Property to industry ü Industry risk reduced through certification ü Low overhead fee-forservice ü SOA e-Biz value proposition (VIRT + VOTS) ü Leverages existing capabilities ü Process change not major investment
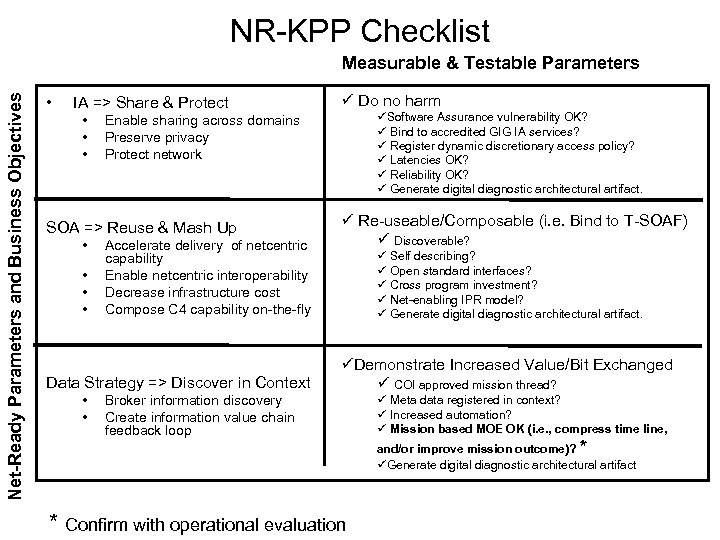
NR-KPP Checklist Net-Ready Parameters and Business Objectives Measurable & Testable Parameters • IA => Share & Protect • • • Accelerate delivery of netcentric capability Enable netcentric interoperability Decrease infrastructure cost Compose C 4 capability on-the-fly Data Strategy => Discover in Context • • üSoftware Assurance vulnerability OK? ü Bind to accredited GIG IA services? ü Register dynamic discretionary access policy? ü Latencies OK? ü Reliability OK? ü Generate digital diagnostic architectural artifact. Enable sharing across domains Preserve privacy Protect network SOA => Reuse & Mash Up • ü Do no harm Broker information discovery Create information value chain feedback loop ü Re-useable/Composable (i. e. Bind to T-SOAF) ü Discoverable? ü Self describing? ü Open standard interfaces? ü Cross program investment? ü Net-enabling IPR model? ü Generate digital diagnostic architectural artifact. üDemonstrate Increased Value/Bit Exchanged ü COI approved mission thread? * Confirm with operational evaluation ü Meta data registered in context? ü Increased automation? ü Mission based MOE OK (i. e. , compress time line, and/or improve mission outcome)? * üGenerate digital diagnostic architectural artifact
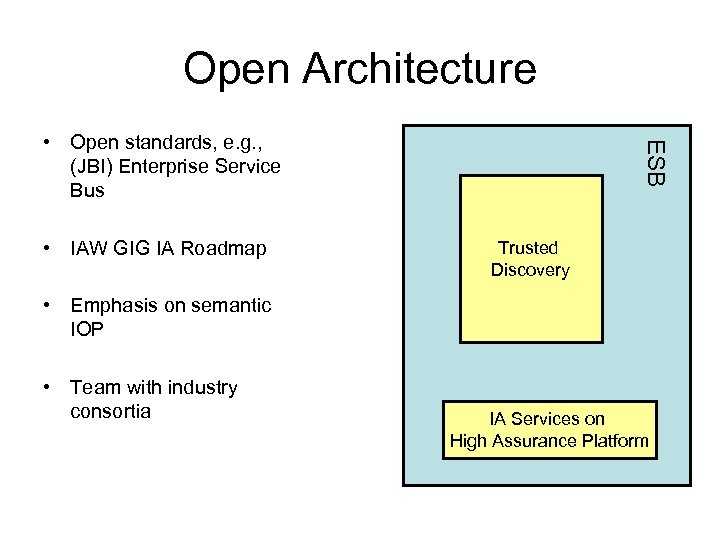
Open Architecture • IAW GIG IA Roadmap ESB • Open standards, e. g. , (JBI) Enterprise Service Bus Trusted Discovery • Emphasis on semantic IOP • Team with industry consortia IA Services on High Assurance Platform
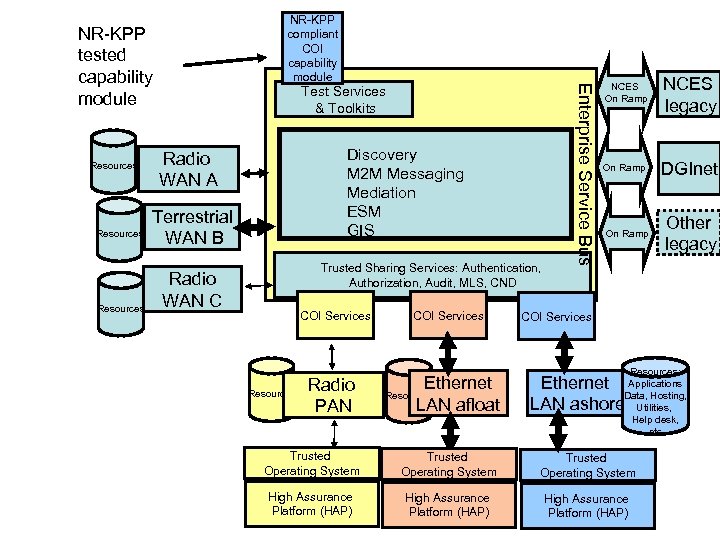
NR-KPP tested capability module Resources Test Services & Toolkits Discovery M 2 M Messaging Mediation ESM GIS Radio WAN A Terrestrial WAN B Trusted Sharing Services: Authentication, Authorization, Audit, MLS, CND Radio WAN C COI Services Resources Radio PAN COI Services Ethernet LAN afloat Resources Enterprise Service Bus NR-KPP compliant COI capability module NCES On Ramp NCES legacy On Ramp DGInet On Ramp Other legacy COI Services Resources: Applications Data, Hosting, Utilities, Help desk, etc Ethernet LAN ashore Trusted Operating System High Assurance Platform (HAP)

W 2 COG Institute: Enabling Trusted Transactions of Valuable Information at the Right Time • An international, collaborative association of networking technology and operational experts • A brokering service that efficiently puts expert providers in touch with customers • An open GIGlite. org on-line environment for rapid prototyping ventures among self-selecting industry, government, and academic experts and dynamic repository of net-ready capability bundles
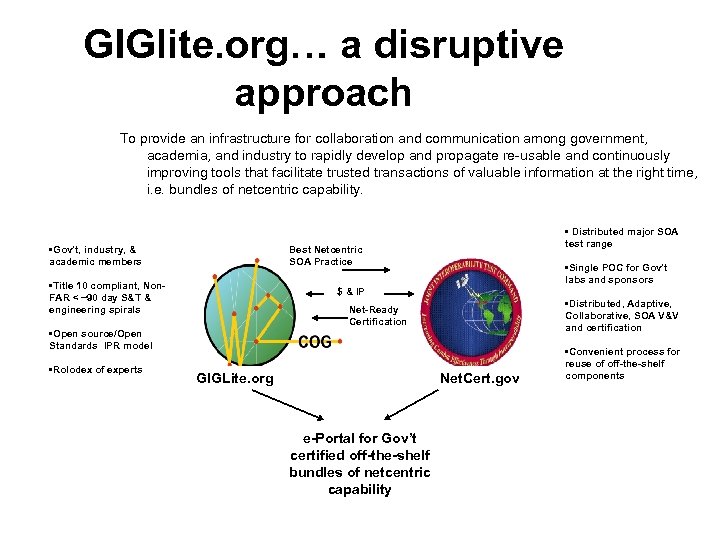
GIGlite. org… a disruptive approach To provide an infrastructure for collaboration and communication among government, academia, and industry to rapidly develop and propagate re-usable and continuously improving tools that facilitate trusted transactions of valuable information at the right time, i. e. bundles of netcentric capability. • Gov’t, industry, & academic members • Distributed major SOA test range Best Netcentric SOA Practice • Title 10 compliant, Non. FAR < ~90 day S&T & engineering spirals • Single POC for Gov’t labs and sponsors $ & IP • Distributed, Adaptive, Collaborative, SOA V&V and certification Net-Ready Certification • Open source/Open Standards IPR model • Rolodex of experts GIGLite. org Net. Cert. gov e-Portal for Gov’t certified off-the-shelf bundles of netcentric capability • Convenient process for reuse of off-the-shelf components
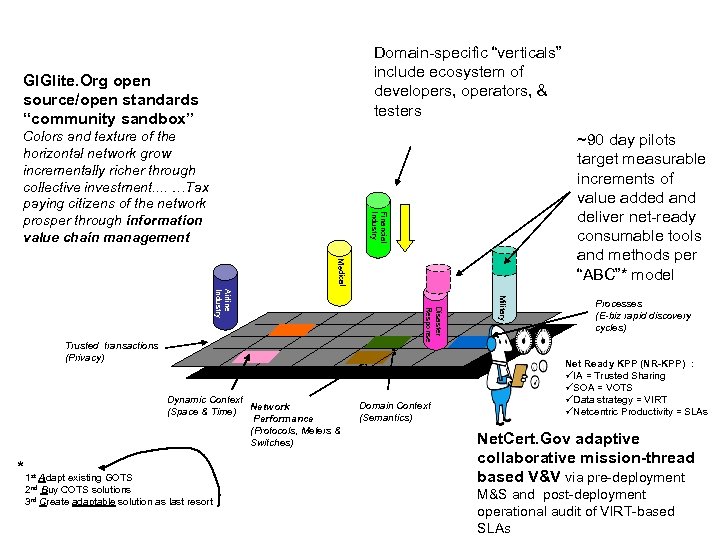
Domain-specific “verticals” include ecosystem of developers, operators, & testers GIGlite. Org open source/open standards “community sandbox” ~90 day pilots target measurable increments of value added and deliver net-ready consumable tools and methods per “ABC”* model Financial Industry Colors and texture of the horizontal network grow incrementally richer through collective investment. . …Tax paying citizens of the network prosper through information value chain management Medical *1 Adapt existing GOTS 2 nd Buy COTS solutions 3 rd Create adaptable solution as last resort st Domain Context (Semantics) Military Dynamic Context (Space & Time) Network Performance (Protocols, Meters & Switches) Disaster Response Airline Industry Trusted transactions (Privacy) Processes (E-biz rapid discovery cycles) Net Ready KPP (NR-KPP) : üIA = Trusted Sharing üSOA = VOTS üData strategy = VIRT üNetcentric Productivity = SLAs Net. Cert. Gov adaptive collaborative mission-thread based V&V via pre-deployment M&S and post-deployment operational audit of VIRT-based SLAs
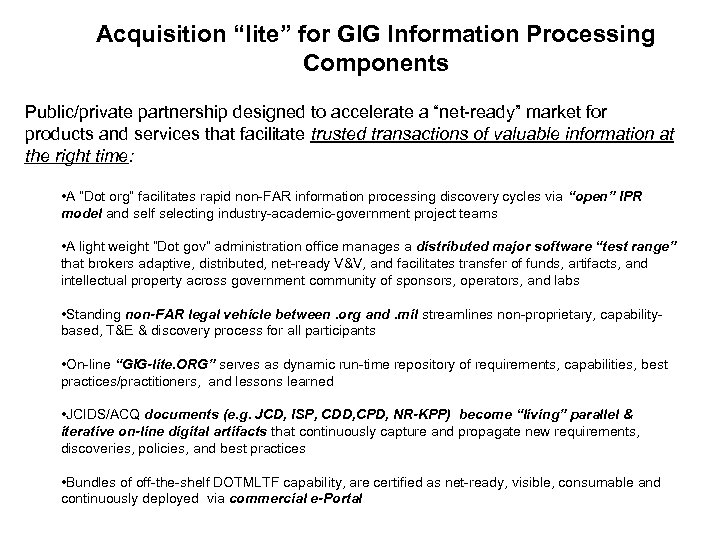
Acquisition “lite” for GIG Information Processing Components Public/private partnership designed to accelerate a “net-ready” market for products and services that facilitate trusted transactions of valuable information at the right time: • A “Dot org” facilitates rapid non-FAR information processing discovery cycles via “open” IPR model and self selecting industry-academic-government project teams • A light weight “Dot gov” administration office manages a distributed major software “test range” that brokers adaptive, distributed, net-ready V&V, and facilitates transfer of funds, artifacts, and intellectual property across government community of sponsors, operators, and labs • Standing non-FAR legal vehicle between. org and. mil streamlines non-proprietary, capabilitybased, T&E & discovery process for all participants • On-line “GIG-lite. ORG” serves as dynamic run-time repository of requirements, capabilities, best practices/practitioners, and lessons learned • JCIDS/ACQ documents (e. g. JCD, ISP, CDD, CPD, NR-KPP) become “living” parallel & iterative on-line digital artifacts that continuously capture and propagate new requirements, discoveries, policies, and best practices • Bundles of off-the-shelf DOTMLTF capability, are certified as net-ready, visible, consumable and continuously deployed via commercial e-Portal
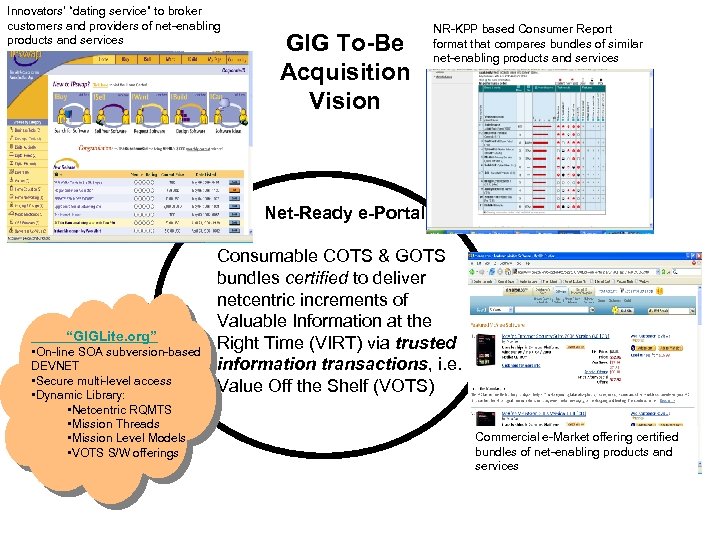
Innovators’ “dating service” to broker customers and providers of net-enabling products and services GIG To-Be Acquisition Vision NR-KPP based Consumer Report format that compares bundles of similar net-enabling products and services Net-Ready e-Portal “GIGLite. org” • On-line SOA subversion-based DEVNET • Secure multi-level access • Dynamic Library: • Netcentric RQMTS • Mission Threads • Mission Level Models • VOTS S/W offerings Consumable COTS & GOTS bundles certified to deliver netcentric increments of Valuable Information at the Right Time (VIRT) via trusted information transactions, i. e. Value Off the Shelf (VOTS) Commercial e-Market offering certified bundles of net-enabling products and services

Join US • www. GIGlite. org – “Trustworthy” ESB – CANES RFI Response – DDTE Testing-as-a-Service Workshop Norfolk 14 June • Practical Guide to Federal SOA – http: //colab. cim 3. net Pgf. SOA Infra. Structure/Draft. One

BACKUP

Approach • Use “ABC”* approach to build SOA Baseline = GIGLite. org Spiral 0 • Test IA, SOA, and data strategy re: – 1. Do no (unacceptable) harm – 2. Bind to the SOA Foundation: • Discoverable • Self describing • Open interfaces – 3. Demonstrate netcentric value added • Leverage “. org” to minimize bureaucracy and overhead = provide valuable service to developer and customer *ABC = Adapt existing capability or Buy COTS before Creating specialized capabilty
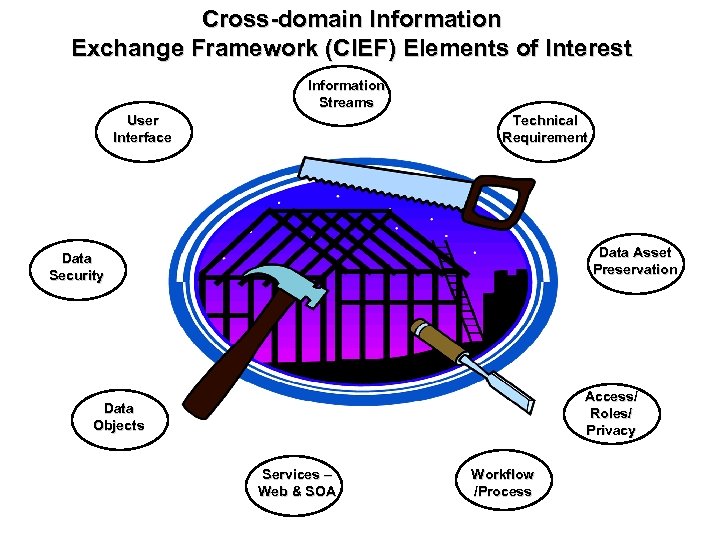
Cross-domain Information Exchange Framework (CIEF) Elements of Interest Information Streams User Interface Technical Requirement Data Asset Preservation Data Security Access/ Roles/ Privacy Data Objects Services – Web & SOA Workflow /Process
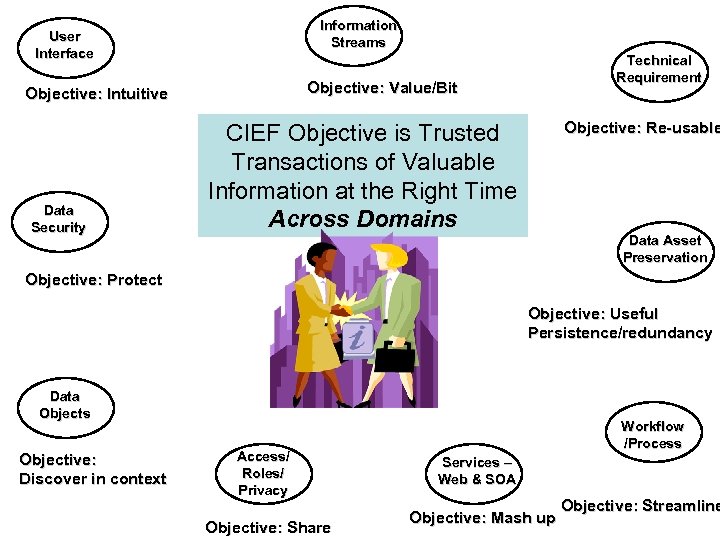
Information Streams User Interface Objective: Value/Bit Objective: Intuitive Data Security Technical Requirement Objective: Re-usable CIEF Objective is Trusted Transactions of Valuable Information at the Right Time Across Domains Data Asset Preservation Objective: Protect Objective: Useful Persistence/redundancy Data Objects Objective: Discover in context Access/ Roles/ Privacy Objective: Share Workflow /Process Services – Web & SOA Objective: Mash up Objective: Streamline

GIGlite. org Logical Stack Business Process Utilities & Services. Objective is Continuous Improvement Publish/Subscribe Utilities & Services: Objective is Seamless Delivery of Value in Context Identity/Privacy Utilities & Services: Objective is Trusted Transactions Computer Network Defense and Software Assurance Utilities & Services: Objective is Protection of Assets

S 2 OAF Technology Stack = NCES legacy + Best of Breed GOTs + OTD + Managed Services via ESB – Security • • • Trusted Authorization Broker (TAB) Trusted Authorization Policy Engine (TAPE) CAC V-LDAP Cyber Operation Information System – Discovery NCES On Ramp • • • – Messaging • • –The DISA Appliance bundles the NCES Services into a single deployment component that is accessible via “NCES on ramp” toolkit to deliver NCES capabilities to ESBs. 3 DV Open Source registry DGInet geospatial services M 2 mi xxx M 2 MI xxx JBI Middleware – Mediation • • • NCES on ramp Commercially viable JBI Enterprise Service Bus SOA tool kits (e. g. Jumpstart, C/JMTK) – ESM • SPAWAR Cross-domain Information Exchange Framework via GIGLite Collabnet Portal – NR-KPP Test Services • • • M&S web suite Web SOA test bench Center fro Assured Software (CAS) evaluation

NR-KPP tested capability module Resources Network A Resources Network C = NCES enabled application or utility = Later spiral enterprise service = S 2 OAF spiral 0 CAC DGInet NCES On Ramp Test Services Trusted: Discovery Messaging Mediation ESM TAB Resources Jumpstart Toolkit To be NCES Foundation Service M 2 MI VIRT engine 3 DVE Registry V-LDAP Other JBI ESB Middle Ware Trusted Service Engine (TSE) TAPE System Assurance OS layer (COIS? ) Operating System High Assurance Platform (HAP) JBI Enterprise Service Bus Network B NR-KPP compliant COI capability module To Be NR-KPP compliant application Service On Ramp C/JMTK NCES legacy Other legacy
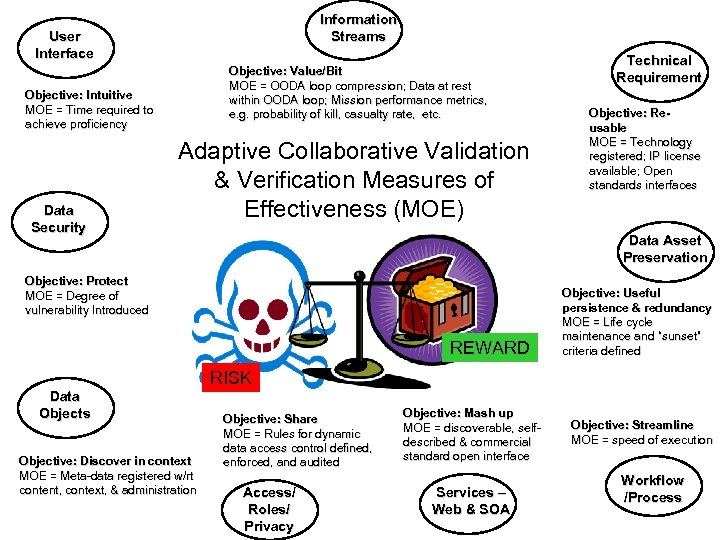
Information Streams User Interface Objective: Value/Bit MOE = OODA loop compression; Data at rest within OODA loop; Mission performance metrics, e. g. probability of kill, casualty rate, etc. Objective: Intuitive MOE = Time required to achieve proficiency Data Security Adaptive Collaborative Validation & Verification Measures of Effectiveness (MOE) Technical Requirement Objective: Reusable MOE = Technology registered; IP license available; Open standards interfaces Data Asset Preservation Objective: Protect MOE = Degree of vulnerability Introduced REWARD Objective: Useful persistence & redundancy MOE = Life cycle maintenance and “sunset” criteria defined RISK Data Objects Objective: Discover in context MOE = Meta-data registered w/rt content, context, & administration Objective: Share MOE = Rules for dynamic data access control defined, enforced, and audited Access/ Roles/ Privacy Objective: Mash up MOE = discoverable, selfdescribed & commercial standard open interface Services – Web & SOA Objective: Streamline MOE = speed of execution Workflow /Process
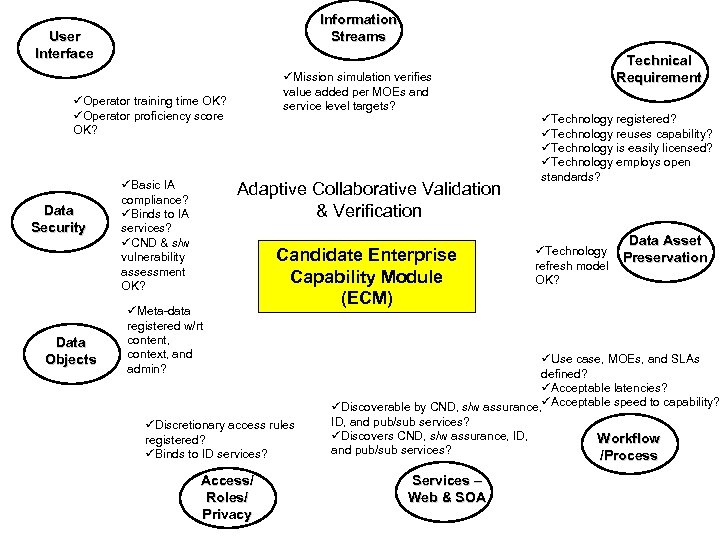
Information Streams User Interface üMission simulation verifies value added per MOEs and service level targets? üOperator training time OK? üOperator proficiency score OK? Data Security Data Objects üBasic IA compliance? üBinds to IA services? üCND & s/w vulnerability assessment OK? Adaptive Collaborative Validation & Verification üMeta-data registered w/rt content, context, and admin? Candidate Enterprise Capability Module (ECM) üDiscretionary access rules registered? üBinds to ID services? Access/ Roles/ Privacy Technical Requirement üTechnology registered? üTechnology reuses capability? üTechnology is easily licensed? üTechnology employs open standards? üTechnology refresh model OK? Data Asset Preservation üUse case, MOEs, and SLAs defined? üAcceptable latencies? üDiscoverable by CND, s/w assurance, üAcceptable speed to capability? ID, and pub/sub services? üDiscovers CND, s/w assurance, ID, and pub/sub services? Services – Web & SOA Workflow /Process
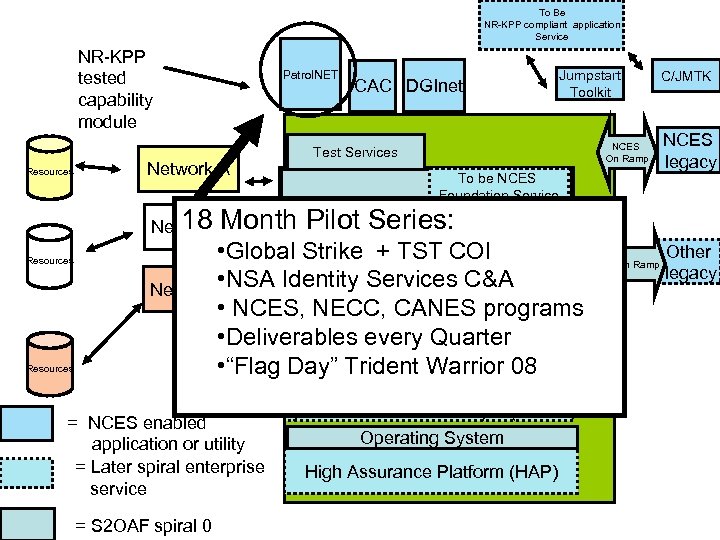
To Be NR-KPP compliant application Service NR-KPP tested capability module Patrol. NET CAC DGInet Jumpstart Toolkit NCES On Ramp Test Services Network A Resources 18 B Pilot Network Month. Trusted: Series: • Global. Discovery + TST COIRegistry Strike 3 DVE Messaging C&A Mediation Network • NSA Identity Services V-LDAP C ESM • NCES, NECC, CANES programs Other JBI ESB To be NCES Foundation Service M 2 MI VIRT engine Middle Ware • Deliverables every Quarter Trusted • “Flag Day” Trident Service Warrior 08 TAB TAPE Resources Engine (TSE) = NCES enabled application or utility = Later spiral enterprise service = S 2 OAF spiral 0 System Assurance OS layer (COIS? ) Operating System High Assurance Platform (HAP) JBI Enterprise Service Bus Resources On Ramp C/JMTK NCES legacy Other legacy
03064326c1217deeb7cc5e56d2fe1841.ppt