ebcaa48aa57842ef02dd73c409dd6c72.ppt
- Количество слайдов: 32

Online Privacy Concerns Week 5 - September 28, 30 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 1

Homework 4 Discussion n http: //lorrie. cranor. org/courses/fa 04/hw 4. html n Questions or comments on reading n Strengths and weaknesses of web site privacy policies n Prohibit or compensate for sale of personal information? «Confusion about Garfinkel 8 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 2

Spam Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 3

How are online privacy concerns different from offline privacy concerns? Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 4

Web privacy concerns n Data is often collected silently « Web allows large quantities of data to be collected inexpensively and unobtrusively n Data from multiple sources may be merged « Non-identifiable information can become identifiable when merged n Data collected for business purposes may be used in civil and criminal proceedings n Users given no meaningful choice « Few sites offer alternatives Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 5
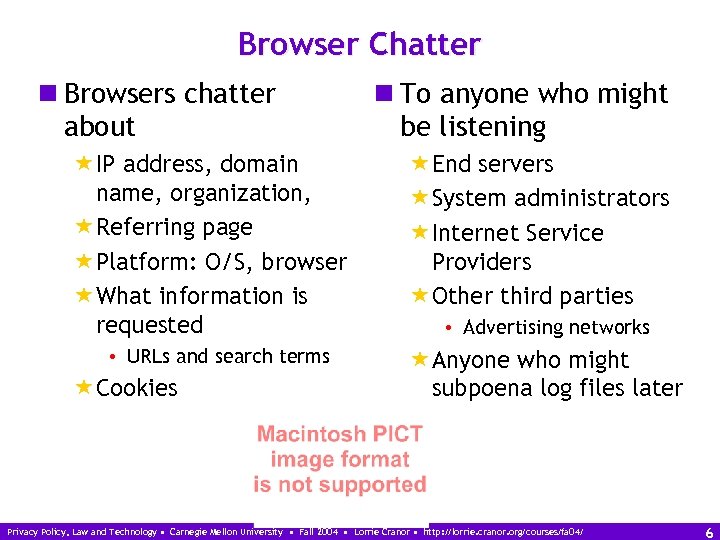
Browser Chatter n Browsers chatter about «IP address, domain name, organization, «Referring page «Platform: O/S, browser «What information is requested • URLs and search terms «Cookies n To anyone who might be listening «End servers «System administrators «Internet Service Providers «Other third parties • Advertising networks «Anyone who might subpoena log files later Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 6
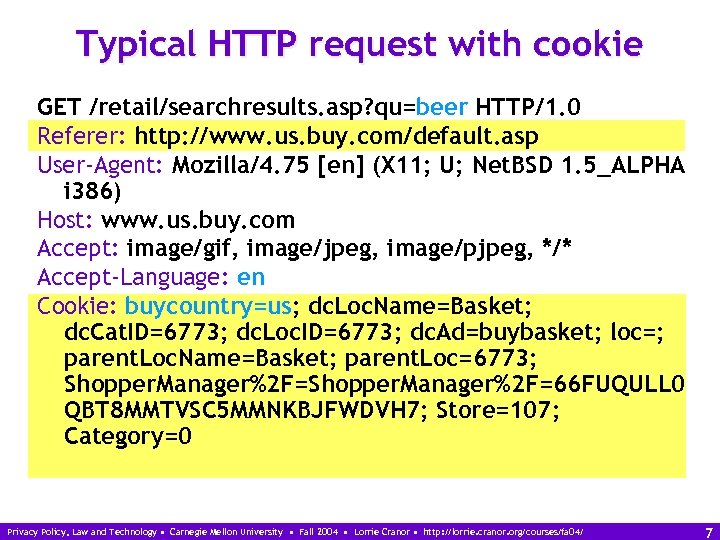
Typical HTTP request with cookie GET /retail/searchresults. asp? qu=beer HTTP/1. 0 Referer: http: //www. us. buy. com/default. asp User-Agent: Mozilla/4. 75 [en] (X 11; U; Net. BSD 1. 5_ALPHA i 386) Host: www. us. buy. com Accept: image/gif, image/jpeg, image/pjpeg, */* Accept-Language: en Cookie: buycountry=us; dc. Loc. Name=Basket; dc. Cat. ID=6773; dc. Loc. ID=6773; dc. Ad=buybasket; loc=; parent. Loc. Name=Basket; parent. Loc=6773; Shopper. Manager%2 F=66 FUQULL 0 QBT 8 MMTVSC 5 MMNKBJFWDVH 7; Store=107; Category=0 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 7

Referer log problems n. GET methods result in values in URL n. These URLs are sent in the referer header to next host n. Example: http: //www. merchant. com/cgi_bin/o rder? name=Tom+Jones&address=here +there&credit+card=234876923234& PIN=1234&->index. html n Access log example Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 8

Cookies n What are cookies? n What are people concerned about cookies? n What useful purposes do cookies serve? Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 9

Cookies 101 n Cookies can be useful «Used like a staple to attach multiple parts of a form together «Used to identify you when you return to a web site so you don’t have to remember a password «Used to help web sites understand how people use them n Cookies can do unexpected things «Used to profile users and track their activities, especially across web sites Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 10
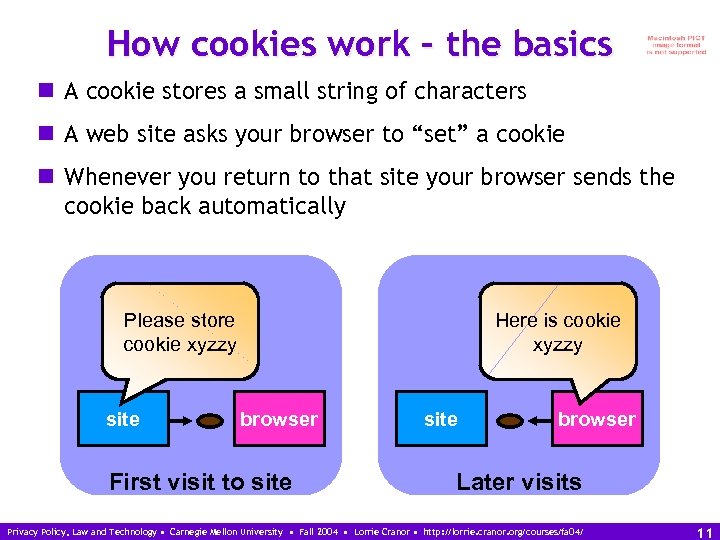
How cookies work – the basics n A cookie stores a small string of characters n A web site asks your browser to “set” a cookie n Whenever you return to that site your browser sends the cookie back automatically Please store cookie xyzzy site Here is cookie xyzzy browser First visit to site browser Later visits Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 11
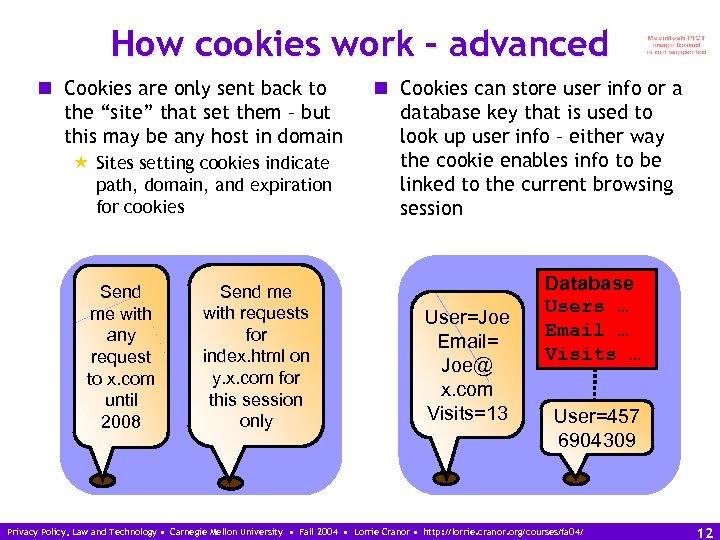
How cookies work – advanced n Cookies are only sent back to the “site” that set them – but this may be any host in domain « Sites setting cookies indicate path, domain, and expiration for cookies Send me with any request to x. com until 2008 Send me with requests for index. html on y. x. com for this session only n Cookies can store user info or a database key that is used to look up user info – either way the cookie enables info to be linked to the current browsing session User=Joe Email= Joe@ x. com Visits=13 Database Users … Email … Visits … User=457 6904309 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 12

Cookie terminology n Cookie Replay – sending a cookie back to a site n Session cookie – cookie replayed only during current browsing session n Persistent cookie – cookie replayed until expiration date n First-party cookie – cookie associated with the site the user requested n Third-party cookie – cookie associated with an image, ad, frame, or other content from a site with a different domain name that is embedded in the site the user requested « Browser interprets third-party cookie based on domain name, even if both domains are owned by the same company Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 13
Web bugs n Invisible “images” (1 -by-1 pixels, transparent) embedded in web pages and cause referer info and cookies to be transferred n Also called web beacons, clear gifs, tracker gifs, etc. n Work just like banner ads from ad networks, but you can’t see them unless you look at the code behind a web page n Also embedded in HTML formatted email messages, MS Word documents, etc. n For software to detect web bugs see: http: //www. bugnosis. org Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 14

How data can be linked n Every time the same cookie is replayed to a site, the site may add information to the record associated with that cookie «Number of times you visit a link, time, date «What page you visited last «Information you type into a web form n If multiple cookies are replayed together, they are usually logged together, effectively linking their data «Narrow scoped cookie might get logged with broad scoped cookie Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 15
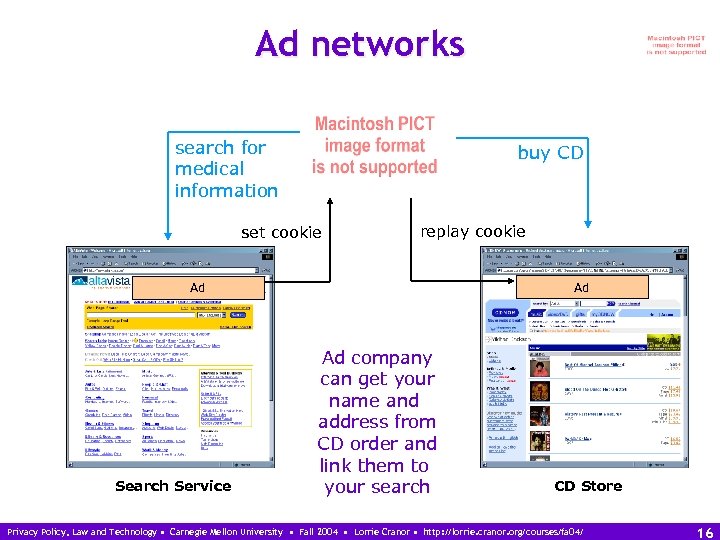
Ad networks search for medical information buy CD set cookie replay cookie Ad Ad Search Service Ad company can get your name and address from CD order and link them to your search CD Store Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 16
What ad networks may know… n Personal data: «Email address «Full name «Mailing address (street, city, state, and Zip code) «Phone number n Transactional data: «Details of plane trips «Search phrases used at search engines «Health conditions “It was not necessary for me to click on the banner ads for information to be sent to Double. Click servers. ” – Richard M. Smith Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 17
Online and offline merging n In November 1999, Double. Click purchased Abacus Direct, a company possessing detailed consumer profiles on more than 90% of US households. n In mid-February 2000 Double. Click announced plans to merge “anonymous” online data with personal information obtained from offline databases n By the first week in March 2000 the plans were put on hold « Stock dropped from $125 (12/99) to $80 (03/00) Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 18
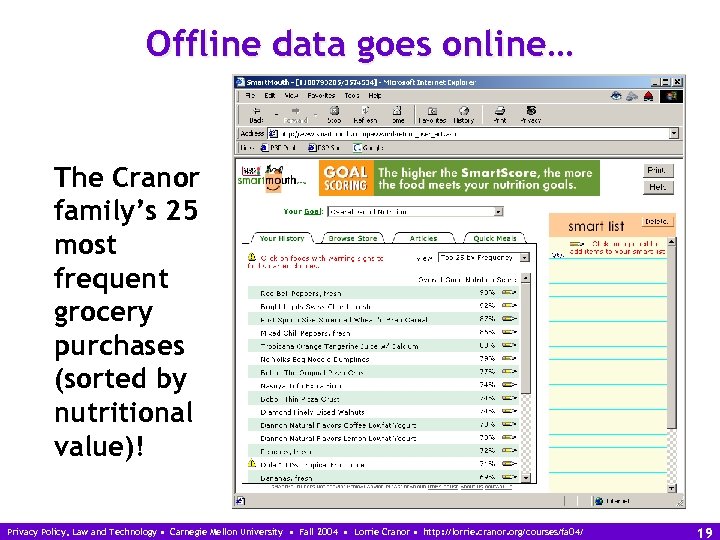
Offline data goes online… The Cranor family’s 25 most frequent grocery purchases (sorted by nutritional value)! Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 19

Steps sites take to protect privacy n Opt-out cookie «Double. Click «http: //www. doubleclick. com/us/about_doubl eclick/privacy/ad-cookie/ n Purging identifiable data from server logs «Amazon. com honor system «http: //s 1. amazon. com/exec/varzea/subst/fx /help/how-we-know. html/002 -18528529525663 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 20
Subpoenas n Data on online activities is increasingly of interest in civil and criminal cases n The only way to avoid subpoenas is to not have data n In the US, your files on your computer in your home have much greater legal protection that your files stored on a server on the network Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 21
Spyware n Spyware: Software that employs a user's Internet connection, without their knowledge or explicit permission, to collect information « Most products use pseudonymous, but unique ID n Over 800 known freeware and shareware products contain Spyware, for example: « Beeline Search Utility « Go. Zilla Download Manager « Comet Cursor n Often difficult to uninstall! n Anti-Spyware Sites: « http: //grc. com/oo/spyware. htm « http: //www. adcop. org/smallfish « http: //www. spychecker. com « http: //cexx. org/adware. htm Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 22

Devices that monitor you Creative Labs Nomad Juke. Box Music transfer software reports all uploads to Creative Labs. Sony e. Marker Lets you figure out the artitst and title of songs you hear on the radio. And keeps a personal log of all the music you like on the emarker Web site. http: //www. nomadworld. com http: //www. emarker. com Sportbrain Monitors daily workout. Custom phone cradle uploads data to company Web site for analysis. http: //www. sportbrain. com/ : Cue. Cat Keeps personal log of advertisements you‘re interested in. http: //www. crq. com/cuecat. html See http: //www. privacyfoundation. org/ Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 23

Ubiquitous Computing n User (devices) communicate with infrastructure that surrounds them «Allows geography to become relevant (new) «Opportunity to aid development n E. g. , Mc. Donald's Coupons «Walking through a mall «… you have been to Mc. Donald’s «… and you like Big Mac’s «Suddenly, Big Mac coupons appear on your PDA n Anybody have a problem with this? Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 24

Tracking (GPS) n Global Positioning System (GPS) uses 15+ satellites to triangulate (locate) receiver « Used to track users, vehicles, E-911 « Very important for commercial navigation, military applications, and tracking (with transmitter) n On. Star uses technology « Offers roadside assistance « Emergency road assistance « Navigation, services locator (e. g. , where is gas) n Like many other technologies, can be abused « Tracking where people go, when they, who they (potentially) meet, … Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 25

When good technologies go bad … n The Nanny Cam «X. 10 Camera (heavily advertised on web) «Allows “small footprint” camera to transmit to local computer/TV (undetectable) «Sold to be used to monitor without detection «Transmits data via 802. 11 n Any problems here? The Nanny-Cam (NBC) Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 26

Research and Communication Skills Evaluating information sources n Don’t believe everything you read! n News sources are usually a reporter's interpretation of what someone else did n Conference and journal papers are first hand reports of research studies that have been peer reviewed « but journals usually have more review than conferences n Technical reports are usually first hand reports of research studies that have not been peer reviewed (yet) « Look for subsequent conference or journal publications n Web sites and books are anything goes, but books at least have an editor (usually) n When possible, cite research results and technical information from peer reviewed sources Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 27

Administrative notes n Discussion with Pulse staff «Nick Ennis, Jason Surovy, and Lindsey Arroyo n Alma Whitten talk today at noon, NSH 1507 Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 28
Homework 6 n http: //lorrie. cranor. org/courses/fa 04/hw 6. html n Note, you may need to use a Windows machine! Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 29
Homework 5 Discussion n http: //lorrie. cranor. org/courses/fa 04/hw 5. html n Privacy software reviews n Why do sites use web bugs? Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 30

Discussion question n What do you think is the best long term approach for combating spam? Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 31

Network security and spam n http: //www. nanog. org/mtg 0310/spam. html Privacy Policy, Law and Technology • Carnegie Mellon University • Fall 2004 • Lorrie Cranor • http: //lorrie. cranor. org/courses/fa 04/ 32
ebcaa48aa57842ef02dd73c409dd6c72.ppt