cfabf5820b86f2f85f013b7265811227.ppt
- Количество слайдов: 27
Objective and Secure Reputation-Based Incentive Scheme for Ad-Hoc Networks Dapeng Oliver Wu Electrical and Computer Engineering University of Florida (Joint work with Qi He and Pradeep Khosla at Carnegie Mellon University) 1
What’s the Problem? • Mobile ad hoc network (MANET) has no fixed infrastructure • Communications rely on intermediate nodes But why should intermediate nodes relay? • Need incentive mechanism for packet forwarding in non-cooperative MANET 2
Outline Problem and motivation Previous work § Reputation-based schemes § Pricing-based schemes Our scheme § Design objective § Basic scheme § Security enhancement Conclusion 3
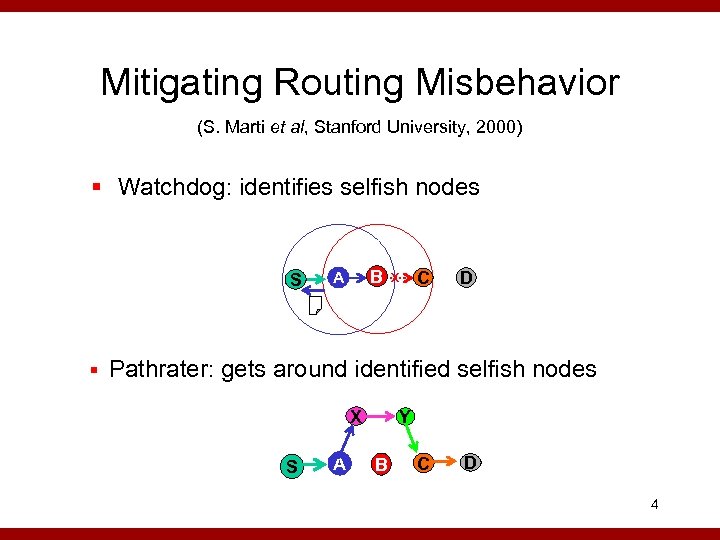
Mitigating Routing Misbehavior (S. Marti et al, Stanford University, 2000) § Watchdog: identifies selfish nodes S B A C X D § Pathrater: gets around identified selfish nodes X S A Y B C D 4

Pros and Cons (S. Marti et al, Stanford University, 2000) Pros: § Improve throughput Cons: § Unfairly makes well behaving nodes busier § Indirectly encourages misbehavior 5
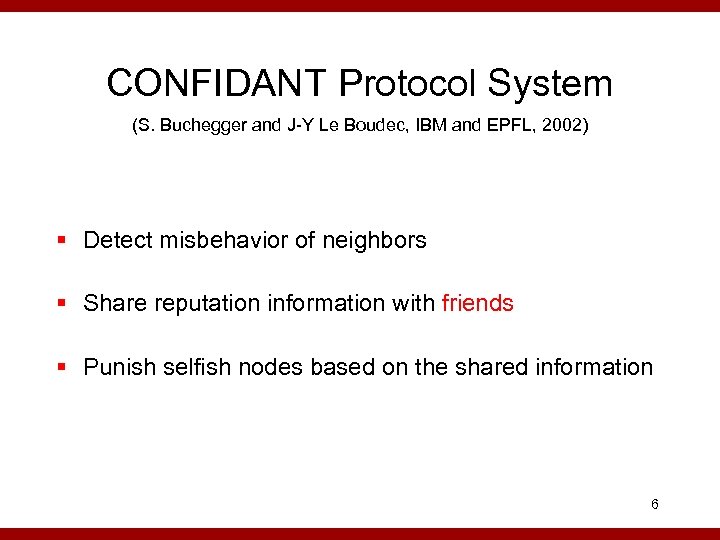
CONFIDANT Protocol System (S. Buchegger and J-Y Le Boudec, IBM and EPFL, 2002) § Detect misbehavior of neighbors § Share reputation information with friends § Punish selfish nodes based on the shared information 6

Pros and Cons (S. Buchegger and J-Y Le Boudec, IBM and EPFL, 2002) Pros § Use keys to authenticate nodes § Identify and punish misbehavior Cons § How to build a network of friends is not clear § Key distribution is not addressed § Globally shared reputation makes it not scalable 7
Where are we? Problem and motivation Previous work § Reputation-based schemes § Pricing-based schemes Our scheme § Design objective § Basic scheme § Security enhancement Conclusion 8

Enforcing Service Availability (L. Buttyan and Hubaux, Swiss Federal Institute of Technology -- EPFL, 2000) Scheme § Virtual currency (nuglet) § Centralized authority issuing nuglets § Same amount of packets to forward § Tamper-resistant hardware Problem: § Require balanced traffic 9
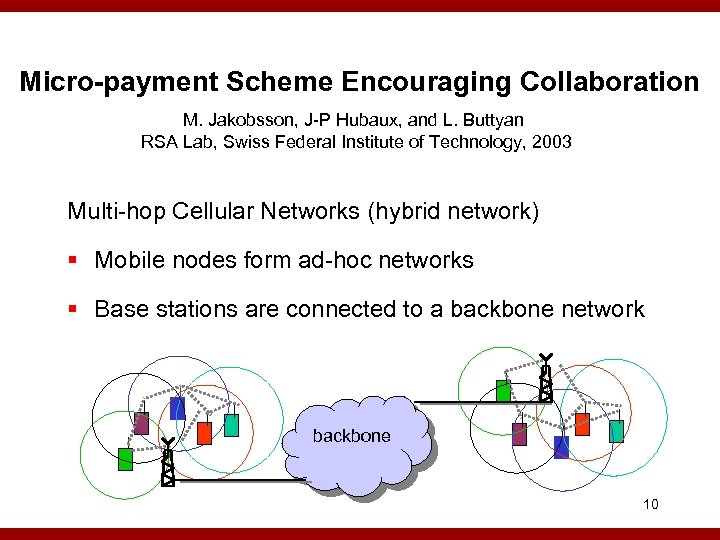
Micro-payment Scheme Encouraging Collaboration M. Jakobsson, J-P Hubaux, and L. Buttyan RSA Lab, Swiss Federal Institute of Technology, 2003 Multi-hop Cellular Networks (hybrid network) § Mobile nodes form ad-hoc networks § Base stations are connected to a backbone network backbone 10
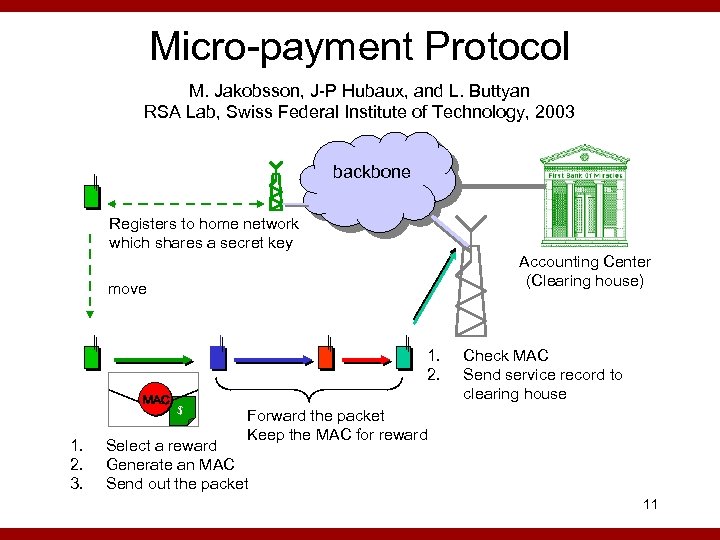
Micro-payment Protocol M. Jakobsson, J-P Hubaux, and L. Buttyan RSA Lab, Swiss Federal Institute of Technology, 2003 backbone Registers to home network which shares a secret key Accounting Center (Clearing house) move 1. 2. MAC 1. 2. 3. $ Check MAC Send service record to clearing house Forward the packet Keep the MAC for reward Select a reward Generate an MAC Send out the packet 11

Pros and Cons M. Jakobsson, J-P Hubaux, and L. Buttyan, RSA Lab, Swiss Federal Institute of Technology 2003 Pros § Symmetric key crypto: reduce computational cost § Payment aggregation: lower communication cost Cons § Substantial communication overhead § Requirement of infrastructure § Centralized trust authority 12
Where are we? Problem and Motivation Previous work § Reputation-based schemes § Pricing-based schemes Our scheme § Design objective § Basic scheme § Security enhancement Conclusion 13

Our Design Objectives § Practicality § Available technologies § Realistic context of ad-hoc networks § Efficiency § Affordable computational cost § Moderate communication overhead 14

Assumptions § Nodes are non-cooperative § No collusion among nodes § Broadcast transmission § All participating nodes desire to communicate § Invariant identity § Selfish but not malicious § Promiscuous mode (listening mode) 15
Where are we? Problem and motivation Previous work § Reputation-based schemes § Pricing-based schemes Our scheme § Design objectives § Basic scheme § Security enhancement Conclusion 16
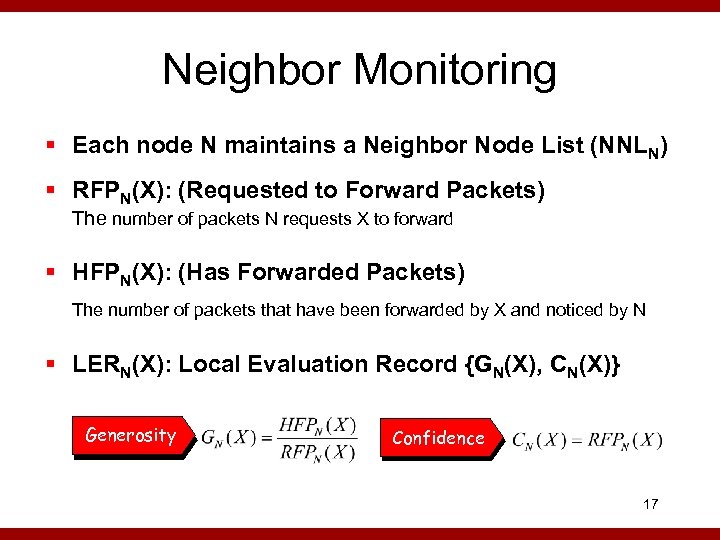
Neighbor Monitoring § Each node N maintains a Neighbor Node List (NNLN) § RFPN(X): (Requested to Forward Packets) The number of packets N requests X to forward § HFPN(X): (Has Forwarded Packets) The number of packets that have been forwarded by X and noticed by N § LERN(X): Local Evaluation Record {GN(X), CN(X)} Generosity Confidence 17
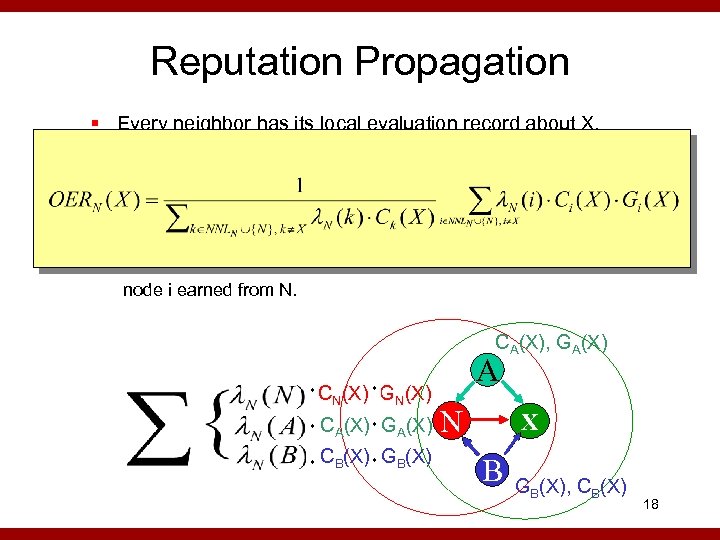
Reputation Propagation § Every neighbor has its local evaluation record about X. § Everyone periodically broadcasts its LER(X). § Compute Overall Evaluation Record OERN(X) if RFPN(X) 0 otherwise Credibility node i earned from N. CA(X), GA(X) * CN(X), GN(X) * CA(X), * GA(X) * A * CB(X), * GB(X) N X B GB(X), CB(X) 18
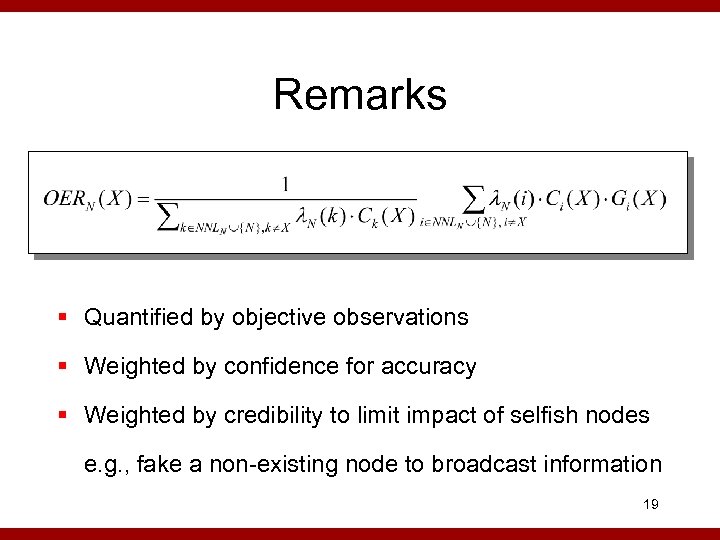
Remarks § Quantified by objective observations § Weighted by confidence for accuracy § Weighted by credibility to limit impact of selfish nodes e. g. , fake a non-existing node to broadcast information 19
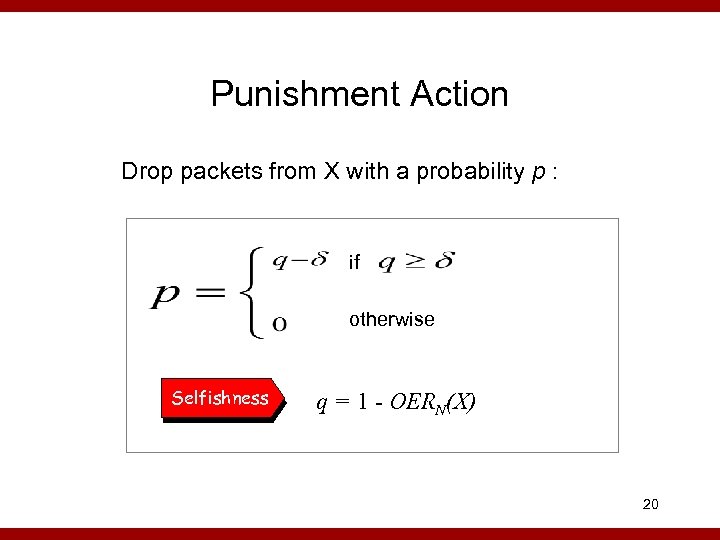
Punishment Action Drop packets from X with a probability p : if otherwise Selfishness q = 1 - OERN(X) 20
Simulation Setup § Network Simulator (NS-2) § Total number of nodes: 50 (5 selfish nodes) § Area: 670 X 670 m 2 § IEEE 802. 11 for medium access control § DSR for routing § CBR traffic: 1 packet/s § No. of connections: 10 § Connection duration: 10 s § Random waypoint mobility model § Max speed of movement: 20 m/s 21
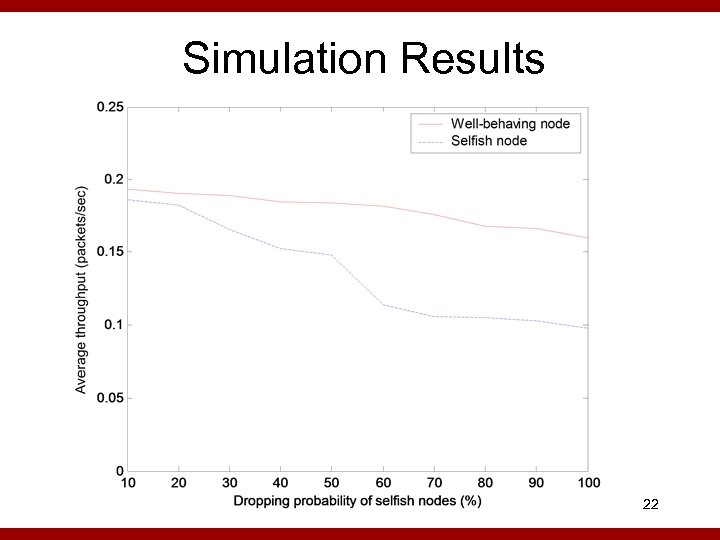
Simulation Results 22
Where are we? Problem and motivation Previous work § Reputation-based schemes § Pricing-based schemes Our scheme § Design objectives § Basic scheme § Security enhancement Conclusion 23
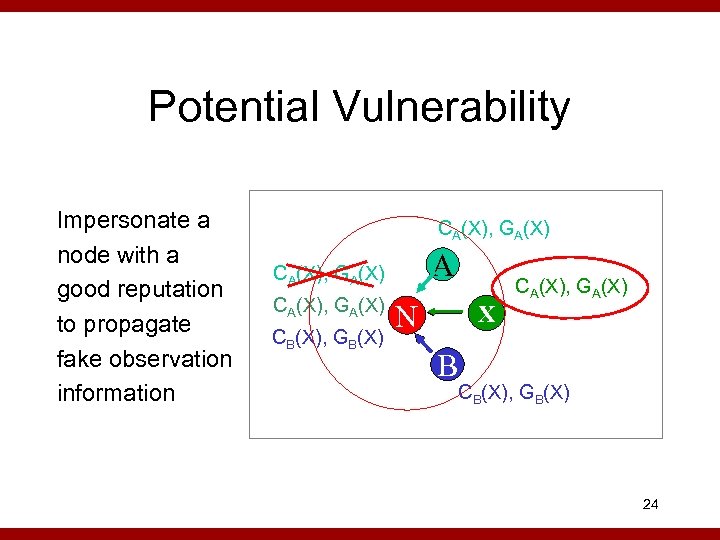
Potential Vulnerability Impersonate a node with a good reputation to propagate fake observation information CA(X), GA(X) A CA(X), GA(X) CB(X), GB(X) N X CA(X), GA(X) B CB(X), GB(X) 24
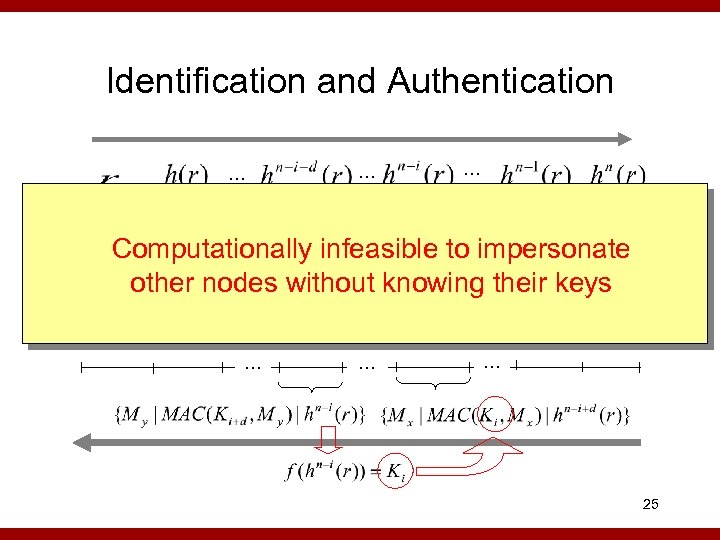
Identification and Authentication … … … f f f Computationally infeasible to impersonate f f other nodes without knowing their keys ID … … … 25

Conclusion § Incentive scheme with punishment mechanism • Reputation objectively quantified by observations • Punishment action quantitatively suggested by reputation • Effectively identify and punish selfish nodes § Security enhancement • Identification and authentication constructed collectively • Protection from impersonation 26

Thank you! 27
cfabf5820b86f2f85f013b7265811227.ppt