b71ca95ba9ef13ab8aa4e75be1992165.ppt
- Количество слайдов: 34
 Open. ID Discovery Using XRI and XRDS n n IDtrust Symposium, March 4 -6, 2008 Drummond Reed, Cordance Les Chasen, Neu. Star William Tan, Neu. Star
Open. ID Discovery Using XRI and XRDS n n IDtrust Symposium, March 4 -6, 2008 Drummond Reed, Cordance Les Chasen, Neu. Star William Tan, Neu. Star
 Overview n n n The OASIS XRI and XRDS specifications played a key role in identity discovery for Open. ID 2. 0 We’ll explain the five key discovery challenges they helped solve We’ll suggest potential interoperability with other identity protocols/frameworks
Overview n n n The OASIS XRI and XRDS specifications played a key role in identity discovery for Open. ID 2. 0 We’ll explain the five key discovery challenges they helped solve We’ll suggest potential interoperability with other identity protocols/frameworks
 What is XRI (Extensible Resource Identifier)? n An OASIS Technical Committee l n An open standard language for abstract structured identifiers l l n Started January 2003 Identifiers that are independent of domain, application, protocol, or language Identifiers that resolve to other identifiers “XML for identifiers”
What is XRI (Extensible Resource Identifier)? n An OASIS Technical Committee l n An open standard language for abstract structured identifiers l l n Started January 2003 Identifiers that are independent of domain, application, protocol, or language Identifiers that resolve to other identifiers “XML for identifiers”
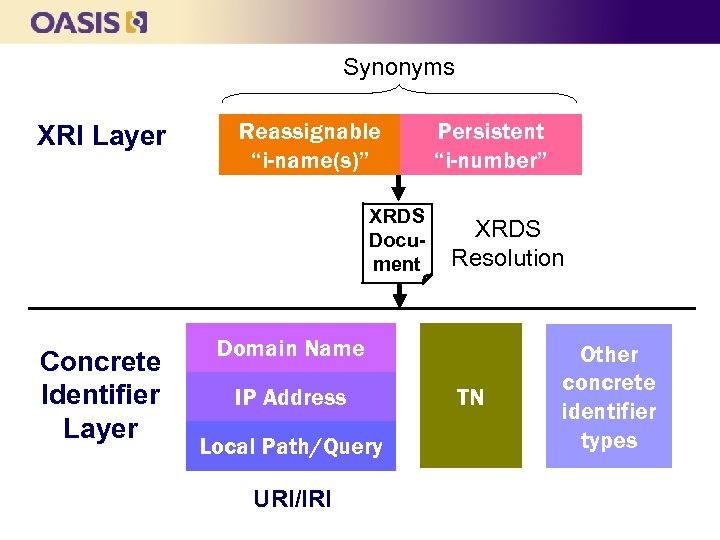 Synonyms XRI Layer Reassignable “i-name(s)” XRDS Document Concrete Identifier Layer Persistent “i-number” XRDS Resolution Domain Name IP Address Local Path/Query URI/IRI TN Other concrete identifier types
Synonyms XRI Layer Reassignable “i-name(s)” XRDS Document Concrete Identifier Layer Persistent “i-number” XRDS Resolution Domain Name IP Address Local Path/Query URI/IRI TN Other concrete identifier types
 What is Open. ID? n An open community specification for user-centric Internet authentication l n Based on the concept that users have their own globally-resolvable identifier and Open. ID authentication service Prime use case: eliminate the need for separate usernames and passwords for different websites
What is Open. ID? n An open community specification for user-centric Internet authentication l n Based on the concept that users have their own globally-resolvable identifier and Open. ID authentication service Prime use case: eliminate the need for separate usernames and passwords for different websites
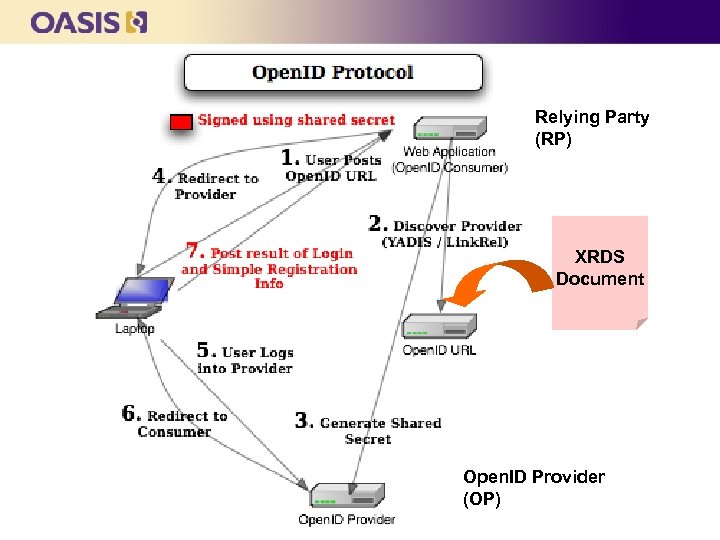 Relying Party (RP) XRDS Document Open. ID Provider (OP)
Relying Party (RP) XRDS Document Open. ID Provider (OP)
 Evolution from Open. ID 1. x to 2. 0 n n n Open. ID 1. 0 “hardwired” a URL to an Open. ID identity server This was very rigid and not extensible As the Open. ID 2. 0 tent grew, it needed a more flexible and robust discovery layer
Evolution from Open. ID 1. x to 2. 0 n n n Open. ID 1. 0 “hardwired” a URL to an Open. ID identity server This was very rigid and not extensible As the Open. ID 2. 0 tent grew, it needed a more flexible and robust discovery layer
 The challenges for Open. ID 2. 0 identity discovery n n n Service description Open. ID recycling Resolution integrity and trust Privacy and non-correlation Extensibility
The challenges for Open. ID 2. 0 identity discovery n n n Service description Open. ID recycling Resolution integrity and trust Privacy and non-correlation Extensibility
 Challenge #1: Service description n Describe what versions of Open. ID an Open. ID identifier supports Enable redundant, prioritized Open. ID provider endpoints Describe what other authentication protocols may be available (e. g. , LID, SAML)
Challenge #1: Service description n Describe what versions of Open. ID an Open. ID identifier supports Enable redundant, prioritized Open. ID provider endpoints Describe what other authentication protocols may be available (e. g. , LID, SAML)
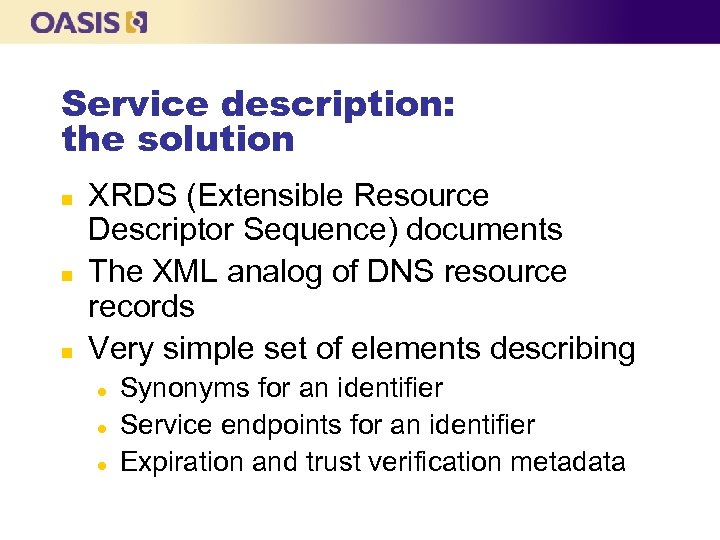 Service description: the solution n XRDS (Extensible Resource Descriptor Sequence) documents The XML analog of DNS resource records Very simple set of elements describing l l l Synonyms for an identifier Service endpoints for an identifier Expiration and trust verification metadata
Service description: the solution n XRDS (Extensible Resource Descriptor Sequence) documents The XML analog of DNS resource records Very simple set of elements describing l l l Synonyms for an identifier Service endpoints for an identifier Expiration and trust verification metadata

 Challenge #2: Open. ID recycling n With usernames/passwords usernames can be recycled l n The service provider controls the binding with the credential With Open. ID, that’s no longer true l l The user controls the binding to the credential Losing control of the identifier = losing control of the credential
Challenge #2: Open. ID recycling n With usernames/passwords usernames can be recycled l n The service provider controls the binding with the credential With Open. ID, that’s no longer true l l The user controls the binding to the credential Losing control of the identifier = losing control of the credential
 Challenge #2: Open. ID recycling n Service providers with large namespaces can’t afford to assign names once and lock them up forever l n Examples: AOL, Yahoo DNS names are inherently recyclable – an entire industry exists to serve the secondary domain name market
Challenge #2: Open. ID recycling n Service providers with large namespaces can’t afford to assign names once and lock them up forever l n Examples: AOL, Yahoo DNS names are inherently recyclable – an entire industry exists to serve the secondary domain name market
 Open. ID recycling: the solution n Synonyms l l l Support the binding of a recyclable identifier with a non-recyclable synonym Authenticate based on the persistent synonym Treat the recyclable identifier as only a temporary handle for the persistent synonym
Open. ID recycling: the solution n Synonyms l l l Support the binding of a recyclable identifier with a non-recyclable synonym Authenticate based on the persistent synonym Treat the recyclable identifier as only a temporary handle for the persistent synonym
 Open. ID recycling: the solution n Persistent synonyms is a primary raison d’être for XRI l l l XRI distinguishes between reassignable “i-names” and persistent “i-numbers” at the syntax level XRDS documents provide automated synonym mapping XRI Resolution 2. 0 includes automated synonym authorization verification
Open. ID recycling: the solution n Persistent synonyms is a primary raison d’être for XRI l l l XRI distinguishes between reassignable “i-names” and persistent “i-numbers” at the syntax level XRDS documents provide automated synonym mapping XRI Resolution 2. 0 includes automated synonym authorization verification

 Challenge #3: Resolution integrity/trust n Open. ID could not specify HTTPS resolution for all Open. ID URLs l l l Too many users do not have access to HTTPS certs or infrastructure Thus the default had to be HTTP This forces users with HTTPS URLs to have to type the entire string, e. g. , https: //my. openid. identifier. tld
Challenge #3: Resolution integrity/trust n Open. ID could not specify HTTPS resolution for all Open. ID URLs l l l Too many users do not have access to HTTPS certs or infrastructure Thus the default had to be HTTP This forces users with HTTPS URLs to have to type the entire string, e. g. , https: //my. openid. identifier. tld
 Resolution integrity/trust: the solution n n As abstract identifiers, XRIs always map to concrete service endpoints XRI resolution offers three trusted modes: l n HTTPS, SAML, or both Thus all XRI i-names can use HTTPS resolution as the default l No need for users to know/do anything
Resolution integrity/trust: the solution n n As abstract identifiers, XRIs always map to concrete service endpoints XRI resolution offers three trusted modes: l n HTTPS, SAML, or both Thus all XRI i-names can use HTTPS resolution as the default l No need for users to know/do anything
 Challenge #4: Privacy & non-correlation n n Open. ID 1. x assumed users would share the same identifier(s) with every RP Violates the Fourth Law of Identity: l A universal identity system must support both "omni-directional" identifiers for use by public entities and "unidirectional" identifiers for use by private entities, thus facilitating discovery while preventing unnecessary release of correlation handles.
Challenge #4: Privacy & non-correlation n n Open. ID 1. x assumed users would share the same identifier(s) with every RP Violates the Fourth Law of Identity: l A universal identity system must support both "omni-directional" identifiers for use by public entities and "unidirectional" identifiers for use by private entities, thus facilitating discovery while preventing unnecessary release of correlation handles.
 Privacy & non-correlation: the solution n Directed identity l l Users can enter the URL or XRI of their identity provider The discovered XRDS doc contains a directed identity service endpoint The RP redirects the user to their OP to select their identifier The OP can also generate a pairwise unique “per relationship” identifier
Privacy & non-correlation: the solution n Directed identity l l Users can enter the URL or XRI of their identity provider The discovered XRDS doc contains a directed identity service endpoint The RP redirects the user to their OP to select their identifier The OP can also generate a pairwise unique “per relationship” identifier
 Privacy & non-correlation: the solution n n Directed identity supports means Open. ID 2. 0 satisfies the Fourth Law It is the only mode some large service providers currently support l n Yahoo Ideally users will have a choice of whether to use a public or directed identifier
Privacy & non-correlation: the solution n n Directed identity supports means Open. ID 2. 0 satisfies the Fourth Law It is the only mode some large service providers currently support l n Yahoo Ideally users will have a choice of whether to use a public or directed identifier
 Challenge #5: Extensibility n n Open. ID is a framework for user-centric identity services RPs need to be able to discover what Open. ID extension specs an OP supports l n SREG, AX, PAPE (more coming) The discovery format itself needs to be extensible
Challenge #5: Extensibility n n Open. ID is a framework for user-centric identity services RPs need to be able to discover what Open. ID extension specs an OP supports l n SREG, AX, PAPE (more coming) The discovery format itself needs to be extensible
 Extensibility: the solution n XRDS documents l l Service types are declared using URIs, IRIs, or XRIs – anyone can extend Multiple types can be declared for the same service endpoint Elements can be added from any XML namespace XRDS documents can redirect or refer to other XRDS documents
Extensibility: the solution n XRDS documents l l Service types are declared using URIs, IRIs, or XRIs – anyone can extend Multiple types can be declared for the same service endpoint Elements can be added from any XML namespace XRDS documents can redirect or refer to other XRDS documents
 Extensibility: the solution n Example: OAuth l l l “Open. ID for services/applications” Allows users to authorize a website or application to access protected resources without providing their credentials directly OAuth Discovery uses XRDS extensibility
Extensibility: the solution n Example: OAuth l l l “Open. ID for services/applications” Allows users to authorize a website or application to access protected resources without providing their credentials directly OAuth Discovery uses XRDS extensibility
 Interoperability with other identity frameworks n n n SAML Information Cards Higgins
Interoperability with other identity frameworks n n n SAML Information Cards Higgins
 SAML n Open. ID can use SAML! l l l Shown by Patterson at the Internet Identity Workshop in December 2006 Same discovery steps, similar protocol flow, just using SAML tokens Can also use XRDS documents for automated discovery of SAML metadata
SAML n Open. ID can use SAML! l l l Shown by Patterson at the Internet Identity Workshop in December 2006 Same discovery steps, similar protocol flow, just using SAML tokens Can also use XRDS documents for automated discovery of SAML metadata
 Information Cards n n n Information cards can carry discoverable Open. ID identifiers XRDS discovery is not used in the information card flow But sharing an Open. ID claim can enable the RP to do XRDS discovery on other identity services
Information Cards n n n Information cards can carry discoverable Open. ID identifiers XRDS discovery is not used in the information card flow But sharing an Open. ID claim can enable the RP to do XRDS discovery on other identity services
 Higgins n n Higgins needed a solution for crossdomain context discovery Higgins resolves a URL or XRI to an XRDS document to discover: l l The service endpoint URI(s) for the context The Higgins context configuration metadata needed to open the context
Higgins n n Higgins needed a solution for crossdomain context discovery Higgins resolves a URL or XRI to an XRDS document to discover: l l The service endpoint URI(s) for the context The Higgins context configuration metadata needed to open the context
 Future work n n Caching and scalability testing Proxying l l n n Performance optimization Integration with authority servers PKI integration Reputation discovery
Future work n n Caching and scalability testing Proxying l l n n Performance optimization Integration with authority servers PKI integration Reputation discovery
 Conclusions n n Open. ID may or may not become an Internet-wide authentication standard But Open. ID identity discovery model has already proved broad utility XRDS resolution provides a common discovery format for URLs and XRIs It can provide an interoperable foundation for Internet identity layer
Conclusions n n Open. ID may or may not become an Internet-wide authentication standard But Open. ID identity discovery model has already proved broad utility XRDS resolution provides a common discovery format for URLs and XRIs It can provide an interoperable foundation for Internet identity layer
 Contact us n Drummond Reed, Co-Chair, XRI TC l l n Les Chasen, Neu. Star, Editor, XRI TC l l n http: //xri. net/=drummond. reed@cordance. net http: //xri. net/=les. chasen@neustar. biz William Tan, Neu. Star, Editor, XRI TC l l http: //xri. net/=wil william. tan@neustar. biz
Contact us n Drummond Reed, Co-Chair, XRI TC l l n Les Chasen, Neu. Star, Editor, XRI TC l l n http: //xri. net/=drummond. reed@cordance. net http: //xri. net/=les. chasen@neustar. biz William Tan, Neu. Star, Editor, XRI TC l l http: //xri. net/=wil william. tan@neustar. biz
 n n n Learn through the IDtrust Knowledgebase of educational materials and background on the standards Share news, events, presentations, white papers, product listings, opinions, questions, and recommendations through postings, blogs, forums, and directories. Collaborate with others online through a wiki interface http: //idtrust. xml. org
n n n Learn through the IDtrust Knowledgebase of educational materials and background on the standards Share news, events, presentations, white papers, product listings, opinions, questions, and recommendations through postings, blogs, forums, and directories. Collaborate with others online through a wiki interface http: //idtrust. xml. org


