7d8315744fd84cc288af7339f7bebba7.ppt
- Количество слайдов: 20
 Optimization of intrusion detection systems for wireless sensor networks using evolutionary algorithms Martin Stehlík Faculty of Informatics Masaryk University Brno
Optimization of intrusion detection systems for wireless sensor networks using evolutionary algorithms Martin Stehlík Faculty of Informatics Masaryk University Brno
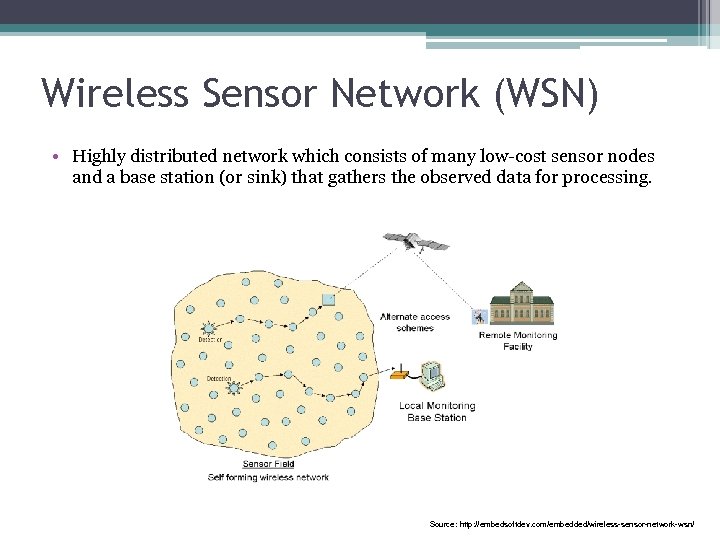 Wireless Sensor Network (WSN) • Highly distributed network which consists of many low-cost sensor nodes and a base station (or sink) that gathers the observed data for processing. Source: http: //embedsoftdev. com/embedded/wireless-sensor-network-wsn/
Wireless Sensor Network (WSN) • Highly distributed network which consists of many low-cost sensor nodes and a base station (or sink) that gathers the observed data for processing. Source: http: //embedsoftdev. com/embedded/wireless-sensor-network-wsn/
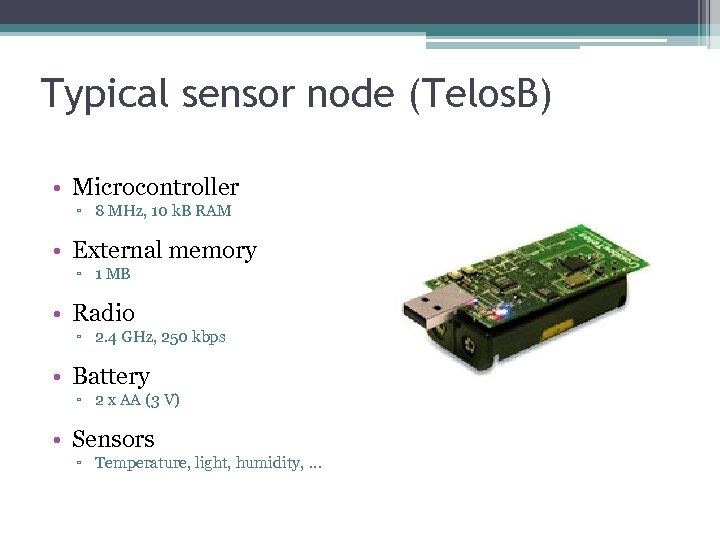 Typical sensor node (Telos. B) • Microcontroller ▫ 8 MHz, 10 k. B RAM • External memory ▫ 1 MB • Radio ▫ 2. 4 GHz, 250 kbps • Battery ▫ 2 x AA (3 V) • Sensors ▫ Temperature, light, humidity, …
Typical sensor node (Telos. B) • Microcontroller ▫ 8 MHz, 10 k. B RAM • External memory ▫ 1 MB • Radio ▫ 2. 4 GHz, 250 kbps • Battery ▫ 2 x AA (3 V) • Sensors ▫ Temperature, light, humidity, …
 Security • Sensor nodes: ▫ Communicate wirelessly. ▫ Have lower computational capabilities. ▫ Have limited energy supply. ▫ Can be easily captured. ▫ Are not tamper-resistant. • WSNs are deployed in hostile environment. • WSNs are more vulnerable than conventional networks by their nature.
Security • Sensor nodes: ▫ Communicate wirelessly. ▫ Have lower computational capabilities. ▫ Have limited energy supply. ▫ Can be easily captured. ▫ Are not tamper-resistant. • WSNs are deployed in hostile environment. • WSNs are more vulnerable than conventional networks by their nature.
 Attacker model • Passive attacker ▫ Eavesdrops on transmissions. • Active attacker ▫ Alters data. ▫ Drops or selectively forwards packets. ▫ Replays packets. ▫ Injects packets. ▫ Jams the network. => can be detected by Intrusion Detection System.
Attacker model • Passive attacker ▫ Eavesdrops on transmissions. • Active attacker ▫ Alters data. ▫ Drops or selectively forwards packets. ▫ Replays packets. ▫ Injects packets. ▫ Jams the network. => can be detected by Intrusion Detection System.
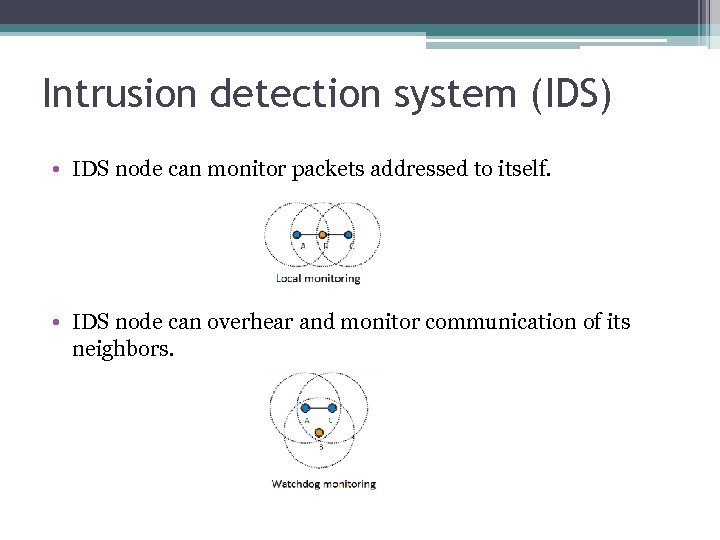 Intrusion detection system (IDS) • IDS node can monitor packets addressed to itself. • IDS node can overhear and monitor communication of its neighbors.
Intrusion detection system (IDS) • IDS node can monitor packets addressed to itself. • IDS node can overhear and monitor communication of its neighbors.
 IDS techniques • Many techniques have been proposed to detect different attacks. • We can measure: ▫ Packet sent & delivery ratio. ▫ Packet sending & receiving rate. ▫ Carrier sensing time. ▫ Sending power. • And monitor: ▫ Packet alteration. ▫ Dropping.
IDS techniques • Many techniques have been proposed to detect different attacks. • We can measure: ▫ Packet sent & delivery ratio. ▫ Packet sending & receiving rate. ▫ Carrier sensing time. ▫ Sending power. • And monitor: ▫ Packet alteration. ▫ Dropping.
 IDS optimization • Sensor nodes are limited in their energy and memory. • Better IDS accuracy usually requires: ▫ Energy (network lifetime). ▫ Memory (restriction to other applications). Þ Trade-off between IDS accuracy and WSN performance and lifetime. High-level aim: • Framework for (semi)automated design and optimization of IDS parameters.
IDS optimization • Sensor nodes are limited in their energy and memory. • Better IDS accuracy usually requires: ▫ Energy (network lifetime). ▫ Memory (restriction to other applications). Þ Trade-off between IDS accuracy and WSN performance and lifetime. High-level aim: • Framework for (semi)automated design and optimization of IDS parameters.
 Why do we simulate WSN? • Time of implementation and runtime (e. g. battery depletion). • Simulation of hundreds or thousands sensor nodes. • Verifiability of results. • Repeatability of tests. • Protocols that work during simulations may fail in real environment because of simplicity of the model. ▫ Thorough comparison of simulators with reality can be found in [SSM 11].
Why do we simulate WSN? • Time of implementation and runtime (e. g. battery depletion). • Simulation of hundreds or thousands sensor nodes. • Verifiability of results. • Repeatability of tests. • Protocols that work during simulations may fail in real environment because of simplicity of the model. ▫ Thorough comparison of simulators with reality can be found in [SSM 11].
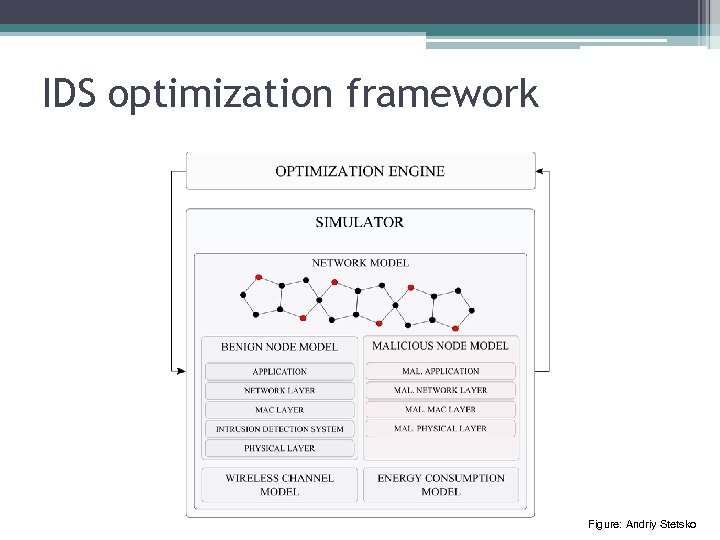 IDS optimization framework Figure: Andriy Stetsko
IDS optimization framework Figure: Andriy Stetsko
 Simulator • Input: candidate solution represented as a simulation configuration. ▫ Number of monitored neighbors. ▫ Max. number of buffered packets. ▫ … • Output: statistics of a simulation. ▫ Detection accuracy. ▫ Memory and energy consumption. • Simulation: specific WSN running predefined time configured according to the candidate solution.
Simulator • Input: candidate solution represented as a simulation configuration. ▫ Number of monitored neighbors. ▫ Max. number of buffered packets. ▫ … • Output: statistics of a simulation. ▫ Detection accuracy. ▫ Memory and energy consumption. • Simulation: specific WSN running predefined time configured according to the candidate solution.
 Optimization engine • Input: statistics from the simulator. ▫ Detection accuracy. ▫ Memory and energy consumption. • Output: new candidate solution(s) in form of simulation configurations. ▫ Number of monitored neighbors. ▫ Max. number of buffered packets. ▫ … • Algorithms: evolutionary algorithms, particle swarm optimization, simulated annealing, …
Optimization engine • Input: statistics from the simulator. ▫ Detection accuracy. ▫ Memory and energy consumption. • Output: new candidate solution(s) in form of simulation configurations. ▫ Number of monitored neighbors. ▫ Max. number of buffered packets. ▫ … • Algorithms: evolutionary algorithms, particle swarm optimization, simulated annealing, …
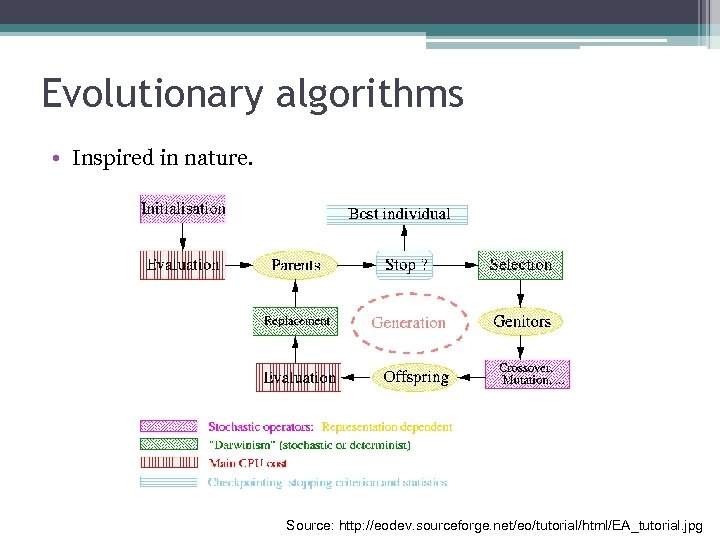 Evolutionary algorithms • Inspired in nature. Source: http: //eodev. sourceforge. net/eo/tutorial/html/EA_tutorial. jpg
Evolutionary algorithms • Inspired in nature. Source: http: //eodev. sourceforge. net/eo/tutorial/html/EA_tutorial. jpg
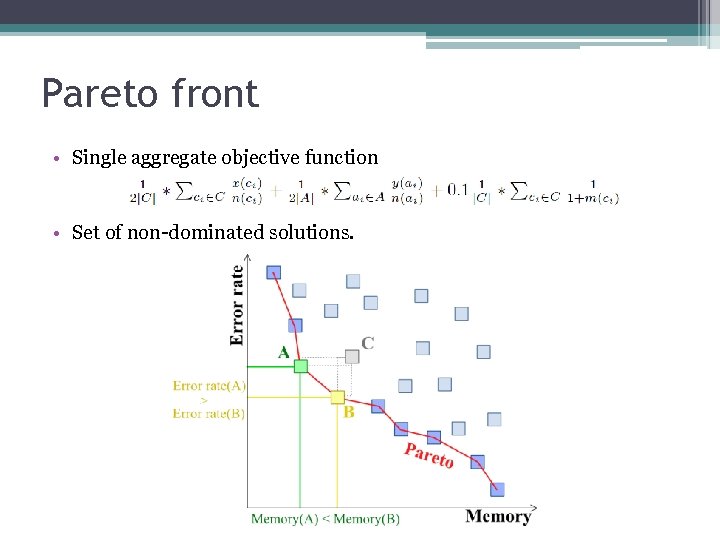 Pareto front • Single aggregate objective function • Set of non-dominated solutions.
Pareto front • Single aggregate objective function • Set of non-dominated solutions.
![Our test case • Pareto front. Source: [SSSM 13] Our test case • Pareto front. Source: [SSSM 13]](https://present5.com/presentation/7d8315744fd84cc288af7339f7bebba7/image-15.jpg) Our test case • Pareto front. Source: [SSSM 13]
Our test case • Pareto front. Source: [SSSM 13]
![Multi-objective evolutionary algorithms • What did the evolution find? Source: [SSSM 13] Multi-objective evolutionary algorithms • What did the evolution find? Source: [SSSM 13]](https://present5.com/presentation/7d8315744fd84cc288af7339f7bebba7/image-16.jpg) Multi-objective evolutionary algorithms • What did the evolution find? Source: [SSSM 13]
Multi-objective evolutionary algorithms • What did the evolution find? Source: [SSSM 13]
 Conclusion • Utilization of MOEAs in unexplored areas of research. • MOEAs enable to choose between optimized solutions according to our requirements. • Main goal: working IDS framework for WSNs. ▫ Design of robust solutions for large WSNs, enabling detection of various attacks.
Conclusion • Utilization of MOEAs in unexplored areas of research. • MOEAs enable to choose between optimized solutions according to our requirements. • Main goal: working IDS framework for WSNs. ▫ Design of robust solutions for large WSNs, enabling detection of various attacks.
 Acknowledgments • This work was supported by the project VG 20102014031, programme BV II/2 - VS, of the Ministry of the Interior of the Czech Republic.
Acknowledgments • This work was supported by the project VG 20102014031, programme BV II/2 - VS, of the Ministry of the Interior of the Czech Republic.
 Thank you for your attention.
Thank you for your attention.
![References • [SSM 11] A. Stetsko, M. Stehlík, and V. Matyáš. Calibrating and comparing References • [SSM 11] A. Stetsko, M. Stehlík, and V. Matyáš. Calibrating and comparing](https://present5.com/presentation/7d8315744fd84cc288af7339f7bebba7/image-20.jpg) References • [SSM 11] A. Stetsko, M. Stehlík, and V. Matyáš. Calibrating and comparing simulators for wireless sensor networks. In Proceedings of the 8 th IEEE International Conference on Mobile Adhoc and Sensor Systems, MASS '11, pages 733 -738, Los Alamitos, CA, USA, 2011. IEEE Computer Society. • [SSSM 13] M. Stehlík, A. Saleh, A. Stetsko, and V. Matyáš. Multi-Objective Optimization of Intrusion Detection Systems for Wireless Sensor Networks. Submitted to 12 th European Conference on Artificial Life. • [SMS 13] A. Stetsko, V. Matyáš, and M. Stehlík. A Framework for optimization of intrusion detection system parameters in wireless sensor networks. Prepared for a journal submission.
References • [SSM 11] A. Stetsko, M. Stehlík, and V. Matyáš. Calibrating and comparing simulators for wireless sensor networks. In Proceedings of the 8 th IEEE International Conference on Mobile Adhoc and Sensor Systems, MASS '11, pages 733 -738, Los Alamitos, CA, USA, 2011. IEEE Computer Society. • [SSSM 13] M. Stehlík, A. Saleh, A. Stetsko, and V. Matyáš. Multi-Objective Optimization of Intrusion Detection Systems for Wireless Sensor Networks. Submitted to 12 th European Conference on Artificial Life. • [SMS 13] A. Stetsko, V. Matyáš, and M. Stehlík. A Framework for optimization of intrusion detection system parameters in wireless sensor networks. Prepared for a journal submission.


