e9e0fd953172683b81a97c0b55f79ab2.ppt
- Количество слайдов: 16

One way encryption system by Adi Sashkis and Yehezkel Horowitz Advisor Prof. Shlomi Dolev
Out line t t t Base concept Lattice Shortest Vector problem System definition Mathematical research Questions

Goal – one way encryption system t t t No pre-shared knowledge (only IP and port). Establish a secure tunnel with individuals (in spite of the fact that all can listen and no one answers). Sounds impossible?
Solution – one way encryption system t t The encryption power – computation gap. We assume that our system can perform the task faster than the advisory. This will give us a gap of time to pass the data in secure way. How?

Encryption system – concept t t Generate randomly a sequence of independent problems. Solve them one by one. Encrypt each problem with the solution of the previous problem. Thus, only who solve all the previous problems can start solve the current problem.

Lattice Shortest Vector Problem t t We need to randomly choose puzzles that are hard in average. Worst case-average case equivalence. Lattice Shortest Vector Problem is an NP problem in the average case [Ajtai 97]. Given matrix m·n above Zq – find a vector such that <matrix>·<vector>=<zero vector>. Notes: Ø The solution can’t be the zero vector. Miklos Ajtai
The system modes t t Symmetric mode – minimal solution Asymmetric mode – build-in solution
Symmetric mode t t t Both sides solve the problem generated by the encryptor. There is only lexicographically first among the minimal solutions. Both sides need to have powerful resources to satisfy the componential gap.
Asymmetric mode t t t Only the decryptor solve the problem generated by the encryptor. The encryptor don’t need powerful resources. How the encryptor know the solution?
. Asymmetric mode – cont t The encryptor have a build-in solution. No guarantee that this is the minimal solution, we can have more than one solution. How the decryptor will know which solution to choose?

. Asymmetric mode – cont t t The decryptor will build a tree-form database to manage all possible solutions and their derived decrypted problems. This can be huge task!

. Asymmetric mode – cont t t Mathematical research can minimize the solutions amount. Choose the matrix size and Zq wisely. The vector amount in the matrix have impact (exponentially) on the problem hardness. The vector length & q have impact on the solution amount. Need to choose m, n, q such that 2 m << qn

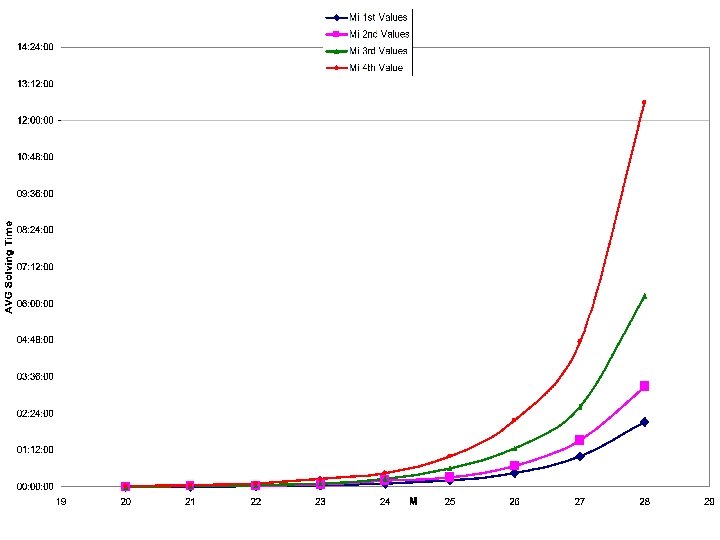
One way encryption system t t To fine tune the parameters, we run automated test program – this take a lot of time… The results we received matched our research’s estimations.
Questions? More information about our project you can find at: http: //www. cs. bgu. ac. il/~adihen/final. Project. htm
The End Thank you for listening us.
e9e0fd953172683b81a97c0b55f79ab2.ppt