d06f0a141fadfeaebd9b08fcfd09a8de.ppt
- Количество слайдов: 20
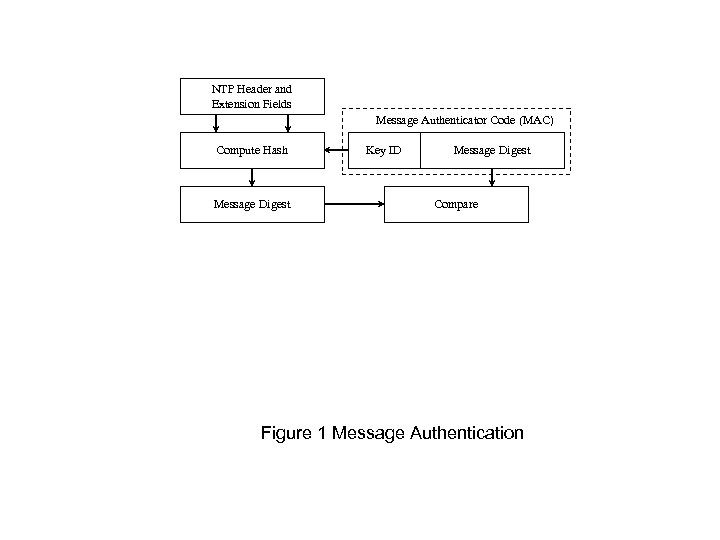 NTP Header and Extension Fields Message Authenticator Code (MAC) Compute Hash Message Digest Key ID Message Digest Compare Figure 1 Message Authentication
NTP Header and Extension Fields Message Authenticator Code (MAC) Compute Hash Message Digest Key ID Message Digest Compare Figure 1 Message Authentication
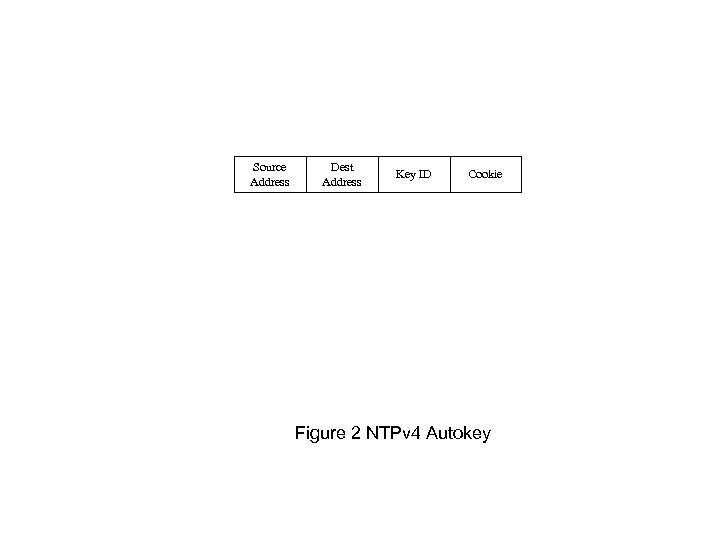 Source Address Dest Address Key ID Cookie Figure 2 NTPv 4 Autokey
Source Address Dest Address Key ID Cookie Figure 2 NTPv 4 Autokey
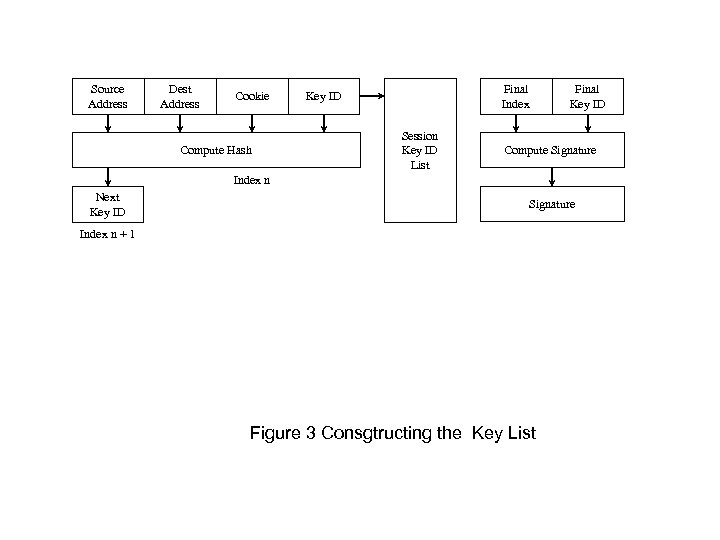 Source Address Dest Address Cookie Compute Hash Final Index Key ID Session Key ID List Final Key ID Compute Signature Index n Next Key ID Signature Index n + 1 Figure 3 Consgtructing the Key List
Source Address Dest Address Cookie Compute Hash Final Index Key ID Session Key ID List Final Key ID Compute Signature Index n Next Key ID Signature Index n + 1 Figure 3 Consgtructing the Key List
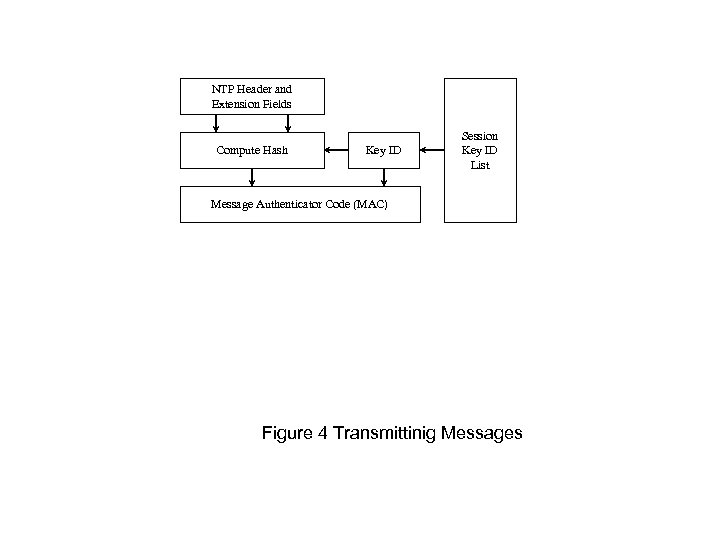 NTP Header and Extension Fields Compute Hash Key ID Session Key ID List Message Authenticator Code (MAC) Figure 4 Transmittinig Messages
NTP Header and Extension Fields Compute Hash Key ID Session Key ID List Message Authenticator Code (MAC) Figure 4 Transmittinig Messages
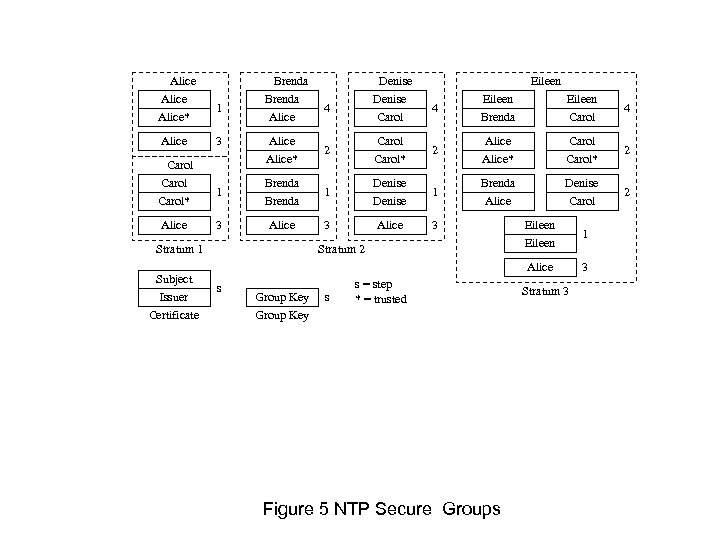 Alice* Alice Carol* Alice 1 3 Brenda Alice 4 Eileen Brenda Eileen Carol 4 Alice* 2 Carol* 2 Alice* Carol* 2 1 Brenda 1 Denise 1 Brenda Alice Denise Carol 2 3 Alice 3 Stratum 2 s Group Key s s = step * = trusted Figure 5 NTP Secure Groups Eileen 1 Alice Stratum 1 Subject Issuer Certificate Denise Carol 3 Stratum 3
Alice* Alice Carol* Alice 1 3 Brenda Alice 4 Eileen Brenda Eileen Carol 4 Alice* 2 Carol* 2 Alice* Carol* 2 1 Brenda 1 Denise 1 Brenda Alice Denise Carol 2 3 Alice 3 Stratum 2 s Group Key s s = step * = trusted Figure 5 NTP Secure Groups Eileen 1 Alice Stratum 1 Subject Issuer Certificate Denise Carol 3 Stratum 3
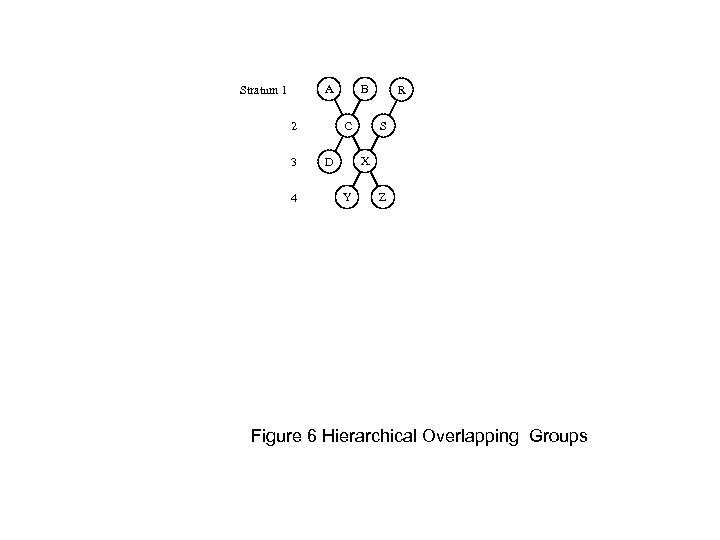 A Stratum 1 C 2 3 4 B R S X D Y Z Figure 6 Hierarchical Overlapping Groups
A Stratum 1 C 2 3 4 B R S X D Y Z Figure 6 Hierarchical Overlapping Groups
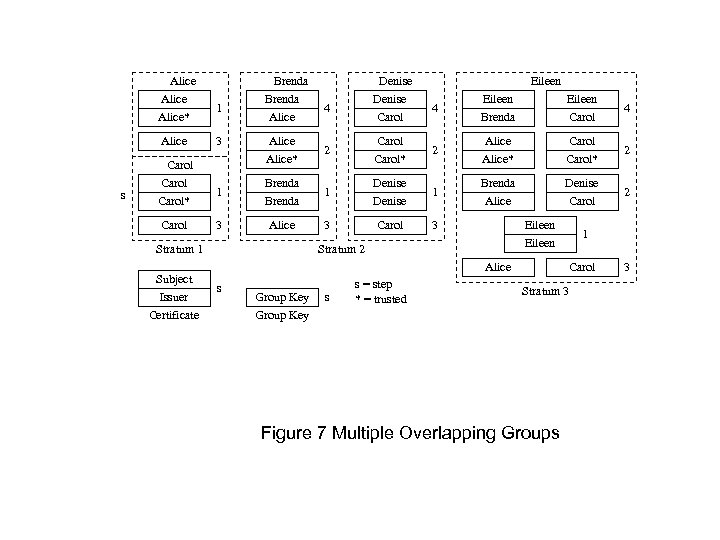 Alice* Alice s Carol* Carol 1 3 Brenda Alice 4 Eileen Brenda Eileen Carol 4 Alice* 2 Carol* 2 Alice* Carol* 2 1 Brenda 1 Denise 1 Brenda Alice Denise Carol 2 3 Alice 3 Carol 3 Stratum 1 Subject Issuer Certificate Denise Carol Eileen Stratum 2 Alice s Group Key s s = step * = trusted 1 Carol Stratum 3 Figure 7 Multiple Overlapping Groups 3
Alice* Alice s Carol* Carol 1 3 Brenda Alice 4 Eileen Brenda Eileen Carol 4 Alice* 2 Carol* 2 Alice* Carol* 2 1 Brenda 1 Denise 1 Brenda Alice Denise Carol 2 3 Alice 3 Carol 3 Stratum 1 Subject Issuer Certificate Denise Carol Eileen Stratum 2 Alice s Group Key s s = step * = trusted 1 Carol Stratum 3 Figure 7 Multiple Overlapping Groups 3
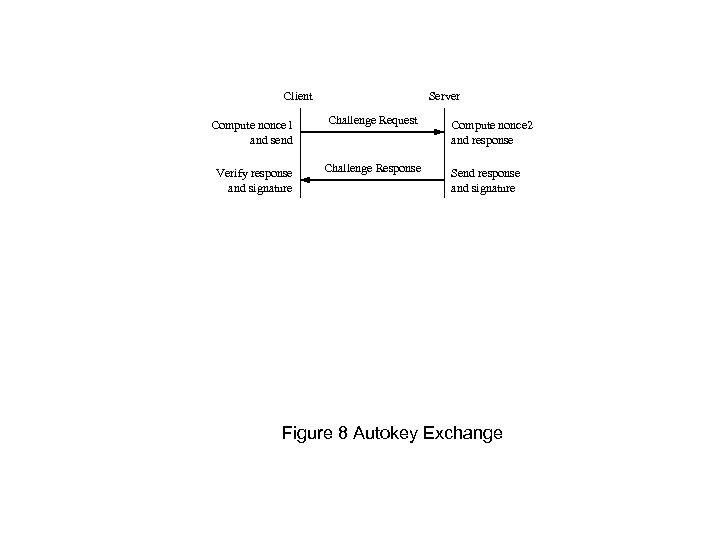 Client Server Compute nonce 1 and send Challenge Request Verify response and signature Challenge Response Compute nonce 2 and response Send response and signature Figure 8 Autokey Exchange
Client Server Compute nonce 1 and send Challenge Request Verify response and signature Challenge Response Compute nonce 2 and response Send response and signature Figure 8 Autokey Exchange
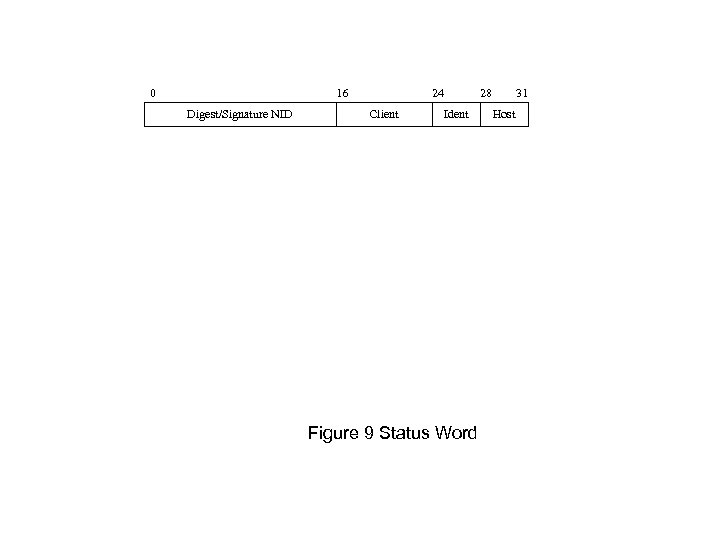 0 16 Digest/Signature NID 24 Client Ident Figure 9 Status Word 28 31 Host
0 16 Digest/Signature NID 24 Client Ident Figure 9 Status Word 28 31 Host
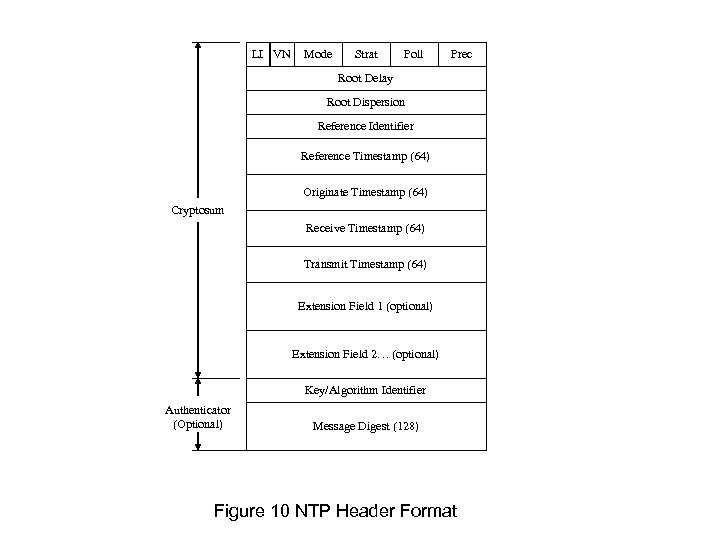 LI VN Mode Strat Poll Prec Root Delay Root Dispersion Reference Identifier Reference Timestamp (64) Originate Timestamp (64) Cryptosum Receive Timestamp (64) Transmit Timestamp (64) Extension Field 1 (optional) Extension Field 2… (optional) Key/Algorithm Identifier Authenticator (Optional) Message Digest (128) Figure 10 NTP Header Format
LI VN Mode Strat Poll Prec Root Delay Root Dispersion Reference Identifier Reference Timestamp (64) Originate Timestamp (64) Cryptosum Receive Timestamp (64) Transmit Timestamp (64) Extension Field 1 (optional) Extension Field 2… (optional) Key/Algorithm Identifier Authenticator (Optional) Message Digest (128) Figure 10 NTP Header Format
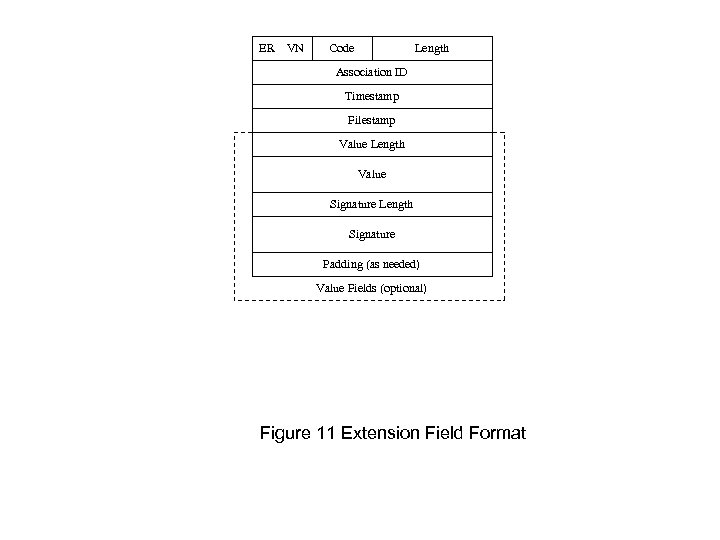 ER VN Code Length Association ID Timestamp Filestamp Value Length Value Signature Length Signature Padding (as needed) Value Fields (optional) Figure 11 Extension Field Format
ER VN Code Length Association ID Timestamp Filestamp Value Length Value Signature Length Signature Padding (as needed) Value Fields (optional) Figure 11 Extension Field Format
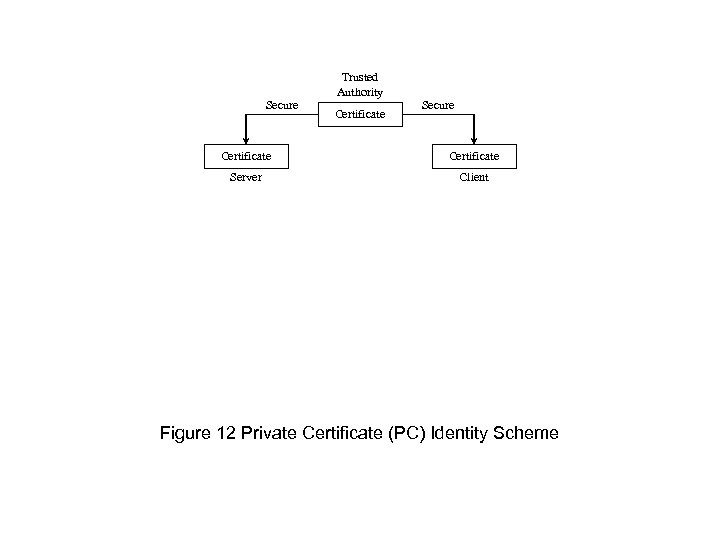 Trusted Authority Secure Certificate Server Client Figure 12 Private Certificate (PC) Identity Scheme
Trusted Authority Secure Certificate Server Client Figure 12 Private Certificate (PC) Identity Scheme
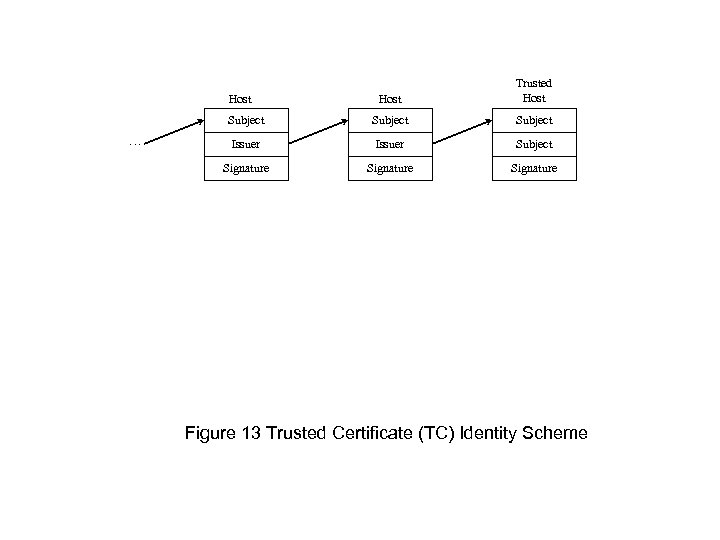 Host Trusted Host Subject Issuer Subject Signature Host … Figure 13 Trusted Certificate (TC) Identity Scheme
Host Trusted Host Subject Issuer Subject Signature Host … Figure 13 Trusted Certificate (TC) Identity Scheme
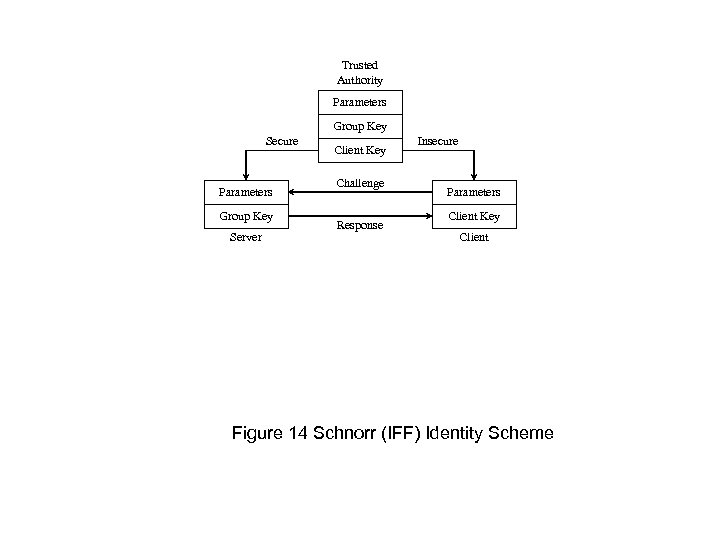 Trusted Authority Parameters Group Key Secure Parameters Group Key Server Client Key Challenge Response Insecure Parameters Client Key Client Figure 14 Schnorr (IFF) Identity Scheme
Trusted Authority Parameters Group Key Secure Parameters Group Key Server Client Key Challenge Response Insecure Parameters Client Key Client Figure 14 Schnorr (IFF) Identity Scheme
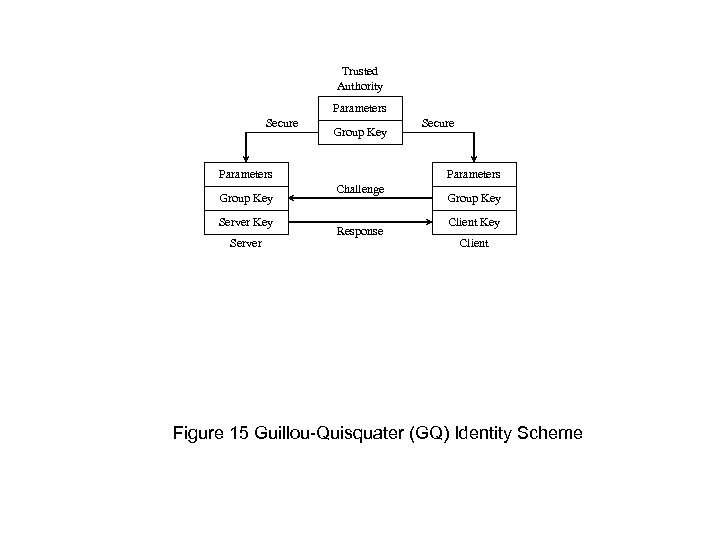 Trusted Authority Parameters Secure Group Key Parameters Group Key Server Secure Parameters Challenge Response Group Key Client Figure 15 Guillou-Quisquater (GQ) Identity Scheme
Trusted Authority Parameters Secure Group Key Parameters Group Key Server Secure Parameters Challenge Response Group Key Client Figure 15 Guillou-Quisquater (GQ) Identity Scheme
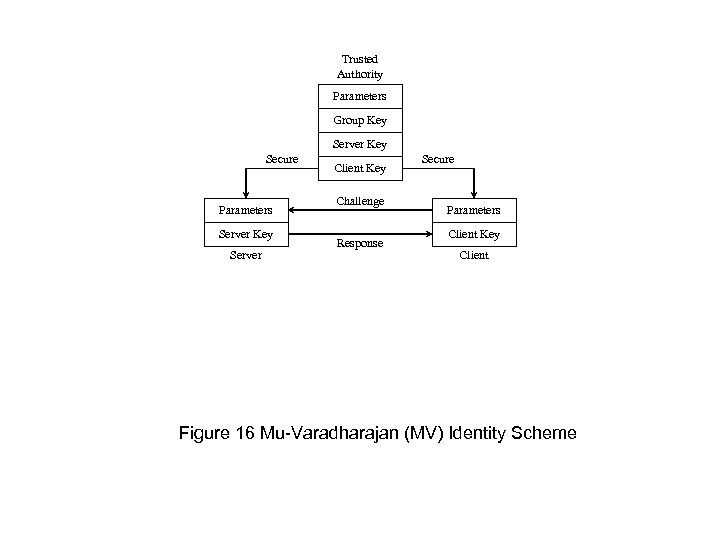 Trusted Authority Parameters Group Key Server Key Secure Parameters Server Key Server Client Key Challenge Response Secure Parameters Client Key Client Figure 16 Mu-Varadharajan (MV) Identity Scheme
Trusted Authority Parameters Group Key Server Key Secure Parameters Server Key Server Client Key Challenge Response Secure Parameters Client Key Client Figure 16 Mu-Varadharajan (MV) Identity Scheme
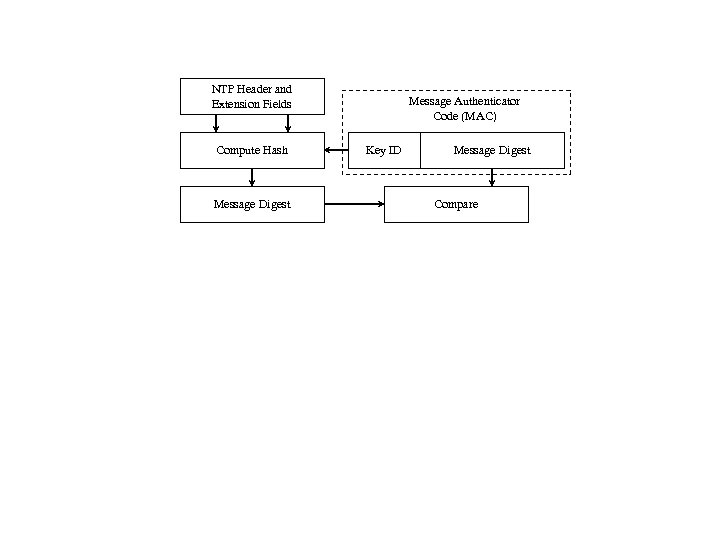 NTP Header and Extension Fields Compute Hash Message Digest Message Authenticator Code (MAC) Key ID Message Digest Compare
NTP Header and Extension Fields Compute Hash Message Digest Message Authenticator Code (MAC) Key ID Message Digest Compare
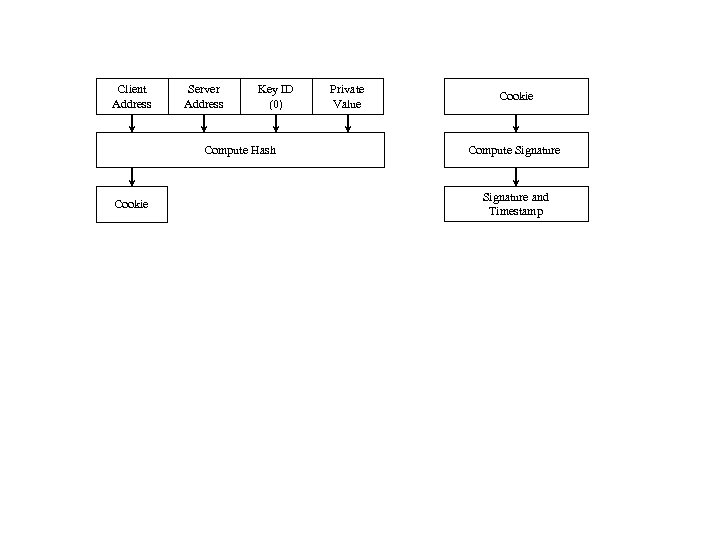 Client Address Server Address Key ID (0) Compute Hash Cookie Private Value Cookie Compute Signature and Timestamp
Client Address Server Address Key ID (0) Compute Hash Cookie Private Value Cookie Compute Signature and Timestamp
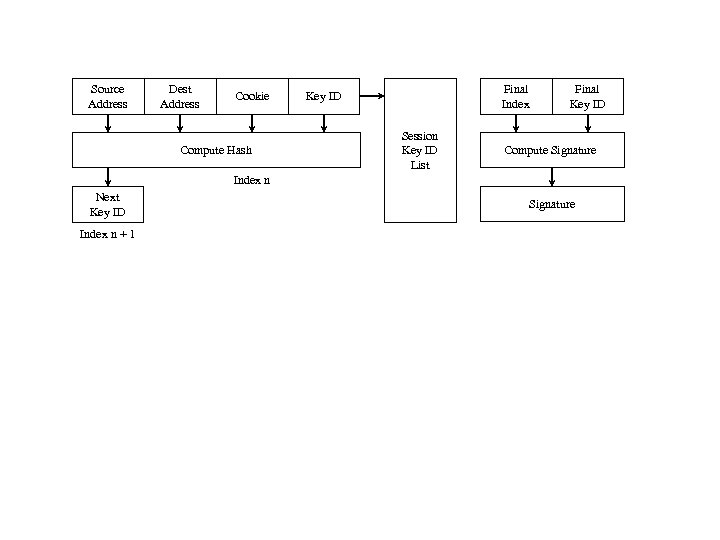 Source Address Dest Address Cookie Compute Hash Final Index Key ID Session Key ID List Final Key ID Compute Signature Index n Next Key ID Index n + 1 Signature
Source Address Dest Address Cookie Compute Hash Final Index Key ID Session Key ID List Final Key ID Compute Signature Index n Next Key ID Index n + 1 Signature
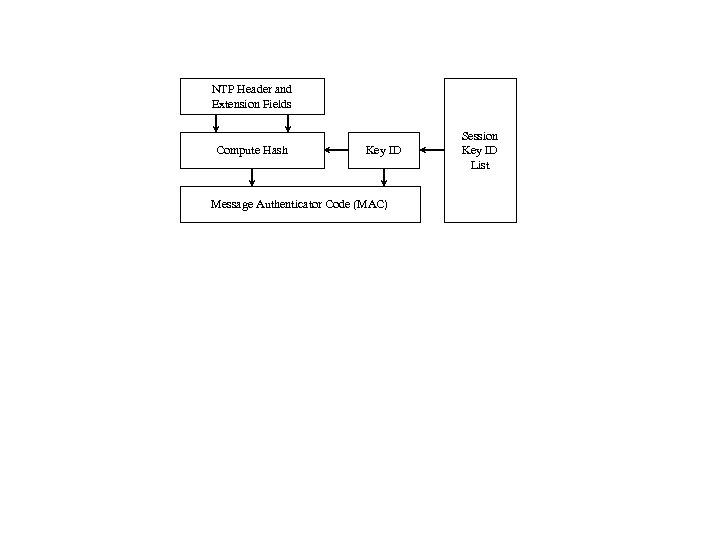 NTP Header and Extension Fields Compute Hash Key ID Message Authenticator Code (MAC) Session Key ID List
NTP Header and Extension Fields Compute Hash Key ID Message Authenticator Code (MAC) Session Key ID List


