18dd883307419c33bdc4fd4740a9c780.ppt
- Количество слайдов: 38
 Operating Systems Unit 11: – Security
Operating Systems Unit 11: – Security
 Security • prevent unauthorized access to resources and information maintained by computers • issues: – Guarantee the privacy and integrity of data – Restricting the use of computer resources – Providing resilience against malicious attempts to incapacitate the system COP 5994 - Operating Systems 2
Security • prevent unauthorized access to resources and information maintained by computers • issues: – Guarantee the privacy and integrity of data – Restricting the use of computer resources – Providing resilience against malicious attempts to incapacitate the system COP 5994 - Operating Systems 2
 Security Mechanisms • Encryption: – Transform data into something that an attacker cannot understand (confidentiality) – check whether something has been modified (integrity) • Authentication: – verify the identity of a subject • Authorization: – determine if a subject is permitted to request service • Auditing: – trace subjects and requests – can help catch an attacker COP 5994 - Operating Systems 3
Security Mechanisms • Encryption: – Transform data into something that an attacker cannot understand (confidentiality) – check whether something has been modified (integrity) • Authentication: – verify the identity of a subject • Authorization: – determine if a subject is permitted to request service • Auditing: – trace subjects and requests – can help catch an attacker COP 5994 - Operating Systems 3
 Encryption • Goal: data readable only to intended reader • Cryptography: – encode and decode data – based on cypher: • function to encode/decode data • ex: substitution cypher, transposition cypher – modern cypher has key • parameter to encoding/decoding function COP 5994 - Operating Systems 4
Encryption • Goal: data readable only to intended reader • Cryptography: – encode and decode data – based on cypher: • function to encode/decode data • ex: substitution cypher, transposition cypher – modern cypher has key • parameter to encoding/decoding function COP 5994 - Operating Systems 4
 Cryptography • issue: key length – 64 bit, 128 bit, … • symmetric – 1 key for encoding and decoding – problem: key needs to be known to both parties • asymmetric – 2 keys COP 5994 - Operating Systems 5
Cryptography • issue: key length – 64 bit, 128 bit, … • symmetric – 1 key for encoding and decoding – problem: key needs to be known to both parties • asymmetric – 2 keys COP 5994 - Operating Systems 5
 Secret-Key Cryptography • symmetric cryptography • one secret key to encrypt / decrypt message – Sender • Encrypts a message using the secret key • Sends encrypted message to the intended recipient – Recipient • Decrypts the message using the same secret key COP 5994 - Operating Systems 6
Secret-Key Cryptography • symmetric cryptography • one secret key to encrypt / decrypt message – Sender • Encrypts a message using the secret key • Sends encrypted message to the intended recipient – Recipient • Decrypts the message using the same secret key COP 5994 - Operating Systems 6
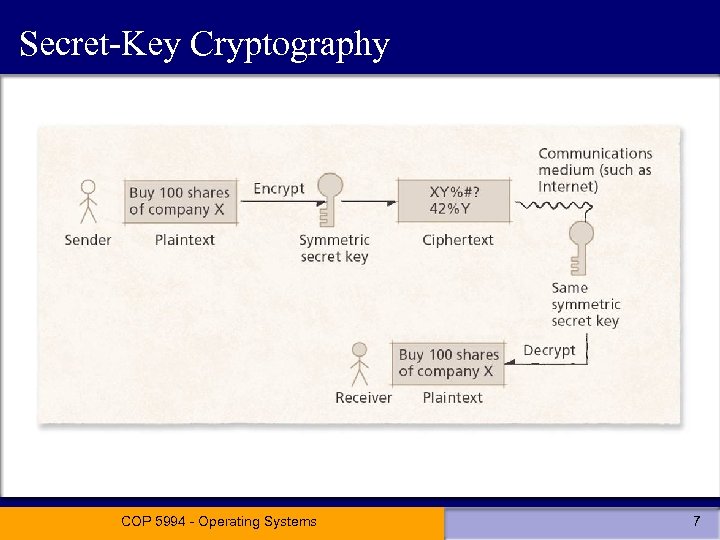 Secret-Key Cryptography COP 5994 - Operating Systems 7
Secret-Key Cryptography COP 5994 - Operating Systems 7
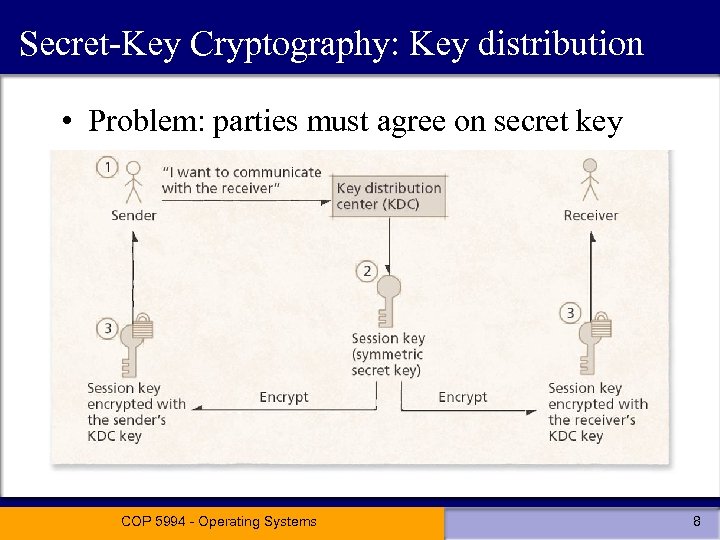 Secret-Key Cryptography: Key distribution • Problem: parties must agree on secret key COP 5994 - Operating Systems 8
Secret-Key Cryptography: Key distribution • Problem: parties must agree on secret key COP 5994 - Operating Systems 8
 Public-Key Cryptography • Asymmetric: – Employs two inversely related keys: • Public key – Freely distributed • Private key – Kept secret by its owner – If the public key encrypts a message, only the corresponding private key can decrypt it COP 5994 - Operating Systems 9
Public-Key Cryptography • Asymmetric: – Employs two inversely related keys: • Public key – Freely distributed • Private key – Kept secret by its owner – If the public key encrypts a message, only the corresponding private key can decrypt it COP 5994 - Operating Systems 9
 Public-Key Cryptography • Scenarios: – sender encrypts message with receivers public key – receiver decrypts message with private key – result: sender has authorized receiver COP 5994 - Operating Systems 10
Public-Key Cryptography • Scenarios: – sender encrypts message with receivers public key – receiver decrypts message with private key – result: sender has authorized receiver COP 5994 - Operating Systems 10
 Public-Key Cryptography • Scenarios: – sender encrypts message with private key – receiver decrypts message with sender’s public key – result: receiver has authenticated sender COP 5994 - Operating Systems 11
Public-Key Cryptography • Scenarios: – sender encrypts message with private key – receiver decrypts message with sender’s public key – result: receiver has authenticated sender COP 5994 - Operating Systems 11
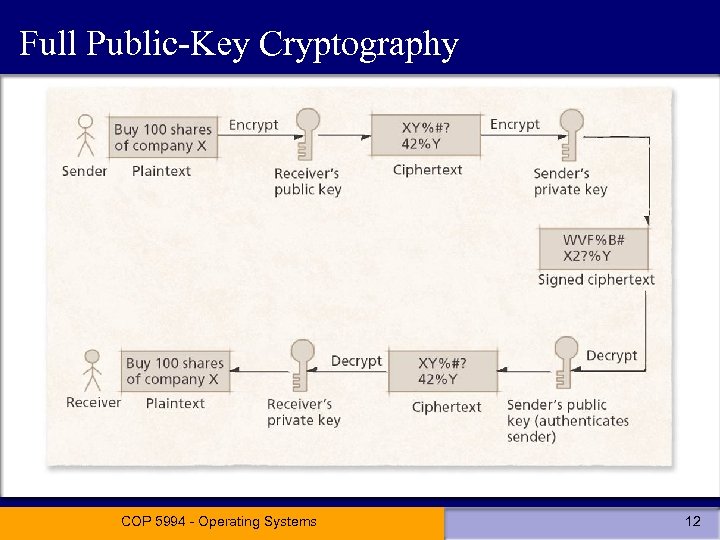 Full Public-Key Cryptography COP 5994 - Operating Systems 12
Full Public-Key Cryptography COP 5994 - Operating Systems 12
 PK-Infrastructure: Certificates • Limitation of public-key cryptography – if users share the same set of keys, it is difficult to establish each party’s identity • Solution: – certify public key – public key is part of certificate – published by certificate authority – certificate authorization hierarchy • rooted at Internet Policy Registration Authority COP 5994 - Operating Systems 13
PK-Infrastructure: Certificates • Limitation of public-key cryptography – if users share the same set of keys, it is difficult to establish each party’s identity • Solution: – certify public key – public key is part of certificate – published by certificate authority – certificate authorization hierarchy • rooted at Internet Policy Registration Authority COP 5994 - Operating Systems 13
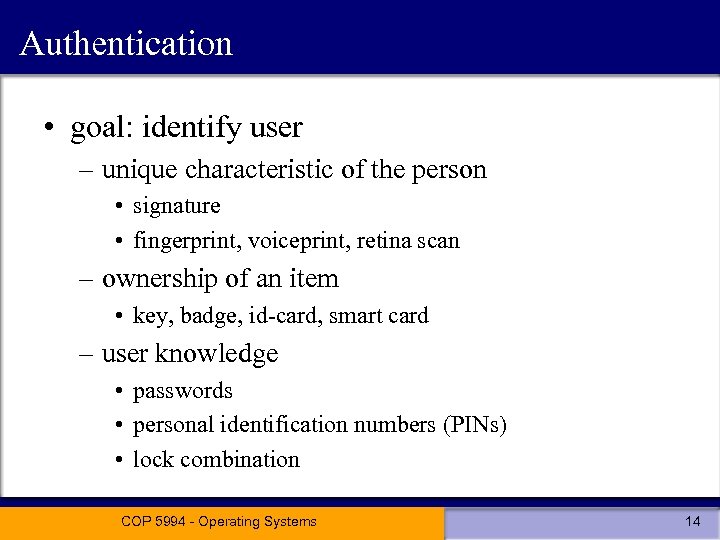 Authentication • goal: identify user – unique characteristic of the person • signature • fingerprint, voiceprint, retina scan – ownership of an item • key, badge, id-card, smart card – user knowledge • passwords • personal identification numbers (PINs) • lock combination COP 5994 - Operating Systems 14
Authentication • goal: identify user – unique characteristic of the person • signature • fingerprint, voiceprint, retina scan – ownership of an item • key, badge, id-card, smart card – user knowledge • passwords • personal identification numbers (PINs) • lock combination COP 5994 - Operating Systems 14
 Digital Signatures • The electronic equivalents of written signatures – Authenticate senders’ identities • Idea: – run hash function on document to produce hash value – create signature as encrypted hash value – message is sent with document, signature, hash function – receiver decrypts signature, runs hash function, compare hash values COP 5994 - Operating Systems 15
Digital Signatures • The electronic equivalents of written signatures – Authenticate senders’ identities • Idea: – run hash function on document to produce hash value – create signature as encrypted hash value – message is sent with document, signature, hash function – receiver decrypts signature, runs hash function, compare hash values COP 5994 - Operating Systems 15
 Authorization Server: Kerberos • protection against internal security attacks – open-source protocol/server developed at MIT • employs secret-key cryptography – to authenticate users in a network – to maintain the integrity and privacy of network communications • components: – authentication server – Ticket Granting Service COP 5994 - Operating Systems 16
Authorization Server: Kerberos • protection against internal security attacks – open-source protocol/server developed at MIT • employs secret-key cryptography – to authenticate users in a network – to maintain the integrity and privacy of network communications • components: – authentication server – Ticket Granting Service COP 5994 - Operating Systems 16
 Kerberos Scenario 1. Client submits username/password to authentication server 2. If valid, the authentication server issues a Ticket. Granting Ticket (TGT) encrypted with the client’s secret key 3. Client sends decrypted TGT to the TGS when requesting a resource. If valid, TGS issues a service ticket encrypted with client’s secret key. 4. Client decrypts service ticket, which it uses to access network resources COP 5994 - Operating Systems 17
Kerberos Scenario 1. Client submits username/password to authentication server 2. If valid, the authentication server issues a Ticket. Granting Ticket (TGT) encrypted with the client’s secret key 3. Client sends decrypted TGT to the TGS when requesting a resource. If valid, TGS issues a service ticket encrypted with client’s secret key. 4. Client decrypts service ticket, which it uses to access network resources COP 5994 - Operating Systems 17
 Authentication: Single Sign-On • Simplifies authentication process – one log in using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • examples: – distributed file system – ACM digital library COP 5994 - Operating Systems 18
Authentication: Single Sign-On • Simplifies authentication process – one log in using a single password to access multiple applications across multiple computers – Important to secure single sign-on passwords • examples: – distributed file system – ACM digital library COP 5994 - Operating Systems 18
 Authorization • Discretionary Access Control (DAC) – File owner controls permissions – ex: read, write, execute, access control list • Mandatory Access Control (MAC) – Predefine a central permission scheme COP 5994 - Operating Systems 19
Authorization • Discretionary Access Control (DAC) – File owner controls permissions – ex: read, write, execute, access control list • Mandatory Access Control (MAC) – Predefine a central permission scheme COP 5994 - Operating Systems 19
 Access Control Security Models • role based access control (RBAC) • model elements – subject has role has privilege to access object – subject can have multiple roles – role has multiple privileges – privilege defines object access • very flexible COP 5994 - Operating Systems 20
Access Control Security Models • role based access control (RBAC) • model elements – subject has role has privilege to access object – subject can have multiple roles – role has multiple privileges – privilege defines object access • very flexible COP 5994 - Operating Systems 20
 Auditing • log all system and network activity • host protection – tripwire. org • Intrusion Detection Systems – commercial and open source systems • snort. org, dshield. org, lids. org – detection strategies • statistical anomaly • pattern-matching COP 5994 - Operating Systems 21
Auditing • log all system and network activity • host protection – tripwire. org • Intrusion Detection Systems – commercial and open source systems • snort. org, dshield. org, lids. org – detection strategies • statistical anomaly • pattern-matching COP 5994 - Operating Systems 21
 Security Attacks • Crypt-analytic attacks • Viruses and worms • Denial-of-service attacks – Domain name system (DNS) attack • Software exploitation – Buffer overflow • System penetration – Web defacing COP 5994 - Operating Systems 22
Security Attacks • Crypt-analytic attacks • Viruses and worms • Denial-of-service attacks – Domain name system (DNS) attack • Software exploitation – Buffer overflow • System penetration – Web defacing COP 5994 - Operating Systems 22
 Cryptanalytic Attack • Attempt to decrypt encrypted text • Goal is to determine the key • Encryption algorithm is analyzed to find relations between bits of the encryption key and bits of the encrypted text • Weak statistical trends between encrypted text and keys can be exploited to gain knowledge about the key COP 5994 - Operating Systems 23
Cryptanalytic Attack • Attempt to decrypt encrypted text • Goal is to determine the key • Encryption algorithm is analyzed to find relations between bits of the encryption key and bits of the encrypted text • Weak statistical trends between encrypted text and keys can be exploited to gain knowledge about the key COP 5994 - Operating Systems 23
 Viruses • executable code – attachment to an e-mail message – hidden within as audio clips, video clips and games • if code is execute, mischief occurs: – – file corruption change application behavior send emails erase hard drive, … • replicates itself – via send email COP 5994 - Operating Systems 24
Viruses • executable code – attachment to an e-mail message – hidden within as audio clips, video clips and games • if code is execute, mischief occurs: – – file corruption change application behavior send emails erase hard drive, … • replicates itself – via send email COP 5994 - Operating Systems 24
 Virus Types • boot sector virus – controls OS • transient virus – runs with another program • resident virus – operates while OS is active • logic bomb – executes its payload at given time COP 5994 - Operating Systems 25
Virus Types • boot sector virus – controls OS • transient virus – runs with another program • resident virus – operates while OS is active • logic bomb – executes its payload at given time COP 5994 - Operating Systems 25
 Worms • Executable code that spreads by infecting files over a network – Rarely requires any user action to propagate – Does not need to be attached to another program or file to spread • Once a virus or worm is released, it can spread rapidly, often infecting millions of computers worldwide within minutes or hours COP 5994 - Operating Systems 26
Worms • Executable code that spreads by infecting files over a network – Rarely requires any user action to propagate – Does not need to be attached to another program or file to spread • Once a virus or worm is released, it can spread rapidly, often infecting millions of computers worldwide within minutes or hours COP 5994 - Operating Systems 26
 Denial-of-Service (Do. S) Attacks • prevent system from servicing legitimate requests • unauthorized traffic saturates a network’s resources, restricting access for legitimate users • typical: flood servers with data packets • attach is carried out by network of computers COP 5994 - Operating Systems 27
Denial-of-Service (Do. S) Attacks • prevent system from servicing legitimate requests • unauthorized traffic saturates a network’s resources, restricting access for legitimate users • typical: flood servers with data packets • attach is carried out by network of computers COP 5994 - Operating Systems 27
 Buffer overflow attacks – occurs when an application sends more data to a buffer than it can hold – can push the additional data into adjacent buffers, corrupting or overwriting existing data – can replace executable code in an application’s stack to alter its behavior • malicious code that will then be able to execute with the same access rights as the application it attacked – depending on the user and application, the attacker may gain access to the entire system COP 5994 - Operating Systems 28
Buffer overflow attacks – occurs when an application sends more data to a buffer than it can hold – can push the additional data into adjacent buffers, corrupting or overwriting existing data – can replace executable code in an application’s stack to alter its behavior • malicious code that will then be able to execute with the same access rights as the application it attacked – depending on the user and application, the attacker may gain access to the entire system COP 5994 - Operating Systems 28
 Attack Prevention and Security Solutions • • Firewalls Antivirus software Security patches Secure file systems COP 5994 - Operating Systems 29
Attack Prevention and Security Solutions • • Firewalls Antivirus software Security patches Secure file systems COP 5994 - Operating Systems 29
 Firewall • Protect against intruders outside the network – Police inbound and outbound traffic for the LAN • Types of firewalls – Packet-filtering firewall • allows only defined traffic • Inspects packets for inconsistencies such as incorrect source address – Application-level gateways • Inspect packets for malicious payloads COP 5994 - Operating Systems 30
Firewall • Protect against intruders outside the network – Police inbound and outbound traffic for the LAN • Types of firewalls – Packet-filtering firewall • allows only defined traffic • Inspects packets for inconsistencies such as incorrect source address – Application-level gateways • Inspect packets for malicious payloads COP 5994 - Operating Systems 30
 Antivirus Software • Attempts to protect against virus attack – monitor file access – identify and remove viruses • many commercial and open source packages – www. clamav. net COP 5994 - Operating Systems 31
Antivirus Software • Attempts to protect against virus attack – monitor file access – identify and remove viruses • many commercial and open source packages – www. clamav. net COP 5994 - Operating Systems 31
 Detection techniques • Signature scanning – Uses a known virus list • Relies on knowledge about the structure of the computer virus’s code • Can be ineffective against variants and polymorphic viruses • Heuristic scanning – looks for virus-like behavior: • Replication, residence in memory and/or destructive code – can detect viruses that have not yet been identified COP 5994 - Operating Systems 32
Detection techniques • Signature scanning – Uses a known virus list • Relies on knowledge about the structure of the computer virus’s code • Can be ineffective against variants and polymorphic viruses • Heuristic scanning – looks for virus-like behavior: • Replication, residence in memory and/or destructive code – can detect viruses that have not yet been identified COP 5994 - Operating Systems 32
 Security Patches • Code releases that address security flaws – Simply releasing a patch for a security flaw is insufficient to improve security • Developers should address security flaws by: – Notifying their users quickly – Providing software that facilitates the process of applying security patches • Example: Hotfixes – Microsoft Automatic Updates COP 5994 - Operating Systems 33
Security Patches • Code releases that address security flaws – Simply releasing a patch for a security flaw is insufficient to improve security • Developers should address security flaws by: – Notifying their users quickly – Providing software that facilitates the process of applying security patches • Example: Hotfixes – Microsoft Automatic Updates COP 5994 - Operating Systems 33
 Secure File Systems • Protect sensitive data regardless of how the data is accessed • Encrypting File System (EFS) – Uses cryptography to protect files and folders in an NTFS file system – Uses secret-key and public-key encryption to secure files COP 5994 - Operating Systems 34
Secure File Systems • Protect sensitive data regardless of how the data is accessed • Encrypting File System (EFS) – Uses cryptography to protect files and folders in an NTFS file system – Uses secret-key and public-key encryption to secure files COP 5994 - Operating Systems 34
 Secure Communication Protocols • Developed to provide security in several layers of the traditional TCP/IP stack • Secure Sockets Layer (SSL) – common extension to http • Internet Protocol Security (IPSec) – needed for IPv 4 • Virtual Private Network (VPN) – uses IPSec channel to virtually extend LAN COP 5994 - Operating Systems 35
Secure Communication Protocols • Developed to provide security in several layers of the traditional TCP/IP stack • Secure Sockets Layer (SSL) – common extension to http • Internet Protocol Security (IPSec) – needed for IPv 4 • Virtual Private Network (VPN) – uses IPSec channel to virtually extend LAN COP 5994 - Operating Systems 35
 Wireless Security • Wired Equivalent Privacy (WEP) protocol – encrypts transmitted data – prevents unauthorized access to the wireless network – shared single key • Wi-Fi Protected Access (WPA) – provides improved data encryption – uses authentication server • enables user authentication • session key for each user COP 5994 - Operating Systems 36
Wireless Security • Wired Equivalent Privacy (WEP) protocol – encrypts transmitted data – prevents unauthorized access to the wireless network – shared single key • Wi-Fi Protected Access (WPA) – provides improved data encryption – uses authentication server • enables user authentication • session key for each user COP 5994 - Operating Systems 36
 Steganography • The practice of hiding information within other information – For example: a message or image, within another image, message or other form of multimedia • Digital watermarks – Used to protect intellectual property – Exploit unused portions of files to store hidden messages, while the digital files maintain their intended semantics COP 5994 - Operating Systems 37
Steganography • The practice of hiding information within other information – For example: a message or image, within another image, message or other form of multimedia • Digital watermarks – Used to protect intellectual property – Exploit unused portions of files to store hidden messages, while the digital files maintain their intended semantics COP 5994 - Operating Systems 37
 Agenda for next week: – Project Presentations – Final Exam COP 5994 - Operating Systems 38
Agenda for next week: – Project Presentations – Final Exam COP 5994 - Operating Systems 38


