3dc755e2ce6be2f1018b4a80b68e92de.ppt
- Количество слайдов: 11

NSF Middleware Initiative: Grid. Shib Tom Barton University of Chicago I 2 MM Fall 2004
NSF Middleware Initiative (NMI) Grant: Policy Controlled Attribute Framework • What: shibbolize NMI Grids • We call it “Grid. Shib” • Participants • • Von Welch, UIUC/NCSA (PI) Kate Keahey, UChicago/Argonne (PI) Frank Siebenlist, Argonne Tom Barton, UChicago • 2 years starting December 1, 2004 • Coordination already established with related JISC-funded project at Oxford I 2 MM Fall 2004 2
Critical mass of impending need §Two types of grid use cases: §Large grid, far-flung participants, several types of roles among them • Examples: NEESgrid, Earth System Grid, Tera. Grid, Grid 3 (Gri. Phy. N, i. VDGL, and PPDG) • Grid-mapfile approach doesn’t scale §Centralized access to campus grid resources for research computing • Examples: UChicago, USC, UAB I 2 MM Fall 2004 3

Enterprise middleware value proposition fits VOs too • Leverage Identity Provider operations at participants’ home organizations rather than duplicate Identity Provider activities within each Virtual Organization • Participants use familiar home-issued credentials • Ease resource provider’s burden by removing need to act as an Identity Provider too • Overall security & auditability is improved by locating these support functions with IT staff tasked specifically for such purposes I 2 MM Fall 2004 4

Time is finally right • Others are now trying non-browser-based shibbolization approaches roughly analogous to what we envision • Shibboleth & SAML have shown how to authorize the anonymous user • Sufficiently abstracted security related interfaces & services provided by NMI Grid componentry • Plug: all code elements in prospective solution are NMI components. We’re building on work of many people over 3+ years. I 2 MM Fall 2004 5
Grid-Shib integration essentials §Design principles • No modification to typical grid client applications • No change to shibboleth’s model of administrative and end-user maintenance of attribute release policies • Leverage high-quality campus Identity Provider operations §Accommodations for Grid shibbolization • Identity Provider Discovery (pull models) • Basic sequence of events (push models) • Use of an identifer in X. 509 certificate as a subject handle for use by the Attribute Authority I 2 MM Fall 2004 6
Project activities § Gather use cases and requirements § Extend and test Globus Toolkit, Grid. Logon, and Shibboleth Attribute Authority to enable 4 modes of operation 1. 2. 3. 4. User identified, attributes pulled User identified, attributes pushed User pseudonymous, attributes pulled User pseudonymous, attributes pushed I 2 MM Fall 2004 7
Highlighted elements of potential solution §Globus Toolkit 4. 0’s support of WSRF (Web Services Resource Framework) • Transportable End Point References, used to identify Attribute Authority and grid resource to each other §Grid. Logon extensions • Itself an extension of My. Proxy • Integrate with local authentication service • Cryptographically bind identified & anonymous X. 509 certificate pairs I 2 MM Fall 2004 8
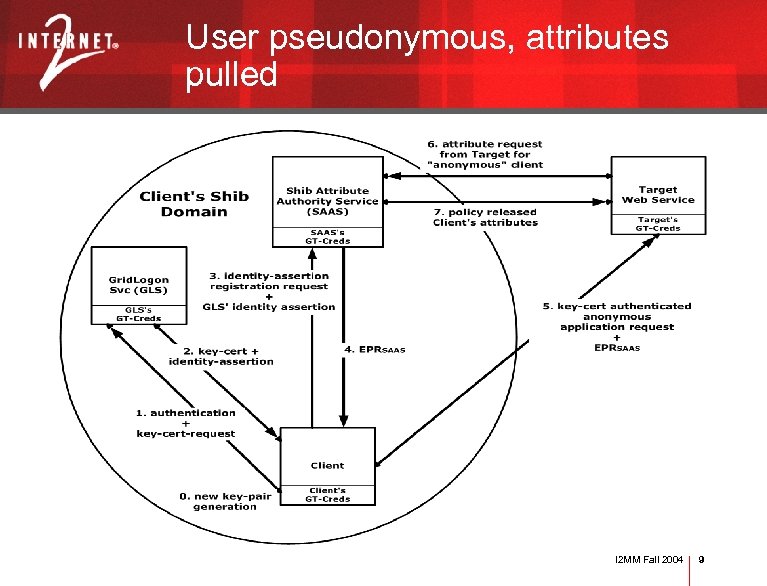
User pseudonymous, attributes pulled I 2 MM Fall 2004 9
Timeline §December 1, 2004: formal start §Year 1 • Basic integration: code supporting pull model with user identified §Year 2 • Advanced integration: code supporting push and user pseudonymity I 2 MM Fall 2004 10
Bigger picture proposition • Middleware value proposition applies to common infrastructure enabling run-time VO security services … • Identity management systems • Authentication services & certificate authorities • Attribute services like the Shibboleth Attribute Authority • … and potentially to common infrastructure for managing VO privileges & groups • VOMS • CAS • Permis • Signet • Grouper I 2 MM Fall 2004 11
3dc755e2ce6be2f1018b4a80b68e92de.ppt