79e593438978c220dce14eb7808db655.ppt
- Количество слайдов: 24
 Onion Routing R. Newman
Onion Routing R. Newman
 Topics Defining anonymity Need for anonymity Defining privacy Threats to anonymity and privacy Mechanisms to provide anonymity Metrics for Anonymity Applications of anonymity technology
Topics Defining anonymity Need for anonymity Defining privacy Threats to anonymity and privacy Mechanisms to provide anonymity Metrics for Anonymity Applications of anonymity technology
 Traffic Analysis Vanilla traffic analysis easy Even if data are encrypted (e. g. , using IPsec) Read src and dest from packet Can see src, dest, since have to route packet Other observations Amounts of data flowing Connections open/close timing
Traffic Analysis Vanilla traffic analysis easy Even if data are encrypted (e. g. , using IPsec) Read src and dest from packet Can see src, dest, since have to route packet Other observations Amounts of data flowing Connections open/close timing
 Onion Routing Bi-directional socket connections Onions used to set up virtual circuits Setup is distinct from data flow over VC Intermediate proxies only know predecessor and successor Onion = layered object Circuit traffic is encrypted Like Chaum Mix-nets Only initiator proxy knows whole path Basis for TOR (The Onion Router) Used worldwide
Onion Routing Bi-directional socket connections Onions used to set up virtual circuits Setup is distinct from data flow over VC Intermediate proxies only know predecessor and successor Onion = layered object Circuit traffic is encrypted Like Chaum Mix-nets Only initiator proxy knows whole path Basis for TOR (The Onion Router) Used worldwide
 Onion Routing Uses proxy servers Used to accommodate firewalls Well-established mechanism Used for www and telnet Data stream follows a path through proxies Path defined by initiating proxy Should be managed by source organization/user Initiating proxy should also be intermediate proxy for other paths
Onion Routing Uses proxy servers Used to accommodate firewalls Well-established mechanism Used for www and telnet Data stream follows a path through proxies Path defined by initiating proxy Should be managed by source organization/user Initiating proxy should also be intermediate proxy for other paths
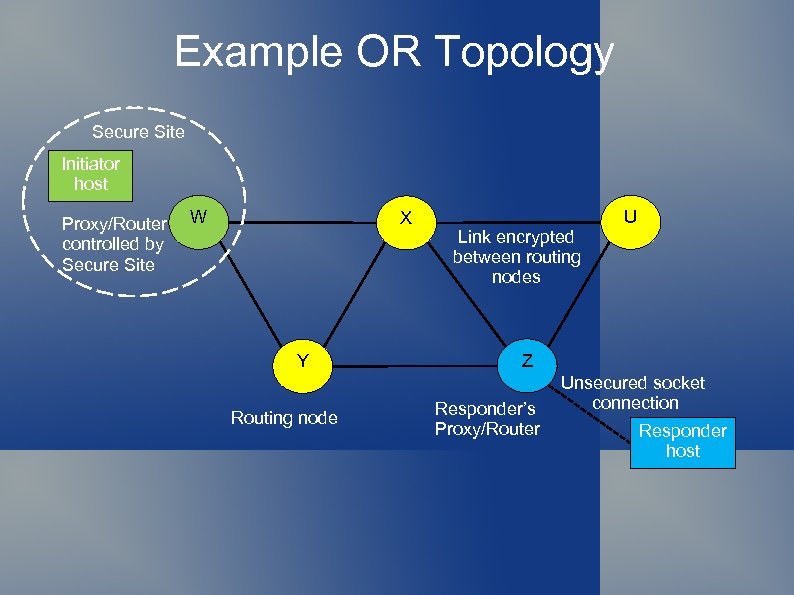 Example OR Topology Secure Site Initiator host Proxy/Router controlled by Secure Site W X Y Routing node Link encrypted between routing nodes U Z Responder’s Proxy/Router Unsecured socket connection Responder host
Example OR Topology Secure Site Initiator host Proxy/Router controlled by Secure Site W X Y Routing node Link encrypted between routing nodes U Z Responder’s Proxy/Router Unsecured socket connection Responder host
 Onion Routing Proxy can combine all traffic from enclave Further confounds traffic analysis Data stream follows a path through proxies Data NOT encrypted between initiator host and proxy Data encrypted along path from proxy to exit router Or between exit router and responder Goal is NOT anonymity per se End parties generally DO know each other But prevent third party from knowing endpoints
Onion Routing Proxy can combine all traffic from enclave Further confounds traffic analysis Data stream follows a path through proxies Data NOT encrypted between initiator host and proxy Data encrypted along path from proxy to exit router Or between exit router and responder Goal is NOT anonymity per se End parties generally DO know each other But prevent third party from knowing endpoints
 Onion Routing Goal is NOT anonymity per se But prevent third party from knowing endpoints Data analytics can reveal interests/intentions from observing history of web searches, e. g. Anonymous Remailers Keep log of packets to prevent replays Not suitable for HTTP traffic Too much data! Requires bi-directional, interactive traffic
Onion Routing Goal is NOT anonymity per se But prevent third party from knowing endpoints Data analytics can reveal interests/intentions from observing history of web searches, e. g. Anonymous Remailers Keep log of packets to prevent replays Not suitable for HTTP traffic Too much data! Requires bi-directional, interactive traffic
 Onion Routing Establishes bidirectional communication End responder does not HAVE to know initiator Individual messages are not logged Anonymous email supported Can include reply onion for responder Keeps initiator anonymous Can be used after current connection closed
Onion Routing Establishes bidirectional communication End responder does not HAVE to know initiator Individual messages are not logged Anonymous email supported Can include reply onion for responder Keeps initiator anonymous Can be used after current connection closed
 Onions Encapsulate routes Constructs onion – to set up virtual circuit Initiator proxy determines a route Data sent after route is set up Forward Onion Encrypt for responder’s proxy (Z) Encrypt for predecessor router (Y), with message for Z as payload Continue adding layers (similar to Chaum Mix-net) for entire route (backwards)
Onions Encapsulate routes Constructs onion – to set up virtual circuit Initiator proxy determines a route Data sent after route is set up Forward Onion Encrypt for responder’s proxy (Z) Encrypt for predecessor router (Y), with message for Z as payload Continue adding layers (similar to Chaum Mix-net) for entire route (backwards)
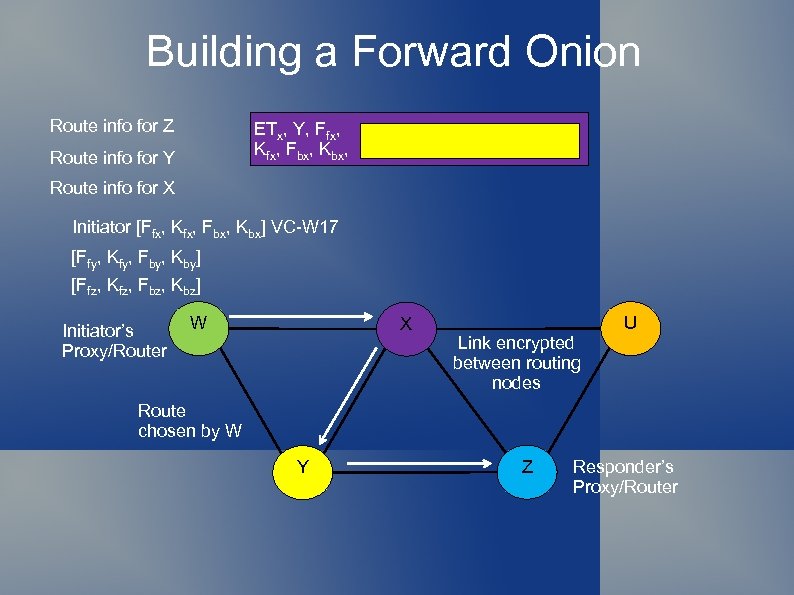 Building a Forward Onion Route info for Z ETx, Y, Ffx, ETy, Z, Ffy, ETz, NULL, Ffz, Kfx, Fbx, Kbx. Kfy, Fby, Kfz, Fbz, Kbz, pad , Route info for Y Route info for X Initiator [Ffx, Kfx, Fbx, Kbx] VC-W 17 [Ffy, Kfy, Fby, Kby] [Ffz, Kfz, Fbz, Kbz] Initiator’s Proxy/Router W X Link encrypted between routing nodes U Route chosen by W Y Z Responder’s Proxy/Router
Building a Forward Onion Route info for Z ETx, Y, Ffx, ETy, Z, Ffy, ETz, NULL, Ffz, Kfx, Fbx, Kbx. Kfy, Fby, Kfz, Fbz, Kbz, pad , Route info for Y Route info for X Initiator [Ffx, Kfx, Fbx, Kbx] VC-W 17 [Ffy, Kfy, Fby, Kby] [Ffz, Kfz, Fbz, Kbz] Initiator’s Proxy/Router W X Link encrypted between routing nodes U Route chosen by W Y Z Responder’s Proxy/Router
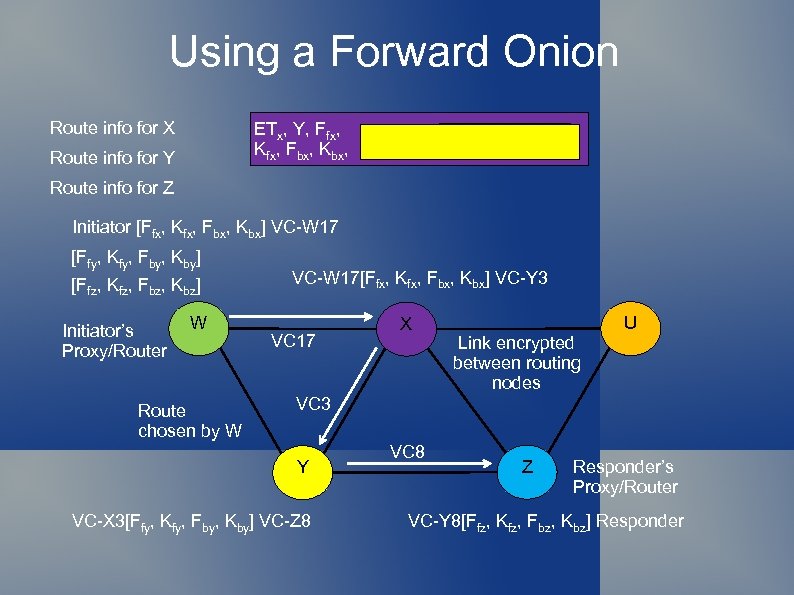 Using a Forward Onion Route info for X ETx, Y, Ffx, ETy, Z, Ffy, ETz, NULL, Ffz, Kfx, Fbx, Kbx. Kfy, Fby, Kfz, Fbz, Kbz, pad , Route info for Y Route info for Z Initiator [Ffx, Kfx, Fbx, Kbx] VC-W 17 [Ffy, Kfy, Fby, Kby] [Ffz, Kfz, Fbz, Kbz] Initiator’s Proxy/Router W Route chosen by W VC-W 17[Ffx, Kfx, Fbx, Kbx] VC-Y 3 VC 17 X Link encrypted between routing nodes U VC 3 Y VC-X 3[Ffy, Kfy, Fby, Kby] VC-Z 8 VC 8 Z Responder’s Proxy/Router VC-Y 8[Ffz, Kfz, Fbz, Kbz] Responder
Using a Forward Onion Route info for X ETx, Y, Ffx, ETy, Z, Ffy, ETz, NULL, Ffz, Kfx, Fbx, Kbx. Kfy, Fby, Kfz, Fbz, Kbz, pad , Route info for Y Route info for Z Initiator [Ffx, Kfx, Fbx, Kbx] VC-W 17 [Ffy, Kfy, Fby, Kby] [Ffz, Kfz, Fbz, Kbz] Initiator’s Proxy/Router W Route chosen by W VC-W 17[Ffx, Kfx, Fbx, Kbx] VC-Y 3 VC 17 X Link encrypted between routing nodes U VC 3 Y VC-X 3[Ffy, Kfy, Fby, Kby] VC-Z 8 VC 8 Z Responder’s Proxy/Router VC-Y 8[Ffz, Kfz, Fbz, Kbz] Responder
 Onions Forward Onion Include Expiration Time for onion Include Next Hop address (except for last router) Layers of encryption using public key of successor Include forward and backward functions and keys Expiration Time Used to detect replays Copy of onion held until expiration time is up If duplicate arrives, discard If expired onion arrives, discard
Onions Forward Onion Include Expiration Time for onion Include Next Hop address (except for last router) Layers of encryption using public key of successor Include forward and backward functions and keys Expiration Time Used to detect replays Copy of onion held until expiration time is up If duplicate arrives, discard If expired onion arrives, discard
 Onions Onion shrinkage Each router removes the plaintext it sees as it processes the onion So onion shrinks as it traverses route Size of onion would reveal location in route! Padding Each router adds random bitstring to end of payload Equal in length to the information it strips from header Router cannot tell how much of payload is padding Except last router Initiator proxy pads central payload to fixed onion size So onions all look the same
Onions Onion shrinkage Each router removes the plaintext it sees as it processes the onion So onion shrinks as it traverses route Size of onion would reveal location in route! Padding Each router adds random bitstring to end of payload Equal in length to the information it strips from header Router cannot tell how much of payload is padding Except last router Initiator proxy pads central payload to fixed onion size So onions all look the same
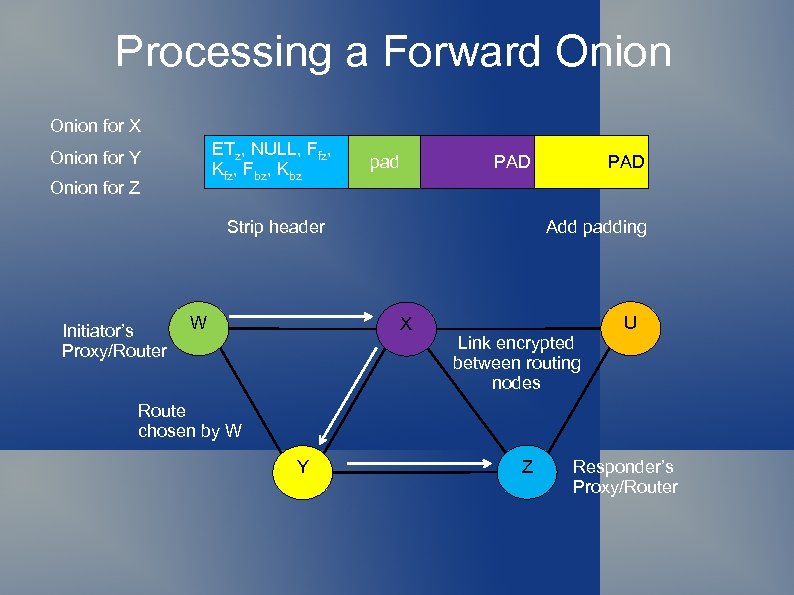 Processing a Forward Onion for X ETy Z, fx NULL, , ETxz, , Y, Ffz. Payload pad Kfz Fbz Kbz Payload Kfz, , Fbz, , Kbz, Onion for Y Onion for Z PAD Strip header Initiator’s Proxy/Router W PAD Add padding X Link encrypted between routing nodes U Route chosen by W Y Z Responder’s Proxy/Router
Processing a Forward Onion for X ETy Z, fx NULL, , ETxz, , Y, Ffz. Payload pad Kfz Fbz Kbz Payload Kfz, , Fbz, , Kbz, Onion for Y Onion for Z PAD Strip header Initiator’s Proxy/Router W PAD Add padding X Link encrypted between routing nodes U Route chosen by W Y Z Responder’s Proxy/Router
 Setting up Virtual Circuits Messages sent on VC Message format Command – identifies message type VCID – identifies virtual circuit Data – payload of message Message types Create – to set up Destroy – to tear down Data – to send data (fwd or bkwd)
Setting up Virtual Circuits Messages sent on VC Message format Command – identifies message type VCID – identifies virtual circuit Data – payload of message Message types Create – to set up Destroy – to tear down Data – to send data (fwd or bkwd)
 Setting up Virtual Circuits Create Command Accompanies an onion Recipient selects VCID Sends create command with massaged onion and VCID to next router Stores VCID pair along with VCID info Fwd and bkwd functions and keys Data Command Intermediate nodes convert VCID Apply appropriate function with key Destroy Remove VCID entry
Setting up Virtual Circuits Create Command Accompanies an onion Recipient selects VCID Sends create command with massaged onion and VCID to next router Stores VCID pair along with VCID info Fwd and bkwd functions and keys Data Command Intermediate nodes convert VCID Apply appropriate function with key Destroy Remove VCID entry
 Data Encryption Crypting Each node applies forward function with forward key to data moving in forward direction Applies backward function with backward key to data moving in backward direction Initiator proxy ”precrypts” ultimate forward msg by applying inverse functions in reverse order Intermediate nodes ”peel off” transforms applied by initiator proxy as data traverses route Data sent in backward direction is ”crypted” by routers along backward route Initiator proxy peels off these layers by applying inverse of backward transforms in forward route order
Data Encryption Crypting Each node applies forward function with forward key to data moving in forward direction Applies backward function with backward key to data moving in backward direction Initiator proxy ”precrypts” ultimate forward msg by applying inverse functions in reverse order Intermediate nodes ”peel off” transforms applied by initiator proxy as data traverses route Data sent in backward direction is ”crypted” by routers along backward route Initiator proxy peels off these layers by applying inverse of backward transforms in forward route order
 Loose Routing Route length is limited Can allow intermediates to add to route! Size of onion restricts number of intermediates But must not overwrite needed info! Loose Routing Initiator can add padding to end of onion, set maximum loose count values for intermediate nodes Intermediate can insert addtional hops on the way to the next prescribed node Intermediate must also crypt data as it passes through Can be used to repair route damage, or when initiator does not know a complete route
Loose Routing Route length is limited Can allow intermediates to add to route! Size of onion restricts number of intermediates But must not overwrite needed info! Loose Routing Initiator can add padding to end of onion, set maximum loose count values for intermediate nodes Intermediate can insert addtional hops on the way to the next prescribed node Intermediate must also crypt data as it passes through Can be used to repair route damage, or when initiator does not know a complete route
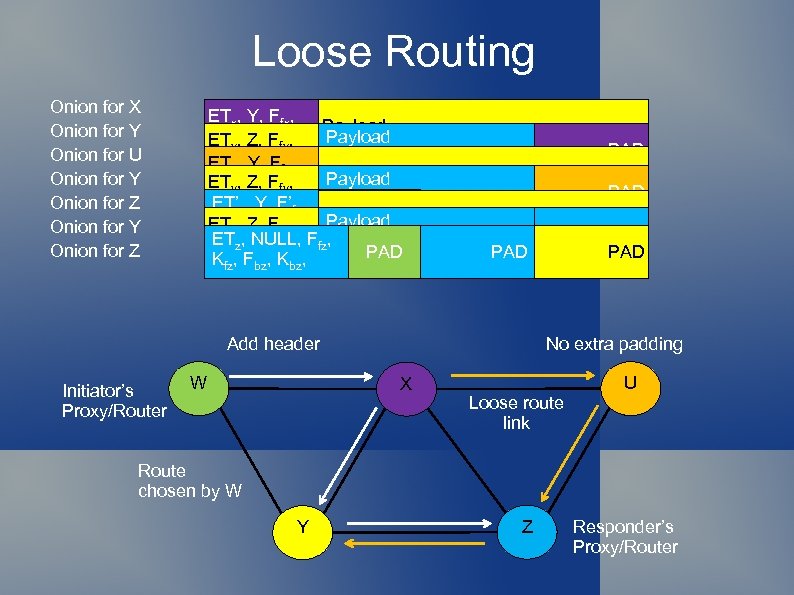 Loose Routing Onion for X Onion for Y Onion for U Onion for Y Onion for Z ETx, Y, Ffx, Payload Kfx, y, FZ, , Ffybx, Payload ET bx K , Kfy, u, FY, , Ffu, , ET by Kby Payload ETy Z, K , Kfu, , Fbu, Ffybu, Payload Kfy, z, by, Kby, , ET’ F Y, F’fz K’ y Z, F K’ Payload ETfz, F’bz, fy, bz, Payload ET , NULL, Kfy, z. Fby, Kby, Ffz, PAD Kfz, Fbz, Kbz, PAD PAD Add header Initiator’s Proxy/Router W PAD No extra padding X Loose route link U Route chosen by W Y Z Responder’s Proxy/Router
Loose Routing Onion for X Onion for Y Onion for U Onion for Y Onion for Z ETx, Y, Ffx, Payload Kfx, y, FZ, , Ffybx, Payload ET bx K , Kfy, u, FY, , Ffu, , ET by Kby Payload ETy Z, K , Kfu, , Fbu, Ffybu, Payload Kfy, z, by, Kby, , ET’ F Y, F’fz K’ y Z, F K’ Payload ETfz, F’bz, fy, bz, Payload ET , NULL, Kfy, z. Fby, Kby, Ffz, PAD Kfz, Fbz, Kbz, PAD PAD Add header Initiator’s Proxy/Router W PAD No extra padding X Loose route link U Route chosen by W Y Z Responder’s Proxy/Router
 Reply Onions Useful to allow recipient to reply after original circuit has been broken down VC no longer available for data transmission Allows responder to remain anonymous also Reply Onion Sent by initiator to responder Can be used as a ”preformed” onion by responder to set up a VC to initiator later Multiple can be sent to allow multiple such VCs Does not need to use the same path as the original VC used
Reply Onions Useful to allow recipient to reply after original circuit has been broken down VC no longer available for data transmission Allows responder to remain anonymous also Reply Onion Sent by initiator to responder Can be used as a ”preformed” onion by responder to set up a VC to initiator later Multiple can be sent to allow multiple such VCs Does not need to use the same path as the original VC used
 Reply Onions Looks like a forward onion Has same format, header information Treated the same as a forward onion by intermediates Here is where ”crypting” comes in handy! Forward and backward functions are indistinguishable Difference is that the payload tells the original initiator’s proxy all it needs to use the VC All the forward and backward functions along path Also indentifier for VC so the initiator can bind it to the reply onion it came from
Reply Onions Looks like a forward onion Has same format, header information Treated the same as a forward onion by intermediates Here is where ”crypting” comes in handy! Forward and backward functions are indistinguishable Difference is that the payload tells the original initiator’s proxy all it needs to use the VC All the forward and backward functions along path Also indentifier for VC so the initiator can bind it to the reply onion it came from
 Reply Onions Data are treated in the same way as in a VC set up by the original initiator in the forward direction Original responder just sends data Intermediates apply ”forward” function given Just use the functions given Original initiator applies all ”backward” functions Multiple reply onions can be set Multiple can even be broadcast! Just have to use an unused onion Onions expire, and duplicates are ignored
Reply Onions Data are treated in the same way as in a VC set up by the original initiator in the forward direction Original responder just sends data Intermediates apply ”forward” function given Just use the functions given Original initiator applies all ”backward” functions Multiple reply onions can be set Multiple can even be broadcast! Just have to use an unused onion Onions expire, and duplicates are ignored
 Attacks GPA can observe message flows No delays introduced, so timing matters! Near simultaneous opening of sockets a give-away Compromised nodes Initiator proxy bad – then all is revealed! One good intermediate complicates TA One bad intermediate can effect DOS Bad responder proxy – if can detect corrupted data, then earlier node can experimentally damage data Clock Synchronization Can result in DOS – onion expiry
Attacks GPA can observe message flows No delays introduced, so timing matters! Near simultaneous opening of sockets a give-away Compromised nodes Initiator proxy bad – then all is revealed! One good intermediate complicates TA One bad intermediate can effect DOS Bad responder proxy – if can detect corrupted data, then earlier node can experimentally damage data Clock Synchronization Can result in DOS – onion expiry


