f8d5f2e53e84c14fdd765b15e05aebfe.ppt
- Количество слайдов: 44


Objectives

Wireless Security Solutions

IEEE 802. 11 i

IEEE 802. 11 i (continued)

IEEE 802. 11 i (continued)

IEEE 802. 11 i (continued)

IEEE 802. 11 i (continued)

Wi-Fi Protected Access (WPA)
Wi-Fi Protected Access (WPA) (continued)

Wi-Fi Protected Access (WPA) (continued)
Wi-Fi Protected Access (WPA) (continued)

Wi-Fi Protected Access 2 (WPA 2)

Wi-Fi Protected Access 2 (WPA 2) (continued)

Wi-Fi Protected Access 2 (WPA 2) (continued)

Wi-Fi Protected Access 2 (WPA 2) (continued)

Transitional Security Model

Authentication

Authentication (continued)

Authentication (continued)

Authentication (continued)

WEP Encryption

WEP Encryption (continued)

Personal Security Model

WPA Personal Security

WPA Personal Security (continued)

WPA Personal Security (continued)

WPA Personal Security (continued)

WPA Personal Security (continued)

WPA Personal Security (continued)

WPA Personal Security (continued)

WPA 2 Personal Security
WPA 2 Personal Security (continued)

WPA 2 Personal Security (continued)

Enterprise Security Model

WPA Enterprise Security
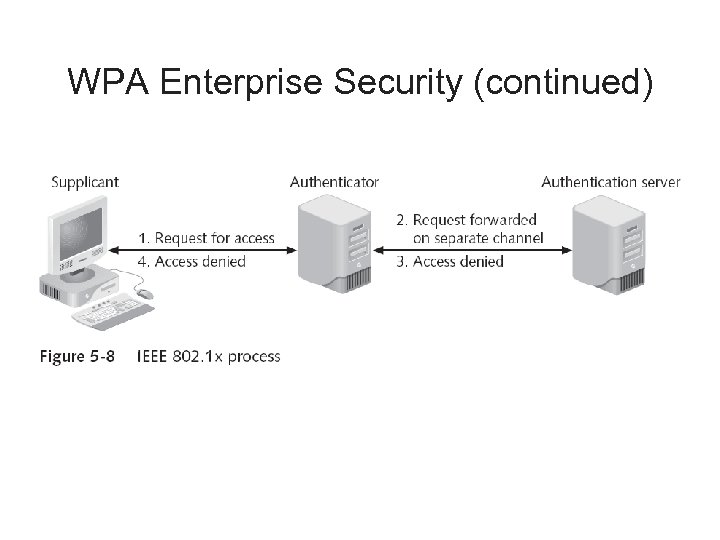
WPA Enterprise Security (continued)

WPA Enterprise Security (continued)

WPA Enterprise Security (continued)

WPA 2 Enterprise Security

WPA 2 Enterprise Security (continued)
WPA 2 Enterprise Security (continued)

Summary
Summary (continued)
f8d5f2e53e84c14fdd765b15e05aebfe.ppt