2acd67e812c9520aecb1971dd9ac9d47.ppt
- Количество слайдов: 106

OPERATING SYSTEMS Chapter 1 Introduction Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

Outline n n n Why study operating system What is an operating system The history of Operating System Hardware of operating system Important concepts of Operating System
Why study operating system n n To learn how computers work To learn how complexity is managed through appropriate abstractions: infinite CPU, infinite memory, files, etc. To learn about system design performance vs. simplicity, HW vs. SW, etc. Because OSs are everywhere!
What Is An Operating System A modern computer consists of: • • • One or more processors Main memory Disks Printers Various input/output devices Managing all these components requires a layer of software – the operating system Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639
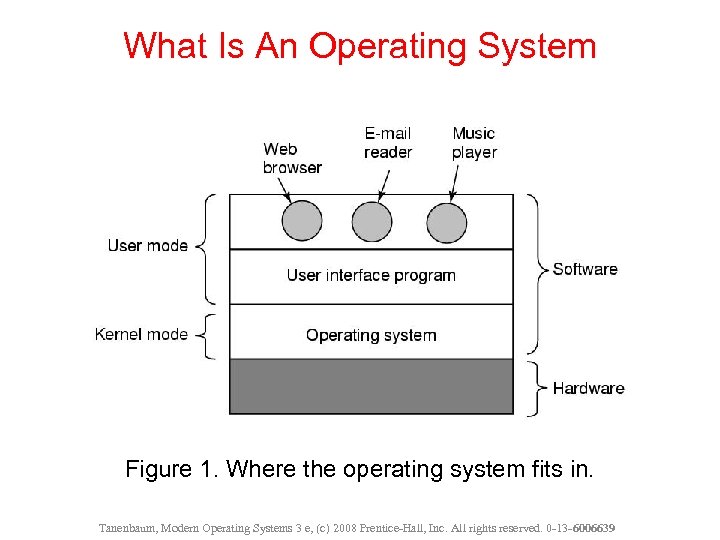
What Is An Operating System Figure 1. Where the operating system fits in. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

What is an Operating System? n Users use various OS q n User interacts with shell or GUI q q n Windows, Linux, Mac OS etc. part of OS? they use OS to get their work done Is device driver part of OS?
What is an Operating System? n n On top of hardware is OS Most computers have two modes of operation: q q Kernel mode and user mode OS runs in kernel mode, which has complete access to all hardware and can execute any instruction Rest of software runs in user mode, which has limited capability Shell or GUI is the lowest level of user mode software
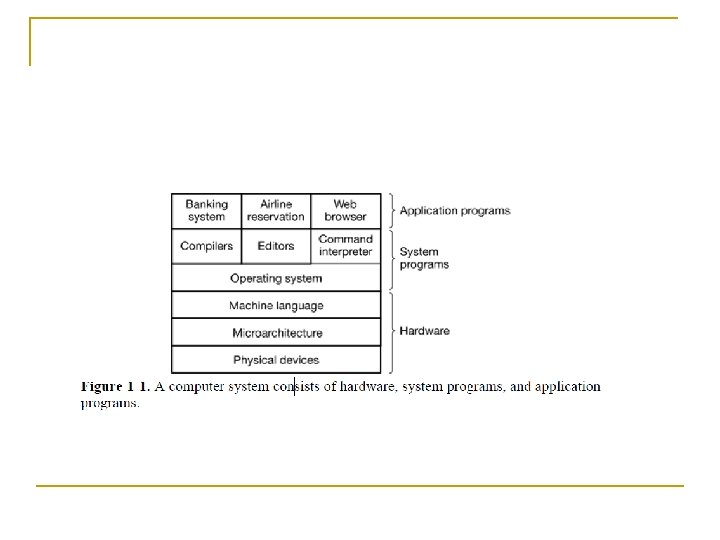
What is an operating system? n Two functions: q q From top to down: provide application programmers a clean abstract set of resources instead of hardware ones From down to top: Manage these hardware resources
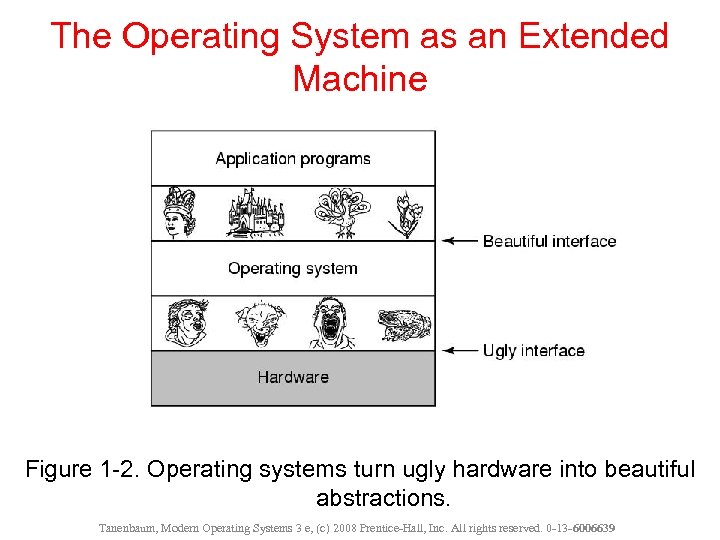
The Operating System as an Extended Machine Figure 1 -2. Operating systems turn ugly hardware into beautiful abstractions. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

The Operating System as a Resource Manager • • • Allow multiple programs to run at the same time Manage and protect memory, I/O devices, and other resources Includes multiplexing (sharing) resources in two different ways: • In time • In space Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 -6006639

The Operating System as a Resource Manager n n When a resource is time multiplexed, different programs or users take turns using it. First one of them gets to use the resource, then another, and so on. For example, with only one CPU and multiple programs that want to run on it, the operating system first allocates the CPU to one program, then after it has run long enough, another one gets to use the CPU, then another, and then eventually the first one again.

Time mux…cont…. n Determining how the resource is time multiplexed who goes next and for how long is the task of-- the operating system. n Example of time multiplexing is sharing the printer. When multiple print jobs are queued up for printing on a single printer, a decision has to be made about which one is to be printed next.
Space Multiplexing n The other kind of multiplexing is space multiplexing, instead of the customers taking turns, each one gets part of the resource. n For example, main memory is normally divided up among several running programs, so each one can be resident at the same time (for example, in order to take turns using the CPU). n This raises issues of fairness, protection, and so on, and it is up to the operating system to solve them.
The First Generation (1945 -55) Vacuum Tubes and Plugboards n n The first ones used mechanical relays but were very slow, with cycle times measured in seconds. Relays were later replaced by vacuum tubes. These machines were filling up entire rooms with tens of thousands of vacuum tubes, but they were still millions of times slower than even the cheapest personal computers available today.
The Second Generation (1955 -65) Transistors and Batch Systems n The introduction of the transistor in the mid 1950 s changed the picture radically. n These machines, now called mainframes, were locked away in specially air conditioned computer rooms

n Only big corporations or major government agencies or universities could afford price. n To run a job (i. e. , a program or set of programs), a programmer would first write the program in FORTRAN or assembler, then punch it on cards. n He would then bring the card deck down to the input room and hand it to one of the operators and go drink coffee until the output was ready.

n When the computer finished whatever job it was currently running, an operator would go over to the printer and tear off the output and carry it over to the output room, so that the programmer could collect it later.
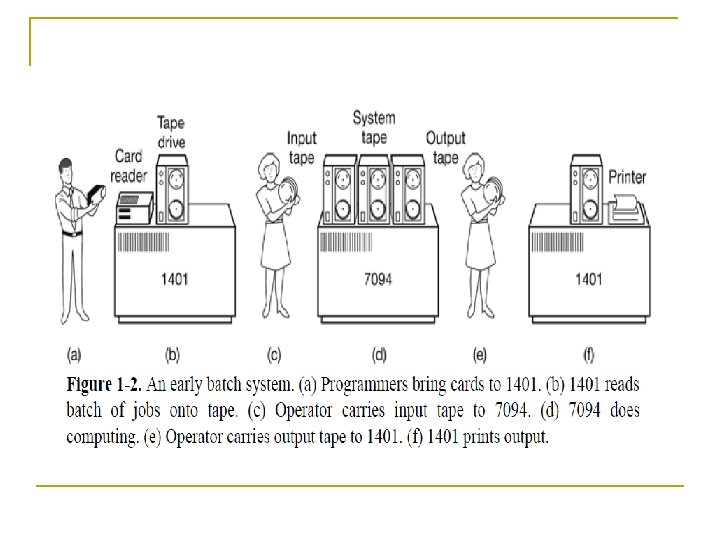
n Given the high cost of the equipment, people quickly looked for ways to reduce the wasted time. The solution was the batch system. n The idea behind it was to collect a tray full of jobs in the input room and then read them onto a magnetic tape using a small (relatively) inexpensive computer n such as the IBM 1401, which was very good at reading cards, copying tapes, and printing output, but not at all good at numerical calculations. Other, much more expensive machines, such as the IBM 7094, were used for the real computing.
The Third Generation (1965 -1980) ICs and Multiprogramming n n The 360 was the first major computer line to use (small-scale) Integrated Circuits (ICs), thus providing a major price/performance advantage over the second-generation machines, which were built up from individual transistors. It was an immediate success, and the idea of a family of compatible computers was soon adopted by all the other major manufacturers.

n They popularized several key techniques absent in second-generation operating systems. Probably the most important of these was multiprogramming. n Having multiple jobs safely in memory at once requires special hardware to protect each job against mischief by the other ones, but the 360 and other third-generation systems were equipped with this hardware.
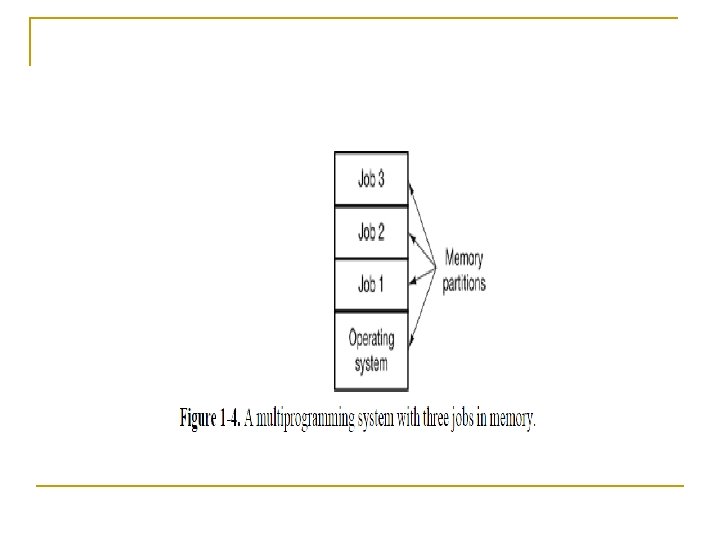

n Another major feature present in third-generation operating systems was the ability to read jobs from cards onto the disk as soon as they were brought to the computer room. n When a running job finished, the operating system could load a new job from the disk into the now-empty partition and run it. This technique is called spooling (from Simultaneous Peripheral Operation On Line) and was also used for output.
n This desire for quick response time paved the way for timesharing, a variant of multiprogramming, in which each user has an online terminal. n In a timesharing system, if 20 users are logged in and 17 of them are thinking or talking or drinking coffee, the CPU can be allocated in turn to the three jobs that want service
The Fourth Generation (1980 Present) Personal Computers n With the development of LSI (Large Scale Integration) circuits, chips containing thousands of transistors on a square centimetre of silicon. n Where the minicomputer made it possible for a department in a company or university to have its own computer, the microprocessor chip made it possible for a single individual to have his or her own personal computer. Engelbart invented the GUI (Graphical User Interface), pronounced “gooey, ” complete with windows, icons, menus, and mouse. n
What is Multiprogramming, Multiprocessing and Multitasking. Multiprogramming: • In a multiprogramming system there are one or more programs loaded in main memory which are ready to execute. • Only one program at a time is able to get the CPU for executing its instructions (i. e. , there is at most one process running on the system) while all the others are waiting their turn.
n Multiprocessing sometimes refers to executing multiple processes (programs) at the same time. n In fact, multiprocessing refers to the hardware (i. e. , the CPU units) rather than the software (i. e. , running processes). If the underlying hardware provides more than one processor then that is multiprocessing.

Multitasking n Multitasking refers to having multiple (programs, processes, tasks, threads) running at the same time. n The illusion of parallelism is achieved when the CPU is reassigned to another task (i. e. process or thread context switching).

48 THE OPERATING SYSTEM ZOO: Mainframe Operating Systems Server Operating Systems Multiprocessor Operating Systems Personal Computer Operating Systems Real-Time Operating Systems Embedded Operating Systems Smart Card Operating Systems
Mainframe Operating Systems n These computers distinguish themselves from personal computers in terms of their I/O capacity. n A mainframe with 1000 disks and thousands of gigabytes of data is not unusual. n Mainframes are also making something of a comeback as high-end Web servers, servers for large-scale electronic commerce sites, and servers for business-to-business transactions

Server Operating Systems n They run on servers, which are either very large personal computers, workstations, or even mainframes. n They serve multiple users at once over a network and allow the users to share hardware and software resources. n Servers can provide print service, file service, or web service. Internet providers run many server machines to support their customers and Web sites use servers to store the Web pages and handle the incoming requests. n Typical server operating systems are UNIX and Windows 2000. Linux is also gaining ground for servers.
Multiprocessor Operating Systems n An increasingly common way to get majorleague computing power is to connect multiple CPUs into a single system. n These systems are called parallel computers, multicomputer, or multiprocessors.
Personal Computer Operating Systems n Their job is to provide a good interface to a single user. n They are widely used for word processing, spreadsheets, and Internet access. n Common examples are Windows 98, Windows 2000, the Macintosh operating system, and Linux.

Real-Time Operating Systems n n n These systems are characterized by having time as a key parameter. For example, in industrial process control systems, realtime computers have to collect data about the production process and use it to control machines in the factory. Often there are hard deadlines that must be met. For example, if a car is moving down an assembly line, certain actions must take place at certain instants of time, if a welding robot welds too early or too late, the car will be ruined. If the action absolutely must occur at a certain moment (or within a certain range), we have a hard realtime system.

n Another kind of real-time system is a soft real-time system, in which missing an occasional deadline is acceptable. Digital audio or multimedia systems fall in this category.
Embedded Operating Systems n n n A palmtop computer or PDA (Personal Digital Assistant) is a small computer that fits in a shirt pocket and performs a small number of functions such as an electronic address book and memo pad. Embedded systems run on the computers that control devices that are not generally thought of as computers, such as TV sets, microwave ovens, and mobile telephones. Examples of such operating systems are Palm. OS and Windows CE (Consumer Electronics).
Smart Card Operating Systems n The smallest operating systems run on smart cards, which are credit card-sized devices containing a CPU chip. n They have very severe processing power and memory constraints. Some of them can handle only a single function, such as electronic payments, but others can handle multiple functions on the same smart card.
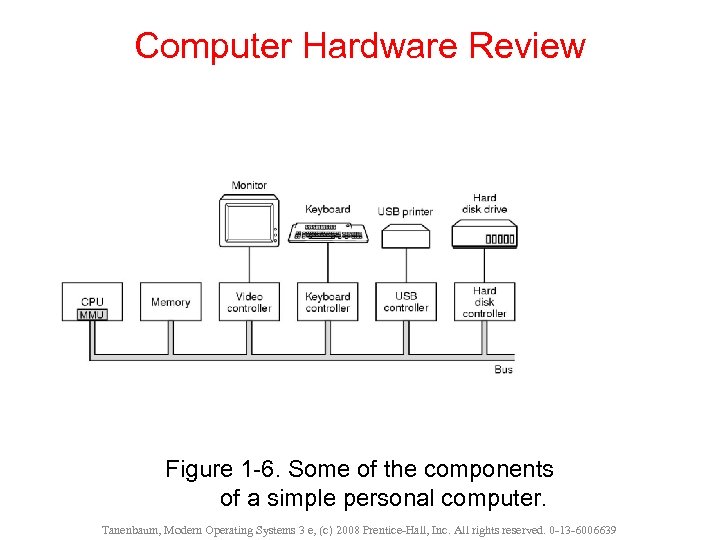
Computer Hardware Review Figure 1 -6. Some of the components of a simple personal computer. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 -6006639
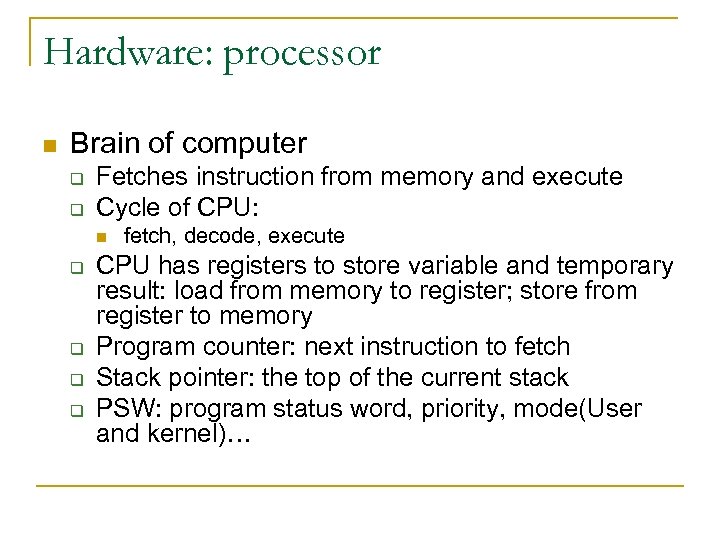
Hardware: processor n Brain of computer q q Fetches instruction from memory and execute Cycle of CPU: n q q fetch, decode, execute CPU has registers to store variable and temporary result: load from memory to register; store from register to memory Program counter: next instruction to fetch Stack pointer: the top of the current stack PSW: program status word, priority, mode(User and kernel)…
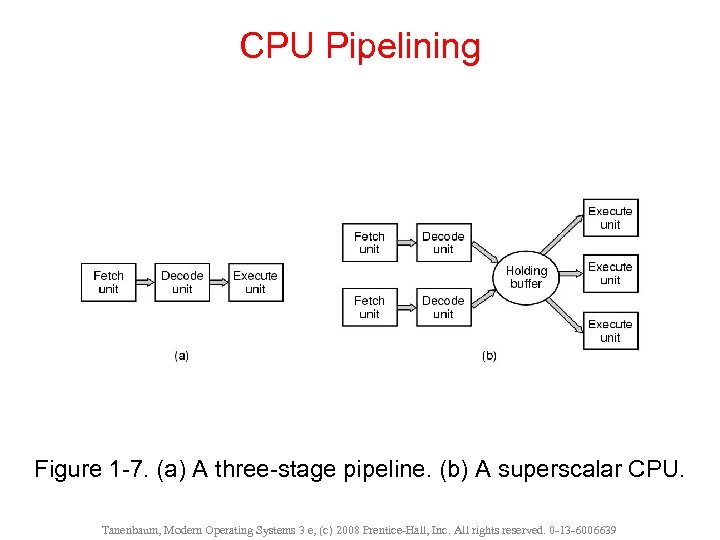
CPU Pipelining Figure 1 -7. (a) A three-stage pipeline. (b) A superscalar CPU. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 -6006639
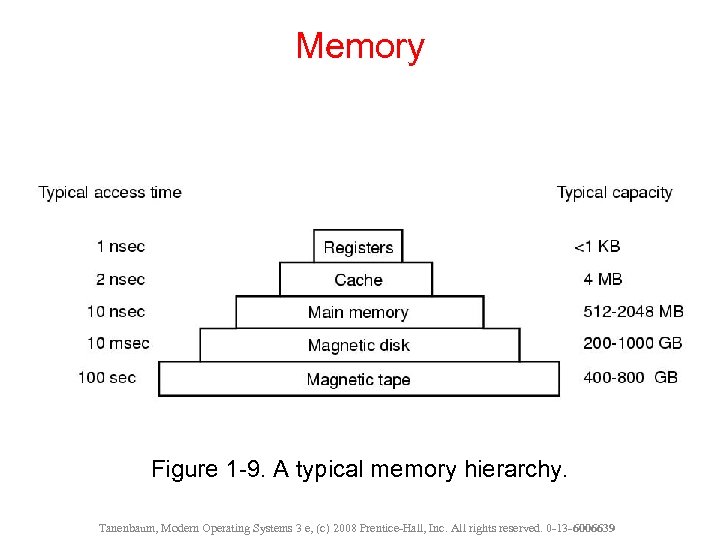
Memory Figure 1 -9. A typical memory hierarchy. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

Disks n Cheap and large: two orders better than RAM n Slow: three orders worse than RAM n Mechanical movement to fetch data n Disk helps to implement Virtual Memory
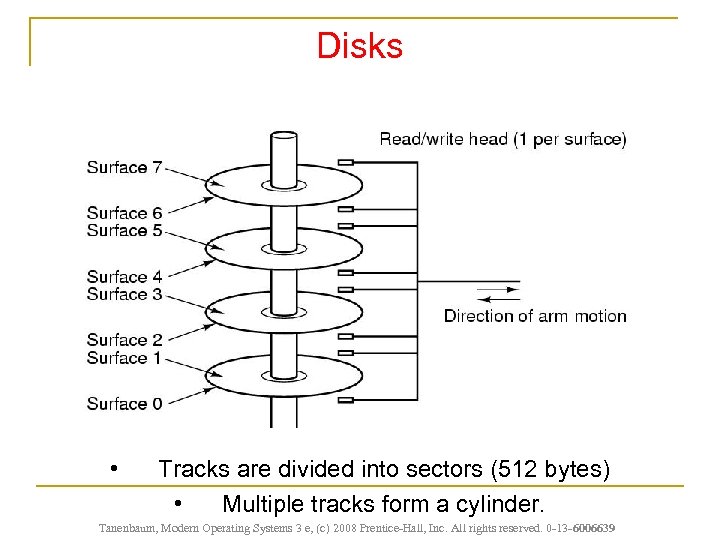
Disks • Tracks are divided into sectors (512 bytes) • Multiple tracks form a cylinder. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639
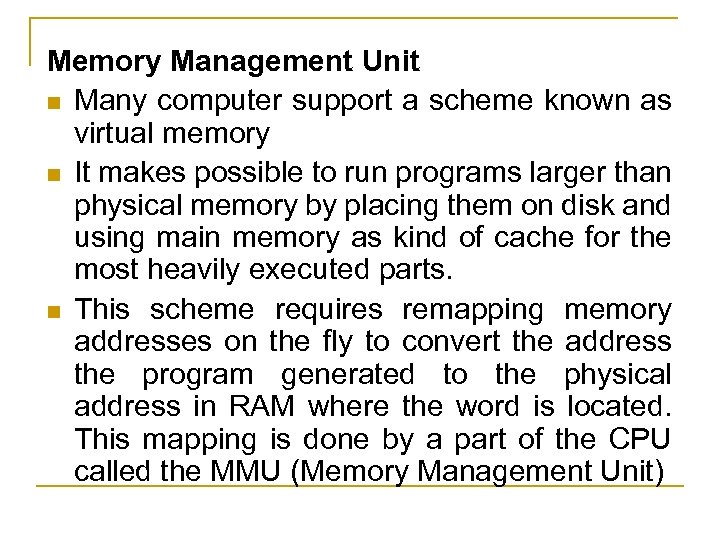
Memory Management Unit n Many computer support a scheme known as virtual memory n It makes possible to run programs larger than physical memory by placing them on disk and using main memory as kind of cache for the most heavily executed parts. n This scheme requires remapping memory addresses on the fly to convert the address the program generated to the physical address in RAM where the word is located. This mapping is done by a part of the CPU called the MMU (Memory Management Unit)

I/O Devices • Controller runs a device-accepts commands from the OS and executes them Complicated business • • Eg. Gets command to read sector x on disk y. Must convert to (cylinder, sector, head) address, move arm to correct cylinder, wait for sector to rotate under the head, read and store bits coming off the drive, compute checksum, store bits as words in memory • Controller contains a computer to run its device
Device Driver • • • OS software that talks to controller-gives commands, accepts responses Each controller manufacturer supplies a driver for each OS Driver runs in kernel mode Controller has registers which are used to communicate with the driver Three modes of communication • • • Polling Interrupts DMA

I/O by polling device • • • Driver issues command to controller Driver polls device until it is ready Eg Send character to printer controller and poll until it is ready to accept the next character Big use of CPU Called programmed I/O-not really used any more
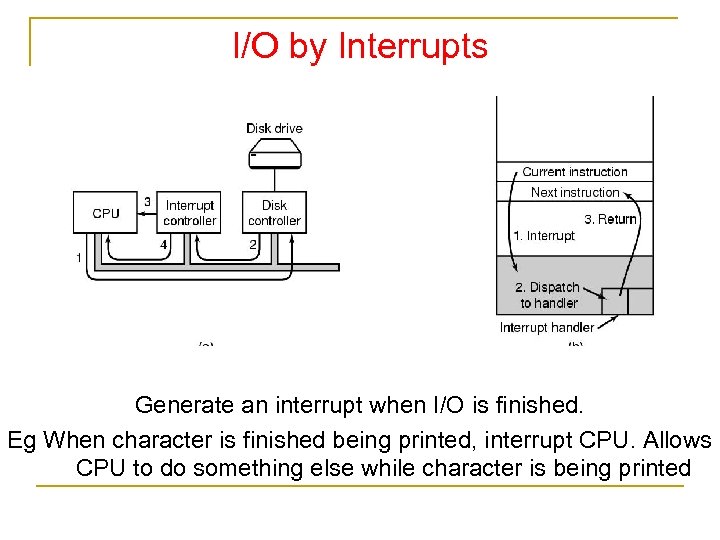
I/O by Interrupts Generate an interrupt when I/O is finished. Eg When character is finished being printed, interrupt CPU. Allows CPU to do something else while character is being printed
I/O by DMA • • Special (controller) chip Avoids using the CPU as part of the transfer to/from memory CPU tells chip to set up transfer and take care of it Chip does as it it told and interrupts CPU when it is finished
The bus hierarchy • • In the beginning there was one bus-couldn’t handle the traffic when cpu and memories got faster and bigger Create a hierarchy of faster buses (PCI) and specialized buses (SCSI-Small Computer System Interface) and USB(Universal Serial Bus-used to connect slow devices )

The Operating System Zoo • • • Mainframe operating systems Server operating systems Multiprocessor operating systems Personal computer operating systems Handheld operating systems Embedded operating systems Sensor node operating systems Real-time operating systems Smart card operating systems

Operating System Concepts • • Processes Address spaces Files Input/Output Protection The shell others Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

processes n Process q A process is fundamentally a container that holds information for a program to run
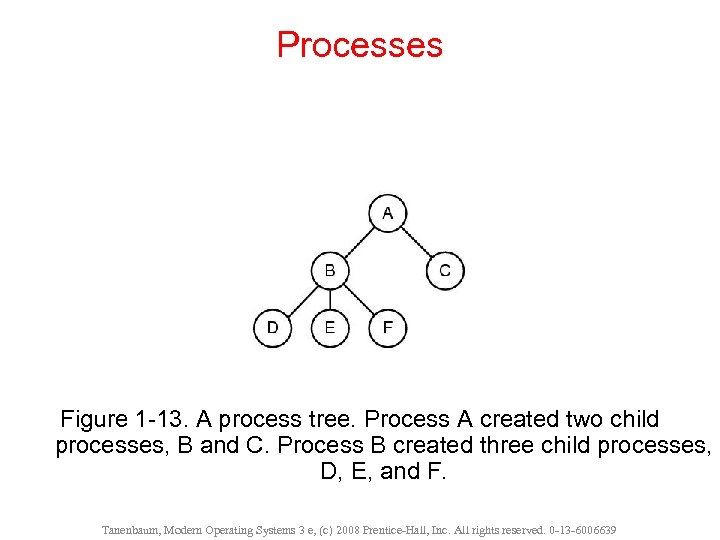
Processes Figure 1 -13. A process tree. Process A created two child processes, B and C. Process B created three child processes, D, E, and F. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 -6006639
Address Space n The memory used by a process, in concept n Some processes need more memory than physically available– virtual memory
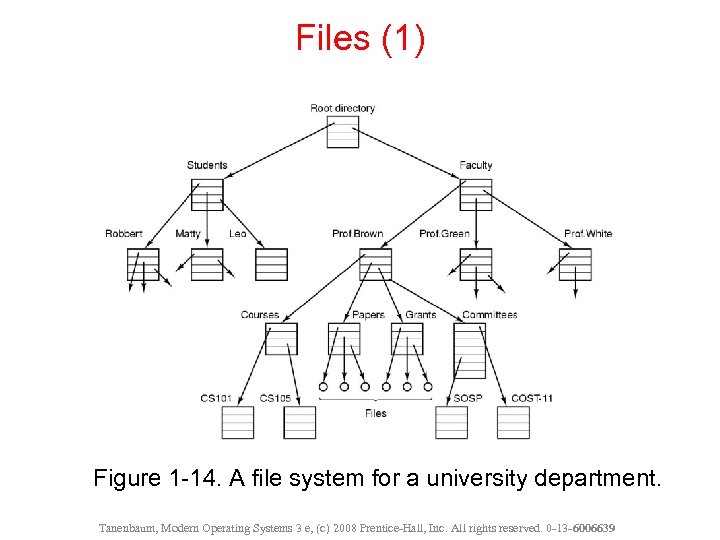
Files (1) Figure 1 -14. A file system for a university department. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639
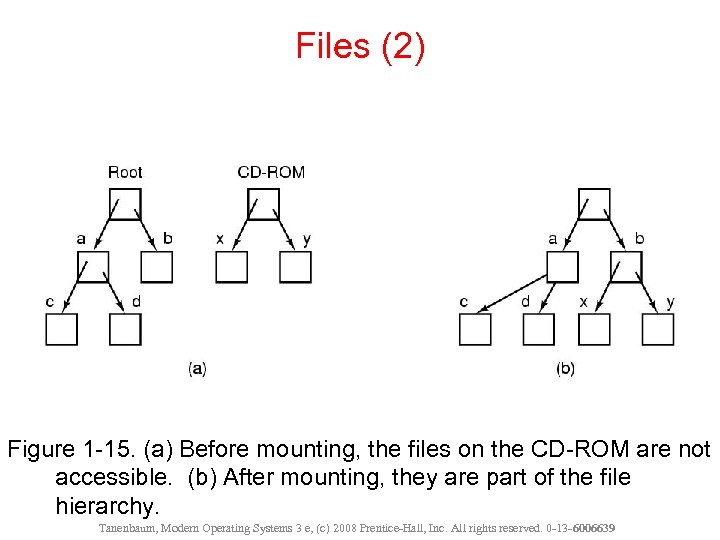
Files (2) Figure 1 -15. (a) Before mounting, the files on the CD-ROM are not accessible. (b) After mounting, they are part of the file hierarchy. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639
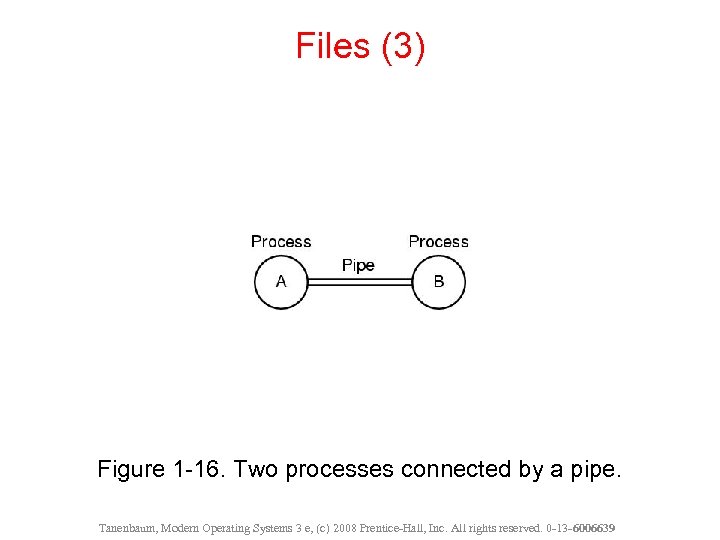
Files (3) Figure 1 -16. Two processes connected by a pipe. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

I/O, Protection/Shell • • I/O-big part of OS Protection-UNIX uses rwx bits for each file • • 3 bits for owner, 3 for group, 3 for everyone else Shell (command interpreter) • • UNIX Has lots of flavors-sh, bash, csh, ksh Sort<file 1>file 2 Cat file 1 file 2 file 3 | sort > /dev/lp

System calls n The goal of interface between user programs and the operating system is primarily about dealing with the abstractions. n System calls is the interface users contact with OS and hardware

Example of read system call It has three parameters: the first one specifying the file, the second one pointing to the buffer, and the third one giving the number of bytes to read. Call from C program will look like count = read(fd, buffer, nbytes); The system call (and the library procedure) return the number of bytes actually read in count n
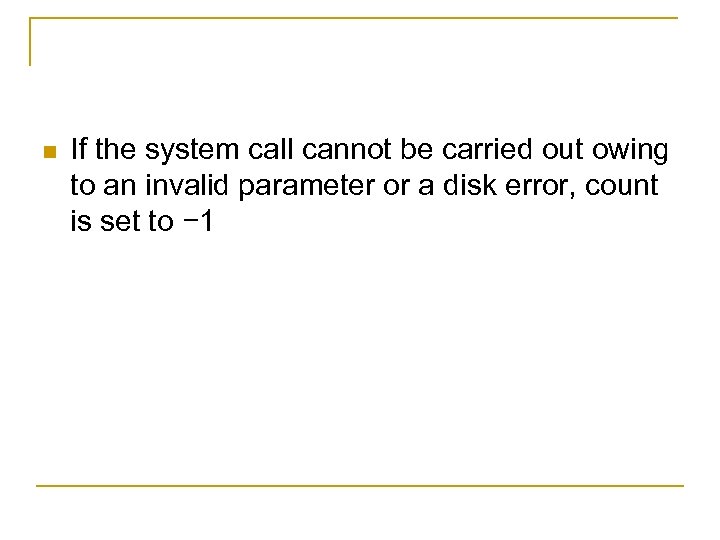
n If the system call cannot be carried out owing to an invalid parameter or a disk error, count is set to − 1
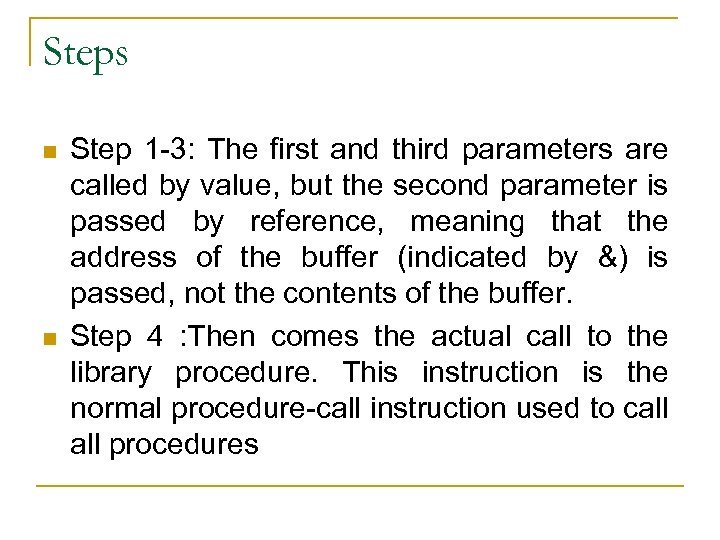
Steps n n Step 1 -3: The first and third parameters are called by value, but the second parameter is passed by reference, meaning that the address of the buffer (indicated by &) is passed, not the contents of the buffer. Step 4 : Then comes the actual call to the library procedure. This instruction is the normal procedure-call instruction used to call procedures
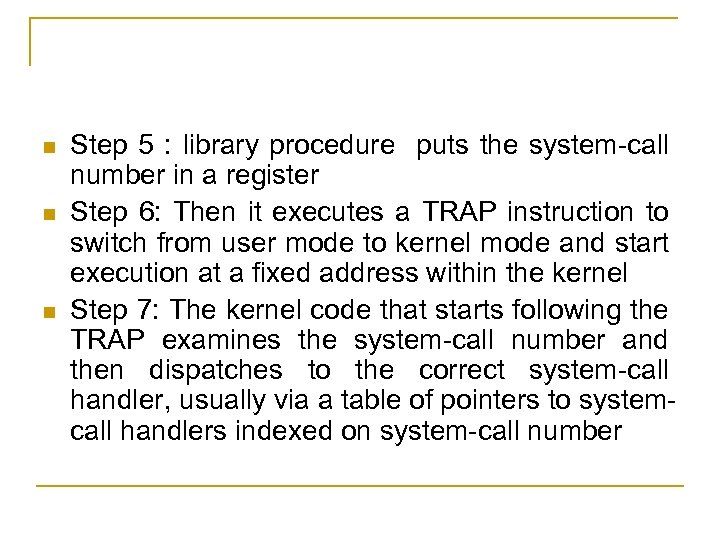
n n n Step 5 : library procedure puts the system-call number in a register Step 6: Then it executes a TRAP instruction to switch from user mode to kernel mode and start execution at a fixed address within the kernel Step 7: The kernel code that starts following the TRAP examines the system-call number and then dispatches to the correct system-call handler, usually via a table of pointers to systemcall handlers indexed on system-call number

n n Step 8: the system-call handler runs Step 9: Once it has completed its work, control may be returned to the user-space library procedure at the instruction following the TRAP instruction Step 10: This procedure returns to the user program in the usual way procedure calls return Step 11: To finish the job, the user program has to clean up the stack, as it does after any procedure call
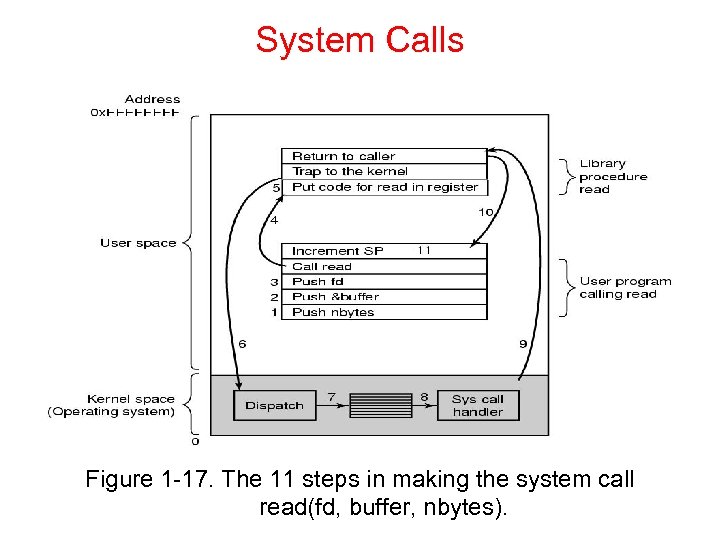
System Calls Figure 1 -17. The 11 steps in making the system call read(fd, buffer, nbytes).
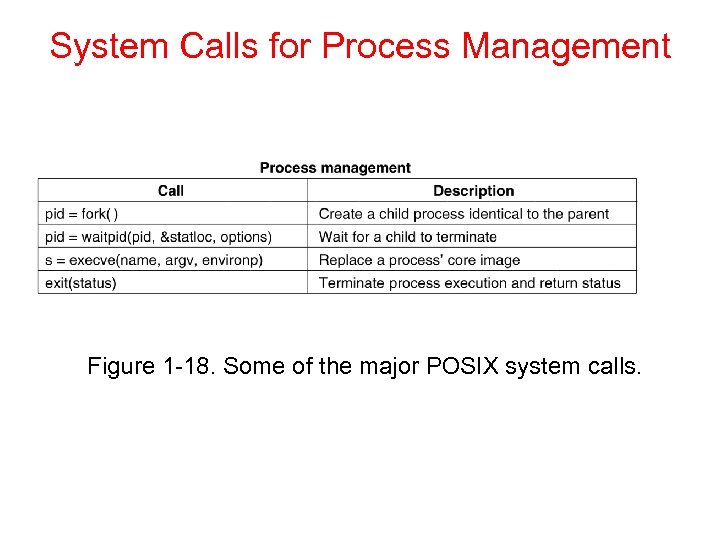
System Calls for Process Management Figure 1 -18. Some of the major POSIX system calls.

Fork System call n n n Fork is used to create a new process. It creates an exact duplicate of the original process The fork call returns a value, which is zero in the child and equal to the child’s PID (Process IDentifier) in the parent. After creation of process both parent and child starts execution from next instruction.

n Main() { fork(); printf(“hi”); }
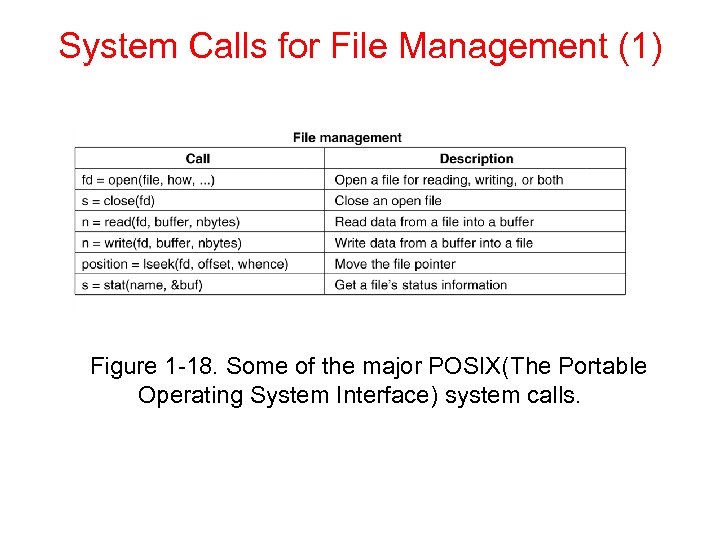
System Calls for File Management (1) Figure 1 -18. Some of the major POSIX(The Portable Operating System Interface) system calls.
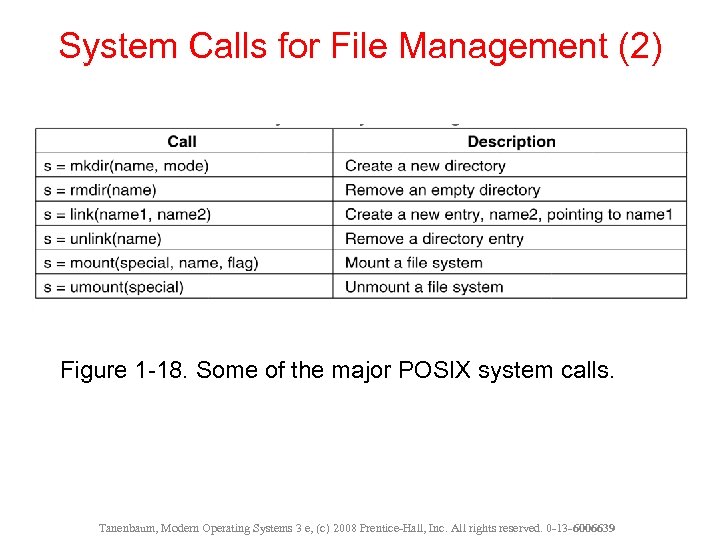
System Calls for File Management (2) Figure 1 -18. Some of the major POSIX system calls. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639
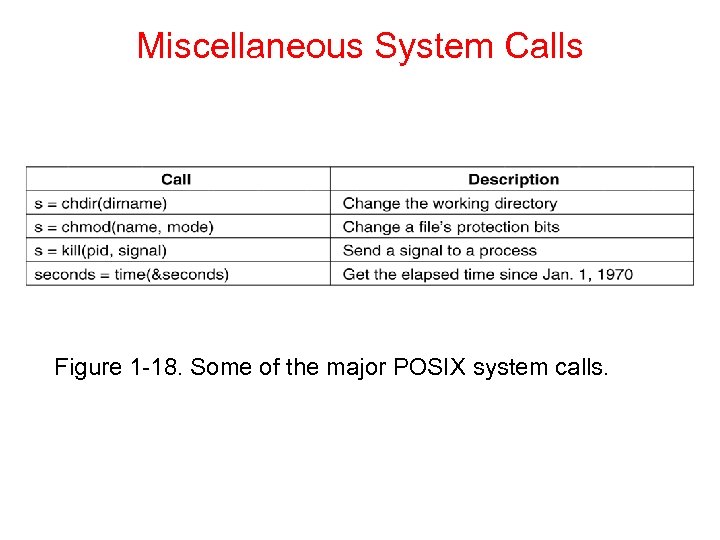
Miscellaneous System Calls Figure 1 -18. Some of the major POSIX system calls.
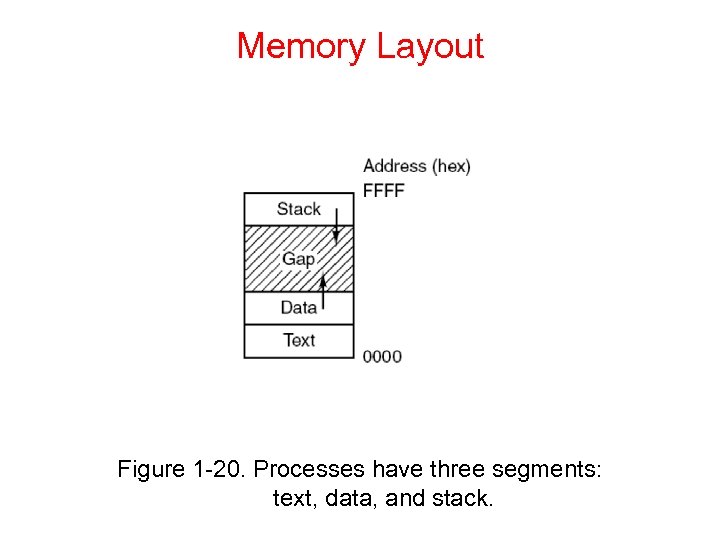
Memory Layout Figure 1 -20. Processes have three segments: text, data, and stack.
Operating Systems Structure Operating system from inside has following types: n Monolithic systems n Layered systems n Microkernels n Client-server systems n Virtual machines n Exo-kernels.

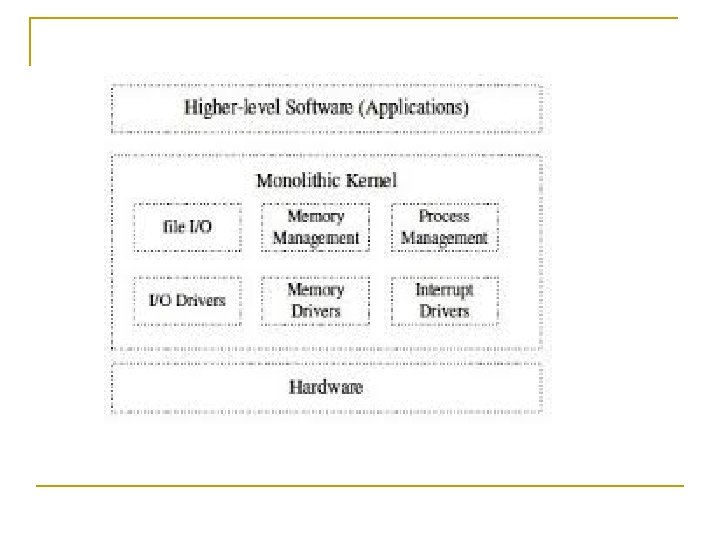
Operating Systems Structure Monolithic systems – basic structure: n n The operating system is written as a collection of procedures, linked together into a single large executable binary program. Each procedure in the system is free to call any other one. A main program that invokes the requested service procedure.

n n In terms of information hiding, there is essentially none—every procedure is visible to every other procedure. The services (system calls) provided by the operating system are requested by putting the parameters in a well-defined place (e. g. , on the stack) and then executing a trap instruction. This instruction switches the machine from user mode to kernel mode and transfers control to the operating system

n Having thousands of procedures that can call each other without restriction may also lead to a system that is difficult to understand. n A crash in any of these procedures will take down the entire operating system. n Example : Unix , DOS

Basic structure for the operating system: n n n 1. A main program that invokes the requested service procedure. 2. A set of service procedures that carry out the system calls. 3. A set of utility procedures that help the service procedures

n For each system call there is one service procedure that takes care of it and executes it.
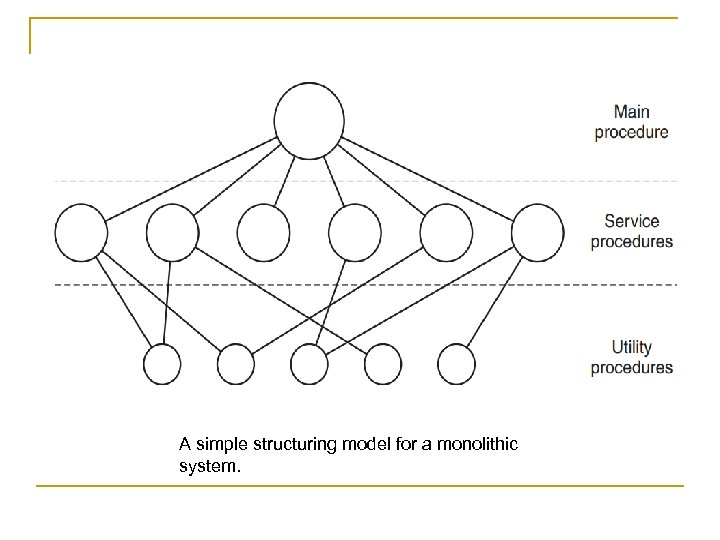
A simple structuring model for a monolithic system.

Layered Systems n A generalization of the approach is to organize the operating system as a hierarchy of layers, each one constructed upon the one below. n Layer 0 deals with allocation of the processor, switching between processes when interrupts occurred. n Above layer 0, the system consisted of sequential processes, each of which could be programmed without having to worry about the fact that multiple processes were running on a single processor
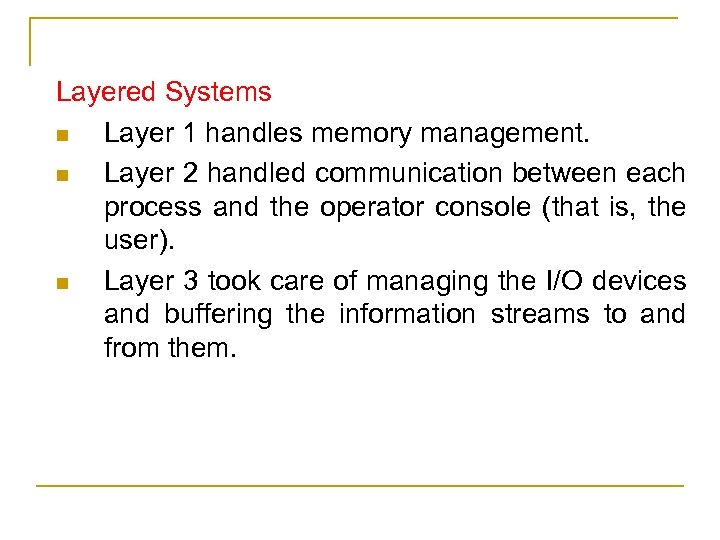
Layered Systems n Layer 1 handles memory management. n Layer 2 handled communication between each process and the operator console (that is, the user). n Layer 3 took care of managing the I/O devices and buffering the information streams to and from them.

Layered Systems Layer 4 was where the user programs were found. They did not have to worry about process, memory, console, or I/O management. The system operator process was located in layer 5. Example: THE system
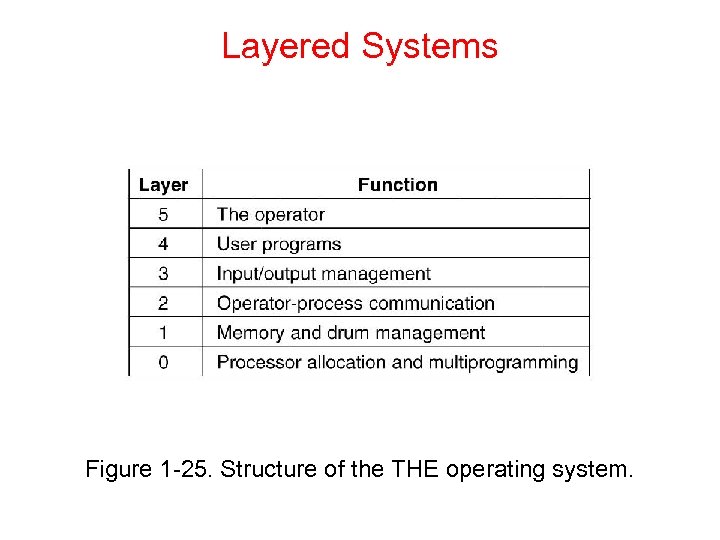
Layered Systems Figure 1 -25. Structure of the THE operating system.

Microkernel n n The basic idea behind the microkernel design is to achieve high reliability by splitting the operating system up into small, well-defined modules, only one of which—the microkernel— runs in kernel mode and the rest run as relatively powerless ordinary user processes. Example : MINIX 3

n In Minix 3 Outside the kernel, the system is structured as three layers of processes all running in user mode. The lowest layer contains the device drivers. n Since they run in user mode, they do not have physical access to the I/O port space and cannot issue I/O commands directly.

n Above the drivers is another user-mode layer containing the servers. One or more file servers manage the file system(s), the process manager creates, destroys, and manages processes n User programs obtain operating system services by sending short messages to the servers asking for the POSIX system calls.

n One interesting server is the reincarnation server, whose job is to check if the other servers and drivers are functioning correctly. n In the event that a faulty one is detected, it is automatically replaced without any user intervention. In this way, the system is self healing and can achieve high reliability.
n The system has many restrictions limiting the power of each process. n drivers can touch only authorized I/O ports
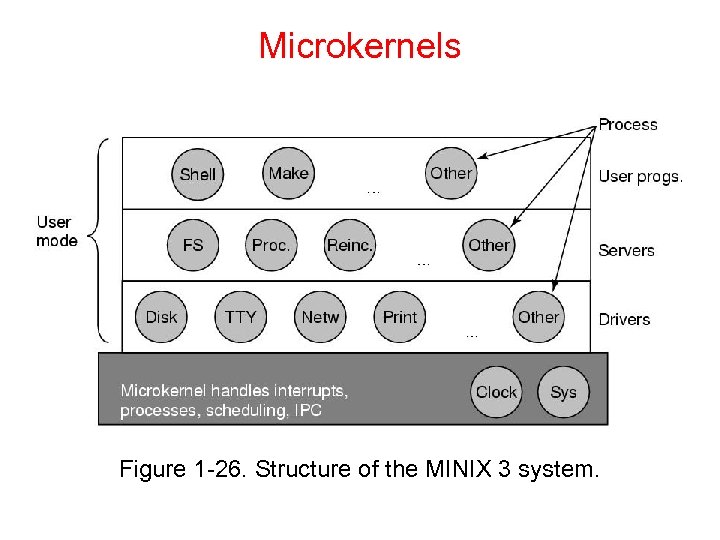
Microkernels Figure 1 -26. Structure of the MINIX 3 system.
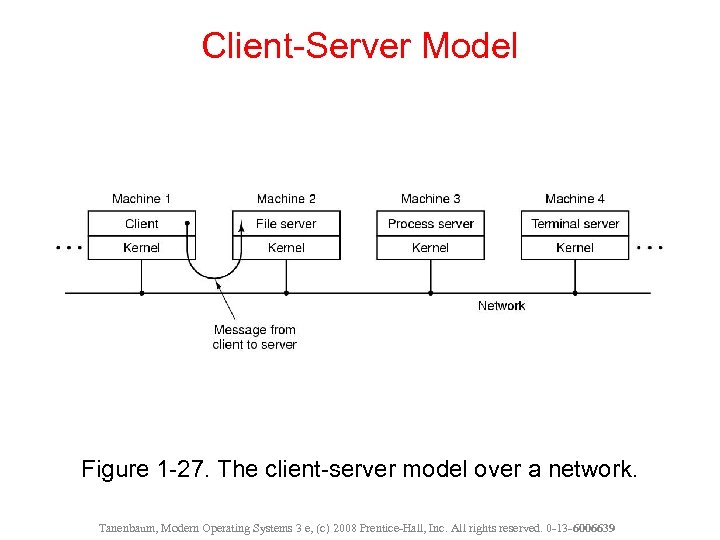
Client-Server Model Figure 1 -27. The client-server model over a network. Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

n Idea is to have two classes of processes, the servers, each of which provides some service, and the clients, which use these services. This model is known as the client-server model. n Communication between clients and servers is often by message passing.
n A PC sends a request for a Web page to the server and the Web page comes back. This is a typical use of the client-server model in a network. n Thus the client-server model is an abstraction that can be used for a single machine or for a network of machines.

Virtual Machines n Virtualization: When a Web hosting company offers virtual machines for rent, a single physical machine can run many virtual machines, each of which appears to be a complete machine. Customers who rent a virtual machine can run whatever operating system and software they want to, but at a fraction of the cost of a dedicated server n Another use of virtualization is for end users who want to be able to run two or more operating systems at the same time, say Windows and Linux, because some of their favorite application packages run on one and some run on the other.
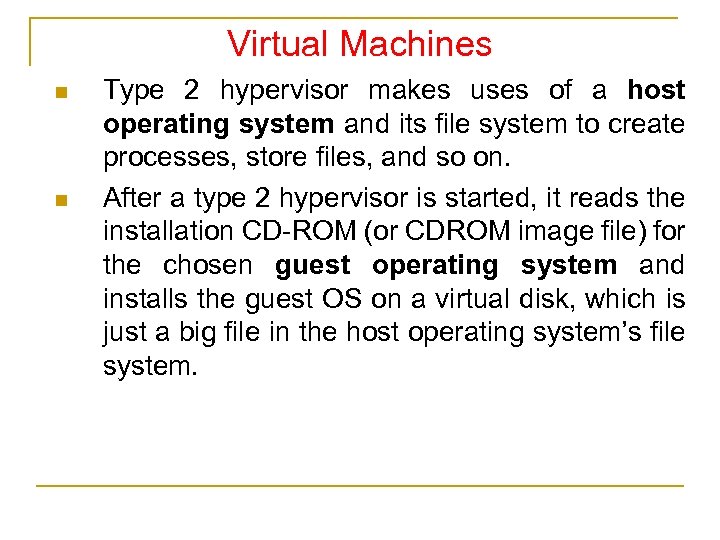
Virtual Machines n n Type 2 hypervisor makes uses of a host operating system and its file system to create processes, store files, and so on. After a type 2 hypervisor is started, it reads the installation CD-ROM (or CDROM image file) for the chosen guest operating system and installs the guest OS on a virtual disk, which is just a big file in the host operating system’s file system.
Exokernel n n n Rather than cloning the actual machine, as is done with virtual machines, another strategy is partitioning it, giving each user a subset of the resources. At the bottom layer, running in kernel mode, is a program called the exokernel. Its job is to allocate resources to virtual machines and then check attempts to use them to make sure no machine is trying to use somebody else’s resources. Example: VM/360
Exokernel n n n The advantage of the exo-kernel scheme is that it saves a layer of mapping. In the other designs, each virtual machine thinks it has its own disk, with blocks running from 0 to some maximum, so the virtual machine monitor must maintain tables to remap disk addresses (and all other resources). With the exokernel, this remapping is not needed.

The World According to C • • The C language Header files Large programming projects The model of run time Tanenbaum, Modern Operating Systems 3 e, (c) 2008 Prentice-Hall, Inc. All rights reserved. 0 -13 - 6006639

World according to C n n Operating systems are large C programs consisting of many pieces written by many programmers C language q q q Data types, variables, control statements… Header files: declaration, definition, macros… For a large programming project
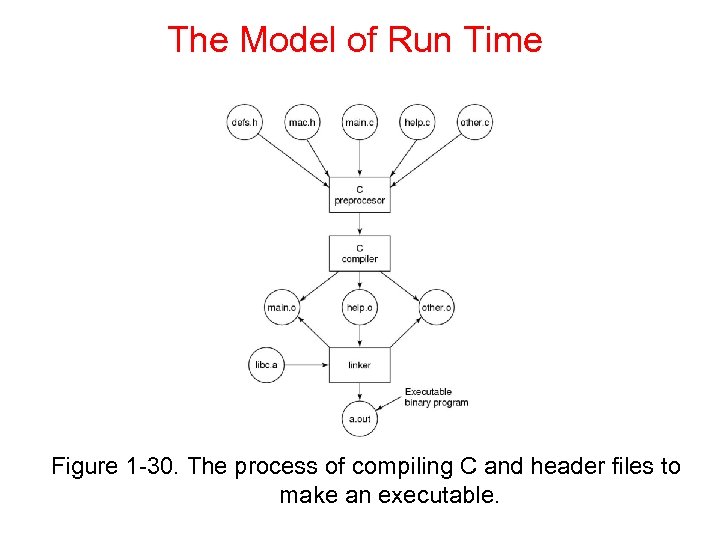
The Model of Run Time Figure 1 -30. The process of compiling C and header files to make an executable.
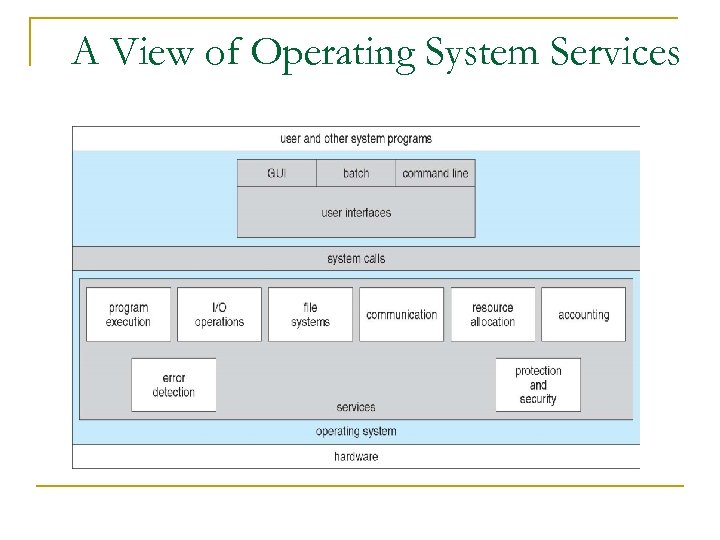
A View of Operating System Services
Operating System Services (Cont) n One set of operating-system services provides functions that are helpful to the user (Cont): q q Communications – Processes may exchange information, on the same computer or between computers over a network Error detection – OS needs to be constantly aware of possible errors n For each type of error, OS should take the appropriate action to ensure correct and consistent computing

Operating System Services (Cont) q q q Resource allocation - When multiple users or multiple jobs running concurrently, resources must be allocated to each of them Accounting - To keep track of which users use how much and what kinds of computer resources Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other n Protection involves ensuring that all access to system resources is controlled n Security of the system from outsiders requires user authentication, extends to defending external I/O devices from invalid access attempts
2acd67e812c9520aecb1971dd9ac9d47.ppt