0cc5adcd99374052f9b9b91edc74c68b.ppt
- Количество слайдов: 61
 Online Privacy Technologies NTIA Online Privacy Technologies Workshop Dr. Lorrie Faith Cranor AT&T Labs-Research http: //www. research. att. com/~lorrie/
Online Privacy Technologies NTIA Online Privacy Technologies Workshop Dr. Lorrie Faith Cranor AT&T Labs-Research http: //www. research. att. com/~lorrie/
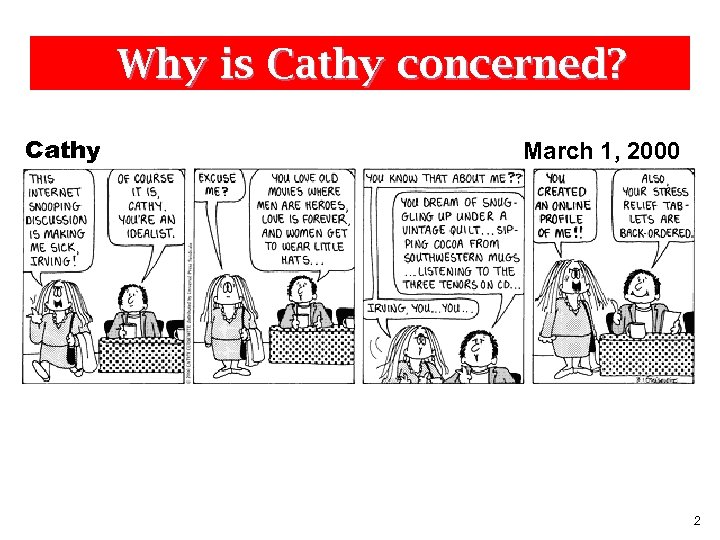 Why is Cathy concerned? Cathy March 1, 2000 2
Why is Cathy concerned? Cathy March 1, 2000 2
 How did Irving find this out? n He snooped her email n He looked at the files on her computer n He observed the “chatter” sent by her browser n He set cookies through banner ads and “web bugs” that allowed him to track her activities across web sites 3
How did Irving find this out? n He snooped her email n He looked at the files on her computer n He observed the “chatter” sent by her browser n He set cookies through banner ads and “web bugs” that allowed him to track her activities across web sites 3
 What do browsers chatter about? n Browsers chatter about «IP address, domain name, organization, «Referring page «Platform: O/S, browser «What information is requested l URLs and search terms «Cookies n To anyone who might be listening «End servers «System administrators «Internet Service Providers «Other third parties l Advertising networks «Anyone who might subpoena log files later 4
What do browsers chatter about? n Browsers chatter about «IP address, domain name, organization, «Referring page «Platform: O/S, browser «What information is requested l URLs and search terms «Cookies n To anyone who might be listening «End servers «System administrators «Internet Service Providers «Other third parties l Advertising networks «Anyone who might subpoena log files later 4
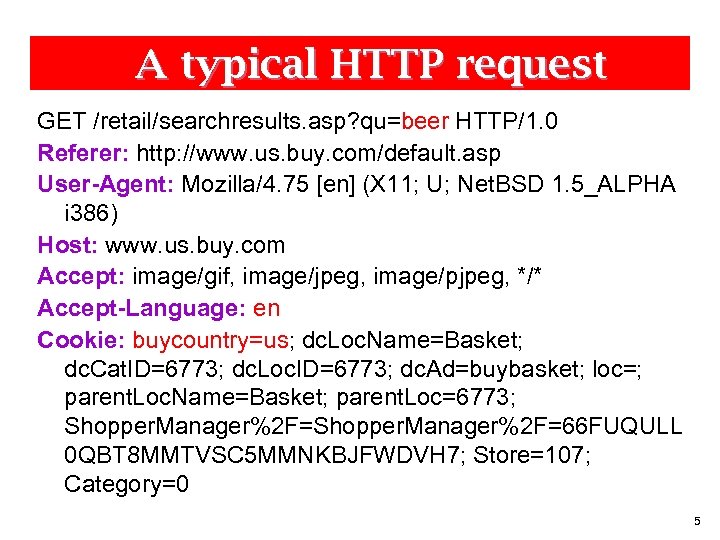 A typical HTTP request GET /retail/searchresults. asp? qu=beer HTTP/1. 0 Referer: http: //www. us. buy. com/default. asp User-Agent: Mozilla/4. 75 [en] (X 11; U; Net. BSD 1. 5_ALPHA i 386) Host: www. us. buy. com Accept: image/gif, image/jpeg, image/pjpeg, */* Accept-Language: en Cookie: buycountry=us; dc. Loc. Name=Basket; dc. Cat. ID=6773; dc. Loc. ID=6773; dc. Ad=buybasket; loc=; parent. Loc. Name=Basket; parent. Loc=6773; Shopper. Manager%2 F=66 FUQULL 0 QBT 8 MMTVSC 5 MMNKBJFWDVH 7; Store=107; Category=0 5
A typical HTTP request GET /retail/searchresults. asp? qu=beer HTTP/1. 0 Referer: http: //www. us. buy. com/default. asp User-Agent: Mozilla/4. 75 [en] (X 11; U; Net. BSD 1. 5_ALPHA i 386) Host: www. us. buy. com Accept: image/gif, image/jpeg, image/pjpeg, */* Accept-Language: en Cookie: buycountry=us; dc. Loc. Name=Basket; dc. Cat. ID=6773; dc. Loc. ID=6773; dc. Ad=buybasket; loc=; parent. Loc. Name=Basket; parent. Loc=6773; Shopper. Manager%2 F=66 FUQULL 0 QBT 8 MMTVSC 5 MMNKBJFWDVH 7; Store=107; Category=0 5
 What about cookies? n Cookies can be useful «used like a staple to attach multiple parts of a form together «used to identify you when you return to a web site so you don’t have to remember a password «used to help web sites understand how people use them n Cookies can be harmful «used to profile users and track their activities without their knowledge, especially across web sites 6
What about cookies? n Cookies can be useful «used like a staple to attach multiple parts of a form together «used to identify you when you return to a web site so you don’t have to remember a password «used to help web sites understand how people use them n Cookies can be harmful «used to profile users and track their activities without their knowledge, especially across web sites 6
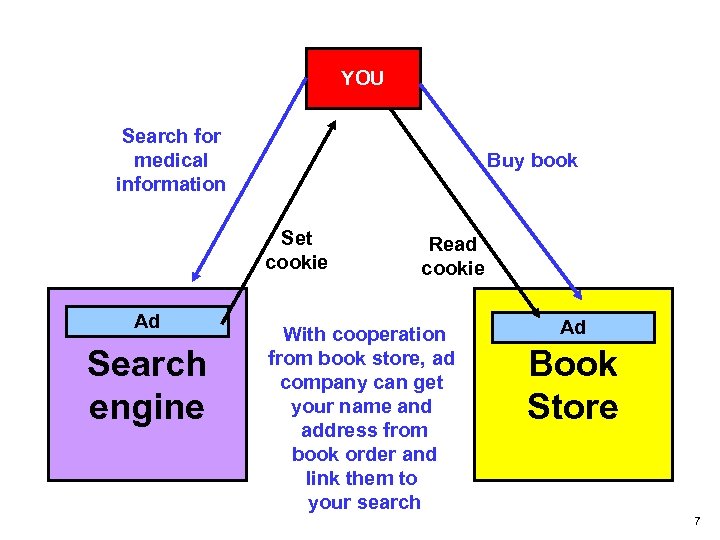 YOU Search for medical information Buy book Set cookie Ad Search engine Read cookie With cooperation from book store, ad company can get your name and address from book order and link them to your search Ad Book Store 7
YOU Search for medical information Buy book Set cookie Ad Search engine Read cookie With cooperation from book store, ad company can get your name and address from book order and link them to your search Ad Book Store 7
 Web bugs n Invisible “images” embedded in web pages that cause cookies to be transferred n Work just like banner ads from ad networks, but you can’t see them unless you look at the code behind a web page n Also embedded in HTML formatted email messages n Can also use Java. Script to perform same function without cookies For more info on web bugs see: http: //www. privacyfoundation. org/education/ 8
Web bugs n Invisible “images” embedded in web pages that cause cookies to be transferred n Work just like banner ads from ad networks, but you can’t see them unless you look at the code behind a web page n Also embedded in HTML formatted email messages n Can also use Java. Script to perform same function without cookies For more info on web bugs see: http: //www. privacyfoundation. org/education/ 8
 Referer log problems n. GET methods result in values in URL n. These URLs are sent in the REFERER header to next host n. Example: http: //www. merchant. com/cgi_bin/order? name=Tom+Jones&address=here+there&cr edit+card=234876923234&PIN=1234& -> index. html 9
Referer log problems n. GET methods result in values in URL n. These URLs are sent in the REFERER header to next host n. Example: http: //www. merchant. com/cgi_bin/order? name=Tom+Jones&address=here+there&cr edit+card=234876923234&PIN=1234& -> index. html 9
 Low tech solutions n Wander around cyber cafes n Use free e-mail service instead of ISP n Set up a pre-paid cash account with ISP «give all phony information n Obtain unusual domain name and get people you trust as name servers n Forge e-mail, spoof IP, etc. n. . . And don’t give out any personallyidentifiable data! 10
Low tech solutions n Wander around cyber cafes n Use free e-mail service instead of ISP n Set up a pre-paid cash account with ISP «give all phony information n Obtain unusual domain name and get people you trust as name servers n Forge e-mail, spoof IP, etc. n. . . And don’t give out any personallyidentifiable data! 10
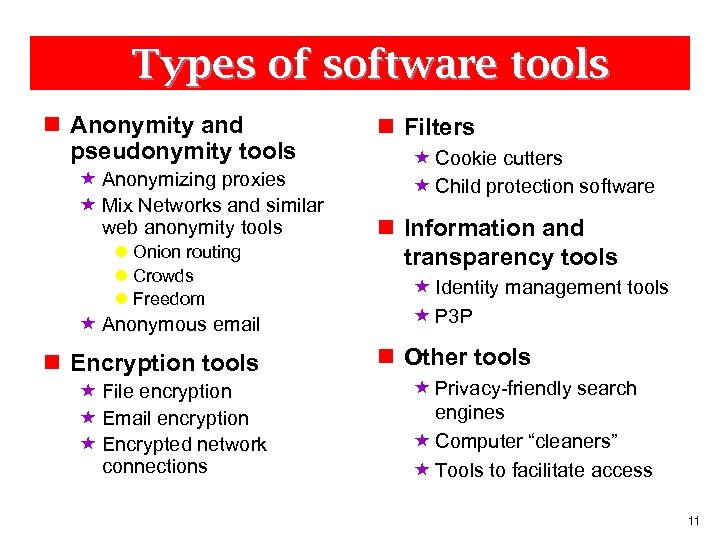 Types of software tools n Anonymity and pseudonymity tools « Anonymizing proxies « Mix Networks and similar web anonymity tools l Onion routing l Crowds l Freedom « Anonymous email n Encryption tools « File encryption « Email encryption « Encrypted network connections n Filters « Cookie cutters « Child protection software n Information and transparency tools « Identity management tools « P 3 P n Other tools « Privacy-friendly search engines « Computer “cleaners” « Tools to facilitate access 11
Types of software tools n Anonymity and pseudonymity tools « Anonymizing proxies « Mix Networks and similar web anonymity tools l Onion routing l Crowds l Freedom « Anonymous email n Encryption tools « File encryption « Email encryption « Encrypted network connections n Filters « Cookie cutters « Child protection software n Information and transparency tools « Identity management tools « P 3 P n Other tools « Privacy-friendly search engines « Computer “cleaners” « Tools to facilitate access 11
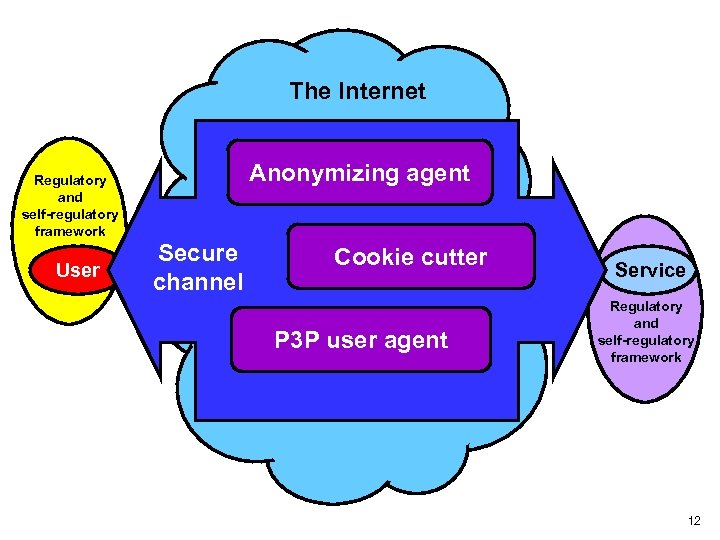 The Internet Anonymizing agent Regulatory and self-regulatory framework User Secure channel Cookie cutter P 3 P user agent Service Regulatory and self-regulatory framework 12
The Internet Anonymizing agent Regulatory and self-regulatory framework User Secure channel Cookie cutter P 3 P user agent Service Regulatory and self-regulatory framework 12
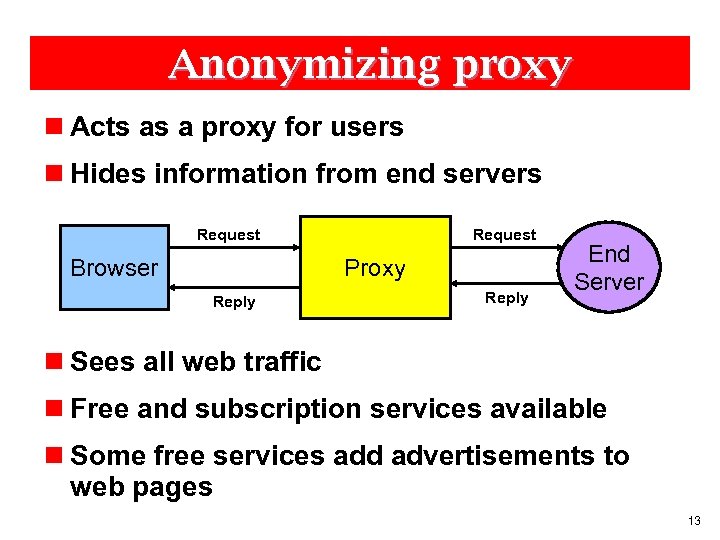 Anonymizing proxy n Acts as a proxy for users n Hides information from end servers Request Proxy Browser Reply End Server n Sees all web traffic n Free and subscription services available n Some free services add advertisements to web pages 13
Anonymizing proxy n Acts as a proxy for users n Hides information from end servers Request Proxy Browser Reply End Server n Sees all web traffic n Free and subscription services available n Some free services add advertisements to web pages 13
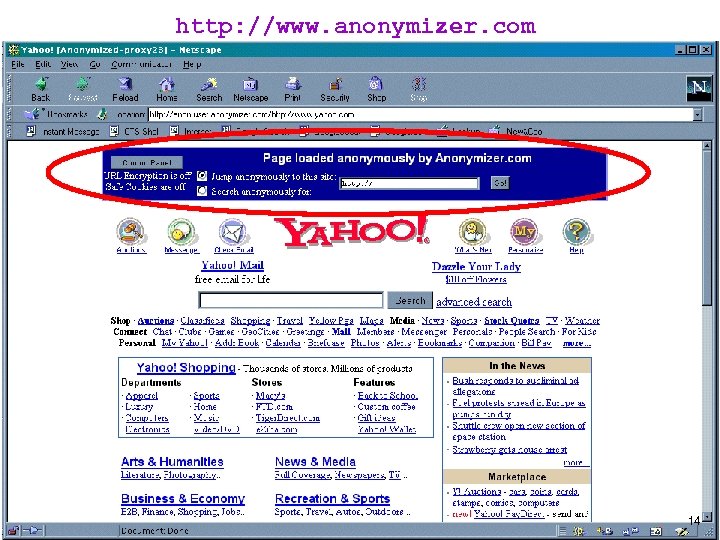 http: //www. anonymizer. com 14
http: //www. anonymizer. com 14
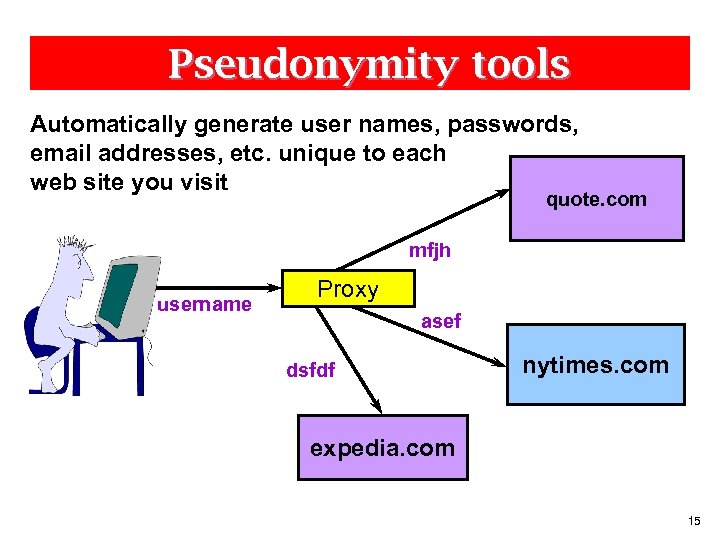 Pseudonymity tools Automatically generate user names, passwords, email addresses, etc. unique to each web site you visit quote. com mfjh username Proxy asef dsfdf nytimes. com expedia. com 15
Pseudonymity tools Automatically generate user names, passwords, email addresses, etc. unique to each web site you visit quote. com mfjh username Proxy asef dsfdf nytimes. com expedia. com 15
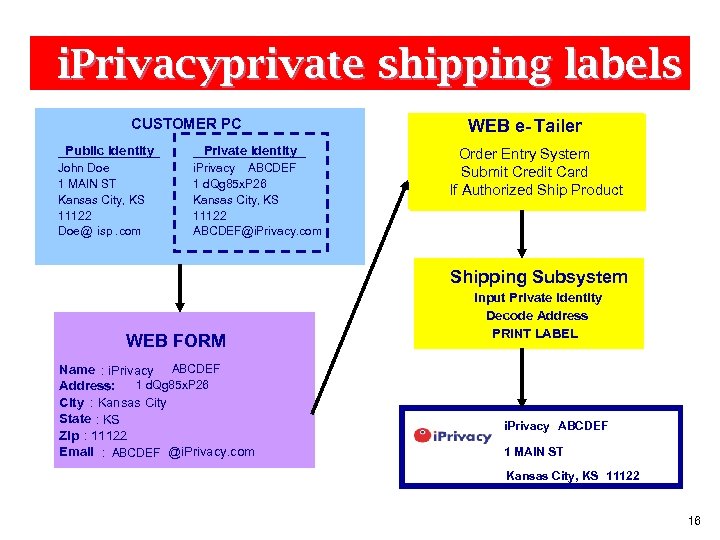 i. Privacyprivate shipping labels CUSTOMER PC Public Identity John Doe 1 MAIN ST Kansas City, KS 11122 Doe@ isp. com Private Identity i. Privacy ABCDEF 1 d. Qg 85 x. P 26 Kansas City, KS 11122 ABCDEF@i. Privacy. com WEB e- Tailer Order Entry System Submit Credit Card If Authorized Ship Product Shipping Subsystem WEB FORM Name : i. Privacy ABCDEF 1 d. Qg 85 x. P 26 Address: : City : Kansas City State : KS Zip : 11122 Email : ABCDEF @i. Privacy. com Input Private Identity Decode Address PRINT LABEL i. Privacy ABCDEF 1 MAIN ST Kansas City, KS 11122 16
i. Privacyprivate shipping labels CUSTOMER PC Public Identity John Doe 1 MAIN ST Kansas City, KS 11122 Doe@ isp. com Private Identity i. Privacy ABCDEF 1 d. Qg 85 x. P 26 Kansas City, KS 11122 ABCDEF@i. Privacy. com WEB e- Tailer Order Entry System Submit Credit Card If Authorized Ship Product Shipping Subsystem WEB FORM Name : i. Privacy ABCDEF 1 d. Qg 85 x. P 26 Address: : City : Kansas City State : KS Zip : 11122 Email : ABCDEF @i. Privacy. com Input Private Identity Decode Address PRINT LABEL i. Privacy ABCDEF 1 MAIN ST Kansas City, KS 11122 16
 17
17
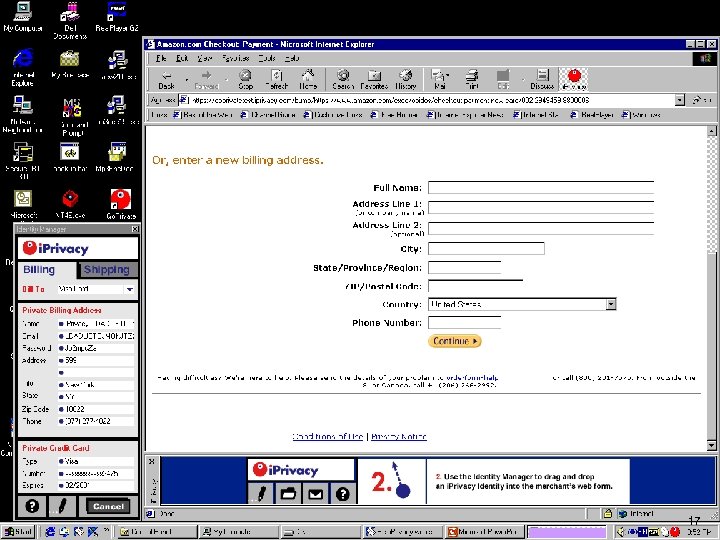
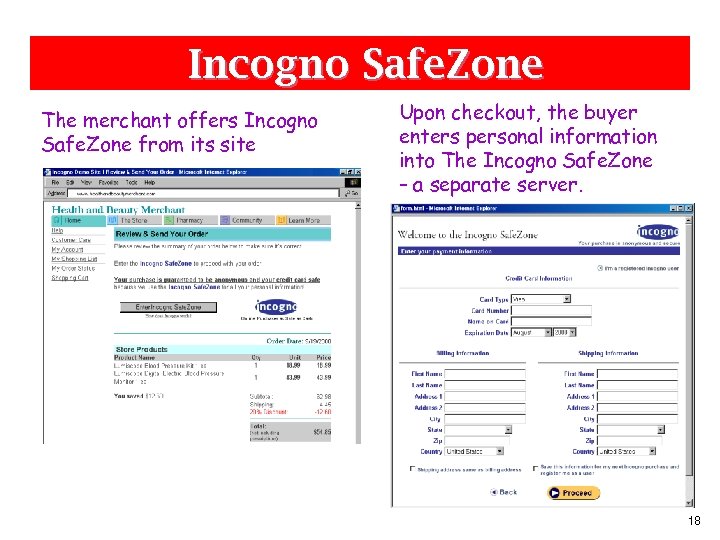 Incogno Safe. Zone The merchant offers Incogno Safe. Zone from its site Upon checkout, the buyer enters personal information into The Incogno Safe. Zone – a separate server. 18
Incogno Safe. Zone The merchant offers Incogno Safe. Zone from its site Upon checkout, the buyer enters personal information into The Incogno Safe. Zone – a separate server. 18
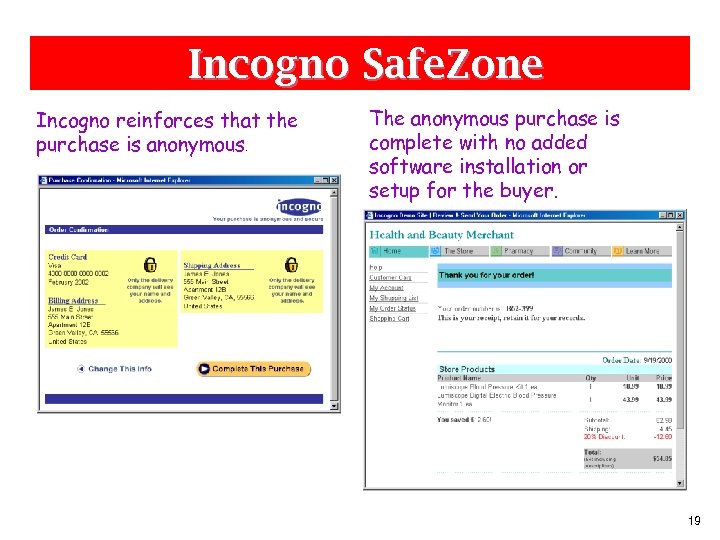 Incogno Safe. Zone Incogno reinforces that the purchase is anonymous. The anonymous purchase is complete with no added software installation or setup for the buyer. 19
Incogno Safe. Zone Incogno reinforces that the purchase is anonymous. The anonymous purchase is complete with no added software installation or setup for the buyer. 19
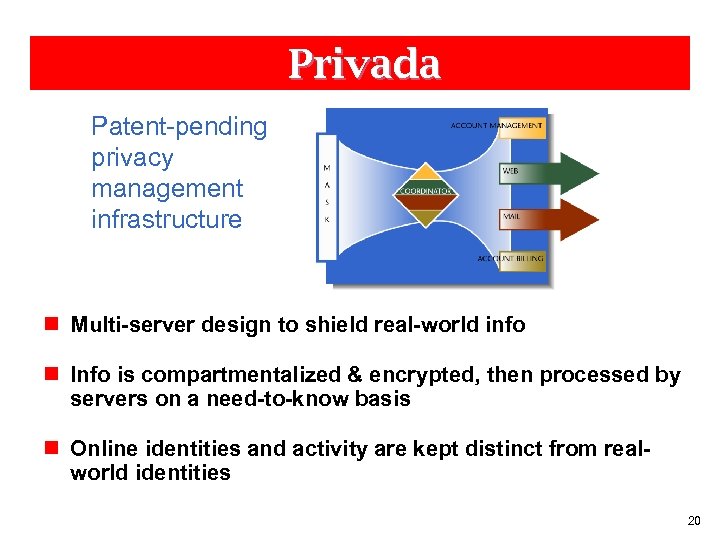 Privada Patent-pending privacy management infrastructure n Multi-server design to shield real-world info n Info is compartmentalized & encrypted, then processed by servers on a need-to-know basis n Online identities and activity are kept distinct from realworld identities 20
Privada Patent-pending privacy management infrastructure n Multi-server design to shield real-world info n Info is compartmentalized & encrypted, then processed by servers on a need-to-know basis n Online identities and activity are kept distinct from realworld identities 20
 21
21
![Mixes [Chaum 81] Sender Destination B, C dest, msg k. C k. B k. Mixes [Chaum 81] Sender Destination B, C dest, msg k. C k. B k.](https://present5.com/presentation/0cc5adcd99374052f9b9b91edc74c68b/image-22.jpg) Mixes [Chaum 81] Sender Destination B, C dest, msg k. C k. B k. A Mix C msg dest, msg k. C Mix A C dest, msg k. C k. B Mix B k. X = encrypted with public key of Mix X Sender routes message randomly through network of “Mixes”, using layered public-key encryption. 22
Mixes [Chaum 81] Sender Destination B, C dest, msg k. C k. B k. A Mix C msg dest, msg k. C Mix A C dest, msg k. C k. B Mix B k. X = encrypted with public key of Mix X Sender routes message randomly through network of “Mixes”, using layered public-key encryption. 22
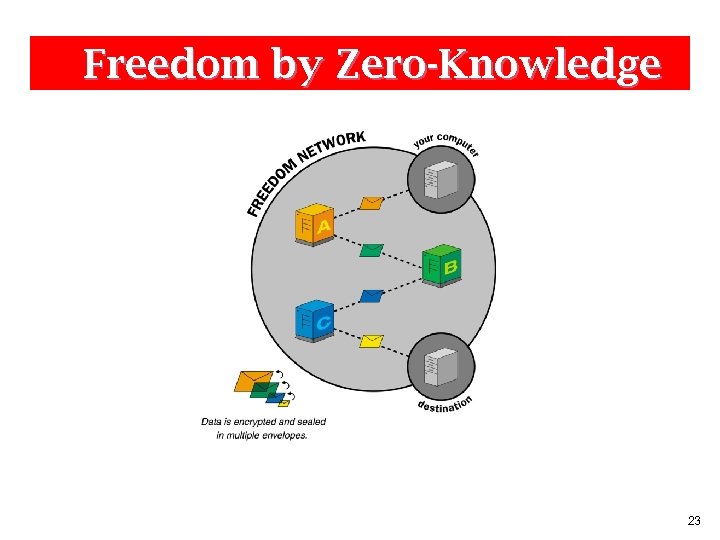 Freedom by Zero-Knowledge 23
Freedom by Zero-Knowledge 23
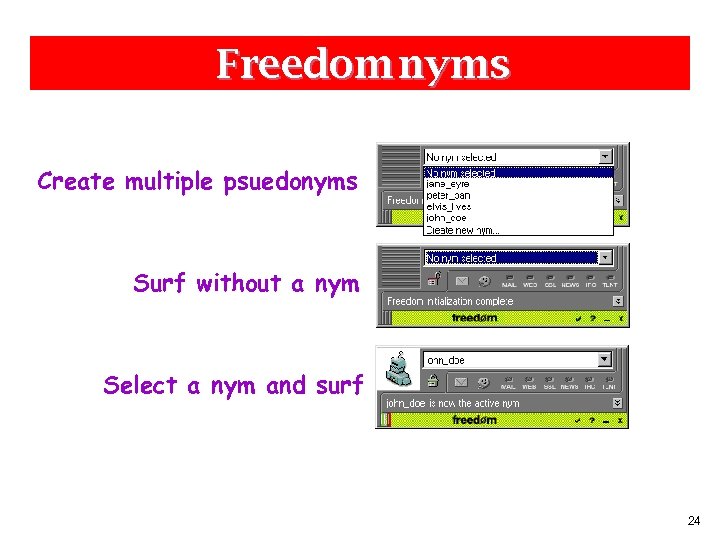 Freedom nyms Create multiple psuedonyms Surf without a nym Select a nym and surf 24
Freedom nyms Create multiple psuedonyms Surf without a nym Select a nym and surf 24
 Crowds n Experimental system developed at AT&T Research n Users join a Crowd of other users n Web requests from the crowd cannot be linked to any individual n Protection from «end servers «other crowd members «system administrators «eavesdroppers n First system to hide data shadow on the web without trusting a central authority http: //www. research. att. com/projects/crowds/ 25
Crowds n Experimental system developed at AT&T Research n Users join a Crowd of other users n Web requests from the crowd cannot be linked to any individual n Protection from «end servers «other crowd members «system administrators «eavesdroppers n First system to hide data shadow on the web without trusting a central authority http: //www. research. att. com/projects/crowds/ 25
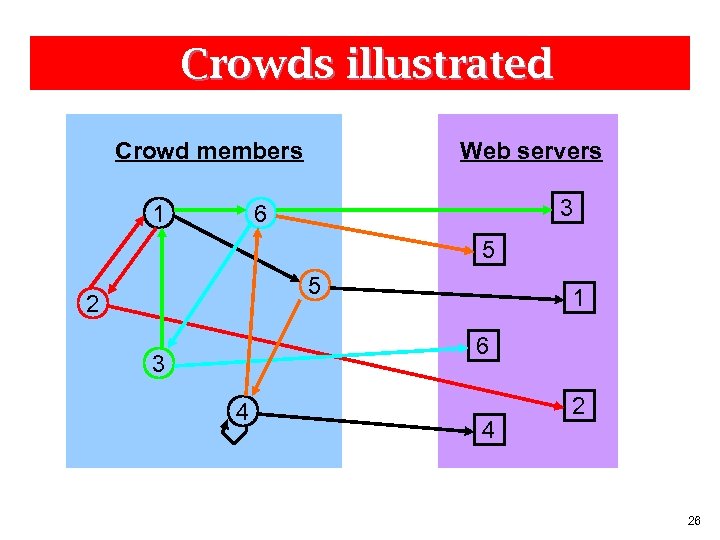 Crowds illustrated Crowd members 1 Web servers 3 6 5 5 2 1 6 3 4 4 2 26
Crowds illustrated Crowd members 1 Web servers 3 6 5 5 2 1 6 3 4 4 2 26
 Anonymous email n Anonymous remailers allow people to send email anonymously n Similar to anonymous web proxies n Some can be chained and work like mixes http: //anon. efga. org/~rlist 27
Anonymous email n Anonymous remailers allow people to send email anonymously n Similar to anonymous web proxies n Some can be chained and work like mixes http: //anon. efga. org/~rlist 27
 Encryption tools n File encryption n Email encryption «Many email programs include encryption features built in or available as plug-ins «Web-based encrypted email l Email that self-destructs – Disappearing, Inc. n Encrypted network connections «Secure socket layer (SSL) «Secure shell (SSH) «Virtual private networks 28
Encryption tools n File encryption n Email encryption «Many email programs include encryption features built in or available as plug-ins «Web-based encrypted email l Email that self-destructs – Disappearing, Inc. n Encrypted network connections «Secure socket layer (SSL) «Secure shell (SSH) «Virtual private networks 28
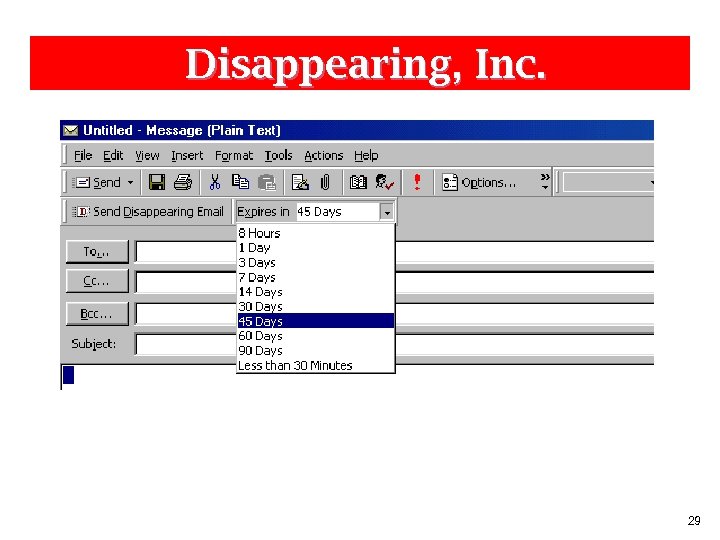 Disappearing, Inc. 29
Disappearing, Inc. 29
 Filters n Cookie Cutters «Block cookies, allow for more fine-grained cookie control, etc. «Some also filter ads, referer header, and browser chatter http: //www. junkbusters. com/ht/en/links. html#measures n Child Protection Software «Block the transmission of certain information via email, chat rooms, or web forms when child is using computer «Limit who a child can email or chat with http: //www. getnetwise. org/ 30
Filters n Cookie Cutters «Block cookies, allow for more fine-grained cookie control, etc. «Some also filter ads, referer header, and browser chatter http: //www. junkbusters. com/ht/en/links. html#measures n Child Protection Software «Block the transmission of certain information via email, chat rooms, or web forms when child is using computer «Limit who a child can email or chat with http: //www. getnetwise. org/ 30
 Identity management tools n Services and tools that help people manage their online identities « Offer convenience of not having to retype data and/or remember passwords « Some let consumers opt-in to targeted advertising (permission marketing), sharing data with sites, etc. l Some pay consumers for providing data « Some check for privacy policies before releasing data or require minimum privacy standards for participating sites n Examples « All. Advantage. com « Digital. Me « Enonymous « Lumeria « Persona « Privacy. Bank. com 31
Identity management tools n Services and tools that help people manage their online identities « Offer convenience of not having to retype data and/or remember passwords « Some let consumers opt-in to targeted advertising (permission marketing), sharing data with sites, etc. l Some pay consumers for providing data « Some check for privacy policies before releasing data or require minimum privacy standards for participating sites n Examples « All. Advantage. com « Digital. Me « Enonymous « Lumeria « Persona « Privacy. Bank. com 31
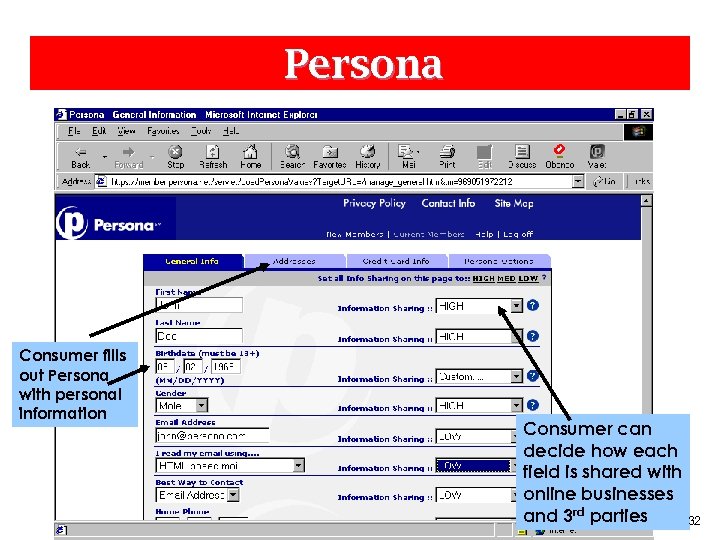 Persona Consumer fills out Persona with personal information Consumer can decide how each field is shared with online businesses and 3 rd parties 32
Persona Consumer fills out Persona with personal information Consumer can decide how each field is shared with online businesses and 3 rd parties 32
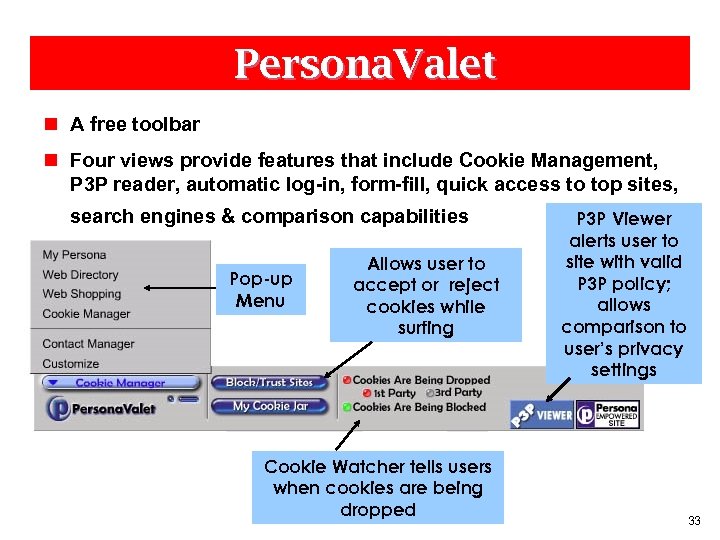 Persona. Valet n A free toolbar n Four views provide features that include Cookie Management, P 3 P reader, automatic log-in, form-fill, quick access to top sites, search engines & comparison capabilities Pop-up Menu Allows user to accept or reject cookies while surfing Cookie Watcher tells users when cookies are being dropped P 3 P Viewer alerts user to site with valid P 3 P policy; allows comparison to user’s privacy settings 33
Persona. Valet n A free toolbar n Four views provide features that include Cookie Management, P 3 P reader, automatic log-in, form-fill, quick access to top sites, search engines & comparison capabilities Pop-up Menu Allows user to accept or reject cookies while surfing Cookie Watcher tells users when cookies are being dropped P 3 P Viewer alerts user to site with valid P 3 P policy; allows comparison to user’s privacy settings 33
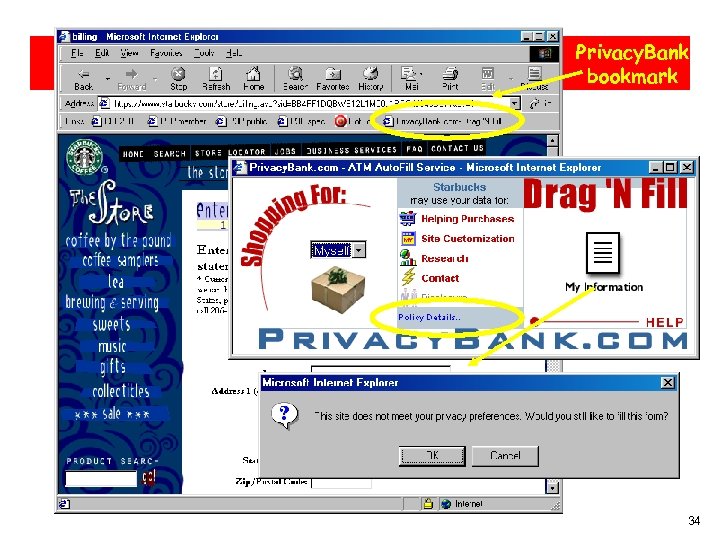 Privacy. Bank. Com Privacy. Bank bookmark 34
Privacy. Bank. Com Privacy. Bank bookmark 34
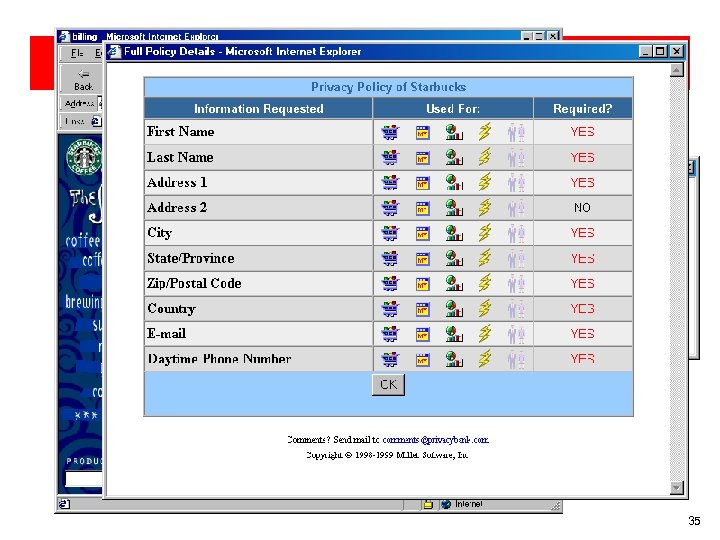 Infomediary example: Privacy. Bank bookmark 35
Infomediary example: Privacy. Bank bookmark 35
 Platform for Privacy Preferences (P 3 P) n Offers an easy way for web sites to communicate about their privacy policies in a standard machine-readable format «Can be deployed using existing web servers n This will enable the development of tools (built into browsers or separate applications) that: «Provide snapshots of sites’ policies «Compare policies with user preferences «Alert and advise the user n For more info see http: //www. w 3. org/P 3 P/ 36
Platform for Privacy Preferences (P 3 P) n Offers an easy way for web sites to communicate about their privacy policies in a standard machine-readable format «Can be deployed using existing web servers n This will enable the development of tools (built into browsers or separate applications) that: «Provide snapshots of sites’ policies «Compare policies with user preferences «Alert and advise the user n For more info see http: //www. w 3. org/P 3 P/ 36
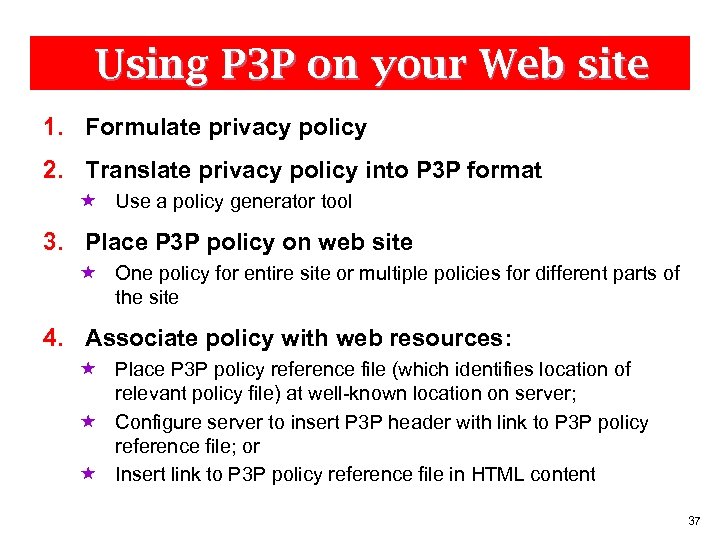 Using P 3 P on your Web site 1. Formulate privacy policy 2. Translate privacy policy into P 3 P format « Use a policy generator tool 3. Place P 3 P policy on web site « One policy for entire site or multiple policies for different parts of the site 4. Associate policy with web resources: « Place P 3 P policy reference file (which identifies location of relevant policy file) at well-known location on server; « Configure server to insert P 3 P header with link to P 3 P policy reference file; or « Insert link to P 3 P policy reference file in HTML content 37
Using P 3 P on your Web site 1. Formulate privacy policy 2. Translate privacy policy into P 3 P format « Use a policy generator tool 3. Place P 3 P policy on web site « One policy for entire site or multiple policies for different parts of the site 4. Associate policy with web resources: « Place P 3 P policy reference file (which identifies location of relevant policy file) at well-known location on server; « Configure server to insert P 3 P header with link to P 3 P policy reference file; or « Insert link to P 3 P policy reference file in HTML content 37
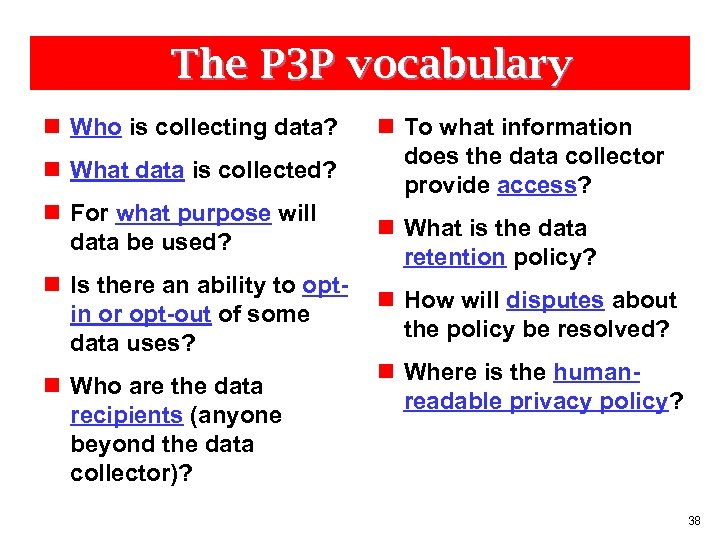 The P 3 P vocabulary n Who is collecting data? n What data is collected? n For what purpose will data be used? n Is there an ability to optin or opt-out of some data uses? n Who are the data recipients (anyone beyond the data collector)? n To what information does the data collector provide access? n What is the data retention policy? n How will disputes about the policy be resolved? n Where is the humanreadable privacy policy? 38
The P 3 P vocabulary n Who is collecting data? n What data is collected? n For what purpose will data be used? n Is there an ability to optin or opt-out of some data uses? n Who are the data recipients (anyone beyond the data collector)? n To what information does the data collector provide access? n What is the data retention policy? n How will disputes about the policy be resolved? n Where is the humanreadable privacy policy? 38
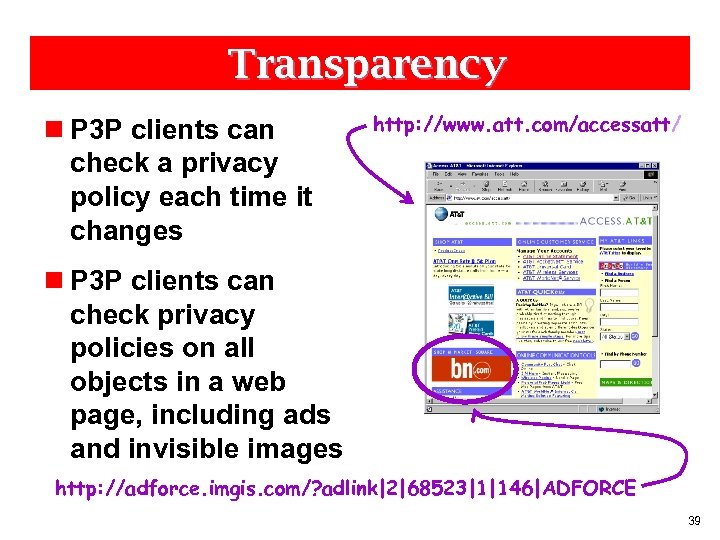 Transparency n P 3 P clients can check a privacy policy each time it changes http: //www. att. com/accessatt/ n P 3 P clients can check privacy policies on all objects in a web page, including ads and invisible images http: //adforce. imgis. com/? adlink|2|68523|1|146|ADFORCE 39
Transparency n P 3 P clients can check a privacy policy each time it changes http: //www. att. com/accessatt/ n P 3 P clients can check privacy policies on all objects in a web page, including ads and invisible images http: //adforce. imgis. com/? adlink|2|68523|1|146|ADFORCE 39
 Microsoft/AT&T P 3 P browser helper object n A prototype tool designed to work with Microsoft Internet Explorer Browser n Not yet fully tested, still missing some features 40
Microsoft/AT&T P 3 P browser helper object n A prototype tool designed to work with Microsoft Internet Explorer Browser n Not yet fully tested, still missing some features 40
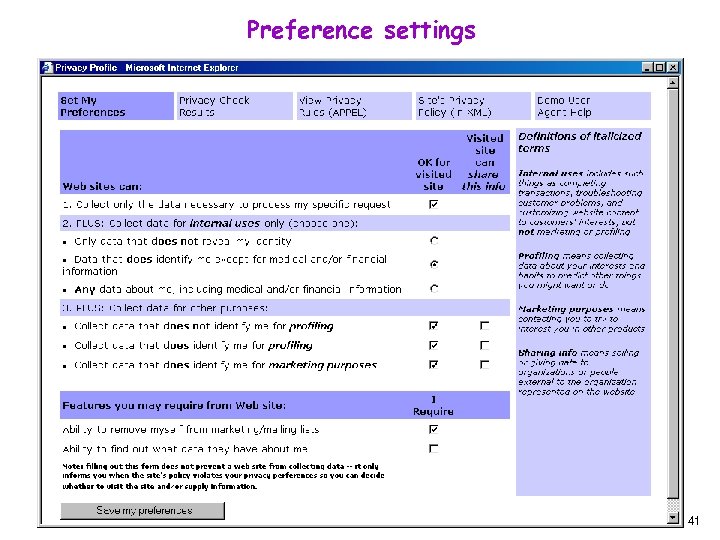 Preference settings 41
Preference settings 41
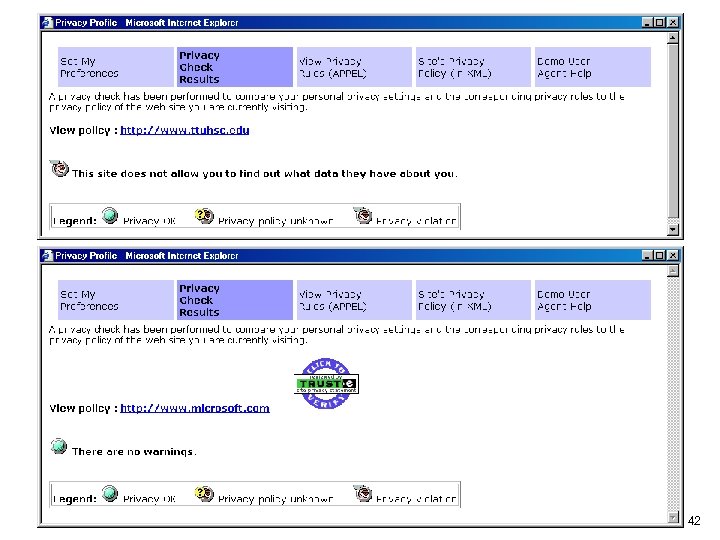 42
42
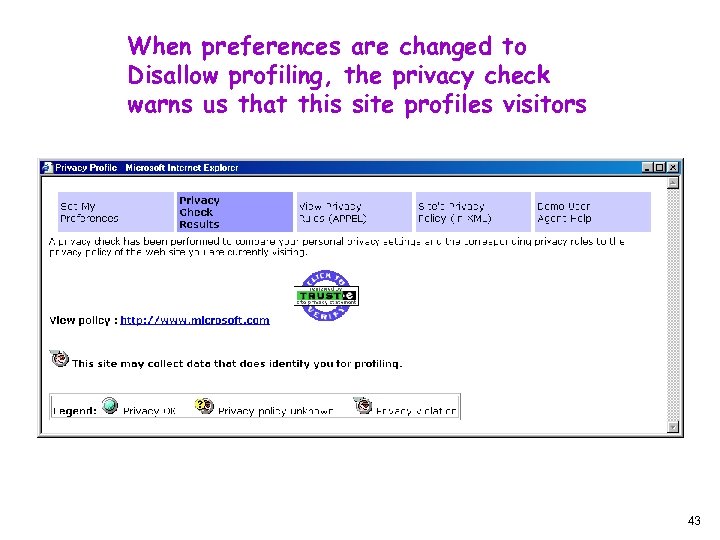 When preferences are changed to Disallow profiling, the privacy check warns us that this site profiles visitors 43
When preferences are changed to Disallow profiling, the privacy check warns us that this site profiles visitors 43
 IDcide Privacy Companion n A browser plug-in that adds functionality to Netscape or Internet Explorer browsers n Includes icons to let users know that sites use firstand/or third-party cookies n Enables users to select a privacy level that controls the cookie types allowed (1 st or 3 rd party) n Prevents data spills to 3 rd parties through “referer” n Lets users view tracking history n Prototype P 3 P-enabled Privacy Companion allows for more fine-grained automatic decision making based on P 3 P policies n http: //www. idcide. com 44
IDcide Privacy Companion n A browser plug-in that adds functionality to Netscape or Internet Explorer browsers n Includes icons to let users know that sites use firstand/or third-party cookies n Enables users to select a privacy level that controls the cookie types allowed (1 st or 3 rd party) n Prevents data spills to 3 rd parties through “referer” n Lets users view tracking history n Prototype P 3 P-enabled Privacy Companion allows for more fine-grained automatic decision making based on P 3 P policies n http: //www. idcide. com 44
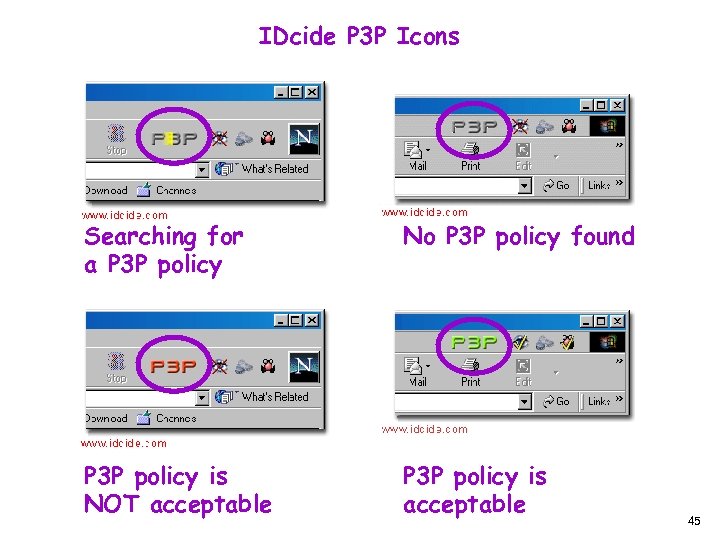 IDcide P 3 P Icons Searching for a P 3 P policy No P 3 P policy found P 3 P policy is NOT acceptable P 3 P policy is acceptable 45
IDcide P 3 P Icons Searching for a P 3 P policy No P 3 P policy found P 3 P policy is NOT acceptable P 3 P policy is acceptable 45
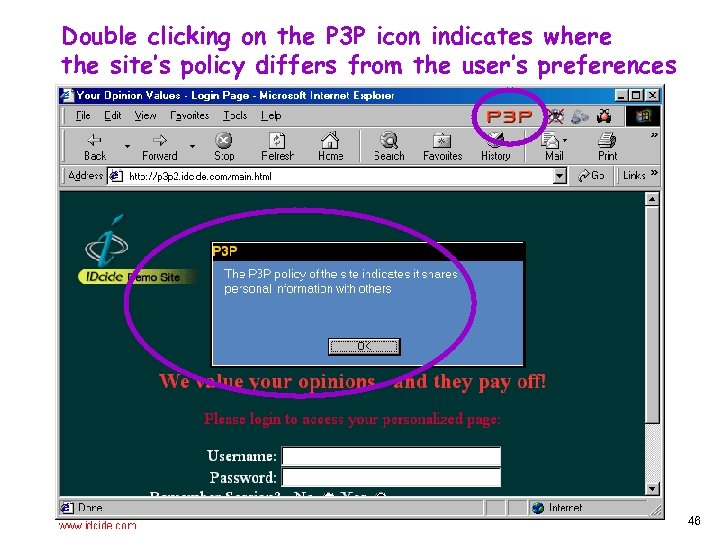 Double clicking on the P 3 P icon indicates where the site’s policy differs from the user’s preferences 46
Double clicking on the P 3 P icon indicates where the site’s policy differs from the user’s preferences 46
 YOUpowered Orby. Privacy Plus n A tool bar that sits at the top of a user’s desktop and allows a user to «Accept or deny cookies while surfing «Decide how, when and where to share personal information «Store website passwords «Enjoy the convenience of "one-click" form-fill n P 3 P features in prototype automatically rate web sites based on their P 3 P policies 47
YOUpowered Orby. Privacy Plus n A tool bar that sits at the top of a user’s desktop and allows a user to «Accept or deny cookies while surfing «Decide how, when and where to share personal information «Store website passwords «Enjoy the convenience of "one-click" form-fill n P 3 P features in prototype automatically rate web sites based on their P 3 P policies 47
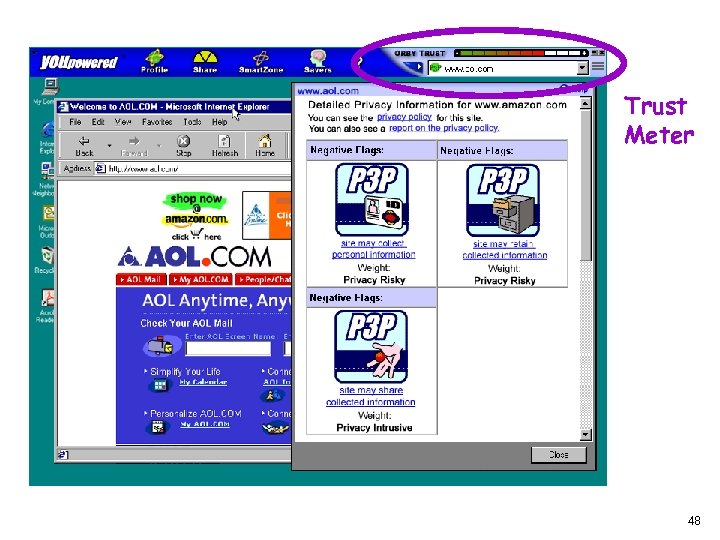 Trust Meter 48
Trust Meter 48
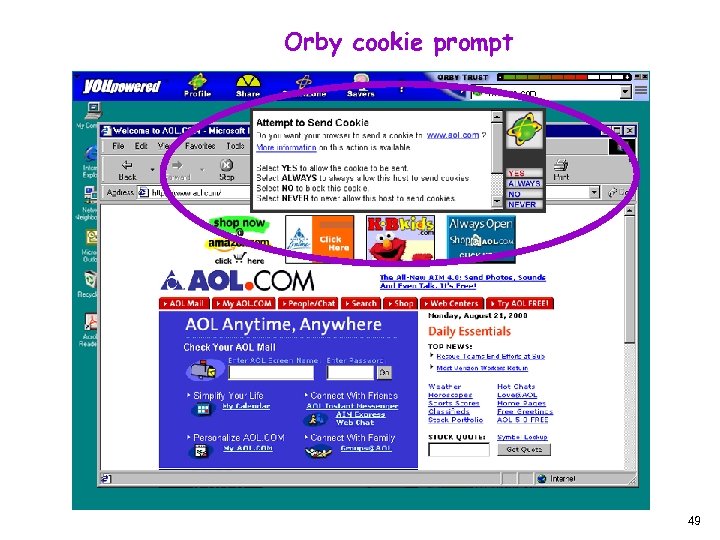 Orby cookie prompt 49
Orby cookie prompt 49
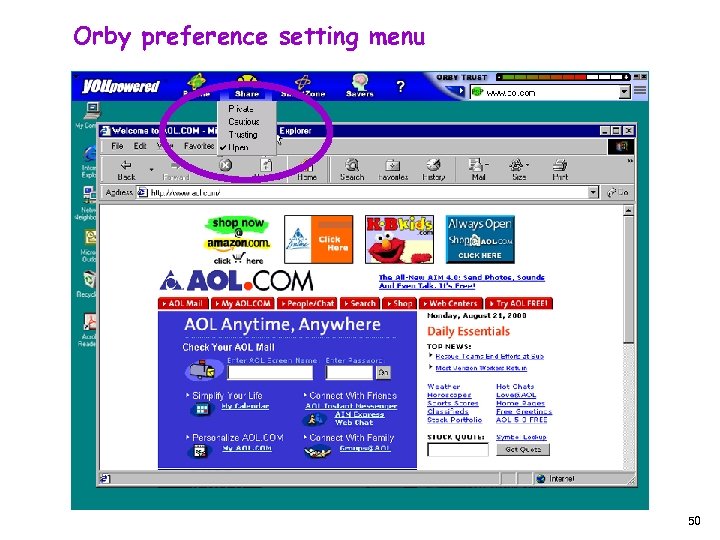 Orby preference setting menu 50
Orby preference setting menu 50
 IBM P 3 P Policy Editor n Allows web sites to create privacy policies in P 3 P and human-readable format n Drag and drop interface n Available from IBM Alpha. Works site: http: //www. alphaworks. ibm. com/tech/p 3 peditor 51
IBM P 3 P Policy Editor n Allows web sites to create privacy policies in P 3 P and human-readable format n Drag and drop interface n Available from IBM Alpha. Works site: http: //www. alphaworks. ibm. com/tech/p 3 peditor 51
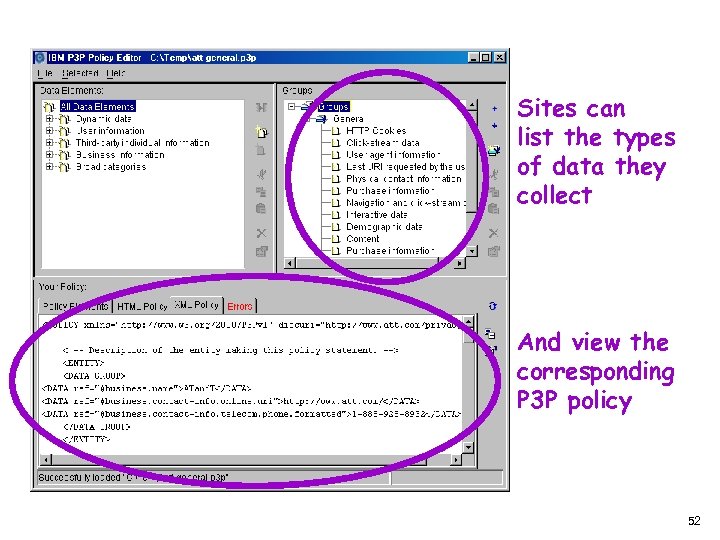 Sites can list the types of data they collect And view the corresponding P 3 P policy 52
Sites can list the types of data they collect And view the corresponding P 3 P policy 52
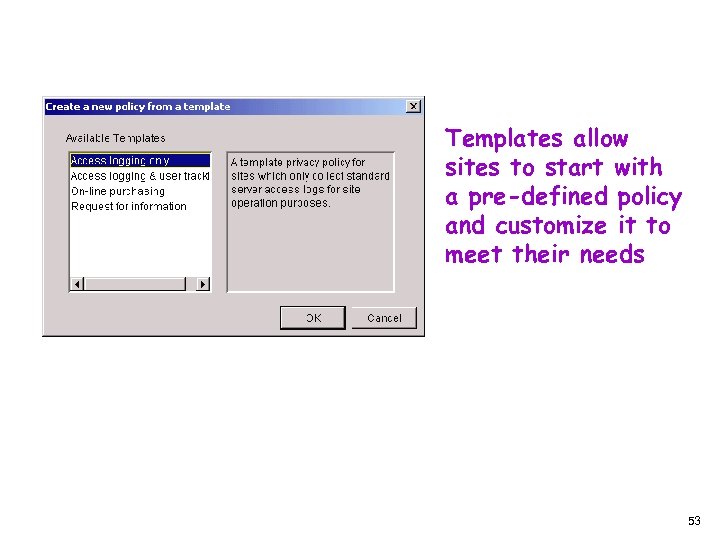 Templates allow sites to start with a pre-defined policy and customize it to meet their needs 53
Templates allow sites to start with a pre-defined policy and customize it to meet their needs 53
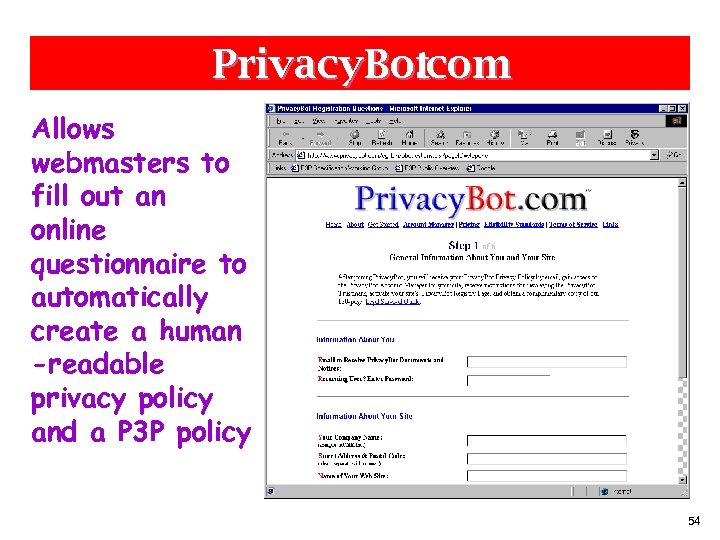 Privacy. Botcom. Allows webmasters to fill out an online questionnaire to automatically create a human -readable privacy policy and a P 3 P policy 54
Privacy. Botcom. Allows webmasters to fill out an online questionnaire to automatically create a human -readable privacy policy and a P 3 P policy 54
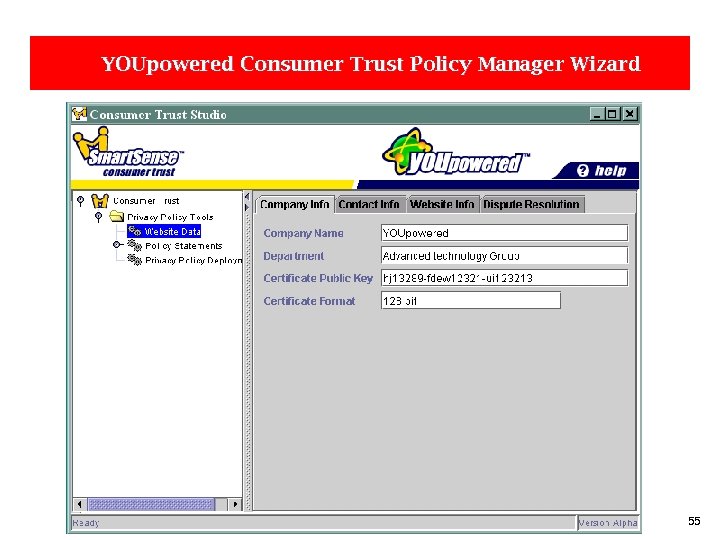 YOUpowered Consumer Trust Policy Manager Wizard 55
YOUpowered Consumer Trust Policy Manager Wizard 55
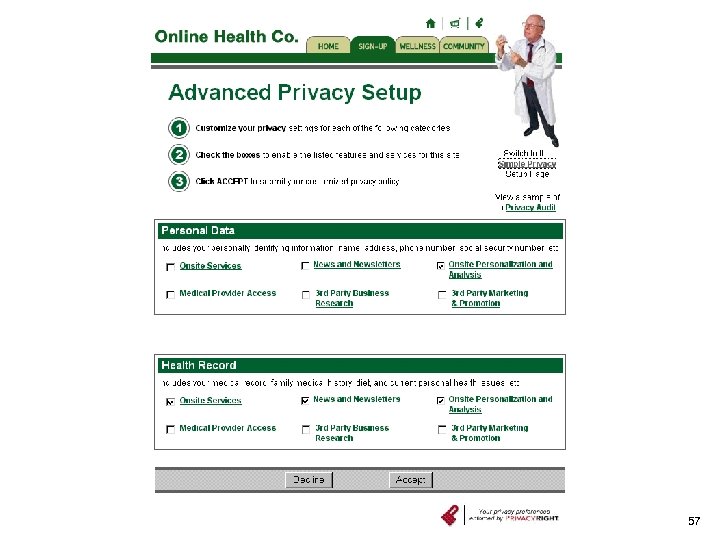
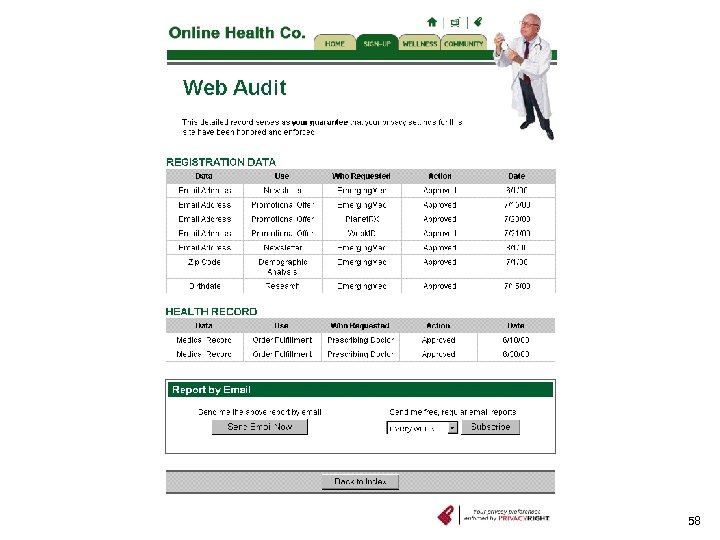
 Other tools n Privacy-friendly search engines «Top. Click n Computer “cleaners” «Window Washer – removes all traces of what web sites you visited, what files you viewed, and what files you deleted n Tools to facilitate access «Privacy. Right 56
Other tools n Privacy-friendly search engines «Top. Click n Computer “cleaners” «Window Washer – removes all traces of what web sites you visited, what files you viewed, and what files you deleted n Tools to facilitate access «Privacy. Right 56
 57
57
 58
58
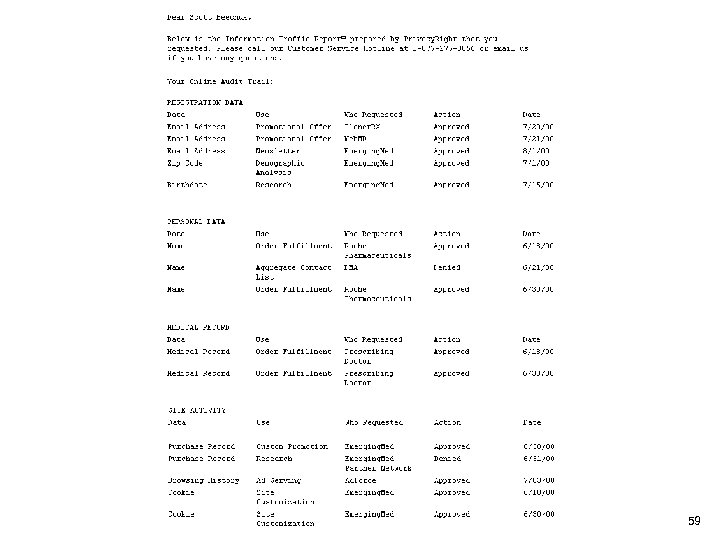 59
59
 Tools work together n P 3 P tools «help users understand privacy policies n Seal programs and regulations «help ensure that sites comply with their policies n Anonymity tools and filtering tools «reduce the amount of information revealed while browsing n Encryption tools «secure data in transit and storage n Laws and codes of practice «provide a base line level for acceptable policies 60
Tools work together n P 3 P tools «help users understand privacy policies n Seal programs and regulations «help ensure that sites comply with their policies n Anonymity tools and filtering tools «reduce the amount of information revealed while browsing n Encryption tools «secure data in transit and storage n Laws and codes of practice «provide a base line level for acceptable policies 60
 Download these slides http: //www. research. att. com/ ~lorrie/privacy/NTIA-0900. ppt 61
Download these slides http: //www. research. att. com/ ~lorrie/privacy/NTIA-0900. ppt 61


