3669ad39d97ea5377ebbbfe91087c9dc.ppt
- Количество слайдов: 25
Open Web Application Security Project Ralf Durkee Rochester OWASP Chapter Leader Lou Leone Rochester OWASP Communications OWASP Andrea Cogliati Rochester OWASP VP Copyright © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http: //www. owasp. org

What is OWASP? Open Web Application Security Project < Worldwide free and open community < Focused on improving the security of Web applications < Promotes secure software development < An open forum for discussion < Provides free resources to the community 4 Publications, Articles, Standards 4 Testing and Training Software 4 Local Chapters and Mailing Lists 4 Software libraries and tools OWASP 2

OWASP membership Membership category Annual membership fee Individual Supporters Organization Supporters Accredited University Supporters $50 $5, 000 FREE (in exchange of meeting space at least 2 x per year) § Funds OWASP Speakers via OWASP On the Move § Funds Season of Code projects § Helps Support Local Chapters OWASP

OWASP Resources and Community Documentation (Wiki and Books) • SAMM, Code Review, Testing, Building, Legal, … Code Projects • Defensive, Offensive (Test tools), Education, Process, more … Chapters • Over 100 and growing Conferences • Major and minor events all around the world OWASP
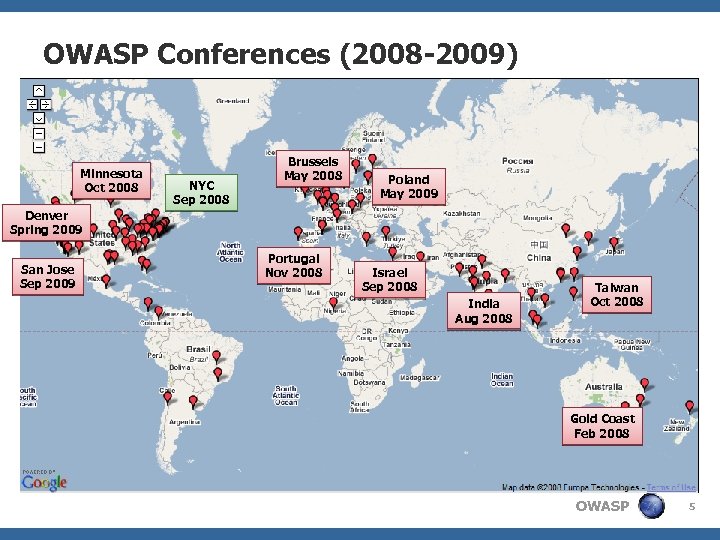
OWASP Conferences (2008 -2009) Minnesota Oct 2008 NYC Sep 2008 Brussels May 2008 Poland May 2009 Denver Spring 2009 San Jose Sep 2009 Portugal Nov 2008 Israel Sep 2008 India Aug 2008 Taiwan Oct 2008 Gold Coast Feb 2008 OWASP 5

Rochester Security Summit < The Rochester Security Summit is a community focal point for education and awareness in collaboration with higher education, business and industry partners, held during National Cyber Security Awareness Month < Area collaboration partners include: 4 Rochester ISSA Chapter 4 Rochester OWASP Chapter 4 Rochester ISACA 4 Area businesses and organizations < Oct 28 -29, 2009 at The Woodcliff Hotel & Spa Conference Center in Fairport, NY < http: //Rochester. Security. org OWASP
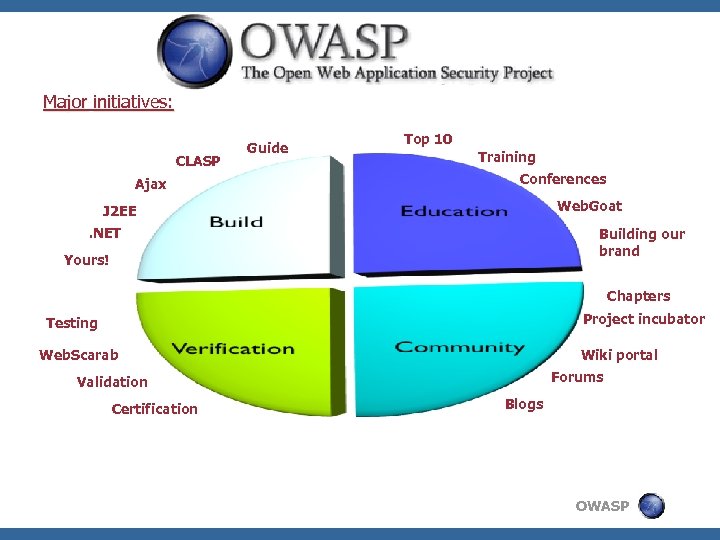
Major initiatives: CLASP Ajax Guide Top 10 Training Conferences Web. Goat J 2 EE. NET Building our brand Yours! Chapters Project incubator Testing Web. Scarab Wiki portal Forums Validation Certification Blogs OWASP

OWASP Publications Major Publications 4 Top 10 Web Application Security Vulnerabilities 4 Guide to Building Secure Web Applications 4 Legal Project 4 Code Review Guide 4 Testing Guide 4 App. Sec Faq 4 Software Assurance Maturity Model 4 Application Security Verification Standards OWASP 8

OWASP Publications Common Features 4 All OWASP publications are available free for download from http: //www. owasp. org 4 Released under any approved free licenses 4 Living Documents § Updating as needed § Ongoing Projects 4 OWASP Publications feature collaborative work in a leading-edge competitive field OWASP 9

OWASP Publications – OWASP Top 10 Web Application Security Vulnerabilities 4 A list of the 10 most severe security issues 4 Updated ever few years 4 Address issues with applications on the perimeter 4 Growing industry acceptance § § Federal Trade Commission (US Gov) US Defense Information Systems Agency VISA (Cardholder Information Security Program) Referenced by PCI-DSS standard 4 Strong push to present as a standard OWASP 10

OWASP Publications - OWASP Top 10 <Current Top Ten Issues (2007) 4 A 1. Cross Site Scripting (XSS) 4 A 2. Injection Flaws 4 A 3. Malicious File Execution 4 A 4. Insecure Direct Object Reference 4 A 5. Cross Site Request Forgery (CSRF) 4 A 6. Information Leakage and Improper Error Handling 4 A 7. Broken Authentication and Session Management 4 A 8. Insecure Cryptographic Storage 4 A 9. Insecure Communications 4 A 10. Failure to Restrict URL Access OWASP 11

OWASP Publications - OWASP Guide to Building Secure Web Applications 4 Provides a baseline for developing secure software § Introduction to security in general § Introduction to application level security § Discusses key implementation areas – Architecture – Authentication – Session Management – Access Controls and Authorization – Event Logging – Data Validation 4 Under continuous development OWASP 12

OWASP Software Common Features 4 All OWASP software provided free for download from http: //www. owasp. org 4 Software is released under any approved free licenses 4 Active Projects § Updating as needed § Ongoing Projects § Many maintainers and contributors 4 OWASP Software is free for download and can be used by individuals or businesses OWASP 13
OWASP Software - Web. Goat 4 Primarily a training application 4 Provides § An educational tool for learning about application security § A baseline to test security tools against (i. e. known issues) 4 What is it? § A J 2 EE web application arranged in “Security Lessons” § Based on Tomcat and JDK 1. 5 § Oriented to learning – Easy to use – Illustrates credible scenarios – Teaches realistic attacks, and viable solutions OWASP 14

OWASP Software - Web. Goat – What can you learn? 4 A number of constantly growing attacks and solutions § § § § Cross Site Scripting SQL Injection Attacks Thread Safety Field & Parameter Manipulation Session Hijacking and Management Weak Authentication Mechanisms Many more attacks added 4 Getting the Tools § http: //www. owasp. org/index. php/Category: OWASP_Web. Goat_Project § Simply download, unzip, and execute the jar file. OWASP 15
OWASP Software - Web. Scarab 4 A framework for analyzing HTTP/HTTPS traffic 4 Web Proxy written in Java 4 Multiple Uses § Developer: Debug exchanges between client and server § Security Analyst: Analyze traffic to identify vulnerabilities 4 Technical Tool § § Focused on software developers Extensible plug-in architecture Open source Very powerful tool 4 Getting the Tool § http: //www. owasp. org/index. php/Category: OWASP_Web. Scarab_Project OWASP 16
OWASP Software - Web. Scarab - What can it do? 4 Features § Proxy – observe traffic between the browser and server, includes the ability to modify data in transit, expose hidden fields, and perform bandwidth manipulation § Fragment Analysis – extract scripts and html as presented to the browser, instead of source code presented by the browser post render § Manual Intercept - allows the user to modify HTTP and HTTPS requests and responses on the fly, before they reach the server or browser. § Spider – identifies new URLs within each page viewed § Session. ID Analysis – Collection and analysis of cookies to determine predictability of session tokens § Much more… OWASP 17

OWASP Local Chapters Building Communities 4 Local Chapters provide opportunities for OWASP members to share ideas and learn information security 4 Open to all; any level of proficiency 4 Provide a forum to discuss issues, latest research, and experiences 4 Provide venue for invited guests to present new ideas and projects OWASP 18

OWASP Rochester Chapter 4 Chapter started 2004, by Ralph Durkee 4 Chapter Web site http: //www. owasp. org/rochester 4 Current Board: § § President: Ralph Durkee Vice President and Treasurer: Andrea Cogliati Communications and Chapter Evangelist: Lou Leone Web and Mail List: Duane Peifer 4 Monthly Meetings & Presentations 4 Mailing Lists 4 Vendor Neutral Environments 4 Open Forums for Discussion OWASP 19

OWASP Rochester Chapter Meetings Semi-Formal meeting with presentations on odd numbered months § Generally 3 rd Monday of each Month § Next Meeting Nov 16 th § Location: Mykonos Software § Food sometimes provided by sponsors. § Questions and Discussion afterwards § Join the mailing lists for meeting announcements as dates and locations sometimes have to change. OWASP 20

OWASP Rochester Chapter Meetings Informal social gatherings on even numbered months § Gatherings for beer, food and informal discussion § An open environment for discussion of information security suitable for novices, professionals, and experts § Next would be Dec 14 th § Currently gathering at – Mac Gregor's Grill & Tap Room – 300 Jefferson Rd (Near RIT) § Each pays for the beverage and food they order OWASP

OWASP Rochester Chapter Mail Lists 2 Rochester Chapter Mailing Lists 4 Rochester Announcement Only List § Need to be subscribed to receive Rochester chapter meeting and organizational announcements. § Closed list, only used by Rochester Chapter Board. 4 Rochester Discussion List § § § Highly Recommended Used for chapter discussions and questions Currently very low traffic All mail list members may post to the list Couple of basics: keep it professional; No sales or marketing materials OWASP 22

OWASP Local Chapters Vendor Neutral Environments 4 Learn about security without the sales pitches 4 Strict guidelines for chapter presentations and sponsorship § All sponsors must be approved § No product presentation may take place at any meeting of a local chapter. § Presentations that focus on a problem or set of problems and discuss solution approaches that may refer to or show examples of various products are allowed. § Sponsorship shall be in the form of donations to The OWASP Foundation in the name of the local chapter and/or to provide food and beverages at meeting events. OWASP 23

OWASP Local Chapters What can you offer? 4 The mailing lists, meetings, and focus groups are open forums for discussion of any relevant topics 4 Members are encouraged to bring forward questions 4 Members are encouraged to participate in OWASP projects § Contribute to existing projects § Propose new projects § Spearhead new ventures 4 Local chapter executive team will work towards building the organization as a free, open, and technically oriented resource for the general public and members OWASP 24
That’s it… <Any questions or comments? <Presentation will be online: Thank you! OWASP 25
3669ad39d97ea5377ebbbfe91087c9dc.ppt